What type of exception does a program raise when it tries to open a nonexistent file?
Answers
When a program tries to open a nonexistent file, it raises a "FileNotFoundError" exception. This exception indicates that the file or directory that the program is trying to access does not exist.
When a program tries to open a nonexistent file, it raises a "FileNotFoundError" exception. This is a specific type of exception in Python that is raised when a file operation (such as opening or reading a file) fails because the specified file cannot be found in the specified location.
Other programming languages may have different names for this type of exception, but it is generally referred to as a "file not found" or "file not exist" exception. This exception is important for handling errors that can occur when working with files, which are a common source of data in many programming applications.
To know more about nonexistent file, visit:
https://brainly.com/question/28558522
#SPJ11
Related Questions
Using Java,Create a JFrame application with a textfield and an
OK button.
The user types in a number, and presses "OK", your application
will get that text, convert it to an int, and display
the square of that number in a messagedialog.
Answers
To create a JFrame application with a text field and an OK button using Java, you can use the following code:
```
import java. swing.*;
import java. awt.*;
import java.awt.event.*;
public class MyFrame extends JFrame implements ActionListener {
private JTextField textField;
private JButton okButton;
public MyFrame() {
super("Square Calculator");
textField = new JTextField(10);
okButton = new JButton("OK");
okButton.addActionListener(this);
JPanel panel = new JPanel(new FlowLayout());
panel.add(textField);
panel.add(okButton);
add(panel);
setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE);
pack();
setVisible(true);
}
public void actionPerformed(ActionEvent e) {
if (e.getSource() == okButton) {
String text = textField.getText();
int number = Integer.parseInt(text);
int square = number * number;
JOptionPane.showMessageDialog(null, "The square of " + number + " is " + square);
}
}
public static void main(String[] args) {
MyFrame frame = new MyFrame();
}
}
```
In this code, we create a JFrame with a textfield and a button. We add an action listener to the button so that when the user clicks it, we get the text from the textfield, convert it to an int, calculate the square of the number, and display the result in a message dialog using the `JOptionPane.showMessageDialog()` method with the `messagedialog` term.
Learn more about Java here:
https://brainly.com/question/16400403
#SPJ11
IF YOU PLAY SURVIV>IO WITH ME RIGHT NOW I WILL GIVE YOU BRAINLIEST
AND IM NOT KAPPING
Answers
Answer:
no
Explanation:
moomoo.io is way better
You want the output to be left justified in a field that is nine characters wide. What format string do you need?
print('{: __ __ }' .format(23)
Answers
Answer:
> and 8
Explanation:
> and 8 format string one will need in this particular input of the java string.
What is a format string?The Format String is the contention of the Format Function and is an ASCII Z string that contains text and configuration boundaries, as printf. The parameter as %x %s characterizes the sort of transformation of the format function.
Python String design() is a capability used to supplant, substitute, or convert the string with placeholders with legitimate qualities in the last string. It is an inherent capability of the Python string class, which returns the designed string as a result.
The '8' specifies the field width of the input The Format String is the contention of the Configuration Capability and is an ASCII Z string that contains the text.
Learn more about format string, here:
https://brainly.com/question/28989849
#SPJ3
pls help me with this question

Answers
write a program that removes all non-alpha characters from the given input. ex: if the input is: -hello, 1 world$!
Answers
Here's a Python program that removes all non-alpha characters from the given input```python input_string = "-hello, 1 world$!" output_string = "" for char in input_string: if char.isalpha(): output_string += char print(output_string) When you run this program, it will output the following string.
helloworld This program starts by defining an input string variable that contains the text we want to remove non-alpha characters from. We also define an empty output string variable to hold the final result. we loop through each character in the input string using a for loop. For each character, we use the `isalpha()` method to check if it's an alphabetic character.
