You are configuring the router for a Small Office Home Office (SOHO) network that uses Voice over Internet Protocol (VoIP). The company wants to make sure teleconferences run smoothly, without network issues. What is the quickest and most cost-efficient way to
Answers
To ensure smooth teleconferences in a SOHO network using VoIP, prioritize VoIP traffic using Quality of Service (QoS) settings on the router and ensure sufficient bandwidth allocation.
The quickest and most cost-efficient way to configure the router for a Small Office Home Office (SOHO) network that uses Voice over Internet Protocol (VoIP) and ensures smooth teleconferences is as follows:
1. Prioritize VoIP Traffic: Enable Quality of Service (QoS) settings on the router to prioritize VoIP traffic over other types of data. QoS ensures that voice packets are given higher priority and allocated sufficient bandwidth to minimize latency and packet loss.
This helps maintain call quality and reduces the chances of voice distortion or dropped calls during teleconferences.
2. Bandwidth Management: Assess the available bandwidth and allocate sufficient resources for VoIP traffic. It is important to have a reliable and high-speed internet connection to support concurrent voice calls. Consider upgrading the internet plan if necessary, ensuring adequate upload and download speeds to handle the expected call volume.
3. Enable Port Forwarding: Configure the router to forward necessary ports for VoIP communication. VoIP typically uses protocols such as SIP (Session Initiation Protocol) or RTP (Real-time Transport Protocol). By enabling port forwarding, incoming and outgoing VoIP traffic will be directed to the appropriate devices on the network, allowing seamless communication during teleconferences.
4. Enable Firewall and Security: Implement robust security measures on the router to protect the network from unauthorized access and potential threats. Enable a firewall to block unwanted traffic and configure security features such as intrusion detection and prevention systems (IDS/IPS) to monitor network activity.
5. Regular Firmware Updates: Ensure the router's firmware is up to date. Manufacturers frequently release updates that address security vulnerabilities and improve overall performance. Regularly check for firmware updates and apply them to keep the router functioning optimally.
By following these steps, you can quickly and cost-effectively configure the router for a VoIP-enabled SOHO network, providing a smooth teleconferencing experience with minimal network issues.
The complete question is:
"You are configuring the router for a Small Office Home Office (SOHO) network that uses Voice over Internet Protocol (VoIP). The company wants to make sure teleconferences run smoothly, without network issues. What is the quickest and most cost-efficient way to configure the router to achieve this?"
Learn more about router:
https://brainly.com/question/24812743
#SPJ11
Related Questions
Define a function CalcPyramidVolume() with double data type parameters baseLength, baseWidth, and pyramidHeight, that returns as a double the volume of a pyramid with a rectangular base. CalcPyramidVolume() calls the given CalcBaseArea() function in the calculation. Relevant geometry equations: Volume
Answers
The CalcPyramidVolume() function provides a simple and reusable way to calculate the volume of a pyramid with a rectangular base, given its dimensions.
Here's an example implementation of the function CalcPyramidVolume() in C++ that takes the base length, base width, and pyramid height as double parameters and returns the volume of a pyramid with a rectangular base:
cpp
Copy code
double CalcPyramidVolume(double baseLength, double baseWidth, double pyramidHeight) {
double baseArea = CalcBaseArea(baseLength, baseWidth);
double volume = (baseArea * pyramidHeight) / 3.0;
return volume;
}
This function first calculates the area of the rectangular base by calling the given CalcBaseArea() function, which takes the base length and width as parameters and returns the base area. It then multiplies the base area by the pyramid height and divides the result by 3.0 to calculate the volume of the pyramid. Finally, it returns the volume as a double.
Note that the CalcBaseArea() function is assumed to be provided by the caller and is not implemented in this example.
You can call this function with the base length, base width, and pyramid height as arguments, like this:
double volume = CalcPyramidVolume(5.0, 6.0, 8.0);
This would set the variable volume to the calculated volume of the pyramid with a base length of 5.0, a base width of 6.0, and a height of 8.0.
Learn more about returns here:
https://brainly.com/question/29569139
#SPJ11
Which of these is NOT an example of intellectual property? O a song you wrote O an article you published O hardware you purchased O a sculpture you created Question 5 9
Answers
Answer:
hardware you purchased
Explanation:
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
Patent can be defined as the exclusive or sole right granted to an inventor by a sovereign authority such as a government, which enables him or her to manufacture, use, or sell an invention for a specific period of time.
