Write a function named vowel_tracker that computes and returns how many strings in a list of strings begin and/or end with a vowel. (The letters a, e, i, o and u are vowels. Both upper and lower case vowels should be tracked.)
Answers
Vowel sounds and the written symbols used to represent them are frequently referred to as the same thing under the word "vowel."
In phonetics, a vowel is a sound in spoken language that is characterized by an open configuration of the vocal tract, as opposed to consonants, which are characterized by a constriction or closure at one or more points along the vocal tract.
Vowels are derived from the Latin word "vocalis," which means "uttering voice" or "speaking."
Vowels are considered to be syllabic, which means that they typically make up the peak or nucleus (the middle portion) of a syllable, whereas consonants make up the onset and coda and vowels.
Thus, Vowel sounds and the written symbols used to represent them are frequently referred to as the same thing under the word "vowel."
Learn more about Vowels, refer to the link:
https://brainly.com/question/31086422
#SPJ4
Related Questions
3 things in terms of photography to learn about.
Answers
The three important principle in photography are;
Photography is about light. Without it, you couldn't even take images, let alone excellent ones.
The quality of light varies from one to photograph, yet it is always what gives your photographs their underlying structure. It doesn't get any more basic than that.
Most of us snap photos because something catches our attention.
Unsurprisingly, that "something" is your subject.
If you're explaining a photograph to someone else, the topic is most likely the first thing you'll mention.
Finally, the composition is the third and most important aspect of every shot.
Simply said, composition is the arrangement of the things in your shot. It includes your camera position, the connections between photo elements, and the things you accentuate, deemphasize, or altogether eliminate. Composition is the method through which you communicate your tale.
Learn more about photography:
https://brainly.com/question/30685203
#SPJ1
Hello Brainly Students!
Have any suggestions to make Brainly better?!
Write them down below!
Thank you,
BrainlyUpdates
Answers
Answer:
i need help on my wuestion and nobody responds
Explanation:
Answer:
?
Explanation:
Write a VBA Function subroutine called Tax that takes a single argument gross Income of type Currency. It should calculate the tax on any income using the following tax schedule: (1) if income is less than or equal to $15,000, there is no tax (2) if income is greater than $15,000 and less than or equal to $75,000, the tax is 15% of all income greater than $15,000 (3) if income is greater than $75,000, the tax is 15% of all income between $15,000 and $75,000 plus 20% of all income greater than $75,000 Then write a Calc Tax subroutine that asks the user for his income, gets the function subroutine to calculate the tax on this income, and reports the tax in a message box
Answers
An example of formulated VBA code comprises a function called "Tax" that takes the gross income as an input and employs the given tax schedule to know the tax amount is given below.
What is the VBA Function?A function in VBA is one that is like that of a sub procedure, except that the former has the ability to provide an output value while the latter does not have this capability. A code fragment that can be invoked within the VBA Editor, saving one from having to repeat the same lines of code.
In order to make use of the code given, access the VBA editor within Microsoft Excel or other Office programs, generate a fresh module, and insert the code. Next, execute the "CalcTax" subroutine either by pressing F5 or by choosing Run from the menu bar.
Learn more about VBA Function from
https://brainly.com/question/29442609
#SPJ4

What are the steps to complete an internet search?
Answers
Answer:
step one: open your search engine
step two: type what you wanna search for in the text box
step three: press enter
and that's it
Which camera does Angelina use?
Angelina uses a
and is a lot smaller than DSLRs.
camera, which is quite popular among photographers since it offers the same photo quality as a DSLR camera
Answers
Answer:
mirrorless cameras have lot more space due to not having mirrors. and they have the same or better quality than DSLR's.
how do i change the security settings on my computer
Answers
To change security settings on your computer, access the Control Panel, navigate to the desired security section, and customize the settings as needed.
To change the security settings on your computer, you can follow these general steps:
1. Open the Control Panel: Click on the "Start" menu, search for "Control Panel," and click on the corresponding result to open the Control Panel.
2. Navigate to the Security Settings: In the Control Panel, find and click on the "Security and Maintenance" or "System and Security" option. This will provide access to various security settings on your computer.
3. Customize Security Settings: Within the Security and Maintenance or System and Security section, you will find options such as "Windows Defender Firewall," "Windows Update," "User Account Control," and others. Click on the relevant option based on the security setting you want to change.
4. Adjust Security Settings: Depending on the specific security setting you selected, you will have various options to customize. For example, in Windows Defender Firewall, you can enable or disable the firewall, configure inbound and outbound rules, and manage program permissions. In User Account Control, you can adjust the level of notifications and permissions required for certain actions.