If it is, we append it to the output string using the `+=` operator. After looping through all the characters in the input string, we print out the output string that contains only the alphabetic characters. The `isalpha()` method is a built-in Python function that returns `True` if a character is an alphabetic character and `False` otherwise. In our program, we use this method to check each character in the input string and only add it to the output string if it is alphabetic. The `+=` operator is a shorthand way of concatenating strings. In our program, we use it to append each alphabetic character to the output string as we loop through the input string. Overall, this program is a simple way to remove non-alpha characters from a given input string. To write a program that removes all non-alpha characters from the given input, such as "-hello, 1 world$!", follow these Define the input string. Create an empty string called "result". Iterate through each character in the input string. Check if the character is an alphabetical character If it is, add it to the "result" string. Print the "result" string. Here's a sample Python program using the above explanation`python # Step 1: Define the input string input_string = "-hello, 1 world$!"# Step 2: Create an empty string called "result" result = "" # Step 3: Iterate through each character in the input strinfor char in input_string:# Step 4: Check if the character is an alphabetical character if char.isalpha(): # Step 5: If it is, add it to the "result" string result += char Print the "result" strin print(result) Running this program with the input "-hello, 1 world$!" would result in the output "helloworld".
To know more about removes visit:
https://brainly.com/question/30455239
#SPJ11
7.2 code practice edhesive. I need help!!
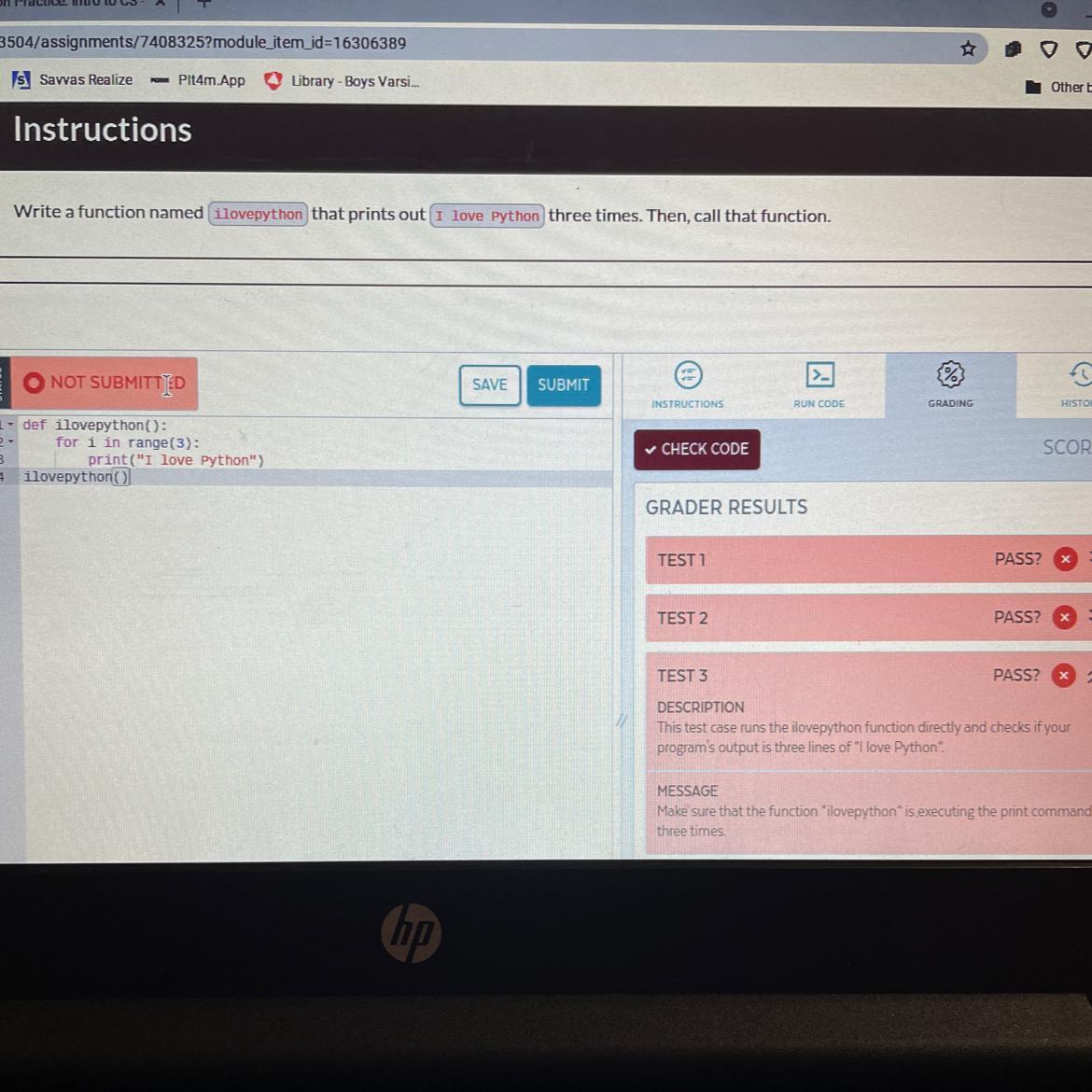
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
you have just finished building a windows server, installing its operating system, updating its security patches, formatting a dedicated data partition, and creating accounts for all of the company's employees. what is the next thing that must be configured to provide users with the ability to access the data contained on the server's data partition?
