Multiple Choice A compiler compiled a program into 25000 instructions. It is run on a processor with a clock frequency of 1GHz. If it takes 3 clocks per instruction on an average, how long will it take for this program to run in seconds
Answers
A compiler compiled a program into 25000 instructions. It is run on a processor with a clock frequency of 1GHz, it will take 0.00005 seconds for this program to run.
We must take into account the amount of instructions, clock frequency, and the number of clocks per instruction to determine how long the program will take to execute.
Here, it is given that:
Number of instructions = 25,000
Clock frequency = 1 GHz (1,000,000,000 Hz)
Clocks per instruction = 2
To calculate the time taken,
Time = (Number of instructions) * (Clocks per instruction) / (Clock frequency)
Plugging in the given values:
Time = (25,000) * (2) / (1,000,000,000)
Time = 0.00005 seconds
Thus, the correct answer is 0.00005 seconds.
For more details regarding compiler, visit:
https://brainly.com/question/28232020
#SPJ4
Related Questions
Please help me on this it’s due now

Answers
I would say the answer is Logistics Manager, Material Handlers, and Inventory Managers.
Definition:
Logistics Manager: person in charge of overseeing the purchasing
and distribution of products in a supply chain
Material Handlers: responsible for storing, moving, and handling
hazardous or non-hazardous materials
Inventory Managers: oversee the inventory levels of businesses
Hope that helps!
Write a Python program that returns (by printing to the screen) the price, delta and vega of European and American options using a binomial tree. Specifically, the program should contain three functio
Answers
To write a Python program that calculates the price, delta, and vega of European and American options using a binomial tree, you can create three functions:
1. `binomial_tree`: This function generates the binomial tree by taking inputs such as the number of steps, the time period, the risk-free rate, and the volatility. It returns the tree structure.
2. `option_price`: This function calculates the option price using the binomial tree generated in the previous step. It takes inputs such as the strike price, the option type (European or American), and the tree structure. It returns the option price.
3. `option_greeks`: This function calculates the delta and vega of the option using the binomial tree and option price calculated in the previous steps. It returns the delta and vega.
Here is an example implementation of these functions:
```
def binomial_tree(steps, time_period, risk_free_rate, volatility):
# Generate the binomial tree using the inputs
# Return the tree structure
def option_price(strike_price, option_type, tree_structure):
# Calculate the option price based on the strike price, option type, and tree structure
# Return the option price
def option_greeks(tree_structure, option_price):
# Calculate the delta and vega of the option based on the tree structure and option price
# Return the delta and vega
# Example usage:
tree = binomial_tree(100, 1, 0.05, 0.2)
price = option_price(50, "European", tree)
delta, vega = option_greeks(tree, price)
# Print the results
print("Option Price:", price)
print("Delta:", delta)
print("Vega:", vega)
```
In this example, the `binomial_tree` function generates a tree with 100 steps, a time period of 1 year, a risk-free rate of 5%, and a volatility of 20%. The `option_price` function calculates the option price for a European option with a strike price of 50. Finally, the `option_greeks` function calculates the delta and vega based on the tree structure and option price. The results are then printed to the screen.
To know more about European visit:
https://brainly.com/question/1683533
#SPJ11
Over the weekend, i was thinking about the process for analyzing the technology needs for this new department. the service department will need a system to support its unique needs of scheduling technicians, obtaining parts for repair, and setting up follow up appointments once parts are in-stock. i want to make sure that none of the analysis and design tasks fall through the cracks. i need you to identify all of the tasks that you will need to complete. i find it is helpful to create a work breakdown structure to identify the tasks. don't forget to include the system and industry analysis, system design, implementation plans, and security tasks in your wbs. what would be an example of a wbs?
Answers
The primary problem to be attained is the estimating of the sources. Its it good that one assign sources to all of the activity as in step with the things that can be done of that pastime and those to be finished efficiently as well as successfully.
What is WBS?The term Work Breakdown Structure (WBS) is known to be a form of an hierarchical statement of the tasks that is needed to complete a project.
Note that the WBS tends to “breaks down” the structure of a project into what we call the manageable deliverables.
