User is directed to a different or fake web-page than believed or intended. It is another type of browser attack. This Browser Attack Type is:
Answers
The type of browser attack which is characterized by a user being directed to a different or fake webpage than intended or believed is known as phishing.
A browser attack is an attack that targets weaknesses in web browsers and their components in order to infect or exploit a user's machine. Phishing is a type of browser attack in which cybercriminals create fake websites or emails that appear to be legitimate in order to obtain sensitive information like usernames, passwords, and financial information from victims. This type of attack is usually carried out through email or social media, and attackers can create convincing websites that appear to be legitimate by copying the design of reputable websites.
Learn more about browser attack:
brainly.com/question/23021587
#SPJ11
Related Questions
PLEASE HELP ME!!!!!! ITS FOR 100 POINTS AND BRAINLIEST!!!!!!!! NO ONE EVER WANTS TO ANSWER MY QUESTION!!! I JUST NEED SOMEONE TO EXPLAIN WHAT THEY'RE ASKING ME TO DO!!!!!!!!
Step 1: Read the Scenario
Because of the great work you’ve been doing for your department at running shoe company Runner Rush, your vice president has elected you to join an innovative cross-departmental team in your organization. The company is looking to launch a new shoe that enhances any runner’s speed. Management wants this new team to create an idea within a month. All the members of the team are alleviated of some of their regular job duties in order to join several meetings a week to brainstorm and design the new product.
Step 2: Develop a Month Plan
You have been appointed as the team leader. Develop a month plan that you will present to your teammates at the initial meeting. Focus on developing a strong team dynamic, setting goals, expectations, deadlines, and other elements that will lead the team to success. Make sure that your plan is easy to follow and clearly outlines all the required information.
Answers
Answer: my suggestion is to ask a teacher and do research like look up the best shoe companies and things like that
Explanation:
Your aunt owns a store and hired you to analyze the customers. You recorded the estimated ages of customers who shopped in the store and whether they made a purchase. Some of your data values are followed. What types of analysis could you do with this data? Select 4 options.

Answers
Answer:
-percentage of customers who made a purchase
-minimum age
-average age
-maximum age
Percentage of customers who made a purchase, minimum age, average age and maximum age are the types of analysis could you do with this data. Hence, option A, B, C and E are correct.
What is data values?A data value is the material that fills the space of a record. For instance, one of the database's numerous data fields might contain a number that indicates the weight of a certain integer.
Data, such as statistics, phone numbers, or inventory counts, are undoubtedly pieces of information that a person would understand as numbers.
Data provides useful information that enhances business decisions. This information is the result of an effective data analytics strategy. Businesses may create a data culture far more easily because of the monetary worth of data.
Thus, option A, B, C and E are correct.
For more information about data values, click here:
https://brainly.com/question/16612044
#SPJ2
In what ways can you sort data by using the sort procedure? Check all that apply.
sort ascending
sort descending
sort diagonal
sort by font color
sort by background color
sort by rows
sort by columns
Answers
Answer:
all except c:)
Explanation:
Answer:
1,2,4,5,6,7
Explanation:
all except C
Which of the following are true when comparing TCP/IP to the OSI Reference Model? (Choose two.)
A. The TCP/IP model has seven layers, while the OSI model has only four layers.
B. The TCP/IP model has four layers, while the OSI model has seven layers.
C. The TCP/IP Application layer maps to the Application, Session, and Presentation layers of the OSI Reference Model.
D. The TCP/IP Application layer is virtually identical to the OSI Application layer.
Answers
Two true comparisons between TCP/IP and OSI Reference Model are as follows:A. The TCP/IP model has seven layers, while the OSI model has only four layers.B. The TCP/IP model has four layers, while the OSI model has seven layers.
The seven-layer OSI (Open System Interconnection) model and the four-layer TCP/IP (Transmission Control Protocol/Internet Protocol) model are two networking models. OSI is a theoretical model that was created in the late 1970s by the International Organization for Standardization (ISO).In comparison, TCP/IP is a practical implementation that has been implemented and used since the late 1970s.