5. Save Changes: After customizing the security settings to your preference, make sure to save the changes by clicking on the appropriate button, such as "Apply" or "OK."
It's important to note that the steps may vary slightly depending on your specific version of Windows or operating system. Additionally, certain security settings may require administrative privileges, so ensure that you have the necessary permissions to make changes. Always exercise caution when modifying security settings and consult official documentation or reputable sources for guidance if you are unsure about specific settings.
Learn more about security settings: https://brainly.com/question/29431325
#SPJ11
What is the difference between concrete language and abstract language? give an example of each.
Answers
The difference between abstract language and abstract language is that abstract language is known through the intellect and concrete language is known through the senses.
What are abstract and concrete languages?The abstract language uses the words like kind, truth, grace, etc. It is a form of language that indicates the intellectual, but concrete language can be known by the senses.
Thus, the distinction between concrete and abstract language is that concrete language is understood via the senses, whereas abstract language is understood through the mind.
To learn more about abstract and concrete languages, refer to the link:
https://brainly.com/question/16550006
#SPJ4
Write a Python function named Random-studentID() that randomly generate any 100 possible student IDs which have 9 digits and start with 900 number, and output these student ID into a text file named randomID.txt.
Answers
Here is an implementation of the Python function random_studentID() that generates 100 random student IDs with 9 digits starting with 900 and writes them to a text file named "randomID.txt":
import random
def random_studentID():
student_ids = []
for i in range(100):
# Generate a random 9-digit student ID starting with 900
student_id = str(900000000 + random.randint(0, 9999999))
student_ids.append(student_id)
# Write the student IDs to a text file
with open("randomID.txt", "w") as file:
file.write("\n".join(student_ids))
random_studentID()
What is the explanation of the above program?This function first creates an empty list called student_ids. It then uses a loop to generate 100 random student IDs. Each student ID is a string representation of a 9-digit integer, obtained by adding a random integer between 0 and 9999999 to the fixed integer 900000000. The generated student ID is added to the student_ids list.
Once all the student IDs have been generated, the function opens a text file named "randomID.txt" in write mode using a with statement. It then writes the contents of the student_ids list to the file, with each student ID on a separate line, using the join() method to convert the list to a single string with newline characters between each element.
Finally, the function exits and the "randomID.txt" file should contain 100 randomly generated student IDs, each on a separate line.
Learn more about Phyton function on:
https://brainly.com/question/18521637
#SPJ1
For this assignment, you will select a digital media career that you would be interested in pursuing. You will need to do some research to identify the right career for you. Next, you will research and discover what kind of training you will need to land your dream job. Finally, you will find available jobs in your career and select a job that you would want. After doing some research and some thinking, you will:
Select a career that is right for you. Write at least 150 words describing the career and why you believe it would be a good fit for you. Keep in mind your interests and talents.
Research and learn about what training the career requires. After you research, write at least 150 words describing the training. You can include what types of course you would take. How long the training program is, and how much it might cost you.
Finally, you will find a job! Research available jobs in your career and select a job you would want. Provide a copy of the job posting. You can snapshot this, copy and paste it, or copy it word for word. Make sure you include where you found the job posted. You will include at least 75 words on why you selected this particular position. Some helpful sites for job hunting are Indeed, Dice, Career Builder, and Monster.
Answers
A digital media career involves using technology to create and distribute various forms of digital content, such as video, audio, graphics, and multimedia. This can include roles such as graphic designers, web developers, social media specialists, digital marketers, and video producers.
How long the training program is, and how much it might cost you.To land a career in digital media, you will typically need a combination of technical skills and creativity, as well as a strong understanding of digital media platforms and technologies. Depending on the specific career path you choose, you may need to have skills in areas such as graphic design, web development, video editing, or social media management.
Training for a digital media career can vary depending on the specific path you choose, but often involves completing a degree or certificate program in a related field such as digital media, graphic design, or marketing. These programs can range in length from a few months to several years, and can cost anywhere from a few thousand dollars to tens of thousands of dollars.
Job opportunities in digital media can be found on job search sites such as Indeed, Dice, Career Builder, and Monster. One example of a job posting for a digital media position is:
Position: Social Media Specialist
Company: XYZ Digital Agency
Location: New York, NY
Job Type: Full-time
Responsibilities:Develop and execute social media strategies for client accounts
Create engaging social media content, including graphics and video
Monitor social media channels for trends and insights
Analyze social media metrics and adjust strategies as needed
Why I selected this particular position:
I am interested in pursuing a career in social media management, and this position seems like a good fit for my skills and interests. I am drawn to the opportunity to create engaging content and develop strategies to help clients achieve their social media goals. Additionally, the location and job type align with my preferences.