Generally, patents are used on innovation for products that are manufactured through the application of various technologies.
Basically, the three (3) main ways to protect an intellectual property is to employ the use of
I. Trademarks.
II. Patents.
III. Copyright.
An intellectual property can be defined as an intangible and innovative creation of the mind that solely depends on human intellect. They include intellectual and artistic creations such as name, symbol, literary work, songs, graphic design, computer codes, inventions, etc.
Hence, a hardware you purchased is not an example of an intellectual property.
Which utility causes the computer to run slow? defragmentation utility OR compression utility?
Answers
Answer:
compression
Explanation:
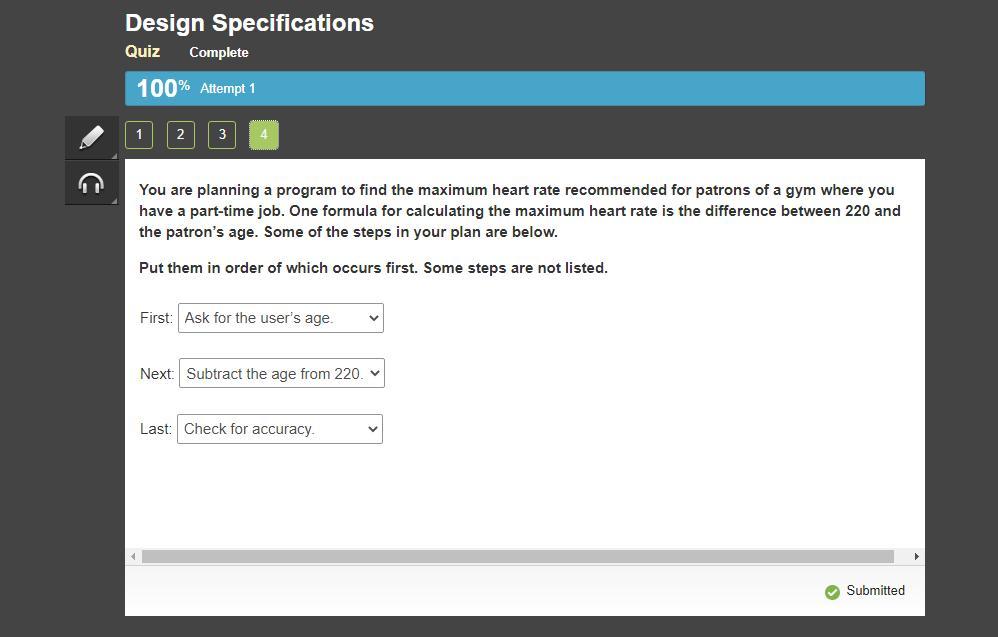
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
Segregation based on laws is called _____
legal segregation
segregation
de jure segregation
de facto segregation
Answers
Answer:
C aka De Jure Segregation
Explanation:
E2021
Segregation based on laws is called de jure segregation. Thus, the correct option for this question is C.
What is meant by segregation in-laws?The meaning of segregation reveals a type of condition that takes one of these classes and isolate it from all the others. It is an act or process of segregating things from other things.
In law, it is an act through which a person separates other persons on the basis of race, color, language, religion, nationality, or national or ethnic origin without an objective and reasonable justification.
Segregation is the official practice and process of keeping two or more people apart, usually people of different sexes, races, or religions. Racial segregation in schools was ruled unconstitutional.
Therefore, segregation based on laws is called de jure segregation. Thus, the correct option for this question is C.
To learn more about segregation in law, refer to the link:
https://brainly.com/question/30186311
#SPJ6
how has the dependence on technology made humanity less intelligent?
Answers
Answer:
People now rely on the internet for answers.
Nobody truly learns stuff and keeps it with them anymore. They know they can just search it again, and get the answer.
Tanya wants to include an instructional video with all its controls on her office website. The dimensions of the video are as follows: width=260, height=200. What code should tanya use to insert the video?

