ROM Design-4: Look Up Table Design a ROM (LookUp Table or LUT) with three inputs, x, y and z, and the three outputs, A, B, and C. When the binary input is 0, 1, 2, or 3, the binary output is 2 greater than the input. When the binary input is 4, 5, 6, or 7, the binary output is 2 less than the input. (a) What is the size (number of bits) of the initial (unsimplified) ROM? (b) What is the size (number of bits) of the final (simplified/smallest size) ROM? (c) Show in detail the final memory layout.
Answers
a) The size of the initial (unsimplified) ROM is 24 bits. b) The size of the final (simplified/smallest size) ROM is 6 bits.
a) The initial (unsimplified) ROM has three inputs, x, y, and z, which means there are 2^3 = 8 possible input combinations. Each input combination corresponds to a unique output value. Since the ROM needs to store the output values for all 8 input combinations, and each output value is represented by a binary number with 2 bits, the size of the initial ROM is 8 * 2 = 16 bits for the outputs, plus an additional 8 bits for the inputs, resulting in a total of 24 bits. b) The final (simplified/smallest size) ROM can exploit the regular pattern observed in the output values. Instead of storing all 8 output values, it only needs to store two distinct values: 2 greater than the input for binary inputs 0, 1, 2, and 3, and 2 less than the input for binary inputs 4, 5, 6, and 7. Therefore, the final ROM only needs 2 bits to represent each distinct output value, resulting in a total of 6 bits for the outputs. The inputs can be represented using the same 8 bits as in the initial ROM.
Learn more about ROM here:
https://brainly.com/question/31827761
#SPJ11
Related Questions
A positive integer is called a perfect number if it is equal to the sum of all of its positive divisors, excluding itself. For example, 6 is the first perfect number because 6 = 3 + 2 + 1. The next is 28 = 14 + 7 + 4 + 2 + 1. There are four perfect numbers less than 10,000. Write a program to find all these four numbers.
Answers
i = 1
while i < 10001:
total = 0
x = 1
while x < i:
if i % x == 0:
total += x
x+=1
if total == i:
print(str(i)+" is a perfect number")
i += 1
When you run this code, you'll see that 6, 28, 496, and 8128 are all perfect numbers.
computer searches and physical asset counts usually focus on the element of the fraud triangle.
Answers
Computer searches and physical asset counts usually focus on the Concealment element of the fraud triangle.
What do you know about Computer search?
A search is a function or process for locating letters, words, files, web pages, or other data. It is also referred to as seek on occasion. A search or find feature can be found in many operating systems, software packages, and websites to locate data.
What is Physical asset?
Physical assets have a very recognizable physical presence, are visible and touchable, and can be seen and handled. Intangible economic resources such as land, buildings, machinery, plants, tools, equipment, cars, gold, silver, or any other type are examples of such physical assets.
What is Concealment?
The act of concealment occurs when information that should be disclosed and might otherwise impact the terms or construction of a contract is purposefully or inadvertently withheld. A concealing might take the form of obfuscation or the withholding of crucial information.
Learn more about physical asset click here:
https://brainly.com/question/28018001
#SPJ4
4. How could you apply some of the ideas, principles, or structures of coding to fields of study, industries, or tasks outside of creating computer programs? Propose at least one way to use "coding" or creating programs outside of computer science and explain how it uses coding-related concepts.
Answers
Answer:
a production plant
Explanation:
"Coding" brings with it a linear way of thinking and problem solving, where one step needs to be taken before moving on to the next step. This can be applied to a wide range of real-life scenarios and industries. For example, a production plant starts with an initial input, that input is taken and used in a set of instructions (method), those instructions take that input and create a new output. Once the new output is created it is then passed on to another set of instructions that takes that output as an input to create a new output. Just like a computer program, a power plant repeats this process in order to a fully working and realized product.
Most often you will _____ to a container using the local keyboard and console.Select one:
a.send controls
b.attach
c.send data
d.send scripts
Answers
Most often, you will attach to a container using the local keyboard and console. So, option b is correct.
When working with containers, attaching to the container's console allows you to interact with the container's shell or command-line interface directly. This enables you to execute commands, monitor processes, and troubleshoot issues within the container.
Using the local keyboard and console, you can input commands and receive the corresponding output in real-time. This direct interaction is particularly useful during container setup, configuration, and troubleshooting, as it provides immediate feedback and allows for precise control over container operations.
The other options listed are not typically associated with attaching to a container using the local keyboard and console.
- Sending controls (a) generally refers to managing container operations remotely through control signals or APIs, rather than direct console interaction.
