Which of the following activities does the USA Patriot Act define? Group of answer choices cyberterrorism identity theft transmitting virus programs credit card fraud
Answers
The USA Patriot Act defines the activities of cyberterrorism.
How does the USA Patriot Act define cyberterrorism?The USA Patriot Act, passed in response to the September 11, 2001 terrorist attacks, includes provisions that define and address various activities related to national security threats. One of the activities specifically defined by the act is cyberterrorism.
Cyberterrorism refers to the use of computer networks and technology to carry out acts of terrorism. It involves the intentional and unlawful use of digital tools to disrupt or damage critical infrastructure, compromise national security, or cause harm to individuals or society as a whole. Examples of cyberterrorism can include hacking into government systems, launching cyberattacks on critical sectors like energy or finance, or spreading malicious software to disrupt communication networks.
By defining cyberterrorism, the USA Patriot Act provides law enforcement agencies with legal authority to investigate, prevent, and prosecute individuals or groups engaged in such activities. It also enables the government to enhance cybersecurity measures, collaborate with private sector entities, and protect the nation's digital infrastructure from potential threats.
Learn more about cyberterrorism
brainly.com/question/32797171
#SPJ11
Related Questions
what is all about programming interactions in the real world.
Answers
Answer:
Programming is everywhere in the modern world and meets you in the street, your workplace, and the local grocery store. You interact with bar-code scanners regularly, and you almost certainly use lots of code while working, whether you're using a word processor to write a letter or an email platform to send messages. Programs used in real-world environments should also be programmed in the real world, so we have developed a new programming paradigm, “Real-World Programming (RWP),” which enables users to make programs for handling real-world environments as well as data in computers
so about computers can you tell me about bit coins and giga watts
Answers
Bitcoin is a decentralized digital money that may be purchased, sold, and exchanged whereas gigawatt hour is a measure of energy that equals one million kilowatt hours.
What is a Bitcoin?Bitcoin's creator, Satoshi Nakamoto, originally described the need for “an electronic payment system based on cryptographic proof instead of trust.” Digital currency known as Bitcoin is completely decentralized and not subject to bank or governmental regulation. Instead, cryptography and peer-to-peer software are employed. A public ledger, a copy of which is stored on servers throughout the world, records every bitcoin transaction.
What is a Giga Watts?1 Kilowatt hour [kWh] = 0.000 001 Gigawatt hour [GWh]
1,449 kilowatt hours (kWh) of energy to mine a single bitcoin.
0.001449 GWh
To know more about Cryptography visit:
https://brainly.com/question/88001
#SPJ1
A company has a central file server that is located 500 m away from the main office where employees work at their computers. Employees send and retrieve files to and from the file server on a daily basis, often at the same time. Identify the type of data transmission that would be most suitable for the given context. Explain why this would be the most suitable method of transmission.
Answers
For the given scenario, the most suitable type of data transmission would be fiber optic cabling.
What is the explanation for the above response?For the given scenario, the most suitable type of data transmission would be fiber optic cabling. This is because fiber optic cables have the ability to transmit large amounts of data over long distances without experiencing significant signal degradation or loss.
This makes it ideal for transmitting data between the main office and the file server which are 500 meters apart. Additionally, fiber optic cables are not susceptible to electromagnetic interference, making them more reliable compared to other types of cables such as copper cables.
The high bandwidth and reliability of fiber optic cables make them the best choice for transmitting large volumes of data at high speeds over long distances, which is exactly what is needed in this scenario.
Learn more about data transmission at:
https://brainly.com/question/14700082
#SPJ1
Which of the following reasons for writing a formal business document would
lead you to write a proposal?
OA. To tell your manager a project is on budget and on schedule
OB. To describe what tasks you completed during the week
OC. To summarize what happened during a meeting
OD. To convince your manager to use a new meeting organization tool
SUBMIT
Answers
Answer:
C. To summarize what happened during a meeting
Explanation:
because it would be a lot easier if u told him the truth...
the three-level memory hierarchy refers to? a. main memory, disk storage, and removable storage b. registers, cache memory, and main memory c. cache memory, main memory, and disk storage d. main memory, dvd, and usb sticks
Answers
The three-level memory hierarchy refers to cache memory, main memory, and disk storage.
Cache memory is the smallest, fastest, and most expensive memory and is used to store recently used information. Main memory is larger and slower than cache memory and is used to store information that is currently being used. Disk storage is the largest and slowest type of memory and is used to store information that is not frequently used.
The three-level memory hierarchy is the basic structure of computer memory and is composed of three levels of memory. Cache memory is the smallest, fastest, and most expensive type of memory, and is used to store recently used information.
