defense in depth is a known practice to mitigate the extent of unauthorized access. which of the following illustrates defense in depth?
Answers
At work, employees increasingly bring and use their own devices. Thankfully, when users use their own devices, advanced technology allows for specific authorization.
A bank would never leave its assets alone inside a safe without guards. In most cases, entering the safe necessitates going through a number of layers of security, some of which may consist of locked doors with unique access controls and human guards. Closed-circuit television, motion sensors, and alarm systems that can quickly identify unusual activity could also be used to monitor the safe's location. The room could be filled with tear gas or the doors could lock automatically upon hearing an alarm. The police could also be notified. As in the previous illustration, layered security is referred to as defense in depth. The three components required to safeguard assets are provided by overlapping layers of this security: avoidance, discovery, and reaction. Defense in depth also tries to make up for the strengths of two or more security layers by making up for the weaknesses of one layer. In the world of information security, defense in depth calls for a series of security devices that protect, detect, and respond to system attacks. To protect the network from potential intruders, routers, firewalls, and intrusion detection systems (IDS) are included in a typical Internet-attached network that has been designed with security in mind. uses real-time human monitors and traffic analyzers to look for anomalies while the network is being used to find any breach in the layers of protection; and relies on automated mechanisms to deny access to the system or remove it from the network when an intruder is detected. Last but not least, before the integrated system is put into use, the security of each of these mechanisms needs to be thoroughly tested. After all, the weakest link in a chain is only as good as the rest.
To know more about intrusion detection systems visit https://brainly.com/question/13993438?referrer=searchResults
#SPJ4
Related Questions
I have a .NET 6 basic website that I built using Entity Framework as the database for updating pages. I am ready to deploy the site/database to a live server somewhere, but I am looking for the best option.
The website is built using the latest .NET Framework 6.0, with Entity Framework 6.0.3. I know about HostGator, GoDaddy and InterServer.
I have read stuff online that said HostGator doesn't actually support the latest .NET 6.0, and GoDaddy only supports .NET Core 3.2?
HostGator is rougly $5.00 a month, GoDaddy is $6.00, and InterServer is $8.00.
I am leaning towards InterServer, because I have read that InterServer supports the latest .NET 6.0 and Entity Framework.
I am used to deploying to servers using LAMP stack, Linux, Apache, PHP, MySQL... The prices there are lower and it is fairly simple to setup. I figure there has to be something similar for windows and .NET.
For something similar, am I looking for Shared Hosting? Or VPS? I really don't understand what I need. I was hoping for Shared Hosting, export my SQL Server database, create it on the live server, then FTP my files over.
InterServer seems like it supports everything, so I am leaning towards that. I know no matter what, Windows Hosting is going to be a little bit more expensive. I just want something that I know is going to work with the latest .NET technologies.
Does anyone have any suggestions?
Answers
In the above scenario, i will recommend Bluehost or InterServer since it is good and can meet your requirement.
What is Bluehost?Bluehost is known to be a software that is said to be a little bit better than HostGator in the aspect of security as it gives offer free SSL certificates, malware tools, and others.
Therefore, In the above scenario, I will recommend Bluehost or InterServer since it is good and can meet your requirement.
Learn more about Bluehost from
https://brainly.com/question/17062016
#SPJ1
Ensure the file named Furniture.java is open.
The file includes variable declarations and output statements. Read them carefully before you proceed to the next step.
Design the logic and write the Java code that will use assignment statements to:
Calculate the profit (profit) as the retail price minus the wholesale price
Calculate the sale price (salePrice) as 25 percent deducted from the retail price
Calculate the sale profit (saleProfit) as the sale price minus the wholesale price.
Execute the program by clicking Run. Your output should be as follows:
Item Name: TV Stand
Retail Price: $325
Wholesale Price: $200
Profit: $125
Sale Price: $243.75
Sale Profit: $43.75
91011121314151617181920212223242526272829303132678345
double profit;
double saleProfit;
// Write your assignment statements here.
Logic:
profit=retailPrice-wholesalePrice
salePrice=retailPrice-(retailPrice*25)/100;
saleProfit=salePrice-wholesalePrice;
can someone write this how the code would be written i think i have it correct but i am getting and error when i run the code
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that calculate the sale profit (saleProfit) as the sale price minus the wholesale price.