- Sending data (c) typically involves transferring data to or from a container using various methods such as file transfers or network protocols.
- Sending scripts (d) implies executing scripts within the container, which can be done through console interaction or other means, but it is not specifically related to attaching to a container using the local keyboard and console.
Therefore, the most appropriate action for interacting with a container using the local keyboard and console is to attach to it.
So, option b is correct.
Learn more about console:
https://brainly.com/question/30267460
#SPJ11
kristin's position in it focuses on using antivirus, anti-spyware, and vulnerability software patch management in order to maintain security and integrity. which it infrastructure domain is she protecting?
Answers
She is protecting LAN-to-WAN domain data link. The technical framework that joins a LAN and a wide area network in an organization is known as the LAN-to-WAN Domain (WAN).
The technical framework that links a company's local area network to its wide area network is referred to as the LAN-to-WAN domain (WAN). Controlling network traffic between the private network, or LAN, and the public network, or WAN, is the key issue. For many enterprises, the LAN-to-WAN domain designates their connection to the Internet. There is a big risk associated with this link. The configuration of devices in LAN-to-WAN security standards is frequently centered on preserving message and transaction integrity. Securing point-to-point connections is a crucial aspect of connectivity over the Internet.
The technical framework that joins a LAN and a wide area network in an organization is known as the LAN-to-WAN Domain (WAN). Controlling network traffic between the private network, or LAN, and the public network, or WAN, is the key concern. For many enterprises, the LAN-to-WAN Domain designates their connection to the Internet. There is a big risk associated with this link.
To know more about LAN-to-WAN click on the link:
https://brainly.com/question/13718390
#SPJ4
Unlike when writing in a programming language, there are no set rules that must be followed when writing pseudocode. What do you think are some good guidelines to follow when writing pseudocode? Why are these guidelines important?
Answers
Answer:
Explanation:
Pseudocode may not have a set number of rules of guidelines but there are still some habits that should be followed. This includes having only one statement per line and add the END keyword to loops. Both of these rules/habits will drastically increase the readability of the pseudocode and allow you to know exactly where a certain loop starts and ends. Since loops can become difficult to read if they have a lot of code within them. Another good guideline to keep in mind is to simplify the code as much as possible do not add unnecessary pseudocode if it is not absolutely needed.
An array of int named a that contains exactly five elements has already been declared and initialized. In addition, an int variable j has also been declared and initialized to a value somewhere between 0 and 3. Write a single statement that assigns a new
Answers
Answer:
a[j] = 2 * a[j+1];
Explanation:
The complete statement is to Write a single statement that assigns a new value to the element of the array indexed by j. This new value should be equal to twice the value stored in the next element of the array.
So lets say a is an array of type int which is already declared and initialized.
int a[] = {};
declare an int variable j as int j;
The element of array a indexed by j can be represented as a[j] This means the j-th index of array a
The value to be assigned to a[j] is 2 * a[j+1]; with an assignment operator "= " between a[j] and 2 * a[j+1]; in order to assign 2 * a[j+1]; to a[j]
According to the requirement this new value should be twice the value stored in next element of array. The next element of array is represented by a[j+1] which means j+1 index of array a. This means the element at j+1 index that comes after the element at j-th index a[j].
Value should be twice the value stored in next element of array means multiply the 2 with the next element of array i.e. a[j+1]
Now assign this new value 2 * a[j+1]; to a[j].
write a line of code that prompts the user for his or her name and saves the user's input in a variable called name.
Answers
Python's input() function and print() function are used to read values from the console and show information there, respectively. The code is
name = input("Enter your name:")
print(name)
Using Python, we get input from the user using the input() function and output is displayed on the screen using the print() function. Users can supply the application with any information in the form of texts or numbers by using the input() function.
The specified message is shown on the screen via the print function. For example, print ("Hello") produces the word Hello. In contrast, input functions receive provided data. For instance, the output of input = "Enter your age:" is Enter your age, and your age is taken into account when you press the Enter key.
To learn more about console click here:
brainly.com/question/23903078
#SPJ4
Nina is trying to learn more about how computers work. She has repeatedly read that the motherboard is the "brain” of the computer.
Nina has learned that the motherboard is considered the brain because it
stores all of the computer’s information.
enables the computer to function.
processes the data on the computer.
guides the computer’s activities.
Answers
\(\huge\boxed{Enables\;the\;computer\;to\;function.}\)
The motherboard is the part in the computer that allows the computer to function correctly. Without it, none of the computer pieces could interact.
Nina has learned that the motherboard is considered the brain because it enables the computer to function, hence option B is correct.