The OSI reference model is more thorough and sophisticated than the TCP/IP model. However, the TCP/IP protocol suite is more adaptable and, as a result, has become the de facto standard for networking. In reality, TCP/IP is a more practical and widespread protocol than OSI.
To know more about comparisons visit:
https://brainly.com/question/25799464
#SPJ11
What two documents describe the purpose of the optask link?
Answers
The two documents describe the purpose of the optask link are:
MTAMTNWhat is responsible for promulgating the Optask link message?The agency that is known to be assigned the role to promulgate the OPTASK LINK is known to be MTA which is said to be the physical configuration.
The MTA is known to be one that contains the physical configuration, functional organization, and also all of the operational methods used in the set up , establishment, changes, and operation of Multi-TDL Networks. The MTA is said to be the physical linkages and equipment of the MTN.
Hence, the two documents describe the purpose of the optask link are:
The MTAThe MTNLearn more about MTA from
https://brainly.com/question/24131225
#SPJ1
Consider sending a stream of packets from host a to host b using ipsec. typically, a new sa will be established for each packet sent in the stream. true or false
Answers
Consider sending a stream of packets from Host A to Host B using Ipsec. Typically, a new SA will be established for each packet sent in the stream. True or False? Tweet Answer FALSE. REASON: Ipsec SA is first connect with Host A and Host B. So, all packets in the stream use the new SA.
Need answer ASAP
In which phrase does software coding and testing happen in the spiral model?
The spiral model does not have a separate testing phase. Both software coding and testing occurs during the _____ phase.
Answers
both software coding and testing occurs during Engineering phase
!WILL GIVE BRAINLIEST!
Write a Python program that prompts the user for a word. If the word comes between the words apple
and pear alphabetically, print a message that tells the user that the word is valid, otherwise, tell
the user the word is out of range.
Answers
Answer:
word = input()
if word > "apple" and word < "pear":
print("Word is valid.")
else:
print("Word is out of range.")
What gift will a customer who orders the book Shortest Poems receive? Use the actual book retail value to determine the gift.
The SQL statement with the traditional approach
Query:
SELECT p.gift FROM books, promotion p WHERE retail BETWEEN minretail AND maxretail AND title = 'SHORTEST POEMS';
Sample Output:
GIFT
---------------
BOOK COVER
The WHERE clause is used to specify the conditions and filters the records in a SQL (Structured Query Language) statement.
Answers
To determine the gift that a customer who orders the book Shortest Poems will receive based on the actual book retail value, the following SQL statement with a traditional approach can be used:
Query:SELECT p.gift FROM books, promotion p WHERE retail BETWEEN minretail AND maxretail AND title = 'SHORTEST POEMS';Sample Output:GIFT---------------BOOK COVER.
In this SQL statement, the WHERE clause is used to specify the conditions and filters the records. In this case, it filters the records by selecting the promotion gift based on the book's retail value that falls between the minimum and maximum retail values specified in the promotion table. The book title is also specified to be 'SHORTEST POEMS'.
The sample output shows that the gift that the customer who orders the book Shortest Poems will receive is a book cover.
To know more about SQL statement, click here:
https://brainly.com/question/30364070
#SPJ11
windows 11 has 3 accessibility categories, what are they?
Answers
Windows 11 has 3 accessibility categories Vision., Hearing., Mobility disabilities easier to find and use, making it one of the most accessible operating systems available.
Windows 11 makes accessibility tools for people with vision, hearing, and mobility disabilities easier to find and use, making it one of the most accessible operating systems available. Although PC hardware is nice, it is of little use without cutting-edge software.
What's coming to Windows 11 accessibility?Voice access, which lets users control most of the operating system with their voice, is another new feature in the Windows 11 2022 Update. Without having to move your hands, you can open and close apps, navigate text, click things, press keyboard keys, and more with this.
