Tasha works as an information technologist for a company that has offices in New York, London, and Paris. She is based out of the New York office and uses the web to contact the London and Paris office. Her boss typically wants her to interact with customers and to run training seminars to teach employees new software and processes. Which career pathway would have this type of employee?
Answers
Answer:
D. Interactive Media
Explanation:
i just took the test right now
The career pathway which would have this type of employee is an interactive media.
What is media?Media is a terminology that is used to describe an institution that is established and saddled with the responsibility of serving as a source for credible, factual and reliable news information to its audience within a geographical location, either through an online or print medium.
In this context, an interactive media is a form of media that avail all media personnels an ability to easily and effectively interact with their customers or audience.
Read more on media here: https://brainly.com/question/16606168
Related Questions
fill in the blank with the correct response

Answers
Answer:
regenerates
Explanation:
a hub regenerates it's signal bit by bit as it travels down the physical medium
i. Explain what Race Condition is and how it can be prevented.
Answers
Answer:
In layman terms, a race condition can be defined as, a condition in which two or more threads compete together to get certain shared resources. For example, if thread A is reading data from the linked list and another thread B is trying to delete the same data.
Explanation:
To prevent the race conditions from occurring, you can lock shared variables, so that only one thread at a time has access to the shared variable.
question below in attachment
Answers
You can use basic HTML elements like input, select and textarea to generate an HTML web-form and gather the data for the code table.
What is the program?The form in this code case is configured to use the "post" method and directs to "insert_item.php", a PHP script that manages the form submissions. The structure comprises of input sections for the "name", "description", and "quantity" cells in the "item" table, as well as a button for submitting the information.
One method of collecting user input from a web-form and adding it to a database table is by utilizing PHP and SQL commands, which enables connectivity to the database and the ability to run the INSERT query.
Learn more about program from
https://brainly.com/question/26134656
#SPJ1



Protecting an IT system from security threats in a small business is the responsibility of the
Question 7 options:
IT Specialist
IT Manager
IT Department
IT CEO
Answers
Protecting an IT system from security threats in a small business is the responsibility of the: IT Specialist. (Option A)
What is an IT security threat?A threat in computer security is a potential bad action or occurrence enabled by a vulnerability that has an unfavorable impact on a computer system or application.
These three frequent network security vulnerabilities are likely the most hazardous to businesses: Malware, advanced persistent threats and distributed denial-of-service assaults are all examples of advanced persistent threats.
IT professionals create, test, install, repair, and maintain hardware and software in businesses. Some businesses will have their own IT team, although smaller businesses may use freelance IT employees for specific jobs.
Learn more about Security Threats:
https://brainly.com/question/17488281
#SPJ1
Answer:
IT Specialist so option A
Multiple Choice: We have been assigned the task of developing a software testing tool (tester) that can assess reachability of statements in a program. Namely, given a program and a statement x in the program (line in the code), the tester should produce a sequence of inputs that demonstrates that the program can reach statement x, or declare that statement x is not reachable under any input sequence. What should we respond to the manager who assigned this task
Answers
Answer:
A. There is no algorithm to decide whether this can be done or not.
Explanation:
We should respond to the manager who assigned this task that there is no algorithm to decide whether this can be done or not. This is because there are many unknowns with the program that is provided. There are various programming languages and each one has its own structure and requirements in order to test them. Also, each function is created differently with different inputs that are necessary and different algorithms used. It is impossible to design a single algorithm that works to test every single provided program. That is why testers have to create custom test cases for each function.
Which company was the first to develop personal computer?
Answers
Answer:
Electronic Controls Company
1.11 zyLab training: Interleaved input / output
Auto-graded programming assignments have numerous advantages, but have some challenges too. Students commonly struggle with realizing that example input / output provided in an assignment's specification interleaves input and output, but the program should only output the output parts. If a program should double its input, an instructor might provide this example:
Enter x:
5
x doubled is: 10
Students often incorrectly create a program that outputs the 5. Instead, the program should only output the output parts:
Enter x:
x doubled is: 10
The instructor's example is showing both the output of the program, AND the user's input to that program, assuming the program is developed in an environment where a user is interacting with a program. But the program itself doesn't output the 5 (or the newline following the 5, which occurs when the user types 5 and presses enter).
