You designed a program to create a username using the first three letters from the first name and the first four letters of the last name. You are testing the program, the last step in the process. For a user named John Smith, what username should the program create
Answers
For the user named John Smith, the program would create the username "JohSmit" based on the specified program design.
The program takes the first three letters from the first name, which are "Joh," and combines them with the first four letters of the last name, which are "Smit." This concatenation results in the username "JohSmit." The program follows the pattern of using the first three letters of the first name and the first four letters of the last name to generate the username.
It is important to note that this program design assumes that the input names are at least three and four letters long for the first and last names, respectively, to ensure the creation of a valid username.
To know more about Programming related question visit:
https://brainly.com/question/14368396
#SPJ11
Related Questions
can someone tell me what to do i’m kinda stuck and don’t know what he’s telling me to do pls ill give brainlist and points

Answers
Answer:
Well a debtor is basically someone owing someone money, basically someone in debt. He’s telling cup head boy to take care of the people who owe him or someone else their or his money. Thats basically it.
For each problem listed below, use the drop-down menu to select the field of the professional who can help solve the issue.
1) An employee is having trouble opening a file on a computer_______________.
2) The president of a company wants to give the company website a fresh new look.___________
3) An employee wants to work from home but can’t connect to the network from there.___________
4) The vice president of sales would like help designing a new software program to keep track of sales. _______________
Answers
Answer:
An employee is having trouble opening a file on a computer.
→ ✔ information services and supportThe president of a company wants to give the company website a fresh new look.
→ ✔ interactive mediaAn employee wants to work from home but can’t connect to the network from there.
→ ✔ network systems administrationThe vice president of sales would like help designing a new software program to keep track of sales.
→ ✔ programming and software developmentOAmalOHopeO
Computer, refers to the device originally meant for the calculations but currently used for doing several other functions such as weather forecasting, communications, storing the data etc. It is a processing device that stores the information, process the information and gives the output to the users.
A worker is having problems using a computer to open a file. The employee has access to support and information services. The firm president wants to give the website a brand-new makeover. He's got access to interactive media.
Network systems administration: An employee wants to work from home but is unable to do so. The vice president of sales is looking for assistance with programming and software development to create a new software program to track sales.
Learn more about Computer here:
https://brainly.com/question/21080395
#SPJ2
which of the answers listed below refers to a standard that relies on serial communication?
Answers
The standard that relies on serial communication is PCIe (Peripheral Component Interconnect Express).The correct answer is option F.
PCIe is a high-speed serial communication protocol that allows for the transfer of data between devices, such as a graphics card and a motherboard, at a faster rate than its predecessor, PCI (Peripheral Component Interconnect).
ISA (Industry Standard Architecture) and PCI (Peripheral Component Interconnect) are both older parallel communication standards that have been largely replaced by newer standards, including PCIe.
PCI-X (PCI Extended) is an extension of the PCI standard that supports higher speeds and larger data transfer rates but still uses a parallel bus.
IEEE 1284 is a parallel communication standard for connecting printers and other peripheral devices to a computer. It has largely been replaced by USB and other serial communication standards.
In summary, PCIe is the standard that relies on serial communication, while ISA, PCI, PCI-X, and IEEE 1284 are all parallel communication standards that have been largely replaced by newer standards.
For more such questions on Peripheral Component Interconnect Express,click on
https://brainly.com/question/29856915
#SPJ11
The probable question may be:
Which of the answers listed below refers to a standard that relies on serial communication?
A.ISA
B.PCI-X
C.IEEE 1284
D.PCI
E,PATA
F.PCIe
What is the difference between soft copy output devices and hard copy output devices
Answers
the output printed on the paper is called hardcopy output. some examples are printer and plotter.
the output produced on display screen and audio sound is called soft copy output. some examples are moniter and speaker.
What does New Vegas Script Extender do?
Answers
The New Vegas Script Extender, also known as NVSE for short, is a modder's tool that enhances Fallout: NV's scripting capabilities.
What is the function of the script extender?You have probably encountered Skyrim Script Extender if you have done any amount of Skyrim modification. It is an add-on that greatly expands the effects that mods can have, and many more involved, game-changing mods require it.
How can the Fallout New Vegas Script Extender be tested for functionality?How can I verify? - Start NV, then type "GetNVSEVersion" into the console (without the quotes). The output ought to read "NVSE version: 1." If it functions, NVSE is in good working order.
