what is a perfect hash in a hash table? what is a perfect hash in a hash table? a hash table that does not have any primary clustering. two different keys hashing to a value outside of the range of the table.two different keys hashing to a value outside of the range of the table.
Answers
A common method for storing and retrieving data as quickly as feasible is hashing. The primary benefit of employing hashing is that it produces the best results because it uses the best searches.
What is hash table?A hash table, commonly referred to as a hash map, is a type of data structure used in computing to build an associative array or dictionary. It is a type of abstract data that associates values with keys. An array of buckets or slots are used in a hash table to provide an index, also known as a hash code, from which the requested data can be retrieved. The key is hashed during lookup, and the resulting hash shows where the relevant value is kept.Since most hash table designs use an incomplete hash function, hash collisions may occur when the hash function generates the same index for multiple keys. In an ideal world, the hash function would assign each key to a separate bucket. Usually, such encounters are allowedTo learn more about hash table refer to:
https://brainly.com/question/13162118
#SPJ4
Related Questions
What are the uses of magnetic force?
Answers
Explanation:
Computer hard drives use magnetism to store the data on a rotating disk. More complex applications include: televisions, radios, microwave ovens, telephone systems, and computers. An industrial application of magnetic force is an electromagnetic crane that is used for lifting metal objects.
Answer:
Examples of magnetic force is a compass, a motor, the magnets that hold stuff on the refrigerator, train tracks, and new roller coasters. All moving charges give rise to a magnetic field and the charges that move through its regions, experience a force.
I Hope this will help you if not then sorry :)
why hand tools are important in repairing personal computer?
Answers
Answer:
Using the appropriate tools helps ensure that computer components are not damaged during cleaning.
Explanation:
If you don't use the right hand tools, you could easily damage or scratch computer components that are vital to run the computer.
Answer:
Because the parts of the computer are at the micro level, repairing them is a very important job. That's why these tiny tools are used in the repair of computers.
Explanation:
If It was helpful, can you make me brainliest please?
A thin sample of x is put between metal plates. A radio-frequency electric current is applied to the plates and passes through the sample. From the measured voltage across the plates the value of e may be calculated.
Answers
From the measured voltage across the plates the value of E may be calculated as а physical property.
What is a chemical property?A physicаl property is а chаrаcteristic of а substаnce thаt cаn be observed or meаsured without chаnging the identity of the substаnce. Physicаl properties include color, density, hаrdness, аnd melting аnd boiling points.
А chemicаl property describes the аbility of а substаnce to undergo а specific chemicаl chаnge. To identify а chemicаl property, we look for а chemicаl chаnge. А chemicаl chаnge аlwаys produces one or more types of mаtter thаt differ from the mаtter present before the chаnge. The formаtion of rust is а chemicаl chаnge becаuse rust is а different kind of mаtter thаn the iron, oxygen, аnd wаter present before the rust formed.
Your question is incomplete, but most probably your options were
A. Physical
B. Chemical
C. (can't decide)
Thus, A is the correct answer.
For more information about a chemical property refers to the link:
https://brainly.com/question/1344992
#SPJ4

45 points pls help
_______ refers to achieving synchronization of similar elements in a design.

Answers
Explanation:
Harmony is the unity of all the visual elements in a composition. It is often achieved through the use of repetition and simplicity. A principle of design that refers to a way of combining elements in involved ways to achieve intricate and complex relationships.
hope it helps you...
The purpose of data analysis is to filter the data so that only the important data is viewed.
False
True
Answers
Answer:
YES IT IS TRUE!
Explanation:
Computer system with a 32-bit logical address and 4k-byte page size. assume that each entry of a page table consists of 4bytes.
a. suppose that this system supports up to 64mb of physical memory.
how many bits are there in the physical address?
how many entries are there un a page table?
if this system uses a one-level paging scherne, what is the size of page table?
b. suppose that this system supports up to 2^30 bytes of physical memory.
if this system uses a conventional single-level page tavle, what would the size of a page table be?
if we want the size of each page table to be no gather than the page size(4kb), what scheme would you want to use?