Answers
To provide users with the ability to access the data contained on the server's data partition, the next thing that must be configured is the network sharing and permissions settings.
Network sharing allows multiple users to access the same resources, such as files and folders, over a network. To set up network sharing on the Windows server, you will need to share the data partition and configure the appropriate permissions to ensure that users have the correct level of access.
To share the data partition, you can right-click on the folder and select "Properties" and then the "Sharing" tab. From there, you can choose to share the folder and set permissions for different users and groups. For example, you may want to give read-only access to some users and full control to others.
It's also important to configure security permissions to ensure that users can only access the data they are authorized to see. You can set security permissions by right-clicking on the folder, selecting "Properties," and then clicking the "Security" tab. From there, you can add or remove users or groups and set their permissions for the folder.
Once network sharing and permissions have been configured, users will be able to access the data contained on the server's data partition by connecting to the server through the network and navigating to the shared folder.
To learn more about Network sharing, visit:
https://brainly.com/question/14672166
#SPJ11
Which design element involves the act of lining up objects vertically or horizontally to give a sense of order?
Answers
Answer:
The answer is "Alignment".
Explanation:
The Alignment was its positioning of visual elements, such that they're coordinate together with such a structure. This is a layout concept that refers to words or pictures lining up with one page. They use coordination in the layout to coordinate entities, a system similar, equilibrium, framework formation, the connection among aspects, and clear and clear result.
4.9 Code Practice Question 4
Write a program that asks the user to enter ten temperatures and then finds the sum. The input temperatures should allow for decimal values.
Sample Run
Enter Temperature: 27.6
Enter Temperature: 29.5
Enter Temperature: 35
Enter Temperature: 45.5
Enter Temperature: 54
Enter Temperature: 64.4
Enter Temperature: 69
Enter Temperature: 68
Enter Temperature: 61.3
Enter Temperature: 50
Sum = 504.3
Answers
total = 0
for x in range(10):
temp = float(input("Enter Temperature: "))
total += temp
print("Sum = {}".format(total))
I hope this helps!
Select all statements from the given choices that are the negation of the statement:
Michael's PC runs Linux.
Select one or more:
a. It is not true that Michael's PC runs Linux.
b. It is not the case that Michael's PC runs Linux.
c. None of these
d. Michael's PC runs Mac OS software.
e. Michael's PC runs Mac OS software and windows.
f. It is false that Michael's PC runs Linux.
g. Michael's PC doesn't run Linux.
h. Michael's PC runs Mac OS software or windows.
i. Michael's PC runs Windows
Answers
The statements that are the negation of "Michael's PC runs Linux" are: a. It is not true that Michael's PC runs Linux. b. It is not the case that Michael's PC runs Linux. d. Michael's PC runs Mac OS software. e. Michael's PC runs Mac OS software and windows. f. It is false that Michael's PC runs Linux. g. Michael's PC doesn't run Linux. h. Michael's PC runs Mac OS software or windows. i. Michael's PC runs Windows.