Answers
Answer:
Explanation:
In this scenario the two pieces of code that Tanya is missing would be controls and type. Controls adds the necessary video player controls while type signals what type of content will be playing. Therefore, the entire code snippet should be the following
<video width="320" height="240" controls>
<video src="file name.mp4" type="video/mp4">
</video>
What are the two components of the FRID system? How does the
reader extract the data stored on the RFID tag.
Answers
The two components of the RFID system are the RFID tag and the RFID reader.
The RFID tag is a small electronic device that contains a microchip and an antenna. It is attached to or embedded in an object or product. The tag stores information or data that can be read by the RFID reader. The data stored on the tag can be unique identification numbers, product details, or other relevant information.
The RFID reader is a device that is used to communicate with the RFID tag. It emits radio frequency signals that power the tag and extract the data stored on it. The reader sends out a radio frequency signal which is picked up by the antenna on the RFID tag. The tag then uses the energy from the signal to power up and transmit the data back to the reader.
Here is a step-by-step process of how the reader extracts the data stored on the RFID tag:
1. The reader emits a radio frequency signal.
2. The antenna on the RFID tag picks up the signal and uses it to power up.
3. Once powered up, the tag sends back a response signal containing the data stored on it.
4. The reader receives the response signal and decodes the data.
5. The decoded data is then processed and used for various applications such as inventory management, access control, or tracking purposes.
For example, let's say you have a library book with an RFID tag attached to it. When you approach the library's entrance with the book, the RFID reader emits a radio frequency signal. The tag on the book picks up the signal, powers up, and sends back the book's identification number. The reader receives the response signal, decodes the identification number, and processes it to check if the book is properly checked out or not.
In summary, the two components of the RFID system are the RFID tag and the RFID reader. The reader extracts the data stored on the tag by emitting a radio frequency signal, which powers up the tag and enables it to transmit the data back to the reader.
To learn more about RFID system
https://brainly.com/question/30498263
#SPJ11
the only software component that’s required to run a web application on a client is
Answers
The only software component that’s required to run a web application on a client is a web browser.
A web application is a program or software that runs on a web server and is used by clients over the internet. Web applications are designed to be compatible with multiple platforms, including smartphones, tablets, and computers.
Because they are platform-independent, web applications can be run on a variety of devices without requiring specialized software.
A web browser is a program that displays web pages and content on the internet. It is a client-side software that is installed on a computer or mobile device and is used to access web applications and websites. It provides users with a graphical interface to access web-based content, such as text, images, videos, and multimedia.
Web browsers use HTTP (Hypertext Transfer Protocol) to request and transmit data to and from web servers. Web applications are accessed using web browsers. A web browser is the only software component that’s required to run a web application on a client.
It acts as a user interface that communicates with the web server where the application is hosted. When a user accesses a web application, the web browser sends a request to the web server to retrieve the necessary data and displays the results on the user’s device.
To learn more about software: https://brainly.com/question/28224061
#SPJ11
PLEASE HELP, Answer Correctly..Will give a bunch of brainlist points

Answers
Answer:
se ve muy dificil amiga
Explanation:
Write this name in your handwriting on a piece of paper best handwriting gets branilist

Answers
Cursive and continuous cursive are often considered to be the best handwriting styles for students to learn.
Which handwriting style is best?The two handwriting techniques that are generally regarded as the finest for students to acquire are cursive and continuous cursive.
Narrow right margins, a clear right slant, and lengthy, tall T-bars are all common writing characteristics. Other characteristics of the writers of the writing were also revealed by other handwriting characteristics.
Even writing with a pen and paper requires the use of muscle memory. Writing nicely will be more difficult for you if you don't regularly practise. Your handwriting will get much better if you spend 10 to 15 minutes each day writing neatly and slowly.
There are three of them: print, pre-cursive, and cursive.
1. Cursive
2. Pre-cursive
3. Print
To learn more about handwriting refer to:
https://brainly.com/question/1643608
#SPJ1
Iciples UI
32
Select the correct answer.
Sheila is using a word processor to describe the procedure for performing a science experiment. What should she do to make it easier to read
the steps in the procedure?
A
use a numbered list to present the steps
B. align the steps with the right margin
C. decrease the line spacing between steps
D
center align the steps
Reset
Next
Answers
Answer:A
Explanation: I took the test !
