BIUX
Type your answer here
E
What does self-regulation look like for you? What are times that you've been successf
skill? (50 word minimum)
Answers
Related Questions
Implement a 3-bit counter that counts in two different orders. Your circuit should have a Button named CLK, a Button named RESET, and an input pin named Gray (for Gray code). It should have 3 LED displays, named L0, L1, and L2. The first thing the Test option does it ensure you have the correct inputs and outputs. The inputs and outputs are identical to those for the previous 3-bit counter except for the addition of the extra pin named Gray. The names are case sensitive.
When G is false, the counter is an up counter, counting in steps of 1. Each clock pulse increases the count by one: 0, 1, 2, 3, 4, 5, 6, 7, 0, etc.
When G is true, the counter is a gray code counter counting in gray code order: 0, 1, 3, 2, 6, 7, 5, 4, then back to 0. In binary, that is (000, 001, 011, 010, 110, 111, 101, 100, then back to 000).
Example: Suppose the current output is 101. If G=1, the value after the next clock will be the next value in the gray code sequence, 100. If G=0, the value after the next clock will be the next value sequentially, 110.
Draw the Karnaugh map and truth table and complete the circuit diagram using D flip-flop SR
Answers
Answer:
gfhfidusbifhgseliuggbdsdbdf
Explanation:
You would like the cell reference in a formula to remain the same when you copy
it from cell A9 to cell B9. This is called a/an _______ cell reference.
a) absolute
b) active
c) mixed
d) relative
Answers
Answer:
The answer is:
A) Absolute cell reference
Explanation:
An absolute cell reference is used in Excel when you want to keep a specific cell reference constant in a formula, regardless of where the formula is copied. Absolute cell references in a formula are identified by the dollar sign ($) before the column letter and row number.
Hope this helped you!! Have a good day/night!!
Answer:
A is the right option absoluteIf the horizon is sloping, it is a good sign that the photograph is not straight. True False
Answers
Answer:
the actual answer is true
Explanation:
A MAC Frame format has a Preamble of 7 octet pattern in the form of alternating 1s and 0s used by a receiver to establish synchronization. Use a Manchester Encoding technique to describe the first octet of the signal pattern produced within the Preamble.
Answers
Answer:
The answer is "10101010".
Explanation:
Description of the above question as follows:
Encryption with Manchester is a bit transmission method that makes synchronizing the receiver with the sender simple. It splits each bit time frame into two, ensuring that the signal levels are always transient in the middle of each bit.The encoding of Manchester explains the first byte of the frequency signal pattern, which produced in the preambles which are given in the attachment.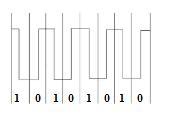
You have two microservices that need to communicate with each other without holding up a thread on either end. One service will receive an ID and return a message once the job is complete. Which communication framework should be used
Answers
Answer:
E.) Use a RESTful architecture for both, send the ID through a POST, and ping the service with a GET until a response is available
Explanation:
In case when there is two microservices that required fro communicating with one another without considering the holding function via thread on each of the end
So here the RESTful architecture is used for the both also the ID is send via post and then the service could be ping with a GET till the response is available
hence, the correct option is e.

The communication framework that should be used is E. Use a RESTful architecture for both, send the ID through a POST, and ping the service with a GET until a response is available.
A communication strategy framework simply means a tool that's used for planning communication with one's suppliers, contractors, employees, etc.
The communication framework that should be used is to use a RESTful architecture for both, send the ID through a POST, and ping the service with a GET until a response is available. This is vital for the two microservices that need to communicate with each other without holding up a thread on either end.
Read related link on:
https://brainly.com/question/17262565
The software used to provide visual support such as slide show during lectures
Answers
Answer:
microsoft powerpoint
Explanation:
Error messages are a key part of an overall interface design strategy of guidance for the user. Discuss strategies to ensure integrated, coordinated error messages that are consistent across an application.
Answers
Answer:
Answered below
Explanation:
In order to not discourage the user, error messages must be implemented in a user-friendly way with the use of strategies which ensure coordination, consistency and simplicity.
