The Python "SyntaxError: leading zeros in decimal integer literals are not permitted" occurs when we declare an integer with leading zeros. To solve the error, remove any leading zeros from the integer or wrap the value in a string.
Answers
To remove the error, one way is to remove any leading zeros from the integer and other way is to wrap the value in a string.
How to remove any leading zeros?lets take an example
SyntaxError: leading zeros in decimal integer literals are not permitted; use an ∅o prefix for octal integers
my_num = 08
my_num = 8
print(my_num) # ️ 8
How to wrap the value in a string?lets take an example
SyntaxError: leading zeros in decimal integer literals are not permitted; use an ∅o prefix for octal integers
my_num = 08
my_num = '08'
print(my_num) # ️ '08'
to know more about Syntax Error, visit
https://brainly.com/question/29883846
#SPJ4
Related Questions
What is the practical application of science to enhance mankind’s problem solving ability
Answers
Answer:
Science is concerned about aggregating and understanding perceptions of the physical world.
Explanation:
Science is concerned about aggregating and understanding perceptions of the physical world. That seeing alone takes care of no issues. Distinctive individuals need to follow up on that comprehension for it to help take care of issues. For example, science has discovered that ordinary exercise can bring down your danger of coronary illness.
A __________ is the blueprint for __________ having similar attributes and behaviors. signature, objects class, parameters header, objects signature, parameters class, objects
Answers
Answer: E. class, objects
Explanation:
A class is the blueprint for objects having similar attributes.
As much as classifying something means to define it based on the characteristics that is has that are similar to other things in that class, so also is a class here.
A class is the blueprint or rather template for making objects that have similar attributes which means that the class therefore gives the object its various attributes and its behavior.
What are some methods of cyber bullying ?
Answers
Answer:
HARASSMENT
IMPERSONATION
INAPPROPRIATE PHOTOGRAPHS
WEBSITE CREATION
VIDEO SHAMING
Software that is decided to intentionally causing harm to a device, server, or network is 
a. Outware
b. Loggerware
c. Attackware
d. Malware
Answers
It's D, so it's Malware
_ is unsolicited junk mail. It can overcrowd your mailbox and deliver malware.
PLEASE HELP ASAP!!
Answers
Answer:
Spam
Explanation:
Spam has been a long term issue with technology, it is unsolicited and can overfill your mailbox. It is called spam because you receive much of it.
3. All of the following are control methods for HVAC systems except:
OA. Cables
OB. Electronics
OC. Hydraulics
OD. Vacuum
Answers
All of the following are control methods for HVAC systems except D. Vacuum
What is the HVAC systems?Cables, hardware, and hydrodynamics are all commonly utilized control strategies for HVAC (warming, ventilation, and discuss conditioning) frameworks. Cables can be utilized to associate sensors and actuators to a control board, whereas hardware can incorporate chip and advanced controllers that mechanize HVAC frameworks.
Therefore, Power through pressure can be utilized to control the stream of liquids in heating and cooling frameworks. In any case, vacuum isn't a control strategy utilized in HVAC frameworks.
Learn more about HVAC systems from
https://brainly.com/question/23989909
#SPJ1
∀פפIN∀W∀ qwda dawdawdawdawd
BAN ME NOW
Answers
Answer:
why
Explanation:
Write a program HousingCost.java to calculate the amount of money a person would pay in renting an apartment over a period of time. Assume the current rent cost is $2,000 a month, it would increase 4% per year. There is also utility fee between $600 and $1500 per year. For the purpose of the calculation, the utility will be a random number between $600 and $1500.
1. Print out projected the yearly cost for the next 5 years and the grand total cost over the 5 years.
2. Determine the number of years in the future where the total cost per year is over $40,000 (Use the appropriate loop structure to solve this. Do not use break.)
Answers
Answer:
import java.util.Random;
public class HousingCost {
public static void main(String[] args) {
int currentRent = 2000;
double rentIncreaseRate = 1.04;
int utilityFeeLowerBound = 600;
int utilityFeeUpperBound = 1500;
int years = 5;
int totalCost = 0;
System.out.println("Year\tRent\tUtility\tTotal");
for (int year = 1; year <= years; year++) {
int utilityFee = getRandomUtilityFee(utilityFeeLowerBound, utilityFeeUpperBound);
int rent = (int) (currentRent * Math.pow(rentIncreaseRate, year - 1));
int yearlyCost = rent * 12 + utilityFee;
totalCost += yearlyCost;
System.out.println(year + "\t$" + rent + "\t$" + utilityFee + "\t$" + yearlyCost);
}
System.out.println("\nTotal cost over " + years + " years: $" + totalCost);
int futureYears = 0;
int totalCostPerYear;
do {
futureYears++;
totalCostPerYear = (int) (currentRent * 12 * Math.pow(rentIncreaseRate, futureYears - 1)) + getRandomUtilityFee(utilityFeeLowerBound, utilityFeeUpperBound);
} while (totalCostPerYear <= 40000);
System.out.println("Number of years in the future where the total cost per year is over $40,000: " + futureYears);
}
private static int getRandomUtilityFee(int lowerBound, int upperBound) {
Random random = new Random();
return random.nextInt(upperBound - lowerBound + 1) + lowerBound;
}
}
Please Complete in Java a. Create a class named Book that has 5 fields variables: a stock number, author, title, price, and number of pages for a book. For each field variable create methods to get and set methods. b. Design an application that declares two Book objects. For each object set 2 field variables and print 2 field values. c. Design an application that declares an array of 10 Books. Prompt the user to set all field variables for each Book object in the array, and then print all the values.
Answers
Answer:
Explanation:
The following code is written in Java. I created both versions of the program that was described in the question. The outputs can be seen in the attached images below. Both versions are attached as txt files below as well.


user intent refers to what the user was trying to accomplish by issuing the query
Answers
Answer:
: User intent is a major factor in search engine optimisation and conversation optimisation. Most of them talk about customer intent ,however is focused on SEO not CRO
Explanation:
the are the uncontrollable faces outside the business industry .
Answers
Answer:
The uncontrollable risk factors are the details that affect the product that a company has no way of changing. These include political and economic climates, competitor choices and even the weather.
Explanation:
Many real world problems that we encounter including Information Systems problems are wicked in nature. The following statements are TRUE of the wickedness of these problems EXCEPT….
Answers
They have clear avenues for solutions that are simple to identify. Wicked problems lack precise problem descriptions, making them ambiguous, complex, and challenging to resolve.
What are some instances of wicked dilemmas in real life?Some of the most difficult and intricate problems of our time—many of which endanger human health—are referred to as "wicked." Examples of such wicked challenges include climate change, biodiversity loss, persistent poverty, the growing obesity pandemic, and food insecurity.
What constitutes a wicked example?adjective a cruel and evil deed In the play, she took on the role of the evil stepmother. After winning, she grinned viciously. Her caustic sense of humour is well recognised. She was a bad case.
To know more about Wicked problems visit:-
https://brainly.com/question/29854616
#SPJ1
Question:
Many real-world problems that we encounter, including Information Systems problems, are wicked in nature. The following statements are TRUE of the wickedness of these problems EXCEPT:
a) They have unclear problem definitions and no definitive solutions.
b) They have multiple and changing constraints.
c) They have well-defined solution paths that can be easily determined.
d) They require a unique approach to every problem instance.
An argument does not always have to be made in words. A piece of music
can make an argument; however, the argument is usually a(n)
one.
A. unfocused
B. emotional
C. credible
D. logical
Answers
Answer:
B. emotional
Explanation:
An emotional argument. An argument does not always have to be made in words.
The piece of music that can make an argument is usually an emotional argument. Thus option B is correct.
What is an emotional argument?An emotional argument is an e that is made in words and expresses its deals in terms of feelings and thoughts. The emotional argument is characterized by the manipulation of the recipient's emotions and has an absence of factual evidence.
Find out more information about the argument.
brainly.com/question/3775579
F(x) = -x^3-x
Is this function odd?