The negation of a statement is the opposite or contradictory statement. In this case, the statement "Michael's PC runs Linux" can be negated in multiple ways.
Options a, b, f, and g all express the negation by denying the truth of the original statement. Option d states that Michael's PC runs Mac OS software, which contradicts the statement that it runs Linux. Option e extends the negation by adding the condition that Michael's PC runs both Mac OS software and Windows, further diverging from the original statement. Option h also offers a contradictory statement by stating that Michael's PC runs either Mac OS software or Windows, but not Linux. Finally, option i simply states that Michael's PC runs Windows, which excludes Linux.
In summary, options a, b, d, e, f, g, h, and i all provide statements that negate the original claim that Michael's PC runs Linux.
Learn more about software.
brainly.com/question/32393976
#SPJ11
What action should you take when using removable media in a scif?
Answers
Explanation:
What actions should you take when printing classified material within a Sensitive Compartmented Information Facility (SCIF)? Retrieve classified documents promptly from printers.
The action which a person should take when using removable media in a SCRIF is:
Retrieve classified documents promptly from printers.According to the given question, we are asked to show the action which a person should take when using removable media in a SCRIF
As a result of this, we can see that a SCRIF is an acronym which stands for Sensitive Compartmented Information Facility and the action which a person should taken when making use of a removable media in SCRIF is to immediately retrieve classified documents promptly from printers.
This is to prevent the information getting into the wrong hands.
Read more here:
https://brainly.com/question/17199136
Why do we need to get the minimum and maximum resistance value of resistors?
Answers
20. Which of the following is an example of plagiarism?
A. Citing information from a fake news site.
B. Illegally downloading a movie that you like from the Internet.
C. Copying your friend's work and claiming it as your own.
D. Sharing an author's words and giving them proper credit.
Answers
Answer: C. Copying your friend's work and claiming it as your own.
Explanation:
plagiarism is taking someone else's work or ideas and passing them off as one's own.
Which statement of the visualization is incorrect? A) Virtualization works on the desktop, allowing only one operating system(Mac OS, Linux, or Windows) to run on the platform B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources C) Virtualization is referred to as the operating system for operating systems D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
Answers
The incorrect statement is A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform. Virtualization on the desktop enables the concurrent execution of multiple operating systems.
Explanation:
A) Virtualization works on the desktop, allowing only one operating system (Mac OS, Linux, or Windows) to run on the platform.
This statement is incorrect because virtualization on the desktop allows multiple operating systems to run concurrently on the same platform. Virtualization software, such as VMware or VirtualBox, enables users to create and run virtual machines (VMs) that can host different operating systems simultaneously, including Mac OS, Linux, and Windows.
B) A server running virtualization software can create smaller compartments in memory that each behaves like a separate computer with its own operating system and resources.
This statement is correct. Virtualization software allows the creation of virtual compartments or containers within a server's memory. Each compartment, known as a virtual machine, can operate independently with its own dedicated operating system and allocated resources.
C) Virtualization is referred to as the operating system for operating systems.
This statement is correct. Virtualization is often referred to as the "operating system for operating systems" because it provides a layer of abstraction and management for multiple operating systems running on the same physical hardware.
D) Virtualization can generate huge savings for firms by increasing the usage of their hardware capacity.
This statement is correct. Virtualization enables efficient utilization of hardware resources by consolidating multiple virtual machines onto a single physical server. This consolidation reduces the need for additional physical servers, leading to cost savings in terms of hardware procurement, maintenance, and power consumption.
To know more about operating system visit :
https://brainly.com/question/29532405
#SPJ11
What does it mean when someone silences notifications?.
Answers
Answer:
Silencing notifications does not alert someone when the notification comes in. It is silent. These settings were invented to help avoid distractions. The notifications still come in just quietly without an alert and can be checked at any time. Lots of people silence notifcations at night, while sleeping, while studying, etc.
Explanation:
explain the importance of the educational apps.give an example to support your answer
Answers
Answer: Students can access high quality educational resources from anywhere in the world.
Explanation:
if a document you are trying to print doesn't print, what is the first step that you should take
Answers
Answer:
Check the error lights!