To know more about Extender visit:-
https://brainly.com/question/13954583
#SPJ4
given an unsorted array of n elements find if the element k is present
Answers
To determine if a given element 'k' is present in an unsorted array of 'n' elements, we can use a linear search algorithm.
A linear search algorithm iterates through each element of the array starting from the first element and compares it with the desired element 'k'. If a match is found, the element 'k' is present in the array. If the entire array is traversed without finding a match, then 'k' is not present in the array. This algorithm has a time complexity of O(n), where 'n' is the number of elements in the array. The linear search approach is suitable for small or unsorted arrays, but for larger arrays or frequently performed searches, more efficient algorithms such as binary search or hashing can be employed.
Learn more about array here-
https://brainly.com/question/31605219
#SPJ11
Find out how to print the below pattern in python and also come up with pseudocode,
you have to use for loop for this, you can use a for loop inside the outer for loop.
You can't use operator like " *" in python , only use print statement to print the below pattern. Find out how to print in 5 lines one by one in python , there is a way to print one line then next
X
XXX
XXXXX
XXXXXXX
XXXXXXXXX
Answers
Answer:
for i in range(5):
for j in range(2*i + 1):
print("*", end="")
print()
Explanation:
for row index going from 0 to 5
for column index going from 0 to 2*row index + 1
print * suppressing new line
print a new line to move to next row
select all statements that are true about html: question 15 options: html can be used to create only static web pages; it can not create a dynamic web page. html can easily integrate with other languages and is easy to develop. html provides a high level of security. html displays content according to the window size or the device. html language is not centralized.
Answers
The true statements about HTML are the following:
1. HTML can be used to create only static web pages; it cannot create a dynamic web page.
2. html can easily integrate with other languages and is easy to develop.
3. HTML provides a high level of security.
4. HTML displays content according to the window size or the device.
What are the true statements?The true statements about HTML include the fact that it is only used in creating static web pages. The kinds of ages developed by this language are not high level so dynamic interactions might be difficult.
Also, this language can be easily integrated with other languages and it is not hard to develop. It also has a good level of security.
Learn more about HTML Here:
https://brainly.com/question/4056554
#SPJ1
Although software and internet technologies were american innovations, the manufacturing of computer hardware moved to latin america and asia.
a. True
b. False
Answers
The statement "Although software and internet technologies were American innovations, the manufacturing of computer hardware moved to Latin America and Asia." is a true statement. It is true because both have a lot of human resources.
What is manufacturing?Manufacturing is the advent or manufacturing of products with the assist of equipment, labor, machines, tools, and chemical or organic processing or formulation. It is the essence of secondary area of the economy. The time period may also seek advice from a variety of human activity, from handicraft to high-tech, however it's miles maximum generally carried out to business design, wherein uncooked substances from the number one area are converted into completed items on a huge scale. Such items can be bought to different producers for the manufacturing of different greater complicated products, or dispensed through the tertiary enterprise to give up customers and consumers.
Learn more about manufacturing https://brainly.com/question/13440987
#SPJ4
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
b. false
Answers
Answer:
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
It is true that a threat vector is an item of code on a distributed device that reports the condition of the device to a central server. The correct option is a.
What is a threat vector?The total number of attack vectors that an attacker can use to manipulate a network or computer system or extract data is referred to as the attack surface.
Threat vector and attack vector are interchangeable terms that describe the various ways a hacker can gain access to data or other confidential information.
The methods used by adversaries to breach or infiltrate your network are referred to as attack vectors.
Malware and ransomware, as well as man-in-the-middle attacks, compromised credentials, and phishing, are all examples of attack vectors.
A threat vector is a piece of code on a distributed device that reports the device's status to a central server.
Thus, the correct option is a.
For more details regarding a threat vector, visit:
https://brainly.com/question/28558110
#SPJ2
because a zip file is not actually a folder, you can avoid possible issues by
Answers
Because a zip file is not actually a folder, you can avoid possible issues by extracting its contents to a designated location before accessing or modifying the files
When we talk about a zip file, it's important to understand that it's not actually a folder, even though it may contain multiple files and subfolders.
Instead, a zip file is a compressed archive that allows you to store and transfer multiple files in a single package. However, using a zip file can sometimes create issues, particularly if you're working with large or complex files.
To avoid these potential problems, it's important to understand the limitations of zip files and use them appropriately.
