Write a program that will search through an array and check to see if the first number in the array occurs more than once. If the first number occurs more than once, return true. Otherwise, return false. If the array is empty, return false.
Answers
Here's a sample implementation of a program in Python that checks if the first number in an array occurs more than once:
def check_duplicate(arr):
if len(arr) == 0:
return False
first_num = arr[0]
count = 0
for num in arr:
if num == first_num:
count += 1
if count > 1:
return True
else:
return False
# Example usage
array1 = [1, 2, 3, 4, 5]
print(check_duplicate(array1)) # False
array2 = [1, 2, 3, 1, 5]
print(check_duplicate(array2)) # True
array3 = []
print(check_duplicate(array3)) # False
In this program, the check_duplicate function takes an array as input. It first checks if the array is empty and returns False in that case. If the array is not empty, it stores the first number in a variable called first_num. Then, it iterates over the array and counts the occurrences of first_num. If the count is greater than 1, indicating that first_num occurs more than once, the function returns True. Otherwise, it returns False. The program includes some example usage scenarios to demonstrate its functionality.
To learn more about array click on the link below:
brainly.com/question/16935847
#SPJ11
Related Questions
who is first prime ministers of nepal?
Answers
Answer:
Bhimsen Thapa
...............
Answer:
The first Prime Minister of Nepal was Bhimsen Thapa
but if it is asked first elected Prime Minister then
he is B. P Koirala.
Hope it will help :)❤
What is the Abacus?
full explanation please
Answers
Answer:
The abacus (plural abaci or abacuses), also called a counting frame, is a calculating tool which has been used since ancient times.
Explanation:
It was used in the ancient Near East, Europe, China, and Russia, centuries before the adoption of the Hindu-Arabic numeral system.[1] The exact origin of the abacus has not yet emerged. It consists of rows of movable beads, or similar objects, strung on a wire. They represent digits. One of the two numbers is set up, and the beads are manipulated to perform an operation such as addition, or even a square or cubic root.
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
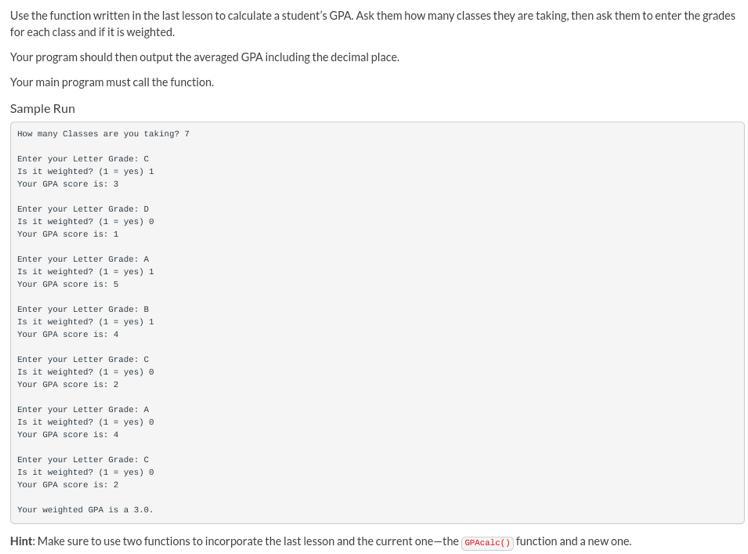
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
what type of network hardware should you implement to prevent this from happening again?
Answers
I need to implement network hardware called firewall. Firewall provide a barrier between your organization's network and public networks such as the Internet. It also prevent unauthorized access to an organization's private network.
What is network hardware and its types?Network hardware, also known as network equipment or computer network devices, is the electronic devices required for communication and interaction between devices on a computer network. Specifically, it mediates data transfers in computer networks.
What are basic network hardware devices?Routers, hubs, switches, and bridges are examples of network hardware devices. Basic device of a computer network is modem that allows your computer to connect to Internet through a telephone line.
