shamika is a networking student who has just moved into a small house with two other roommates. she has purchased a new dsl modem and is planning on configuring the built-in firewall. she needs to change the default username and password for the device first. what is her concern?
Answers
The default username and password are likely available on the Internet and anyone could use those credentials to hack into the modem and access the home network.
What is the use and importance of username and password ?A username and password are required for two (2) reasons:
To ensure the safety of your account. It will prevent unwanted people from accessing your Domain Name information. To gain access to the Member Management and Manage Domains functions, which will allow you to efficiently make changes to your Domain Name.The following is how the user name and password work:
Step 1: A user goes to a website and fills out a form to generate a username and password.
Step 2 - The password is hashed and the resulting hash is saved in the database.
Step 3 - When a user logs in, they must re-enter their password on the website.
What is built-in firewall ?A firewall is a security device either computer hardware or software — that can help safeguard your network by filtering traffic and preventing unauthorized access to your computer's confidential data.A firewall not only blocks unwanted traffic, but it can also assist prevent harmful malware from infiltrating your computer.Different levels of protection can be provided by firewalls. The key is to determine how much protection you require.Complete question is :
Shamika is a networking student who has just moved into a small house with two other roommates. She has purchased a new DSL modem and is planning on configuring the built-in firewall. She needs to change the default username and password for the device first. What is her concern?
A. She is being overly cautious, as home networks are a low priority for hackers.
B. She will be unable to configure the firewall until those temporary default credentials have been changed.
C. The DSL company has those credentials and could use them to monitor her network communications.
D. The default username and password are likely available on the Internet and anyone could use those credentials to hack into the modem and access the home network.
Can learn more about username and password from https://brainly.com/question/28344005
#SPJ4
Related Questions
identify two (2) best practices for security requirements for laptops that may store sensitive info. quizlet
Answers
When it comes to security requirements for laptops that may store sensitive information, there are several best practices that you can follow to ensure the protection of the data.
One of the key ways to secure sensitive information on a laptop is by encrypting the data. Encryption is the process of converting data into a format that can only be read or accessed with the use of a decryption key. By encrypting the data on a laptop.
There are various encryption methods available, such as full disk encryption, which encrypts the entire hard drive, or file-level encryption, which encrypts specific files or folders. It is important to choose a strong encryption algorithm and to regularly update encryption software to ensure the highest level of security.
To know more about security visit:
https://brainly.com/question/33718338
#SPJ11
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
Which statement best describes the difference between a spreadsheet and a database?
Spreadsheets store data in tables that interact; databases store data in cells that interact.
Databases store data in tables that interact; spreadsheets store data in cells that interact.
Spreadsheets store binary data; databases store hexadecimal data.
Spreadsheets store hexadecimal data; databases store binary data,
Answers
Answer:
Databases store data in tables that interact; spreadsheets store data in cells that interact.
Explanation:
The main difference between between a spreadsheet and a database is that databases store data in tables that interact; spreadsheets store data in cells that interact.
What is a data?A data can be defined as the representation of facts, concepts, instructions in a formalized manner which is suitable for communication by the user.
The spreadsheet is an application that is used for the analysis and storage of data in a cell that can be manipulated, formatted or edited within the cell.
The database is an application that can be used for the analysis and storage of data in an external tabular form.
Therefore, the main difference between between a spreadsheet and a database is that databases store data in tables that interact; spreadsheets store data in cells that interact.
Learn more about spreadsheet here:
https://brainly.com/question/25879801
#SPJ2
What are the possible values you can store in the C# "bool" data type?
Group of answer choices
true or false
1 or 2
more or less
A or B
Answers
Answer:
n
Explanation:
Bool is a boolean and it stores True and False values.
The physical things you can touch that make up a computer
Answers
The physical things you can touch that make up a computer are monitor, mouse, keyboard, and CPU.
What is computer?A computer can be defined as an electronic device which accepts data, processes data and brings out information known as results.The computer is used to type and edit different forms of documents like word, PDF and Excel.
A computer can be used to perform business transactions online. It is used by both sellers and buyers to market and purchase product respectively.A computer can be used to play music, watch movies and play games.