The scientific procedure used by Sheila in the word processor can be processed for the ease with the numbering of the steps in the list.
What is a word processor?The word processor is given as the computer program that has been used for the working of the document with making it editing, formatting, and adding the features to the document.
The word processing for the scientific experiment involves the series of events that takes place in the sequential order, thereby the easier way to read the process used by Sheila must be the numbering of the list.
Therefore, Sheila using the word processor describe the scientific procedure in the number list presenting steps. Thus, option A is correct.
Learn more about word processor, here:
https://brainly.com/question/14126052
#SPJ2
Which are popular two-factor authentication strategies used by online services like cloud storage or online banking?
Answers
The two popular two-factor authentication strategies used by online services like cloud storage or online banking are: 1) SMS-based authentication, and 2) Time-based One-Time Password (TOTP).
In SMS-based authentication, the user receives a unique code via text message to their registered mobile phone number. The user must enter this code on the platform to verify their identity.
TOTP, on the other hand, involves generating a temporary, unique password (usually valid for 30-60 seconds) using an authenticator app on the user's mobile device. The app is synced with the service, and the user must enter the generated password to gain access. Both methods aim to provide an additional layer of security beyond traditional username and password combinations, making it more challenging for unauthorized individuals to gain access to sensitive accounts and information.
Learn more about authentication here:
https://brainly.com/question/31525598
#SPJ11
What is the relationship between hardware and software technology tools?
Hardware tools are internal and external data programs that are used by software to perform a given task.
Software tools are internal and external data programs that are used by hardware to perform a given task.
Hardware tools are the programs used by software to perform a certain task.
Software tools are the programs used by hardware to perform a certain task.
Answers
Answer: Hardware consists of the physical devices associated with a computer system. Software is the set of instructions that the hardware executes to carry out specific tasks.
Answer:
Answer is Software tools are the programs used by hardware to perform a certain task.
Explanation:
Got the question right
A computer game allows a player to repeat a level until they run out of lives. Which two of the following loops would work correctly?

Answers
Answer:
c.
Explanation:
because this is the right syntax for the following loops
what is the minimum media type that must be used to run 1000base-t?
Answers
The 1000BASE-T standard for gigabit Ethernet recommends maximum length for each 1000BASE-T network segment is 100 metres (330 feet), and Category 5 cable or above is required (including Cat 5e and Cat 6).
The Institute of Electrical and Electronics Engineers' abbreviation for 1000Base-T (IEEE). The 1,000 stands for baseband signalling, which means that solely Ethernet signals are being transported over this medium, and "base" stands for the transmission speed of 1,000 Mbps. The twisted pair of wires used by this technology are denoted by the letter "T."
Copper wires are the medium for the gigabit Ethernet networking technology known as 1000Base-T. 1000Base-T can be utilised in desktop PCs for broadband applications or in data centres for quick server switching.
The main benefit of 1000Base-T is that it may utilise existing copper wiring, eliminating the requirement to redesign the system with more recent optical fibre lines. Due to its 10 times faster speed, 1000Base-T progressively replaced fast Ethernet for wired local networks and into widespread use in 1999.
By 2011, equipment and cables were widely available and reasonably priced, and they were substantially similar to earlier Ethernet standards. These were the main determinants of the widespread acceptance of this standard.
To learn more about Cat 5e click here:
brainly.com/question/27204453
#SPJ4
what kind of off brand Apple Pencil work with an iPad Air 2?
Answers
When it comes to finding an off-brand Apple Pencil that is compatible with an iPad Air 2, there are a few things to consider. The first thing is that the iPad Air 2 does not have the same technology as the iPad Pro models, which means that it cannot use the same Apple Pencil.
Instead, the iPad Air 2 requires a stylus that uses a capacitive touch screen, which is the same technology used in most other touch screen devices. This means that any stylus that is compatible with a capacitive touch screen should work with the iPad Air 2.
There are many off-brand styluses on the market that claim to work with the iPad Air 2, so it can be difficult to know which ones to choose. Some popular options include the Adonit Jot Pro, the Wacom Bamboo Sketch, and the Fifty Three Pencil. These styluses all have different features and designs, so it's important to do your research and find one that meets your needs.
