Search the web to discover the 10 most common user-selected passwords, and store them in an array. Design a program that prompts a user for a password, and continues to prompt the user until the user has not chosen one of the common passwords. Ensure that you store their password and can add that to the list so they cannot choose that password when they must change their password in the future.
Answers
Answer:
passwords = ["123456", "123456789", "qwerty", "password", "111111", "12345678", "abc123", "1234567", "password1", "12345"]
used_passwords = []
while True:
password = input("Choose a password: ")
if password in passwords:
print("You must not choose a common password!")
continue
elif password in used_passwords:
print("You used this password before. Choose a new one.")
continue
else:
used_passwords.append(password)
break
Explanation:
*The code is in Python.
Initialize the passwords array with 10 most common user-selected passwords
Initialize the used_passwords array as empty
Create an infinite while loop. Inside the loop, ask the user to choose a password. Check if entered password is in the passwords or not. If it is, print a warning and ask the user to choose again using continue statement. If the entered password is in the used_passwords, print a warning message and ask the user to choose again using continue statement. If the previous conditions are not satisfied, it means the password is valid. Add the password to the used_passwords array and stop the loop using break statement.
Related Questions
In the RSA system, the receiver does as follows:1. Randomly select two large prime numbers p and q, which always must bekept secret.2. Select an integer number E, known as the public exponent, such that (p 1)and E have no common divisors, and (q 1) and E have no commondivisors.3. Determine the private exponent, D, such that (ED 1) is exactly divisible byboth (p 1) and (q 1). In other words, given E, we choose D such that theinteger remainder when ED is divided by (p 1)(q 1) is 1.4. Determine the product n = pq, known as public modulus.5. Release publicly the public key, which is the pair of numbers n and E, K =(n, E). Keep secret the private key, K = (n, D).The above events are mentioned in the correct order as they are performed whilewriting the algorithm.Select one:TrueFalse
Answers
Answer:
False.
Explanation:
The correct option is false that is to say the arrangement is not true. So, let us check one or two things about the RSA System.
The RSA system simply refer to as a cryptosystem that was first established in the year 1973 but was later developed in the year 1977 by Ron Rivest, Adi Shamir and Leonard Adleman.
The main use of the RSA system is for encryption of messages. It is known as a public key cryptography algorithm.
The way the algorithm should have been arranged is;
(1). Randomly select two large prime numbers p and q, which always must bekept secret.
(2). Determine the product n = pq, known as public modulus.
(3). Select an integer number E, known as the public exponent, such that (p 1)and E have no common divisors, and (q 1) and E have no commondivisors.
(4). Determine the private exponent, D, such that (ED 1) is exactly divisible by both (p 1) and (q 1). In other words, given E, we choose D such that the integer remainder when ED is divided by (p1)(q 1) is 1.
(5). Release publicly the public key, which is the pair of numbers n and E, K =(n, E). Keep secret the private key, K = (n, D).
Therefore, The way it should have been arranged in the question should have been;
(1) , (4), (2), (3 ) and ( 5).
which of the following is an example of application software

Answers
Answer:
A messaging app
Explanation:
Its an software application you can download, so...yeah.
(You might've thought it was an anti-virus program lol)
Option-D.A messaging app is the correct answer.
A messaging app is an application software that can be installed jn your phone and computer in order to send messages.
To learn about the DIfference between application software and Opertaing system click here-
https://brainly.com/question/17798901
#SPJ2
g Write an UPDATE statement that changes the address for the row with vendor_id 4 so the suite number (Ste 260) is stored in vendor address instead of vendor address 1. Then, use SQL Developer to verify the change (you may need to click the Refresh button at the top of the Data tab to see the change). If this works correctly, go back to the tab for the UPDATE statement and click the Commit button to commit the change.
Answers
Answer:
UPDATE 'Vendors' SET 'address' = 'Ste 260' WHERE 'vendor_id' = 4
Explanation:
Required
Write an update statement
The question is incomplete as the table name is not given.
So, I will make the following assumptions.
Table name = Vendors
So, the update statement is:
UPDATE 'Vendors' SET 'address' = 'Ste 260' WHERE 'vendor_id' = 4;
The above statement queries the vendors table and changes the address of vendor_id 4 from the initial value to Ste 260
Which of these ports listed is the fastest? IEEE 1394 USB2.0 FIREWIRE ESATA
Answers
The port which is the fastest is ESATA.
What is ESATA?eSATA can be described as the SATA connector which can be access from outside the computer and it help to give the necessary signal connection that is needed for external storage devices.
