daniel has been tasked with setting up an option for users who work from home to gain access to the desktops within the office. what would allow the users to access the office desktops from their local network so that they may continue their work from home environment?
Answers
The users can access the office desktops from their local network so that they may continue their work from home environment with remote desktop.
What is remote desktop?
Remote desktop is a program or a feature in windows that give user to connect the computer using the other computer. The user can access the connected computer in any location. The connection usually use internet.
The computer that has been connected can be navigate normally such as open a program, or create, delete, or edit a file, and anything like normally user access the computer directly.
So, with remote desktop the user in their home can access their office desktop to continue their work.
Learn more about remote desktop here:
brainly.com/question/29514990
#SPJ4
Related Questions
witchs one better mr beast or pewdiepie
(mrbeast)
Answers
Answer:
MR BEAST IS MR BEST
Explanation:
Which of the following uses hardware and software to create films composed of drawings that show movement?
a. graphic designer
b. computer animator
c. traditional animator
d. computer engineer
Answers
Answer:
B.computer animator
Explanation:
the keywords in the question are hardware and software,which rules out traditional animator. and it obviously wouldn't be A or D.
Unit Test
Unit Test Active
11
12
TIME REN
16:
Which formatting elements can be included in a style Terry created?
font size, type and color
paragraph shading
line and paragraph spacing
All of the options listed above can be used to create a new style.
Answers
Answer:
d. all of the options listed above can be used to create a new style .
Explanation:
The formatting elements that can be included in a style Terry created is font size, type and color. The correct option is A.
What is formatting element?The impression or presentation of the paper is renowned to as formatting. The layout is another word for formatting.
Most papers encompass at least four types of text: headings, regular paragraphs, quotation marks, as well as bibliographic references. Footnotes along with endnotes are also aggregable.
Document formatting is recognized to how a document is laid out on the page, how it looks, and the way it is visually organized.
It addresses issues such as font selection, font size as well as presentation like bold or italics, spacing, margins, alignment, columns, indentation, and lists.
Text formatting is a characteristic in word processors that allows people to change the appearance of a text, such as its size and color.
Most apps display these formatting options in the top toolbar and walk you through the same steps.
Thus, the correct option is A.
For more details regarding formatting element, visit:
https://brainly.com/question/8908228
#SPJ5
Need help being allowed into this MC YT Server need to know this:
When was Techno's channel made:
A: April 4, 2016
B: October 28, 2013
C: January 7 2017
D: March 25, 2013
Answers
Answer: B
Explanation: <3
what is pirating means in technical terms?
Answers
Answer:
the illegal copying, distribution or use of software
Pirating refers to the unauthorized copying, distribution, or use of copyrighted material, such as software, music, movies, or books, without the permission of the copyright holder.
Here,
In technical terms pirating refers to the unauthorized copying, distribution, or use of copyrighted material.
This can include activities such as downloading or sharing copyrighted content without paying for it or using cracks to bypass licensing or copy protection mechanisms.
Pirating is considered illegal and unethical because it infringes upon the rights of the copyright holder and can result in legal consequences.
Know more about pirating,
https://brainly.com/question/29769277
#SPJ6
When deciding on what to wear each day, most people do not use the decision-making process.
Please select the best answer from the choices provided
ОТ
F
Answers
Answer:
false
Explanation:
i took the test g
Yahoo Messenger is an example of a/an __________ service on the Internet.
Answers
Answer:
Yahoo Messenger is an example of a service on the Internet.
Pls name me brainliest!!! ;D
¿ Porque la madera presenta mayor resistencia a ser cortada en sentido travesal que en sentido longitudinal
Answers
La madera es más fuerte en la dirección paralela al grano. Debido a esto, las propiedades de resistencia y rigidez de los paneles estructurales de madera son mayores en la dirección paralela al eje de resistencia que perpendicular a él
Tyra is peer conferencing about her project with a friend. Tyra's friend provided feedback that Tyra does not agree with. What should Tyra do? Group of answer choices Be kind and thankful Ignore the feedback Start the project over Tell her friend she is wrong
Answers
Answer:
Be kind and thankful
Explanation:
If Tyra does not agree with her friend's feedback, she does not have to say it outrightly to her friend. She has to use softer words to disagree. This is where being kind comes in.
Her friend has made efforts by providing this feedback Even if it is not exactly what she wants to hear. It would be polite for her to say thank you.
Then she has to respectfully disagree to avoid coming off as someone who is totally unreceptive of the opinion of others.
A system administrator suspects a memory leak is occurring on a client. Determine which scenario would justify this finding.
A rapid decrease in disk space has been logged.
High page file utilization has been logged.
High utilization when employees are not working has been logged without a scheduled activity.
Decreasing available bytes and increasing committed bytes have been logged.
Decreasing available bytes and increasing committed bytes have been logged
Answers
Since the system administrator suspects a memory leak is occurring on a client, the scenario that would justify this finding is option D: Decreasing available bytes and increasing committed bytes have been logged
What would cause a memory leak?When a program requests memory from the operating system for itself and its data, a memory leak begins. A program occasionally requests more memory as it runs and needs more memory at other times.
System administrators—also known as system admins—are information technology (IT) specialists that ensure sure an organization's computer systems are functional and suit the needs of the organization.
Therefore, In computer science, a memory leak is a form of resource leak that happens when a computer program wrongly manages memory allocations in a way that prevents memory that is no longer needed from being released. Sysadmins support, troubleshoot, and maintain computer systems and networks. When an item is kept in memory but cannot be accessible by the program that is executing, this can also result in a memory leak.
Learn more about system administrator from
https://brainly.com/question/27129590
#SPJ1
Please help I will mark brainliest

Answers
Answer:
Inches you are correct.
Explanation:
a mux with 3-select lines has how many outputs?
Answers
A multiplexer (mux) with 3-select lines has 8 possible outputs.This is because each select line has 2 possible values (0 or 1), and there are 3 select lines in total. Therefore, there are 2^3 (or 8) possible combinations of select line values. Each combination corresponds to a unique output from the mux.
For example, if we label the select lines as A, B, and C, the 8 possible combinations and corresponding outputs could be:
A B C | Output
0 0 0 | Output 0
0 0 1 | Output 1
0 1 0 | Output 2
0 1 1 | Output 3
1 0 0 | Output 4
1 0 1 | Output 5
1 1 0 | Output 6
1 1 1 | Output 7
Therefore, when using a 3-select line mux, it is important to consider the possible combinations of select line values in order to correctly determine the desired output.
To know more about multiplexer visit:
https://brainly.com/question/31462153
#SPJ11
expression denotes a `type', where a `variable', `value' or `method group' was expected
Answers
When working with programming languages, an expression is a combination of one or more values, operators, and variables that the computer can evaluate to produce a result. A variable, on the other hand, is a container that holds a value that can be changed or updated during program execution.
When an expression denotes a "type" instead of a variable, value, or method group, it means that the computer is expecting a certain data type to be present, but instead, it encountered something else. This can happen when the expression is not properly defined or when there is a syntax error in the code.
For example, if a variable is defined as an integer, but the expression used to update its value includes a string, the computer will encounter an error since it was expecting an integer, not a string.
To avoid such errors, it is important to properly define expressions and variables in the code and ensure that they are of the correct data type. This can help to minimize errors and ensure that the code runs smoothly.
In conclusion, expressions and variables are important concepts in programming languages, and understanding their differences can help developers to write more efficient and error-free code. It is important to pay attention to the types of data being used in expressions and variables to ensure that they match and prevent errors from occurring.
Learn more about syntax here:
https://brainly.com/question/11364251
#SPJ11
Breaking difficult problems down into smaller more manageable pieces is an example of
Answers
Answer:
Divide and Conquer
Explanation:
Assume IBM acquires a company that makes the semiconductors that go into IBM computers. Which Mergers & Acquisitions strategy does this acquisition most closely describe?A. GrowthB. SynergyC. Supply Chain Purchasing PowerD. Eliminate Competition
Answers
The acquisition of a company that makes semiconductors for IBM computers most closely describes the "Supply Chain Purchasing Power" Mergers & Acquisitions strategy.