Network hardware that amplifies network signals is called amplifier.
To learn more about Network hardware visit:
https://brainly.com/question/28040336
#SPJ4
You are the network administrator for a small organization. Recently, you contracted with an ISP to connect your organization's network to the Internet to provide users with Internet access. Since doing so, it has became to your attention an intruder has invaded your network from the Internet on three separate occasions. What type of network hardware should you implement to prevent this from happening again?
Which tab on the Ribbon contains the command to show the slide show from the current slide?
A.Home
B.Slide Show
C.File
D.View
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The correct answer to this question is B: Slide Show.
You can use the Slide Show tab on the ribbon that contains commands to show the slide show from the current slide. As you click on the Slide Show tab on the ribbon, you see a group of commands name "Start Slide Show", in these group of command, there is an option to start slide show From Current Slide. when you will click this option the slide show will start from your current slide.
Other options are not correct because:
The home tab on the ribbon contains commands related to slide, font, paragraph, editing, etc. File tab contains commands related to opening new or existing presentation documents and saving them, etc. While the View tab on the ribbon has a group of commands related to presentation view, master, zoom, etc. These tabs are used to show the slide show from the current slide.
Lab 18. 16 Java Script Password Strength zybooks
Answers
Here is an example of a JavaScript function that checks the strength of a password:
The Java Script Functionfunction checkPasswordStrength(password) {
var strength = 0;
// check the length of the password
if (password.length >= 8) {
strength += 1;
}
// check for lowercase letters
if (password.match(/[a-z]/)) {
strength += 1;
}
// check for uppercase letters
if (password.match(/[A-Z]/)) {
strength += 1;
}
// check for numbers
if (password.match(/\d/)) {
strength += 1;
}
// check for special characters
if (password.match(/[^\w\s]/)) {
strength += 1;
}
return strength;
}
This function takes a password as an argument and returns a strength score between 0 and 5, where 0 is the weakest and 5 is the strongest.
Read more about Javascript here:
https://brainly.com/question/28021308
#SPJ1
Question #6
ent
Fill in the Blank
You have defined your player data type.
class player:
life = 3
magic = False
name = "
You created an instance of your player data type and assigned values.
myPlayer = player()
myPlayer.life = myPlayer.life - 1
myPlayer.life = 4
myPlayer.magic = True
myPlayer.name = 'Kris'
What will be the value displayed after this line of code?
print(myPlayer.life)
You will see
Answers
Answer:
The answer is 4
Proof

6.18 lab: word frequencies write a program that reads a list of words. then, the program outputs those words and their frequencies. ex: if the input is: hey hi mark hi mark the output is: hey 1 hi 2 mark 1 hi 2 mark 1
Answers
A program that reads a list of words. then, the program outputs those words and their frequencies is given below:
The Programline = input ( )
norm = line . split ( )
low = line . lower ( ) . split ( )
for chr in low :
freq = low . count ( chr )
print ( freq )
for x in norm:
print ( x )
The Output1
2
2
2
2
hey
Hi
Mark
hi
mark
There are other ways to write a program that does this same function and they are given below:
1. for word, word_lower in zip ( norm, low ):
print ( word, low. count (word _ lower ) )
2. wordInput = input ( )
myList = wordInput . split ( " ")
for i in myList :
print ( i , myList . count ( i ) )
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Kyra is protesting corruption in the mayoral office. She is afraid that the mayor has access to her emails where she discusses his wrongdoings. Which of the following laws protects her electronic communication from being accessed by the government or law enforcement agencies?
A. Children's Online Privacy Protection Act
B. Electronic Communications Privacy Act
C. California Online Privacy Protection Act
D. Online Data Security Act
Answers
Answer: B. Electronic Communications Privacy Act
Explanation: If you look up what Electronic Communications Privacy Act it tells you the answer in the meaning or definition. Therefore Electronic Communications Privacy Act is the correct answer. Please rate me a 5/5. Your welcome.