Also, if the instructor configured the test cases to observe whitespace, then according to the above example, the program should output a newline after Enter x: (and possibly after the 10, if the instructor's test case expects that).
The program below incorrectly echoes the user's input to the output.
1. Try submitting it for grading (click "Submit mode", then "Submit for grading"). Notice that the test cases fail. The first test case's highlighting indicates that output 3 and newline were not expected. In the second test case, the -5 and newline were not expected.
2. Remove the code that echoes the user's input back to the output, and submit again. Now the test cases should all pass.

Answers
The code is System.out.println(x); //use print method to print value.
What is Java programming used for?In order to have as few implementation dependencies as feasible, Java is a high-level, class-based, object-oriented programming language.Java is a programming language used by programmers to create programmes for laptops, data centres, game consoles, scientific supercomputers, mobile phones, and other gadgets. According to the TIOBE index, which ranks the popularity of programming languages, Java is the third most used programming language in the world, after Python and C.Python and Java are two of the most popular and robust programming languages. Java is a compiled language, which means it is typically quicker and more effective than Python. Python's syntax is shorter and clearer than Java's because it is an interpreted language. It uses fewer lines of code than Java to do the same task.Given data :
In the given question, it simplifies or deletes code in the 11th line. This line has a large major statement.
In the case, the tests fail because only 1 line of output is required by the tester, but two lines are obtained instead.
It's to demonstrate that the input/output or testing requirements function throughout the model.
Learn more about Java programming refer to :
https://brainly.com/question/26789430
#SPJ1
Which Sophos Firewall feature can be used to limit the amount of bandwidth an application can use?
Answers
The firewall feature can be used to limit the amount of bandwidth an application can use.
Sophos Firewall offers a Traffic Shaping feature that can be used to limit the amount of bandwidth an application can use. With Traffic Shaping, you can allocate specific bandwidth limits to different types of traffic, such as web browsing, email, or video streaming. This feature allows you to prioritize important applications and limit the bandwidth of less critical applications to ensure that network performance is not impacted. Traffic Shaping can be configured to apply to specific users, groups, or applications and can be adjusted based on the time of day or other criteria.
learn more about Sophos Firewall here:
https://brainly.com/question/30731117.
#SPJ4
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
Which of the following are labels used to identify illustrations such as tables, charts and figures in a document?
O Headers
O Footers
O Captions
O Citations
Answers
There are data which are given charts, tables and illustrated by the help of some labelling. This labelling helps us to identify the data and makes us understand what the data says.
This labelled data has to be given some name and thus in order to represent the figures in a document. This term caption is given to those data sets in the form of tables and illustrations.Hence the option C is correct,
Learn more about the labels used to identify the tables, charts and figures in a document.
brainly.in/question/11644668.
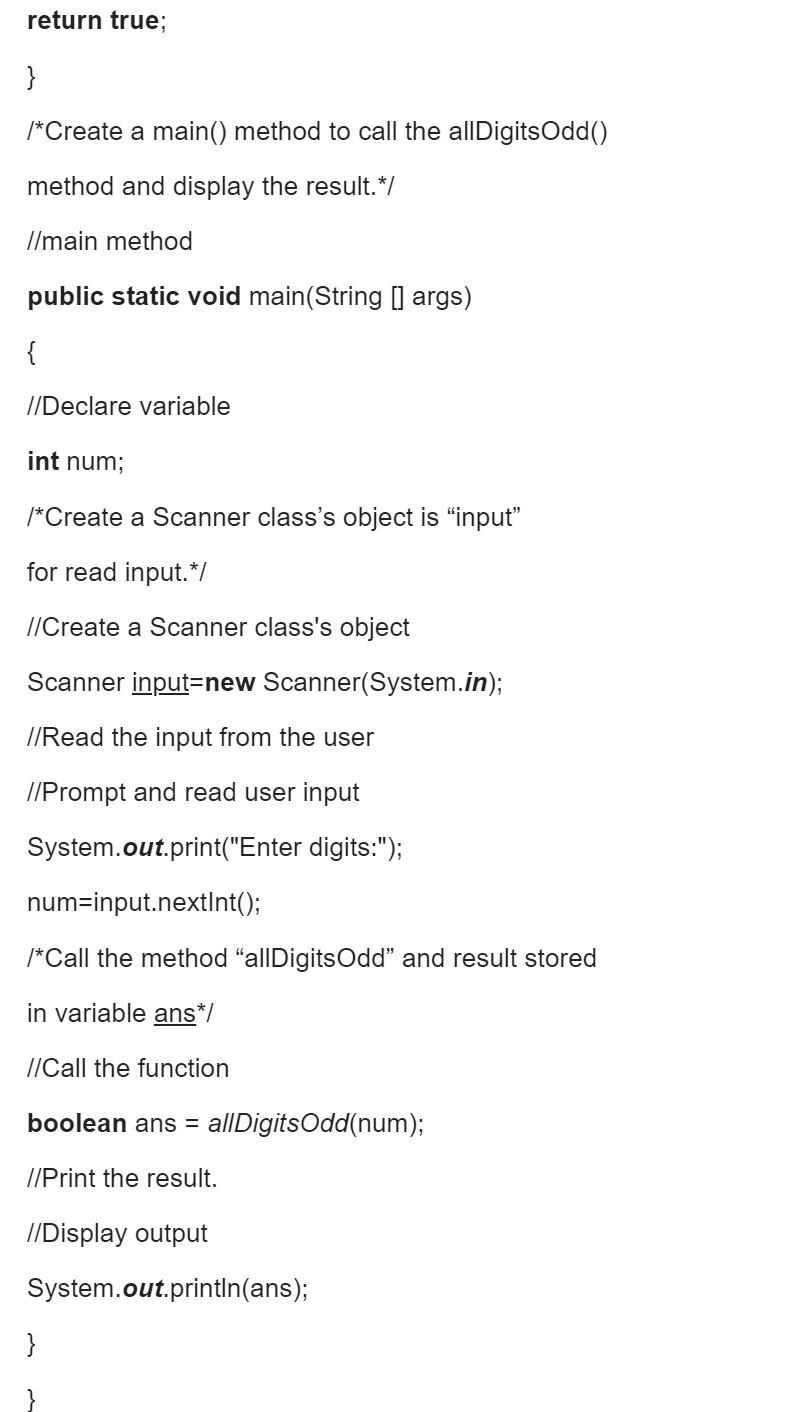
Write a method called allDigitsOdd that returns whether every digit of a positive integer is odd. Return true if the number consists entirely of odd digits (1, 3, 5, 7, 9) and false if any of its digits are even (0, 2, 4, 6, 8). For example, the call allDigitsOdd(135319) returns true but allDigitsOdd(9145293) returns false.
Answers
Answer:
Sample output:
Enter integer 3232423
true
Enter integer 12131231
false
Explanation:
Above is the output of the program and for the solution check the screenshots attach to understand clearly the program.
Thanks



In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
During slide show mode, hitting the B key will do which of these things? Responses end your presentation end your presentation, blank the screen with black screen (or return to the slide if you are currently blank) blank the screen with black screen (or return to the slide if you are currently blank), move to the first page of your presentation move to the first page of your presentation, move back one page move back one page,
Answers
During slide show mode, hitting the B key will do B. Blank the screen with black screen (or return to the slide if you are currently blank).
When in Slide Show mode and what does the B button do?
It is one that help you to Make your way through your slides. Press P to return to the previous slide. Hit Esc to end Slide Show. Press B to make the screen completely black.
Note that this is one that also helps you to be able to restore visibility of the current slide, press B once more.
Therefore, based on the above, During slide show mode, hitting the B key will do B. Blank the screen with black screen (or return to the slide if you are currently blank).
Learn more about slide show from
https://brainly.com/question/3594774
#SPJ1
Answer:
blank the screen with black screen (or return to the slide if you are currently blank)
Explanation:Hoped This Helped :D
a computer memory that acts as the main storage available to user for programs and data
Answers
Answer:
Primary storage. Primary storage (also known as main memory, internal memory, or prime memory), often referred to simply as memory, is the only one directly accessible to the CPU.
Which technologies combine to make data a critical organizational asset?
Answers
Answer: Is in the image I attached below of my explanation. Hope it helps! Have a wonderful day! <3
Explanation: Brainliest is appreciated, I need 2 more for my next last rank please!

A ___________ is a variable used to pass information to a method.
Answers
Answer:
A parameter is a variable used to pass information to a method.
Explanation:
A parameter is a variable used to pass information to a method.
What are the features of parameter?In general, a parameter "beside, subsidiary" is any quality that aids in describing or categorizing a certain system. In other words, a parameter is a component of a system that is crucial or useful for identifying the system or assessing its functionality, status, or other characteristics.
In some fields, such as mathematics, computer programming, engineering, statistics, logic, linguistics, and electronic music production, the term "parameter" has more precise definitions.
In addition to its technical applications, it also has broader meanings, particularly in non-scientific situations. For example, the terms "test parameters" and "game play parameters" refer to defining qualities or boundaries.
A novel method of characterizing surface texture, in particular surfaces having deterministic patterns and features, is the use of feature parameters.
Traditional methods for characterizing surface texture, such profile and areal field parameters, are considered as supplementary to the feature parameter approach.
Learn more about parameter, here
https://brainly.com/question/29911057
#SPJ6
What method is used in the following line of code to associate clicking the left button with the event handler "clickSingle"?
widget._____(' ', clickSingle)
eventHandler
eventHandler
attach
attach
connect
connect
bind
Answers
Answer:
Bind
Explanation:
widget.bind('<Button-1>', clickSingle)
Q18. Evaluate the following Java expression ++z
A. 20
B. 23
C. 24
D. 25
y+z+x++, if x = 3, y = 5, and z = 10.

Answers
Answer: C. 25
Explanation:
Should be the answer
Write a statement that calls the recursive method backwardsAlphabet() with parameter startingLetter.
Answers
Answer:
Explanation:
public class RecursiveCalls {
public static void backwardsAlphabet(char currLetter) {
if (currLetter == 'a') {
System.out.println(currLetter);
}
else {
System.out.print(currLetter + " ");
backwardsAlphabet(--currLetter);
}
return;
}
public static void main (String [] args) {
char startingLetter = '-';
startingLetter = 'z';
// Your solution goes here
backwardsAlphabet(startingLetter);
return;
}
}
Select the correct answer from each drop-down menu. What data types can you suggest for the given scenario? Adja is working in a program for the school grading system. She needs to use a(n) (First drop down) to store the name of the student and a(n) array of (Second drop down) to store all the grade of each subject of each student.
Options for the first drop down are- A. Integer, B.String, C.Character.
Options for the second drop down are- A.Floats, B.Character, C.String.
Answers
Based on the given scenarios, the data types that would be best suited for each is:
C. Character.A. FloatsWhat is a Data Type?This refers to the particular type of data item that is used in order to define values that can be taken or used in a programming language.
Hence, it can be seen that based on the fact that Adja is working in a program for the school grading system, she would need to use a character to store the name of the student and a float to store all the grades of each subject of each student because they are in decimals.
With this in mind, one can see that the answers have been provided above.,
In lieu of this, the correct answer to the given question that have been given above are character and floats.