Therefore, The physical things you can touch that make up a computer are monitor, mouse, keyboard, and CPU.
Learn more about CPU on:
https://brainly.com/question/16254036
#SPJ1
When your friend DaJuan turns on his computer, he hears four beeps. The computer won’t fully boot. DaJuan has a Dell computer with a quad core processor and has recently upgraded his RAM. Apply the troubleshooting methodology to help DaJuan understand and resolve his problem. The steps of the methodology are listed for you. You can write directly on the write suggestions for DaJuan at each step. 1. Identify the Problem (beeps are key here) 2. Internet Research. 3. Establish a Theory of Probable Cause 4.Test the Theory 5.Establish a Plan of Action 6.Implement the Solution or Escalate 7. Verify Full System Functionality 8. Document Findings
Answers
Answer:
4 beeps indicate a Memory Read / Write failure. Try re-seating the Memory module by removing and reinserting it in the slot. This could mean it could've just jiggled loose after a while or dust, there could be a hundred other problems but those are the two most common.n:
The Dell desktop personal computer has diagnostic indicators built into it including Beep Codes to help diagnose issues if those errors cannot be displayed on the screen
Step 1: The likely problem is the Dell support article indicates that 4 beeps is due to a RAM read/write failureStep 2: Based on internet research, the likely ram modules will be required to be removed, the connecting slot for the RAM modules on the mother board, should be cleaned and the RAM will require cleaning with certified canned air. The RAM modules require proper reinstallationStep 3. The theory that can be established is that the reason the computer emits four beeps and won't fully start is because the upgraded RAM modules DaJuan had installed are only in partial contact with the gold fins in their motherboard slotsStep 4. Remove the RAM module on a similar computer that is functional and verify that the same sound is emittedStep 5. The RAM modules are to be reached for cleaning by opening the covering of the system's CPU and blowing the RAM and RAM slots with canned airStep 6. Clean the RAM and the RAM slots and reinstall the RAMStep 7. Power on the system and verify that the four beeps previously heard has stopped and that the system is fully functionalStep 8. The observation after the RAM has been cleaned and reinstalled are documented for referenceLearn more about troubleshooting computer issues here:
https://brainly.com/question/19871972

E) ¿Entiende usted que tendría repercusión legal un mal manejo de los datos del cliente por parte de la empresa? ¿Por qué?
Answers
Answer:
Efectivamente, un mal manejo de los datos del cliente por parte de la empresa tendría repercusiones legales que afectarían negativamente a la compañía. Esto es así porque un eventual mal manejo de los datos personales de los clientes implicaría una filtración de dichos datos hacia el resto del público, con lo cual los datos personales y privados de cada cliente se verían expuestos en forma pública, generando así posibles daños a estos a través de la mala utilización de dicha información por parte de terceros malintencionados.
Write a program that outputs a subtraction practice problem for a student, outputting the larger random number
first and the smaller random number second.
this is in C++ and i cant figure it out
Answers
Answer:
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
int main(void)
{
srand(time(NULL));
int num1, num2;
int val;
while (true)
{
num1 = rand() % 100 + 1; //Random number between 1-100
num2 = rand() % 100 + 1; //Random number between 1-100
if (num1 >= num2)
{
printf("%d - %d = ", num1, num2);
scanf("%d",&val);
if (val == num1-num2)
{
printf("Correct!\n");
}
else
{
printf("Incorrect!\n");
}
}
else
{
printf("%d - %d = ", num2, num1);
scanf("%d",&val);
if (val == num2-num1)
{
printf("Correct!\n");
}
else
{
printf("Incorrect!\n");
}
}
}
}
Explanation:
First, we create two random numbers and save the values. Then we check to see which value is larger. Based on that, we change how we display the format to the user. Then we check to see if the user input number is equivalent to the subtraction problem. If it is, we display Correct! Else, we display Incorrect!
Cheers.
What are the 4 most common types of data in computer science?(Give an example of each and explain when and why you might use them)
Answers
In computer science, the four most frequent data types are boolean (also known as true/false), floating-point (3.14), strings (such as "hello"), and integers (5, for example).