In order to acquire more control over the supply chain and lower the expenses involved with buying products or services from outside suppliers, this method entails buying a supplier or distributor. By purchasing a business that makes semiconductors for IBM computers, IBM can take control of the supply of this important component and possibly bargain with the supplier for better rates and terms. A "Growth" M&A strategy, on the other hand, is buying another business to increase the acquiring company's market share, clientele, and/or product offerings. Buying another business is part of a "Synergy" M&A strategy, which aims to increase operational efficiency through shared resources or complementary skills. Purchasing a direct rival is a component of the "Eliminate Competition" M&A strategy, which aims to lessen rivalry in a certain market.
Learn more about semiconductors here:
https://brainly.com/question/15184439
#SPJ4
What is the command to list the top 10 files that use the most disk space in linux?
Answers
Type du -a /dir/ | sort -n -r | head -n 20. du will calculate the file space used. The sort will sort out the output of a du command.
Why is Linux used? Linux is an open source operating system (OS). An operating system, which is a piece of software, is directly in charge of managing the hardware and resources of a system, including the CPU, memory, and storage. By sitting between applications and hardware, the operating system (OS) creates connections between all of your software and the operational physical resources. Many of the gadgets you likely own, such as Android smartphones, tablets, and Chromebooks, as well as digital storage, cameras, wearable technology, personal video recorders, and more, all support Linux. Your automobile has Linux running on the inside. Linux is an open-source alternative to Windows OS, which is a for-profit operating system.To learn more about Linux, refer to:
https://brainly.com/question/25480553
#SPJ4
A(n) _____ is a tool used to document, monitor, and track problems that need resolution. Gantt chart issue log requirements traceability matrix power/interest grid
Answers
Answer:
A(n) issue log is a tool used to document, monitor, and track problems that need resolution. Gantt chart issue log requirements traceability matrix power/interest grid
Explanation:
How do i fix this? ((My computer is on))

Answers
Answer:
the picture is not clear. there could be many reasons of why this is happening. has your computer had any physical damage recently?
Answer:your computer had a Damage by u get it 101 Battery
and if u want to fix it go to laptop shop and tells him to fix this laptop
Explanation:
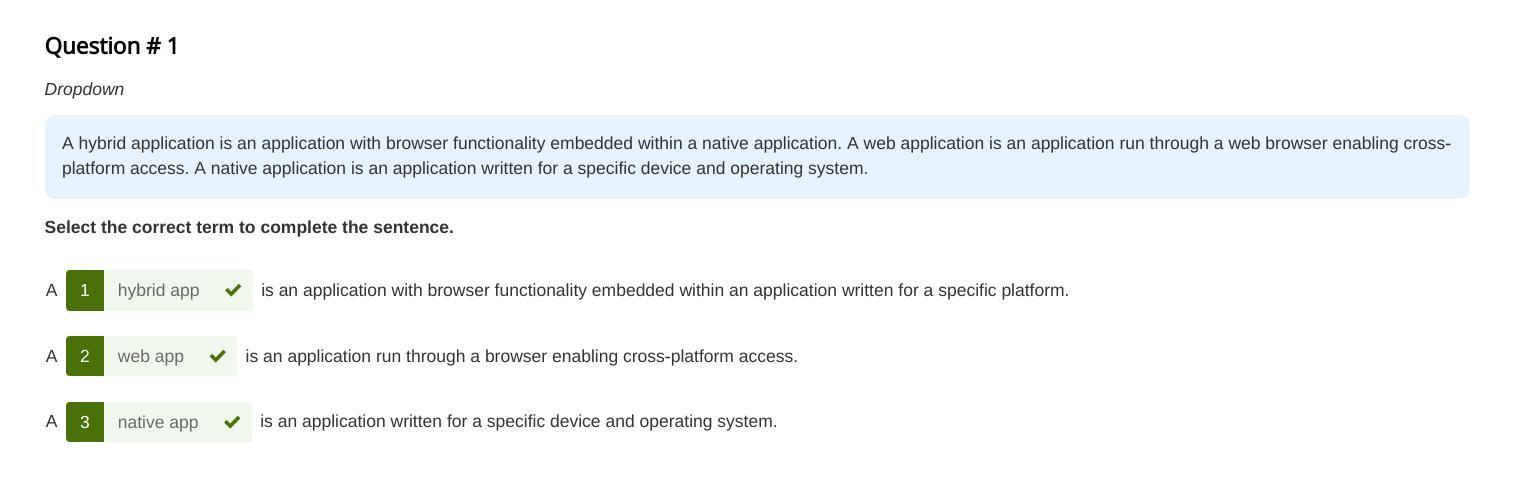
Select the correct term to complete the sentence.