Error messages should be short, direct and communicate clearly, the right amount of information to a user. These messages should be sorted into categories which represent different kinds of errors. These specific categories should have a brief alphanumeric code that can be easily shared with a customer support personnel for solution and also to help users search for solutions themselves, on the internet.
The first three elements of the Continuous Delivery Pipeline work together to support delivery of small batches of new functionality which are released in accordance with what?
Answers
Answer:
is Market needs
Explanation:
The first three elements of the continuous delivery pipeline mediates the support to the small batches thereby to be released in accordance with the market demand.
What is continuous delivery pipeline?The continuous delivery pipeline can be given as the software application that enables the development of the new code with the automation to speed.
The first three elements of the continuous delivery pipeline are Continuous Exploration (CE), Continuous Integration (CI), and Continuous Deployment (CD).
The elements mediates the support to the small batches to be released in accordance with the market demand.
Learn more about continuous delivery, here:
https://brainly.com/question/14402781
#SPJ2
How could using WellConnect help you with time management and in personal health and wellness?
Answers
Answer:
Well Connect help in personal health and wellness
Explanation:
Well Connect is a collaboration of the individuals, and it focused on optimizing the experience of health. Rochester improves healthcare. Well, Connect created. Half of the adults have a physical, mental health condition. Chronic conditions are acute conditions as they cannot be cured. They manage and prevented it. They manage healthcare. Well Connect supports individuals. Well Connect brings the public health community to create a unified system. It is designed to develop relationships with healthcare. Everyone is involved in Well Connect with passion.
Secure websites use technology that scrambles the information you send. This is known as
A. hacking.
B. encryption.
C. padlocking.
D. digital media.
Answers
Answer:
B. Encryption.
Explanation:
Encryption encrypts data so that it can not be understood if/when it is intercepted by a third party between the sender and the recipient.
For example, if you're encrypting via the keyword vanilla, and then sending an email to Bob saying "Hi Bob", it would get encrypted as something like Vjh D5xx. The recipient would then use the keyword vanilla to decrypt this message so they can read it as Hi Bob. Anyone who intercepts this wouldn't have the keyword, and would just see incoherent letters, numbers, and symbols that they couldn't make heads or tails of.
Secure websites use technology that scrambles the information you send. This is known as, Encryption. So, the correct option is B.
Given that,
Secure websites use technology that scrambles the information you send.
Since, Secure websites use encryption technology to scramble the information you send, ensuring that it remains secure and protected during transmission.
Encryption involves the use of mathematical algorithms to transform data into an unreadable format, making it extremely difficult for unauthorized parties to access or understand the information.
This is a fundamental method used to safeguard sensitive data on the internet.
So, Option B is true.
To learn more about Encryption visit:
https://brainly.com/question/30408255
#SPJ6
List and briefly describe the major types of system in organization?
Answers
1. operational-level systems
2. management-level systems
3. strategic-level systems
1. operational-level systems = support operational activities by keeping track of the elementary activities and transactions of the organization, such as assigning employees to tasks and recording the number of hours they work, or placing a purchase order. Operational activities are short-term in nature.
2. management-level systems = Management-level systems serve the monitoring, controlling, decision-making, and administrative activities of middle managers. Management-level systems typically provide periodic reports rather than instant information on operations.
3. strategic-level systems = Strategic-level systems (SLS) are information systems at the strategic level of an organization designed to address unstructured decision-making.
The major types of systems in the organization are:
Operational Level systemManagement Level systemStrategic Level systemThe classification of information systems based on organization levels is determined by the specialties and interests in some functional areas.
Operational-level systems assist operational managers by tracking the organization's basic operations and transactions, as well as the movement of materials in a factory. The primary function of systems at this level is to respond to routine inquiries and to record the movement of transactions via the organization. In general, information must be easily accessible, up to date, and accurate.
Management-level systems support middle managers' observing, regulating decision-making, and administrative operations. The primary question tackled by such systems is:
Are things running smoothly?Management-level systems usually give regular reports rather than real-time operational data.
Strategic-level systems assist senior management in addressing strategic challenges and long-drawn patterns, both inside the organization and in the external world. Their primary focus is harmonizing external adjustments in the environment with current organizational capacity.
Therefore, from the above explanation, we can conclude that we've fully understood the types of systems in the organization of information systems.