What are the top three sorts of data?The majority of programming languages allow the fundamental data types of characters, Booleans, floating-point numbers, and integer numbers (of various sizes).
Which five popular data kinds are there?Integral, Floating Point, Character, Character String, and Composite types are the five basic kinds of data types that are recognised by the majority of current computer languages. Each broad category also includes a number of particular subtypes.
To know more about data visit:-
https://brainly.com/question/11941925
#SPJ1
I’m building a pc name some good parts I need some help on some parts? And prices plz
Answers
Answer:$25
Explanation:
when asking a question how do u add a photo for others to also see
Answers
Answer:
click on the thing that looks like a paper clip and select a file (microsoft computers)
Explanation:
Write a for loop to print all the even numbers from 200 to 300.
Expected Output
200
202
204
206
208
210
212
214
216
218
220
222
224
226
228
230
232
234
236
238
240
242
244
246
248
250
252
254
256
258
260
262
264
266
268
270
272
274
276
278
280
282
284
286
288
290
292
294
296
298
300
Answers
for x in range(200, 301, 2):
print(x)
I hope this helps!
1. Which of the following CAN NOT be considered as information? (1) The average height of students in a class.
(2) The total sales of a company for the month of May.
(3) The body temperature of a patient.
(4) The number of copies of a book sold at the end of the day. (5) Literacy rate of a country.
Answers
Answer:
Explain three most significant features of computer
blueprint could not be loaded because it derives from an invalid class. check to make sure the parent class for this blueprint hasn't been removed! do you want to continue (it can crash the editor)?
Answers
The error message, "Blueprint could not be loaded because it derives from an invalid class" implies that the blueprint could not be loaded due to the fact that it is based on an invalid class. This error message can occur when a blueprint's parent class has been deleted or is no longer present in the game.
Thus, the blueprint cannot be loaded by the game engine. The message goes further to ask the user to ensure that the parent class has not been removed before continuing. If the user chooses to continue, the engine may crash. This can happen if the engine is not able to identify the base class of the blueprint and thus, cannot load the blueprint's content. If you encounter this issue, it is advisable to try to locate and restore the parent class for the blueprint in order to fix the error. One of the ways to do this is to restore the base class that was removed or to rebuild the parent class.
It is important to note that if the blueprint is critical to the game, a crash may result if the blueprint is loaded without fixing the error. In conclusion, Blueprint could not be loaded because it derives from an invalid class can be fixed by restoring the parent class or rebuilding it to ensure that the game engine can load the blueprint without crashing.
To know more about blueprint visit:
https://brainly.com/question/28187253
#SPJ11
There are several qualitative tools for generating and sorting ideas and information. They can be used at different points in time and for various aspects of a QI project (for example, to identify performance problems and potential solutions). Pick any one of such tools, briefly describe it, and highlight one way it contributes to a QI project.
Answers
One qualitative tool for generating and sorting ideas and information in a Q I project is the Fish bone Diagram, also known as the Cause and Effect Diagram.
This tool helps identify the potential causes of a problem and organize them into categories for further analysis. It is called a Fish bone Diagram because it resembles the shape of a fish skeleton.To create a Fish bone Diagram, start with a problem statement and draw a horizontal line representing the problem. Then, draw diagonal lines branching out from the main line, like the bones of a fish.
These diagonal lines represent different categories of causes that may contribute to the problem. Common categories include people, process, materials, equipment, and environment.Next, brainstorm and list potential causes under each category. For example, under the "process" category, you might list causes such as lack of standard operating procedures or poor training.
To know more about qualitative visit:
https://brainly.com/question/30602672
#SPJ11
What gets printed after the following code is run?
var name;
console.log(name);
Select the one choice that best answers the prompt above:
Answer 1
undefined
Answer 2
nothing
Answer 3
error
Answer 4
name
Next......
Answers
Answer:
Mia Khalifa jenny since
When should the Clean Up command be used?
to move all message conversations to the deleted items folder
to ensure that no future messages of that type are delivered to him
to remove redundant messages to free up space in his inbox
to clean up the deleted items folder and permanently delete messages
Answers
Answer:
the correct option in c
Explanation:
Answer: The person below me is right, its C.
Explanation: I did it on Edg and I got it right.
what command can be used to repair a dual boot system?
Answers
Answer:
bootrec utility
Explanation:
It entirely depends on your version of windows and if you are even on windows, so I have no explanation, but for windows it is possible.
10. What is the value of favorite Animal after the code below is run?
animals = [ 'dog', 'cat', 'cow', 'pig' ]
favoriteAnimal = animals[2]
[1 point]
O a. dog
O b.cat
O c. cow
O d. pig
Answers
Running the code
animals = [ 'dog', 'cat', 'cow', 'pig' ]
favoriteAnimal = animals[2]
will give a result of
"cow"
Document management provides tools to manage and store documents securely and to keep track of the multiple versions of these documents.True or false
Answers
The given statement "document management provides tools to manage and store documents securely and to keep track of the multiple versions of these documents." is true because document management systems provide a centralized location for storing and managing documents, and typically include features for version control, access control, and secure storage.
These systems enable organizations to manage their documents more efficiently, ensuring that they are up-to-date, accessible only to authorized users, and protected from unauthorized access, modification, or deletion. By keeping track of document versions, document management systems can also help prevent errors or inconsistencies that can arise when multiple versions of a document are being used simultaneously.
You can learn more about document management systems at
https://brainly.com/question/13907906
#SPJ11
All of the following exemplifies the PRECEDE-PROCEED model EXCEPT: Group of answer choices The model is not an example logic model. The model outlines a diagnostic planning process to assist in the development of targeted and focused public health programs. Process evaluations allow the community to compare actual implementation with ideal implementation. The model includes the assessment that intends to articulate the community needs, community capacity, strengths, resources, and readiness to change. The model includes a phase that focuses mainly on community-level theories.
Answers
The PRECEDE-PROCEED model is a planning framework used in public health to develop and implement effective health promotion and disease prevention programs. It is a widely recognized model that has been used extensively in various public health settings.
The PRECEDE-PROCEED model is a comprehensive planning framework that provides a step-by-step process for developing targeted and focused public health programs. It consists of two main phases: the first phase is the PRECEDE phase, which focuses on assessing the needs and priorities of the community, and the second phase is the PROCEED phase, which focuses on the development, implementation, and evaluation of the program. The model is based on the premise that health-related behaviors are complex and multifaceted and that interventions should be tailored to address the unique needs and characteristics of the target population. The model emphasizes the importance of community participation, collaboration, and empowerment in the planning and implementation of public health programs. All of the options listed in the question exemplify the PRECEDE-PROCEED model except for the first option, which states that the model is not an example logic model. The other options describe key components of the model, such as the assessment of community needs, community capacity, and readiness to change, the focus on community-level theories, and the use of process evaluations to compare actual implementation with ideal implementation. Overall, the PRECEDE-PROCEED model is a useful framework for developing effective public health programs that address the complex and multifaceted nature of health-related behaviors.
To learn more about planning framework, visit:
https://brainly.com/question/31543518
#SPJ11
if you use a computer system in your volunteer work, is it okay to write your password on a piece of piaper
Answers
No, it is not okay to write your password on a piece of paper.
Writing your password on a piece of paper is not secure and could lead to unauthorized access to your computer system. Passwords should be kept confidential and not shared with anyone, including writing them down. Instead, it is recommended to use a password manager or memorize your passwords to ensure the security of your computer system. Storing passwords electronically in a secure password manager encrypts the passwords, making them more difficult for hackers to access. Additionally, memorizing passwords eliminates the risk of physical documents being lost or stolen. By following these practices, you can enhance the security of your computer system and protect sensitive information.
Know more about password here:
https://brainly.com/question/32892222
#SPJ11
What is a captcha? how has the collective efforts of internet users contributed to analyzing images through captchas?
Answers
Captcha is a spam prevention tool integrated into many user-facing websites.
What is a Captcha?The captcha tool is a modern-day internet invention that helps to separate human internet users from bots any time they interact on a website. What this tool does is provide a series of challenges that only a human mind would easily understand and perform, such as asking the user to type in letters into a box, or identify certain images.
Indeed, the collective efforts of internet users have contributed to preventing spam traffic on websites today as a result of captcha integration on websites.
You can learn more about captchas here https://brainly.com/question/12552047
#SPJ1
Below is a format code used within excel: "mmmm"
Which function would possibly use the above format code?
a. PMT function
b. YEAR function
c. CONCATENATE function
d. TEXT function
e. EOMONTH function
Answers
The function that would possibly use the format code "mmmm" in Excel is: b. YEAR function.
The "mmmm" format code is used to display the full name of the month in a date format. It represents the month spelled out in full. For example, if you have a date cell with the value "06/01/2023" and apply the "mmmm" format code, it will display "June" in the cell.
The YEAR function in Excel is used to extract the year from a given date. It returns the four-digit year value as a result. While the YEAR function itself does not directly use the "mmmm" format code, you can combine the YEAR function with a date cell formatted with the "mmmm" format code to extract the year along with the full month name.
Therefore, while the specific "mmmm" format code is not directly associated with the YEAR function, it can be used in conjunction with the function to achieve specific formatting requirements.
Learn more about function:https://brainly.com/question/11624077
#SPJ11
What is an example of a composite key in a database table?
InvoiceID
CustomerID
ProductID
OrderID + ProductID
Answers
Answer:
b
Explanation:
OrderID + ProductID is an example of a composite key in a database table. The correct option is 4.
What is composite key?A composite key is a key in a database table that consists of two or more columns that uniquely identify each row.
In a database table, a composite key is the combination of OrderID and ProductID in a table that tracks sales transactions.
Because a single order can contain multiple products and multiple orders can contain the same product, neither column can uniquely identify a row by itself.
However, by combining the two columns, each row can be uniquely identified, ensuring that the data is accurate and complete.
Similarly, a combination of CustomerID and ProductID might be used in a sales system to track the products purchased by each customer.
Thus, the correct option is 4.
For more details regarding composite key, visit:
https://brainly.com/question/10167757
#SPJ3
Where do you enter characters for a simple search?
Choose the answer.
Navigation Pane
Replace dialog box
Clipboard
Find Pane
Answers
Navigation Pane
Your create a document in Microsoft Word and you want to select text using the on-screen cursor.Which following device will you use? A.keyboard. B.Web cam. C.Microphone. D.Mouse.
Answers
HELP ME ⚠️‼️⚠️‼️ DUE IN EXACTLY 27 MINUTES
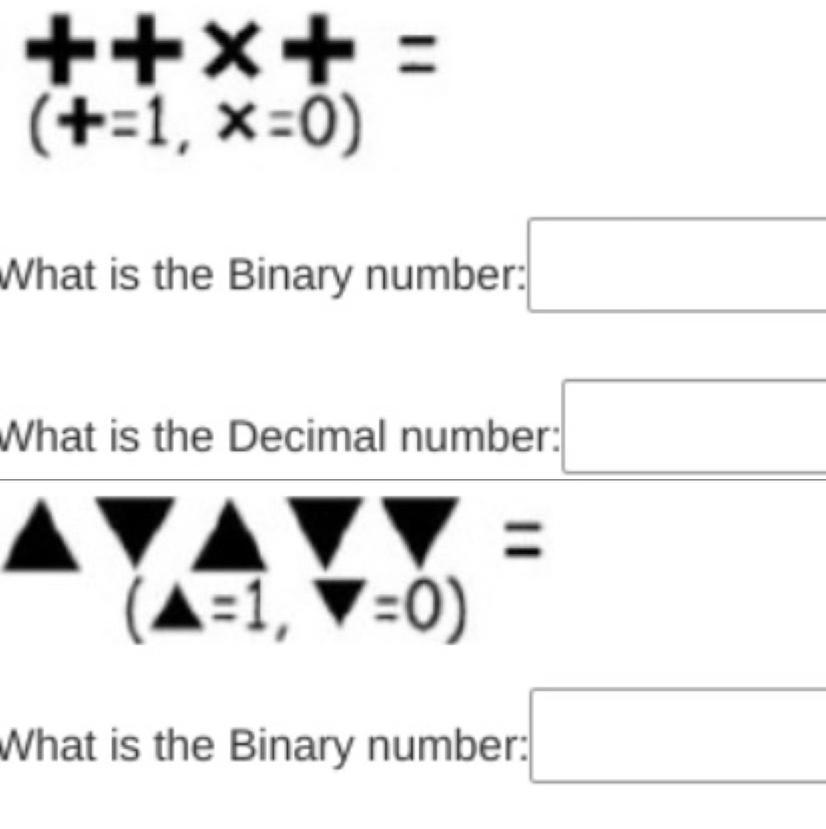
Answers
Answer:
the binary for the first one is 1101
and the binary for the second one is 10100
Explanation:
Answer the question with the code you would use to get the answer. you can list the output as long as it has no more than 4 columns and 30 row, but if i can run your code then that will also work.you have three data sets:1. a list of all olympic medalists from 1896 - 2008: medallists.csv2. a list of country codes: country_codes.csv3. data on population size of countries in 2008: 2008_populations.csvyour goal is to list the top 30 countries, in order of olympic medals (all types) per capita from only the year 2008.you will need to merge all three data sets, but make sure you do the correct types of merges.please complete in pandas or sqlif you cant access csv please at least write code out as if you could