Read more on digital media career here https://brainly.com/question/29363025
#SPJ1
what are the software is there ? their uses
Answers
Answer:
Computer software is programming code executed on a computer processor. The code can be machine-level code, or code written for an operating system. An operating system is software intended to provide a predictable and dependable layer for other programmers to build other software on, which are known as applications.
What are binary and denary?
Answers
Answer:
The binary system on computers uses combinations of 0s and 1s. In everyday life, we use numbers based on combinations of the digits between 0 and 9. This counting system is known as decimal, denary or base 10. ... Denary is known as base 10 because there are ten choices of digits between 0 and 9.
Explanation:
Answer:
A denary number is a number in the base 10, or decimal, system.
A number system where a number is represented by using only two digits (0 and 1) with a base 2 is called a binary number system.
Explanation:
please make me Brainlist
3.19.6 checkerboard answers for codehs
Answers
Teachers can forbid their students from copying and pasting text into the Code Editor using CodeHS Pro. Students registered in that area cannot copy, paste, or cut to or from the Editor once Copy/Paste Prevention is enabled.
What role of checkerboard answers for codehs?CodeHS is a short web-based curriculum for computer teachers. For younger students, I advise using offline activities to enhance the teachings. The AP Computer Science curriculum from CodeHS has been quite helpful to us.
Therefore, CodeHS Certifications provide as proof that students have acquired knowledge and abilities via our thorough, secure exam. Through increasing students' and potential employers' confidence in their skill set.
Learn more about codehs here:
https://brainly.com/question/29227777
#SPJ1
A business can use a wiki in the following ways EXCEPT _____.
A. accessing schedules and procedures
B. exchanging ideas
C. sharing policies
D. aggregating content
Answers
A business can use a wiki in the following ways except aggregating content. Hence, option D is correct.
What is aggregating content?A business known as a content aggregator gathers media content, apps, or both from online sources for use or sale later on. It is a technique for curating content. The two types of content aggregators are those who gather news and other content from various sources for putting on their own websites.
Content aggregation is the process of gathering information on any topic in order to publish it on a single platform, website, or blog. It collects data solely based on keywords and is automated.
Thus, option D is correct.
For more information about aggregating content, click here:
https://brainly.com/question/7692248
#SPJ1
What are at least three common technologies used within this pathway?.
Answers
Multitasking , in a variety of environments, long distance communications
how can you identify if a grammatical error has been detected in the document?
Answers
A blue double-underline appears beneath the text in the document to indicate the error.
What is grammatical error?The word was first employed by the Greeks to describe what they considered to be grammatical errors in their language. The phrase was used to denote making something ludicrous. The dialect of the people of Soli, Cilicia, was seen by ancient Athenians as a distorted version of their original Attic dialect, and the mistakes in the form were known as "solecisms." Therefore, when referring to similar grammatical errors in Athenians' speech, they called them "solecisms," and that term has since been adopted as a label for grammatical errors in all languages. In Greek, the relevant terms frequently differ in that a barbarism refers to an error in semantics, whereas solecism refers to errors in syntax, or in the construction of sentences.
To know more about grammatical error visit:
https://brainly.com/question/10466654
#SPJ4
which data structure is preferable when storing large data types that often need to be inserted at random positions? for the linked list option, assume you have a pointer to the element where you want to insert.
Answers
When storing large data types that often need to be inserted at random positions, a linked list is preferable.
The complexity of inserting an element is O(1), since you have a pointer to the element you want to insert, and no reindexing is required. This makes linked lists an efficient and fast data structure for inserting elements.
They are dynamic and allow for insertion and deletion of elements without the need to reallocate memory. This makes them ideal for applications where data is constantly changing and needs to be quickly and easily updated. Additionally, linked lists can be used to implement various data structures such as stacks, queues, and graphs. Also, linked lists can be used to implement more efficient algorithms for sorting and searching, as well as for more complex operations such as selection, union, intersection, and difference.
Learn more about algorithms
https://brainly.com/question/13800096
#SPJ4
(a) generate a simulated data set with 20 observations in each of three classes (i.e. 60 observations total), and 50 variables. use uniform or normal distributed samples. (b) perform pca on the 60 observations and plot the first two principal component score vectors. use a different color to indicate the observations in each of the three classes. if the three classes appear separated in this plot, then continue on to part (c). if not, then return to part (a) and modify the simulation so that there is greater separation between the three classes. do not continue to part (c) until the three classes show at least some separation in the first two principal component score vectors. hint: you can assign different means to different classes to create separate clusters
Answers
A: Part (a): We can generate a simulated data set with 20 observations in each of the three classes, and 50 variables using uniform or normal distributed samples.
For example, we can generate random numbers between 0 and 1 for each of the 50 variables, and assign a class label to each of the observations. For example, if the value of the first variable is less than 0.34, we can assign it to class A, if it is between 0.34 and 0.67, we can assign it to class B, and if it is greater than 0.67, we can assign it to class C. We can then repeat this process for the other 49 variables.
Part (b): We can then perform PCA on the 60 observations and plot the first two principal component score vectors, using a different color to indicate the observations in each of the three classes.
To perform PCA on the 60 observations and plot the first two principal component score vectors, we can use a scatter plot. We can then assign a different color to each of the three classes, so we can visually see if there is any separation between the classes.
Part (c): If the three classes show at least some separation in the first two principal component score vectors, then we can continue to analyze the data by looking at the other principal component score vectors, and the correlations between the variables.
For more questions like Samples click the link below:
https://brainly.com/question/29561564
#SPJ4
An office building has two floors. A computer program is used to control an elevator that travels between the two floors. Physical sensors are used to set the following Boolean variables.
The elevator moves when the door is closed and the elevator is called to the floor that it is not currently on.
Which of the following Boolean expressions can be used in a selection statement to cause the elevator to move?
answer choices
(onFloor1 AND callTo2) AND (onFloor2 AND callTo1)
(onFloor1 AND callTo2) OR (onFloor2 AND callTo1)
(onFloor1 OR callTo2) AND (onFloor2 OR callTo1)
(onFloor1 OR callTo2) OR (onFloor2 OR callTo1)
Answers
The following Boolean expressions, "onFloor1 AND callTo2" or "onFloor2 AND callTo1," can be used in a selection statement to move the elevator.
The commands to move the lift may be simply determined based on the other commands designed to be provided and received by the lift, which indicate what operation it is engaged in.
When the elevator is on the first floor and has to be taken to the second floor, the order "onFloor1 AND callTo2" can be used. The order "onFloor2 AND callTo1" would serve as the reverse of the previously given instruction and cause the lift to operate in the exact opposite manner.
To know more about elevator visit:-
https://brainly.com/question/2168570
#SPJ4
which of the following is not accomplished using the query tools tab?
Answers
The query tools tab in most software programs is used to create and manipulate queries for databases. The following tasks are commonly accomplished using the query tools tab: creating, modifying, and running queries; filtering data; sorting data; joining tables; and summarizing data.
However, tasks such as designing forms, reports, and macros are not typically accomplished using the query tools tab. These tasks are usually completed using other tabs or menus within the software program.
The Query Tools tab typically provides a set of tools and options for working with queries in a database management system (DBMS). While the specific functionality may vary depending on the software or application being used, one common task that is generally not accomplished using the Query Tools tab is data manipulation or modification.
The Query Tools tab is primarily focused on assisting with query development, execution, and analysis. It may include features such as query builders, SQL editors, query execution options, query performance analysis, and result set manipulation.
On the other hand, tasks related to data manipulation, such as inserting, updating, or deleting records, are typically performed using different tools or interfaces within the DBMS. These tasks are often handled through dedicated forms, data entry screens, or specific data manipulation tools provided by the DBMS.
Learn more about DBMS here: https://brainly.com/question/14806077
#SPJ11
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
Montel needs to add a calculated field into a report that he has built that will show the total sale price of items sold in a given month. Which type of control should he add in Design view?
control box
text box
label
subreport
Answers
pls mark brainleist
Answer:
D. Subreport
Explanation:
A subreport is a report inserted into another report.
Let me know if this is correct.
Hope this helps!
Any Suggestions on what to do here? I already restarted my PC twice, cleared my browsing data, and rebooted the wifi network....

Answers
Answer:
if u r at school, then it might be blocked.
if not, get a vpn proxy.
Write the pseudocode that could be used for a program that will test if a
number is odd or even and print the result.
esult.
Answers
1. Ask the user for an integer input and store it in a variable called "number."
2. Check if the number is divisible by 2 using the modulo operator (%).
3. If the result of the modulo operator is 0, print "The number is even."
4. If the result of the modulo operator is 1, print "The number is odd."
Here's an implementation of the pseudocode using Python:
```
number = int(input("Enter an integer: "))
if number % 2 == 0:
print("The number is even.")
else:
print("The number is odd.")
```
This program will ask the user to enter an integer and then check if it is even or odd using the modulo operator. If the number is even, it will print "The number is even." If the number is odd, it will print "The number is odd."