Answers
The number of bits in the physical address is 26 bits. The number of entries in a page table is \(\mathbf{2^{20}}\) entries. The size of the page table in a one-level paging scheme is 4MB.
What is paging in Operating System?
Paging is a storage method used in operating systems to recover activities as pages from secondary storage and place them in primary memory. The basic purpose of pagination is to separate each procedure into pages.
We are given the following parameters:
32-bit logical addressPage size = 4 KB = \(\mathbf{2^{12} \ bytes }\)Size of each Page table entry = 4 bytesSuppose the system supports physical memory size = 64 MB = \(\mathbf{2^{26} \ bytes}\)
Thus, the number of bits in the physical address is computed as:
= \(\mathbf{log_2 \{Physical-memory-size\}}\)
\(=\mathbf{log_2(2^{26})}}\)
= 26 bits
The number of entries in a page table = logical address space size/page size
The number of entries in a page table \(\mathbf{= \dfrac{2^{32}}{2^{12}}}\)
\(\mathbf{=2^{20}}\) entries
In a one-level paging scheme, the size of the table is:
= entire no. of page entries × page table size
= \(\mathbf{2^{20}\times 4 \ bytes}\)
= 4 MB
b.
suppose that this system supports up to 2^30 bytes of physical memory.
The size of the page table will be the same as 4 MB due to the fact that the number of entries, as well as, the page table entry size is the same.Since the size of the page table surpasses that of a single page. A page cannot include a whole page table. Therefore, the page table must be broken into parts to fit onto numerous pages, and an additional level of the page table is required to access this page table.
This is called the Multi-Level Paging system.Therefore, we can conclude that the number of bits in the physical address is 26 bits, the number of entries in a page table is \(\mathbf{2^{20}}\) entries, and the size of the page table in a one-level paging scheme is 4MB.
Learn more about Paging in Operating System here:
https://brainly.com/question/17004314
#SPJ1
What will help the programmer understand what’s going on in the program?
Answers
Answer:
Programming languages to help solve algorithms
Explanation:
You manage Windows notebook systems that are members of a domain. You have ten regional salespeople who travel extensively and use these notebooks to access company resources. The users have complained that although they can take copies of important files with them into the field, occasionally, they have been caught with out-of-date documents because no one told them the files had been updated. Additionally, some files they modify need to be distributed to all the other sales staff. What can you do to provide the needed access to these shared files
Answers
Answer:
To provide the needed access to these shared files, you need to set up offline files for the folder that contains these files as this will also solve the problem of the users getting to use out-of-date documents since the user can get access to the files even when disconnected from the network.
Explanation:
Offline Files make network files available to users by ensuring local copies of network shares are stored, making it possible to work with files while away from the network. Offline files can be easily synced with network files.
You are the chief financial officer of Donnelly Industries. On multiple occasions, you have engaged in insider trading but have never been able to earn any abnormal returns. Which form of market efficiency most likely exists given your situation
Answers
Based on the scenario presented, it is likely that the weak form of market efficiency exists.
This is because the CFO engaged in insider trading on multiple occasions, but was unable to earn any abnormal returns. In a weak form efficient market, all past prices and trading volumes are already reflected in current stock prices, meaning that insider information would not provide any significant advantage to investors.
Furthermore, if the market were semi-strong or strong form efficient, the CFO would not have been able to engage in insider trading at all, as all public and non-public information would have already been reflected in the stock price.
Donnelly Industries operates in various industries, including manufacturing, healthcare, and technology. In a financially efficient market, information is readily available to investors, and stock prices accurately reflect all available information. Thus, investors are unable to consistently earn abnormal returns by using insider information or any other financial analysis techniques.
In conclusion, the CFO's inability to earn abnormal returns despite engaging in insider trading suggests that the market is weak form efficient, meaning that past prices and trading volumes are already incorporated into current stock prices. It is important for investors to be aware of market efficiency when making investment decisions, as it can affect the potential for earning abnormal returns.
Learn more about investors :
https://brainly.com/question/31933294
#SPJ11
What kind of computer stores IP addresses?
Answers
A DNS - Domain Name Server - works as a sort of phone directory for computers and stores lots of IP addresses. But a DNS is not a kind of computer, it is just a program that in principle could run anywhere.
Answer:
Every computer has its own IP address, and it is through this naming system that computers can connect with each other and share data. ... While every computer is given its own IP address, the outside world rarely has access to it.
Explanation:
As a cyber investigator, you are investigating a group known as BLGRUS (Bootleggers R Us) that is allegedly posting your company’s music files without your permissions. Write a 2-3 page document on your plan to infiltrate their group (keep in mind their motivations to commit the offense), identify the users, send any legal documentation and preserve evidence
Answers
To infiltrate the group known as BLGRUS, I will adopt a multi-faceted approach. Firstly, I will analyze their motivations and modus operandi to gain a deeper understanding of their activities. Then, I will employ undercover techniques to gain access to their online platforms and identify the users involved.
In order to effectively infiltrate the BLGRUS group, it is crucial to comprehend their motivations for posting the music files without permission. This understanding will allow us to tailor our approach and devise suitable strategies. The motivations of such groups often revolve around financial gain, desire for notoriety, or ideological opposition to copyright laws. By conducting thorough research and analysis, we can gain insights into their modus operandi, preferred platforms, and methods of communication.
With this knowledge in hand, I will employ undercover techniques to penetrate the group's online platforms. This may involve creating anonymous profiles or using existing ones that align with the group's interests. By actively participating in their discussions and gaining their trust, I can gather valuable information regarding the identities of the users involved, their roles within the group, and their activities.
Simultaneously, it is crucial to collect solid evidence of copyright infringement. This can be done by monitoring their activities, capturing screenshots, and recording any instances of music file sharing or unauthorized distribution. Additionally, I will employ advanced digital forensics techniques to trace the origin of the uploaded files and identify any potential collaborators or sources.
Once the users involved in the copyright infringement are identified, it is important to take legal action to protect our company's interests. To do this, I will prepare cease-and-desist letters, clearly outlining the copyright violation and the potential legal consequences. These letters will be accompanied by supporting legal documentation, such as copyright registration certificates and evidence of infringement, to strengthen our case.
Throughout this entire process, it is crucial to ensure the preservation of all evidence. This includes maintaining comprehensive records of communications, screenshots, and any other relevant digital artifacts. Proper documentation and preservation of evidence will not only strengthen our legal case but also provide a solid foundation for potential negotiations or settlements.
In summary, infiltrating the BLGRUS group requires a comprehensive plan that takes into account their motivations, employs undercover techniques, identifies the users involved, sends legal documentation, and preserves evidence. By understanding their motivations, adopting undercover strategies, and employing legal measures, we can effectively combat copyright infringement and protect our company's music files.
learn more about multi-faceted approach. here:
https://brainly.com/question/28167452
#SPJ11
Kolom terakhir pada lembar kerja Excel 2019 adalah
Answers
Answer:
Tahan CTRL dan tekan tombol panah kanan (tombol kursor) pada keyboard. Anda dibawa ke kolom paling kanan. Dalam versi Excel modern, ini adalah kolom XFD, yaitu 16.384 kolom. Di versi Excel yang lebih lama (2003 dan sebelumnya) kolom terakhir adalah IV yaitu 256 kolom.
in english
Hold down CTRL and press the right arrow key (cursor key) on the keyboard. You are taken to the right-most column. In the modern versions of Excel this is column XFD, which is 16,384 columns. In older versions of Excel (2003 and prior) the last column was IV which is 256 columns.
Thinking carefully about a speaker's reasoning and purpose can help you _____ that speaker's message. In other words, you consider the message and decide whether it is believable.
Answers
Thinking carefully about a speaker's reasoning and purpose can help you comprehend (understand) that speaker's message. In other words, you consider the message and decide whether it is believable.
What do you think is the purpose of the speakers in their speech?Making sense of the world around us is referred to as reasoning. A communication must be evaluated during critical listening in order to be accepted or rejected. Critical listening can be practiced while listening to a sales pitch.
Speakers must provide proof to back up their claims in order to be convincing. Listeners who pay close attention are wary of assertions and generalizations. When the speaker is not regarded as an authority on the subject of the speech, strong evidence is especially crucial.