Writting the code:public class Furniture
{
public static void main(String args[])
{
String itemName = "TV Stand";
double retailPrice = 325.00;
double wholesalePrice = 200.00;
double salePrice;
double profit;
double saleProfit;
// Write your assignment statements here.
profit = retailPrice - wholesalePrice;
salePrice = retailPrice * (1 - 0.25);
saleProfit = salePrice - wholesalePrice;
System.out.println("Item Name: " + itemName);
System.out.println("Retail Price: $" + retailPrice);
System.out.println("Wholesale Price: $" + wholesalePrice);
System.out.println("Profit: $" + profit);
System.out.println("Sale Price: $" + salePrice);
System.out.println("Sale Profit: $" + saleProfit);
System.exit(0);
System.exit(0);
}
}
See mroe about JAVA at brainly.com/question/12975450
#SPJ1

Write short notes on the types of mouse
Answers
Explanation:
Definition – Mouse is a pointing input device of computer. Mouse help to control cursor that is visible on the computer screen while moving the mouse on flat surface place. Its name was originated by its shape that look as mouse, because it has elliptical shaped with mouse tail. Mouse reduces usability of a keyboard
In object-oriented programming, what are attributes? (5 points)
Actions an object performs
Characteristics of an object
Instances of an object
Templates of an object
Answers
In object-oriented programming, attributes refer to the characteristics or properties of an object. They describe the state or data associated with an object and define its behavior and characteristics.
Here are five key points about attributes:
Characteristics of an object: Attributes represent the state or properties of an object. They define the data associated with the object and describe its characteristics. For example, if we have an object representing a car, attributes could include its color, model, year, and mileage.
Data variables: Attributes are typically implemented as data variables within a class. Each object instantiated from the class will have its own set of attribute values. These variables store the specific data associated with each object.
Object state: Attributes define the state of an object, meaning they represent the values that the object holds at any given time. The state can change as the object's attributes are modified or updated during the execution of a program.
Learn more about attributes on:
https://brainly.com/question/30024138
#SPJ1
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Use the strategy of the decimal to binary conversion implemented in Project 4, and the bit shift left operation defined in Project 5 to code a new encryption algorithm. The algorithm should Add 1 to each character’s numeric ASCII value. Convert it to a bit string. Shift the bits of this string one place to the left. A single-space character in the encrypted string separates the resulting bit strings. An example of the program input and output is shown below: Enter a message: Hello world! 0010011 1001101 1011011 1011011 1100001 000011 1110001 1100001 1100111 1011011 1001011 000101
Answers
The Python code that implements the encryption algorithm described is given below:
The Python Codedef encrypt(message):
# Initialize an empty string to store the encrypted message
encrypted = ""
# Loop through each character in the message
for char in message:
# Add 1 to the character's numeric ASCII value
new_char = ord(char) + 1
# Convert the new character to a bit string
bit_string = bin(new_char)[2:]
# Shift the bits of the bit string one place to the left
shifted_bit_string = bin(int(bit_string, 2) << 1)[2:]
# Add the shifted bit string to the encrypted message
encrypted += shifted_bit_string + " "
# Return the encrypted message, removing the last space
return encrypted[:-1]
# Example usage
message = "Hello world!"
encrypted_message = encrypt(message)
print(encrypted_message)
Output:
10010010 11001101 10110110 10110110 11000010 00011000 11100010 11000010 11001100 10110110 10010110 00010100
Note that to decrypt the message, you can simply reverse the steps: shift the bits of each bit string one place to the right, convert each resulting bit string to an integer, subtract 1 from each integer to get the original ASCII value, and then convert each ASCII value to its corresponding character.
Read more about encryption algorithms here:
https://brainly.com/question/9979590
#SPJ1
Mrs Jones had p hens then she decided to buy p more hens. how many hens does she have in all?
Answers
Answer:
2p
Explanation:
if she had p, then she got p again, she got two p amounts. p+p = p*2 = 2p
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Select the correct answer from each drop-down menu.
Which two components help input data in a computer and select options from the screen, respectively?
✓inputs data into computers in the form of text, numbers, and commands. However, a
commands from the screen.
A
Reset
Next
✓selects options and
Answers
Which two components help input data in a computer and select options from the screen, respectively?
✓ Keyboard inputs data into computers in the form of text, numbers, and commands. However, a
✓ Mouse selects options and commands from the screen.
