In the context of data-flow diagrams (DFDs), the _____ includes arrows that show the direction of data movement.
Answers
In the context of data-flow diagrams (DFDs), the flowlines includes arrows that show the direction of data movement
A Data Flow Diagram is a graphical representation of a system's data flow and processing as well as the system's inputs and outputs. It visualizes how data flows through a system, providing a clear picture of how data is processed and moved from one stage to the next.
Flowlines are the connectors or lines in a DFD that depict the path of data movement from one system component to another. They're arrows that show the flow of data from the source to the destination.
Each flowline must have a label that identifies the data that it carries, and an arrowhead that shows the direction of the flow of data. Flowlines show the path that data takes from one location to another, and they indicate the data content of the movement.
Learn more about data flow at:
https://brainly.com/question/32260309
#SPJ11
Related Questions
Using more than one array to store related data is called _____________ arrays.
Answers
Answer:
Using more than one array to store related data is called parallel arrays.
Explanation:
I just did it and got 100% on the quiz
Using more than one array to store related data is called parallel arrays.
What is array?An array is a type of data structure used in computer science that holds a set of elements that are all uniquely recognised by at least one array index or key.
An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple.
In parallel arrays, a collection of data is represented by two or more arrays, where each corresponding array index represents a field that matches a particular record.
For instance, the array items at names and ages would explain the name and age of the third person if there were two arrays, one for names and one for ages.
Thus, the answer is parallel array.
For more details regarding parallel array, visit:
https://brainly.com/question/27041014
#SPJ6
Consider the following JavaScript program:var x, y, zfunction sub1 () {var a, y, z,function sub2 () {......}......}function sub3 () {var a, x, v;;;;;;}List all the variables, along with the program units where they are declared, that are visible in the bodies of sub1, sub2, and sub3, assuming static scoping is used.
Answers
Using static scoping, the visibility of variables is determined by the nesting structure of functions.
Therefore, the variables visible in the bodies of sub1, sub2, and sub3 are as follows:
sub1:
Declared variables: a (in sub2), y, z
Visible variables: a (in sub2), y, z, x (in sub3), v (in sub3)
sub2:
Declared variables: none
Visible variables: a (in sub2), y (in sub1), z (in sub1), x (in sub3), v (in sub3)
sub3:
Declared variables: a, x, v
Visible variables: a, x, v, y (in sub1), z (in sub1)
Note that variables declared in sub1 and sub3 are not visible in sub2 since sub2 is nested inside sub1, and sub3 is not visible in sub1 since it is not nested inside sub1. Also, the variable a in sub2 and the variable a in sub1 are different variables since they have different scopes.
Learn more about static scoping here:
https://brainly.com/question/30736807
#SPJ11
What is shoulder browsing? A. accessing someone else’s computer without permission B. deceptively observing people type in personal information C. distributing illegal software D. using internet search engines for information
Answers
Essentially, think of it as someone standing behind you, looking over your shoulder, watching everything you do on a computer.
Answer:
b
Explanation:
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
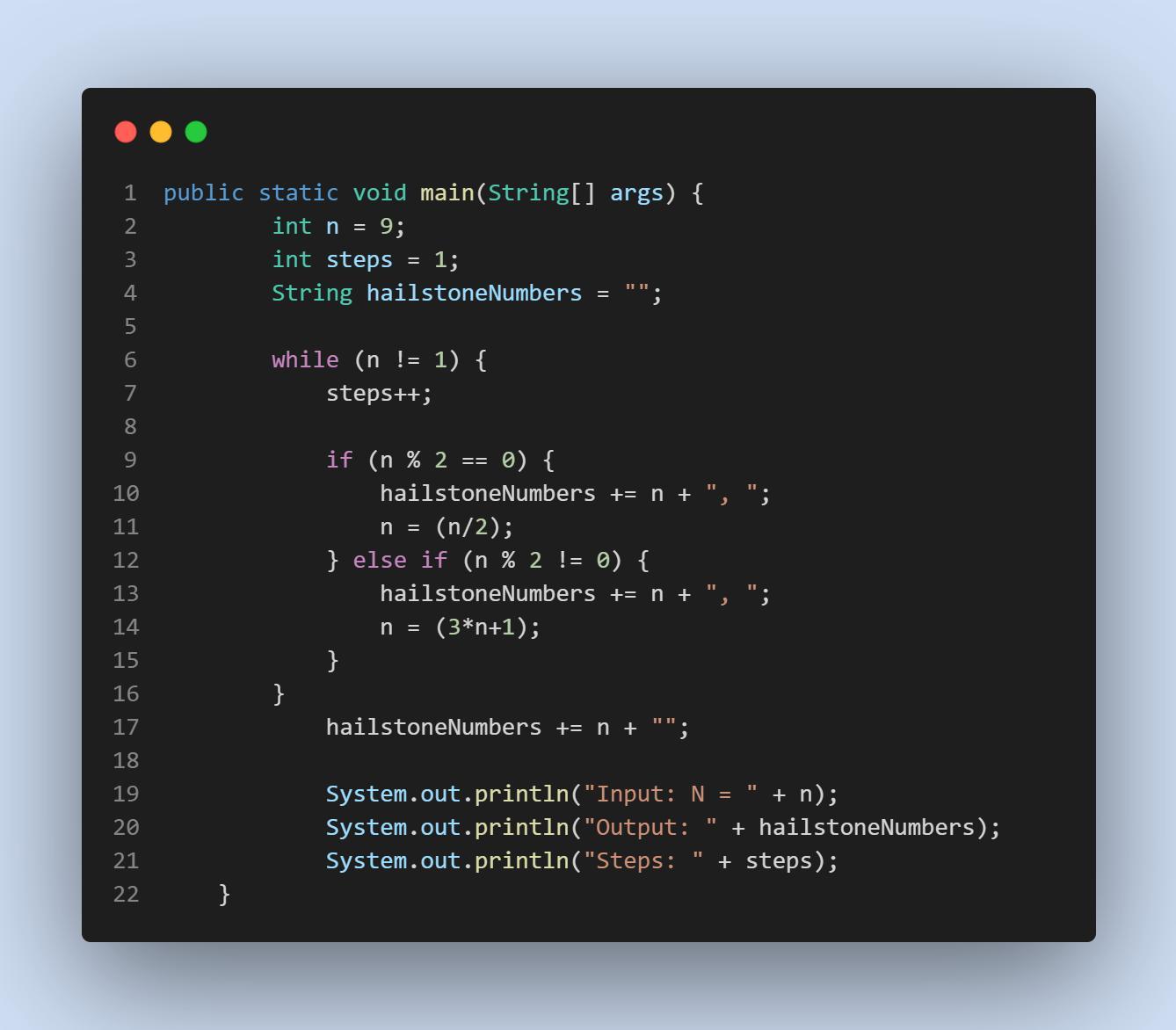
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
Which item best describes fiber optic transmission?
a
analog signals sent through tiny glass strands
b
signals carried on electromagnetic waves
c
light pulses sent through tiny glass strands
d
light pulses sent through copper wires
Answers
Answer:
a
Explanation:
analog signal sent through tiny glass strands
which of the following is the best example of an installation issue
Answers
Answer:
A user made an error while trying to set up a software program.
Answer:
A computer can't find the file that it needs to perform an operating system function. A computer displays error messages, and then the Blue Screen of Death appears. A user made an error while trying to set up a software program.
Explanation:
A software development company has created an application called FileCleanUp. When the application is run on a user device, it searches for all files (including pictures, videos, and documents) that have not been accessed in the past month, stores them on the company’s Web server, and deletes them from the user device. The application runs once each day. Users have the ability to manually retrieve files from the server if they are needed.
Which of the following is most likely to be a harmful effect of using FileCleanUp?
A. It prevents users from accessing frequently used files when there is no Internet connectivity.
B. It prevents users from accessing infrequently used files when there is no Internet connectivity.
C. It prevents users from accessing frequently used files when there is reliable Internet connectivity.
D. It prevents users from accessing infrequently used files when there is reliable Internet connectivity.
Answers
Answer:
B
Explanation:
The app will delete files that have not been accessed in the past month and store them on a web server. This means that the user cannot access those files unless they have an internet connection
The app will delete files that have not been accessed in the past month and store them on a web server. This means that the user cannot access those files unless they have an internet connection.
What is Software development?Supercomputing and other computing methods are sometimes used interchangeably. Yet, there are times when the synonyms aren't clear. To assist clarify some similarities and differences between various computer types, here are some common analogies.
While supercomputing typically refers to the process of complex and massive calculations used by supercomputers, high-performance computing (HPC) is the utilization of several supercomputers to execute difficult and huge computations.
Supercomputers are often known as parallel computers since they can perform parallel processing. Parallel processing is the simultaneous use of many Processors to solve a single calculation.
Therefore, The app will delete files that have not been accessed in the past month and store them on a web server. This means that the user cannot access those files unless they have an internet connection.
To learn more about Software, refer to the link:
https://brainly.com/question/985406
#SPJ6
what is the storage of a modern hard disk drive?
Answers
Answer:
80 gigs of storage
Explanation:
it gives a bunch of room because of the calculations the vomputer
"please help i have exam
Discuss three phases of social media marketing maturity.
Answers
The three phases of social media marketing maturity are: 1. Foundation Phase 2. Growth Phase 3. Optimization Phase
1. Foundation Phase: In this phase, businesses establish their presence on social media platforms and focus on building a solid foundation for their marketing efforts. They create social media accounts, develop a consistent brand voice, and start engaging with their audience. The primary goal is to increase brand awareness and establish a basic level of social media presence.
2. Growth Phase: During this phase, businesses expand their social media strategies and start leveraging the full potential of social media marketing. They focus on growing their audience, increasing engagement, and driving traffic to their website or physical stores. This phase involves implementing more advanced strategies such as content marketing, influencer partnerships, and targeted advertising campaigns.
3. Optimization Phase: In the optimization phase, businesses refine their social media strategies based on data-driven insights and continuous improvement. They use analytics tools to measure the effectiveness of their campaigns, identify areas for improvement, and optimize their social media content and advertising strategies. This phase emphasizes the importance of data analysis, testing, and ongoing optimization to achieve better results and maximize return on investment.
The three phases of social media marketing maturity represent a progression from establishing a basic presence to achieving strategic growth and continuous optimization. As businesses advance through these phases, they develop a deeper understanding of their target audience, refine their messaging, and refine their tactics to drive meaningful results from their social media marketing efforts.
To learn more about website click here: brainly.com/question/32113821
#SPJ11
Victor and Ellen are software engineers working on a popular mobile app. Victor has been in his position for 10 years longer than Ellen, who is a recent graduate. During the development of a new feature, Ellen expressed her concern that VIctor's purpose code would create instability in the app. Victor told Ellen he would address her concern with their supervisor. When Victor met privately with his supervisor, he claimed that he had discovered the problem, and that Ellen had dismissed it. Which principle of the Software Engineering Code of Ethics has Victor violated?A. Principle 6: Profession B. Principle 7: Colleagues C. Principle 3: Product D. Principle 8: Self
Answers
Victor has violated Principle 7: Colleagues of the Software Engineering Code of Ethics by making false statements to their supervisor about Ellen's dismissal of a concern related to the app's stability.
Victor's actions violate Principle 7: Colleagues of the Software Engineering Code of Ethics. This principle emphasizes the importance of respecting and supporting colleagues and fostering a positive working environment. By falsely claiming that Ellen dismissed a concern about the app's stability, Victor has undermined trust and collaboration within the team.
The principle encourages software engineers to be honest and transparent in their communication with colleagues. Victor's dishonesty not only reflects poorly on his professional conduct but also hampers effective teamwork and the pursuit of quality software development.
In this situation, it would have been more appropriate for Victor to honestly communicate with his supervisor about the concern raised by Ellen, without misrepresenting her position. By doing so, he would have upheld the ethical principles of professionalism, integrity, and respectful interaction with colleagues, fostering a supportive and collaborative work environment.
Learn more about Software here: https://brainly.com/question/985406
#SPJ11
suppose a network could gaurantee that all delivered packets were delivered in order. if a reliable transport protocol designer wanted to simplify the transport layer for this network, what could they do
Answers
When there is a reliable transport protocol designer They can make use of the TCP because it is one that guaranteed delivery.
What is the TCP?TCP is known to be one that has been set up as a kind of built-in systems. Its role is to look for errors and to help to guarantee data delivery in the order it was sent.
It is one that makes a perfect protocol for transferring information such as still images, data files, and others.
Learn more about transport protocol from
https://brainly.com/question/26284086
which command can an administrator execute to determine what interface a router will use to reach remot netowrks
Answers
Determine the path between two connections by using the traceroute command. A connection to another device frequently needs to pass via several routers.
How do I get my Cisco router's interface status?Use the show interface summary command to provide a summary of the system interfaces' details. There are no arguments or keywords for this command. Use the show interface command to display the system interfaces' details. information about the redundancy management interface is displayed in full.
What router command would a system administrator enter to check whether the exit interface was operational?The show is interface short command can be used by the network administrator to check that the interface connected to the next hop address or the exit interface is operational. To check if the next hop address is reachable, use the ping command. The routing table is displayed via the show IP route command.
to know more about routers here:
brainly.com/question/29768017
#SPJ4
The standard form of a linear programming problem will have the same solution as the original problem. True or false?.
Answers
THE BONUS QUESTION PART FOUR:
what is the most popular game that's lived for soo long
Answers
Answer:
Senet
Explanation:
The ____________________ keywords create a join automatically between two tables, based on columns with matching names.
Answers
The NATURAL JOIN keywords create a join automatically between two tables, based on columns with matching names.
The NATURAL JOIN operation is a type of join in SQL that eliminates the need to specify the join condition explicitly. It matches the columns with the same name in the two tables and performs the join based on those matching columns. It effectively combines rows from the two tables where the values in the matching columns are equal. By using NATURAL JOIN, you can simplify the syntax of your SQL query and avoid explicitly specifying the join condition. It can be convenient when you have tables with common column names and want to join them based on those common columns.
Learn more about NATURAL JOIN here:
https://brainly.com/question/30168153
#SPJ11
what actions can be performed via voice commands using 2022 sentra’s siri® eyes free?
Answers
New mobile cars produce nowadays often have new features that follows it. The actions that can be performed via voice commands using 2021 Sentra's Siri® Eyes Free are;
Send and receive text messagesMake and receive calls
Select and play music
Siri® Eyes Free command can be used to play music, report on the news, show movies, play games, and give us navigation from one place to the other.
It ha been made available in some selected cars and it often use one's voice to control features of your iPhone without viewing or touching the phone.
Learn more from
https://brainly.com/question/13429053
QUESTION
Which weld type is shaped like a right triangle and is commonly used to make lap joints,
corner joints, and T-joints?
POSSIBLE ANSWERS:
O Slot weld
O Fillet weld
O Plug weld
O Groove weld
Answers
Answer:
The weld that is shaped like a right triangle and is commonly used to make lap joints corner joints, and T-joints is;
Fillet weld
Explanation:
Fillet welds are defined as welds that have a cross section that is approximately triangular in shape that is used for joining two surfaces that form a perpendicular of near perpendicular alignment to each other in joint configurations including a lap joint, T-joint, and corner joint, such that the cross section of the weld is approximately the same as a right triangle.
suppose the keys 3, 4, 45, 21, 92, 12 are inserted into a bst (binary search tree) in this order. what is the inorder traversal of the elements?
Answers
The inorder traversal of the elements in the binary search tree (BST) with the keys 3, 4, 45, 21, 92, 12 inserted in that order is: 3, 4, 12, 21, 45, 92.
In a BST, the inorder traversal visits the nodes in ascending order. Starting from the root, the left subtree is explored first, then the current node is visited, and finally, the right subtree is traversed.
In this case, the keys are inserted in the order of 3, 4, 45, 21, 92, 12. The initial key, 3, becomes the root of the tree. The next key, 4, is greater than 3, so it becomes the right child of 3. The key 45 is greater than 3 and 4, so it becomes the right child of 4. The key 21 is less than 45 but greater than 4, so it becomes the left child of 45. The key 92 is greater than 45, so it becomes the right child of 45. Finally, the key 12 is less than 45 and 21, so it becomes the left child of 21.
The inorder traversal of the BST results in the sorted order of the elements: 3, 4, 12, 21, 45, 92.
learn more about binary here
https://brainly.com/question/30226308
#SPJ11
Part B
The store owner put 8 T-shirts on clearance. The T-shirts were originally priced at $18.00 each. The owner marked down the price of the
T-shirts by 35%
How much money did the store owner receive for selling all 8 T-shirts? $50.40
$93.60
$116.00
a $141.20
Answers
Answer:
$93.60
Explanation:
Given the following data;
Number of T-shirts = 8
Cost price = $18 each
Discount = 35%
To find the selling price;
First of all, we would calculate the price after the discount.
Discount price = 35/100 × 18
Discount price = 630/100
Discount price = $6.3
Now, we find the selling price for each;
Selling price = cost price - discount price
Selling price = 18 - 6.3
Selling price = $11.7
Total revenue = selling price * number of shirts
Total revenue = 11.7× 8
Total revenue = $93.60
Therefore, the store owner received $93.60 for selling all 8 T-shirts.
Use wireshark to capture packets on the enp2s0 interface for five seconds. analyze the wireshark packets to determine whether arp poisoning is taking place. use the 192.168.0.2 ip address to help make your determination. answer the questions.
Answers
In the case above, the Questions that need to be answered is:
"What is the MAC address of the 1st responding device and the answer will be: 00:00:1B:11:22:33"The second question will be "What was the MAC address of the duplicate responding device and the answer will be 00:00:1B:33:22:11".How do you use wireshark to capture packets?The steps are:
Do Open Wireshark and then one can go to under Capture folder and then click on enp2so.Click on Blue fin to start capture.In about 5 seconds after that operation, , click red box to stopLook at the Apply a display filter type arp and click on Enter to depict those packetsLooking at the Info column, you will see lines having the 192.168.0.2 IP. Then Answer questions above.Learn more about wireshark from
https://brainly.com/question/13139168
#SPJ1
a helpdesk operator is trounbleshooting issues on a windows client and wants to try to flush their dynamic ip address so that they can pull another one. which command will help the helpdesk operator do this?
Answers
The command that will help the helpdesk operator flush the dynamic IP address on a Windows client is ipconfig /release.
What is a dynamic IP address?A dynamic IP address is a type of IP address that is assigned to networked devices dynamically by the DHCP (Dynamic Host Configuration Protocol) server. The DHCP server assigns a new IP address every time the computer connects to the network.
The DHCP client sends a DHCP release message to the server with the assigned IP address when the device is disconnected from the network. In order to flush the dynamic IP address, a command is used. The command is "ipconfig /release." It allows the helpdesk operator to release the current IP address from the client device and get a new IP address from the DHCP server, which would help them troubleshoot their problems effectively.To release the current dynamic IP address, type the following command at the command prompt and press Enter:
ipconfig /release.Learn more about DHCP: https://brainly.com/question/7584053
#SPJ11
Which THREE of the following are examples of formatting data?
changing the color of a cell
changing the color of text in a cell
entering a formula to find the total of the numbers in a column
making the spreadsheet software interpret a number as a dollar amount
increasing the height of a row
Answers
Answer:
changing the color of a cell
changing the color of text in a cell
increasing the height of a row
Answer:
The answers are:
Changing the color of a cell
Changing the color of text in a cell
Making the spreadsheet software interpret a number as a dollar amount
Explanation:
I got it right on the Edmentum test.
for Jenny's personal computer?
id videos. Which operating
system would be appropriate Jenny's needs to buy a computer to create word documents, make presentations, listen to music, and watch movies and videos.
OA. UNIX
O B. Linux
O C. Microsoft Windows
O D. MS-DOS
Answers
Answer: C
Explanation: Microsoft Windows would be the most viable option here because UNIX and Linux are used for server-side applications, and MS-DOS is an old operating system which is not supported anymore. There is also the Microsoft 365 suite on Microsoft Windows, which can allow Jenny to make presentations using powerpoint, and edit videos.
Error-correcting codes are used in order to compensate for errors in transmission of messages (and in recovery of stored data from unreliable hardware). You are on a mission to Mars and need to send regular updates to mission control. Most of the packets actually don't get through, but you are using an error-correcting code that can let mission control recover the original message you send so as long as at least 1024 packets are received (not erased). Suppose that each packet gets erased independently with probability 0.7. How many packets should you send such that you can recover the message with probability at least 99% Use the Central Limit Theorem to approximate the answer, using the continuity correction. Your answers should be correct to 4 decimal places.
Answers
The origin of the transaction either transmits a data packet at that point or indicates that it has no data to deliver.
The transaction's origin then either transmits a data packet or says it has no data to deliver. Transmission of handshake packets If the transmission was successful, the target device replies with a handshake packet. Message and stream transfers are both supported by USB.
Packet switching is the way through which the internet works, it comprises transmission of packets of data between devices over a common network. For instance, you might send an email to a buddy or the school web server might send you a web page through the internet.
To learn more about data packet transmission refer to:
brainly.com/question/14219758
#SPJ1
Which system procedure is normally done with both hand valves opened on a gauge manifold connected to a refrigeration system?
Answers
Answer:
The answer is "Evacuation".
Explanation:
The evacuation in coolants was its removal from the coolant of heat, air, and non-condensable toxic gases. Its seal HVAC system is drawn to a vacuum and use a pressure washer throughout this process.
It loses the air and water vapor throughout the coolant point is called it. The two primary goals are accomplished by evacuating, that are eliminates content and hydrates.Answer:
the answer is c i belive
Explanation:
i belive this is the answer good luck :>
True or False: Cookies placed on a visitor's browser can include enough information to instruct an ad network which types of products a web user was interested in purchasing.
Answers
The statement "Cookies placed on a visitor's browser can include enough information to instruct an ad network which types of products a web user was interested in purchasing" is true.
What are cookies?Cookies are the small containers of data that are used in websites, when a person opens a website, and it accepts the cookies, much information of the users is got by the websites.
Thus, the statement is true.
Learn more about cookies
https://brainly.com/question/14102192
#SPJ1
Latonya wants to include a website link in her newsletter so readers can click the link and go straight to the website. What kind of formatting does she need to use
Answers
Based on the information given the kind of formatting she need to use is hyperlink.
Hyperlink is link that enables users or readers to go directly to another website or another webpage.
Hyperlink can be included in a website in form of text or in form of a bookmark which help to lead user to another page once the user click on the link.
This link can be included in a webpage or newsletter to serve as a reference for user and they are often underlined or may include "click here".
Inconclusion the kind of formatting she need to use is hyperlink.
Learn more about hyperlink here:https://brainly.com/question/3027709
A hacker is trying to gain remote access to a company computer by trying brute force password attacks using a few common passwords in conjunction with multiple usernames. what specific type of password attack is the hacker most likely performing?
Answers
Answer: Password Spraying Attack
Explanation: A password spraying attack happens in two steps. An attacker acquires a list of usernames, then attempts logins across all usernames using the same password. The attacker repeats the process with new passwords until the attack breaches the target authentication system to gain account and systems access.
HELP I WILL MARK BRAINLIEST!
Which of the following are correct details of the early life of the Wright brothers? You may choose more than one
answer.
The brothers had other mechanics create engines for their airplanes
The brothers worked in Dayton, Ohio
The brothers constructed gliders in their free time
The brothers operated a bicycle repair shop
Answers
Answer:
The last one
Explanation:
They started a bicycle repair rental and sales business in 1892 according to text books
Answer:
The brothers constructed gliders in their free time
The brothers operated a bicycle repair shop
Explanation:
At the end of the 1800s and the beginning of the 1900s, the Great Lakes region was home to a number of important inventors. Orville and Wilbur Wright were brothers who flew the first airplane. The Wright brothers operated a bicycle repair shop and factory in Dayton, Ohio. In their free time, they constructed gliders and other aircrafts in their shop. They were fascinated with flying. They conducted many experiments to determine the best design for airplane wings. Orville also constructed an engine for the airplane.
As the different network types have evolved, careers in the Network Systems pathway
have changed over time. Discuss an example of how network system careers have
changed and how those changes have impacted society.
Answers
A network of computers known as a local area network, or LAN, is set up within a boundary, such as a building complex, office, or residential neighborhood. Alternatively, a wide-area network (WAN) is a kind of computer network.
What is a local area network?A local area network (LAN) is made up of several computers that are connected to create a network in a certain area. LANs use TCP/IP ethernet or Wi-Fi to connect the computers.An institution, like a school, office, association, or church, will typically be the only one to use a Network.A local area network (LAN) is a type of computer network that links computers that are near one another, such as those in a home, business building, school, lab, or university campus. A local area network is known as LAN. A LAN is a network that is contained inside a specific geographic region, typically a single building and is distinguished from a network by the number of linked computers it consists of.To learn more about local area network, refer to:
https://brainly.com/question/8118353