Explanation:
Check Your Printer's Error Lights.
Clear the Printer Queue.
Solidify the Connection.
Ensure You Have the Right Printer.
Install the Drivers and Software.
Add Printer.
Check that Paper Is Installed (Not Jammed)
Fiddle With the Ink Cartridges.
When you use the implicit syntax for coding joins, the join conditions are coded in the ____________ clause.
Answers
When you use the implicit syntax for coding joins, the join conditions are coded in the WHERE clause.
What is syntax?It should be noted that syntax simply means the rule that defines the language structure in programming.
In this case, when you use the implicit syntax for coding joins, the join conditions are coded in the WHERE clause.
Learn more about syntax on:
brainly.com/question/21926388
#SPJ12
Which of the following
statements about take home pay is TRUE?

Answers
Answer:
Take home pay is amount left over from your monthly paycheck after deductions.
Explanation:
It is how much you get to keep after taxes and whatnot.
It is how much you get to keep after taxes and whatnot.
What is Home pay?It is full-service pay processing capabilities and nanny-specific experience, HomePay is one of our top-recommended nanny payroll providers.
Instead of just offering you the knowledge and resources to do it yourself, its representatives manage the payroll process for you. The supplier will even set up your tax accounts if you're a new household employer, making it simpler for you to get started.
Using HomePay gives you access to payroll tax professionals who keep up with changing requirements and can save you money in the long term, even if it is more expensive than handling payroll yourself. Moreover, there are no startup or registration costs.
Therefore, It is how much you get to keep after taxes and whatnot.
To learn more about Homepay, refer to the link:
https://brainly.com/question/6868391
#SPJ2
Dependence and addiction will make you
a drug.
Answers
Answer: When a person stops taking a medicine, their body goes through "withdrawal":
A mobile device user has tried to install a new app numerous times without success. She has closed all unused apps, disabled live wallpapers, and restarted the device in an attempt to get the app to install.
Which of the following steps should the user take next?
A. Back up all user data and perform a factory reset.
B. Check for sufficient available storage space.
C. Disable full device encryption.
D. Generate a new public key.
Answers
The correct answer is B. Check for sufficient available storage space.
Explanation:
One of the factors that can cause it is not possible to install a new app is insufficient storage as space in the mobile device is needed to save the app. This can be easily solved either by deleting apps and other content or expanding the memory available through a Micro SD card. Also, before attempting any major procedure such as a complete reset it is important to check the storage space availability. In this context, the user should check for sufficient available storage space (option B) because this might be the cause of the issue she is experiencing; also, this is a basic step before considering others such as performing a factory reset.
2) A Chief Information Security Officer(CISO) request a report of
employees who access the datacenter after business hours. The report
prepared by analyzing log files in comparison to business hours, Which of
the following BEST describes this scenario?
Relationship of Data to Information
Importance of investing in Security
Data Capture and collection
Data and information as Assets
Answers
The scenario highlights the importance of data capture and collection, the relationship between data and information as assets, and the importance of investing in security measures to protect these assets.
Explanation:
The BEST description for this scenario is "Data Capture and Collection." The CISO is requesting a report that involves analyzing log files, which is a form of capturing and collecting data. This data can then be used to identify employees who are accessing the datacenter after business hours, which is important for maintaining security. This scenario highlights the importance of data and information as assets, as well as the importance of investing in security measures to protect these assets.
This scenario involves the Chief Information Security Officer (CISO) requesting a report on employees who access the datacenter after business hours. To prepare this report, log files are analyzed to identify which employees are accessing the datacenter outside of business hours. This process involves capturing and collecting data, specifically log files, which can then be used to extract meaningful information. This information can then be used to identify potential security risks and inform security measures to mitigate these risks.
The scenario highlights the importance of data and information as assets. Log files are a type of data that can provide valuable insights into employee behavior and potential security risks. The ability to capture and analyze this data is critical for protecting these assets and maintaining the security of the organization. Additionally, investing in security measures to protect these assets is crucial for ensuring that the data and information remain secure.