The Work breakdown structure (WBS) in project management is also known as a method for finishing a complex, multi-step project and as such, The primary problem to be attained is the estimating of the sources. Its it good that one assign sources to all of the activity as in step with the things that can be done of that pastime and those to be finished efficiently as well as successfully.
Learn more about Work Breakdown Structure from
https://brainly.com/question/3757134
#SPJ1
plsss helppp me with thisss plsss

Answers
Answer:
Here is an example of what you're asking in Python.
import random
def buildList(x):
# Create an empty list to store the random integers
random_list = []
# Use a for loop to generate x random integers
for i in range(x):
# Append a random integer between 100 and 199 to the list
random_list.append(random.randint(100, 199))
return random_list
# Get the number of random integers from the user
x = int(input("Enter the number of random integers to generate: "))
# Call the buildList function to generate the random integers
random_integers = buildList(x)
# Print the list of random integers
print(random_integers)
Explanation:
This script uses the 'random.randint()' function from the built-in 'random' module to generate a random integer between 100 and 199, and then it saves the generated random integers in a list. The script also prompts the user for the number of random integers to generate and calls the buildList function with the user input. Finally, it prints the list of random integers.
Which statement describes compute nodes in a NetApp HCI appliance chassis?
Answers
Overall, compute nodes play a crucial role in enabling the consolidation of compute and storage resources, facilitating efficient virtualization, and supporting a wide range of applications and workloads in the NetApp HCI environment.
Compute nodes in a NetApp HCI (Hyper-Converged Infrastructure) appliance chassis serve as the computing resources in the system. They are responsible for running virtual machines and executing workloads within the HCI environment.
The compute nodes in a NetApp HCI appliance chassis are designed to provide high-performance computing capabilities. They typically consist of powerful processors, ample memory, and storage resources to support the virtualized workloads. These nodes are integrated with the storage nodes, which handle the storage functions and provide the necessary data services.
Compute nodes in a NetApp HCI appliance chassis are tightly integrated with the storage nodes to form a cohesive and scalable infrastructure. They work together to deliver compute and storage resources as a unified solution, simplifying management and improving resource utilization.
To know more about powerful processors, visit:
https://brainly.com/question/13014278
#SPJ11
4.9 Code Practice: Question 1

Answers
total = 0
for x in range(3, 67, 3):
total += x
print(total)
I hope this helps!
The program sums all the values in a given range and assigns the total to the sum variable. The program is written in python 3 thus :
sum = 0
#initialize a sum variable, initialized as 0
for x in range(3, 67, 3):
#loop through the range taking a step of 3 after each iteration.
sum+= x
#add the iterated value to the sum variable after each iteration
print(sum)
#display the sum
A sample run of the program is attached
Learn more :https://brainly.com/question/14899725
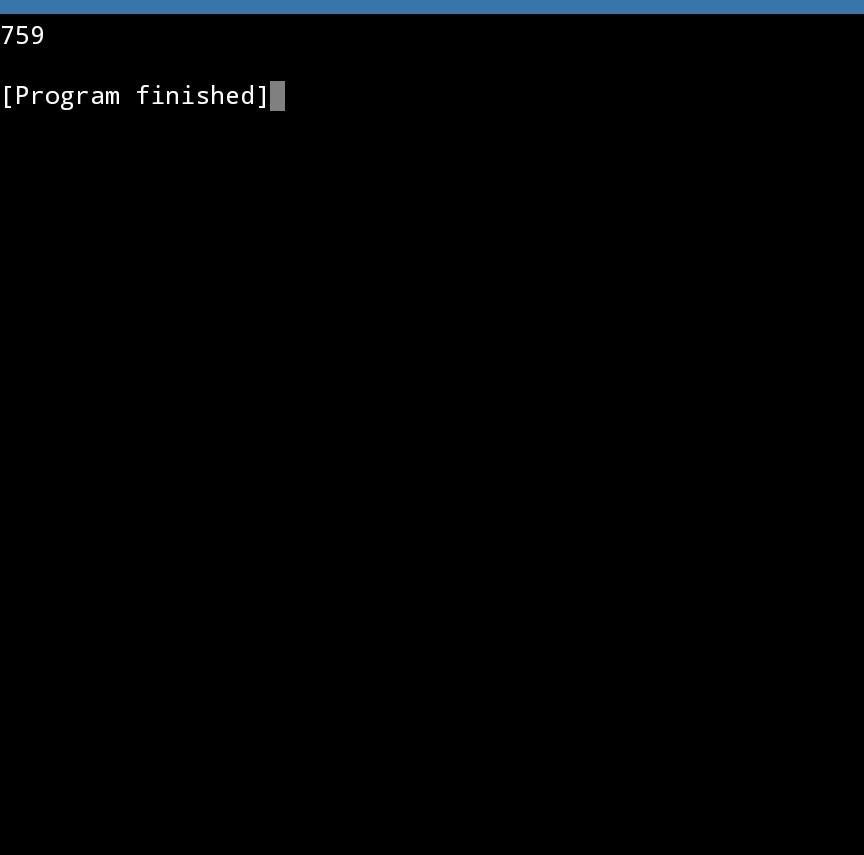
What is the value of numC when this program is executed?