Ultimately, the best off-brand Apple Pencil for your iPad Air 2 will depend on your specific needs and preferences. It's important to read reviews and compare different models to find one that works well with your device and meets your needs.
To know more about Pencil visit:
brainly.com/question/25153759
#SPJ11
It is a cooking equipment used to heat and cook food
Answers
Answer: Oven
Explanation:
Define a function calc_pyramid_volume() with parameters base_length, base_width, and pyramid_height, that returns the volume of a pyramid with a recta
Answers
Answer:
Te ayuda
Explanation:¿Cuál es la fórmula para calcular el volumen de una pirámide rectangular?
Resultado de imagen para Defina una función calc_pyramid_volume() con los parámetros base_length, base_width y pyramid_height, que devuelve el volumen de una pirámide con una recta
El volumen de una pirámide rectangular es definido como el espacio tridimensional ocupado por esta figura. Podemos calcular la medida de este volumen al multiplicar al área de la base por la altura de la pirámide y dividir por tres.
Which of the following selectors will target this paragraph?
Paragraph 1
a) p
b) #firstP
c) p#firstP
d) all of the above
Answers
aaaaaaaaaaaaaaaaaaaaa
A network administrator is designing a new network infrastructure that includes both wired and wireless connectivity. Under which situation would a wireless connection be recommended?.
Answers
Wireless connectivity is recommended for use with laptops or mobile devices, especially as newer devices are less likely to have ethernet connectivity built in. In either case, use of wireless technology make it easier for users to move around without having to worry about being plugged in. Wired connections are still recommended for anything that doesn't need to be able to move as it is generally more reliable, and depending on the devices involved, could offer a faster connection.
Jett has agreed to invest $12,000 in a partnership with her sister and brother-in-law. Jett does not plan to work in the partnership, nor does she wish to risk any of her own wealth other than the $12,000 she invests, but she does intend to share in any profits earned by partnership. Evidently, Jett will be a(n):
Answers
Jett will be a limited partner in the partnership. As a limited partner, she has agreed to invest a specific amount of capital, in this case, $12,000, and will not be actively involved in the day-to-day operations or management of the partnership. This means that Jett will not be taking on any personal liability for the partnership's debts or obligations beyond her initial investment.
The role of a limited partner is primarily that of an investor. Jett's main objective is to share in any profits earned by the partnership. Typically, the share of profits is determined by the partnership agreement and may be based on the amount of capital invested or through other agreed-upon terms.
By not actively participating in the partnership, Jett is able to mitigate her risk and protect her personal wealth. This is in contrast to general partners who are actively involved in the partnership's operations and assume personal liability for the partnership's debts and obligations.
It is important to note that the specific rights and responsibilities of limited partners may vary depending on the jurisdiction and the partnership agreement. Therefore, it is crucial for Jett to review the partnership agreement carefully to understand the terms and conditions of her involvement as a limited partner.
Learn more about Investing Partnership :
https://brainly.com/question/28458958
#SPJ11
Writing a program to calculate a person's BMI is an example of using a math algorithm. In the BMI case,
you used a formula to find a person's BMI and assigned the result to a category. Your program handled
possible errors. This man needs to be concerned about his potential errors.
Answers
Answer:
BMI is calculated = mass or weight in kilograms / height in meters.
Examples:
Input : height(in meter): 1.79832
weight(in Kg): 70
Output : The BMI is 21.64532402096181, so Healthy.
Explanation : 70/(1.79832 ×1.79832)
Input : height(in meter): 1.58496
weight(in Kg): 85
Output : The BMI is 33.836256857260594 so Suffering from Obesity
Explanation : 70/(1.58496×1.58496).
What is a benefit of interference in quantum computing?
Answers
By enhancing or weakening the wave functions of quantum particles, interference is a technique for regulating the quantum states of a quantum system.
As a result, quantum states producing the right output can be increased, whereas those producing the wrong output can be cancelled later. Interference is a method for controlling the quantum states of a quantum system by strengthening or weakening the wave functions of quantum particles. As a result, quantum states that produce the desired results can be strengthened, while those that produce undesirable results can be later cancelled. Quantum computers are tremendously quick and efficient when used properly. They are capable of calculations that would take today's supercomputers decades or perhaps millennia to complete.