Learn more about three-level memory hierarchy:
https://brainly.com/question/14207493
#SPJ4
6
Select the correct answer.
Jorge needs to print out an essay he wrote, but he does not have a printer. His neighbor has a printer, but her internet connection is flaky. Jorge is
getting late for school. What is the most reliable way for him to get the printing done?
O A. send the document to his neighbor as an email attachment
О в.
share the document with his neighbor using a file sharing service
OC.
physically remove his hard disk and take it over to his neighbor's
OD. copy the document onto a thumb drive and take it over to his neighbor's
Answers
Since Jorge needs to print out an essay, Jorge should D. Copy the document onto a thumb drive and take it over to his neighbor's
What is the printer about?In this scenario, the most reliable way for Jorge to get his essay printed would be to copy the document onto a thumb drive and take it over to his neighbor's.
Therefore, This method does not depend on the internet connection, which is flaky, and it also avoids any potential issues with email attachments or file sharing services. By physically taking the document over to his neighbor's, Jorge can ensure that the document will be printed on time.
Learn more about printer from
https://brainly.com/question/27962260
#SPJ1
if you had a chance to see what your life would be like in 20 years
Answers
But I mean if I was to be alive somehow, I would say, coronavirus is gone perhaps, but now there some bigger issue going on?
That’s my opinion ︎
What is a package containing one or more files that address a flaw in a platform? group of answer choices
Answers
do u see abs??????????

Answers
Answer
of course, y u askin tho, im pretty sure every person who doesnt have a sight disability can see her abs as well
Explanation:
which operational command is used to view status messages sent to a file named test as they are sent
Answers
Monitor start test is operational command that is used to view status messages sent to a file named test as they are sent. A command is an instruction or request to perform a specific action or task.
What is meant by command?
Command can be described as direct with special authority or prerogative; order. A command is a directive to a computer program to perform a specific task, in computing, a command is a directive to a computer program to perform a specific task. It may be issued via a command-line interface, such as a shell, or as input to a network service as part of a network protocol, or as an event in a graphical user interface triggered by the user selecting an option in a menu. In computing, a command is a directive given to a computer program or operating system to carry out a specific operation. This can be done through a command line interface (CLI), where the user types in commands, or through a graphical user interface (GUI), where the user interacts with the program using buttons, menus, and other graphical elements.
Learn more about command, in here brainly.com/question/30319932
#SPJ4
How do u create a game
Answers
suppose that two processes detect the demise of the coordinator simultaneously and both decide to hold an election using the bully algorithm. what happens?
Answers
When two processes detect the demise of the coordinator simultaneously and both decide to hold an election using the bully algorithm, they will both send election messages to all the processes with higher process IDs.
What happens when two processes detect the demise of the coordinator simultaneously and both decide to hold an election using the bully algorithm?If two processes detect the demise of the coordinator simultaneously and both decide to hold an election using the bully algorithm, then both processes will broadcast an election message to other processes with lower process IDs.
Other processes will respond to the message by sending an "OK" message back to the sender. Since both processes in this scenario have higher process IDs than any other processes, they will receive no "OK" messages and thus both assume the role of the new coordinator.
This leads to a split brain scenario where there are two coordinators running simultaneously, which can cause conflicts and inconsistencies in the system.
Learn more about bully algorithm
brainly.com/question/29491320
#SPJ11
what are tasks performed by pascaline?
Answers
Answer:
The Pascaline is a direct adding machine (it has no crank), so the value of a number is added to the accumulator as it is being dialed in. By moving a display bar, the operator can see either the number stored in the calculator or the complement of its value.
Explanation:
outline 4 IDE features that makes software development much faster and more convenient than other alternatives.
Answers
Answer:
IDEs can let you code without internet.
Explanation:
1. you can code without wifi.
2. it combines common developer tools into 1 GUI (grafic user interface).
3. it gives a warning about memory leaks.
4. it can correct synaxes.
Hope This Helps! :)
Multiple
Choice
What will be the output?
