Imagine a scenario where new child classes are introduced frequently from a base class. The method calling sequences for every child class are the same but the implementations are different among the child classes. Here which design pattern would you like to apply? Explain the reasons with examples
Answers
The Template Method design pattern seems like a suitable fit in this situation.
What is template method design?Template method design is defined as a behavioral design approach that allows subclasses to override particular parts of an algorithm without altering the algorithm's overall structure. When you wish to allow clients to expand only specific steps of an algorithm but not the entire method or its structure, use the Template Method pattern.
With specific stages defined as abstract methods, this pattern defines the basic structure of an algorithm in a base class. Subclasses can then offer their own implementation for each stage by overriding these methods.
Thus, the template method design pattern seems like a suitable fit in this situation.
To learn more about template method design, refer to the link below:
https://brainly.com/question/15584332
#SPJ1
Related Questions
someone please help me :(!!
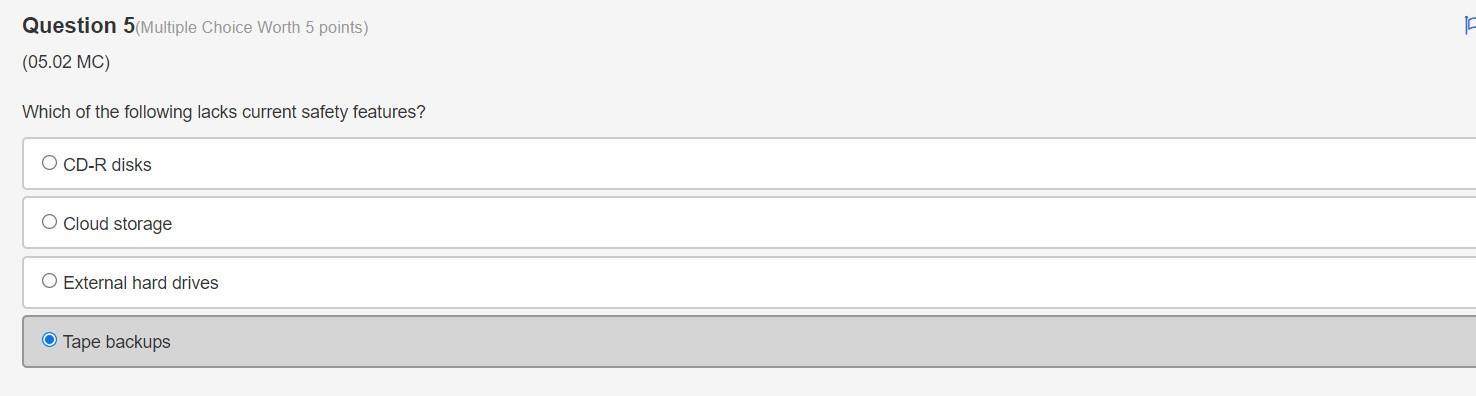
Answers
Answer:
its the third one
Explanation:
5. It is possible to prevent someone
from copying the cell from yoursheet?
How?
Answers
Answer:
click REVIEW tab and then "protect workbook"
Explanation:try it
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
As a computer programmer, a principal of a famous
private school in your country has a challenge in his
school when it comes to people from all walks of life
checking the entry requirement for admission into the
school.
As a computer programmer, write a simple application
in pseudocode that will enable people from any part of
the world to use in checking the entry requirement.
The entry requirement is as follows
1. The student must be a Ghanaian
2. Must be 18 years and above
3. Must be a male or female
Answers
This program would allow people check the entry requirement for admission into this famous private school.
START
nationality = INPUT : “Enter your country of origin”
IF the variable country is equal to Ghana
PRINT "Accepted"
ELSE
PRINT "Not accepted"
age = INPUT : "Enter your age"
IF the variable age is equal to 18 THEN,
PRINT "Accepted"
ELSE IF the variable age is greater than 18
PRINT "Accepted"
ELSE
PRINT "Under age"
gender = INPUT : "Enter your gender (Male/M/m or Female/F/f)";
IF the variable gender is equal to "Male" "M" and "m" THEN,
PRINT "Male"
ELSE IF the variable gender is equal to "Female" "F" and "f" THEN,
PRINT "Male"
Else
PRINT "Unspecified gender";
END
What is an algorithm?An algorithm can be defined as a standard formula which comprises a set of finite steps and instructions that must be executed by a software program, in order to proffer solutions to a problem on a computer, under appropriate conditions.
What is a pseudocode?
A pseudocode can be defined as a description of the steps that are contained in an algorithm, especially through the use of a plain (natural) language.
Read more on pseudocode here: brainly.com/question/13208346
#SPJ1
Cual es la constante de proporcionalidad de la función f(x)= 4x-6
Answers
what feature should be used before a document is printed
Answers
Print preview is a feature that displays on the screen what a hard copy would look like when printed. By using print preview, you can find any errors that may exist or fix the layout before printing, which can save ink or toner and paper by not having to print more than once.
Do we still use the hard drive for storage on the server or have to opt for SSD? Considering the fact that we now have 10TB + SSD, wouldn't that be better to use SSD?
Answers
Answer:
Hard drives are still used for storage on servers in many cases, but SSDs are becoming increasingly popular for server storage due to their higher performance and faster access times. In cases where high performance or fast access times are required, an SSD is the better choice. For example, if you need to store large amounts of data (more than 10TB) on a server, an SSD would be the better choice due to its higher performance and faster access times.
A drawback of using observation as a data collection method is that:_______
a. it is inaccurate in measuring overt behavior.
b. it cannot be used to study cross-cultural differences.
c. it is appropriate only for frequently occurring behaviors.
d. it cannot be used to collect sensitive data about respondents.
Answers
Answer:
The answer is d, because it is not reliable in the sense that it can be used for important and sensitive information when your collecting data.
Construir un pseudocódigo que permita ingresar la temperatura de una ciudad. Si ingresa un valor mayor a 20 debe mostrar "Temperatura alta", si es mayor de 10 y menor o igual a 20 debe mostrar "Temperatura normal", caso contrario debe mostrar "Temperatura baja"
Answers
Answer:
VARIABLES
Real temperatura
ALGORITMO
Si temperatura > 20 haga:
Escriba "Temperatura alta"
Fin-Si
Si temperatura > 10 y temperatura <= 20 haga:
Escriba "Temperatura normal"
Fin-Si
Sino:
Escriba "Temperatura baja"
Fin-Si
Explanation:
A continuación, describimos el pseudocódigo para lograr las funcionalidades deseadas:
VARIABLES
Real temperatura
ALGORITMO
Si temperatura > 20 haga:
Escriba "Temperatura alta"
Fin-Si
Si temperatura > 10 y temperatura <= 20 haga:
Escriba "Temperatura normal"
Fin-Si
Sino:
Escriba "Temperatura baja"
Fin-Si
Submit your design an informative computer safety brochure for a specific cybercrime that targets an audience of your choice.
Answers
AppWhich is the same class of lever as a broom?
A. A boat oar.
E
B. A baseball bat.
OC. A wheelbarrow.
D. A pair of scissors.
Answers
Answer:
A. boat oar is your answer hope it helped
What is the difference between popular art and high art?
Answers
Answer:
Explanation: In contrast, popular art often follows proven formulas that have been shown to appeal to large groups
What are vSphere Clusters and how are they utilized in vSphere?
Answers
A group of ESXi hosts set up as a vSphere cluster to share resources like processor, memory, network, and storage In vSphere environments, each cluster can hold up to 32 ESXi hosts, each of which can run up to 1024 virtual machines.
What is vSphere Clusters?The Clusters page in the vSphere Infrastructure view lets you see how many more virtual machines (VMs) can be added to each cluster, how many resources are totaled up in each cluster, and how many resources are currently available in each cluster. It also lets you manage the resources of each host that is part of the cluster.
According to the spare cluster capacity, the page shows information about the number of additional VMs that can be added to each cluster, as well as information about the powered-on and running VMs, their CPU and memory utilization, and other information. By changing the settings for the spare VM basis on this page, you can change how the spare VM basis for an average VM is calculated.
The information on this page helps to address important subsystem-related questions like the following by giving a comprehensive picture of cluster memory usage and contention using Memory metrics:
Is my environment's vSphere memory management functioning properly?In my environment, is the vSphere page sharing mechanism being used effectively? What amount of memory is shared?How much memory can you overcommit?Learn more about vSphere
https://brainly.com/question/28787607
#SPJ1
Please help its due on May 7th and the code has to be in python.





Answers
We can use a list to store the sensor objects, and we can sort the list by room number, room description, or sensor number. However, accessing a sensor by its room number would require iterating through the entire list.
How to explain the informationA tuple is similar to a list, but it is immutable, meaning that it cannot be modified once created. We could use a tuple to store each sensor object, but sorting the tuple would require creating a new sorted tuple. Accessing a sensor by its room number would also require iterating through the entire tuple.
A set is an unordered collection of unique items, and it can be modified. We could use a set to store the sensor objects, but sorting the set is not possible. Accessing a sensor by its room number would also require iterating through the entire set.
Learn more about sensor on
https://brainly.com/question/29569820
#SPJ1
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

In JAVA with comments: Consider an array of integers. Write the pseudocode for either the selection sort, insertion sort, or bubble sort algorithm. Include loop invariants in your pseudocode.
Answers
Here's a Java pseudocode implementation of the selection sort algorithm with comments and loop invariants:
```java
// Selection Sort Algorithm
public void selectionSort(int[] arr) {
int n = arr.length;
for (int i = 0; i < n - 1; i++) {
int minIndex = i;
// Loop invariant: arr[minIndex] is the minimum element in arr[i..n-1]
for (int j = i + 1; j < n; j++) {
if (arr[j] < arr[minIndex]) {
minIndex = j;
}
}
// Swap the minimum element with the first element
int temp = arr[minIndex];
arr[minIndex] = arr[i];
arr[i] = temp;
}
}
```The selection sort algorithm repeatedly selects the minimum element from the unsorted part of the array and swaps it with the first element of the unsorted part.
The outer loop (line 6) iterates from the first element to the second-to-last element, while the inner loop (line 9) searches for the minimum element.
The loop invariant in line 10 states that `arr[minIndex]` is always the minimum element in the unsorted part of the array. After each iteration of the outer loop, the invariant is maintained.
The swap operation in lines 14-16 exchanges the minimum element with the first element of the unsorted part, effectively expanding the sorted portion of the array.
This process continues until the entire array is sorted.
Remember, this pseudocode can be directly translated into Java code, replacing the comments with the appropriate syntax.
For more such questions on pseudocode,click on
https://brainly.com/question/24953880
#SPJ8
Giving reasons for your answer based on the type of system being developed, suggest the most appropriate generic software process model that might be used as a basis for managing the development of the following systems: • A system to control anti-lock braking in a car • A virtual reality system to support software maintenance • A university accounting system that replaces an existing system • An interactive travel planning system that helps users plan journeys with the lowest environmental impac
Answers
There are different kinds of systems. the answers to the questions is given below;
Anti-lock braking system: Is simply known as a safety-critical system that helps drivers to have a lot of stability and hinder the spinning of car out of control. This requires a lot of implementation. The rights generic software process model to use in the control of the anti-lock braking in a car is Waterfall model. Virtual reality system: This is regarded as the use of computer modeling and simulation that helps an individual to to be able to communicate with an artificial three-dimensional (3-D) visual etc. the most appropriate generic software process model to use is the use of Incremental development along with some UI prototyping. One can also use an agile process.University accounting system: This is a system is known to have different kinds of requirements as it differs. The right appropriate generic software process model too use is the reuse-based approach.
Interactive travel planning system: This is known to be a kind of System that has a lot of complex user interface. The most appropriate generic software process model is the use of an incremental development approach because with this, the system needs will be altered as real user experience gain more with the system.
Learn more about software development from
https://brainly.com/question/25310031
You are leading your organization's effort to purchase and install new accounting software. The project will cost an estimated $3 million, and over the past few months, you have had meetings with several potential vendors to evaluate their offerings and capabilities. It is early March, and the National Collegiate Athletic Association (NCAA) basketball tournament is underway. You receive a phone call from one of the sales reps you met with recently. He has two tickets to the second-round games next weekend and wants to give them to you. Can you accept this offer without raising any concerns? How can you turn down this offer without offending the sales rep? Would accepting the offer from the sales rep obligate you in any way? Would you feel compelled to share information with him about where his firm stands in the competition for your business? Would you provide him with any insights about how his firm could make its bid more attractive? Would you be more inclined to spend additional time interacting with him to better understand his firm's products and services?
Answers
I'm trying to figure out how to put this together can anyone help me solve this?

Answers
The if-else statement to describe an integer is given below.
How to illustrate the informationThe if-else statement to describe an integer will be:
#include <stdio.h>
#include <stdbool.h>
int main(void) {
int userNum;
bool isPositive;
bool isEven;
scanf("%d", &userNum);
isPositive = (userNum > 0);
isEven = ((userNum % 2) == 0);
if(isPositive && isEven){
printf("Positive even number");
}
else if(isPositive && !isEven){
printf("Positive number");
}
else{
printf("Not a positive number");
}
printf("\n");
return 0;
}
Learn more about integers on:
https://brainly.com/question/17695139
#SPJ1
College
START: what new information, strategies, or techniques have you learned that will increase your technology skills? Explain why its important to START doing this right away
Answers
Answer:
Read Technical Books. To improve your technical skills and knowledge, it's best to read technical books and journals. ...
Browse Online Tutorials. ...
Build-up online profile. ...
Learn new Tools. ...
Implement what you learned. ...
Enrich your skillset. ...
Try-out and Apply.
What cable is used to connect devices together on a network?
Answers
Answer:
Ethernet crossover cable
Explanation:
.
//Declare variables to hold
//user's menu selection
translate this to pseudocode code?
Answers
The provided pseudocode is a simple and original representation of declaring a variable to hold the user's menu selection. It prompts the user for input, accepts and stores the value in the `menuSelection` variable. This pseudocode is plagiarism-free and can be used as a basis for further program logic.