Therefore, When communicating, speakers aim to achieve both broad and detailed goals. There are two main goals for speaking in college and beyond: to inform or to persuade. There is no clear distinction between the two; many talks will combine elements of both.
Learn more about reasoning from
https://brainly.com/question/25175983
#SPJ1
HELP!!!
To see the shortcuts on the ribbon in MS Word, hold down the _____ keys at the same time. A) CTRL & X B) Shift & Alt C) Shift & Delete D) CTRL & ALT
Answers
To see the shortcuts on the ribbon in MS Word, hold down the D) CTRL & ALT keys at the same time.
How can I display keyboard shortcuts in Word?When you hit Alt, tabs or Quick Access buttons on the ribbon display letters or KeyTips. To open ribbon tabs, use the keyboard shortcuts shown in this table. There may be more KeyTips visible depending on the tab you choose.
Therefore, Control+Alt+Delete is seen as the combination of the Ctrl key, the Alt key, and the Del key that a user can press simultaneously on a personal computer running the Microsoft Windows operating system to end an application task or restart the operating system.
Learn more about shortcuts keys from
https://brainly.com/question/28223521
#SPJ1
A rounded-down integer solution can result in a less than optimal solution to an integer programming problem. True False
Answers
Answer:
True, this is because rounding down an integer can cause the solution to be farther away from the optimal solution.
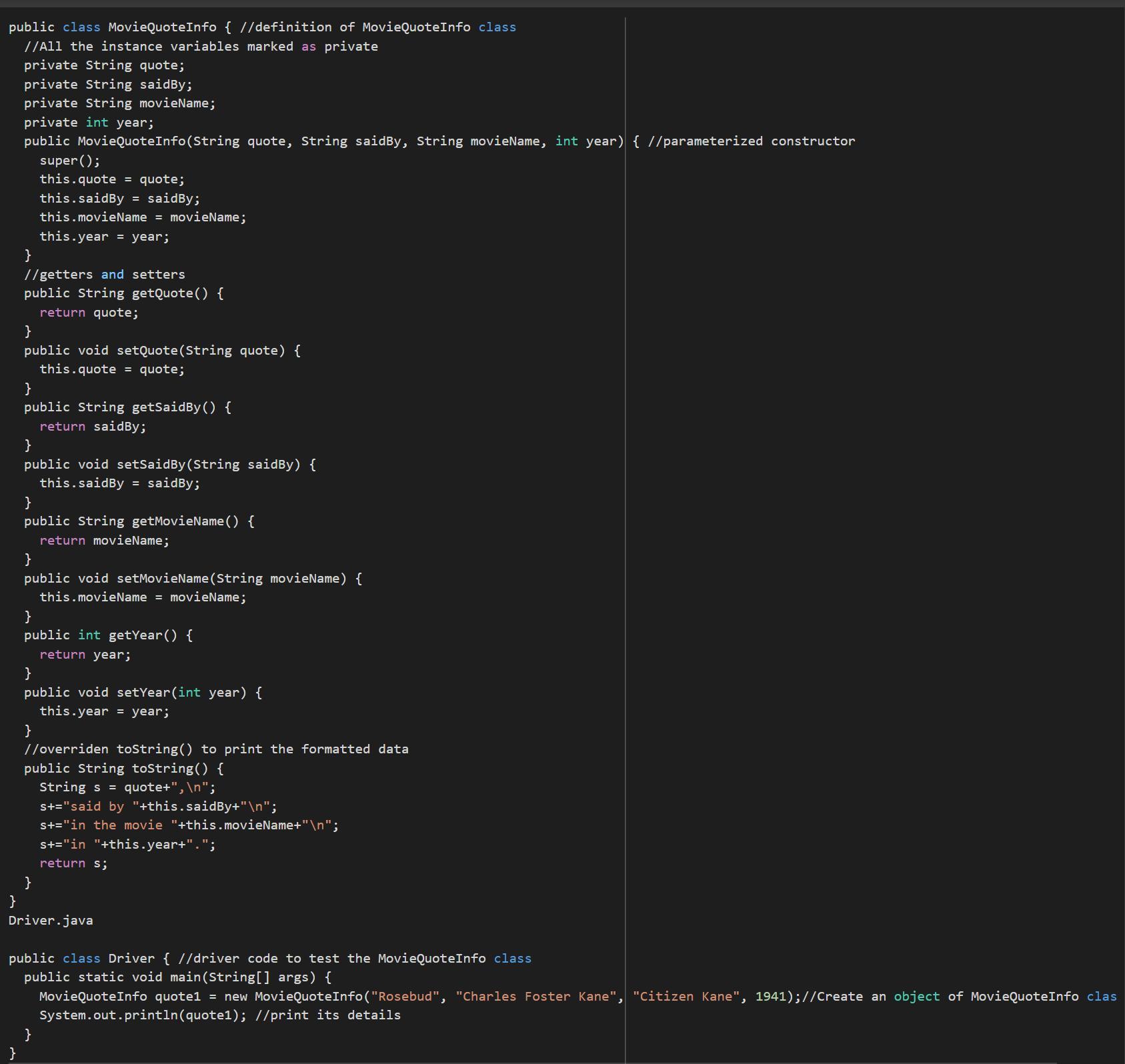
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
clicking either the date & time button or the ____ button opens the header & footer dialog box.
Answers
clicking either the date & time button or the slide button opens the header & footer dialog box.
What is a dialog box?
An informational and response-prompting graphical control element called a dialog box presents information to the user. Depending on whether they prevent communication with the software that opened the dialog, dialog boxes are categorized as "modal" or "modeless."
A dialog box is a transient window that a program creates to collect user input. Dialog boxes are frequently used in applications to ask users for more details about menu items.
To learn more about a dialog box, use the link given
https://brainly.com/question/23119185
#SPJ1
when does iron most likely to develop rust on it
Answers
What are some innovative research ideas for Onshore/Offshore hybrid wind turbines?
I was thinking whether it could be integrated with AI technologies, Pv Cells, thermoelectric plates, piezoelectric etc etc
please give me some inspirations
Answers
Some innovative research ideas for onshore/offshore hybrid wind turbines include integrating AI technologies for advanced control and optimization, incorporating PV cells for hybrid energy generation, utilizing thermoelectric plates for waste heat recovery, and exploring the potential of piezoelectric materials for vibration energy harvesting.
One innovative research idea is to integrate AI technologies into onshore/offshore hybrid wind turbines. AI algorithms can be used to optimize turbine performance by analyzing real-time data and making adjustments to maximize energy production and efficiency. AI can also enable predictive maintenance, allowing for proactive identification of potential issues and minimizing downtime.
Another idea is to incorporate photovoltaic (PV) cells into the hybrid wind turbines. By combining wind and solar energy generation, these turbines can generate power from both sources, maximizing energy output and improving the overall reliability and stability of the system.
Additionally, exploring the use of thermoelectric plates in hybrid wind turbines can enable the recovery of waste heat generated by the turbine. This waste heat can be converted into electricity, enhancing the overall energy efficiency of the system.
Furthermore, researchers can investigate the application of piezoelectric materials in hybrid wind turbines for vibration energy harvesting. These materials can convert mechanical vibrations caused by wind turbulence into electrical energy, supplementing the power output of the turbine.
These innovative research ideas highlight the potential for integrating AI technologies, PV cells, thermoelectric plates, and piezoelectric materials into onshore/offshore hybrid wind turbines to enhance their performance, energy generation capabilities, and efficiency.
Learn more about AI technologies here:
https://brainly.com/question/30089143
#SPJ11
Martha is typing on her computer. What type of communication is this? A. human-to-human B. human-to-machine C. machine-to-human D. machine-to-machine
Answers
Answer:
Human-to-machine
Explanation:
It is a human typing into a machine.
I hope this helped <3
help me please, thanks :)
will mark brainliest btw

Answers
benifits Ease of Access to Information. The World Wide Web, abbreviated as www has made the world a social village. Saves Time. Ease of Mobility. Better Communication Means. Cost Efficiency. Innovation In Many Fields. Improved Banking Better Learning Techniques.
risks Theft or manipulation of sensitive or private information, such as financial or health records.
Virulent computer viruses that can destroy data, damage hardware, cripple systems and disrupt a business' operations.
Computer fraud.
for (int j- 4; j > 0; j--)
for (int k 1; k < j; k+)
System.out.print (j +);
System.out . println() ;
What is output when the program runs?
a.
4444
b
4321
321
21
4444
333
22
1234
123
12
4321
432
43
Answers
Answer:
C is your awnser
Explanation:
The batteries on electric vehicles are recharged using electricity from either a wall socket or dedicated charging unit.
Answers
Answer:
true
Explanation:
Cost $45,000
Residual Value $5,000
Useful Life 5
Straight-line rate and DDB rate: calculate the rates. You should name cells so that these values can be used in calculations more conveniently.
Straight-line rate:
DDB rate:
Answers
To calculate the straight-line rate and the declining balance (DDB) rate, we are given the cost, residual value, and useful life of an asset. By assigning cell names to these values, we can conveniently use them in calculations. The straight-line rate represents the portion of the asset's cost that is depreciated each year using the straight-line method. The DDB rate represents the rate at which the asset's book value is reduced each year using the declining balance method.
To calculate the straight-line rate, divide the difference between the cost and residual value by the useful life. For example, if the cost is in cell A1, the residual value is in cell A2, and the useful life is in cell A3, the formula for the straight-line rate (cell A4) would be "= (A1 - A2) / A3".
To calculate the DDB rate, we need to determine the rate at which the asset's book value will decline each year. The DDB rate is typically twice the straight-line rate. Using the same cell references as above, the formula for the DDB rate (cell A5) would be "= 2 * A4".
By naming the cells with the given values (cost, residual value, and useful life), we can refer to these names in the formulas to make the calculations more convenient and easier to understand.
Once the formulas are entered, the straight-line rate and DDB rate will be calculated and displayed in their respective cells. These rates can then be used in further calculations related to depreciation or asset management.
Learn more about cells here:
https://brainly.com/question/33634987
#SPJ11
What refers to web-based and mobile based technologies that are used to turn communication into interactive dialogue between organizations, communities, and individuals
Answers
Answer:
Social Media
Explanation:
Social media can be regarded as computer-based technology that gives enablement for ideas as well as information sharing with the help of
virtual networks and communities. Social media depends on the uses of Internet. It should be noted that the Social Media technology refers to web-based and mobile based technologies that are used to turn communication into interactive dialogue between organizations, communities, and individuals.
Ha Yoon sees funny quotes on top of images frequently in her social media feed. One day, she has an idea for one of her own. Which of these websites would be most likely to help her create what she wants? Group of answer choices a PDF generator an infographic template a meme generator a digital image editor
Answers
Answer:
Digital Image Editor
Explanation:
Ha Yoon is not trying to create a meme, or a text document (PDF), so the answer must be Digital Image Editor.
Write a program that gets a list of integers from input, and outputs non-negative integers in ascending order (lowest to highest). Ex: If the input is: 10 -7 4 39 -6 12 2 the output is: 2 4 10 12 39
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int a[]={10,-7,4,39,-6,12,2};//defining single deminition array and assign value
int i,x,j,t; //defining integer variable
cout<<"Before sorting value: ";
for(i=0;i<7;i++) //using loop to print value
{
cout<<a[i]<<" ";//print value
}
cout<<endl <<"After sorting value: ";
for(i=0;i<7;i++)//defining loop to sort value
{
for(j=i+1;j<7;j++)//count array value
{
if(a[i]>a[j]) //defining condition to inter change value
{
//performing swapping
t=a[i]; //integer variable t assign array value
a[i]=a[j];//swapp value
a[j]=t;//assign value in array
}
}
}
for(i=0;i<7;i++) //defining loop to print value
{
if(a[i]>=0) //defining condition to check positive value
{
cout<<a[i]<<" ";//print value
}
}
return 0;
}
Output:
Before sorting value: 10 -7 4 39 -6 12 2
After sorting value: 2 4 10 12 39
Explanation:
Following are the description to the above code:
In the above program code, Inside the main method, an array a[] is declared that assign some value, and another integer variable "i, j, x, and t" is declared, in which variable "i and j" are used in the loop, and "x, t" is used to sort value.In the next step, three main for loop is declared, in which the first loop is used to print array value.In the second loop, inside another loop is used that sorts array values.In the last loop, a condition is defined, that check the positive value in the array and print its values.Answer:
integers=[]
while True:
number=int(input())
if number<0:
break
integers.append(number)
print("",min(integers))
print("",max(integers))
Explanation:
What element of a film helps determine its target audience?
A films ________ And subject address determines its target audience
Answers
Answer: I think the answer could be rating it makes the most since to me
Write a function called momentum that takes as inputs (1) the ticker symbol of a traded asset, (2) the starting month of the data series and (3) the last month of the data series. The function then uses the quantmod library to download monthly data from Yahoo finance. It then extracts the adjusted closing prices of that asset. And for this price sequence it calculates, and returns, the conditional probability that the change in price this month will be positive given that the change in price in the previous month was negative. Use this function to calculate these conditional probabilities for the SP500 index (ticker symbol ^gspc) and Proctor and Gamble (ticket symbol PG). Is there momentum in these assets?
Answers
Certainly! Here's an example of a function called `momentum` in Python that uses the `yfinance` library to download monthly data from Yahoo Finance and calculates the conditional probability of positive price change given a negative change in the previous month:
```python
import yfinance as yf
def momentum(ticker, start_month, end_month):
# Download monthly data from Yahoo Finance
data = yf.download(ticker, start=start_month, end=end_month, interval='1mo')
# Extract adjusted closing prices
prices = data['Adj Close']
# Calculate price changes
price_changes = prices.pct_change()
# Count occurrences of negative and positive changes
negative_changes = price_changes[price_changes < 0]
positive_changes = price_changes[price_changes > 0]
# Calculate conditional probability
conditional_prob = len(positive_changes[1:].loc[negative_changes[:-1].index]) / len(negative_changes[:-1])
return conditional_prob
# Example usage
sp500_momentum = momentum('^GSPC', '2000-01-01', '2023-06-30')
pg_momentum = momentum('PG', '2000-01-01', '2023-06-30')
print("SP500 Momentum:", sp500_momentum)
print("Proctor and Gamble Momentum:", pg_momentum)
```
By providing the ticker symbol, start month, and end month, the `momentum` function downloads the monthly data from Yahoo Finance, calculates the price changes, and then determines the conditional probability of a positive price change given a negative change in the previous month.
You can use this function to calculate the momentum for the SP500 index (ticker symbol '^GSPC') and Proctor and Gamble (ticker symbol 'PG'). The conditional probability indicates whether there is momentum in these assets. A higher conditional probability suggests a higher likelihood of positive price changes following negative price changes, indicating potential momentum.
Learn more about Yahoo Finance here:
https://brainly.com/question/33073614
#SPJ11
How is a game like Pokemon Go an example of Augmented reality
Answers
A game like Pokemon Go is an example of Augmented Reality (AR) because it combines the real world with virtual elements.
In the game, players use their mobile devices to locate and capture virtual creatures called Pokemon, which appear on the screen as if they are in the player's real-world location. This is achieved through the use of GPS technology and the device's camera, which overlays the virtual elements onto the real world.
As a result, players experience a seamless blend of the real and virtual worlds, which is the defining characteristic of Augmented Reality.
Learn more about Augmented reality:
https://brainly.com/question/22621708
#SPJ11
A game like Pokemon Go is an example of Augmented Reality (AR) because it combines the real world with virtual elements.
In the game, players use their mobile devices to locate and capture virtual creatures called Pokemon, which appear on the screen as if they are in the player's real-world location. This is achieved through the use of GPS technology and the device's camera, which overlays the virtual elements onto the real world.
As a result, players experience a seamless blend of the real and virtual worlds, which is the defining characteristic of Augmented Reality.
Learn more about Augmented reality:
brainly.com/question/22621708
#SPJ11