class num:
def __init__(self,a):
self. number = a
def_mul__(self, b)
return self.number + b.number
numA = num(5)
numB = num(10)
product = numA * numb
print(product)
50
O 5
an error statement
15

Answers
Answer:
15
Explanation:
Edge 2021

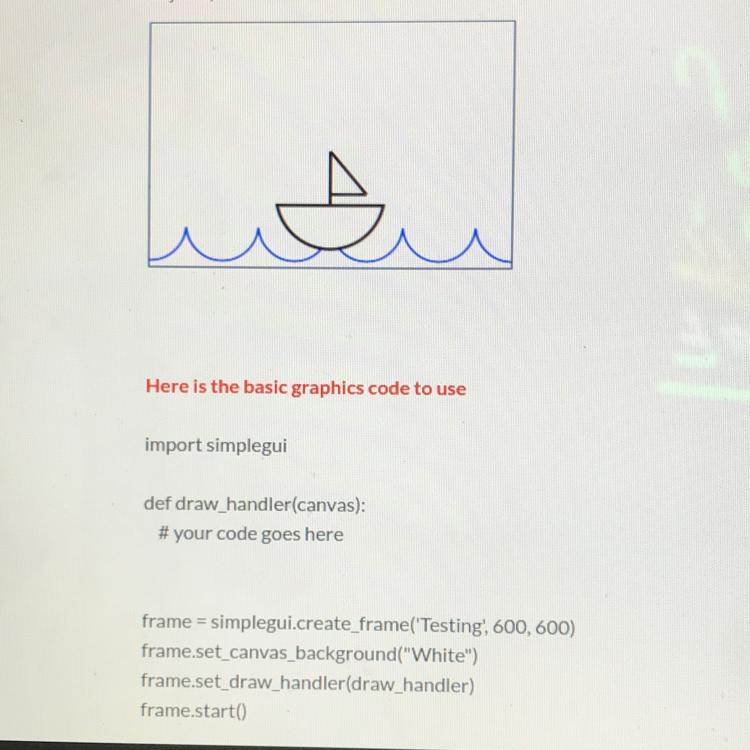
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
How do we calculate the BMI in python?
the formula is kg/m²
Answers
Answer:
height = float(input("Enter your height in m: "))
weight = float(input("Enter your weight in kg: "))
BMI = weight / (height/100)**2
print(f"You BMI is {BMI}")
Explanation:
The python code for calculating BMI is as follows -
height = float(input("Enter your height in m: "))
weight = float(input("Enter your weight in kg: "))
BMI = weight / (height/100)**2
print(f"You BMI is {BMI}")
Some conditions can also be added such as
if BMI <= 15:
print("You are underweight.")
elif BMI <= 30:
print("You are healthy.")
elif BMI <= 40:
print("You are over weight.")
Smiling and nodding are two ways to show a(n)
or situation.
OA. positive
B. frightened
OC. negative
OD. uninterested
о
attitude about a person
SUBMIT
Answers
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
in a factorial design with two independent variables, researchers would need to review one – and two – . if each independent variable has two levels, this design would also yield four – , which are the averages of each level of an independent variable across all levels of the other independent variable.
Answers
In a factorial design with two independent variables, researchers will need to review one interaction effect & two main effects. This design will also yield four marginal means, which are averages of each level of the independent variable collapsed across the levels of other independent variable.
What is an independent variables?In statistical modeling, experimental sciences, and mathematical modeling, independent variables are variables. Dependent variables are so-called because, during an experiment, their values are examined under the presumption or requirement that they do so in accordance with some law or rule (for example, a mathematical function) governing the values of other variables.
In turn, independent variables are not perceived in the context of the experiment in question as depending on any other variable. In this sense, common independent variables include time, space, density, mass, fluid flow rate, and previous values of some observed value of interest (such as the size of the human population) (the dependent variable).
Learn more about independent variables
https://brainly.com/question/25223322
#SPJ4
I need some questions and answers in spreadsheet
Answers
Answer:
you need to show what you need help with
Explanation:
Given that two int variables , total and amount, have been declared , write a loop that reads integers into amount and adds all the non-negative values into total. The loop terminates when a value less than 0 is read into amount. Don't forget to initialize total to 0.
total=0;
do{
cin >> amount;
if (amount>0)
total += amount;
}
while (amount >=0);
Answers
Given that two int variables, total and amount, have been declared, write a loop that reads integers into amount and adds all the non-negative values into total. The loop terminates when a value less than 0 is read into amount.
Don't forget to initialize total to 0.The code to perform the above-mentioned scenario is as follows:total = 0;do {cin >> amount;if (amount > 0)total += amount;}while (amount >= 0);The loop starts by setting the total to zero. Then, it continues to read the value of amount using cin. The value entered in the amount variable is tested to see whether it is positive or not.If the entered value is positive, the value is added to the total variable. If it is negative, the loop will end. The loop continues until the user enters a negative value.To write a loop that reads integers into the variable 'amount' and adds all non-negative values to the variable 'total', you can follow these steps:1. Initialize the 'total' variable to 0.
2. Create a do-while loop to continuously read values into 'amount'.
3. Within the loop, use an if statement to check if the value of 'amount' is greater than 0.
4. If the value is greater than 0, add it to 'total'.
5. The loop terminates when a value less than 0 is read into 'amount'.
Here's the code:
```
total = 0;
do {
cin >> amount;
if (amount > 0)
total += amount;
} while (amount >= 0);
```
Learn more about code: https://brainly.com/question/26568485
#SPJ11
Type the correct answer in the box. What is the output of the formula =NOT(12+12=24)? The output of the formula =NOT(12+12=24) is .
