Query users and groups a) Login with all your new users (use the login command). Use "w" or "who" command to see current users. Compare the output format between the two commands. b) Use "whoami", or "who am i" command to see your own login. Compare the output format between the two commands. c) Search for users: how to search for a user using part of his login name? (Hint: use "grep".) Can you write a script to do it? d) How to list all members in a particular group? Can you write a script to do it?
Answers
(a) The "w" and "who" commands display information about currently logged-in users, but their output formats differ.
(b)Both the "whoami" and "who am i" commands provide information about the current user's login.
(c)To search for a user using part of their login name, you can utilize the "grep" command.
(d)To list all members in a particular group, you can use the "getent" command combined with "grep" and "cut" commands.
(a) The "w" command provides a more detailed output compared to the "who" command. It displays information such as the username, terminal, remote host, login time, idle time, and the current command or process being executed by each user. On the other hand, the "who" command provides a simpler output, typically showing only the username, terminal, and login time.
b) The "whoami" and "who am i" commands both display the username of the currently logged-in user. However, the output format may vary depending on the system and configuration. In most cases, the output will simply be the username of the logged-in user.
c) The "grep" command allows you to search for patterns within a file or command output. To search for a user using part of their login name, you can pipe the output of the command that lists all users to "grep" and provide the partial login name as the pattern. For example, if you want to search for a user with the login name "john" in the list of all users, you can use the following command:
command-that-lists-all-users | grep "john"
Replace "command-that-lists-all-users" with the appropriate command to list all users on your system.
d) To list all members of a specific group, you can use the following script:
#!/bin/bash
group_name="your_group_name"
members=$(getent group "$group_name" | cut -d: -f4)
for member in $members; do
echo "$member"
done
Replace "your_group_name" with the name of the group you want to list members for. This script uses the "getent" command to retrieve group information, then pipes the output to "cut" to extract the member usernames. Finally, it loops through the list of members and prints each member's username.
To learn more about commands Click Here: brainly.com/question/4340417
#SPJ11
Related Questions
Which of the following is true of planning and buying TV and radio advertising? O Radio formats appeal to mass audiences, giving it more spillover than TV. O Radio ads are much more expensive to produce than TV ads. O A disadvantage of TV is that it is unable to build awareness quickly. O TV advertising takes up a lesser portion of the IMC budget as compared to radio. O TV is still the best medium to generate excitement around a brand.
Answers
When it comes to planning and purchasing TV and radio advertising, TV is still the strongest medium for generating excitement about a brand.
Which of the following is NOT a benefit of television advertising?Television gives a transient message with nothing concrete for the audience to scrutinize or think about, which is one of its benefits. For a very long time, advertisers have utilized television commercials to promote their goods and services to customers.
Which of the following is true regarding radio advertising's benefits?With radio, communications may be customized and regionalized for each intended audience. Advertisers can target particular demographics, psychographics, geographic regions, as well as events and genres within a market.
To know more about radio technology visit:-
https://brainly.com/question/14455347
#SPJ4
There is a weird green and black kinda growth on my screen that moves when I squeeze the screen, it also looks kinda like a glitchy thing too,Please help
Answers
LCD stands for Liquid Crystal Display. So yes, what you're seeing is liquid. it's no longer contained where it needs to be.
Implement the function printTwoLargest that inputs an arbitrary number of positive numbers from the user. The input of numbers stops when the first negative or zero value is entered by the user. The function then prints the two largest values entered by the user. If fewer than two distinct positive numbers are entered a message to that effect is printed instead of printing any numbers. Hint: Duplicates will cause problems. Try to make sure that you find a way to ignore them.
Answers
Answer:
The function in Python is as follows:
def printTwoLargest():
chk = 0
list1 = []
num = int(input("Enter: "))
while num > 0:
for i in list1:
if i == num:
chk+=1
break;
if chk == 0:
list1.append(num)
chk = 0
num = int(input("Enter: "))
list1.sort()
if len(list1) >= 2:
print("Largest:", list1[-1])
print("Second:", list1[-2])
else:
print("Length of list must be at least 2")
Explanation:
This defines the function
def printTwoLargest():
This initializes a check variable to 0
chk = 0
This initializes an empty list
list1 = []
This prompts the user for input
num = int(input("Enter: "))
The following loop is repeated until input is 0 or negative
while num > 0:
The following for loop checks for duplicate
for i in list1:
if i == num: If duplicate is found
chk+=1 The check variable is set to 1
break; And the for loop is exited
The input is appended to the list if the check variable is 0 (i.e. no duplicate)
if chk == 0:
list1.append(num)
This sets the check variable back to 0, for another input
chk = 0
This prompts the user for another input
num = int(input("Enter: "))
This sorts the list
list1.sort()
This prints the two largest if valid user input is 2 or more
if len(list1) >= 2:
print("Largest:", list1[-1])
print("Second:", list1[-2])
if otherwise, this prints that the length must be at least 2
else:
print("Length of list must be at least 2")
The advantage of a digital camera in taking nighttime photographs is that you can see
the results right away.