In summary, the scenario highlights the importance of data capture and collection, the relationship between data and information as assets, and the importance of investing in security measures to protect these assets.
Know more about the data and information click here:
https://brainly.com/question/31419569
#SPJ11
you want to apply a subtotal to a dataset containing names, departments, and salaries. what is the first step you need to do? filter the dataset by salaries select the function to be used for the subtotal insert new rows where you want the subtotal rows within the dataset sort the dataset by a field containing categories
Answers
The first step to apply a subtotal to a dataset containing names is to filter the dataset by salaries.
This will allow you to select the data that you need to apply the subtotal to. Once the dataset is filtered, you can then select the function to be used for the subtotal, insert new rows where you want the subtotal rows within the dataset, and sort the dataset by a field containing categories. To apply a subtotal to a dataset containing names, departments, and salaries, the first step you need to do is to insert new rows where you want the subtotal rows within the dataset.A subtotal is a part of a dataset that calculates a summary for a group of records. Here are the steps that you need to follow to apply a subtotal to a dataset containing names, departments, and salaries:Insert new rows where you want the subtotal rows within the dataset.
Learn more about dataset: https://brainly.com/question/28332864
#SPJ11
how old is the letter 3 on its 23rd birthday when your car turns 53 and your dog needs gas and your feet need lave then when is your birthday when your mom turns 1 and your younger brother is older then you
Answers
Answer:
ummm...idr.k..u got me....wat is it
Explanation:
What is the formula in cell F9?
Answers
The F9 key in Microsoft Excel is a simple and fast way to check and debug formulas. By substituting it with the actual values that part of the formula acts on or with the calculated result, it enables you to solely assess the specified portion of the formula.
Almost everyone is aware that in Excel, pressing the F9 key causes all open workbooks' worksheets to be recalculated. However, a lot of people are unaware that F9 can also be used to comprehend and troubleshoot formulas.
There are numerous ways to evaluate formulas in Excel because there are often numerous ways to do a given task.
Pressing CTRL + is the quickest way to evaluate a calculation in Excel (tilde). This toggles the current worksheet's display, enabling you to switch between viewing cell values and cell formula. The F9 key can be used to assess your formula or a portion of your formula in order to get around the limits.
Know more about F9 key:
https://brainly.com/question/28959274
#SPJ4
Sally is an online retailer who engages in third-party network transactions via nettrans, inc. payment company to facilitate financial transactions in the sale of her products. for 2022, what is the minimum aggregate sales and number of sales per year required to trigger a 1099-k by nettrans, inc. payment company?
Answers
Answer:
Under the Internal Revenue Service (IRS) rules, a payment settlement entity (such as Nettrans, Inc.) is required to file a Form 1099-K with the IRS and furnish a copy to the relevant payee if it processes more than 200 transactions with a payee and the payee receives gross payments of more than $20,000 in a calendar year. This means that if Sally receives more than $20,000 in gross payments through Nettrans, Inc. in a calendar year, and Nettrans, Inc. processes more than 200 transactions with Sally in that year, Nettrans, Inc. will be required to file a Form 1099-K with the IRS and furnish a copy to Sally.
It's important to note that this requirement applies to the gross payments Sally receives, not the net amount she receives after deducting any fees or other expenses. Additionally, it's worth noting that this requirement applies to all payees who receive gross payments through Nettrans, Inc., not just online retailers like Sally.
If Sally has any questions about the Form 1099-K or her tax obligations, she should consult with a tax professional or refer to IRS guidance.
Explanation:
Sally should speak with a tax expert or review the IRS guidelines if she has any concerns regarding the Form 1099-K or her tax responsibilities.
What is third-party network transaction?Any transaction that is resolved through a third-party payment network is referred to as a third-party network transaction, but only if the aggregate value of all such transactions surpasses minimal reporting limits.
According to Internal Revenue Service regulations, if a payment settlement organization performs more than 200 transactions with a payee and the payee gets gross payments of more than $20,000 in a calendar year.