A
Reset
Next
To know more about input data refer here
https://brainly.com/question/30256586#
#SPJ11
A cookie that lasts only until the browser is closed is called a ________ cookie. 1. session 2. persistent 3. temporary 4. timed
Answers
Answer:
Session Cookie
Explanation:
A session cookie is a file containing an identifier (a string of letters and numbers) that a website server sends to a browser for temporary use. When the browser closes at the end of a session, the file is deleted.
A session cookie is a document holding an identification, which would be a string of numbers and letters, that a web server sends to a browser for temporary use during a set period.
This file gets erased when the browser is closed after a transaction. The temporary cookie is also known as a transitory cookie.These cookies are only ever retained on a device until the web browser shuts down. Permanent cookies remain on your device after you have completed your browsing session until they expire or are erased, therefore A session cookie lasts till the browser was closed.Therefore, the answer is "Option 2".
Learn more about the session cookie:
brainly.com/question/804307
Which search strategy is most similar to greedy search?
A.
depth-first search
B.
breadth-first search
C.
bidirectional search
D.
uniform-cost search
Answers
Answer:
I think the answer would be A.
Explanation:
If I'm wrong plz let me know (I think I may be wrong)
Multimedia Presentation: Mastery Test
Select the correct answer.
Helen wants to use actual voice testimonials of happy employees from her company in her presentation. What is the best way for her to use these
testimonials in the presentation?
OA. She can provide a link in her presentation where the audience can listen to the testimonials.
She can ask the employees to write down their thoughts for the presentation.
She can record the testimonials directly in her presentation.
D. She can read out the testimonials from a transcript.
B.
O C.
Reset
>
Next
Answers
The best way for Helen to use actual voice testimonials of happy employees from her company in her presentation is A) She can provide a link in her presentation where the audience can listen to the testimonials.
Using actual voice testimonials adds authenticity and credibility to Helen's presentation.
By providing a link, she allows the audience to directly hear the employees' voices and genuine expressions of satisfaction.
This approach has several advantages:
1)Audio Engagement: Listening to the testimonials in the employees' own voices creates a more engaging experience for the audience.
The tone, emotions, and enthusiasm conveyed through voice can have a powerful impact, making the testimonials more relatable and persuasive.
2)Employee Representation: By including actual voice testimonials, Helen gives her colleagues an opportunity to have their voices heard and to share their positive experiences.
This approach emphasizes the importance of employee perspectives and allows them to become active participants in the presentation.
3)Convenience and Accessibility: Providing a link allows the audience to access the testimonials at their own convenience.
They can listen to the testimonials during or after the presentation, depending on their preferences.
It also allows for easy sharing and revisiting of the testimonials.
4)Time Management: Including voice testimonials via a link enables Helen to efficiently manage the timing of her presentation.
She can allocate the appropriate time for other aspects of her talk while still giving the audience access to the full testimonials, without the need to rush or omit important information.
For more questions on presentation
https://brainly.com/question/24653274
#SPJ8
Which virus is also known as hybrid virus ?
Answers
Answer:
A multipartite virus
Explanation:
To start slide show of a presentation from the first slide.
A. From Slide Show Tab choose from Beginning button
B. From Slide Show Tab choose View Show button
C. From Slide Show Tab choose Rehearse timing button
D. From Slide Show Tab choose Custom Slide Show button
Answers
step by step explanation:
Answer:
a
Explanation:
Print a message telling a user to press the letterToQuit key numPresses times to quit. End with newline. Ex: If letterToQuit = 'q' and numPresses = 2, print:

Answers
You can find in the photo. Good luck!

In order to implement the classic DoS flood attack, the attacker must generate a sufficiently large volume of packets to exceed the capacity of the link to the target organization. Consider an attack using ICMP echo request (ping) packets that are 500 bytes in size (ignoring framing overhead). How many of these packets per second must the attacker send to flood a target organization using a 0.5-Mbps link
Answers
Answer:
131 packets
Explanation:
Given
W (link ) =0.5 M bits, and Ping packets ( P ) = 500bytes
To flood a target organization that has a bandwidth of W bits using a packet Mbits, you will require a W / P packet
P ( required ) = 500 * 8 = 4000 bits
therefore the W /P packet is calculated as
= 0.5 M bits / 4000 bits
given that : 1 M bits = 1,048,576 bits
0.5 M bits / 4000 bits= 131.07
hence approximately 131 packets/ sec is required to flood the target organization
In VPython, a ___ object is used to create an object that looks like a ball.