Answers
Answer:
yes it is odd beacuse 3 is a odd number
it's a odd function
Explanation:
a function is even if its F(-X) r F (x) and a function
is odd if its F(-X)= -F(x).
We have F(x)=x^3 - x and F (- x) = (-x)^3 - (-x)= -x^3
+ x = -(x^3 - x) = -F (x)
sorry if its confusing but it's an odd function ♡
A shot made while running is a ____________.
Answers
Answer:
A shot made while running is called a layup.
why computer is now considered a commodity.
Answers
Answer:
Computers are considered commodities because they are relatively easy to produce and there is a lot of competition in the market. This means that prices are relatively low and there is not a lot of differentiation between products.
Explanation:
Hope this helps!
what are the uses of navigation keys
Answers
We can sell the Acrobat Reader software to the other users”. Do you agree with this statement? Justify your answer.
Answers
No, as a User, one CANOT sell Acrobat Reader software to the other users.
What is Adobe Reader?Acrobat Reader is a software developed by Adobe and is generally available as a free PDF viewer.
While individuals can use Acrobat Reader for free,selling the software itself would be in violation of Adobe's terms of use and licensing agreements.
Therefore, selling Acrobat Reader to other users would not be legally permissible or aligned with Adobe's distribution model.
Learn more about Adobe Reader at:
https://brainly.com/question/12150428
#SPJ1
The process of providing only the essentials and hiding the details is known as _____. a. algorithm b. data structure c. abstraction d. optimization
Answers
Hope it helped (:
The process of providing only the essentials and hiding the details is known as abstraction.
What is abstraction?Abstraction in its main sense is a conceptual process wherein general rules and concepts are derived from the usage and classification of specific examples, literal ("real" or "concrete") signifiers, first principles, or other methods.
"An abstraction" is the outcome of this process—a concept that acts as a common noun for all subordinate concepts and connects any related concepts as a group, field, or category.
Conceptual abstractions may be formed by filtering the information content of a concept or an observable phenomenon, selecting only those aspects which are relevant for a particular purpose. For example, abstracting a leather soccer ball to the more general idea of a ball selects only the information on general ball attributes and behavior.
Therefore, The process of providing only the essentials and hiding the details is known as abstraction.
To learn more about abstraction, refer to the link:
https://brainly.com/question/23774067
#SPJ5
PLEASE ANSWER QUCIK 100 POINTS AND BRAINLIEST TO WHOEVER IS CORRECT
The models below represent nuclear reactions. The atoms on the left of the equal sign are present before the reaction, and the atoms on the right of the equal sign are produced after the reaction.
Model 1: Atom 1 + Atom 2 = Atom 3 + energy
Model 2: Atom 4 = Atom 5 + Atom 6 + energy
Which of these statements is most likely correct about the two models?
Both models show reactions which use up energy in the sun.
Both models show reactions which produce energy in the sun.
Model 1 shows reactions in the sun and Model 2 shows reactions in the nuclear power plants.
Model 1 shows reactions in the nuclear power plants and Model 2 shows reactions in the sun.
Answers
Answer:
Both models show reactions which produce energy in the sun.
Model 1 represents a nuclear fusion reaction, which occurs in the sun. During fusion, two lighter atomic nuclei combine to form a heavier nucleus, releasing a significant amount of energy in the process.
Model 2 represents a nuclear fission reaction, which can also occur in the sun but is less common. In fission, a heavier atomic nucleus splits into two or more smaller nuclei, also releasing energy.
Both reactions result in the release of energy, which contributes to the sun's overall energy production. However, it's worth noting that nuclear fission is the primary reaction type used in nuclear power plants on Earth.
Explanation:
Which of the following is not a concern when storing sensitive files in cloud storage?
Answers
A statement which is not a concern when storing sensitive files in cloud storage is: C. automatic scaling of services.
What is cloud computing?Cloud computing can be defined as a type of computing service that requires the use of shared computing resources (files) over the Internet, rather than the use of local servers and hard drives.