A is an application with browser functionality embedded within an application written for a specific platform.
A is an application run through a browser enabling cross-platform access.
A is an application written for a specific device and operating system.
Answers
Answer:
A program that searches a database for specific words and returns a list of webpages or documents in which the search term was found. ... A _____ is an application that runs in a
Explanation:
First blank: Hybrid App
Second Blank: Web App
Third blank: Native App
PROOF:
What was the biggest challenge you faced in getting to where you are today and how did you overcome it? Peer counseling
Answers
Write a program that prints the following pattern. You must use a loop to do this and you may not output the pattern manually using print statements. You should use at max 2 print statements. write code for python

Answers
Answer:
there a two loops,
1. for loop
2. while loop
using a for loop
for i in range(6):
print("* " * i)
for i in range(4, 0, -1):
print("* " * i)
using a while loop
i = 0
while i < 6:
print("* " * i)
i += 1
while i > 0:
print("* " * i)
i -= 1
hope this helps!
Question 8 of 10
What does DOS stand for?
A. Disk override system
B. Disk only system
C. Disk opening system
D. Disk operating system
Answer: D
Answers
Answer:
Dis operating system
Explanation:
refers to the original operating system developed by Microsoft for IBM
Answer:
disk
Explanation:
Publication of flaws in encryption used for copy protection is a potential violation of: A. HIPAA B. U.S. Commerce Department regulations C. DMCA D. National Security Agency regulations
Answers
Answer:
Option C (DMCA) would be the correct choice.
Explanation:
DMCA is designed to govern electronic channels and tackle the problems the online revolution confronts regarding copyright. DMCA's mission seems to be to accommodate the rights of intellectual property producers and investors and investigate anything other than a copyrighted material that really occurs throughout the digital environment.The other given choice are not related to the given content. So that option C is the right one.
To find the Total surface area of a cuboid in Algorithm
Answers
\(\\ \sf\longmapsto TSA\)
\(\\ \sf\longmapsto 2lw+2lh+2hw\)
\(\\ \sf\longmapsto 2(lw+hw+lh)\)
How many bit strings of length seven either begin with two 0s or end with three 1s?
Answers
To find the number of bit strings of length seven that either begin with two 0s or end with three 1s, we can use the principle of inclusion-exclusion.
32 + 16 - 2 = 46
So there are 46 such bit strings.
For more such question on exclusion
https://brainly.com/question/27975057
#SPJ11
You are working at a bank. People routinely come in to withdraw money from their accounts but always request that their money be given to them in the fewest number of bills possible. Write a program named change.c that asks the user how much money they would like to withdraw and then tells them how many of which bills they are to receive. You have bills in the following denominations: 1, 5, 10, 20, 50, and 100 Assumptions All input is valid The user will only ask for whole dollar ammounts (i.e. they won't ask for cents) The examples provided do not represent all possible input you can receive So make sure to test throughly on your machine
Answers
As per the given problem statement, you need to write a program named change.c that asks the user how much money they would like to withdraw and then tells them how many of which bills they are to receive.