The eSATA serves as a version of the eSATA port which is been regarded as the External SATA port, therefore, The port which is the fastest is ESATA.
Read more on the port here:
https://brainly.com/question/16397886
#SPJ1
2) How should you transcribe a spelled word?
a) It is transcription.
b) It is transcription. TRANSCRIPTION.
c) It is transcription. T-R-A-N-S-C-R-I-P-T-I-O-N.
d) It is transcription. T.R.A.N.S.C.R.I.P.T.I.O.N.
T_R_A_N_S_C_RIPTION.
Answers
The ways to you can transcribe a spelled word is that :
Option c) It is transcription. T-R-A-N-S-C-R-I-P-T-I-O-N.What is transcription?This is known to be a depiction in writing of the real pronunciation of a speech sound, word, or any form of piece of continuous text.
Note that the definition of a transcription is seen as anything or something that is known to be fully written out, or the act of of fully writing something out.
Transcription is known to be one that can be done word for word and there seems to be two kinds of transcription practices which is verbatim and clean read type of transcription. In Verbatim kind, one do transcribes a given text word-for-word.
Therefore, The ways to you can transcribe a spelled word is that :
Option c) It is transcription. T-R-A-N-S-C-R-I-P-T-I-O-N.Learn more about transcription from
https://brainly.com/question/3604083
#SPJ1
Write a C++ program that displays the total running time of a given algorithm based on
different situations such as processor speed, input size, processor load, and software
environment (DOS and Windows).
Answers
Answer: Your welcome!
Explanation:
#include <iostream>
#include <cmath>
using namespace std;
int main()
{
int processorSpeed; //in MHz
int inputSize; //in Kb
int processorLoad; //in %
int softwareEnvironment; //1: DOS, 2: Windows
int runningTime; //in ms
cout << "Enter processor speed (MHz): ";
cin >> processorSpeed;
cout << "Enter input size (Kb): ";
cin >> inputSize;
cout << "Enter processor load (%): ";
cin >> processorLoad;
cout << "Enter software environment (1-DOS, 2-Windows): ";
cin >> softwareEnvironment;
if(softwareEnvironment == 1)
{
//DOS running time calculation
runningTime = (inputSize / processorSpeed) + (processorLoad / 10);
}
else
{
//Windows running time calculation
runningTime = (inputSize / (processorSpeed/2)) + (processorLoad / 10);
}
cout << "Total running time: " << runningTime << "ms" << endl;
return 0;
}
A company has created a form that will be used to submit quarterly earnings. The form is created in a workbook. How should it be saved so that all employees can open this form, input their data, and turn it in?
It should be saved as an Excel workbook.
It should be saved as XML data.
It should be saved as an Excel template.
It should be saved as a web page.
Answers
Because there can be a lot of different analyses of entered information. And the most technologies are working in GSPR networks
What causes them to catch your attention in advertisements?
Answers
Answer:
advertisement should be nice and attractive to get attention of people
Work out and List the Big-Oh notation that corresponds to each of the following examples. Afterwards, list them by the order of complexity from LEAST to MOST.
(1.1) A bacteria that doubles itself every generation N.
(1.2) Following a single path along a branching story with N choices that change the story until you reach an ending.
(1.3) Pulling a single ball out of a pit filled with N balls.
(1.4) Searching the N rooms in a house for your keys.
(1.5) Trying to route a band’s world tour through N cities with the shortest mileage possible.
(1.6) Breaking an equation with N pieces down into smaller, simpler pieces, then solving those pieces to solve the entire equation.
Answers
An example of an O(2n) function is the recursive calculation of Fibonacci numbers. O(2n) denotes an algorithm whose growth doubles with each addition to the input data set. The growth curve of an O(2n) function is exponential - starting off very shallow, then rising meteorically.This function runs in O(n) time (or "linear time"), where n is the number of items in the array.
If the array has 10 items, we have to print 10 times. If it has 1000 items, we have to print 1000 timesHere we're nesting two loops. If our array has n items, our outer loop runs n times and our inner loop runs n times for each iteration of the outer loop, giving us n2 total prints.
Thus this function runs in O(n2) time (or "quadratic time"). If the array has 10 items, we have to print 100 times. If it has 1000 items, we have to print 1000000 times.An example of an O(2n) function is the recursive calculation of Fibonacci numbers. O(2n) denotes an algorithm whose growth doubles with each addition to the input data set.