Read more about data types here:
https://brainly.com/question/179886
#SPJ1
Answer:
A- String
B- Character
Online education _____. Select 3 options.
offers students flexibility
has pros and cons
does not have challenges
is free for everyone
has its challenges
Answers
Answer:
answers are A,B, and E
Explanation:
Online education offers students flexibility, it also;
Has pros and cons. Has its challenges.What are the pros and cons of online education?Online education is known to be a form of education where people are said to school over the internet. It has its own pros and cons such as:
It is very Flexibility. Its Reputation is low when compared to other forms of education.There is Ease of Access, etc.Conclusively, Online education offers students flexibility and it also has its own pros and cons.
Learn more about Online education from
https://brainly.com/question/14591988
#SPJ2
please I need help.
Select the correct answer. of the four email features listed below, which is the most important?
O A. the To address
O B. the Bcc address
OC. the attachments
O D. the domain name
Answers
Answer:
The answer is the "TO address"
Explanation:
i just took the test and got it right sooooooo
Answer: A “The To adress”
Explanation:
got it right
TO EXIT WORD YOU CLICK WHAT
Answers
(Or the X in the corner?)
Answer:
To exit Word, you can click on the "File" menu and then click "Exit" or "Close".
what is data abstraction and data independence?
Answers
Data abstraction and data independence are two key concepts in computer science and database management systems. They are closely related and aim to improve the efficiency, flexibility, and maintainability of data management.
What is data abstraction and data independence?The definitions of these two are:
Data Abstraction:
Data abstraction refers to the process of hiding the implementation details of data and providing a simplified view or interface to interact with it. It allows users to focus on the essential aspects of data without being concerned about the underlying complexities. In programming languages, data abstraction is often achieved through the use of abstract data types (ADTs) or classes.
By abstracting data, programmers can create high-level representations of data entities, defining their properties and operations.
Data Independence:
Data independence refers to the ability to modify the data storage structures and organization without affecting the higher-level applications or programs that use the data. It allows for changes to be made to the database system without requiring corresponding modifications to the applications that rely on that data. Data independence provides flexibility, scalability, and ease of maintenance in database systems.
Learn more about data at:
https://brainly.com/question/179886
#SPJ1
You are working with a client who wants customers to be able to tap an image and see pricing and availability. As you are building the code in Java, what will you be using?
graphical user interface
icon public use
graphical public use
icon user interface
Answers
Answer:
A. Graphical user interface
Explanation:
In Java the graphical user interface is what manages interaction with images.
Answer: A.)
Explanation:
The answer is A because
I was born to rule the world
And I almost achieved that goal
(Giovanni!)
But my Pokémon, the mighty Mewtwo,
Had more power than I could control
(Giovanni!)
Still he inspired this mechanical marvel,
Which learns and returns each attack
(Giovanni!)
My MechaMew2, the ultimate weapon,
Will tell them Giovanni is back!
There'll be world domination,
Complete obliteration
Of all who now defy me.
Let the universe prepare,
Good Pokémon beware,
You fools shall not deny me!
Now go, go, go, go!
It will all be mine,
Power so divine
I'll tell the sun to shine
On only me!
It will all be mine,
Till the end of time
When this perfect crime
Makes history
Team Rocket! This is our destiny!
Listen up, you scheming fools,
No excuses, and no more lies.
(Giovanni!)
You've heard my most ingenious plan,
I demand the ultimate prize
(Giovanni!)
Now bring me the yellow Pokémon
And bear witness as I speak
(Giovanni!)
I shall possess the awesome power
In Pikachu's rosy cheeks!
There'll be world domination,
Complete obliteration
Of all who now defy me.
Let the universe prepare,
Good Pokémon beware,
You fools shall not deny me!
Now go, go, go, go!
It will all be mine,
Power so divine
I'll tell the sun to shine
On only me!
It will all be mine,
Till the end of time
When this perfect crime
Makes history
Team Rocket! This is our destiny!