In Computer technology, some examples of shared computing resources (files) on a cloud storage service include the following:
Computer power.Software programs (applications).Cloud storage (data storage).Network (web) servers.In conclusion, we can reasonably infer and logically deduce that a factor which should not be considered when storing sensitive files in cloud storage is an automatic scaling of services because the amount of computational resource does not have to be adjusted.
Read more on cloud computing here: brainly.com/question/17247526
#SPJ1
Complete Question:
Which of the following is not a concern when storing sensitive files in cloud storage?
Access to data during an outage
Compliance with state and federal laws
Automatic scaling of services
Third party access to data
Your company has been assigned the 194.10.0.0/24 network for use at one of its sites. You need to calculate a subnet mask that will accommodate 60 hosts per subnet while maximizing the number of available subnets. What subnet mask will you use in CIDR notation?
Answers
To accommodate 60 hosts per subnet while maximizing the number of available subnets, we need to use a subnet mask that provides enough host bits and subnet bits.
How to calculateTo calculate the subnet mask, we determine the number of host bits required to accommodate 60 hosts: 2^6 = 64. Therefore, we need 6 host bits.
Subsequently, we determine the optimal quantity of subnet bits needed to increase the quantity of accessible subnets: the formula 2^n >= the amount of subnets is used. To account for multiple subnets, the value of n is set to 2, resulting in a total of 4 subnets.
Therefore, we need 2 subnet bits.
Combining the host bits (6) and subnet bits (2), we get a subnet mask of /28 in CIDR notation.
Read more about subnet mask here:
https://brainly.com/question/28390252
#SPJ1
Mission statement base on shoes company ? Help me
Answers
Here are 2 examples:
- Bringing comfortable walking, running, biking, and adventuring to the world.
- Transforming the way you live your life, two soles at a time.
A mission statement should be focused on what a company is about at its core roots. What's the driver for why the company does what it does? Often it is related to why a company is relevant in its industry.
In a Microsoft office application what is the item at the top that contains most of the commands used to perform task in application
Answers
Answer:
home tab
Explanation:
hope this helps :D
Research is much concerned with proper fact finding, analysis and evaluation.” Do you agree with this statement? Give reasons in support of your answer.
Answers
Answer:
Yes, I agree.
Explanation:
Research is basically trying to find out new ways of doing things or challenging an already established claim or theory, with the aim of disproving or improving on it.
So, research is much concerned with proper fact-finding, which would ensure that the results and samples are accurate, analysis and evaluation which would make sure that the new data gotten is properly investigated.
I agree that Research is much concerned with proper fact finding, analysis because research increases the stock of knowledge and requires different analysis and facts base on past research.
What is Research?Research can be regarded as reactive and systematic work which is been carried out to bring about improvement in knowledge of the reseacher.
In research, findings needs to be done, it could requires experiments and field work, evaluation of the results is also needed to compare with past results of the past scholars.
Learn more about Research at:
https://brainly.com/question/968894
Katie needs to apply styles to titles and headings in a document that she has created. What is the easiest way to do this? O Create a custom style. O Manually format the headings and titles. O Use the Quick Styles Gallery. O none of the above
Answers
Answer:
Use the quick styles gallery
Explanation:
quizlet told me
The easiest way for Katie to apply styles to titles and headings in a document that she has created is to use the quick styles gallery.
What is a Quick Styles gallery?In a Word application, the Quick Styles gallery is used to provides a useful one-click method of applying a style.
Hence, the easiest way for Katie to apply styles to titles and headings is to use the quick styles gallery.
Therefore, the Option C is correct.
Read more about Quick Styles gallery
brainly.com/question/3326108
Design the logic for a program that allows a user to enter a number. Display the sum of every number from 1 through the entered number. In pseudocode or flow chart.
Answers
Answer:
START
DECLARE total_sum = 0
DISPLAY "Enter a number: "
GET user_input
FOR i from 1 to user_input:
SET total_sum = total_sum + i
END FOR
DISPLAY "The sum of every number from 1 through " + user_input + " is " + total_sum
END
give the synyax and example of any three mathematical functions in spreadsheet
Answers
Answer:
The answer to this question is given below in the explanation section
Explanation:
There are different mathematical functions that can be used in the spreadsheet for performing some required calculations on data such as taking the average of numbers, adding numbers, multiplying the numbers.