The growth curve of an O(2n) function is exponential - starting off very shallow, then rising meteorically.When you're calculating the big O complexity of something, you just throw out the constantsThis is O(1 + n/2 + 100), which we just call O(n).
Why can we get away with this? Remember, for big O notation we're looking at what happens as n gets arbitrarily large. As n gets really big, adding 100 or dividing by 2 has a decreasingly significant effect.
O(n3 + 50n2 + 10000) is O(n3)O((n + 30) * (n + 5)) is O(n2)
Again, we can get away with this because the less significant terms quickly become, well, less significant as n gets big.
hope it helps you.....*_*
Help is greatly appreciated! I need a step but step explanation and a startup would be perfect.


Answers
The point we should pay attention to in this section is the following;
The type of the variable that we will store the temperature from the user must be a float. Because in the formula we will use, an integer is not generated for every integer we give.Below is the Python Code of this problem with comments added.
#Variables we need to store the data from user.
city = input("Enter the city name: ")
temperature_celcius = float(input("Enter the current temperature in Celcius: "))
#Calculation section by using the formula.
temperature_fahrenheit = (temperature_celcius * 9/5) + 32
#Inform the user.
print(f"The current temperature in {city} is {temperature_celcius}°C, which is {temperature_fahrenheit}°F.")

What is the grooming process as it relates to online predators
Answers
the process by which online predators lure in minors to get close enough to hurt them.
2.
a.
b.
c.
d.
What is the answer to the following calculation: (4+6)*2-10/2? Select the correct option.
5
3
15
-30
Help please
Answers
Answer:
15
Explanation:
(4+6) x 2-10/2
10 x 2 - 10/2
10 x 2 - 5
20 - 5
15
The given problem is solve by the BODMAS Rule. So, the final result of the given equation is 15. Thus, the correct option is c.
What is BODMAS Rule?The BODMAS Rule is the mathematical method for solving a complex equation that involves multiple steps. The steps involved in the BODMAS Rule are:
BracketsDivisionMultiplicationAdditionSubtractionComputation:
(4+6) x 2-10/2
10 x 2 - 10/2
10 x 2 - 5
20 - 5
15
Therefore, the correct option is c. 15.
Learn more about BODMAS Rule, here:
https://brainly.com/question/23827397
#SPJ2
Balance is the design principle that is represented when using the Crop tool?

Answers
Answer:
The answer is "False".
Explanation:
The rule of thirds implies to the subject, which is not centered mostly on the picture because of new photography formats their shots. Its main object is a little off with one side by using a third-party principle, which draws your attention for the audience into another design, instead of only looking at the center. In another word, we can say that this rule is used as the definition to design the Crop tool to represent as an overlay.
Can someone please help me with 6.8 Code Practice adhesive.
Answers
Answer:
I'm looking for this one too
Answer:
import simplegui
import random
# global constants
WIDTH = 600
HEIGHT = 400
PARTICLE_RADIUS = 5
COLOR_LIST = ["Red", "Green", "Blue", "White"]
DIRECTION_LIST = [[1,0], [0, 1], [-1, 0], [0, -1]]
# definition of Particle class
class Particle:
# initializer for particles
def __init__(self, position, color):
self.position = position
self.color = color
# method that updates position of a particle
def move(self, offset):
self.position[0] += offset[0]
self.position[1] += offset[1]
# draw method for particles
def draw(self, canvas):
canvas.draw_circle(self.position, PARTICLE_RADIUS, 1, self.color, self.color)
# string method for particles
def __str__(self):
return "Particle with position = " + str(self.position) + " and color = " + self.color
# draw handler
def draw(canvas):
for p in particle_list:
p.move(random.choice(DIRECTION_LIST))
for p in particle_list:
p.draw(canvas)
# create frame and register draw handler
frame = simplegui.create_frame("Particle simulator", WIDTH, HEIGHT)
frame.set_draw_handler(draw)
# create a list of particles
particle_list = []
for i in range(100):
p = Particle([WIDTH / 2, HEIGHT / 2], random.choice(COLOR_LIST))
particle_list.append(p)
# start frame
frame.start()
Explanation:
this worked for me, sorry if its to late. let me know if anything is wrong
Develop a c program to display the following input output interphase enter a number 5
The table of 5 is
5*1=5
5*2=10
Answers
Answer:
int main()
{
int number;
printf("Enter a number: ");
scanf_s("%d", &number, sizeof(number));
for (int i = 1; i <= 2; i++) {
printf("%d*%d=%d\n", number, i, number * i);
}
}
Explanation:
I used the safe scanf_s() that takes a third parameter to indicate the size of the buffer. In this case it is the size of an integer.
A motor takes a current of 27.5 amperes per leaf on a 440-volt, three-phase circuit. The power factor is 0.80. What is the load in watts? Round the answer to the nearer whole watt.
Answers
The load in watts for the motor is 16766 watts
To calculate the load in watts for the given motor, you can use the following formula:
Load (W) = Voltage (V) × Current (I) × Power Factor (PF) × √3
In this case:
Voltage (V) = 440 volts
Current (I) = 27.5 amperes per phase
Power Factor (PF) = 0.80
√3 represents the square root of 3, which is approximately 1.732
Now, plug in the values:
Load (W) = Voltage (V) × Current (I) × Power Factor (PF) × √3
Load (W) = 440 × 27.5 × 0.80 × 1.732
Load (W) = 16765.7 watts
Rounded to the nearest whole watt, the load is approximately 16766 watts.
Know more about the motor here :
https://brainly.com/question/29713010
#SPJ11
find four
reasons
Why must shutdown the system following the normal sequence
Answers
If you have a problem with a server and you want to bring the system down so that you could then reseat the card before restarting it, you can use this command, it will shut down the system in an orderly manner.
"init 0" command completely shuts down the system in an order manner
init is the first process to start when a computer boots up and keep running until the system ends. It is the root of all other processes.
İnit command is used in different runlevels, which extend from 0 through 6. "init 0" is used to halt the system, basically init 0
shuts down the system before safely turning power off.
stops system services and daemons.
terminates all running processes.
Unmounts all file systems.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1
working with the tkinter(python) library
make the window you create always appear on top of other windows. You can do this with lift() or root.attributes('-topmost', ...), but this does not apply to full-screen windows. What can i do?
Answers
To make a tkinter window always appear on top of other windows, including full-screen windows, you must use the wm_attributes method with the topmost attribute set to True.
How can I make a tkinter window always appear on top of other windows?By using the wm_attributes method in tkinter and setting the topmost attribute to True, you can ensure that your tkinter window stays on top of other windows, even when they are in full-screen mode.
This attribute allows you to maintain the window's visibility and prominence regardless of the current state of other windows on your screen.
Read more about python
brainly.com/question/26497128
#SPJ1
Modify your main.c file so that it allocates a two dimensional array of integers so that the array has 20 rows of 30 integers in each row. Fill up the entire array so that the first row contains 0-29 the second row contains 1-30, the third row contains 2-31 and so on until the last row contains 19-48. Print the results in a grid so that your output looks like:
Answers
Answer:
Explanation:
b
When working with a shared worksheet, how do you know it's shared?
The word "Shared is saved in the name of the file.
The email in which you received the file says "Shared."
The word "Shared" appears after the workbook title in the title bar.
The word "Shared" appears at the bottom next to the worksheet tabs.
Answers
Answer:
The Word shared appers in the email and appears next to the worksheet tab
Explanation:
Hope this answers your question :)
Answer:
C
Explanation:
hope this helps :)
2. What is the implication of media killings in the Philippines?
Answers
Answer:
Throughout the clarification below, the description of the query is mentioned.
Explanation:
In the Philippines, the Implication of media indicates that perhaps the Philippines isn't a safe environment for reporters, and therefore more remains to be improved to change this pattern.But it didn't start underneath Duterte before you could even say that, as well as he didn't order strikes. If he had instructions in which he would criticize, for perhaps a long period presently Ressa had died as one of his other very resolute and influential media commentators.Which phrase or phrases suggest a security issue in data mining?
Travis often BUYS BUSINESS BOOKS ONLINE. Recently, he LOGGED INTO THE WEBSITE to buy a marketing book. He noticed a part on the screen that RECOMMENDED BOOKS BASED ON HIS BROWNING HISTORY. Due to this recommendation, Travis could easily locate the book. A few days later, he FOUND BOOK RECOMMENDATIONS FROM UNKNOW SOURCES. Eventually, he STARTED GETTING SPAM EMAIL FROM THESE SOURCES.
Answers
Based on web search results, data mining security issues are related to the protection of data and its resources from unauthorized access, misuse, or theft. Some of the factors that can suggest a security issue in data mining are:
- Data provenance: The source and history of the data should be verified and traced to ensure its authenticity and integrity.
- Access controls: The identity of the person or system accessing the data should be verified and authorized to prevent unauthorized access.
- Data anonymization: The sensitive or private information in the data should be masked or removed to protect the privacy of individuals or entities.
- Data storage location: The location where the data is stored should be secure and compliant with the relevant laws and regulations.
- Distributed frameworks: The data should be encrypted and protected when it is transferred or processed across different nodes or systems.
Based on these factors, the phrase or phrases that suggest a security issue in data mining in your question are:
- FOUND BOOK RECOMMENDATIONS FROM UNKNOWN SOURCES
- STARTED GETTING SPAM EMAIL FROM THESE SOURCES
These phrases indicate that the data provenance and access controls were compromised, and that the data was exposed to unauthorized parties who could misuse it for malicious purposes.
What are not type of analytical procedures?
A
Spreadsheet analysis
B
Trend analysis
C
Ratio analysis
D
Reasonable testing
Answers
Answer:
A) spreadsheet analysis
Explanation:
Hope this helps
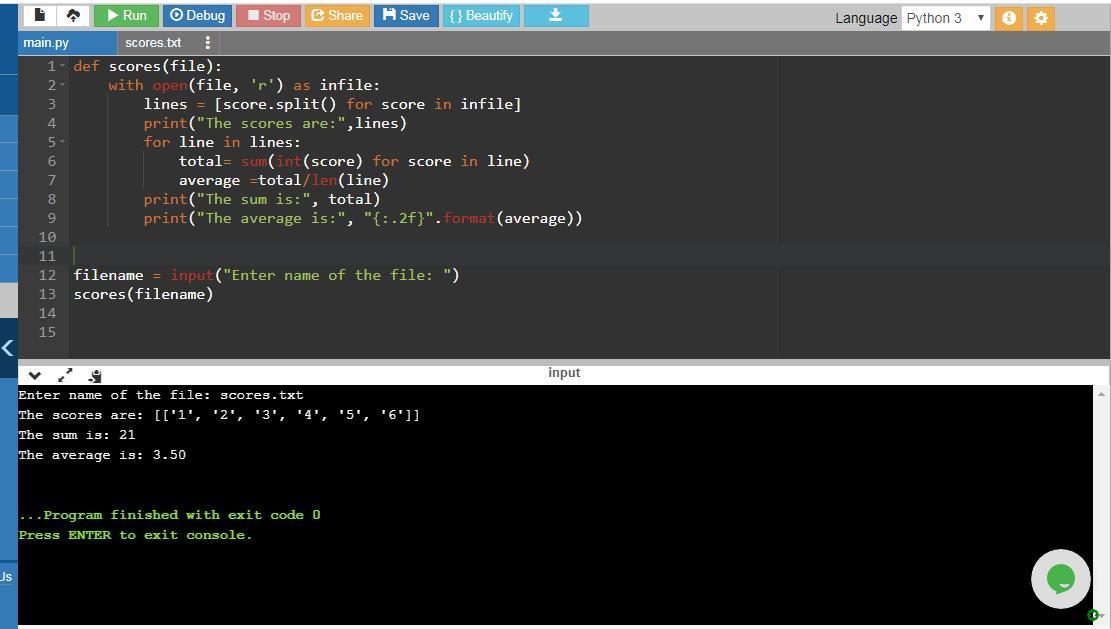
(Process scores in a text file) Suppose that a text file contains an unspecified number of scores. Write a program that reads the scores from the file and displays their total and average. Scores are separated by blanks. Your program should prompt the user to enter a filename. Here is a sample run:
Answers
Answer:
Here is the Python program:
def scores(file): # method scores that takes a file name as parameter and returns the sum and average of scores in a file
with open(file, 'r') as infile: # open the file in read mode
lines = [score.split() for score in infile] # split the scores into a list
print("The scores are:",lines) #print the scores
for line in lines: # loops through each score
total= sum(int(score) for score in line) # adds the scores
average =total/len(line) # computes average by taking sum of scores and dividing by number of scores in file
print("The sum is:", total) #prints the sum of scores
print("The average is:", "{:.2f}".format(average)) #prints the average
filename = input("Enter name of the file: ") #prompts user to enter name of file
scores(filename) #calls scores method by passing the file name to it in order to compute sum and average of file contents i.e. scores
Explanation:
It is assumed that the scores in the file are separated by a blank space.
The scores() method takes a file name as parameter. Then it opens that input file in read mode using object infile.
split() method is used to split the scores in a file into a list. Suppose the scores are 1 2 3 4 5 6 . So after the split, they become ['1', '2', '3', '4', '5', '6']
The loop iterates through each score in the file, splits them into a list and stores this list in lines. The next print statement prints these scores in a list.