It must file Form 1099-K with the IRS and provide a copy to the relevant payee. This implies that Nettrans, Inc. will be required to file a Form 1099-K with the IRS and provide a copy to Sally.
If Sally gets more than $20,000 in gross payments through Nettrans, Inc. in a calendar year and Nettrans, Inc. performs more than 200 transactions with Sally in that year.
Thus, this can be the solution for Sally for the given scenario.
For more details regarding third-party network transactions, visit:
https://brainly.com/question/29646130
#SPJ2
What best describes the development of 3-D graphics in the video game industry? Responses The ability to create them did not exist until the 2000s, and while they are easy to do, they are not widespread. The ability to create them did not exist until the 2000s, and while they are easy to do, they are not widespread. The ability to create them did not exist until the 1990s, but they became widespread as soon as the technology was there. The ability to create them did not exist until the 1990s, but they became widespread as soon as the technology was there. The ability to create them existed in the 1970s, but their use in the gaming industry did not become widespread until the 1990s. The ability to create them existed in the 1970s, but their use in the gaming industry did not become widespread until the 1990s. The ability to create them existed in the 1960s, but their use in the gaming industry has never really become popular. The ability to create them existed in the 1960s, but their use in the gaming industry has never really become popular.
Answers
The option that best describes the development of 3-D graphics in the video game industry is option d: The ability to create them existed in the 1970s, but their use in the gaming industry did not become widespread until the 1990s.
What do the visuals in video games mean?Any video game's graphics are crucial since they determine what the player sees. The locations, characters, and even the lighting all contribute to how the game looks and feels.
Therefore, In order to execute computations and create digital images, often 2D ones, 3D computer graphics, also known as "3D graphics," 3D-CGI, or three-dimensional computer graphics, require a three-dimensional representation of geometric data that is stored in the computer.
Learn more about video game from
https://brainly.com/question/28282278
#SPJ1
From a structural point of view, 3nf is better than _____.
a. 2nf.
b. 5nf.
c. 6nf.
d. 3nf.
Answers
From a structural point of view, 3NF is better than 2NF.
In 3NF (Third Normal Form), each non-key attribute is dependent only on the candidate key and not on other non-key attributes. This eliminates transitive dependencies and reduces data redundancy, making the structure more efficient and flexible.
On the other hand, 2NF (Second Normal Form) allows for partial dependencies, where non-key attributes depend on only a portion of the candidate key. This can result in data redundancy and make the structure more complex.
By achieving 3NF, we ensure that the data is organized in a way that minimizes duplication and provides a clearer and more logical structure. This improves data integrity and simplifies data maintenance and updates. It also enhances query performance by reducing the need for complex joins and providing a more streamlined data model.
Learn more about 3NF
brainly.com/question/33474617
#SPJ11
The first photo in the collage is what I should make a copy of, anyone has any knowledge on how to add the numbers apart of the spreadsheet and the letters?

Answers
Type the formula, with double quotes within the file. For instance: ="Due in "&A3 &" days"
NOTE: End or begin the text string with a space to separate the text strings from the numbers.
To complete the formula, press Enter
Which layer(s) of the web application are being used when the user hits the button?
Answers
When a user hits a button on a web page the three layers including presentation layer, logic layer, and data layer, of the web application are being used.
For data processing the web applications are organized into three layers which are the presentation layer, the logic layer, and the data layer. Based on the given scenario in the question, all the three layers of the web application are being utilized when the user hits a button on a web page/web application.
The working of each layer of the web application upon hitting a button is as follows:
The presentation layer: It allows the user to hit the button. It provides an interface through which the user interacts with the web application by clicking a button. The user hits the button on the presentation layer.The logic layer: The presentation layer then communicates to the logic layer where the request generated by clicking the button is processed. For processing the request, the logic layer interacts with the data layer to acquire the data needed. After receiving the data, the logic layer processes it and sends it back up to the presentation layer to be displayed to the user. The function of the logic layer is to process the requested data.
The data layer: The data layer sends the required data to the logic layer for processing. The data layer stores and manages all the data associated with the application.
You can learn more about web application layers at
https://brainly.com/question/12627837
#SPJ4