Answers
To get the answer to the problem, you can use the following code: Make sure you have all the necessary CSV files. `import pandas as pdimport numpy as npimport matplotlib. pyplot as plt% matplotlib inline##Loading the three datasets medalists = pd.
read_ csv("medallists.csv") country_ codes
= pd. read_ csv("country_codes.csv")populations
= pd. read_csv("2008_populations.csv")##Cleaning the medalists data medalists
= medalists[medalists. Edition == 2008]medalists
= medalists. drop_ duplicates(['City', 'Edition', 'Sport', 'Discipline', 'Athlete', 'NOC', 'Event', 'Event_ gender', 'Medal'])medalists
= medalists[medalists. NOC != 'IOA']medalists = medalists [medalists. NOC != 'ZZX']##Merge the data sets medalists_ populations
= pd. merge(medalists, populations, how='inner', left_ on
='NOC', right_ on='Country Code')medalists_ populations_ codes
= pd. merge(medalists_ populations, country_ codes, how='inner', left_ on
='NOC', right_ on='NOC')##Getting the medals by country medalists_ by_ country
= medalists_ populations_ codes. group by (['Country'])medalists_ count = medalists_ by_ country. Medal. count()##Getting the populations by country populations_ by_ country
= medalists _populations_ codes. group by (['Country'])populations = populations_ by_ country. Population. unique()##Creating a new Data Frame with medals and populations medals_ and_ population
= pd. Data Frame({'Medals': medalists_ count, 'Population': populations})medals_ and_ population
= medals_ and_ population[~medals_ and_ population. Population. is null()]medals_ and_ population['Population']
= medals_ and_ population['Population']
.apply(lambda x: x[0])##Calculating the medals per capita MEDALS_ PER_ CAPITA
= (medals_ and_ population. Medals /medals_ and_ population. Population) * 1000000##Sorting the data and selecting the top 30data
= medals_ and_ population. copy()data['medals_ per_ capita']
= MEDALS_ PER_ CAPITA. sort_ values(ascending=False)data = data. sort_ values('medals_ per_ capita', ascending=False).head(30)```The above code loads the three datasets and cleans the medalists' data. Then the code merges the datasets and calculates the medals per capita. Finally, the data is sorted and the top 30 countries are selected.
To know more about datasets refer to:
https://brainly.com/question/29342132
#SPJ11
What is meant by technological progress?
Answers
Technological progress refers to the advancement and development of technology over time.
Technological progress has played a significant role in shaping human society and culture, and it continues to have a major impact on the way people live and work. Technological progress can be seen in various areas such as medicine, agriculture, communication, transportation, education, and entertainment.
For instance, the invention of the telephone and the internet has made communication faster and easier, while advancements in medicine have made it possible to cure or manage many diseases. Technological progress is driven by scientific discoveries, research, and development, as well as by competition and market demand.
The pace of technological progress has increased significantly in recent years, leading to rapid changes in many industries and sectors.
To know more about Technological progress:https://brainly.com/question/722255
#SPJ11