Brian is a computer engineer who writes security software for a banking system. The
pathway in the Information Technology career cluster that Brian's job falls into is
Network Systems
Information Support and Services
Web and Digital Communications
Programming & Software Development
Answers
Answer:
Programming & Software Development
Explanation:
Software development life cycle (SDLC) can be defined as a strategic process or methodology that defines the key steps or stages for creating and implementing high quality software applications.
Some of the models used in the software development life cycle (SDLC) are;
I. A waterfall model.
II. An incremental model.
III. A spiral model.
Also, programming refers to a software development process which typically involves writing the sets of instructions (codes) that are responsible for the proper functioning of a software.
In this scenario, Brian is a computer engineer who writes security software for a banking system.
Thus, the pathway in the Information Technology career cluster that Brian's job falls into is Programming & Software Development.
Answer: D) Programming and Software Development.
Explanation:
Hope this helps, please mark me brainliest!
1. Read the following scenario. What type of business letter do you think is required in this situation? (1 point)
Melissa and Melrose are both first-year students at a local community college. They both have interest in volunteering with a nonprofit organization. They decided to reach out to nonprofit organizations to ask about the steps they need to take in order to volunteer.
Answers
Answer:
It requires a formal letter.
Answer:
This would require a formal business letter, the type being a cover letter or inquiry.
Explanation: yes
This week's discussion is on loops. With a code snippet, explain either while loop, for loop, or do-while loop. When is it advantageous to use a do-while loop rather than other kinds of loops? Come up with examples that are not explained in the textbook. Provide a meaningful reply to at least one post..something new that you learned, commenting on the syntax of the code, clarifying a concept, relating to the example provided, etc.
Answers
A for loop is a control flow statement for iterating a specific number of times. It consists of an initialization expression, a condition, and an increment expression. This code will print "hello", "world", "foo", and "bar" to the console. For example:
for (int i = 0; i < 10; i++) {
System.out.println("i is " + i);
}
This code will print "i is 0" through "i is 9" to the console. It is advantageous to use a for loop when the number of iterations is known beforehand.
An example not explained in the textbook could be to iterate through a list of strings and print each one to the console:
arduino
Copy code
String[] words = {"hello", "world", "foo", "bar"};
for (int i = 0; i < words.length; i++) {
System.out.println(words[i]);
}
This code will print "hello", "world", "foo", and "bar" to the console.
Note: It's essential to note that the initialization expression initializes the loop; the condition expression decides when the loop should stop and the increment expression increases or decreases the variable value on each iteration.
learn more about code here:
https://brainly.com/question/17204194
#SPJ11
You have 3 work orders in your queue, in what order would you prioritize them. WO#1 - Owner/Pres of company is unable to open a word document and needs assistance. WO#2 - User/employee monitors are not working or pc is dead they are unsure. WO#3 - User/employee is unable to print a document *
Answers
Here is the order in which I would prioritize the work orders, incorporating the safety guidelines:
WO#1 - Owner/Pres of company is unable to open a word document and needs assistance.
WO#2 - User/employee monitors are not working or pc is dead they are unsure.
WO#3 - User/employee is unable to print a document
I would prioritize WO#1 first because the owner/president of the company is unable to work without access to their computer. This could have a significant impact on the company's operations, so it is important to resolve this issue as quickly as possible.
I would prioritize WO#2 second because it is possible that the user's computer is completely dead, in which case they would not be able to do any work at all. However, it is also possible that the user's monitors are simply not working properly, in which case they could still access their computer by connecting it to a different monitor. I would need to investigate the issue further to determine the exact cause of the problem.
I would prioritize WO#3 third because it is the least urgent of the three issues. The user is still able to do their work, even if they are unable to print a document. I would still try to resolve this issue as quickly as possible, but it would not be as high of a priority as the other two work orders.