Learn more about information systems here:
https://brainly.com/question/13299592?referrer=searchResults
Describe what each of the following functions in R do.1. t2. matplot3. c4. seq5. legend6. matrix7. rownames8. colnames9. type of
Answers
Answer:
1. t is a function used to transpose a matrix object. The object is passed as an argument to the function.
2. matplot is a graphical function in R used for data visualization.
3. The c function is used to combine arguments.
4. seq is an R function used to derive a range of numbers, optionally specifying a start, stop and step argument or simply a single numeric argument.
5. legends are used in data visualization to list and define items in the graphical presentation.
6. matrix is a function in R used to create and work with matrix and data frame objects.
7. rownames and colnames are functions used to label the row and columns of a data frame in R.
8. The typeof function return the data type of an object.
Explanation:
The R programming language is a dedicated programming language for data analysis and visualization.
Why dose enginuty suck like really
Answers
Answer:
if you don't like it why u doin it?
Explanation:
A mobile base station (BS) in an urban environment has a power measurement of 15 µW at 175 m. If the propagation follows an inverse cube-power law (Section 3.2.2), what is a reasonable power value, in µW, to assume at a distance 0.7 km from the BS?
Answers
Answer:
The reasonable power will be "0.234 μW".
Explanation:
The given values are:
P = 15 μW
d = 175 m
As we know,
Propagation follows inverse cube power law, then
∴ \(Power \ \alpha \ \frac{1}{d^3}\)
⇒ \(Power=\frac{K}{d^3}\)
On substituting the estimated values, we get
⇒ \(15\times 10^{-6}=\frac{K}{(173)^3}\)
⇒ \(K=15\times (175)^3\times 10^{-6}\)
Now,
"P" at 0.7 km or 700 m from BS will be:
⇒ \(P=\frac{K}{d^3}\)
⇒ \(P=\frac{15\times (175)^3\times 10^{-6}}{(700)^3}\)
⇒ \(P=0.234 \ \mu W\)
1. What criteria must be maintained once a clinical record has been created ?
Answers
The criteria that must be maintained once a clinical record has been created are:
All vital clinical findings are accurate.A record of the decisions made are true and exact.What is maintained in a medical record?Medical records are known to be any kind of document that helps to tell all detail in regards to the patient's history, as well as their clinical findings, their diagnostic test results, medication and others.
Note that If it is written rightly, the, notes will help to aid the doctor about the rightness of the treatment of the patient.
Therefore, some of the criteria for high quality form of clinical documentation are they must be :
AccurateExactClearConsistentCompleteReliableLegible, etc.Therefore, based on the above, The criteria that must be maintained once a clinical record has been created are:
All vital clinical findings are accurate.A record of the decisions made are true and exact.Learn more about clinical record from
https://brainly.com/question/21819443
#SPJ1
A wedding photographer taking photos of the happy couple at a variety of locations prior to their wedding would be classified as a reactive system on the service system design matrix.A. TrueB. False
Answers
Answer:
True
Explanation:
Which meter would you use to determine which lamp is defective in the shortest possible time? Explain how you would use this meter and why.
Answers
Answer:
bla bla bla bla
Explanation:
I dont anther stand
How many NOTS points are added to your record for not completely stopping at a stop sign?
Answers
In some jurisdictions, failing to stop at a stop sign can result in a citation for running a stop sign or a similar violation. In other jurisdictions, it may be categorized as a failure to obey traffic signals or a similar violation. The number of NOTS points added to your record, if any, will depend on the specific violation charged and the point system used by the jurisdiction in question.
It's important to note that NOTS points are used to track and measure the driving record of a driver, and they may impact insurance rates and license status. It's always a good idea to familiarize yourself with the laws and regulations in your area and drive safely to reduce the risk of violations and penalties.
Suppose a subnet has a prefix 15.119.44.128/26. If an ISP owns a block of addresses starting at 15.119.44.64/26 and wants to form four (4) subnets of equal size, what prefixes of the form a.b.c.d/x should be used? Explain. How many hosts can each of the new subnet have?
Answers
Any IP address that can be seen within the subnet 15.119.44.128/26 and 15.119.44.191/26 network addresses.
The four equal subnets that can be derived from the subnet 15.119.44.64/26 are said to be:
15.119.44.64/28 15.119.44.80/28 15.119.44.96/2815.119.44.112/28.Why the subnet above?The appropriate host or subnet number and mask are used to determine the IP addresses in the subnet 15.119.44.128/26.
Note that the host formula is 2n -2, where n is the number of zeros on the place of the fourth octet and two is subtracted from the value signifying the network and broadcast addresses of the network address.
Therefore, The subnet is determined by the formula 2n, where n is the number of borrowed bits from the fourth octet.
Learn more about subnet from
https://brainly.com/question/14895074
#SPJ1
To address cybercrime at the global level, law enforcement needs to operate
.
Answers
In order to address cybercrime on a worldwide scale, it is imperative that law enforcement agencies work together in a collaborative and cooperative manner across international borders.
What is the cybercrime?Cybercrime requires collaboration and synchronization among countries. Collaboration among law authorization organizations over different countries is basic for the effective request, trepidation, and conviction of cybercriminals.
In arrange to combat cybercrime in an compelling way, it is pivotal for law authorization to collaborate and trade insights, capability, as well as assets.
Learn more about cybercrime from
https://brainly.com/question/13109173
#SPJ1
3.Personal Information Class
Design a class that holds the following personal data: name, address, age, and phone number. Write appropriate accessor and mutator methods. Demonstrate the class by writing a java
program that creates three instances of it. One instance should hold your information, and
the other two should hold your friends' or family members' information.
Answers
Here's an example Java class that holds personal data and provides accessor and mutator methods:
public class PersonalData {
private String name;
private String address;
private int age;
private String phoneNumber;
public PersonalData(String name, String address, int age, String phoneNumber) {
this.name = name;
this.address = address;
this.age = age;
this.phoneNumber = phoneNumber;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getAddress() {
return address;
}
public void setAddress(String address) {
this.address = address;
}
public int getAge() {
return age;
}
public void setAge(int age) {
this.age = age;
}
public String getPhoneNumber() {
return phoneNumber;
}
public void setPhoneNumber(String phoneNumber) {
this.phoneNumber = phoneNumber;
}
}
And here's an example Java program that creates three instances of this class:
public class PersonalDataDemo {
public static void main(String[] args) {
PersonalData myData = new PersonalData("John Smith", "123 Main St, Anytown USA", 35, "555-1234");
PersonalData friend1Data = new PersonalData("Jane Doe", "456 Oak St, Anytown USA", 28, "555-5678");
PersonalData friend2Data = new PersonalData("Bob Johnson", "789 Elm St, Anytown USA", 42, "555-9012");
System.out.println("My personal data:");
System.out.println("Name: " + myData.getName());
System.out.println("Address: " + myData.getAddress());
System.out.println("Age: " + myData.getAge());
System.out.println("Phone number: " + myData.getPhoneNumber());
System.out.println();
System.out.println("Friend 1's personal data:");
System.out.println("Name: " + friend1Data.getName());
System.out.println("Address: " + friend1Data.getAddress());
System.out.println("Age: " + friend1Data.getAge());
System.out.println("Phone number: " + friend1Data.getPhoneNumber());
System.out.println();
System.out.println("Friend 2's personal data:");
System.out.println("Name: " + friend2Data.getName());
System.out.println("Address: " + friend2Data.getAddress());
System.out.println("Age: " + friend2Data.getAge());
System.out.println("Phone number: " + friend2Data.getPhoneNumber());
}
}
The above mentioned codes are the answers.
For more questions on Java, visit:
https://brainly.com/question/26789430
#SPJ11
The Environmental Master Equation includes all of the following terms except:
O Resource use per person
O Population
•Percent of resource emitted into the atmosphere
•Environmental impact per unit of resource use
Answers
Answer: [C]: " percent of resource emitted into the atmosphere ."
________________________
Explanation:
In the "Environmental Master Equation"—
Note that the:
"Environmental impact" ;
= (population) * (resource use per unit population) *
(environmental impact per unit of resource use) .
________________________
The question asks:
"The Environmental Master Equation includes all of the following terms —EXCEPT ...[with 4 (four) answer choices following.]."
________________________
Consider the given answer choices:
[A]: "resource user per person"—which is the same as"
"(resource use per UNIT [emphasis added] population" ;
— which does appear in the equation;
→ so we can rule out "Choice: [A]."
________________________
[B]: "population" —this is included within the equation; so we can rule out "Choice: [B]."
________________________
[C]: "percentage of resource emitted into the atmosphere" ;
Note: This clearly does NOT appear within the equation; so this is a likely answer choice.
________________________
Note: There is one more answer choice—so let us examine:
________________________
[D]: "environmental impact per unit of resource use" —this is included within the equation, so we can rule out "Choice: [D]."
________________________
Furthermore, the particular answer choices given—A, B, and D ; constitute all elements within the "Environmental Master Equation."
________________________
As such: The correct answer is:
[C]: "percent of resource emitted into the atmosphere."
________________________
Hope this is helpful to you!
Best wishes in your academic pursuits!
________________________
Answer:
•Percent of resource emitted into the atmosphere
Explanation:
Hope this will help
Which two sentences describe the necessary hardware skills that information support and services professionals need to develop?
knowing how to update and fix operating systems
knowing how to build or install computer systems
knowing how to secure computer networks
knowing the basic parts of a computer system
knowing how to code using programming languages
Answers
The sentence that describe the necessary hardware skills that information support and services professionals need to develop is that they know whether a system meets their needs and requirements.
What is an information system?An information system can be defined as a set of components or computer systems, which is used to collect, store, and process data, as well as dissemination of information, knowledge, and distribution of digital products.
Generally, it is an integral part of human life because individuals, organizations, and institutions rely on information systems in order to perform their duties, functions or tasks and to manage their operations effectively.
Therefore, The sentence that describe the necessary hardware skills that information support and services professionals need to develop is that they know whether a system meets their needs and requirements.
Learn more about sentence on:
https://brainly.com/question/16890064
#SPJ1
Answer:
knowing how to build or install computer systemsknowing the basic parts of a computer systemExplanation:
I hope this helps
BTW PLATO
A ______ can hold a sequence of characters such as a name.
Answers
A string can hold a sequence of characters, such as a name.
What is a string?A string is frequently implemented as an array data structure of bytes (or words) that records a sequence of elements, typically characters, using some character encoding. A string is typically thought of as a data type. Data types that are character strings are the most popular.
Any string of letters, numerals, punctuation, and other recognized characters can be stored in them. Mailing addresses, names, and descriptions are examples of common character strings.
Therefore, a string is capable of storing a group of characters, such as a name.
To learn more about string, refer to the link:
https://brainly.com/question/17091706
#SPJ9
The binary number system is suitable for computer system. Give reason.
Answers
Answer: It enables devices to store, access, and manipulate all types of information directed to and from the CPU or memory.
THIS DOES NOT BELONG TO ME!
Explanation:
In the following table, complete the marginal cost, average variable cost, and average total cost columns. Quantity Variable Cost Total Cost Marginal Cost Average Variable Cost Average Total Cost (Vats of juice) (Dollars) (Dollars) (Dollars) (Dollars) (Dollars) 0 0 30 1 8 38 2 18 48 3 30 60 4 50 80 5 80 110 6 120 150 On the following graph, use the orange points (square symbol) to plot the marginal-cost curve for Jane's Juice Bar. (Note: Be sure to plot from left to right and to plot between integers. For example, if the marginal cost of increasing production from 1 vat of juice to 2 vats of juice is $5, then you would plot a point at (1.5, 5).) Then use the purple points (diamond symbol) to plot the average-variable cost curve starting at 1 vat of juice, and use the green points (triangle symbol) to plot the average-total-cost curve also starting at 1 vat of juice.
Answers
The marginal cost of production is the change in total production cost which comes from making one additional unit.
What is the average variable cost?The average variable cost is the total variable cost per unit of output. It is found by dividing the total variable cost (TVC) by the output.
The average total cost is found by dividing the total cost (TC) by the output.
The average variable cost is determined by dividing the total variable cost by the quantity produced. In this case, subtract the average variable cost from the average total cost: This will give the average fixed cost per unit.
Learn more about cost on:
https://brainly.com/question/25109150
#SPJ1

Can someone help me with the following logical circuit, perform two actions. FIRST, convert the circuit into a logical
statement. SECOND, create a truth table based on the circuit/statement. (20 pts. each for statement and
truth table.

Answers
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
Given the logical circuit, we are required to perform two actions on it. Firstly, convert the circuit into a logical statement. Secondly, create a truth table based on the circuit/statement. Let's understand how to do these actions one by one:Conversion of Circuit into Logical Statement.
The given circuit contains three components: NOT gate, AND gate and OR gate. Let's analyze the working of this circuit. The two input variables A and B are first passed through the NOT gate, which gives the opposite of the input signal.
Then the NOT gate output is passed through the AND gate along with the input variable B. The output of the AND gate is then passed through the OR gate along with the input variable A.We can create a logical statement based on this working as: (not A) and B or A. This can also be represented as A or (not A) and B. Either of these statements is correct and can be used to construct the truth table.
Creation of Truth Table Based on the logical statement, we can create a truth table as shown below:
A B (not A) (not A) and B (not A) and B or A A or (not A) and B 0 0 1 0 1 0 0 1 0 0 1 0 1 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 1 1
In the truth table, we have all possible combinations of input variables A and B and their corresponding outputs for each component of the circuit.
The first two columns show the input values, the next column shows the output of the NOT gate, then the output of the AND gate, then the output of the OR gate and finally the output of the logical statement.
We can observe that the output of the logical statement is the same as the output of the OR gate.
For more such questions on Truth Table, click on:
https://brainly.com/question/13425324
#SPJ8
You have a 20-bit network part and a 4-bit subnet part. How many hosts can you have per subnet?
A) 14
B) 16
C) 254
D) none of the above
Answers
Answer:
tiddies
Explanation:
sukk
HELP ASAP PLZ PLZ PLZTegan is playing a computer game on her smartphone and the battery is getting low. When she goes to charge her phone, she notices that the cord is broken. What can Tegan do to solve her problem?
Plug in the smartphone to charge.
Put tape around the broken part of the cord.
Ask a trusted adult for help replacing the cord.
Use the laptop charger instead.
Answers
Answer:
3rd choice
Explanation:
use CPN Tools V4.0.1 ONLY.
Scenario: In the Lecture we simulated the simple example of a Process
reading a file and then writing back to it. Now, imagine the scenario, with
two Process trying to read or write to the same file.
Task(s):
1. Try to implement any form of locking mechanism of your choice, so
that the file is not written to while another Process is writing to it, and
vice versa
Answers
To implement a locking mechanism for a file in a scenario where two processes are trying to read or write to the same file, one approach is to use a file lock. A file lock is a mechanism that allows a process to lock a file, preventing other processes from accessing it until the lock is released.
Below is an example of how you could implement a file lock using the fs module:
const fs = require('fs');
let filePath = 'example.txt';
let fd;
try {
// Open the file and set an exclusive lock
fd = fs.openSync(filePath, 'r+');
fs.flockSync(fd, 'ex');
// Read the file contents
let data = fs.readFileSync(filePath, 'utf8');
// Modify the file contents
data = data + '\nAdded new line';
// Write the modified data back to the file
fs.writeFileSync(filePath, data, 'utf8');
} catch (err) {
console.error(err);
} finally {
// Release the lock
if (fd) {
fs.flockSync(fd, 'un');
fs.closeSync(fd);
}
}
What is the code about?In the above example, the fs.openSync() method is used to open the file and set an exclusive lock on it. This means that any other process trying to access the file will be blocked until the lock is released. The file is then read, modified, and written back to using the fs.readFileSync(), fs.writeFileSync() method. The fs.flockSync(fd, 'un') method is used to release the lock on the file.
It's important to note that this example uses synchronous methods, as they are simpler to understand and use. But in real-world scenarios, using asynchronous methods is more recommended.
Therefore, It's also important to make sure that the lock is released when you're done with the file. This is why the lock is released in the finally block of the try catch block. This way, the lock will be released even if an error occurs while working with the file.
Learn more about program from
https://brainly.com/question/26134656
#SPJ1