• True
© False
Answers
Answer:
Ima say true
Explanation:
PLEASE HELP ME
Microsoft VWord is a graphical word processing program that has helpful tools to
enable users to produce their own professional documents. Which one of the
following is not a feature of Word?

Answers
Answer:
the 1st one is wrong as word isn't used for that
You have been asked to create a file that will contain a series of Windows command-prompt commands that automate the creation of a VPN client that connects to your company VPN server. What type of file should you create
Answers
Based on the information given, the type of file that the user should create is the batch file.
Batch file simply means a script file in Microsoft Windows. A batch file consists of a series of commands that will be executed by the command-line interpreter.
Since the user has been asked to create a file that will contain a series of Windows command-prompt commands that automate the creation of a VPN client, the batch file will be vital in this case.
Read related link on:
https://brainly.com/question/25520771
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
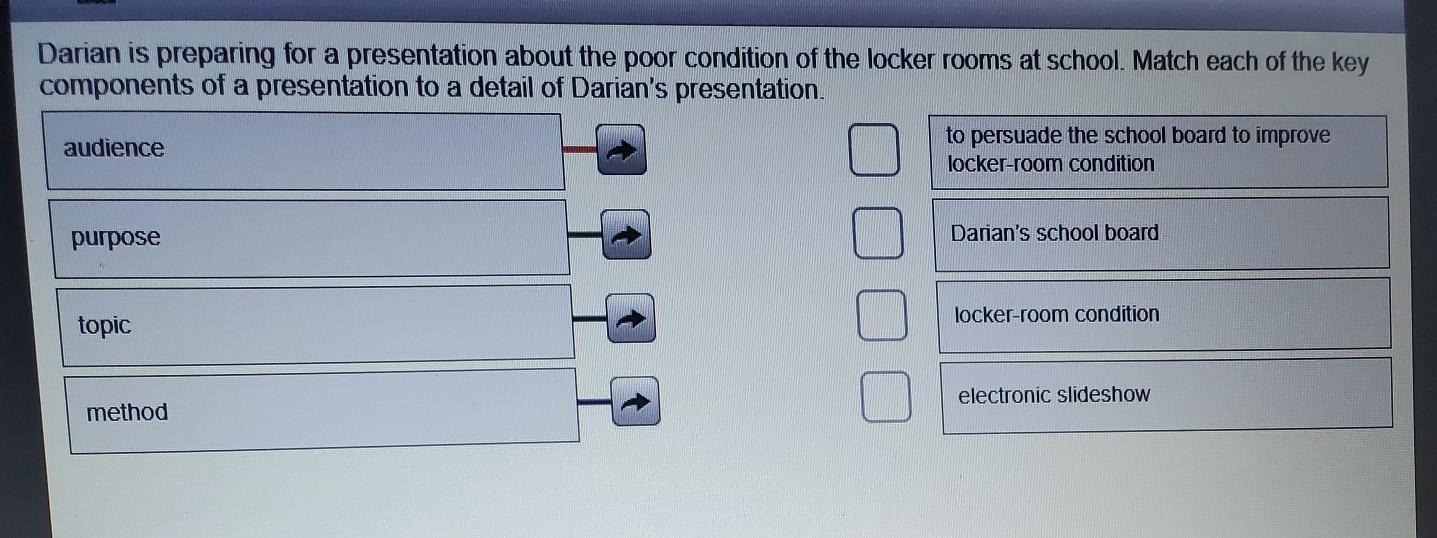
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
What is data and information
Answers
Answer:
data is the unprocessed information where as information is a processed output
Select the correct word to complete the sentence.
_______connections tend to be more reliable, secure, and faster than______
connections.
______connections tend to be more convenient than_______
allowing users to be more mobile.
Answers
Answer:
Wired, Wireless, Wireless, Wired
Explanation:
Answer:
Wired connections tend to be more reliable, secure, and faster than wireless connections. While wireless connections tend to be more convenient, allowing users to be mobile. Many businesses and homes use a combination of wired and wireless.
Explanation:
Edge 2022

what includes invoices, spreadsheets, time sheets, and transactions? group of answer choices data aggregation. competitive monitoring. data map. source data.
Answers
A technological resource that includes invoices, spreadsheets, time sheets, and transactions is: D. source data.
What is a spreadsheet software?A spreadsheet software can be defined as a type of software program which is typically designed and develop with cells that are arranged in a tabulated format in rows and columns, in order to help an end user do the following on a data:
SortCalculateFormatArrangeIn Computer technology, source data simply refers to a technological resource that is made up of invoices, spreadsheets, time sheets, and transactions, which can be used to sort, format, analyze and simulate information about a subject matter.
Read more on spreadsheets here: https://brainly.com/question/26919847
#SPJ1
A software license gives the owner the _____
to use software.
human right
understanding
password
legal right
Answers
Answer:
A software license gives the owner the legal right to use software.
What is phishing? Answer
Answers
Answer:
Phishing is a type of online scam where an attacker sends a fraudulent email purporting to be from reputable companies, designed to deceive a person into revealing sensitive and personal information (card numbers, passwords etc).
Hope this helps.
which type of database allows users to view multiple dimensions of the same static data in business intelligence examples, such as comparative or multi-year inventory levels and sales performance?
Answers
The type of database that allows users to view multiple dimensions of the same static data in business intelligence examples, such as comparative or multi-year inventory levels and sales performance is known as OLAP database.
OLAP (Online Analytical Processing) is a type of database designed for multidimensional querying and analysis. It allows users to view data from different angles, or dimensions, and drill down into the data to gain deeper insights. OLAP databases are specifically designed to handle complex queries and large volumes of data.
They are optimized for read-intensive workloads and are typically used in business intelligence (BI) applications.OLAP databases are different from traditional relational databases in that they use a multidimensional data model instead of a two-dimensional table-based model. This allows for more flexible querying and analysis of data, as well as faster response times.
To know more about database visit:
https://brainly.com/question/30163202
#SPJ11
___ design uses the same webpage content, but applies styling depending on the viewport size of the device
Answers
which tab on the ribbon contains the command to record a macroa. Home. b. Insert. c. View. d. Design
Answers
Answer:
D. I'm pretty sure, sorry if I'm wrong
Explanation:
write a second function called round2() that is similar to round1() except that it uses k2 and returns the concatenation of r2 and l2.
Answers
To write a second function called round2() that is similar to round1() but uses k2 and returns the concatenation of r2 and l2, we can follow these steps:
Start by defining the function header with two arguments, r1 and l1, which represent the right and left halves of the output of round1().
Generate the subkeys k2a, k2b, k2c, and k2d using the same process as in round1(), but using k2 instead of k1.
Apply the Feistel function using the subkeys k2a, k2b, k2c, and k2d, and the input l1 and r1. The output of the Feistel function will be the new left and right halves, l2 and r2.
Concatenate r2 and l2 to obtain the output of round2().
Here is the implementation of the round2() function in Python:
def round2(r1, l1, k2):
# Generate subkeys k2a, k2b, k2c, k2d
k2a, k2b, k2c, k2d = generate_subkeys(k2)
# Apply Feistel function using subkeys k2a, k2b, k2c, k2d, and input l1 and r1
l2 = r1
r2 = xor(l1, feistel_function(r1, k2a, k2b, k2c, k2d))
# Concatenate r2 and l2 to obtain output of round2
output = r2 + l2
return output
The round2() function takes the right and left halves of the output of round1() as input, along with the subkey k2.
It generates the subkeys k2a, k2b, k2c, and k2d using the generate_subkeys() function, applies the Feistel function using these subkeys and the input r1 and l1, and concatenates the resulting r2 and l2 to obtain the output of round2(). The output is returned as a single string.
For more such questions on second function visit:
https://brainly.com/question/22527663
#SPJ11
Need answer ASAP. I’ll mark brainliest if correct

Answers
Answer:
I am pretty sure for the first option the answer is tasks, and for the second option, it is logical.
Explanation:
"tasks to be performed in a logical manner" sounds right to me.
You have a server with two physical processors, each with four cores for a total of 8 cores. How many license packs must you buy in order to cover this server
Answers
Answer:
You must buy eight 2-core license packs, for a total of 16 core licenses.
Explanation:
Brainliest pls
Aubrey uses the following formula to calculate a required value. Which elements of the formula use mixed cell referencing?

Answers
Answer:
$1A
brainiest plz
Explanation:
The elements of a formula only can have the following format:
1) Letter Number as C1
2) Letter $ Number as A$1
3) $ Letter Number as $A1
4) $ Letter $ Number as $A$1
The element $1A is not in the format
Answer:
A$1$A1Explanation:
Plato correct!
what instruction would i use to save the current value of the flags register?
Answers
With the PUSHF instruction, which pushes the flags register's contents onto the stack, you can save the flags register's current value in x86 assembly code.
Describe the stack pointer.The memory address of the most recent data element added to the stack, or, in other situations, the first address that became available on the stack, is kept in a tiny register known as a stack pointer.
The stack pointer is stored in which register?The last item added to the stack is located using the Stack Pointer (SP) register. The SP is reduced before the item is added to the stack when you PUT anything ONTO the stack (PUSH something onto the stack).
To know more about flags register's visit:-
https://brainly.com/question/29488807
#SPJ4
What is the process that creates a shortcut on your taskbar?
pinning
O saving
sharing
O tying
Answers
Answer:
A. Pinning
Explanation:
I just took the test.
Answer:
a
Explanation:
Suppose you have a mixture of nickels, dimes, and quarters in a piggy bank and that mixture has a value of $3.50. If there are twice as many dimes as there are quarters and 15 more nickels than dimes, determine the number of each coin in the piggy bank.
Answers
The piggy bank contains 10 nickels, 20 dimes, and 5 quarters. Let's assign variables to the number of each coin: N for nickels, D for dimes, and Q for quarters.
We can create a system of equations based on the given information.
From the value equation, we know that 0.05N + 0.10D + 0.25Q = 3.50.
From the second statement, we know that D = 2Q (twice as many dimes as quarters).
From the third statement, we know that N = D + 15 (15 more nickels than dimes).
Substituting the second and third statements into the value equation, we get 0.05(D + 15) + 0.10D + 0.25Q = 3.50.
Simplifying, we have 0.05D + 0.75 + 0.10D + 0.25Q = 3.50.
Combining like terms, we get 0.15D + 0.25Q = 2.75.
Multiplying both sides by 20 to eliminate decimals, we have 3D + 5Q = 55.
Using the second statement again, we substitute D = 2Q into the equation, resulting in 3(2Q) + 5Q = 55.
Simplifying, we get 11Q = 55, which gives Q = 5.
Substituting Q = 5 back into D = 2Q, we have D = 2(5) = 10.
Finally, substituting D = 10 into N = D + 15, we get N = 10 + 15 = 25.
Therefore, the piggy bank contains 10 nickels, 20 dimes, and 5 quarters.
Learn more about piggy bank here:
https://brainly.com/question/28954223
#SPJ11
Which sentence describes a contract comprehensively?
A contract needs to have an offer and a legal purpose. A contract includes an offer and acceptance without any consideration. A contract
includes an offer, acceptance, and consideration without a legal purpose. A contract includes an offer, acceptance, consideration, and a legal
purpose.
Answers
Answer:The sentence that describes a contract comprehensively is the last option - a contract includes an offer, acceptance, consideration, and a legal purpose.
These four terms are all very important parts of a contract, without which an agreement couldn't even exist. A contract has to have all four parts in order to be legally valid, so this is the reason why the other options cannot be correct as all of them lack one or more terms.
Explanation:
Answer:
A contract includes an offer, acceptance, and consideration without a legal purpose.
Explanation:
you are working as a cybersecurity expert in an enterprise. while examining the newly established enterprise network, you found that when a request to write data to the drive is made, the controller sends that request to each drive. when a read action is required, the data is read twice, once from each drive. which type of raid is used in the newly established network?
Answers
Based on the information provided, it appears that the enterprise network uses a RAID 1 configuration.