To protect the world from devastation
To unite all peoples within our nation
To denounce the evils of truth and love
To extend our reach to the stars above
Jessie!
James!
There'll be total devastation,
Pure annihilation
Or absolute surrender.
I'll have limitless power,
This is our finest hour
Now go, go, go, go!
how can IT infrastructure be linked to the business strategy of any organization
Answers
Answer:
The overview of the situation is discussed in the following part.
Explanation:
It's indeed real that perhaps IT technology will have a strategic edge and improved market efficiency. IT technology can improve the protection, accessibility, and efficiency of any enterprise.
Numerous massive, small as well as medium-sized companies or beginning are currently preparing their growth plans by sustaining a stable IT infrastructure throughout the place that will ensure and increase their profitability.
Those same years, the accompanying IT infrastructure is being used to connect the market strategy:
Broadband and Wireless Connectivity,Security and Risk Management,IT Structure Strategy,Performance Strategy, etc.What is the best way to protect against the loss of important files?
a-firewalls
b-antivirus software
c-backup files
d-secure passwords
Answers
Answer:
Backup files
Explanation:
Answer: they are correct it's C) backup files
Explanation: i got the question right on the test
Ć
Asking your teacher to figure out your current grade in his class cannot help increase your grades.
True or false
Answers
Answer:
false
Explanation:
if you ask your teacher to check your grade you know what work your missing and can turn it in for a better grade
Answer:
f
Explanation:
numDistance is read from input as the size of the vector. Then, numDistance elements are read from input into the vector bikingNumbers. Use a loop to access each element in the vector and if the element is an odd number, output the element followed by a newline.
Ex: If the input is 4 128 173 129 47, then the output is:
173
129
47
Answers
The distance between and is the difference between the two numbers.
Thus, Since the distance is a positive quantity, we want to subtract a small number from a big number to get a positive result. However, sometimes we don't know which of the two numbers is bigger.
If the number line above wasn't given, we wouldn't know is greater than. To get a positive result every time, we take the absolute value of the difference.
The number line serves as the primary visual representation in statistics, it is common practice to compare two points on the number line and calculate their distance from one another.
Thus, The distance between and is the difference between the two numbers.
Learn more about Number distance, refer to the link:
https://brainly.com/question/19946572
#SPJ1
9.4 code practice edhesive. PLEASE PLEASE PLEASE HELP
Answers
Answer:
a = [[34,38,50,44,39],
[42,36,40,43,44],
[24,31,46,40,45],
[43,47,35,31,26],
[37,28,20,36,50]]
for r in range(len(a)):
for c in range (len(a[r])):
if (a[r][c]% 3 != 0):
a[r][c]=0
for i in range(len(a)):
for j in range (len(a[i])):
print(a[i][j], end=" ")
print(" ")
Explanation:
We start off by declaring an array called "a". As introduced in the previous lessons, we use two for loops to fully go through all the rows and columns of the two-dimensional arrays. We then add in the line that checks if the remainder of any of these is not equal to zero, then print them as zero on the grid.
(I also got 100%)
mark as brainliest pls hehe
In this exercise we have to use the knowledge in computational language in python to describe a code that best suits, so we have:
The code can be found in the attached image.
What is the function range?The range() function returns a number series in the range sent as an argument. The returned series is an iterable range-type object and the contained elements will be generated on demand. It is common to use the range() function with the for loop structure. In this way we have that at each cycle the next element of the sequence will be used in such a way that it is possible to start from a point and go incrementing, decrementing x units.
To make it simpler we can write this code as:
a = [[34,38,50,44,39], [42,36,40,43,44], [24,31,46,40,45], [43,47,35,31,26],
[37,28,20,36,50]]
for r in range(len(a)):
for c in range (len(a[r])):
if (a[r][c]% 3 != 0):
a[r][c]=0
for i in range(len(a)):
for j in range (len(a[i])):
print(a[i][j], end=" ")
print(" ")
See more about python at brainly.com/question/19705654