numA = 4
numB = 10
if numA == 2:
numC = 10
elif numA > numB:
numC = 20
else:
numC = 30
Answers
numA = 4 and numB = 10
for the if statement to run, numA has to equal 2, which it doesn't.
for the elif statement to run, numA has to be greater than numB, which it isn't.
That leaves the else statement, therefore, numC = 30
Answer:
30
Explanation:

Assume that your body mass index (BMI) program calculated a BMI of 20.6. What would be the value of category after this portion of the program was executed? # Determine the weight category. if BMI 39.9: category = "morbidly obese" elif BMI <= 24.9: category = "normal" elif BMI <= 39.9: category = "overweight"
The value of category will be _______.
A) overweight
B) normal
C) underweight
D) morbidly obese
Answers
Assume that your body mass index (BMI) program calculated a BMI of 20.6. The value of category will be option A) overweight.
What is the body mass index about?Body mass index (BMI) is a measure of body fat based on height and weight that applies to adult men and women. It is calculated by dividing a person's weight in kilograms by their height in meters squared.
A BMI of 20.6 falls within the normal weight range, which is a BMI of 18.5 to 24.9. However, based on the given code snippet, if the BMI is 39.9 or greater, the category is "morbidly obese." If the BMI is less than or equal to 24.9, the category is "normal." If the BMI is less than 39.9 but greater than 24.9, the category is "overweight."
Therefore, if the BMI calculated by the program is 20.6, the value of the category will be "overweight."
Learn more about body mass index from
https://brainly.com/question/10091149
#SPJ1
Suppose two hosts, A and B, are separated by 20,000 kilometers and are connected by a direct link of R = 2 Mbps. Suppose the propagation speed over the link is 2.5 · 10⁸ meters/sec.
How many TCP congestion windows are needed in slow start to send out the entire file? Assume that a congestion window contains segments of the equal size 1000 bytes.
Answers
To send the entire file over the 20,000 km link with a bandwidth of 2 Mbps, we need to divide the file size by 40,000 to get the number of TCP congestion windows needed in slow start.
To calculate the number of TCP congestion windows needed in slow start to send out the entire file, we first need to determine the bandwidth-delay product (BDP), which is the maximum amount of data that can be in transit on the link at any given time.
BDP = R * RTT
where RTT is the round-trip time for a packet to travel from A to B and back to A.
Since the distance between A and B is 20,000 kilometers and the propagation speed is 2.5 · 10⁸ meters/sec, the one-way propagation delay is:
Propagation Delay = distance / propagation speed = 20,000 km / 2.5 · 10⁸ m/s = 0.08 seconds
Therefore, the round-trip time (RTT) is twice the propagation delay:
RTT = 2 * Propagation Delay = 0.16 seconds
Substituting the values, we get:
BDP = 2 Mbps * 0.16 seconds = 320,000 bits
Since a congestion window contains segments of 1000 bytes or 8000 bits, the number of segments in a congestion window is:
Segments per window = BDP / segment size = 320,000 bits / 8000 bits per segment = 40 segments
In slow start, the congestion window size starts at one segment and doubles every round trip until it reaches a certain threshold value. Thus, the number of windows required to send the entire file can be calculated as:
Number of windows = (File size in bytes / segment size) / segments per window
Assuming the file size is F bytes, the number of windows required is:
Number of windows = (F / 1000) / 40
Therefore, the main answer is:
Number of windows = F / 40,000
This calculation is based on the bandwidth-delay product, which represents the maximum amount of data that can be in transit on the link at any given time, and the fact that in slow start, the congestion window size doubles every round trip until it reaches a certain threshold value.
For more questions like Bandwidth visit the link below:
https://brainly.com/question/30550995
#SPJ11
Some critics say that flash mobs: O A. exploit people's talents. O O B. should not be inclusive. C. cost too much money. D. invade public space.
Answers
Answer: D. invade public space.
Explanation:
Flash mob refers to the group of people who gather in a public place, and then perform for a brief time and then leave after they perform. The performance is typically meant for satire, entertainment, satire, or can be a form of artistic expression. An example of flash mob is people gathering to sing a song, choreography or people involved in a pillow fight.
Some critics of flash mobs believes that flash mobs invade public space and can sometimes be out of control when there are a large number of people who are participating.
Using the what-if function in excel to make a decision is considered a type of __________.
Answers
Using the what-if function in excel to make a decision is considered a type of forecast and scenario model
In Excel, which function is used for decision making?The IF function is one of the most commonly used in Excel. It enables you to make logical comparisons between a value and your expectations. In its simplest form, the IF function says something like: If the value in a cell is what you expect (true) - do this.
What exactly is an Excel what-if analysis?What-If Analysis is the process of changing the values in cells to see how those changes affect the results of worksheet formulas. Three kinds of What-If Analysis tools come with Excel: Scenarios, Goal Seek, and Data Tables. Scenarios and data tables take input values and generate possible outcomes.
What function is responsible for decision-making?Decision-making is an essential component of modern management. Essentially, the primary function of management is rational or sound decision making. Every manager makes hundreds of decisions, either subconsciously or consciously, as the key component in the role of a manager.
learn more about Excel visit:
brainly.com/question/3441128
#SPJ4
you are developing an azure-based application that stores all application settings in the azure app configuration service. you provision a standard tier azure app configuration instance and enable the customer-managed key capability on the instance. you need to allow the azure app configuration instance to use an azure key vault key. which two actions should you perform? each correct answer presents part of the solution. a. enable the purge-protection feature on the azure key vault. b. assign a managed identity to the azure app configuration instance. c. configure a private endpoint for the azure app configuration instance. d. configure managed identity permission to access the azure key vault. e. create a dns cname resource record for the azure app configuration instance.
Answers
(b) assign a managed identity to the azure app configuration instance and (d) configure managed identity permission to access the azure key vault are the two actions that need to perform for this situation.
What is the azure key vault?
By leveraging keys that are guarded by hardware security modules, Microsoft Azure Key Vault, a cloud-hosted management solution, enables customers to encrypt keys and tiny secrets (HSMs). Small secrets include passwords and other data that is less than 10 KB in size. PFX documents
Both managed hardware security module (HSM) pools and vaults are supported by the Key Vault service. Keys, secrets, and certificates secured by an HSM can be stored in vaults. Managed HSM pools only accept keys with an HSM backup.
To learn more about the azure key vault, use the link given
https://brainly.com/question/29433704
#SPJ1
During active listening, which response is NOT an example of providing feedback to the speaker to show that you understand his or her thoughts?
A.
nodding your head
B.
turning your back to the speaker
C.
saying, "You're saying that his reaction made you feel appreciated?"
D.
saying, "Sorry to interrupt, but can you explain that part again?"
Answers
Answer:
The answer is D.
Explanation:
They/you are asking the speaker to clarify what they just said.
Answer:
B. turning your back to the speaker
Explanation:
Is the GPU shortage over? What do you think this means for other
chip-using industries? Why else do you think the prices are falling
on chip based products?
Respond to the question in full sentences.