Learn more about Management here:
https://brainly.com/question/30415374
#SPJ11
the aca directed cms to create a standardized format for which of the following mtm-related documents? beneficiary cover letter, medication action plan, and personal medication list.
Answers
The ACA directed the (CMS) to create a standardized format for Medication Therapy Management (MTM)-related documents, specifically the beneficiary cover letter, medication action plan, and personal medication list.
MTM is a service provided to eligible Medicare beneficiaries to optimize medication use and improve health outcomes. It involves comprehensive medication reviews, targeted interventions, and ongoing monitoring to ensure the safe and effective use of medications. Standardizing the format of MTM-related documents is essential for consistency, clarity, and improved communication between healthcare providers, pharmacists, and Medicare beneficiaries.
The ACA (Affordable Care Act) recognized the need to streamline the MTM process and promote better coordination of care. The beneficiary cover letter is an important component of the MTM program as it introduces the beneficiary to the service and explains its purpose. By creating a standardized format for the cover letter, CMS(Centers for Medicare and Medicaid Services) ensures that beneficiaries receive consistent and accurate information about the MTM services available to them.
The medication action plan is a document that outlines the specific actions to be taken by the beneficiary regarding their medications. It includes instructions for medication use, dosage, timing, and any other relevant information. Standardizing the format of the action plan enhances clarity and reduces confusion, ensuring that beneficiaries have a clear understanding of their medication regimens.
The personal medication list is a comprehensive record of all the medications a beneficiary is taking, including prescription drugs, over-the-counter medications, and supplements. Standardizing the format of the medication list allows for easy identification of medications, accurate documentation, and better sharing of information among healthcare providers.
know more about Medication Therapy Management here:
https://brainly.com/question/31946655
#SPJ11
1 point
4. Part of a computer that allows
a user to put information into the
computer ?
O Output Device
O Operating System
O Input Device
O Software
Answers
Answer:
adwawdasdw
Explanation:
Answer:
I'm so sorry about the comment of that person down there
anyways I think its Number 2.
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
Description:
Create an object-oriented program that performs calculations on a rectangle in PYTHON
Console:
Rectangle Calculator
Height: 10
Width: 20
Perimeter: 60
Area: 200
Continue? (y/n): y
Height: 5
Width: 10
Perimeter: 30
Area: 50
Continue? (y/n): n
Bye!
Specifications:
Use a Rectangle class that provides attributes to store the height and width of a rectangle. This class should also provide methods that calculate the perimeter and area of the rectangle.
When the program starts, it should prompt the user for height and width. Then, it should create a Rectangle object from the height and width and use the methods of that object to get the perimeter, area, and string representation of the object.
Answers
In the main function, we can prompt the user for the height and width of the rectangle, create a new Rectangle object with those values, and then call the get_perimeter() and get_area() methods of the Rectangle object to print the results. We can also ask the user if they want to continue and calculate the perimeter and area of another rectangle.
To create an object-oriented program that performs calculations on a rectangle in Python, we can define a Rectangle class with attributes for height and width, as well as methods to calculate the perimeter and area of the rectangle.
When the program starts, it can prompt the user for the height and width of the rectangle, create a Rectangle object from those values, and then use the methods of that object to calculate the perimeter and area of the rectangle.
To implement this program, we can define a Rectangle class with the following methods:
1) init(self, height, width): Initializes a new Rectangle object with the given height and width.
2) get_perimeter(self): Calculates and returns the perimeter of the rectangle.
3) get_area(self): Calculates and returns the area of the rectangle.
4) str(self): Returns a string representation of the Rectangle object.