1. canvas
2. ball
3. sphere
4. vector
Answers
Answer: canvas
Explanation:
Build a class and a driver for use in searching your computer’s secondary storage (hard disk or flash memory) for a specific file from a set of files indicated by a starting path. Lets start by looking at a directory listing. Note that every element is either a file or a directory.
Introduction and Driver
In this assignment, your job is to write a class that searches through a file hierarchy (a tree) for a specified file. Your FindFile class will search a directory (and all subdirectories) for a target file name.
For example, in the file hierarchy pictured above, the file "lesson.css" will be found once in a directory near the root or top-level drive name (e.g. "C:\") . Your FindFile class will start at the path indicated and will search each directory and subdirectory looking for a file match. Consider the following code that could help you build your Driver.java:
String targetFile = "lesson.css";
String pathToSearch ="
C:\\WCWC"; FindFile finder = new FindFile(MAX_NUMBER_OF_FILES_TO_FIND);
Finder.directorySearch(targetFile, pathToSearch);
File Searching
In general, searching can take multiple forms depending on the structure and order of the set to search. If we can make promises about the data (this data is sorted, or deltas vary by no more than 10, etc.), then we can leverage those constraints to perform a more efficient search. Files in a file system are exposed to clients of the operating system and can be organized by filename, file creation date, size, and a number of other properties. We’ll just be interested in the file names here, and we’ll want perform a brute force (i.e., sequential) search of these files looking for a specific file. The way in which we’ll get file information from the operating system will involve no ordering; as a result, a linear search is the best we can do. We’d like to search for a target file given a specified path and return the location of the file, if found. You should sketch out this logic linearly before attempting to tackle it recursively.
FindFile Class Interface
FindFile(int maxFiles): This constructor accepts the maximum number of files to find.
void directorySearch(String target, String dirName): The parameters are the target file name to look for and the directory to start in.
int getCount(): This accessor returns the number of matching files found
String[] getFiles(): This getter returns the array of file locations, up to maxFiles in size.
Requirements
Your program should be recursive.
You should build and submit at least two files: FindFile.java and Driver.java.
Throw an exception (IllegalArgumentException) if the path passed in as the starting directory is not a valid directory.
Throw an exception if you've found the MAX_NUMBER_OF_FILES_TO_FIND and catch and handle this in your main driver. Your program shouldn't crash but rather exit gracefully in the unusual situation that we've discovered the maximum number of files we were interested in, reporting each of the paths where the target files were found.
The only structures you can use in this assignment are basic arrays and your Stack, Queue, or ArrayList from the previous homeworks. Do not use built-in data structures like Java's ArrayList. To accomplish this, put in the following constructor and method to your ArrayList, Stack, or Queue:
public ArrayList(Object[] input) { data = input;
numElements = input.length;
}
public Object get(int index) {
return data[index];
}
Answers
Answer:
hxjdbjebjdbdubainsinnsubd jdn dkdjddkndjbdubdb su djsbsijdnudb djdbdujd udbdj. djdjdjidndubdu dubdjdbdinndjndidn s dj dudbdjubd dujdjjdjdb djdbdjd udbdudb jndjdbudbdue idbd dudbid d dujejdunebudbdjdj d
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
someone please help me :(!!
Answers
Answer:
its the third one
Explanation:
Write a new method in the Rectangle class to test if a Point falls within the rectangle. For this exercise, assume that a rectangle at (0,0) with width 10 and height 5 has open upper bounds on the width and height, i.e. it stretches in the x direction from [0 to 10), where 0 is included but 10 is excluded, and from [0 to 5) in the y direction. So it does not contain the point (10, 2). These tests should pass:
Answers
Answer:
Explanation:
The Rectangle and Point class is not provided in this question but was found online. Using that code as guidance I created the following method named contains. This method takes in a Point object and checks to see if the x-axis point is inside the parameters of the Rectangle class and then checks the same for the y-axis. If it is inside the Rectangle then the method returns true otherwise it returns false.