Date Underline the correct answer from the options. 1. How many basic input devices does a desktop computer have? .. a)2 b)3 c) 1 d)4 2. The computer equipmentwhich feeds the computer with data is called. a) Storage device b) Processing device c) Diskette d) Input device 3.When an output is displayed in a printed form it is termed as a) Softcopy output b) File c) Document d) Hardcopy output
4. Which computer device will convert human voice into digital voice? a) Projector b) Loudspeaker c) Microphone d) Joy. 5) All the following are hardcopy output devices except a) Photocopier b) Printer c) Projector d) Plott
Answers
Answer:
1. 3
2. D (Input Device)
3. B (File)
4. C (Microphone
Gemima has converted her table to a clustered column
chart. She now wants to add a title.
What should Gemima do first?
Select the table.
What should Gemima do next?
What should Gemima do last?
Use Ctrl+A
Use Ctrl+C
Use Ctrl+V.
Answers
Answer:
1. Select the table
2. use Ctrl A
3. type the title
Answer: select the table,Crtl+a,Type the title
Explanation:

When you right-click a picture in a word processing program, which actions can you choose to perform on that image?
You can choose to
an image when you right-click the picture in the word processing program. You can also choose to
an image when you right-click the picture in the word processing program
Answers
Answer:
Lots to choose from such as "copy" or "crop"

which of the following statements about browser security settings are true

Answers
The options that are true regarding browser security settings are options:
A. You can choose which sites run pop-ups.
C. You can deny cookies and
D. Sites can be allowed or blocked from running scripts
How can you check browser security settings?To inspect your security settings, pull down the notification bar and press the gear symbol. Scroll down to the security and location section. The screen lock setting may be found under device security.
Option B is incorrect. Web history is not always saved indefinitely and can be erased manually or automatically depending on the browser settings.
Never submit your password or credit card information on sites that display this warning. If you must use the site, contact its owner or administrator and inform them that it is not secure.
Learn more about browser security settings at:
https://brainly.com/question/25014794
#SPJ1
Full Question:
Which of the following statements about browser security settings are true? Select all that apply. A. You can choose which sites run pop-ups. B. Your accumulated web history is stored forever. C. You can deny cookies. D. Sites can-- be allowed or blocked from running scripts
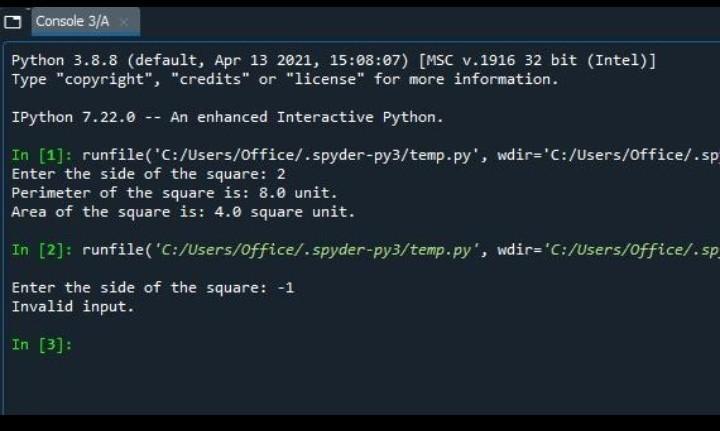
Problem: Write the Python code of a program called ComputeSquare that asks the user to enter the length of the side of the square and displays the area and perimeter of the square. Check that the side length is greater than zero, and if it is not, display an informative error message to the user.
Answers
The given problem is solved in Python.
def ComputeSquare():
side = float(input('Enter the side of the square: '))
if side > 0:
perimeter = 4 * side
area = side * side
print('Perimeter of the square is:',
perimeter, 'unit.')
print('Area of the square is:', area, 'square unit.')
else:print('Invalid input.')
ComputeSquare()
Explanation :-In this program, we create a function ComputeSquare() to calculate the perimeter and area of a square.The function asks the user to enter the side of the square. The side is then stored in a variable.Now, we check whether the side is greater than 0 or not using if-else statement.If the condition is true, the perimeter and area is calculated which is displayed using print() statement.If the condition is false, the else blocks executes printing the error message.Refer to the attachment for output.
3. Special keys labelled Fl to F12.
A. Function Keys
B. Special Keys
C. Modifier Keys
D. Alpha Numeric Keys
Answers
Answer:
The answers is Function Keys
What is the minimum number of connections that must be broken or removed in the network before computer E can no longer communicate with computer F
Answers
Answer:
To reach best results:
Break down all connections.