For example, you may need to consider using a different file format, such as a folder or cloud storage, if you need to maintain file structures or work with large amounts of data.
Learn more about Zip File at https://brainly.com/question/28495274
#SPJ11
sql which animal(s) have a `time to feed' larger than every rare animal? give the id and name of the animal.
Answers
The SQL to solved that problems are SELECT id, name FROM animals WHERE time_to_feed > ALL (SELECT time_to_feed FROM animals WHERE rare = 'true');
To find the animal(s) with a `time to feed' larger than every rare animal, we can use a subquery to find the maximum `time to feed' value for rare animals and then compare it to the `time to feed' value for all animals. The query would look something like this: ```sql SELECT id, name FROM animals WHERE time_to_feed > (SELECT MAX(time_to_feed) FROM animals WHERE rare = 1); ``` This query first finds the maximum `time to feed' value for rare animals using the subquery `(SELECT MAX(time_to_feed) FROM animals WHERE rare = 1)`. It then compares this value to the `time to feed' value for all animals using the `>` operator. The result will include the id and name of any animals with a `time to feed' value larger than the maximum `time to feed' value for rare animals.
Here you can learn more about SQL https://brainly.com/question/30478519
#SPJ11
Which key will s the ring finger located on
Answers
Each hand's fingers should rest on four different keys. The "A" key is pressed with the pinky finger of the left hand, the "S" key with the ring finger, the "D" with the middle finger, and the "F" with the index finger.
Which hand should the ring be on?right hand, Just prior to the wedding ceremony, the wedding band is exchanged for the engagement ring on the right hand so that it can be worn on the left hand, which is closest to the heart. Following the ceremony, the wedding band is replaced with the engagement ring.
On what letter or key is the left ring finger placed?The home row keys on an English keyboard are A-S-D-F and J-K-L-;. The left hand's pointer is on the F, the ring finger is on the S, the middle finger is on the D, and the little finger is on the A.
to know more about keys here:
brainly.com/question/16860977
#SPJ1
ASAP! Due by tonight!!!! Please help!!!

Answers
Answer: e
Explanation:
TRUE OR FALSE (1 POINT EACH) 11. Most computers typically fall into one of three types of CPU organization: (1) general Register organization; (2) single accumulator organization;or (3) stack organization.
Answers
TRUE. Most computers typically fall into one of three types of CPU organization: general Register organization, single accumulator organization, or stack organization.
There are three main types of CPU organization that are commonly used in computer architecture:
General register organization: In this type of organization, the CPU has a set of general-purpose registers that can be used to hold data and perform arithmetic and logical operations. Each register has a unique identifier, and data can be moved between registers using load and store instructions.Single accumulator organization: In this type of organization, the CPU has a single accumulator register that is used as the primary location for arithmetic and logical operations. Data is loaded into the accumulator from memory or other registers, and the result of an operation is stored back into the accumulator.Stack organization: In this type of organization, the CPU uses a stack to store data and perform operations. Data is pushed onto the stack and popped off the stack as needed, and arithmetic and logical operations are performed on data that is on the top of the stack.Learn more about registers here:
https://brainly.com/question/16740765
#SPJ11
How might you use what you learned about
creating a vision board in the future?
Answers
How to resolve' command phasescriptexecution failed with a nonzero exit code
Answers
To resolve the 'command phase script execution failed with a nonzero exit code' error, you can check your project settings, make sure your code is properly configured, or update any dependencies that may be causing the error.
The 'command phase script execution failed with a nonzero exit code' error is a common issue that can occur when running code on a computer or server. It often indicates that there is a problem with the project settings or that the code is not properly configured to run.
To resolve the error, you can check your project settings and ensure that everything is configured correctly. You can also review your code and make sure that it is free of errors or issues. If the error persists, you may need to update any dependencies or packages that are causing the problem. By taking these steps, you can resolve the 'command phase script execution failed with a nonzero exit code' error and get your project back on track.
You can learn more about coding errors at
https://brainly.com/question/28583871
#SPJ4
Digital signals transmit zeros and ones through changes in
frequency
light intensity
voltage
Answers
Answer
voltage
Explanation:
the other person is correct i got a 100 % thanks to them
Which situations make use of interactive multimedia and which do not? Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister. Roy is going through a tutorial on his laptop that explains a do-it-yourself project. Jaden is listening to a presentation on early music in his class. Fred is answering an online quiz that requires him to select correct answers. Linear Multimedia Kristen is watching an educational film on her tablet. Non-linear Multimedia
Answers
The situation that make use of interactive multimedia is Roy is going through a tutorial on his laptop that explains a do-it-yourself project, and that do not is Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister.