Answers
The GPU shortage is not entirely over, but there have been some improvements in recent months. The GPU shortage has primarily been driven by a combination of factors, including the global semiconductor supply chain constraints, increased demand due to the growth of gaming and remote work, and the high demand for GPUs in cryptocurrency mining.
As for the impact on other chip-based products, the semiconductor shortage has affected various industries such as automotive, consumer electronics, and telecommunications. Manufacturers of these products have faced challenges in meeting the high demand, leading to delays and increased costs. However, as production capacity for semiconductors gradually ramps up and various governments invest in domestic chip production, the situation may improve in the coming months.
In summary, the GPU shortage is still ongoing but showing signs of improvement. The consequences of this shortage extend to other chip-based products, leading to production delays and increased costs across different industries. As semiconductor production increases and global efforts to resolve the issue continue, we can hope to see more stable supply chains and reduced shortages in the near future.
Learn more about GPU here:
https://brainly.com/question/27139687
#SPJ11
Retirement (50 Points) Data File needed for this exercise: Retirement.xlsx As a Human Resources Manager at the Oshawa clinic, you have decided to create a workbook template that can help employees plan their retirement based on their annual contributions to their retirement account. The template allows an employee to enter the age to start contributions, the projected retirement age, the number of years in retirement, and the rate of return expected to earn on the money when he/she retires. Subsequently, the template determines the total amount contributed, the amount accumulated for retirement, and the pension amount per period during retirement. Your goal is to establish formulas to determine the above-mentioned values, perform sensitivity analysis using the What-if analysis tools, and summarize your results using charts. Open and Save the Workbook (a) Open the Retirement.xlsx workbook and save it as Retirement Template.xlsx. (b) Insert a Documentation worksheet and add an appropriate title for the workbook in cell A1. In cell B3, enter your name. In cell B4, enter your student number. In cell B5, enter the completion date of your assignment, and in cell B6, enter a sentence to describe the purpose of the workbook. (c) Save the workbook. Pension Calculations (a) Switch to the Retirement worksheet, and enter the following information into cells B3:B9. Label Value Annual contribution $2,000 Age when contributions start 20 Retirement age 69 Rate of return 4.0% Years in retirement 25 Rate of return during retirement 5.0% Periods per year 12 (b) In cell B12, enter a formula to calculate the total annual contribution. (c) In cell B13, enter a function to calculate the amount accumulated (future value) for retirement. Hint: Use the FV function. (d) In cell B14, enter a function to calculate the pension amount per period during retirement. Hint: the PMT function. (e) Save the workbook. One- and Two-Variable Data Table (a) Use the Data Table feature (from the What-If Analysis tools) to calculate the total annual contribution (B12), the amount accumulated for retirement (B13), and the pension amount per period during retirement (B14) by changing the annual contribution (B3) value ranging from $1,000 to $10,000 in increments of $1,000. Apply custom number format to the three formula cell references to show descriptive column headings. (b) Similarly, create a two-variable data table to calculate the pension amount per period during retirement (B14) by changing the annual contribution (B3) values from $1,000 to $10,000 in increments of $1,000 and the rate of return during retirement (B8) value from 3.0% to 10.0% in increments of 1.0%. Apply custom number format to the formula cell reference to show a descriptive heading. (c) Save the workbook. Scenario Manager (a) Using the Scenario Manager from the What-If Analysis tools, create three scenarios based on the table provided below. Changing Values Case 1 Case 2 Case 3 Annual contribution $1,000 $3,000 $5,000 Age when contributions start 20 25 30 Retirement age 65 67 69 Rate of return 2.5% 3.0% 4.0% Years in retirement 20 25 30 Rate of return during retirement 2.5% 3.0% 4.0% Periods per year 12 12 12 (b) Generate a scenario summary report for the total annual contribution (B12), the amount accumulated for retirement (B13), and the pension amount per period during retirement (B14). (c) Using the scenario summary results, create a Clustered Column chart based on the total annual contribution and the amount accumulated for retirement results. Be sure to add appropriate chart elements for your chart. (d) Save the workbook. Use Goal Seek (a) Using the Goal Seek tool from the What-If Analysis tools, determine the annual contribution amount required to earn a pension amount of $5,000 per month during retirement. Keep the Goal Seek result as the new annual contribution amount. (b) Format your workbook as desired (Headings, Font, Fill color, Number format...) (
Answers
The Retirement Template.xlsx workbook helps employees plan their retirement based on their annual contributions to their retirement account. It includes pension calculations, one- and two-variable data tables, scenario analysis, and the use of the Goal Seek tool. The
The workbook provides a comprehensive analysis of the total annual contribution, amount accumulated for retirement, and pension amount per period during retirement. Sensitivity analysis is performed by changing the annual contribution and rate of return values, and scenarios are created to explore different retirement parameters. The results are summarized using charts, including a Clustered Column chart comparing the total annual contribution and amount accumulated for retirement. The Goal Seek tool is used to determine the required annual contribution amount to achieve a specific pension amount during retirement.
The Retirement Template.xlsx workbook consists of several sections to assist employees in retirement planning. It starts with documenting the purpose of the workbook and includes information about the creator. The Pension Calculations section on the Retirement worksheet allows users to input their retirement parameters, such as annual contribution, age to start contributions, retirement age, rate of return, years in retirement, rate of return during retirement, and periods per year. Formulas and functions are used to calculate the total annual contribution, amount accumulated for retirement (future value), and pension amount per period during retirement.
The workbook then proceeds to perform sensitivity analysis using one- and two-variable data tables. The Data Table feature is utilized to calculate the values of total annual contribution, amount accumulated for retirement, and pension amount per period by changing the annual contribution value in a range from $1,000 to $10,000. A two-variable data table is also created by changing the annual contribution value and the rate of return during retirement from 3.0% to 10.0%.
A Clustered Column chart is created based on the scenario summary results, comparing the total annual contribution and amount accumulated for retirement. The workbook concludes by utilizing the Goal Seek tool to determine the annual contribution amount required to achieve a specific pension amount during retirement.
Throughout the process, the workbook is saved, and formatting is applied to enhance the visual appeal of the document, including headings, font, fill color, and number format.
learn more about data tables here
https://brainly.com/question/32133369
#SPJ11
Alma will make the honor roll if she has at least a 3.80 GPA and misses less than 5 days of school in a year. In which of the following cases will Alma make honor roll?
1. Alma has a 3.84 GPA and misses 5 days of school
2. Alma has a 3.78 GPA and misses 2 days of school
3. Alma has a 3.68 GPA and misses 6 days of school
4. Alma has a 3.81 GPA and misses 3 days of school
Answers
Answer: 4. Alma has a 3.81 GPA and misses 3 days of school
Explanation: The others don't meet the requirments.
The only case where Alma will make honor roll is the fourth case where she has a 3.81 GPA and misses 3 days of school.
What is GPA?GPA stands for Grade Point Average, and it is a measure of a student's academic performance in a given period.
It is calculated by assigning a numerical value to each grade received in a course and then averaging those values.
Based on the given criteria, Alma will make honor roll if she has at least a 3.80 GPA and misses less than 5 days of school in a year.
Alma has a 3.84 GPA and misses 5 days of school: Alma has the required GPA, but she misses 5 days of school which is greater than the allowed 5 days. Therefore, she will not make honor roll.
Alma has a 3.78 GPA and misses 2 days of school: Alma misses less than 5 days of school, but her GPA is less than the required 3.80. Therefore, she will not make honor roll.
Alma has a 3.68 GPA and misses 6 days of school: Alma misses more than 5 days of school, and her GPA is less than the required 3.80. Therefore, she will not make honor roll.
Alma has a 3.81 GPA and misses 3 days of school: Alma has the required GPA and misses less than 5 days of school. Therefore, she will make honor roll.
Thus, Alma will only make honour roll if she has a 3.81 GPA and misses three days of school in the fourth case.
For more details regarding GPA, visit:
https://brainly.com/question/15170636
#SPJ2
What is an equation of the line that passes through th e points (-2,-7) and (-1,-3)
Answers
Answer:
y=4x+1
Explanation:
Check the devices that are external peripheral devices:

Answers
Answer:
Mouse, and keyboard
Explanation:
Common Sense
What is the area of I LIKE YA CUT G?
Answers
why can’t methods in java change the values of arguments to a method which are of a primitive type?
Answers
Methods in Java cannot change the values of arguments that are of a primitive type because Java uses pass-by-value for method arguments.
The values of the arguments are copied and passed to the method, and any modifications made to the copies within the method do not affect the original values in the calling code. In Java, when a method is called and arguments are passed, a copy of the value of each argument is created and passed to the method. This is known as pass-by-value. For primitive types like int, boolean, float, etc., the actual value of the argument is passed, not a reference to the variable. Any changes made to the copies of the arguments within the method do not affect the original values in the calling code because they are separate copies.
To modify the value of a primitive type in a method and have the change reflected in the calling code, you would need to return the modified value from the method and assign it back to the variable in the calling code. This is in contrast to objects in Java, where changes made to object properties within a method are reflected in the original object since objects are passed by reference.
Learn more about Java here;
https://brainly.com/question/16996584
#SPJ11
how do we benefit from this increased interconnectivity?
Answers
What percentage of cyber stalking cases escalate to real-world violence?
A. 90% or more
B. Less than 1%
C. 25%
D. About 19%
Answers
The percentage of cyber stalking cases escalate to real-world violence is D. About 19%
What is cyber stalking?
The percentage of cyber stalking incidents that lead to physical violence as there are multiple barriers such as scarce data and underreporting. Furthermore, there is a scarcity of research regarding this particular subject matter.
Hence, It is commonly recognized that even though a few instances of cyber stalking could lead to actual violence, the majority of such cases do not end up with physical harm.
Learn more about cyber stalking from
https://brainly.com/question/27995900
#SPJ4
Write the introduction to your feasibility or recommendation report. Purpose, Background, and Scope of the report.
Using the Outline Format for a feasibility report or a recommendation report, create an outline.
There should be some specific detail in your outline. For instance, in the Discussion Section, identify the criteria (topics) you researched to find data that supports your proposal solution to the problem. Ex: If you are updating an application, criteria could be resources needed, costs, and risks.
Explain why you chose the criteria
Provide a source (data) to support your ideas
Explain how the data is relevant to your problem
Answers
Introduction to Feasibility/Recommendation Report:Purpose:
The purpose of this feasibility report is to provide a comprehensive assessment of the feasibility of a new program that we propose.Background: The program that we propose is a new service that will be offered by our organization. This service will be designed to meet the needs of our clients. Scope: The scope of this report is to provide a detailed analysis of the feasibility of the program, including an assessment of the resources that will be required to implement it, the risks that may be associated with it, and the benefits that are expected to be derived from it. We will also discuss the criteria that we used to research the data that supports our proposed solution to the problem. Outline Format for a Feasibility Report:1. Introduction. Purpose. Backgrounds. Scope2. Discussion. Criteria used to research the data. Source to support ideas. Relevance of data to the problem3. Conclusion. Summary of findings. Recommendations. Next StepsExplanation of Criteria: We chose the following criteria to research data that supports our proposed solution to the problem: i. Resources needed. Costiii. RiskWe chose these criteria because they are critical to the feasibility of the program. Without adequate resources, the program may not be able to be implemented. Similarly, if the costs are too high, the program may not be financially viable. Finally, if the risks associated with the program are too great, it may not be feasible to proceed with it. Source of Data: The source of data for this report is a comprehensive analysis of the market, which was conducted by our team of experts. This analysis provides us with valuable insights into the feasibility of the program and will be used to inform our recommendations. Relevance of Data to the Problem: The data that we have collected is highly relevant to the problem that we are trying to solve. It provides us with valuable insights into the feasibility of the program and will help us to make informed decisions about how to proceed.
Learn more about Feasibility here: brainly.com/question/14009581
#SPJ11
the district sales director at cloud kicks wants to share the leaderboard component on his dashboard with his sales team. what two actions should an administrator take to enable this functionality?
Answers
To enable the functionality of sharing the leaderboard component on his dashboard with his sales team, an administrator should take two actions including providing access to the sales team to the leadership component and adding the leadership component to the template.
1. Add the leaderboard component to a template that is shared with the sales team:
The leaderboard component can be added to a template that is shared with the sales team. By adding the leaderboard component to a template, all users who can access the template can see the leaderboard component.
2. Share the dashboard that contains the leaderboard component with the sales team:
Once the dashboard is created, the dashboard that contains the leaderboard component can be shared with the sales team. By sharing the dashboard, the sales team can access and view the leaderboard component. In order for the sales team to view the dashboard, the administrator must provide the sales team with access to the dashboard.
You can learn more about dashboard at: brainly.com/question/29023807
#SPJ11
show the binary search tree that results when the following values are added, in order, to a new tree. 14 45 28 49 6 12 84 4
Answers
When the values 14, 45, 28, 49, 6, 12, 84, and 4 are added in order to a new binary search tree, the resulting tree would look like the following:
14
/ \
6 45
/ \ \
4 12 49
\
84
In this binary search tree, each node has at most two children, and the left child of each node has a value less than its parent, while the right child has a value greater than its parent. This property ensures that searching for a value in the tree can be done efficiently by recursively traversing the left or right subtree depending on whether the value is smaller or greater than the current node's value. Therefore, the resulting binary search tree with the given values provides an efficient way to search for and access these values in logarithmic time.
learn more about binary search tree, here:
https://brainly.com/question/12946457
#SPJ11
___________________________________________________________________________________________PLS HE;LP!
Answers
Answer: Oh okay, what do I help with
Explanation:
explain the following joke: “There are 10 types of people in the world: those who understand binary and those who don’t.”
Answers
It means that there are people who understand binary and those that do not understand it. That is, binary is said to be the way that computers are known to express numbers.
What is the joke about?This is known to be a popular joke that is often used by people who are known to be great savvy in the field of mathematics.
The joke is known to be one that makes the point that a person is implying that the phrase is about those who only understands the decimal system, and thus relies on numbers in groups of 10.
The binary system is one that relies on numbers that are known to be in groups of 2.
Therefore, If the speaker of the above phrase is one who is able to understand binary, that person would be able to say that that the phrase is correctly written as "there are 2 types of people that understand binary".
Learn more about binary from
https://brainly.com/question/21475482
#SPJ1
the perception of higher-pitched sounds is called ________ coding.
Answers
The perception of higher-pitched sounds is called place coding. Place coding is also known as tonotopic organization, which refers to the way sound frequency is processed by the cochlea.
Place coding, which is the perception of higher-pitched sounds, is based on the location of the hair cells along the basilar membrane within the cochlea. The cochlea is a tiny snail-shaped part of the inner ear that is responsible for processing sound vibrations and sending them to the brain for interpretation.
The basilar membrane of the cochlea is the structure that separates the upper and lower chambers of the cochlea. The vibration of the basilar membrane is proportional to the frequency of the sound wave that entered the ear canal.
In general, higher-pitched sounds cause the basilar membrane to vibrate more at the base of the cochlea, whereas lower-pitched sounds cause the basilar membrane to vibrate more at the apex of the cochlea, which is the farthest end from the oval window.
To learn more about perception: https://brainly.com/question/1670120
#SPJ11
What is output if the user types in 8
Answers
Answer: 8
And if you hold shift while typing it, it gives *
Choose the most common numbers for a digital audio recording.
Sampling rate: samples per second
Bit depth:
The answer choices for the first one are 44,100, 128, 16, and 440. They're the same answer choices for the second one and I'll give Branliest to whoever gives me the correct answer.
Answers
Answer:
here's the answer yo! ik it's late but hey it's still the answer

The most common numbers for a digital audio recording: the sampling rate is 44, 100 per second, and the bit depth is 16 bit.
What is bit depth and sampling rate?The bit depth is the information of color stored in an image. The more the bit depth, the more will be the storage for colors on the image.
The sampling rate is the most common audio sample rate that is used in CDs. It is 441 kHz.
Thus, the correct options are 44,100 and 16.
Learn more about bit depth
https://brainly.com/question/14172868
#SPJ2