def contains(self, point):
return self.width > point.x >= self.corner.x and self.height > point.y >= self.corner.y
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
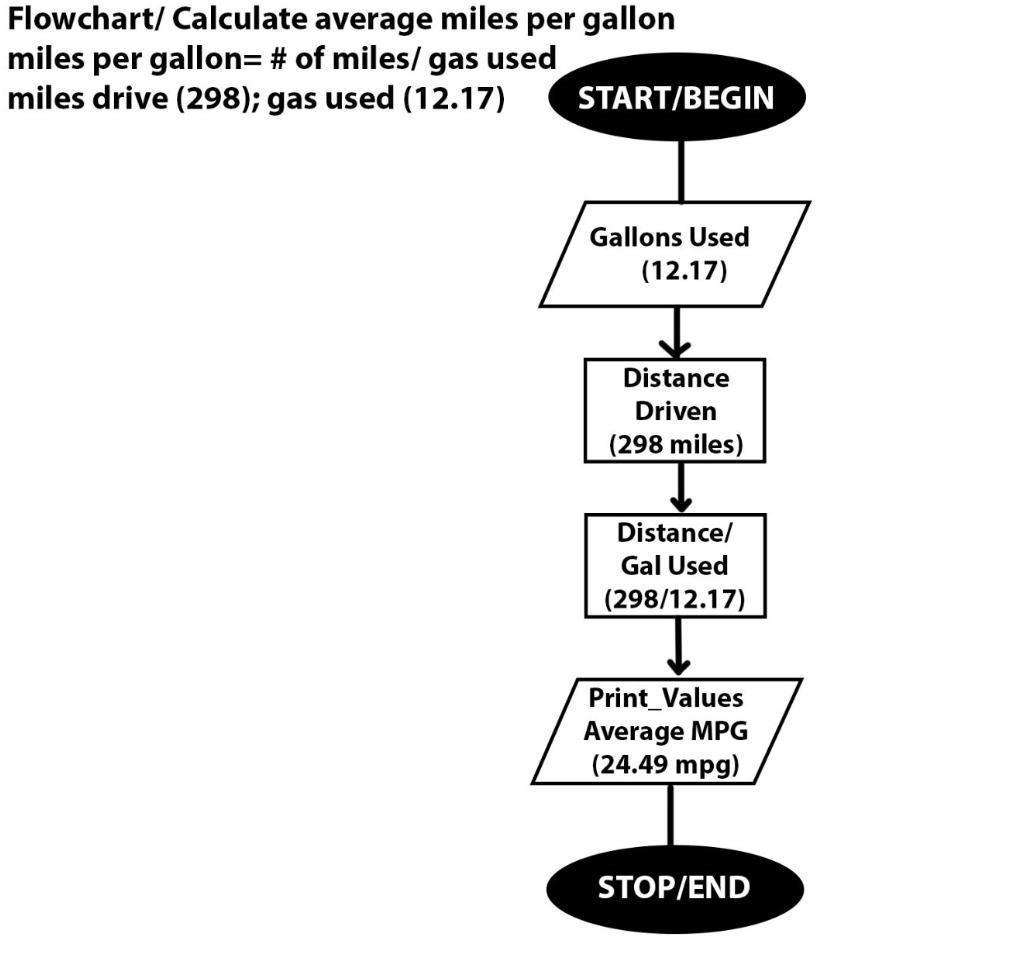
Build a flowchart that will calculate the average miles per gallon obtained on a trip. Input the amount of gas used and the number of miles driven. (The formula to calculate miles per gallon is miles per gallon = number of miles driven / amount of gas used. ) Use these values to test the calculation: (number of miles driven = 298) and (amount of gas used = 12.17). Python language
Answers
Flowchart is in the image and the average miles per gallon attained on a journey. Input the amount of gas consumed and the distance travelled, which comes to 24.4.
INPUT number_of_miles_driven
INPUT amount_of_gas_used
miles_per_gallon = number_of_miles_driven / amount_of_gas_used
PRINT miles_per_gallon
END
You can then use this pseudocode to create a python program and test it with the provided values (number of miles driven = 298) and (amount of gas used = 12.17).
# Calculation of average miles per gallon
number_of_miles_driven = 298
amount_of_gas_used = 12.17
miles_per_gallon = number_of_miles_driven / amount_of_gas_used
print(miles_per_gallon)
You should get the output of 24.4
Pseudocode is a simplified form of a programming language that is used to describe a computer program or algorithm. It is a way of expressing the logic of a program or algorithm using natural language, rather than using a specific programming language.