What is an interactive multimedia?Interactive multimedia is a type of interaction in which the user can operate, control, and change the text, image, and picture, and function in a phone or computer.
Thus, the correct options are A and B.
Learn more about interactive multimedia
https://brainly.com/question/26090715
#SPJ1
with respect to saving energy, what aspect of using two-sided printing was discussed in class as providing the most signifiant benefit?
Answers
The use of double-sided printing will contribute to energy savings because we only need one sheet of paper instead of two to print two pages.
Why duplex printing can save the world?Duplex printing is an environmentally friendly printing method. It uses half a sheet of paper, requires less power, and takes up less space than single-sided printing. Arizona State University has saved more than 700 trees after switching to double-sided printing. It is estimated that duplex printing can save your business about half the cost of printing single-sided pages. Because duplex printing uses half the amount of paper used for single-sided printing, businesses can reduce material costs. You are not only protecting the trees of our planet, but you are also saving your business money.
Learn more about the benefit of double-sided printing https://brainly.com/question/29817229
#SPJ4
Should a student have to redo work even though it was the teacher's fault for losing the assignment(s)?
My biology teacher lost TWO of my assignments. He KNOWS that I gave the assignments to him. We both came to the conclusion that either he had misplaced it or it was stolen.
Answers
One of my teachers kept saying he didn’t get an assignment from me so I redid it and he once again said I didn’t do it so I ended up doing it three times and then a few weeks later he found all three
So no
list 4 functions of algorithm .ASAP,pls no Links!!! Thanks
Answers
Answer:
Simple recursive algorithms.
Backtracking algorithms.
Divide and conquer algorithms.
Dynamic programming algorithms.
Explanation:
a content management system (cms) is hosted on a fleet of auto-scaled, on-demand ec2 instances that use amazon aurora as its database. the system stores the file documents users upload on attached ebs volumes and system performance is slow. what will you do to implement a scalable, high-available posix-compliant shared file system?
Answers
To implement a scalable, high throughput POSIX-compliant file system, migrate the file documents to an Amazon Elastic File System (EFS).
EFS provides scalable, high throughput, highly durable file storage for use with Amazon EC2 instances. It is POSIX-compliant and provides a simple and cost-effective way to deliver file storage to applications. With EFS, you can auto-scale your file system capacity up and down based on your file storage needs, providing a reliable, performance storage option for the content management system. There are a few steps that you can follow to implement a scalable, high throughput POSIX-compliant file system. The steps are as follows,
1. The first step is to create an Amazon EFS file system that is POSIX-compliant.
2. The next step is to configure Amazon EFS with the content management system (CMS) that is hosted on the fleet of auto-scaled, On-Demand EC2 instances.
3. After configuring Amazon EFS with the content management system (CMS), you can start using the POSIX-compliant file system for storing file documents uploaded by the users. This will improve the system's performance and enable the system to handle high throughput.
To summarize, to implement a scalable, high throughput POSIX-compliant file system, you should create an Amazon EFS file system that is POSIX-compliant and configure it with the content management system (CMS). After configuration, use the file system for storing file documents uploaded by the users.
The Complete question is:
A content management system (CMS) is hosted on a fleet of auto-scaled, On-Demand EC2 instances which use Amazon Aurora as its database. Currently, the system stores the file documents that the users uploaded in one of the attached EBS Volumes. Your manager noticed that the system performance is quite slow and he has instructed you to improve the architecture of the system.
In this scenario, what will you do to implement a scalable, high throughput POSIX-compliant file system?
Know more about Elastic File System (EFS) here :
https://brainly.com/question/13769983
#SPJ11
What is a ternary operator? Explain with the help of an example.
The ternary operator deals with three operands. It is also known as a conditional operator. In this operator, the value of the variable depends on the logical expression.
Example:
int a = 5:
int b = 3;
int max = (a > b)? a : b;
Answers
A ternary operator, also called a conditional operator, is a special kind of operator used in some programming languages as a shorter way of writing an if..else block. It is denoted by a question mark and then a colon (? : ). It takes 3 operands:
i. A boolean expression which would evaluate to a true or a false.
ii. A first value that will be assigned if the boolean expression gives a true.
iii. A second value that will be assigned if the boolean expression gives a false.
The general format is:
variable = boolean expression ? first_value : second_value;
For example:
A ternary expression can be written as;
String f = (3 > 5) ? "yes" : "no";
In the above expression;
The boolean expression is 3 > 5
The value to be assigned, to f, if the boolean expression is true is "yes"
The value to be assigned, to f, if the boolean expression is false is "no"
So in this case, since (3 > 5) evaluates to false, "no" will be assigned to f.
Therefore, the above expression will give the same result as;
String f = "no"
Another example:
=================
int a = 5:
int b = 3;
int max = (a > b)? a : b;
==================
In the above code snippet,
Since a > b i.e 5 > 3, the first value a (which is equal to 5) will be assigned to max.
Therefore, int max = 5.
The value of max is 5
PS:
These examples and explanations are given using Java. Similar scenario, maybe different syntax, will be obtainable in other programming languages.
true/false. the output unit of a pc performs calculation and logical decisions.
Answers
The given statement, "The output unit of a pc performs the calculation and logical decisions" is false, because the output unit of a PC is responsible for displaying information to the user and presenting the results of calculations and logical decisions made by the computer's processor.
The output unit of a PC is critical in displaying data and information in a way that the user can readily see and understand. This category contains monitors, printers, speakers, and other output peripherals. Its major role is to translate processed data into a human-readable form or format, allowing users to efficiently engage with the computer system.
While the output unit can display the results of the computer's processor's calculations and logical decisions, it is important to note that the actual execution of these calculations and logical decisions take place within the central processing unit (CPU) or other components of the computer system. The output unit's role is to convey the processed information to the user in a meaningful way, whether through visual, auditory, or other sensory means.
To learn more about the Central processing unit, visit:
https://brainly.com/question/26991245
#SPJ11
To qualify an examination, candidates must pass one compulsory subject S1 and one of the three optional subjects S2, S3, and S4. Write the Boolean Expression which correctly represents this scenario?
Answers
Answer:
S1 AND (S2 OR S3 OR S4)
Explanation:
Above expression doesn't exclude passing more than one of S2, S3 and S4, which makes sense.
he Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Answers
The function "Get_Winnings(m, s)" takes a string for the number of gold medals and an integer for the sponsored dollar amount, returning the money won as an integer or "Invalid" if the amount is invalid.
The function "Get_Winnings(m, s)" takes two parameters: a string "m" representing the number of gold medals and an integer "s" representing the sponsored dollar amount. Here's a step-by-step explanation of the function.
Check if the input values are valid. If the "m" parameter is not a string or the "s" parameter is not an integer, return the string "Invalid".Convert the string "m" to an integer to calculate the total winnings based on the number of gold medals won.Calculate the money won by multiplying the number of gold medals with the sponsored dollar amount.Return the calculated winnings as an integer.If the input values are not valid or cannot be converted, the function will return the string "Invalid" to indicate an invalid amount. Otherwise, it will return the calculated money won as an integer.
For more such question on Integer
https://brainly.com/question/30030325
#SPJ8
write a specification file of a class name sample, with private data members( one intezer, one character, one boolean) and all the necessary methods, including (find(), isthere()) methods?
Answers
The specification file for the "Sample" class with private data members and necessary methods including "find()" and "isThere()" methods should be written in a proper format as per the class definition.
An explanation of how to write a specification file for a class named "Sample" with private data members (an integer, a character, and a boolean) and necessary methods including "find()" and "isThere()" methods is as follows:
The specification file should begin with the class definition and its private data members. The class should have an integer, a character, and a boolean data member declared as private. Following the private data members, necessary public methods must be declared.
The "find()" method should be a public method that accepts an integer parameter and returns a boolean. This method checks whether the passed integer parameter matches the integer data member of the class. If the integer parameter matches the integer data member, then the method returns "true"; otherwise, it returns "false."
The "isThere()" method should be a public method that accepts a character parameter and returns a boolean. This method checks whether the passed character parameter matches the character data member of the class. If the character parameter matches the character data member, then the method returns "true"; otherwise, it returns "false."
To know more about data members visit:
brainly.com/question/15694646
#SPJ11
what are the answers for theses question?




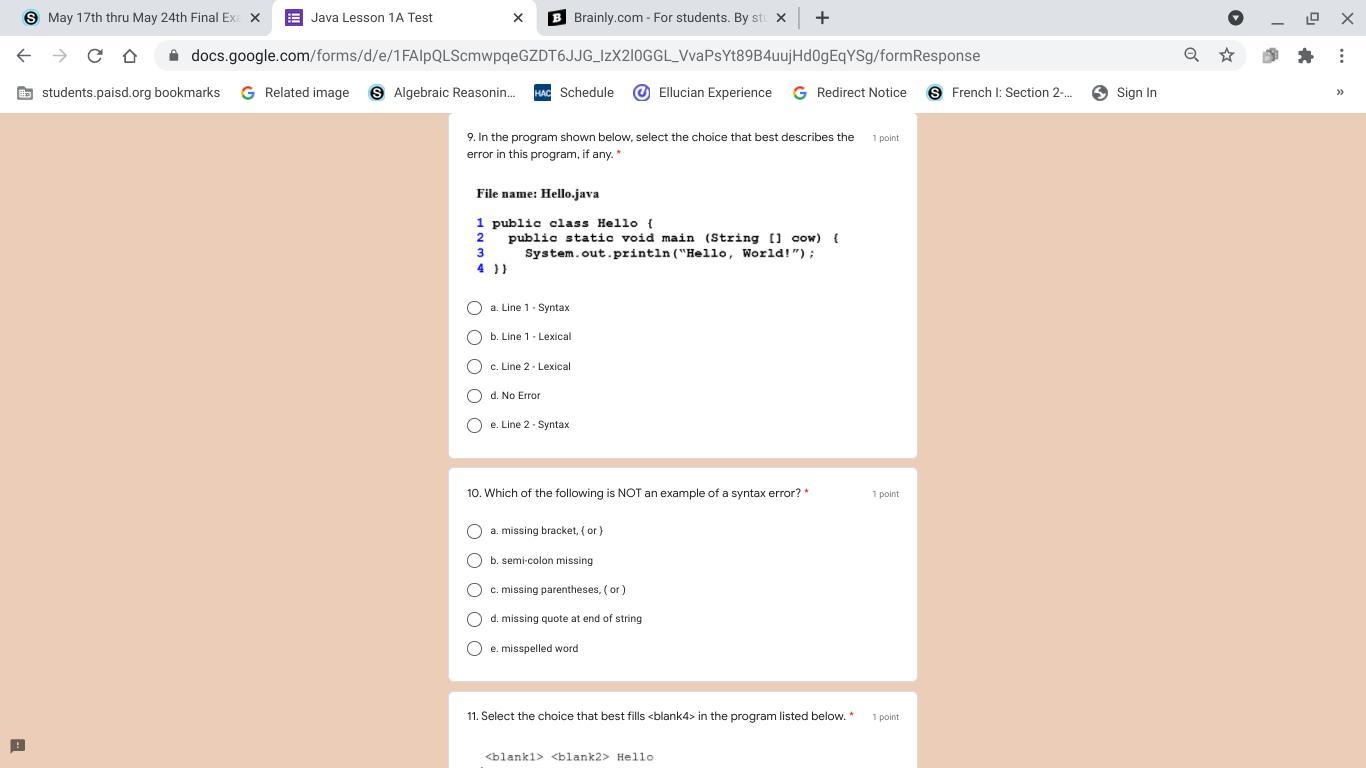
Answers
Answer: me no comprende coding
Explanation:
sorry
Database Systems
1) To change a column that currently rejects null values so that it accepts null vlaues, use the ___ clause in the ALTER TABLE command.
2) If you specified ___ for the column when you created the table, then changing a value in a column to null is prohibited.
Answers
1) The NULL keyword is used in the ALTER TABLE command to change a column that currently rejects null values so that it accepts null values. In addition, it also makes an already existing column in the table able to accept null values. The NULL keyword is used to explicitly specify that the column accepts null values.
2) If you specified NOT NULL for the column when you created the table, then changing a value in a column to null is prohibited. NOT NULL indicates that the column will not allow null values. You can, however, use the ALTER TABLE statement to change this constraint so that it allows null values. You will first need to delete any existing values in the column before it can be changed to accept null values.
Know more about NULL here:
https://brainly.com/question/31559630
#SPJ11