For such more questions on Main function:
https://brainly.com/question/29418573
#SPJ11
Here's a possible implementation of the Rectangle class and the main program in Python:
python
Copy code
class Rectangle:
def __init__(self, height, width):
self.height = height
self.width = width
def perimeter(self):
return 2 * (self.height + self.width)
def area(self):
return self.height * self.width
def __str__(self):
return f"Rectangle(height={self.height}, width={self.width})"
def main():
print("Rectangle Calculator")
while True:
height = float(input("Height: "))
width = float(input("Width: "))
rectangle = Rectangle(height, width)
print("Perimeter:", rectangle.perimeter())
print("Area:", rectangle.area())
cont = input("Continue? (y/n): ")
if cont.lower() != "y":
print("Bye!")
break
if __name__ == "__main__":
main()
When you run the program, it will prompt the user for the height and width of a rectangle, create a Rectangle object with those values, and then print the perimeter and area of the rectangle. It will then ask if the user wants to continue or exit. If the user chooses to continue, it will prompt for another rectangle; otherwise, it will exit the program. The output should look like the sample console session provided in the specifications.
Learn more about program here:
https://brainly.com/question/14368396
#SPJ11
What type of character can also be referred to as an avatar, main, or alt
Answers
Answer:
The main character or antagonist.
to use geolocation in a javascript program, you must call the getcurrentposition() method on the _____. object and pass in a callback function to run when the device's coordinates are successfully retrieved.
Answers
To use geolocation in a JavaScript program, you need to call the `getCurrentPosition()` method on the `navigator` object.
How can geolocation be implemented in JavaScript programs?To use geolocation in a JavaScript program, you need to call the `getCurrentPosition()` method on the `navigator` object.
This method is used to retrieve the device's current coordinates, such as latitude and longitude.
When calling `getCurrentPosition()`, you need to pass in a callback function as a parameter. This callback function will be executed when the device's coordinates are successfully obtained.
Within the callback function, you can access and utilize the retrieved location information for various purposes, such as displaying the user's position on a map or providing location-based services.
Learn more about JavaScript program
brainly.com/question/13266367
#SPJ11
A critical aspect of a good internal control system is:_____.
a. adequate compensation.
b. camera security.
c. separation of duties.
Answers
The correct option is (C).A critical aspect of a good internal control system is the separation of duties.
1. Separation of duties means that different individuals should be responsible for different aspects of a process or task. This helps to prevent fraud, errors, and conflicts of interest.
2. For example, if one person is responsible for handling cash transactions from start to finish, there is a higher risk of misappropriation or manipulation. However, if the duties of handling cash, record-keeping, and reconciliation are divided among different individuals, it creates a system of checks and balances.
3. By separating duties, companies can reduce the risk of errors or intentional wrongdoing and increase the reliability of their financial reporting. This is an essential element of a good internal control system, as it ensures accountability and transparency.
Overall, separation of duties is crucial for maintaining effective internal controls and safeguarding a company's assets.
To learn more about control system
https://brainly.com/question/31452507
#SPJ11
Define a function that generates a random vector field on the grid. This function may take as input, for instance, the size of the grid or where it is located in space. How you generate random vectors will be left up to you, but you are encouraged to make use of numpy.random functions to generate your random vectors. This function should return the vector field (as an nd.array, for instance). This function does not perform any graphing.
Answers
Here's an example of a function that generates a random vector field using numpy.random functions:
```python
import numpy as np
def generate_random_vector_field(size):
vector_field = np.random.rand(size, size, 2) # Generate random vectors for each point in the grid
return vector_field
```
The function `generate_random_vector_field` takes the size of the grid as input and generates a random vector field using numpy's `random. rand` function. The size parameter determines the dimensions of the grid, assuming it is a square grid. The function creates a numpy array of shapes `(size, size, 2)` to represent the vector field. Each point in the grid is assigned a random 2D vector using the `random.rand` function, representing the x and y components of the vector. The resulting vector field is then returned as an nd.array. This function does not perform any graphing or visualization; it solely focuses on generating the random vector field.
learn more about numpy here:
https://brainly.com/question/12907977
#SPJ11
why is it important to bring standalone systems into the domain?