The second loop for line in lines iterates through each score of the list and the statements: total= sum(int(score) for score in line) and average =total/len(line) computes the total and average of scores.
total= sum(int(score) for score in line) statement works as follows:
for loop iterates through each element of list i.e. each score
int() converts that string element into integer.
sum() method adds the integers to compute their total.
So if we have ['1', '2', '3', '4', '5', '6'] each element i.e. 1,2,3,4,5,6 is converted to integer by int() and then added together by sum method. So this becomes 1+2+3+4+5+6 = 21. This result is stored in total. Hence
total = 21.
average = total/len(line) works as follows:
The computed sum of scores stored in total is divided by the number of scores. The number of scores is computed by using len() method which returns the length of the line list. So len() returns 6. Hence
average = total/len(line)
= 21 / 6
average = 3.5
The next two print statement prints the value of sum and average and "{:.2f}".format(average)) prints the value of average up to 2 decimal places.
The screenshot of the program along with its output is attached.
What are some of the ways that people communicate or share with others over digital
media?
Answers
Answer:
Social networks, apps, websites.
Explanation:
Social media allows others to talk during the pandemic! Weather or not its "Tik-tak" or "Facebok", "Twiter", etc. Social media has made a huge impact on our society as we know it. Social media has broadened our social life now that we can call each other and see each other digitally while a county away. Or even share something on the internet to a million different eyes! Social media also has negative impacts such as cyberbullying and other things.
~ LadyBrain
A poetry reading is a type of
A. performance
B. blog
C. installation
D. zine
Answers
Which phrase best describes a scenario in Excel 2019?
O a type of what-if analysis that allows a user to define a single variable for a single function or formula
O a type of what-if analysis that allows a user to define multiple variables for multiple functions or formulas
a type of chart analysis that allows a user to predict outcomes using data
O a type of chart analysis that allows a user to set predetermined outcomes using data
Answers
Answer:
a type of what-if analysis that allows a user to define multiple variables for multiple functions or formulas.
Explanation:
Answer:
B
Explanation:
NP
Write a program that receives a series of numbers from the user and allows the user to press the enter key to indicate that he or she is finished providing inputs. After the user presses the enter key, the program should print the sum of the numbers and their average.
Answers
The program that receives a series of numbers from the user is:
theSum = 0.0
# stores the number of terms entered by the user
n = 0
# loop until user presses the enter key
# infinite loop
while True:
# get user input from user
data = input("Enter a number or press Enter to quit: ")
# if user presses enter
if data == '':
# break out of the loop
break
# convert data into float using float()
number = float(data)
# add the entered number to theSum
theSum += number
# increase the number of terms
n += 1
print()
print("The sum is", theSum)
# if numbers of terms entered are greater than 0
if n > 0:
# calculate average
average = theSum / n
print('The average is', average)
# if no terms are entered
else:
print('Average : undefined (as the number of terms entered are 0)')
What is a program?A computer program is a set of instructions written in a programming language that a computer is supposed to obey.
Computer programs are one of the intangible components of the software, which also includes documentation and other components. The version of a computer program that humans can read is called the source code.
Learn more about program on;
https://brainly.com/question/23275071
#SPJ1

Write a SELECT statement that returns these columns from the Orders table:
The order_date column
A column that uses the DATE_FORMAT function to return the four-digit year that’s stored in the order_date column
A column that uses the DATE_FORMAT function to return the order_date column in this format: Mon-DD-YYYY. In other words, use abbreviated months and separate each date component with dashes.
A column that uses the DATE_FORMAT function to return the order_date column with only the hours and minutes on a 12-hour clock with an am/pm indicator
Answers
Answer:
see below
Explanation:
SELECT date_format(order_date,"%Y"), date_format(order_date,"%a-%d-%Y"), date_format(order_date,"%r")
Database systems are exposed to many attacks, including dictionary attack, show with implantation how dictionary attack is launched?(Java or Python) ?
Answers
A type of brute-force attack in which an intruder uses a "dictionary list" of common words and phrases used by businesses and individuals to attempt to crack password-protected databases.
What is a dictionary attack?
A Dictionary Attack is an attack vector used by an attacker to break into a password-protected system by using every word in a dictionary as a password for that system. This type of attack vector is a Brute Force Attack.
The dictionary can contain words from an English dictionary as well as a leaked list of commonly used passwords, which, when combined with common character replacement with numbers, can be very effective and fast at times.
To know more about the dictionary attack, visit: https://brainly.com/question/14313052
#SPJ1