It is used as a tool to plan and describe the structure of a program before it is written in a specific programming language. It is often used by programmers and computer scientists to express the logic of a program in a clear and concise way, making it easier to understand and implement. Pseudocode is not a programming language and cannot be executed on a computer, but it can be easily translated into a specific programming language once the logic and structure of the program have been determined.
Learn more about Pseudocode here:
https://brainly.com/question/17442954
#SPJ4
what is logic unit of a computer processing unit
Answers
Answer:
Arithmetic logic unit
Explanation:
An arithmetic logic unit (ALU) is a digital circuit used to perform arithmetic and logic operations. It represents the fundamental building block of the central processing unit (CPU) of a computer. Modern CPUs contain very powerful and complex ALUs. In addition to ALUs, modern CPUs contain a control unit (CU).
Your organization's data cannot be pasted here. Only 300 characters are allowed.
Answers
This error message is informing you that the amount of data you are attempting to paste exceeds the maximum limit of 300 characters.
Explain this error in detail?
Many online platforms and applications have character limits in place to prevent users from entering or pasting an excessive amount of data, which can cause performance issues or make it difficult to read and manage the content.
To resolve this error, you may need to either reduce the amount of data you are trying to paste or find an alternative method for entering or transferring the information.
To learn more about data, visit: https://brainly.com/question/29621691
#SPJ1
How are codecs related to audio file formats?
Choose all that apply.
(A)Codecs convert audio files from one file
format into another.
(B)Codecs encode audio files as a particular
audio file format.
(C)Codecs compress and decompress audio
files.
(D)Codecs are transducers that play various
audio file formats.
SELECT ALL THAT APPLY!
Answers
Answer:
The correct options are (B) and (C)
Explanation:
Solution
Codecs are programs which are used to encode or decode the data streams or signals and audio.
The codecs related to audio file formats is shown below:
(B) Codecs encode audio files as a particular audio file format .
(C) Codecs compress and decompress audio files.
each interior angle of a regular polygon is 150°.how many sides has the polygon
Answers
Answer:
12 sides
Explanation:
{(n-2)x180}÷n
150=\(\frac{(n-2)*180}{n}\)
150n=(n-2) x 180
150n= 180n-360
150n-180n=- 360
-30n= -360
n= 12
Sides of polygon is 12
Mainframe computers are multi-programming, high-performance computers, and multi-user, which means it can handle the workload of more than 100 users at a time on the computer.
a. True
b. False
Answers
Answer:
a. True
Explanation:
A computer can be defined as an electronic device that is capable of receiving of data in its raw form as input and processes these data into information that could be used by an end user. Computers can be classified on the basis of their size and capacity as follows;
I. Supercomputers.
II. Mainframe computers.
III. Mini computers.
IV. Micro computers.
Mainframe computers were developed and introduced in the early 1950s.
Mainframe computers are specifically designed to be used for performing multi-programming because they are high-performance computers with the ability to handle multiple users. As a result, it simply means that mainframe computers can be used to effectively and efficiently perform the work of over one hundred (100) users at a time on the computer. Some examples of mainframe computers include the following; IBM Es000 series, CDC 6600 and ICL39 Series.
Furthermore, mainframe computers are mostly or commonly used by large companies, business firms or governmental institutions for performing various complex tasks such as census, financial transactions, e-commerce, data sequencing, enterprise resource planning, etc.
Answer:
a. True
Explanation:
A mainframe computer, informally called a mainframe or big iron, is a computer used primarily by large organizations for critical applications, bulk data processing (such as the census and industry and consumer statistics, enterprise resource planning, and large-scale transaction processing).
#include <stdio.h>
void foo(int n, int sum)
{
int k = 0, j = 0;
if (n == 0) return;
k= n % 10;
j = n/10;
k = sum *k;
sum = sum *k + 1;
foo (j, sum);
printf ("%d", k%10);
}
int main()
{
int a = 5179, sum = 2;
foo (j, sum);
printf("%d",k%10);
}
int main()
{
int a =5179,sum=2;
foo(a,sum);
printf("%d",sum);
getchar();
}
Answers
Name three situations when a copy constructor executes.
Answers
Answer:
1. When an object of the class is passed (to a function) by value as an argument.
2. When an object is constructed based on another object of the same class.
3. When compiler generates a temporary object.
Explanation: