Brody is concerned that he is going to exceed the quota set for his mailbox. Where should he go to access the Mailbox Cleanup tools
Answers
To access the Mailbox Cleanup tools, Brody should navigate to the settings or options menu in his email client or webmail interface, where he can find options like "Account Settings" or "Mail Settings" to manage his mailbox quota.
Where can Brody find the Mailbox Cleanup tools in Microsoft Outlook?Brody can find the Mailbox Cleanup tools in Microsoft Outlook to address his concern about exceeding the mailbox quota. In Microsoft Outlook, these tools provide various options for managing mailbox size and organizing emails efficiently.
To access the Mailbox Cleanup tools, Brody should open Microsoft Outlook on his computer and navigate to the "File" tab at the top left corner of the screen. From there, he should select "Options" and then click on "Advanced" in the left-hand pane. Within the Advanced settings, Brody will find the "Mailbox Cleanup" button, which leads him to the Mailbox Cleanup tools.
Learn more about Microsoft Outlook
brainly.com/question/30311315
#SPJ11
Related Questions
Missy loves her old Windows games. When she upgrades her Windows system, the games run fine, but the output looks fuzzy since the programs are designed only to run in VGA mode. What can she do to make the games work properly in Windows
Answers
Complete Question:
Missy loves her old Windows games. When she upgrades her Windows system, the games run fine, but the output looks fuzzy since the programs are designed only to run in VGA mode.
Group of answer choices;
A. Reboot into Safe Mode
B. Run compatibility mode for 640 x 480 resolution.
C. Reduce her screen resolution to 640 x480
D. Reboot into Low Resolution Mode
Answer:
B. Run compatibility mode for 640 x 480 resolution.
Explanation:
In this scenario, Missy loves her old Windows games. When she upgrades her Windows system, the games run fine, but the output looks fuzzy since the programs are designed only to run in VGA mode. In order to make the games work properly in Windows, Missy should run compatibility mode for 640 x 480 resolution.
The video graphics array (VGA) is the standard graphics or display interface used for computer monitors. It was developed in 1987 by IBM and it had a standard display resolution of 640 x 480 pixels.
Hence, if the output of a software program (games) looks fuzzy or is not being displayed properly, you should run compatibility mode for 640 x 480 resolution. This is to enable low resolution video mode on the computer.
The VGA mode is very basic because only minimal video drivers are being loaded on the windows.
Unicornscan optimizes ____ scanning beyond the capabilities of any other port scanner.
a. TCP c. ICMP
b. UDP d. IP
Answers
Unicornscan optimizes UDP scanning beyond the capabilities of any other port scanner.
Unicornscan is a powerful network scanner that specializes in asynchronous TCP, UDP, and ICMP scanning. However, it is widely known for its exceptional ability to perform fast and accurate UDP scanning. This is due to its unique architecture, which uses a modular design with a multithreaded engine that enables it to scan multiple targets simultaneously. Additionally, Unicornscan has the ability to perform scan tuning, which allows users to customize and fine-tune scan parameters to their specific needs. These optimizations make it possible for Unicornscan to scan UDP ports faster and more accurately than other port scanners. As a result, it has become a popular tool for security professionals and network administrators.
Learn more about UDP here:
https://brainly.com/question/13068616
#SPJ11
Permit Traffic
The Fiji router is already configured with a standard IP access list number 11. The access list is applied to the FastEthernet0/0 interface. The list should allow all traffic except traffic coming from hosts 55.44.33.22 and 99.88.77.66. You've noticed that it's preventing all traffic from being sent on FastEthernet0/0. You know that access lists contain an implied deny any statement. Any traffic not permitted by the list is denied. For this reason, access lists should contain at least one permit statement, or all traffic is blocked.
In this lab, your task is to:
Add a permit any statement to the access list 11 to allow all traffic other than the restricted traffic.
Save your changes in the startup-config file.
Answers
In this lab, the task is to modify the existing access list on the Fiji router to permit all traffic except traffic from two specific hosts.
To modify the access list on the Fiji router, the user must enter privileged mode by typing "enable" and then enter the configuration mode by typing "configure terminal". Then, they should navigate to the access list by typing "access-list 11" and add a permit statement to allow all traffic by typing "permit any". Next, they should exit the configuration mode by typing "exit" and save the changes to the startup-config file by typing "copy running-config startup-config". This will ensure that the changes made to the access list are saved and will persist across reboots. After these steps are completed, the access list on the Fiji router will allow all traffic other than traffic from the two specified hosts.
Learn more about configuration here;
https://brainly.com/question/30278472
#SPJ11
if you bet and another person bets do you get the money you bet and the money the other person bets?
example : say you bet on a computer game and your sister bets $5 and you bet $10 that you will win. Do you get the $10 and the $5 if you win from your sister or just the $5?
Answers
Answer:
I believe you would get both because since you both did a bet and you won, that would mean you should automatically get both of what yall put down.
Explanation:
I think that's what should happen but I'm not sure though.
Complete the sentence with the correct response. In a two-way selection, if the initial statement is evaluated as , the code skips to the ELSE command.
Answers
Answer:
True.
The code skips the else command
Explanation:
I will answer this question with the following code segment
n = 1
If n > 0:
Print("greater than 0")
else:
Print("not greater than 0")
From the code segment above
Print("greater than 0") will be executed because the condition If n > 0 is true
Since the if condition is true, the else condition will not be executed
Which of the following could not go on a resumes for a position in the fashion and interior design field?
a) favorite fashion designer
b) volunteer positions
c) participation in school activities
d) relevant class is taken
Answers
Answer: I believe it would be your favorite fashion designer, because it just seems irrelevant... :)
What file format is best to give a printer when working with Adobe InDesign?
GIF
TIFF
HTML
IDML
Answers
Answer:
TIFF
Explanation:
GIFs are animated image files, and printers can't print animations
TIFFs are basically image files
HTML is a coding file, you were to print it, it would print the HTML text of the image
IDML is an XML representation of an InDesign document or components, if you were to print it, its outcome would be basically the same as printing an HTML file.
With ______________ encryption, one key is used to encrypt a message, and another is used to decrypt the message.
Group of answer choices
Private key
Public key
Cipher
Plain
Answers
With the private key encryption, one key is used to encrypt a message, and another is used to decrypt the message.
Private key encryption, also known as symmetric encryption, is a method of encrypting data where the same key is used for both encryption and decryption. Private key encryption is much faster than public key encryption, which uses two keys (one for encryption and one for decryption) to encrypt and decrypt data.
Private key encryption works by generating a secret key that is shared between the sender and recipient of the data. The key is then used to encrypt and decrypt data, ensuring that only the sender and recipient can read the data. The key must be kept secret, or the security of the encrypted data will be compromised.
Private key encryption is commonly used for encrypting data that does not need to be shared with others, such as sensitive financial information, medical records, and personal messages. It is also used for encrypting data that is stored on a computer or other device, such as passwords, credit card numbers, and other sensitive data.
Thus, With the private key encryption, one key is used to encrypt a message, and another is used to decrypt the message.
Know more about Private key here,
https://brainly.com/question/30410707
#SPJ11
Which of the following statements about NEXTVAL and CURRVAL is incorrect?
a. The pseudocolumn NEXTVAL is used to actually generate the sequence value. b. After the value is generated, it is stored in the CURRVAL pseudocolumn so it can be
referenced again by a user. c. A reference to CURRVAL will not cause Oracle to generate a new sequence number, a
reference to NEXTVAL, however, will generate a new number. d. NEXTVAL and CURRVAL are pseudocolumns that store unique names for database
objects.
Answers
The incorrect statement about NEXTVAL and CURRVAL is d. NEXTVAL and CURRVAL are not pseudocolumns that store unique names for database objects.
The correct statement is D.
NEXTVAL and CURRVAL are pseudocolumns in Oracle used for generating and referencing sequence values. The NEXTVAL pseudocolumn is used to generate the next value in the sequence, while the CURRVAL pseudocolumn is used to reference the current value in the sequence. After a value is generated using NEXTVAL, it is stored in the CURRVAL pseudocolumn so that it can be referenced again by a user. However, a reference to CURRVAL does not cause Oracle to generate a new sequence number. Only a reference to NEXTVAL will generate a new number.
It is important to note that NEXTVAL and CURRVAL are not pseudocolumns that store unique names for database objects. They are used exclusively for generating and referencing sequence values. NEXTVAL and CURRVAL. The incorrect statement among the given options is: NEXTVAL and CURRVAL are pseudocolumns that store unique names for database objects. NEXTVAL and CURRVAL are pseudocolumns used in Oracle databases to generate and reference sequence values, not to store unique names for database objects.
To know more about pseudocolumns visit:
https://brainly.com/question/32111782
#SPJ11
Assume a file containing a series of integers is named numbers.txt and exists on the computers disk. Write a program that calculates the average of all the numbers stored on the file. Write this in Python
Answers
Answer:Here is one way to calculate the average of all the numbers stored in a file named "numbers.txt" in Python:
Explanation:
# Open the file for reading
with open("numbers.txt", "r") as file:
# Read all the lines in the file
lines = file.readlines()
# Convert each line to an integer
numbers = [int(line.strip()) for line in lines]
# Calculate the sum of the numbers
total = sum(numbers)
# Calculate the average by dividing the total by the number of numbers
average = total / len(numbers)
# Print the result
print("The average of the numbers is", average)
Which of the following functions returns the highest value in a range of cells?
MIN
MAX
SUM
TOTAL
Answers
Answer:
MAX
Explanation:
The function that returns the highest value in a range of cells is MAX.
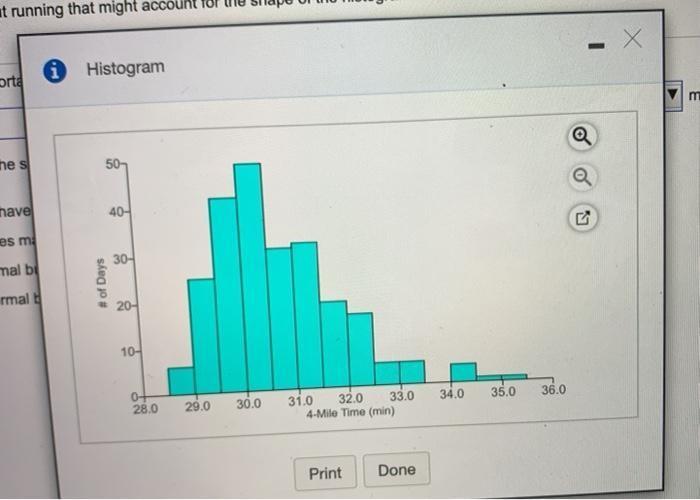
describe the distribution and and summarize the important feature. what is it about running that might account for the shape you see
Answers
We may deduce from the histogram that the distribution is unimodal and biased to the right. The median value is between 30 and 31 minutes, while the majority of the running times are between 29 and 32 minutes.
How is this so?The histogram is biased to the right, with most of the outliers occurring at higher running times, since it is more probable for a person to run slowly and take longer to run 4 miles than to sprint quickly and take less time.
The distribution is said to be unimodal since there is just one peak, which is the highest.
Because the majority of the outliers are located on the left side of the peak, the distribution is skewed to the right.
Learn more about distribution:
https://brainly.com/question/26702002
#SPJ1
Full Question:
An author collected the times (in minutes) it took him to run 4 miles on various courses during a 10-year period. The accompanying histogram shows the times. Describe the distribution and summarize the important features. What is it about running that might account for the shape of the histogram?
See histogram attached.
Sue follows these steps to create a chart in her presentation. Step 1: Navigate to the Insert tab. Step 2: Click the Chart button in the Illustrations command group. Step 3: Choose the column chart. Step 4: Click OK. Which objects appear on the slide after she clicks OK? Check all that apply.
Answers
Answer:
a table with sample values
a chart with sample values
Explanation:
Microsoft powerpoint is a powerful presentation tool. It has several tools and can be used to present even excel files, charts and other graphical data.
When a chart is created in powerpoint, the slide of the application shows a table and a chart with sample values.
a table with sample values
a chart with sample values

Name 2 ways that body temperature can be taken.
Answers
Answer:
Under the armpit, which is called the axillary method, and also through mouth, which is called the oral method.
Explanation:
This resource is a collection of 20,000 detailed job profiles. O*NET, the online version of the DOT, is a database of job profiles
Answers
Answer:
The ONET database holds data or details of job profiles available to applicants on the internet.
Explanation:
A database is an important tool in web development. Commercial or e-commerce websites use databases to store important information needed by the customers to make purchases of goods and services.
Other websites like government agencies and research communities use these databases to collect and store data retrieved from visitors to the sites.
Etna works on many projects. As she creates a new project file, she goes to the File tab, selects Options, and then goes to the advanced category for the General section to check a box. What is she trying to do
Answers
What Etna is trying to do by going to the file tab and the general section is to Create a new file with a set of parameters.
Steps to creating a new file.In order to create a new file you have to do the following:
You have to go to the file tab.Then you go to click optionsThe next is the advanced categorythe checkbox is located in the general section.Following all of the steps that are listed above would help Etna as she works on her project.
Read more on ways to create files here:
https://brainly.com/question/25554117
1 the background image on the desktop of computer is called
1 image 2 icon 3 desktop 4 wallpaper
2 this command is a duplicate of a file or
folder
1 copy 2 move 3 duplicate 4 none of these
Answers
Answer:
4. Wallpaper
Explanation:
The background image for your computer is called a wallpaper
Answer:
Wallpaper
Explanation:
(a) Let L
1
and L
2
denote two regular languages defined over an alphabet Σ. We define the follows: L
1
−L
2
={x:x∈Σ
∗
,x∈L
1
and x∈
/
L
2
}. Is L
1
−L
2
regular? Explain. (b) The symmetric difference of two sets S
1
and S
2
is defined as follows; S
1
⊕S
2
={x:x∈S
1
or x∈S
2
, but not both }. Are regular languages closed under the symmetric difference operation?
Answers
If L1 and L2 are both regular languages, it does not guarantee that L1 - L2 will also be regular. Regular languages are closed under some operations such as union, concatenation, and Kleene closure, but they are not closed under set difference.
(a) To determine if L1 - L2 is regular or not, we need to consider the regularity of the individual languages L1 and L2 and analyze their properties.
To illustrate this, consider the following example:
Let L1 = {aⁿ bⁿ | n ≥ 0} and L2 = {aⁿ | n ≥ 0}.
L1 represents the language of balanced parentheses of the form "aⁿ bⁿ," and L2 represents the language of unmatched "a" characters.
In this case, L1 is a regular language, and L2 is also a regular language. However, L1 - L2 results in a language that represents unmatched parentheses, which is not a regular language.
Therefore, L1 - L2 is not necessarily regular, as regular languages are not closed under set difference.
(b) Regular languages are closed under union and intersection, but they are not closed under the symmetric difference operation. The symmetric difference of two sets S1 and S2, denoted as S1 ⊕ S2, consists of elements that belong to either S1 or S2 but not both.
To show that regular languages are not closed under the symmetric difference operation, we can provide a counterexample. Consider the following languages:
L1 = {aⁿ bⁿ | n ≥ 0} and L2 = {bⁿ cⁿ | n ≥ 0}.