Learn more about quantum here-
https://brainly.com/question/14894495
#SPJ4
which listing of brain-imaging technologies is from oldest to newest
Answers
The listing of brain-imaging technologies from oldest to newest is as follows: 1) X-rays, 2) Computed Tomography (CT), 3) Magnetic Resonance Imaging (MRI), 4) Positron Emission Tomography (PET), and 5) functional Magnetic Resonance Imaging (fMRI).
X-rays:
X-rays were one of the earliest imaging technology used in medicine, including brain imaging. However, they have limited ability to visualize brain structures and are now less commonly used for brain imaging due to the availability of more advanced techniques.Computed Tomography (CT):
CT scans use X-rays and computer processing to create detailed cross-sectional images of the brain. It provides better structural information than X-rays alone.Magnetic Resonance Imaging (MRI):
MRI utilizes strong magnetic fields and radio waves to generate detailed images of the brain's structures. It provides high-resolution anatomical images.Positron Emission Tomography (PET):
PET scans involve injecting a radioactive tracer into the body, which emits positrons. The scanner detects these positrons to measure blood flow, metabolism, and other functions of the brain.Functional Magnetic Resonance Imaging (fMRI):
fMRI measures changes in blood oxygenation to detect brain activity. It provides detailed images of brain function and is commonly used in cognitive neuroscience research.To learn more about technology: https://brainly.com/question/7788080
#SPJ11
a diagram of a flow chart to find the average of 10 numbers
Answers
Answer:
Kindly check attached picture
Explanation:
Flowchart gives a graphical representation of a steps taken towers the execution of a program.
In the flowchart attached, A variable was initialized and set to 0 ; then a for loop was used to iterate integers 1 up to 10, for each number. It is added to the initialized variable sum until all the 10 integer numbers are added. The the average is obtained by dividing by 10.

What is the full form of UNIVAC, QBASIC?
Answers
UNIVersal Automatic Computer (UNIVAC)
Quick Beginner's All-Purpose Symbolic Instruction Code (QBasic)
Explanation:
UNIVAC:Universal Automatic Computer
QBASIC:Quick Beginner's All-Purpose Symbolic
Instruction Code
Keep smiling and hope u r satisfied with my answer.Have a great day :)
speed(?)
penup?
? (-200, -200)
? (90)
Pendown?
begin_fill?
? ("tan")
#Trace the outside of the grid (shape is a square)
? (400)
right(?)
? (400)
right(?)
? (400)
right(?)
? (400)
right(?)
end_fill?
? Go to lower, left corner of R and have turtle look up. Pen and shape fill blue
?()
set position(?)
?()
? ("blue")
begin_fill?
? Trace the outside of the letter R.
forward(?)
? (90)
? (160)
right(?)
forward(?)
? (90)
? (20)
? (100)
? (120)
right(?)
? (40)
right(?)
? (120)
? (80)
forward(?)
left(?)
? (120)
? (90)
? (40)
right(?)
end fill ()
? Move to inside of R (lower left corner). Color tan and fill the shape.
penup?
? (-40,20)
?()
color ("?")
begin_fill?
? Trace the inside of R (shape is a square).
forward(?)
? (90)
? (80)
right(?)
forward(?)
? (90)
? (80)
right(?)
end_fill?
? Go to lower, left corner of R. Make pen white and pensize 8.
?()
? (-80, -140)
? ("white")
pensize(?)
?()
? Trace outside of the letter R.
forward(?)
? (90)
? (160)
right(?)
forward(?)
? (90)
? (20)
? (100)
? (120)
right(?)
? (40)
right(?)
? (120)
? (80)
forward(?)
left(?)
? (120)
? (90)
? (40)
right(?)
? Move to inside of R (lower left corner).
penup?
? (-40,20)
?()
? Trace the inside of R (shape is a square).
forward(?)
? (90)
? (80)
right(?)
forward(?)
? (90)
? (80)
right(?)
Answers
Answer:
used HP UC visit relationship Nurs.Makrapar.
how do you get your winkey wet??
Answers
Answer:
what
Explanation:
what
sorry but what
Answer:
what is a winkey.
Explanation:
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11