Answers
Bringing standalone systems into the domain is important for several reasons. It enables centralized management, enhances security, improves collaboration and resource sharing, and simplifies system administration.
When standalone systems are brought into a domain, they become part of a centralized network infrastructure that allows for easier management and control. Domain controllers can enforce security policies, manage user accounts and permissions, and provide centralized authentication and access control, which enhances the overall security of the network.
Additionally, being part of a domain enables better collaboration and resource sharing among users. Files, printers, and other resources can be easily shared and accessed across the network, improving productivity and efficiency.
Lastly, system administration becomes more streamlined as domain administrators can manage and update software, deploy updates and patches, and perform other administrative tasks centrally, reducing the effort and complexity of managing individual standalone systems.
Learn more about the standalone system here: brainly.com/question/32364660
#SPJ11
assume you have fully replicated data store implemented on n servers, with each server replicating the entire dataset. it is sufficient for clients to be access any single server (ie., eventual consistency). if the mttf of each server is m, what is the overall mttf of the entire system?
Answers
The overall Mean Time To Failure (MTTF) of the entire system can be calculated using the formula:
Overall MTTF = 1 / (1/MTTF1 + 1/MTTF2 + ... + 1/MTTFn)
where MTTF1, MTTF2, ..., MTTFn are the MTTFs of each server in the system.
In this case, since all servers are replicating the entire dataset and clients can access any single server, the system is fully replicated. This means that if one server fails, the others can still handle client requests. Therefore, the overall MTTF of the system is simply the MTTF of a single server, which is m. Thus, the overall MTTF of the system is also m.
To learn more about Mean Time To Failure
https://brainly.com/question/30054062
#SPJ11
using force feedback is an example of how virtual reality systems incorporate what human sense into their virtual environments?
Answers
Through the sense of touch we can feel the real sensation in the driving of a virtual car through its steering wheel, since we can feel the tremors, the falls, and transmit force or impulse to the steering wheel to direct it correctly.
In conclusion we can say that force feedback transmits to the player through the steering wheel more real and stronger emotions than other types of systems for PC and consoles.
You can find more information in the following link: https://brainly.com/question/1758453
what report can help show the duration between a user's first exposure and their subsequent conversion?
Answers
The Time Lag report can help show the duration between a user's first exposure and their subsequent conversion in online advertising or marketing campaigns.
The Time Lag report provides insights into the time duration or lag between a user's initial interaction or exposure to a marketing touchpoint (such as an ad, email, or website visit) and their subsequent conversion, which could be a purchase, sign-up, or any desired action.
By analyzing the Time Lag report, marketers can understand how long it takes for users to convert after their initial engagement. This information is valuable for optimizing marketing strategies, understanding the customer journey, and determining the effectiveness of different touchpoints and channels.
The Time Lag report typically presents data in a distribution or histogram format, showing the number or percentage of conversions occurring within specific time ranges or intervals. This allows marketers to identify patterns and trends in user behavior, such as whether conversions tend to occur quickly or if there is a longer decision-making process involved.
Overall, the Time Lag report provides valuable insights into the duration between a user's first exposure to a marketing touchpoint and their subsequent conversion, helping marketers make informed decisions and optimize their campaigns accordingly.
Learn more about marketing campaigns here :
https://brainly.com/question/30237897
#SPJ11
A Time Lag Report can show the duration between a user's first exposure and their subsequent conversion. It's useful in observing the customer journey and improving marketing strategies by revealing behavior patterns.
Explanation:The report that can help show the duration between a user's first exposure and their subsequent conversion is called a Time Lag Report. The Time Lag Report is an aspect of digital marketing analytics, particularly useful in observing the customer journey. It measures the time taken between a user's initial interaction with an online ad or website and the point when the user makes a 'conversion' or desired action, such as making a purchase, signing up for a newsletter, or filling out a form.
This report can be beneficial to businesses as it provides insights into consumer behavior patterns and the effectiveness of their marketing strategies. By analyzing this data, a business may adjust its strategies to shorten this duration and increase conversion rates.
Learn more about Time Lag Report here:https://brainly.com/question/33709594
Do a quick search for “The Sun”. What types of results do you see?
Answers
Answer:
What happens when you look at the Sun?
When you stare directly at the sun—or other types of bright light such as a welding torch—ultraviolet light floods your retina, literally burning the exposed tissue. Short-term damage can include sunburn of the cornea—known as solar keratitis. ... This occurs when UV light literally burns a hole in the retinal tissues.Oct
Using induction on i, prove that (wR)} = (wi)R for any string w and all i 2 0. Hints: feel free to use the following Theorem in your proof Let u, v e 2*, then (uv)R = vrur.
Answers
Base case shows equality for i = 0. Inductive step assumes validity for i and proves it for i + 1. Therefore, the equation holds for all i ≥ 0.
Using induction on i, prove that (wR)} = (wi). R for any string w and all i 2 0. We are also given a hint:
feel free to use the following Theorem in your proof Let u, v e 2*, then (uv)R = vrur.
When i = 0, the left side of the equation becomes {(wR)} = {w} since a string reversed twice is equivalent to the original string. On the right side, (wi)R becomes (w0)R = wR = {w}. Thus, both sides are equal.
Inductive : We assume that the equation holds for some i > 0. That is, (wR)} = (wi)R is true. Now, we want to show that the equation also holds for i + 1. For simplicity, let's denote w' = wi. Then, we have:(w'R)} = ((wi)R)R (by definition of w')= (wi)(RR)R (by Theorem)= (wi)R (since RR = ε, the empty string).
Thus, by the principle of mathematical induction, the equation holds for all i ≥ 0.
Learn more about validity: brainly.com/question/26251731
#SPJ11
people who use a/an ________________ design logic believe that the given context determines what type of communication is appropriate.
Answers
People who use a/an contextual design logic believe that the given context determines what type of communication is appropriate.
Contextual design logic emphasizes the importance of considering the specific situation, environment, and audience when determining the most effective and appropriate means of communication. It recognizes that different contexts require different communication strategies and channels to convey information effectively.
By adopting a contextual design logic, individuals or organizations take into account factors such as cultural norms, social dynamics, communication goals, and the characteristics of the intended recipients. This approach helps ensure that the communication is tailored to the specific context, taking into consideration factors such as language, tone, medium, and level of formality.
Contextual design logic encourages a more nuanced and adaptable approach to communication, recognizing that what may be suitable in one context may not be effective or appropriate in another. It promotes sensitivity and responsiveness to the context in order to achieve clear, meaningful, and impactful communication.
learn more about "communication ":- https://brainly.com/question/28153246
#SPJ11
Write Syntax and function of :A)Rem B)Input
Answers
FUNCTION OF INPUT
The function of an input to communicate information to a computer or other sort of information processing equipment.
Security is essential to keep in mind when doing business online. Select three tips for keeping customers' private
information secure.
R
0 Always use a reputable web server and ask about their security.
C Store customer information In the same place as other business information.
0 Make sure credit card processing uses a digital certificate to verify the processing site.
O Always run virus protection and use firewalls.
Trust your merchant accounts and companies that process payment
Answers
Security is essential to keep in mind when doing business online. Three tips for keeping customers' private information secure is
Always use a reputable web server and ask about their security.
Make sure credit card processing uses a digital certificate to verify the processing site.
Always run virus protection and use firewalls.
What is an online business?Online business is a platform where business takes place over the internet.It includes the activity of buying and selling products on an online service. An online business can increase brand awareness and customer engagement. The main advantage of using online businesses is less expensive operating costs than traditional businesses. the main types are e-commerce, digital marketing, etc.To learn more about online business refer to:
https://brainly.com/question/27602536
#SPJ2