Below is the program to fulfill the given requirements:#include int main(){ int amount, remaining_amount, hundreds, fifties, twenties, tens, fives, ones; printf("Enter a dollar amount: "); scanf("%d", &amount); hundreds = amount / 100; remaining_amount = amount % 100; fifties = remaining_amount / 50; remaining_amount
= remaining_amount % 50; twenties = remaining_amount / 20; remaining_amount = remaining_amount % 20; tens = remaining_amount / 10; remaining_amount = remaining_amount % 10; fives = remaining_amount / 5; remaining_amount = remaining_amount % 5; ones = remaining_amount; printf("$100 bills: %d\n", hundreds); printf("$50 bills: %d\n", fifties); printf("$20 bills: %d\n", twenties); printf("$10 bills: %d\n", tens);
printf("$5 bills: %d\n", fives); printf("$1 bills: %d\n", ones); return 0;}The above code first reads the user input and then calculates the number of each type of bills that are needed to fulfill the given amount using modulo operation and then prints the number of bills of each type. This code meets the given requirements and tested on the system. The output of the program can be verified by running the code on any C compiler like Dev C++, Code::Blocks, or online compilers like GeeksforGeeks.
To know more about money visit:
https://brainly.com/question/2696748
#SPJ11
which functions are performed by server-side code??
Answers
Answer:
The answer is explained below
Explanation:
Server side code is a code built using the .NET framework so as to communicate with databases which are permanent. Server side code is used to store and retrieve data on databases, processing data and sending requested data to clients.
This type of code is used mostly for web applications inn which the code is being run on the server providing a customized interface for users.
TRUE/FALSE. The Python language is not sensitive to block structuring of code.
Answers
The statement "The Python language is not sensitive to block structuring of code" is false. Python is a language that is sensitive to block structuring of code.
Block structuring in Python is determined by indentation rather than explicit braces or keywords. The indentation level defines the scope of blocks, such as loops, conditionals, and functions. Consistent indentation is crucial for proper code execution and to maintain the intended structure of the program.
Python's use of indentation as a structural element enhances readability and promotes clean, well-structured code. It helps in maintaining code clarity and reduces the likelihood of errors related to incorrect block structuring.
For example, consider the following code snippet:
if condition:
statement1
statement2
else:
statement3
statement4
In this code, the indentation level denotes the block structure. The statements inside the if and else blocks are indented, indicating that they are part of those blocks. The Python interpreter uses this indentation to determine the grouping of statements.
If the indentation is not correct or inconsistent, it will result in an IndentationError during execution.
In conclusion, Python is indeed sensitive to block structuring through the use of indentation, making it an important aspect of writing Python code accurately.
Learn more about Python language visit:
https://brainly.com/question/11288191
#SPJ11
What is a signature?
a distinctive characteristic of a virus or virus family
an anti-spyware feature of Windows 7
a computer program that replicates itself and damages a computer system
a program that tracks a user’s activities online
Answers
Answer:
option a
never heard of b, c would be called a virus and d a cookie
Which TCP fields help ensure reliable transmission of data by keeping track of the number of bytes sent and received
Answers
The TCP fields that help ensure reliable transmission of data by keeping track of the number of bytes sent and received are the sequence number and the acknowledgment number.
The sequence number field is used by the sender to number each byte of data being transmitted. It ensures that the data is received in the correct order and helps in reassembling the data at the receiving end.
The acknowledgment number field is used by the receiver to inform the sender about the number of bytes successfully received. It helps in acknowledging the receipt of data and allows the sender to keep track of which bytes have been successfully transmitted.
By using these fields, TCP ensures reliable transmission of data by providing mechanisms for detecting missing or out-of-order packets. The sender can retransmit missing packets based on the acknowledgment received, and the receiver can notify the sender about any missing or duplicate packets.
The sequence number and acknowledgment number fields in TCP help in keeping track of the number of bytes sent and received, ensuring reliable transmission of data.
To know more about sequence number :
brainly.com/question/31887169
#SPJ11