L1 represents the language of balanced parentheses of the form "a^n bⁿ," and L2 represents the language of balanced parentheses of the form "bⁿ cⁿ."
Both L1 and L2 are regular languages. However, if we take the symmetric difference of L1 and L2, L1 ⊕ L2, it results in the language that represents strings of the form "aⁿ bⁿ" or "bⁿ cⁿ," but not both.
This resulting language is not regular because it violates the pumping lemma for regular languages. Hence, regular languages are not closed under the symmetric difference operation.
Learn more about symmetric difference operation https://brainly.com/question/33545620
#SPJ11
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
6. Python indexes lists beginning with the number 1.
True
False
Answers
Answer:
True
Explanation:
Python is like coding
What is LinkedIn?
A job search website
A virtual job fair
A recruiter website
Answers
Answer:
A job search website.
Explanation:
Which word can best be used to describe an array ?
Answers
The term that best describes an array is collection.
An array is a data structure that allows the storage and organization of a fixed number of elements of the same type.
It provides a systematic way to store multiple values and access them using an index.
The word "collection" aptly captures the essence of an array by highlighting its purpose of grouping related elements together.
Arrays serve as containers for homogeneous data, meaning all elements in an array must have the same data type.
This collective nature enables efficient data manipulation and simplifies the implementation of algorithms that require ordered storage.
By describing an array as a collection, we emphasize its role as a unified entity that holds multiple items.
Furthermore, the term "collection" conveys the idea of containment, which aligns with the way elements are stored sequentially within an array.
Each element occupies a specific position or index within the array, forming a cohesive whole.
This concept of containment and ordered arrangement emphasizes the inherent structure and organization within an array.
For more questions on array
https://brainly.com/question/29989214
#SPJ8
the only software component that’s required to run a web application on a client is
Answers
The only software component that’s required to run a web application on a client is a web browser.
A web application is a program or software that runs on a web server and is used by clients over the internet. Web applications are designed to be compatible with multiple platforms, including smartphones, tablets, and computers.
Because they are platform-independent, web applications can be run on a variety of devices without requiring specialized software.
A web browser is a program that displays web pages and content on the internet. It is a client-side software that is installed on a computer or mobile device and is used to access web applications and websites. It provides users with a graphical interface to access web-based content, such as text, images, videos, and multimedia.
Web browsers use HTTP (Hypertext Transfer Protocol) to request and transmit data to and from web servers. Web applications are accessed using web browsers. A web browser is the only software component that’s required to run a web application on a client.
It acts as a user interface that communicates with the web server where the application is hosted. When a user accesses a web application, the web browser sends a request to the web server to retrieve the necessary data and displays the results on the user’s device.
To learn more about software: https://brainly.com/question/28224061
#SPJ11
what statement about constructors is false? group of answer choices all constructors are passed a pointer argument constructors may take arguments you must write at least one constructor for every class classes may have more than one constructor constructors have no return type
Answers
A return type cannot exist in the constructor. It ought to produce and deliver fresh objects. Consequently, a compilation error would result.
Including a return type in a constructor declaration is not allowed. A constructor has to accept one or more input parameters. In the absence of explicitly declared constructors for the class, Java will give a default constructor. The name of the constructor should match the class name. 2) The compiler will automatically produce a default parameterless constructor for a class if you don't define one. 3) All instance variables are initialized to default values, such as 0, null, and super(), by the default constructor.
Learn more about variable here-
https://brainly.com/question/13375207
#SPJ4
What will be values of AL, AH, and BL after the following piece of code is excuted?
Answer in decimal
mov (100, AX);
mov (9, BL);
div (BL);
Answers
The values of AL, AH, and BL after the assembly code has been executed is:
AL = 11 (decimal)
AH = 1 (decimal)
BL = 9 (decimal)
Why is this so ?The provided assembly code snippet includes the instructions mov, div, and some register assignments. Let's break down the code step by step to determine the values of AL, AH, and BL.
mov (100, AX);: This instruction moves the value 100 into the AX register. Assuming AX is a 16-bit register, the value 100 is stored in the lower 8 bits of AX, which is AL, and the upper 8 bits, which is AH, will be set to 0.
