All of the following are examples of software, except:
Question 4 options:
Video games
Speakers
Web browsers
Photo editors
Answers
The speaker is not an example of the software. Then the correct option is B.
What is the software?Software is a collection of instructions, data, or computer programs used to run computers and carry out particular activities. Software instructs a computer on how to run, to put it another way.
It's a general phrase for programs, scripts, and apps that operate on computers, cell phones, laptops, and other intelligent watches. Hardware, or the actual components within a computer that does the job, competes with software.
All of the following are examples of software, except the speaker.
The actual parts of an electronic system, such as a computer, include the hardware, wiring, and other parts. Speaker is a hardware device. Then the correct option is B.
More about the software link is given below.
https://brainly.com/question/1022352
#SPJ6
Related Questions
a. What is this age called?
Answers
Answer:
The Information Age (also known as the Computer Age, Digital Age, or New Media Age) is a historical period that began in the mid-20th century, characterized by a rapid epochal shift from traditional industry established by the Industrial Revolution to an economy primarily based upon information technology.
OR
Age, epoch, era, period all refer to an extent of time.
Explanation:
can i have brainliest pls?
Plockton Scotland is located about as far north of the equator as Juneau, Alaska. yet cabbage trees, which are similar to palm trees, can grow there. how can these warm-weather trees survive so close to the arctic?
Answers
Cabbage trees, also known as Cordyline australis, are indeed native to warm regions such as New Zealand and Australia. However, they are also capable of adapting to colder climates, as evidenced by their ability to grow in places like Plockton, Scotland, which is located at a similar latitude as Juneau, Alaska.
What is the explanation for the above response?One reason why cabbage trees can survive in colder climates is their ability to withstand frost and cold temperatures. They have evolved to develop a range of adaptations, such as thicker trunks and leaves, and the ability to grow at lower temperatures. In addition, cabbage trees are able to go dormant during winter months, which helps them conserve energy and survive the colder weather.
Another factor that may contribute to the survival of cabbage trees in colder climates is the moderating effect of the ocean. Coastal areas like Plockton tend to have milder temperatures due to the warming effect of ocean currents. This can create a microclimate that is more hospitable to warm-weather trees like cabbage trees.
Thus, cabbage trees have developed a range of adaptations that allow them to survive in colder climates, and their ability to grow in areas like Plockton, Scotland, demonstrates the resilience and adaptability of plant species.
Learn more about Cabbage trees at:
https://brainly.com/question/12057008
#SPJ1
app stores can lower distribution costs compared to packaged software alternatives. true or false
Answers
The statement "app stores can lower distribution costs compared to packaged software alternatives" is True. This is because app stores allow for digital distribution, eliminating the need for physical packaging, shipping, and inventory management.
App stores provide a centralized platform for users to discover, download, and update software applications. By leveraging app stores, software developers can reach a wide user base without the need for physical packaging, shipping, and retail distribution.
This eliminates the costs associated with manufacturing physical copies, inventory management, and logistics. Additionally, app stores handle the payment processing and provide a secure platform for transactions, reducing the administrative and financial burden on developers.
Overall, app stores offer a more efficient and cost-effective distribution channel for software compared to traditional packaged software alternatives. So the statement is True.
To learn more about software: https://brainly.com/question/28224061
#SPJ11
principles and practice of automatic process control 3rd edition pdf
Answers
Principles and Practice of Automatic Process Control 3rd Edition PDF is a textbook that provides a comprehensive understanding of automatic process control. It is designed for undergraduate students studying chemical engineering, control engineering, and related fields.
What is Automatic Process Control?
Automatic process control refers to the use of a control system to regulate a process without any human intervention. The system is programmed to adjust the process parameters automatically to maintain optimal conditions. The system receives input signals from sensors and sends output signals to actuators to make adjustments to the process variables. The principles of automatic process control are based on the mathematical modeling of the process. The models are used to develop control algorithms that can predict the behavior of the process under different conditions. The algorithms are then implemented in the control system to regulate the process.
The practice of automatic process control involves the design, implementation, and maintenance of the control system. The design phase involves the selection of sensors, actuators, and control algorithms that are appropriate for the process. The implementation phase involves the programming of the control system and the integration of the sensors and actuators. The maintenance phase involves the monitoring of the process and the control system to ensure that they are operating correctly. The Principles and Practice of Automatic Process Control 3rd Edition PDF covers the following topics: Introduction to Automatic Process Control Mathematical Modeling of Processes Dynamic Behavior of Processes Feedback Control Systems Advanced Control Strategies Digital Control Systems Multivariable Control Systems Plantwide Control Systems Applications of Automatic Control
Conclusion The textbook provides examples and case studies that demonstrate how the principles and practices of automatic process control can be applied to real-world situations. The PDF version of the textbook can be downloaded from various online sources.
Learn more on feedback control here: brainly.com/question/16230467.
#SPJ11
How do you flatten a 2D array to become a 1D array in Java?
Answers
Answer:
With Guava, you can use either
int[] all = Ints.concat(originalArray);
or
int[] all = Ints.concat(a, b, c);
Explanation:
Use GUAVA
which of the following method ensures if a running virtual machine fails? A. Virtual Machine
B. Hard Drive
C. USB
D. DVD
Answers
Correct option is A. virtual machine,it ensures failover through features like snapshots, high availability, and fault tolerance, which provide resilience and automatic recovery in case of failure.
How does a virtual machine ensure failover?A virtual machine (VM) is a software emulation of a physical computer system, which operates as an independent entity within a host machine. The VM runs its own operating system and applications, separate from the host machine.
In the event of a failure, such as a system crash or software malfunction, the virtual machine can be restarted or restored to a previous state without affecting the underlying hardware or other virtual machines.
This resilience is achieved through features like snapshots, which capture the VM's state at a specific point in time, allowing for easy rollback in case of failure.
Furthermore, virtualization technologies often include features like high availability and fault tolerance, which provide redundancy and automatic failover mechanisms to ensure continuous operation even if a VM or its host machine encounters issues.
These capabilities enhance the reliability and stability of virtual machines, making them a robust solution for ensuring the availability of running applications.Therefore,Correct option is A. virtual machine.
Learn more about virtual machine
brainly.com/question/31674424
#SPJ11
6C: Given the following AVL tree with a newly inserted node in double outline), choose the correct sequence of rotations to restore the height balance property + Inserts Single right rotation: move 2 up/right; 4 down/right B: Single left ratation move 7 up/left: 4 dawn/left Double rotation: first 6 up/right: 7 down/right then 6 up/left: 4 down/left D: Double rotation: first 7 up/left; 4 down/left then 6 upleft:4 down/left B D
Answers
Based on the given AVL tree, the correct sequence of rotations to restore the height balance property after a newly inserted node would be:
Single right rotation: Move 2 up/right; 4 down/right
Double rotation: First 7 up/left; 4 down/left then 6 up/left: 4 down/left
So the correct answer would be B and D.
For more questions like node visit the link below:
https://brainly.com/question/14448757
#SPJ11
A _______ web page's content can change based on how the user interacts with it.
Answers
Answer:
Dynamic web page shows different information at different point of time.
question 4 a design team wants to add a new, secret page on their app that only observant users will be able to find. they only want to change one element of the current design. which visual design strategy would best allow them to adjust just one element of the current design and draw visual attention to the secret page?
Answers
A design team wanting to add a secret page in their app while only changing one element can effectively use the visual design strategy known as "contrast" to draw attention to the secret page.
What's contrast?Contrast can be achieved by adjusting the color, size, or shape of the element, making it stand out from the rest of the design.
By subtly modifying a single element in a way that it attracts observant users, the team can successfully create curiosity and guide users towards discovering the secret page.
This strategy ensures minimal disruption to the overall design while still accomplishing the goal of drawing attention to the hidden feature.
Learn more about design team at
https://brainly.com/question/31147028
#SPJ11
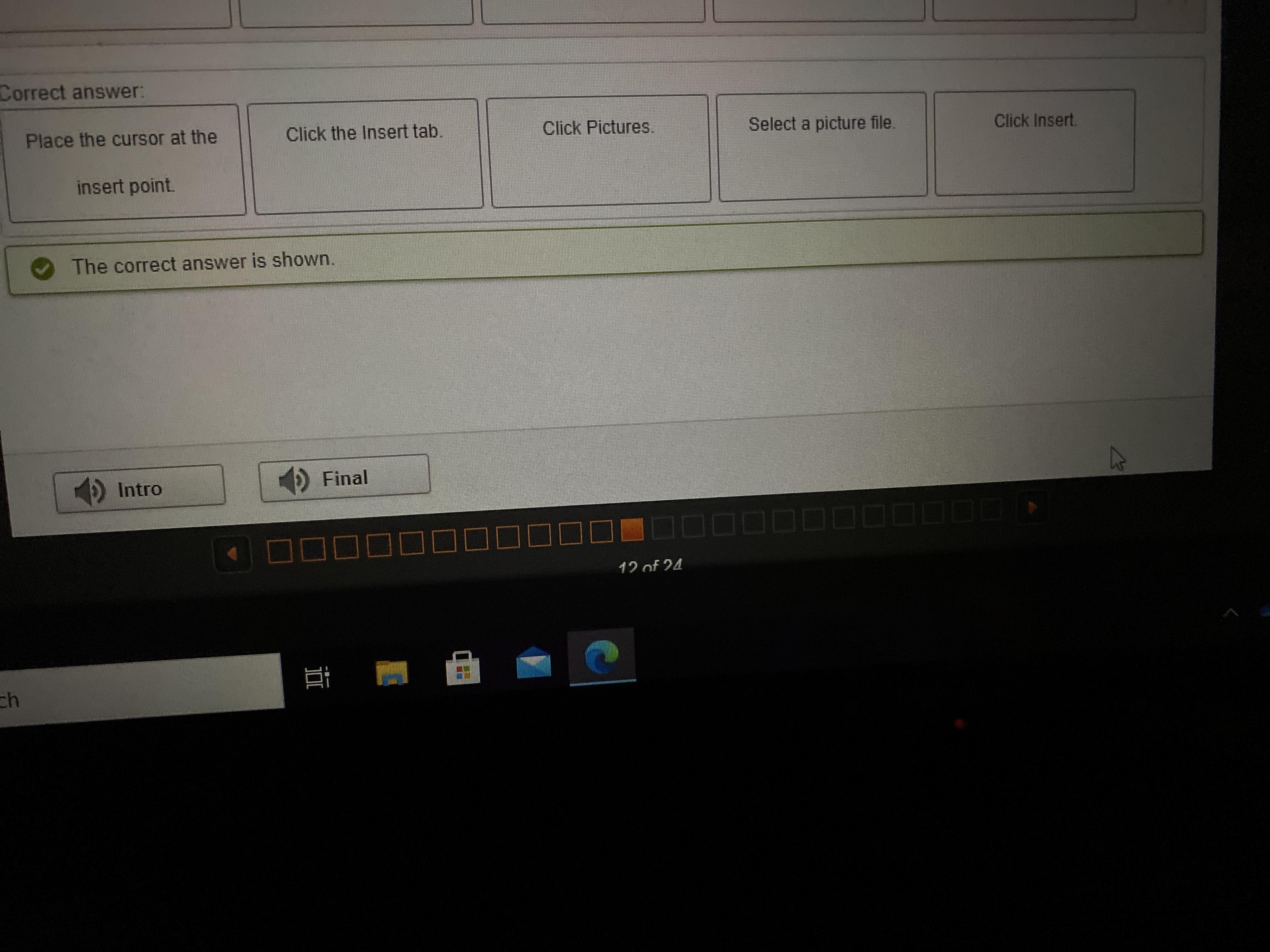
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
Mark just finished reading the cay and must write a book report comparing events in the book to events in his life. based on each application strengths and weaknesses, which one would be the best to choose for this task?
A. word
B. power point
C. excel
B. office
Answers
The option that would be the best to choose for this task of book report is word.
What is book report?Book reports is known to be a report of what occurs in a work or book. it can be a summary of every event that took place.
The use of Microsoft or other word application is the best as on can be able to outline the one's account of the plot, characters, thesis and other things one has read or seen.
Learn more about book report from
https://brainly.com/question/1909141
How many electrons are there in 4.25 coulombs of charge?
Answers
Answer:
10 *18
Explanation:
The formula for quantisation of charge is given as q=ne.
where, q is the amount of charge in Coulumbs, n is the number of charges and e is the charge on the electron.
In this case, q=4/25 C
So, e = 1.6×10
−19
C.
Peter took a selfie in his room. He was a wearing a light blue shirt. But he failed to realize that that shirt would clash in color with the light blue walls in his room. He wants to edit this photo using editing software. Which tool can Peter use to darken the background in his photo?
Answers
Answer:
A wand tool is to do that in an editing software.
Answer: Peter should use the burn tool
Create a C++ program that will accept five (5) numbers using the cin function and display the numbers on different lines with a comma after each number.
Answers
Answer:
code:
#include<iostream>
using namespace std;
int main()
{
//declare an array of size 5
int array[5];
cout<<"Enter the numbers"<<endl;
//applying the for loop
for(int i=0;i<5;i++)
{
//taking the input from user
cin>>array[i];
}
cout<<"The Entered numbers are : "<<endl;
for(int i=0;i<5;i++)
{
//displaying the output
cout<<array[i]<<", "<<endl;
}
return 0;
}
Explanation:
First of all you will declare an array of size 5
then you are going to apply the for loop logic where you will take input from the user
again you will apply the for loop to print the entered numbers on screen
#include <iostream>
int store[5];
int main() {
for(int i=0;i<5;i++) {
std::cin>>store[i];
}
for(auto& p:store) {
std::cout << p << ",\n";
}
return 0;
}
Select the 3 TRUE statements about storing digital images.
Group of answer choices
When storing the original file, use highest resolution possible if you are not sure how the images might be used.
Back up important documents on an external storage device.
Don't include descriptive information, version or size, and intended use information, as this increases file size.
Keep the original high resolution file in a separate place and make a copy to edit and process.
To get a higher resolution image of a low resolution picture, simply resave it at a higher resolution.
Answers
Answer:
When storing the original file, use highest resolution possible if you are not sure how the images might be used.Back up important documents on an external storage device.Keep the original high resolution file in a separate place and make a copy to edit and process.Explanation:
The other two are incorrect. -->
Descriptive info hardly affects file size. In fact this should be a requirement to identify the image.
You cannot go from a lower resolution image to a higher resolution image, only the other way around
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
Write the function my_readline ) according to the following specification Requires: * If *bufp is not NULL, then *bufp must point to a buffer that wa:s * previously allocated by malloc) or realloc() and *lenp must be less * than or equal to the size of that buffer. k Effects: *Attempts to read a '\n'-terminated line from the given file descriptor, *fd. Copies this line, including the '\n', into the buffer referenced * by *bufp. If *bufp is NULL or the current size of the buffer, as given * by *lenp, is too small to store the entire line, then realloc) is * performed on the buffer to enlarge it. The enlarged buffer is returned *by reference uslng bufp. Similarly, the number of characters stored in * the buffer is returned by reference using lenp *Returns 0 upon success. Returns EOF if read() returns an end-of-file * indication before a ,\n' is encountered. Nonetheless, the buffer
* referenced by *bufp will contain all of the characters successfully * read before that end-of-file indication, and *lenp will equal the number of characters in that buffer. Returns the value of errno if * either realloc) returns NULL or read() returns -1. In either case, as *with read() returning an end-of-file indication, the buffer referenced * by *bufp will contain all of the characters successfully read before *the error occurred, and *lenp will equal the number of characters in that buffer. Returns EINVAL if either bufp or lenp is NULL Notes: * In contrast to rio_readlineb), the returned line should not be NUI terminated * The only functions that your implementation may call are read (2) and * realloc(3) int my_readline(int fd, void **bufp, size_t *lenp) FILL THIS IN. */
Answers
The my_readline function takes three parameters: fd (file descriptor), bufp (pointer to a buffer), and lenp (pointer to the length of the buffer). The function attempts to read a line terminated by '\n' from the given file descriptor.
The my_readline function reads a line from a file descriptor, fd, into a dynamically allocated buffer referenced by *bufp. If the buffer is too small to store the entire line, it is enlarged using realloc. The function returns the number of characters stored in the buffer and 0 for success. It returns EOF if an end-of-file is encountered before a newline character. If realloc returns NULL or read returns -1, the function returns the value of errno. If bufp or lenp is NULL, it returns EINVAL.
First, it checks if the buffer referenced by *bufp is large enough to store the line. Next, it uses the read() function to read characters from the file descriptor into the buffer. If the read() function encounters an end-of-file before a '\n' character, it returns EOF. If either realloc returns NULL or read returns -1, indicating an error, the function returns the value of errno. If bufp or lenp is NULL, the function returns EINVAL to indicate an invalid argument. Finally, the function returns the number of characters stored in the buffer upon successful execution.
Learn more about my_readline here;
https://brainly.com/question/32067398
#SPJ11
how many bits and bytes are occupied by six long variables
Answers
Answer:
24 bytes = 192 bits
Explanation:
A long is typically 4 bytes or 4*8 = 32 bits
However, on some 64 bit systems, a long is defined as 64 bits so the answer is not universal.
What is meant by Paradigm programming?
Answers
Answer:
a way to classify programming languages based on their features
Choose the sentences that describe techniques of formatting text.
Olivia was sending out Thanksgiving Invitations to her relatives. She thought it would be best to make a card as an invitation. She gathered her
family and asked them to pose in front of the fireplace. She set her new DSLR camera on a timer with the automatic multiple shooting mode
and rushed by her family's side. The camera took multiple shots of the family.
She opened the best photo in her photo editing software. She changed the tone of the image to sepia to give the image a traditional feel. She
brightened the colors in the background. While editing she felt that the window on the side of the fireplace was disturbing the symmetry of the
photo. She cropped the window out of the image.
She opened her type tool and wrote in 'Happy Thanksgiving at the bottom of the image. She smoothed the edges of the text and changed its
color. She then placed the text on a rug and tilted it to create an effect that showed as if the text was written on the rug
She gave the photo some finishing touches and sent the invitations out through email to all her relatives.
Answers
I'm sorry if this answer has come to late.
Answer:
She opened her type tool and wrote in 'Happy Thanksgiving at the bottom of the image. She smoothed the edges of the text and changed its color. She then placed the text on a rug and tilted it to create an effect that showed as if the text was written on the rug.
Hope this helps!
She opened her type tool and typed 'Happy Thanksgiving.' She smoothed the text's edges and changed its color. She then positioned the text on a rug and tilted it to create the illusion that the text was written on the rug.
What is formatting text?Text formatting is a feature in word processors that allows you to change the appearance of a text, such as its size and color.
Most apps display these formatting options in the top toolbar and walk you through the same steps.
In computer science, formatted text, styled text, or rich text, as opposed to plain text, is digital text that contains styling information in addition to the minimum of semantic elements: colors, styles, sizes, and special HTML features.
The goal of formatting is to change the font style, size, color, and overall appearance of the text.
'Happy Thanksgiving,' she typed into her type tool. She rounded the edges of the text and changed its color. She then placed text on a rug and tilted it to give the impression that the text was written on the rug.
Thus, this shows the techniques of formatting text.
For more details regarding formatting, visit:
https://brainly.com/question/21934838
#SPJ5
Which of the following is NOT one of the purposes of establishing a security policy for an organization? Question 1 options: Providing legal support for any intrusion or unauthorized use of information. Preventing and monitoring loss of information. Absolving users of individual liability on the network systems. Protecting the value of vital corporate information.
Answers
Answer:
Initially, national security was defined as the government's ability to protect its citizens from military attacks. Today, this definition also includes other non-military areas such as defense against crime and terrorism, economic security, environmental security, food security, energy security and cyber security.
Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
How is a procedure different than a function?
Answers
Answer: A procedure is used to perform certain task in order.
Does anybody play nba2k21 On ps4
Answers
Answer:
yeah but I gotta re-download it
Answer:
Nope but can i get it on switch
Explanation:
a router on the border of your network detects a packet with a source address from an internal client, but the packet was received on the internet-facing interface. which attack form is this an example of?
Answers
Attack form is this an example of spoofing.
What is Spoofing?A common spoofing scenario occurs when an email is sent from a spoofed sender address and the recipient is asked to provide confidential information. Recipients are typically asked to click a link to log into their account and update their personal and financial information. Spoofing is a cybercrime that occurs when someone pretends to be a trusted contact or brand to gain access to sensitive personal information while impersonating a trusted person. Spoofing attacks copy identity, the appearance of a name brand, or the address of a trusted website.
Learn more about spoofing: https://brainly.com/question/23021587
#SPJ4
The range of positive integers possible in an 8-bit two's complement system is: A) 1 to 256. B) 1 to 127. C) 1 to 255. D) 1 to 128.
Answers
Answer:
The correct answer is B) 1 to 127.
Explanation:
In an 8-bit two's complement system, the range of positive integers possible is from 0 to (2^8)-1 = 255. However, since the two's complement system allocates the most significant bit (MSB) to represent the sign of the number, the range of positive integers would be halved. Therefore, the range of positive integers in an 8-bit two's complement system is from 1 to 127.
you must use a postman collection to create a custom connector. which two components are required for any requests added to the collection? each correct answer presents a part of the solution.
Answers
When using a postman collection to create a custom connector, the two components that are required for any requests added to the collection are:
HTTP method (Option A); andAuthorization header (Option C)What is a postman collection?Postman Collections are a collection of previously stored requests. Every Postman request you send is saved in the sidebar's History tab.
Reusing requests through the history section is handy on a small scale. Finding a certain request in your Postman history might become time-consuming as your use rises.
You can organize your workspace by grouping Postman requests and examples into collections, interact with peers, develop API documentation and API tests, and automate request runs. To view a list of collections in a workspace, select Collections from the sidebar.
Learn more about Connectors:
https://brainly.com/question/13398645
#SPJ1
Full Question:
You must use a Postman collection to create a custom connector.
Which two components are required for any requests added to the collection? Each correct answer presents a part of the solution.
Select all answers that apply.
A. HTTP method
B. Request URL
C. Authorization header
D. Content type
1) Using the topics below, in 150 words or more for each item, describes how Threat Modeling fits into each:
a) System development life cycle.
b) Software development life cycle (address software development and not system items).
c) Security maturity.
d) Security plan and policies.
Answers
Threat modeling can be described as the method of analyzing a software system or application in order to identify and address any potential security threats and vulnerabilities. This analysis takes into account the components and structure of the system, as well as the external environment in which it will operate. Threat modeling is a crucial aspect of secure software development and can be integrated into various stages of the system development life cycle (SDLC), software development life cycle (SDLC), security maturity, and security plan and policies.
a) System development life cycle: Threat modeling can be integrated into the system development life cycle in several stages, including the design and implementation phase. At this stage, the threat model will help developers identify potential threats and vulnerabilities and ensure that they are addressed early on in the development process. This will help to prevent security issues from being introduced into the system later on and ultimately save time and resources in the long run.
b) Software development life cycle: Threat modeling can be integrated into the software development life cycle by addressing software development and not system items. At the coding stage, developers can use the threat model to help identify potential security vulnerabilities and ensure that they are addressed before the code is deployed. This can help prevent common security issues like SQL injection, cross-site scripting, and other types of attacks.
c) Security maturity: Threat modeling is a critical aspect of security maturity. By using threat modeling, organizations can develop a more comprehensive security strategy that takes into account potential threats and vulnerabilities and addresses them before they can be exploited by attackers. A mature security posture includes a proactive approach to identifying and addressing potential security risks and the use of tools like threat modeling can help organizations achieve this.
d) Security plan and policies: Threat modeling can be used to inform security plans and policies by identifying potential threats and vulnerabilities that need to be addressed. This information can then be used to develop policies and procedures that will help to mitigate these risks and ensure that the system is secure. Threat modeling can also be used to ensure that policies and procedures are effective by identifying potential gaps or areas for improvement. Overall, threat modeling is an essential component of developing effective security plans and policies.
Learn more about System development life cycle here:
https://brainly.com/question/19977141
#SPJ11
which of the following tools can be used to block unauthorized access while allowing authorized communications on a device or network? a. antivirus software b. netstat c. digital certificate d. firewall
Answers
The tools that can be used to block unauthorized access while allowing authorized communications on a device or network is option d. firewall
What is the tools about?Antivirus is known to be a kind of program utilized to anticipate, filter, identify and erase infections from a computer. Once installed, most antivirus software runs naturally within the foundation to supply real-time assurance against infection attacks.
Therefore, an example of attack is brute drive attack that uses trial-and-error to figure login information, encryption keys, or discover a covered up web page. Programmers work through all conceivable combinations trusting to figure rightly.
Learn more about tools from
https://brainly.com/question/25860017
#SPJ1
Pls help me this quation give me the answer Do you think that dealing with big data demands high ethical regulations, accountability, and responsibility of the person as well as the company? Why?
Answers
Answer:
yes, in case of big data demand it's duty of person as well as company to follow ethical principal and adhere the moral standard for keeping the information of the big data company confidential.
Explanation:
may it's help you