What exactly are access permissions?Android Accessibility Services was made to help app developers make their apps more accessible to people with disabilities and to help them overcome the obstacles they face when using smartphones. To take advantage of these advantages, users must enable "Accessibility Permissions" when downloading these apps.
Learn more about windows 11 :
brainly.com/question/30613269
#SPJ4
Which of these are considered I/O devices? Check all that apply.
Answers
Answer:
Hard disk drives; Any devices that receive input or send out output are considered I/O devices. I/O devices such as speakers, web cams, and monitors.
Explanation:
The hardware used to interact with a machine by a human operator or other systems is an input/output device. As the name implies, input/output devices have the ability to provide data that is output to a computer and receive data that is input from a computer.
A hard drive is a need for all computers; they would not work without one. These days, the majority of computers contain input/output devices like a CD-RW or DVD-RW drive, a network card, and a sound card or inbuilt sound on the motherboard.
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
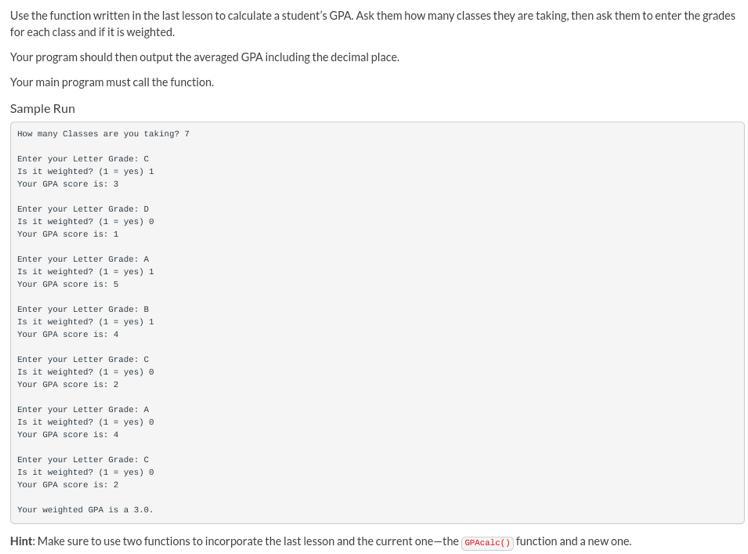
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
How do I convert BCD to denary and denary to BCD? (For Both positive and Negative integer of denary)
Answers
Answer:
BCD is very similar to regular binary code. Decimal digits are represented as binary like so:
0 = 0000
1 = 0001
2 = 0010
3 = 0011
etc...
9 = 1001
However, in BCD the structure of decimal code is maintained, so e.g., the number 123 would be encoded digit-by-digit as:
0001 0010 0011
whereas in pure binary it would be encoded as
01111011
So you immediately see that BCD is not so efficient. That's why it is not used very often. Encoding and decoding is very easy as you take the same approach as with pure binary, but perform it per digit (ie., per group of 4 bits).
you manage a notebook system running windows. which task can you perform to log all packets that are dropped by the firewall on your computer?you manage a notebook system running windows. which task can you perform to log all packets that are dropped by the firewall on your computer?
Answers
To log all packets that are dropped by the firewall on your computer, you can perform the task of enabling logging in Windows Firewall. This will create a log file containing details of all packets that are dropped by the firewall.
What is Windows Firewall?
Windows Firewall is a security application that comes pre-installed with the Windows operating system. It is designed to protect the system from unauthorized access by blocking incoming network traffic. It is also capable of logging all incoming and outgoing network traffic, including the packets that are dropped by the firewall. Enabling logging in Windows Firewall
Here are the steps to enable logging in Windows Firewall:
1. Press the Windows key + R to open the Run dialog box.
2. Type wf.msc and press Enter to open the Windows Firewall with Advanced Security window.
3. Click on the Properties link located on the right side of the screen.
4. Click on the Advanced tab.
5. Under the Logging section, click on Customize.
6. Select Yes in the Log dropped packets drop-down menu.
7. Select the log file location, log file name, and maximum size of the log file.
8. Click on OK to save the changes.
9. Close the Windows Firewall with Advanced Security window.
10. Now, Windows Firewall will log all dropped packets to the specified log file location.
Learn more about Windows Firewall:https://brainly.com/question/10431064
#SPJ11
how can a search be narrowed to only search a particular website????
plzzzzzzzzzzzz ill give brainliest
Answers
Answer:
There are a variety of ways to narrow down your search results in a library database. The two most direct ways are to focus your search with more specific keywords and/or to limit by various criteria before or after searching. The more specific you are with your search terms, the more relevant your results will be
Hope it helped!!!
Which office setup would be difficult to host on a LAN?
hardware.
RAM.
storage.
software.
Answers
The office setup would be difficult to host on a LAN is option C: storage.
What is the office LAN setup like?A local area network (LAN) is a network made up of a number of computers that are connected in a certain area. TCP/IP ethernet or Wi-Fi is used in a LAN to link the computers to one another. A LAN is typically only used by one particular establishment, like a school, office, group, or church.
Therefore, LANs are frequently used in offices to give internal staff members shared access to servers or printers that are linked to the network.
Learn more about LAN from
https://brainly.com/question/8118353
#SPJ1
Which of the following applies to a trademark?
o belongs to just one company or organization
O always shown on the outside of a garment
O a way for people to copy a pattern
0 a mark that represents a product's "sold"
status
Answers
Answer:
a
Explanation:
Answer:
belongs to just one company or organization
Explanation:
edge 2021
Describe how each command is used by matching the command to its purpose.
removes data fror
places it on the cli
Paste
cancels a previou
Undo
restores a previou
Copy
duplicates data a
clipboard
Cut
Redo
places data in its
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
The correct command matches its use are given below:
Paste Places data in its
Undo Cancel a previous
Copy Duplicates data on the clipboard
Cut Removes data for places it on the clipboard
Redo restores a previous
Paste term is used when you are placing copied data. Undo is used to cancel a previous action performed while Redo is used to restores a previously performed action. The copy is used to duplicate data on the clipboard while Cut is used to removes data for places/ to paste somewhere else.
Who did Connie Macpherson think her visitor was?
Answers
Connie Macpherson thought that her visitor was her husband,Jim!
I hope it will helps you!
one security component that doubles as a network component
Answers
Answer:
is the sentence above the question?
Answer:
It is to enter the site and then it will protect you in terms of form and appearance, and so on as required
I request that it is done in C++. Giving 100 points. To find the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
Sample Output:
Enter Amount: 489.98
The number of 100 dollar bills: 4
The number of 20 dollar bills: 4
The number of 10 dollar bills: 0
The number of 5 dollar bills: 1
The number of 1 dollar bills: 4
The number of Quarters: 3
The number of Dimes: 2
The number of Nickels: 0
The number of Pennies: 3
I have this so far.(look at attachment)
Answers
A program that finds the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
The Program#include<iostream>
using namespace std;
int main () {
double bill=0.0, twenty=0.0, ten=0.0, five=0.0, one=0.0, quarter=0.0, dime=0.0, nickel=0.0, penny=0.0, payment=0.0, cashBack=0.0;
// We need to gather a value for the bill.
while (bill==0) {
cout << "Please enter the amount of the bill (ex. $15.67): \n";
cin >> bill;
cout << "Your bill is "<< bill << ".\n";
}
do {
cout << "Please pay for bill by entering \nthe count of each dollar bill denomination and coin denomination.\n";
// Gathers an amount for each denomination and then gives it a value equal to its monetary value.
cout << "\nTwenty dollar bills:"; cin >> twenty;
twenty *= 20.00;
cout << "\nTen dollar bills:"; cin >> ten;
ten *= 10.00;
cout << "\nFive dollar bills:"; cin >> five;
five *= 5.00;
cout << "\nOne dollar bills:"; cin >> one;
one *= 1.00;
cout << "\nQuarters:"; cin >> quarter;
quarter *= .25;
cout << "\nDimes:"; cin << dime;
dime *= .10;
cout << "\nNickels:"; cin >> nickel;
nickel *= .05;
cout << "\nPennies:"; cin >> penny;
penny *= .01;
// Add the money together and assign the value to payment.
payment = twenty + ten + five + one + quarter + dime + nickel + penny;
cout << "\nYour payment totals: $" << payment << "\n";
if (payment < bill) {
cout << "\nYou didn't pay enough money to cover the bill. \nPlease re-enter your amount.\n";
// If payment isn't greater than bill then they're asked to reenter their money.
}
// Determine the amount of cash to give back and assign the value to cashBack.
cashBack = payment - bill;
} while (cashBack <= 0);
cout << "\nI owe you $" << cashBack <<"\n";
// Reset the values of each denomination to 0
twenty = 0;
ten = 0;
five = 0;
one = 0;
quarter = 0;
dime = 0;
nickel = 0;
penny = 0;
// These while loops will subtract the monetary value from cashBack and add a value of 1 each time it is looped.
while (cashBack >= 20) {
cashBack -= 20;
twenty += 1;
}
while (cashBack >= 10) {
cashBack -= 10;
ten += 1;
}
while (cashBack >= 5) {
cashBack -= 5;
five += 1;
}
while (cashBack >= 1) {
cashBack -= 1;
one += 1;
}
while (cashBack >= .25) {
cashBack -= .25;
quarter += 1;
}
while (cashBack >= .10) {
cashBack -= .10;
dime += 1;
}
while (cashBack >= .05) {
cashBack -= .05;
dime += 1;
}
while (cashBack >= .01) {
cashBack -= .01;
penny += 1;
}
// For each denomination that has a value greater than 0, the person is payed back the amount.
if (twenty > 0) {
cout << "\n" << twenty << " Twenty dollar bills.\n";
}
if (ten > 0) {
cout << "\n" << ten << " Ten dollar bills.\n";
}
if (five > 0) {
cout << "\n" << five << " Five dollar bills.\n";
}
if (one > 0) {
cout << "\n" << one << " One dollar bills.\n";
}
if (quarter > 0) {
cout << "\n" << quarter << " Quarters.\n";
}
if (dime > 0) {
cout << "\n" << dime << " Dimes.\n";
}
if (nickel > 0) {
cout << "\n" << nickel << " Nickels.\n";
}
if (penny > 0) {
cout << "\n" << penny << " Pennies.\n";
}
}
Read more about C++ programming here:
https://brainly.com/question/20339175
#SPJ1
which type of computer is used in plane
Answers
Answer:
Such airborne systems are usually bespoke software, but the following systems are known to be used in some airplanes: WindRiver 's VxWorks (see Aerospace & Defense uses), QNX (actually not sure if QNX is used in airplanes, but it's used in ground control systems)
Explanation:
Answer: A flight computer is a form of circular slide rule used in aviation and one of a very few analog computers in widespread use in the 21st century. Sometimes it is called by the make or model name like E6B, CR, CRP-5 or in German, as the Dreieckrechner.
Marsha found her sister's diary that listed all of her passwords. However, it wasn't listed for which s the passwords were used. She tried each password listed until she was able to log into her sister's computer. What method of code-breaking did Marsha use?
Answers
Answer:
Brute Force
Explanation:
Brute Force - a method of hacking were the attacker submits many combination of attempts in hope of getting into the system eventually.
I'm having trouble changing my google account password
I tried to contact Google account recovery for can't change my password I tried to verify Google with my phone I used phone password and my fingerprint to let google verify me and keep making same pages both ways didn't work but I really need this account well its actually my school account and I keep reveive this message:contact your domain for your help and only option had is learn more or go back
only way to fix this problem is create account ,contact google account recovery ,delete my school account but deleting my school account requires to enter my google account password what should I do please help me !!!!!!
Answers
contact your school and see what they can do
(B) PStudio File Edit Code View Plots Session Build Debug Profile Took Help - Addins. (3) Untitled1* 60 makecov × 49 #Create and execute an R function to generate a covariance matrix. 50 rho <−0.5 51n<−5 52 - makecov <- function (rho,n){ 53 m< matrix ( nrow =n,nco⌉=n)I H we are returning a matrix of 54m<− ifelse(row (m)==col(m),1, rho ) 55 return (m) 56−3 57m= makecov (rho,n) 58 m 53.43 In makecov(rho, n) = Console Terminal × Background Jobs x
Answers
The code provided is incomplete and contains some syntax errors. Here is the corrected version of the code:
R
makecov <- function(rho, n) {
m <- matrix(nrow = n, ncol = n)
for (i in 1:n) {
for (j in 1:n) {
if (i == j) {
m[i, j] <- 1
} else {
m[i, j] <- rho
}
}
}
return(m)
}
rho <- -0.5
n <- 5
m <- makecov(rho, n)
m
This code defines a function makecov that takes two arguments rho and n to generate a covariance matrix. The function creates an n x n matrix m and sets the diagonal elements to 1 and the off-diagonal elements to rho. Finally, it returns the generated covariance matrix m.
The code then assigns values to rho and n variables and calls the makecov function with these values. The resulting covariance matrix m is printed to the console.
To know more about syntax errors
https://brainly.com/question/32567012
#SPJ11
a computer has power, but there are no beeps and the computer does not boot. which of the following would be the MOST LIKELY cause?
a. no operating system installed
b. CPU failure
c. outdated bios
d. hard drive failure
HELP!!
Answers
Answer:
CPU failure
Explanation:
CPU is what runs the computer which if the CPU is broken the computer will not start
A computer has power, but there are no beeps and the computer does not boot. The most likely cause is CPU failure. Thus the correct option is B.
What is Computer?A computer is an electronic device used to perform arithmetic and logical operations within seconds accurately without causing any error and make ease people's life.
A CPU is referred to as the central processing unit of a computer which plays a significant role in its functions and operations. It helps to convert the data by processing it into output for humans.
When the computer has power but there is no beep its means that there is a problem in the power supply unit which reflects a disruption in the power supply and causes the failure of the CPU.
Therefore, option B CPU failure is appropriate.
Learn more about CPU, here:
https://brainly.com/question/16254036
#SPJ6
Can someone tell me why I turn my mix on everyday and today I turned my computer on, put my headphones on and my mix started playing...
Answers
Answer:
LOL FELT THAT
Explanation:
Answer:
must have been a lucky day
Explanation
slide view definiton
Answers
Answer:
huh
Explanation:
Which encryption protocol does gre use to increase the security of its transmissions?
Answers
The encryption protocol to increase the security of its transmissions is to use IPsec for security when transmitting. The correct option is c.
What is encryption protocol?Encryption is done by the encryption algorithm. Thews algorithms for encryption are used to perform encryption. These algorithms perform all cryptographic operations on the plaintext data while utilizing the encryption key.
Then, in encryption protocols, these techniques are applied to safeguard data for a variety of purposes.
Thus, the correct option is c. IPsec regarding the encryption protocol to increase security.
To learn more about encryption protocol, refer to the link:
https://brainly.com/question/14635177
#SPJ4
The question is incomplete. Your most probably complete question is given below:
a. SSL b. SFTP c. IPsec d. SSH.
Technological advances have led to worldwide increased ______.
a.
Job security
b.
Economic stability
c.
Communicative ability
d.
Military Security
Answers
Answer:
C
Explanation:
Answer:
C.
Communicative ability