Therefore, after this instruction, the values are
AL = 100 (decimal)
AH = 0
mov (9, BL);: This instruction moves the value 9 into the BL register.
After this instruction, the value is
BL = 9 (decimal)
div (BL);: This instruction divides the 16-bit value in the DX:AX register pair by the value in the BL register. Since the DX register is not explicitly assigned in the given code snippet, we'll assume it contains 0.
The div instruction performs unsigned division, and it divides the 32-bit value (DX:AX) by the value in the specified register (BL) and stores the quotient in AX and the remainder in DX.
In this case, the initial value in AX is 100 and BL is 9.
Performing the division: 100 / 9 = 11 with a remainder of 1.
After the div instruction, the values are updated as follows:
AL = quotient = 11 (decimal)
AH = remainder = 1 (decimal)
Therefore, the final values after the code execution are:
AL = 11 (decimal)
AH = 1 (decimal)
BL = 9 (decimal)
Learn more about assembly code:
https://brainly.com/question/30762129
#SPJ1
CMU 7.4 Christmas Tree. Has anyone done it? Can somebody give me more hints?
Answers
Answer: Christmas is on feb
Explanation:
CMU CS Academy is an online, interactive, and self-paced computer science curriculum developed by Carnegie Mellon University (CMU).
What is CMU CS Academy?CMU CS Academy is an online, interactive, and self-paced computer science curriculum developed by Carnegie Mellon University (CMU). It is designed to give students the opportunity to learn computer science fundamentals in a fun and engaging way. With its interactive and self-paced structure, students can learn at their own pace and engage with the materials in an engaging, dynamic way.
The curriculum covers topics such as problem solving, programming, algorithms, data structures, computer architecture, and more. With its intuitive and interactive design, students can learn and apply the concepts learned in a step-by-step manner. CMU CS Academy also provides tools and resources to help students on their learning journey, such as online quizzes, tutorials, and project-based learning.
To learn more about Carnegie Mellon University on:
brainly.com/question/15577152
#SPJ2
which of the following gestures would you use if you want to activate a mode that enables you to move an item with one finger to a new location on your new tablet?
Answers
On your new tablet, you can toggle on a mode that lets you move an object to a new spot only with one finger by swiping your finger across the screen.
What are gestures ?
A gesture is a visible body activity that conveys specific messages in place of or in addition to words. It is a type of nonverbal or non-vocal communication. Gestures might include the movements of the hands, face, or other body parts. Physical non-verbal communication like proxemics, purely expressive displays, or displays of shared attention are different from motions in that they convey specific messages. People can express a wide range of emotions and ideas through motions, from hostility and scorn to admiration and affection.
To know more about gestures
https://brainly.com/question/12115354
#SPJ4
what is the meaning of the digit 2 immediately prior to the username (rod)?
Answers
Answer:
represents the number of filenames that point to the file
Explanation: becuz i said
What is the value of the variable result after these lines of code are executed?
>>> a = 2
>>> b = -3
>>> c = 4
>>> result = (a - b) * c
The value of result is ______.
Answers
Answer:
5 i just found the answer
like the profile from dagunrapa 3 killing harmony kokichi oma
Answer:
5
Explanation:
Maxie created a presentation about cats, and she would like her teacher to critique her. Which critique item will help her know if the audience could hear her well?
Answers
Maybe telling her to speak up and face where she wants to speak
Answer:
Are you speaking loud and clear
Explanation:
(04.06 LC)
Maxie created a presentation about cats, and she would like her teacher to critique her. Which critique item will help her know if the audience could hear her well?
Group of answer choices
Are you speaking loud and clear?
Are you using facial expressions?
Are you focusing on your topic?
Are you speaking at a good pace?