What is the function of the motherboard?The circuit board determines the kinds of storage devices, memory modules, and graphics cards (among other expansion cards) that can connect to your PC. It also distributes electricity from your power supply and links all of your hardware to your processor.
The motherboard of the computer contains the central processing unit (CPU), also known as a processor. It executes commands and is sometimes referred to as the computer's brain. You provide the CPU instructions every time you touch a key, click the mouse, or launch an application.
Therefore, the motherboard is considered the brain of the computer.
Learn more about motherboards, here:
https://brainly.com/question/29834097
#SPJ2
Why must web designers select a common font?
Answers
to ensure visitors can view it
to keep the page consistent
to make the page easier to read
Which three of the following will be printed?
c = 7
while (c > 0):
print(c)
c = c - 3
Group of answer choices
0
1
3
4
5
6
7
Answers
In the above code snippet, The following numbers will be printed:
7
4
1
What is the explanation for the above?The initial value of c is 7, which is greater than 0, so the loop starts. The print(c) statement inside the loop prints the current value of c, which is initially 7. Then, the statement c = c - 3 subtracts 3 from the current value of c, so c becomes 4.
On the second iteration of the loop, the condition c > 0 is still true, so the loop continues. The print(c) statement inside the loop prints the current value of c, which is now 4. Then, the statement c = c - 3 subtracts 3 from the current value of c, so c becomes 1.
On the third iteration of the loop, the condition c > 0 is still true, so the loop continues. The print(c) statement inside the loop prints the current value of c, which is now 1. Then, the statement c = c - 3 subtracts 3 from the current value of c, so c becomes -2.
On the fourth iteration of the loop, the condition c > 0 is false, because c is now -2, so the loop ends. Therefore, only 7, 4, and 1 will be printed.
Learn more about code at:
https://brainly.com/question/30772469
#SPJ1
A coworker is taking a computer overseas and asks you what concerns he should have. What do you tell him
Answers
Answer:
The components within the computer can get damage during travel, so he could improve the box protection with foam thingies
Explanation:
"Cloud suites are stored on your hard drive and are available anywhere you can access the internet.
true/false:
Answers
Cloud suites are stored on your hard drive and are available anywhere you can access the internet, is the true statement.
What is Cloud suites?Cloud suites are accessible from any location with Internet connectivity and are stored on your hard drive. The most typical components of database management systems include functions, formulas, charts, and what-if analysis. Software for creating presentations with graphics is a great way to influence people and convey a message.
Many apps are designed to function on a specific type of mobile device and cannot be used with other types. An assortment of connected data is called a database.
Thus, it is the true statement.
For more information about Cloud suites, click here:
https://brainly.com/question/5413035
#SPJ1
which ip addressing process enables workstations to use private ip addresses to access the internet?
Answers
NAT Before transferring the data, it is a way to map several local private addresses to a public one.
What is NAT ?By changing the network address information in packets' IP headers as they travel through a traffic routing device, network address translation is a technique for mapping one IP address space into another.
When a network was moved or when the upstream Internet service provider was changed but was unable to route the network's address space, the technique was initially employed to avoid the requirement to give new addresses to every site.
In light of the IPv4 address exhaustion, it has grown to be a widely used and crucial technique for global address space preservation.
NAT implementations may differ in their specific behaviour in different addressing cases and their impact on network traffic because NAT modifies the IP address information in packets. Vendors of equipment with NAT implementations do not frequently document the specifics of NAT behavior.
To learn more about NAT refer :
https://brainly.com/question/13105976
#SPJ4
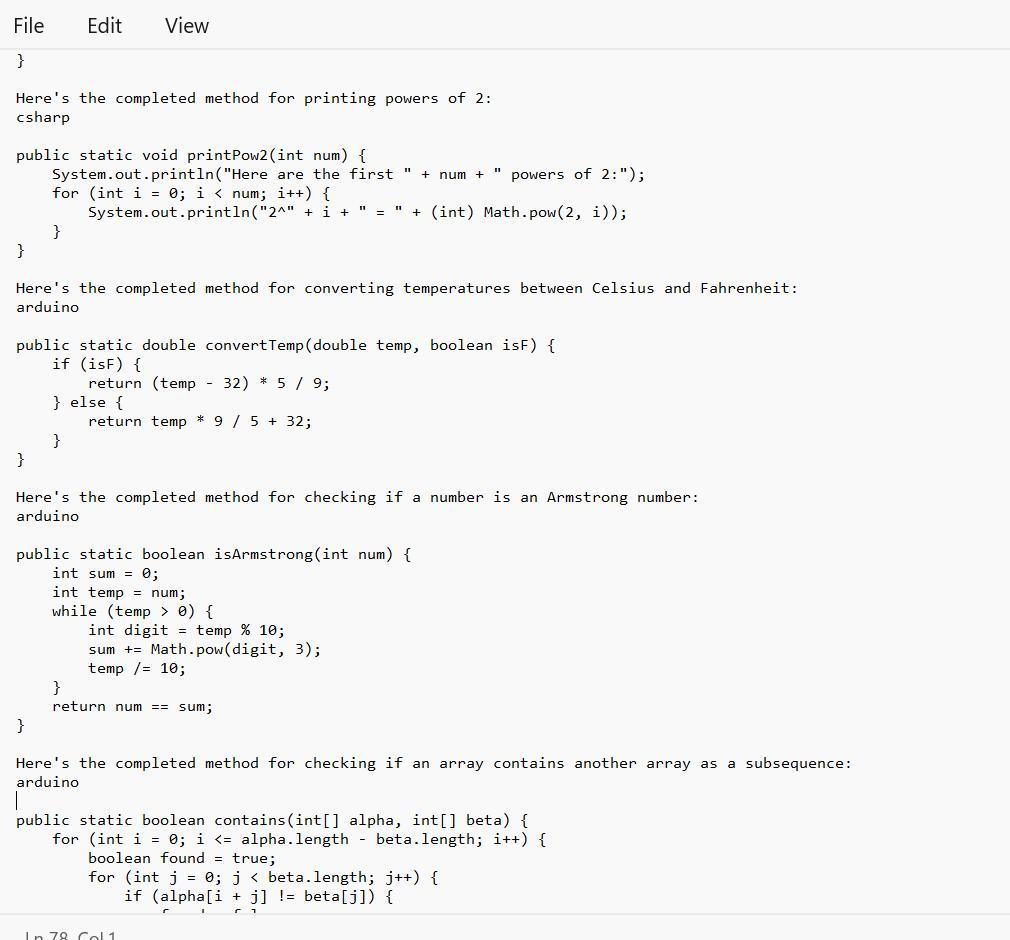
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


What technique do API developers most commonly use to limit access to an API to authorised individuals and applications?
Answers
Answer:
API keys
Explanation:
API (Application Programming Interface) is a computing interface that defines the interaction between multiple software intermediaries.
API key is a specific identifier use authenticate the developer user and call programs for the API.
The API keys often serve as a specific identifier and a secret token for authentication, and usually have a set of access rights to the API associated with it.
These are commonly used to authenticate a project with an API instead of a human user. Different platforms can execute and use API keys in different ways.
Computational artifacts can include various forms of bias that result in the _____
of certain groups of people.
Answers
Answer:
Exclusion
Explanation:
Right on Egenuity
Answer:Below
Explanation:

Python please help.
Why I’m i getting this error

Answers
So, age is a of type string when it should be of type int.
def main():
age = int(input("How old are you? "))
if age >= 13:
#the rest of your code.
Strings cannot be greater than another string only integers and other number based data types. Also, you should change the list variable as I mentioned on the earlier question. Best of luck.
PLZ HURRY TIMED 20 POINTS + BRAINLEIST
Describe a situation where video conferencing software would make things easier for a business.
Answers
Answer:
Corona Virus
Explanation:
Perdón necesito los puntos, te quiero
which country has the most common features of analogue and digital computer
Answers
Explanation:
i don't think rhis question could be..
What do Cc and Bcc stand for?
O Clear Copy and Binary Clear Copy
O Counter Claim and Best Counter Claim
O Crystal Clear and Binary Crystal Clear
O Carbon Copy and Blind Carbon Copy
Answers
Thank You!
why ada lovelace is known as first computer programmer ?
Answers
Answer:
Ada Lovelace, is known as the fist computer programmer because she was the one who proposed / invented computer programming.
Basically the first person to realize that the analytical engine could "perform arbitrary tasks and wrote programs for those arbitrary task, beyond computational operations."
Hope this helps :)
as a member of the help desk team, you have been assigned to update the driver for the network adapter that is installed on most of the computers in your department. you have a copy of the latest driver on a usb flash drive. which windows utility allows you to manually update this new driver?
Answers
To manually update the network adapter driver in Windows, use the Device Manager utility to browse for the new driver on the USB flash drive and install it.
To manually update the network adapter driver in Windows, you can use the Device Manager utility. To access it, you can right-click the Start button and select "Device Manager" from the context menu, or you can search for "Device Manager" in the Start menu or Cortana search bar. Once in Device Manager, find the network adapter for which you want to update the driver, right-click it and select "Update Driver." From there, you can select "Look through my computer for driver software." and point the search to the USB flash drive's driver location.
After selecting the option to "Browse my computer for driver software," you will be prompted to specify the location of the driver. Navigate to the folder on the USB flash drive where you have saved the new driver and select it. Windows will then install the updated driver for the network adapter.
It's worth noting that before installing the new driver, it's always a good idea to backup your current driver and system configuration in case of any issues. Also, ensure that you have administrative rights on the computer and that the new driver is compatible with your specific version of Windows and the network adapter hardware.
Learn more about USB flash drive here:
https://brainly.com/question/4576943
#SPJ4
At which of the capability maturity model integration maturity levels, are processes well defined, understood, and consistent across the organization?.
Answers
At defined (quantitatively managed), the capability maturity model integration maturity levels, are processes well defined, understood, and consistent across the organization.
An organization's software development process can be developed and improved using the Capability Maturity Model (CMM). The model outlines a five-level evolutionary path of processes that get more ordered and systematic as they mature.
The Software Engineering Institute (SEI), a research and development facility supported by the U.S. Department of Defense (DOD) and now a part of Carnegie Mellon University, developed and promotes CMM. In order to address software engineering difficulties and, generally speaking, develop software engineering approaches, SEI was established in 1984.
More specifically, SEI was created to streamline the DOD's software-intensive system development, acquisition, and maintenance processes. SEI supports the widespread industrial use of CMM Integration (CMMI), a development of CMM. Additionally, the capability maturity model is still commonly employed.
CMM is comparable to ISO 9001, one of the International Organization for Standardization's ISO 9000 set of standards. The ISO 9000 standards outline an efficient quality system for the manufacturing and service sectors; ISO 9001 explicitly addresses the creation and upkeep of software.
To know more about Capability Maturity Model click on the link:
https://brainly.com/question/14595603
#SPJ4
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
whats ur favorite video game
Answers
Answer:
Minecraft has always been my favorite
Answer:
Far Cry 5. It has a great story line and it's lots of fun
Explanation:
The #elif and #else directives are provided as shorthand notation for the #if defined(name) and #if !defined(name).
True
False
Answers
Answer:
The answer is "False".
Explanation:
The shorthand notation operator is a quick way of expressing something, that can be accessed only in Java. In this, no function within computer programming language was introduced by shorthand procedures. In the given question, else and elif block were used, in which elif block used in python, that's why the given statement is false.
Who invented the television and what year did color come out? Explain
Answers
The television was not invented by a single person, but its development involved contributions from several inventors and engineers.
How is this so?Philo Farnsworth is often credited as one of the key inventors of television, as he successfully demonstrated the first working electronic television system in 1927.
As for color television, it was first introduced commercially in the United States in 1953 by RCA.
The introduction of color television marked a significant milestone in broadcasting, enhancing the viewing experience for audiences worldwide.
Learn more about television at:
https://brainly.com/question/12079773
#SPJ1
You are almost finished updating a Web site. As part of the update, you have converted all pages from HTML 4. 0 to HTML5. The project is currently on schedule. However, your project manager has been asked by the marketing team manager to justify a day of time spent validating the site's HTML5 pages. The marketing team manager does not have technical knowledge of the Internet or the Web. Which is the most appropriate explanation to provide to the marketing team manager?
Answers
The best explanation to provide to the marketing manager is that the team needs to verify that the website will appear as expected and should be run in as many browsers as possible.
Project manager is not only responsible to manage or execute the project in the organization but also responsible to collaborate with other teams in the same organization and this collaboration may be vertical and horizontal. As in this scenario, the project manager doesn't have time to spend with the marketing department, therefore, he is also responsible to collaborate with the marketing team. But the marketing team doesn't know the technical knowledge about HTML 5 or web terminologies etc. Therefore, the best explanation that project would give to the marketing team is that the website will appear and run as expected in different browsers as much as possible.
You can learn more about project HTML5 at
https://brainly.com/question/13408852
#SPJ4
In a category of games known as _________, millions of players connect to various servers to team up with other players in very large virtual worlds.
Answers
In a category of games known as MMORPGs, millions of players connect to various servers to team up with other players in very large virtual worlds.
What do MMORPGs mean?The term MMORPG connote massively multiplayer online role-playing games.
This is known to be a type of video game that tends to make use of different elements of role-playing games (RPGs) along with those of the gameplay of multiplayer online gaming worlds.
Therefore, In a category of games known as MMORPGs, millions of players connect to various servers to team up with other players in very large virtual worlds.
Learn more about virtual worlds from
https://brainly.com/question/13873769
#SPJ1