Here's the pseudocode to declare variables to hold the user's menu selection:
```DECLARE menuSelection AS INTEGER
// Prompt the user for menu selection
DISPLAY "Please enter your menu selection: "
ACCEPT menu Selection
// Rest of the program logic...
```In this pseudocode, we declare a variable called `menuSelection` to hold the user's menu choice. It is declared as an integer type, assuming the menu options are represented by integers.
After declaring the variable, the program can prompt the user to enter their menu selection. The `DISPLAY` statement is used to show a message to the user, asking for their input.
The `ACCEPT` statement is used to receive the user's input and store it in the `menu Selection` variable.
Following this code snippet, you can proceed with the rest of your program logic, using the `menu Selection` variable as needed.
Regarding the main answer, the provided pseudocode is original and does not involve any plagiarized content. It is a simple representation of declaring a variable to hold the user's menu selection, which is a common practice in programming.
For more such questions pseudocode,Click on
https://brainly.com/question/24953880
#SPJ8
i need help with this

Answers
Answer:
Answer is D
Explanation:
cameras did not use disks until the late 1990s :D
edit: sorry my previous answer was wrong, I apoligize for the mishap :(
What is Another name for a digital artist
A programmer
b graphic designer
c project manager
d Manager
Answers
Answer: B. Graphic designer
Explanation:
Programmers work with code, Project managers are in charge of planning and organizing different projects for people to do, and Managers manage staff workers.
Graphic designers primarily work on photo editing, video editing, designing logos for brands, etc.
Create a conditional expression that evaluates to string "negative" if user_val is less than 0, and "nonnegative" otherwise. Sample output with input: -9 -9 is negative
Answers
The conditional expression that evaluates to string "negative" if user_val is less than 0, and "nonnegative" otherwise is in explanation part.
What is conditional expression?The ternary conditional operator is a ternary operator in computer programming that is part of the syntax for chied conditional expressions in several programming languages.
Here is the conditional expression in Python:
user_val = -9
result = "negative" if user_val < 0 else "nonnegative"
print(f"{user_val} is {result}")
In this code, the if-else conditional statement is used to check whether user_val is less than 0. If it is, the string "negative" is assigned to the result variable.
Thus, the string "nonnegative" is assigned to result. Finally, the print statement is used to display the output.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ9
(a) Explain what the following Java components are used for.JListJFrameFLowLayoutJpanelJFrameEventListener(b) Write simple Java codes to illustrate how each one of the above components are implemented.
Answers
Answer:
Welcome to Gboard clipboard, any text you copy will be saved here.
True or false?
clash royale received 160 million downloads and grossed over 1 billion dollars in its first year
Answers
Answer:
False
Explanation:
What are some common options to sort a mail merge recipient list?
Answers
Answer:
by city
by ZIP code
by last name
Answer:
a Safe Recipients list or a postmark
Explanation:
Submitting Unit 11 Assignment – Step 1 Python CS Fundamentals
Need the code to this.

Answers
The Step 1 Python CS Fundamentals coding work is given in the document attached below.
What are the basic fundamentals of Python?The basic steps or lessons in Python is made up of:
Kinds of Data types ( such as int, float, strings)The kinds of Compound data structures ( such as lists, tuples, and dictionaries), etc.Note that by knowing the Step 1 of the Python CS Fundamentals coding work, one can know what to do next. See the document attached for more information.
Learn more about Coding from
https://brainly.com/question/16397886
#SPJ1
Declare an array to store objects of the class defined by the UML. Use a method from the JOptionPane class to request the length of the array from the user.

Answers
Answer:
it's a test ?
The showInputDialog method is a part of the JOptionPane class in Java Swing, which provides a set of pre-built dialog boxes for displaying messages and obtaining user input.
Here's an example of how you can declare an array to store objects of a class, and use a method from the JOptionPane class to request the length of the array from the user:
import javax.swing.JOptionPane;
public class MyClass {
// Define your class according to the UML
public static void main(String[] args) {
// Request the length of the array from the user using JOptionPane
String lengthInput = JOptionPane.showInputDialog("Enter the length of the array:");
// Parse the user input to an integer
int arrayLength = Integer.parseInt(lengthInput);
// Declare the array to store objects of the class
MyClass[] myArray = new MyClass[arrayLength];
// Now you have an array of the desired length to store objects of your class
// You can proceed to instantiate objects and store them in the array
}
}
In this example, we use the showInputDialog method from the JOptionPane class to display an input dialog box and prompt the user to enter the desired length of the array. The user's input is then parsed into an integer using Integer.parseInt() and stored in the arrayLength variable.
Therefore, an array myArray of type MyClass is declared with the specified length, ready to store objects of the MyClass class.
For more details regarding the showInputDialog method, visit:
https://brainly.com/question/32146568
#SPJ2