What is RAID 1?RAID 1 is a type of RAID (Redundant Array of Independent Disks) configuration in which data is mirrored across two or more drives, so that the same data is written to each drive.
This provides redundancy and improved data availability, since the data can still be accessed even if one of the drives fails.
In a RAID 1 configuration, when a request to write data to the drive is made, the controller sends the request to each drive, and the data is written to both drives simultaneously.
When a read action is required, the data is read from both drives and compared to ensure that the data is consistent and accurate.
The description of the enterprise network's behavior matches the characteristics of a RAID 1 configuration, so it is likely that this is the type of RAID used in the newly established network.
To Know More About Data redundancy, Check Out
https://brainly.com/question/13438926
#SPJ4
Programs that allow you to mix text and graphics to create publications of professional quality. Desktop publishing
Answers
A program that allows you to combine text and graphics to create professional-quality publications is b) desktop publishing
It is commonly used for designing and printing books, newsletters, brochures, and other documents with a combination of text and graphics.DTP software offers a wide range of features for customizing page layouts, typography, and graphic elements. Users can create, import, and edit text and images, as well as manipulate page layouts and styles, add color and visual effects, and preview and print finished documents.
Desktop publishing is a type of productivity software, but it is not a database or presentation software.
The correct answer is option b) Desktop Publishing.
Learn more about Desktop Publishing:https://brainly.com/question/7221406
#SPJ11
Your question is incomplete but probably the complete question is:
Program that allows you to mix text and graphics to create publications of professional quality.
a) database
b) desktop publishing
c) presentation
d) productivity
An excerpt of a sample business cover letter. The text uses curly font and has a warm to cold color background. What change does NOT need to be made to the above cover letter excerpt before sending it to an employer? a. Remove background color b. Change text to a basic font c. Remove business letter format d. Change font color to black Please select the best answer from the choices provided A B C D.
Answers
Answer:The answer is c because i took the quiz hope this helps
Explanation:
cccccccccccccccccccc
2.7 Code Practice: Question 1
Write a program that takes three numbers as input from the user and prints the largest
Can someone please help me with this because I’ve been struggling all day
Answers
Answer:
You didn't specify the programming language
I'll answer using Python
nums = []
for i in range(1,4):
inp = int(input("User Input: "))
nums.append(inp)
nums.sort()
print(nums[-1])
Explanation:
I made use of list in answering this question.
Start by declaring an empty list
nums = []
Use iteration to enter the list elements
for i in range(1,4):
inp = int(input("User Input: "))
nums.append(inp)
Sort the list
nums.sort()
Then print the element on the last index
print(nums[-1])
The code below is in Java
It uses if-else structure to find out the largest number among three numbers given by the user.
Comments are used to explain each line of the code
//Main.java
import java.util.Scanner;
public class Main
{
public static void main(String[] args) {
//Create a Scanner object to be able to get input
Scanner input = new Scanner(System.in);
//Declare the variables
int number1, number2, number3, largest;
//Ask the user to enter three numbers
System.out.print("Enter the first number: ");
number1 = input.nextInt();
System.out.print("Enter the second number: ");
number2 = input.nextInt();
System.out.print("Enter the third number: ");
number3 = input.nextInt();
/*
Check if the first number is greater than or equal to the second and third number.
If it is, the largest is the first one.
Otherwise, check if the second number is greater than or equal to the first and third number.
If it is, the largest is the second one.
If the previous conditions are not satisfied that means third is the largest one
*/
if(number1 >= number2 && number1 >= number3)
largest = number1;
else if(number2 >= number1 && number2 >= number3)
largest = number2;
else
largest = number3;
//Print the largest number
System.out.println("The largest number is " + largest);
}
}
You may see a similar question in the following link:
brainly.com/question/17132559
Do you think coded communication is just as important to winning wars today? Why or why not? How has sending or the use of codes changed over time?
Answers
Answer: Do you think coded communication is just as important to winning wars today? Why or why not? How has sending or the use of codes changed over time?
Explanation:
HELP ME PLEASE PLEASE PLEASE!!!! IM BEGING YOU!!!!
In your own words, describe in detail the different types of image licensing. How does image metadata play a role in these licenses and why is that important.
Answers
Answer:
Photo metadata is a set of data describing and providing information about rights and administration of an image. It allows information to be transported with an image file, in a way that can be understood by other software and human users.
Explanation:
why do i need this here when i just want i simple question