But most commonly used three mathematical functions in the spreadsheet is given below:
1. AVERAGE(): The average function is used to find the average of a given number of cells.
Syntax of Average() function: average(number1, number2,.....).
2. SUM(): The sum function is used to add all the values within a range of cells.
Syntax: of sum() function: sum(cell address1: cell address2)
3.COUNT(): Count () function is used to count the number of data.
Syntax of Count() function: count(cell address1: cell address2)
How do you draw on a computer?
Answers
hello, I think i can help you.
There are different ways. to start, you may want to download a program, if you need one for free, Krita is a good one, but if you are willing to pay, Clip studio paint is a great option.
when you get to draw, you can do some of the following
-you can try and use your mouse, this is way harder, but not impossible.
-get a drawing tablet. There are different types and prices, some of them have no screen, but are an excellent way to start and are way cheaper. The ones with screen are kinda expensive, but are more professional.
You can also use your phone or a tablet/iPad.
in this case, Clip studio, Sketchbook or Ibis paint are great options, but if you have an apple device, you will be able to use the previously mentioned programs, and some others, Procreate is an amazing example, tho you have to play for this one.
I hope this helps! :D
Draw the resulting image on the grub below using the following rules: it
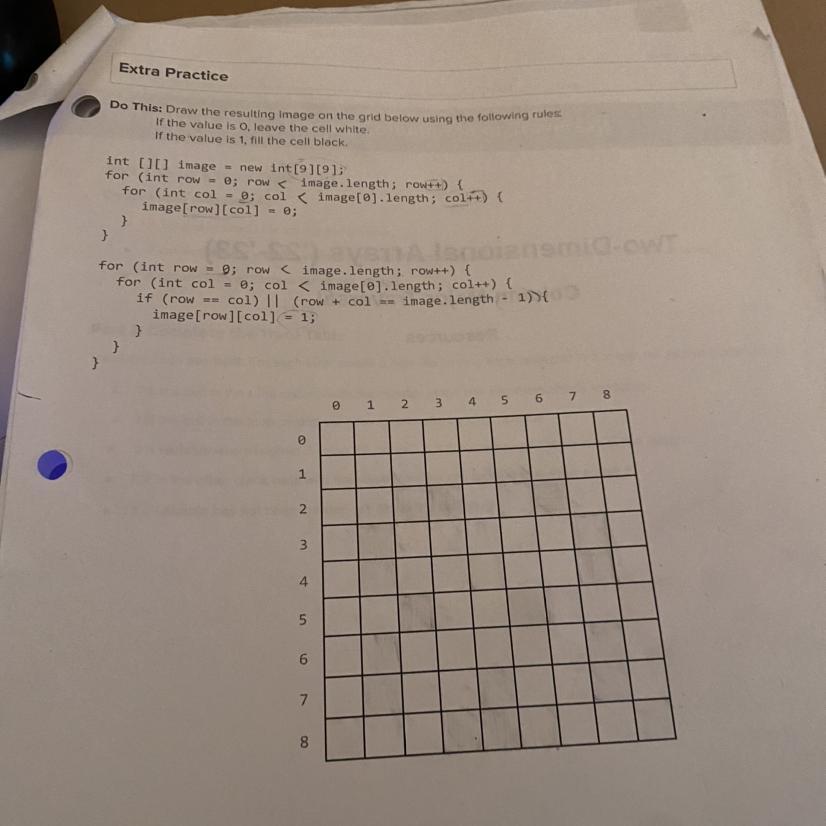
Answers
Explanation:
I just answered this.
I cannot draw here.
but it will mark all dots, where row number = column number.
and all dots, where row number + column number = 8.
this will create a giant X.
the 2 lines go from (0, 8) to (8, 0), and from (0, 0) to (8, 8) with (4, 4) being the central intersection point.