Answers
Answer:
In a programming language, the formula is that it is printing out whatever equation is NOT 12+12. This would mean it's printing out any other number than 24, or 12.
Explanation:
I hope this helps
imagine that you wanted to write a program that asks the user to enter in 5 grade values. the user may or may not enter valid grades, and you want to ensure that you obtain 5 valid values from the user. which nested loop structure would you use?
Answers
In a computer program, loops are used to perform repetitive operations until a condition is met.
The nested loop structure to use in this case is: A "while" loop inside of a "for" loop
The outer loop
First, you must iterate through each student.
This can be done using a for loop or a while loop.
However, it is faster to implement this kind of iteration on a for loop, than a while loop
So, the algorithm of the outer loop would look like the following:
for student = 1 to 5 step 1
The inner loop
Next, you must get input for the 5 grades for each student
After getting input for the grade of each student, a loop would be used to test if the input is valid.
The loop would be repeated until the user enters a valid input.
This can only be done using a while loop.
So, the algorithm of the inner loop would look like the following:
input grade
while grade is invalid:
input grade
Hence, the nested loop structure to use is:
A "while" loop inside of a "for" loop
Read more about loops at:
https://brainly.com/question/11608024
The physical parts of a computer are called application software.
Answers
Answer:
false
Explanation:
problem 1) simple boolean logic operations. assume we have four input data samples {(0, 0), (0, 1), (1, 0), (1, 1)} to a model. perform the followings in python: a) plot the four input data samples. label the axes and title as appropriate. b) write a function that takes two arguments as an input and performs and operation. the function returns the result to the main program. c) write two additional functions like in part (b); each would perform or and xor operations and return the result to the main program. d) create a for loop to call the three functions each for data sample each time. e) store the output of each function in a separate list/array. f) print out the results for the three functions at the end of your program. g) note: do not use the internal boolean (and, or, xor) functions in python; instead, utilize conditional statements to perform the desired operations.
Answers
Utilizing Python to Execute Boolean Logic Operations on Input Data Samples: Plotting, Creating and Executing Functions, Storing, and Printing
What are the Boolean operations?A type of algebra known as boolean logic is based on three straightforward words known as boolean operators: Or, "And," "Not," and "And" The logical conjunctions between your keywords that are used in a search to either broaden or narrow its scope are known as Boolean operators. The use of words and phrases like "and," "or," and "not" in search tools to get the most related results is known as boolean logic. The use of "recipes and potatoes" to locate potato-based recipes is an illustration of Boolean logic.
The use of words and phrases like "and," "or," and "not" in search tools to get the most related results is known as boolean logic. The use of "recipes AND potatoes" to locate potato-based recipes is an illustration of Boolean logic.
What are the three for-loop functions?
The initialization statement describes where the loop variable is initialized with a starting value at the beginning of the loop. The condition until the loop is repeated is the test expression. The update statement, which typically specifies the incrementing number of the loop variable.
Learn more about boolean logic :
brainly.com/question/29426812
#SPJ4
Select the correct answer. Frank works for an organization that wishes to install a software program on a single server with multiple users connected. Which of these computing services should Frank consider to make the software available to multiple users connected to the server? A. cloud computing B. mobile computing C. digital computing D. end-user computing
Answers
Answer:
A. cloud computing
Explanation:
Frank's organization wishes to install a program that can connect multiple users on a single server. They can achieve this through cloud computing. Cloud computing is a description of data centers which are available to many or multiple users all over the internet. Through cloud computing services, users can check their emails from any computer system. Also cloud services such as Dropbox, Google drive, are available for users to store files.
Which describes a design theme in PowerPoint?
Answers
What would happen if there is no option to save Temporary internet files (Cookies) while using the internet
Answers
When there is no option to keep temporary internet files (cookies) while browsing the internet, the user's browsing experience might suffer in numerous ways.
Login credentials: Because cookies are frequently used to save login credentials for websites, users may need to manually input their login information each time they visit a page if cookies are not kept. Cookies can also be used to remember users' specific settings, such as language preferences or display options. Users may need to modify these settings every time they visit a website if cookies are not used. Shopping cart items: Cookies can assist e-commerce internet websites remember things that users have placed to their shopping cart. Users may need to manually add products to their shopping cart if cookies are not present.
learn more about internet here:
https://brainly.com/question/13308791
#SPJ4
WNOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOOW
Answers
Answer:
yes.
Explanation: