GIVING 10 or 20 POINTS for brainliest HELP ASAP!! Instructions Click the links to open the resources below. These resources will help you complete the assignment. Once you have created your file(s) and are ready to upload your assignment, click the Add Files button below and select each file from your desktop or network folder. Upload each file separately. Your work will not be submitted to your teacher until you click Submit. Documents Upload Instructions File Upload Accepted file types: .ppt, .pptx, .xls, .xlsx, .doc, .docx, .zip, .pdf, .accdb, .msg
Answers
Answer:
sorry it wont let me do it
Explanation:
Related Questions
Tonya is creating a program that will allow the user to input their work address. Which kind of variable should Tonya use for this?
A.
a syntax variable
B.
a float variable
C.
a string variable
D.
an alphabetic variable
Answers
Answer:
B.
a float variable is the answer
Explanation:
becouse it is float variable
What will be the result of the following lines of CSS?
body{
background-color:yellow;
}
A.
The background of the header will be yellow.
B.
The text will be highlighted yellow.
C.
The background of the body of the webpage will be yellow.
D.
The photo will change to a yellow box if the user clicks on the photo.
Answers
Answer:
C.
Explanation:
The correct option that explains the result of the given lines of CSS is:
C. The background of the body of the webpage will be yellow.
The CSS code provided sets the background color of the body element to yellow. The "body" selector targets the entire body of the webpage, and the "background-color" property sets the background color to yellow. This means that the background of the entire webpage will be displayed in yellow.
Answer:
C. The background of the body of the webpage will be yellow.
Which of the following events happened first?

Answers
Answer:
D. ARPANET was created
Explanation:
The correct answer is D because ARPANET was created in October 1969, Web 2.0 was created in 1999, email was invented in 1971, and the world wide web was created in 1989
Answer:
D. ARPANET was developed
Explanation:
lol took the quiz just now
1. What do you think is the most important event in the history of the internet? What event has had the biggest impact on your daily life?
Answers
Answer:
The biggest event in internet history was YuTubers punching each other in the face. Months of hype came to a peak Saturday for the self-declared “biggest event in internet history” a boxing match between two YuTube celebrities in Manchester, England.
Explanation:
There is no particular event but the whole journey till now which shaped my personality. Every person even if they are the worst has something good in them.
The impact it has had:
Developed into the globally used Internet which is now integrated into modern society and is seen as an essential for good quality of life.
Mario forgot to do his book report until midnight the night before it was due, so he used a couple of paragraphs from a book review he found online as part of his report. What sort of ethical violation is he guilty of?
Question 3 options:
A hacking
B data breach
C plagiarizing
D piracy
Answers
Answer:
Explanation:
the answer is C
Answer:
c.
Explanation:
he is copying someone else's work that is ILLEGAL
What process is a project manager doing when she or he defines and documents the stakeholders' needs to meet the project objectives?
Answers
The point on the middle of an edge in SketchUp is called a...
midsurface
midpoint
midline
midplane
Answers
Answer:
.
Explanation:
.
Which best describes desktop publishing? the process of designing and laying out printed material the positioning of text, graphics, and white space on a page the style of letters and how they are arranged the use of images and colors
Answers
Explanation:
the process of designing and laying out printed material.
Answer:A photographic proof where all colors are shown in blue, best used for spot color jobs, and it is used primarily to ... WYSIWYG is technical jargon that describes.
Explanation:
Write the importance of software in computer . In 6 points
Answers
Answer:
Software is a set of instructions, data or programs used to operate computers and execute important tasks but can also help you work more efficiently.
Uses of Software
Uses of Software in Office.Uses of Software in Business.Uses of Software for Play Game.Uses of Software in Shop.Uses of Software for Entertainment.Explanation:
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
I was logging into my origin account and this popped up. I can’t seem to click the NEXT button at the bottom. The blank spaces says a name is optional though.
1: I tried typing a name in (didn’t work)
2: tried restarting the computer (don’t work)
3: logging out doesn’t work either.
HELPPP!!
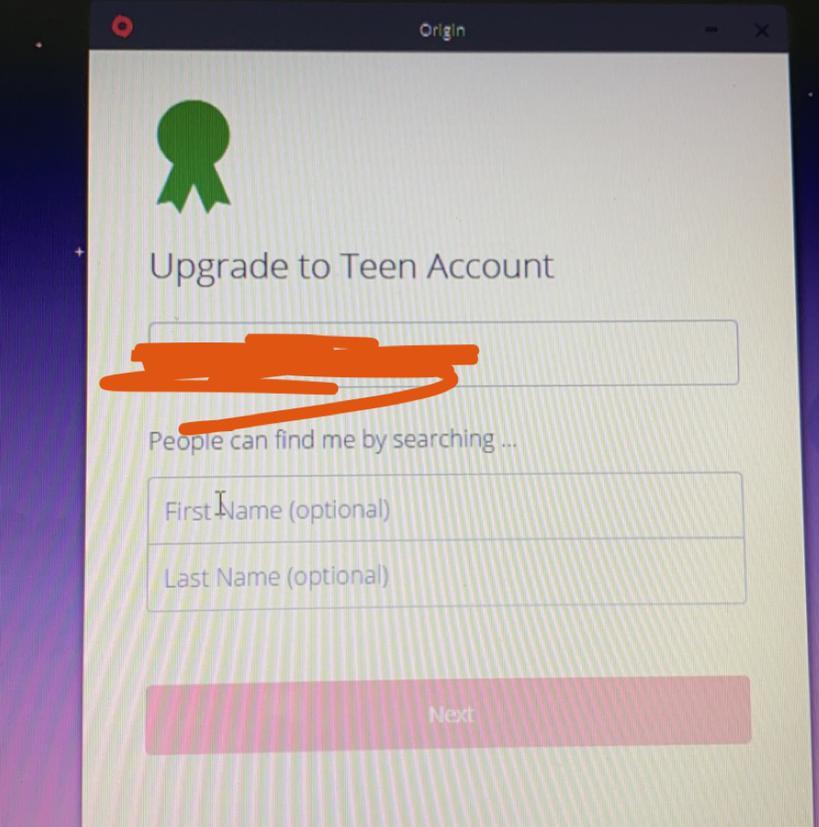
Answers
Answer:
Contact the company to find out what the problem is.
Explanation:
Is a poster the best media form to make a call to action to the government and major corporations? What other media forms could be effective?
Answers
Answer:
A Poster can be an effective media form to make a call to action to the government and major corporations, as it allows for visually impactful messaging. However, other media forms could also be effective, such as:
Social media campaigns: Utilize platforms like Twitt..er, Fa..cebook, or Ins..tagram for awareness and mobilization.Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.Answer:
Explanation:
Online petitions: Collect signatures and demonstrate public support.Video campaigns: Engage viewers emotionally through compelling videos.Mass media advertising: Utilize TV, radio, or print media for broader reach.Advocacy websites: Provide information, resources, and a platform for action.Public demonstrations and rallies: Gather supporters for visible advocacy.what is a logic circuit?
Answers
Answer:
A logic circuit is an electronic circuit that performs a specific logical operation on one or more binary inputs to produce a binary output. Logic circuits are made up of electronic components, such as transistors, diodes, and resistors, which are arranged in a specific way to implement a particular logical function, such as AND, OR, NOT, and XOR.
Logic circuits are used in many digital electronics applications, such as computers, calculators, and electronic control systems. They are designed to process digital signals, which consist of binary data represented by voltage levels or current flow. By manipulating these signals with logical operations, logic circuits can perform arithmetic, comparison, and decision-making functions, among others.
There are many different types of logic circuits, ranging from simple gates that perform basic logical functions, to more complex circuits that implement more advanced functions, such as flip-flops and registers that can store and manipulate data. The design and analysis of logic circuits is an important area of study in electrical engineering and computer science.
Explanation:
Answer: a circuit for performing logical operations on input signals.
Explanation: Pleas give brainliest
If you want to develop an Android app, you need to become a registered developer with which platform?

Answers
Check photos
what is 8 4/7 divided by 15
Answers
Answer: 4/7
Explanation:
8 4/7 ÷ 15
60/7× 1/15
=4/7
ok so...you first are going to convert the mix fraction 8 4/7 to improper fraction by multiplying the denominator and the whole number which is 56 then add the numerator 56 +4= 60 and put back the denominator which is going to be 60/7.
Then flip the fraction or the whole number 15 which is also 15/1 that is on the right which is going to be 1/15 and change the division sign to multiplication which is going to be 60/7 × 1/15.
then you can cancel, 15 go into 60, 4 times, so you are going to multiply 4 times 1 and 7 times one, which gives you 4/7.
I hope this help you to understand
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
Which device would help someone train for a marathon?
Drone
Navigation system
Smart watch
VR headset
Answers
i hope this is correct and i hope it helps
I think Smart watches will be good as it will track your breathing, heartbeat, and steps. VR head set will not make you go so far, drones can look at the track you are running but it is not helping you run, and i don’t know about navigation systems.
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
Jaime has been hired as a consultant for a company. His task is to help the company spend less time and money writing code. Jaime notices that, even for very complicated programs, the programmers at this company start programming without an overall plan for the development of the code. What might Jaime suggest that they do instead?
A.
begin by writing the final lines of the program instead of the first lines
B.
program in C++ instead of in Python
C.
begin by creating a pseudocode
D.
spend more time debugging
Answers
Answer:
C
Explanation:
i had to answer this question on a test and ended up getting it right, hope this helps!! :D
1 What was the first European colony in the western part of North America?
Santa Fe
Rio Grande
Albuquerque
St. Augustine
2 What did the Spanish bring to the New World?
Furs
Honeybees and tobacco
Barley, oats, wheat, and oranges
Gold and Juniper
3 What was used to cure skin irritations?
Horehound
Carrots
Garlic
Cornstarch
4 Why did Hernando de Soto explore Florida?
To establish permanent settlements
To find both gold and a water passage to China and Japan
To find a mythical group of seven cities made of gold
To spread Christianity
.
5 What did the Proclamation of 1763 do?
Prevented French from going past the mountains
Prevented fur trade from going on past the mountains
Prevented settlers from going past the mountains
Prevented Native Americans from going past the mountains
6 What did a joiner do?
Taught school
Built houses
Joined wood together into things like cupboards and staircases
Introduced members of the colony to the church
7 Which of the plants below was used to cure diseases?
Carrots
Horehound
Potatoes
Garlic
8 How did the False Face society heal people?
1They would wear very frightening masks to scare the evil spirits away. They believed that evil spirits caused illness.
2They would use various herbs and wild plants to create a paste which they would rub all over the sick person.
3They were the first of all Native Americans to practice conventional medicine.
4They would have patients wear a mask for 30 days and nights to ward off the evil spirits that they believed caused illness.
PLS HELP ME!
Who was the greatest enemy of the Susquehannock?
Iroquois
Cherokee
Mohawk
Apache
Answers
2.Barley, Oats, Wheat, and Oranges
3. Horehound
4. To find a mythical group of seven cites made of gold
(I made this up teehee) what anime is katski bakugo from
Answers
Advantages and disadvantages of using the command-line interface to manage files and folders
PLZ HELP I WILL MARK YOU AS BRAINLIEST ASAP
Answers
Hope this helps! And I hope to get brainliest!
Which statements properly describe hackers? Check all that apply.
Hackers secretly get into other people’s computers.
Hackers make their identities known.
Hackers fix peoples’ broken computers.
Hackers steal information and cause damage.
Hackers are the same as computer viruses.
Answers
Answer:
1,4
Explanation:
took the test
Hackers secretly get into other people’s computers and Hackers steal information and cause damage.
What are Hackers?Iain Softley's 1995 criminal thriller Hackers, starring Jonny Lee Miller, Angelina Jolie, Jesse Bradford, Matthew Lillard, Laurence Mason, Renoly Santiago, Lorraine Bracco, and Fisher Stevens, is an American production.
The movie follows a group of high school hackers as they seek to steal something. It echoes the ideas stated in the Hacker Manifesto, which is cited in the movie and was written in the middle of the 1990s when the Internet was just starting to gain widespread public acceptance.
The world of the electron and the switch. We exist without regard to our race, nation of origin, or place of worship, and you still refer to us as criminals.
Therefore, Hackers secretly get into other people’s computers and Hackers steal information and cause damage.
To learn more about Hackers, refer to the link:
https://brainly.com/question/30563643
#SPJ3
give me a random piece of Binary code to translate
Answers
Answer:
100110
Explanation:
Answer:
01001000 01000001 01001000 01000001 00100000 01000011 01001111 01001101 01010000 01010101 01010100 01000101 01010010 01010011 00100000 01010111 01001001 01001100 01001100 00100000 01010010 01010101 01001100 01000101 00100000 01010100 01001000 01000101 00100000 01010111 01001111 01010010 01001100 01000100
create a 3 to 5 step plan for checking out a post on social media for the next time you encounter something questionable.
Answers
2. Block or unfollow user
3. Tell parent
Answer:
Report. Block. Tell mommy or dada
Explanation:
Eliza is the head instructor at a ballet academy. Eliza works in the ______ pathway of the Arts, AV Technology, and Communication cluster.
Question 11 options:
A. AV Technology and Film
B. Printing Technology
C. Journalism and Broadcasting
D. Performing Arts
Answers
Identify each situation as either internal conflict or external conflict.
a teacher thinking about
whether to call the parents
of a misbehaving child
siblings fighting over the
television remote
a man on a diet wondering if
it would be OK to eat a
cheeseburger
two strangers arguing at the
supermarket over who will
check out first
Answers
Answer:
internal
external
internal
external
B) Internal Conflict
C) Internal Conflict
D) External Conflict
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
what is the answer i need them now pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls

Answers
Answer: Insert ribbon > table drop down menu
Explanation:
Answer:Insert ribbon > table drop down menu
Explanation:
multiple choice q: pls answer
Marco has just written an algorithm for how to solve a Sudoku puzzle. He says that he just written a computer program. Is Marco correct?
A.
Yes, because an algorithm is a computer program
B.
No, because Marco’s algorithm is most likely incorrect
C.
No, because an algorithm for a Sudoku puzzle cannot be run by a computer
D.
No, because a program must be written in computer code, and algorithms are not code
Answers
Answer:
D
Explanation:
No, because a program must be written in computer code, and algorithms are not code