A programmer wants to communicate with a software application on a controller. which of the following would the programmer use?
Answers
A programmer wishes to interact with a controller's software program. Which option would the coder choose. The so-called northbound interface is how the application layer interacts with the control layer.
which of the following would the programmer use?
The Infrastructure layer is another name for this layer. The so-called northbound interface is how this layer interacts with the Control layer. Open These APIs, which are often referred to as public APIs, can be accessed by anyone since they are made available to the public. Layer of transport. responsible for offering communication and packet services to the application layer.
TCP and other protocols are included at this layer. Simple Mail Transfer Protocol, or SMTP, is in charge of email message transmission. network. This controller, which is housed on a server, controls network-wide policies and traffic patterns.
To learn more about programmer use from given link
brainly.com/question/11345571
#SPJ4
Related Questions
A Queue can be used to implement a line in a store. If George, Judy, John, and Paula get in line and the cashier checks out two customers. Who is the person in line that would be checked out next? (This is a so-called "peek" operation on queues). Group of answer choices Return John, and remove him from the line. Return John Return John and Paula
Answers
Answer:
Explanation:
The following code is written in Java. It creates a Queue/Linked List that holds the names of each of the individuals in the question. Then it returns John and removes him and finally returns Paula and removes her.
package sample;
import java.util.*;
class GFG {
public static void main(String args[])
{
Queue<String> pq = new LinkedList<>();
pq.add("John");
pq.add("Paula");
pq.add("George");
pq.add("Judy");
System.out.println(pq.peek());
pq.remove("John");
System.out.println(pq.peek());
pq.remove("Paula");
}
}
Briefly explain the risks we face in augmented reality,iot and AI
Answers
Augmented Reality (AR), Internet of Things (IoT), and Artificial Intelligence (AI) are all cutting-edge technologies that offer many benefits, but they also come with certain risks. Some of the main risks associated with these technologies include:
Augmented Reality: One of the main risks associated with AR is that it can distract users from their real-world surroundings, potentially leading to accidents or injuries. Additionally, AR can also be used to spread misinformation or to manipulate people's perceptions of the world.
Internet of Things: The IoT is vulnerable to cyber attacks, as the interconnected nature of these devices makes them an attractive target for hackers. A security breach of an IoT device can lead to the loss of sensitive information or to unauthorized control of the device.
Artificial Intelligence: AI systems can be trained on biased data, which can lead to biased decisions, particularly in sensitive areas such as criminal justice or hiring. Additionally, AI can be used to automate certain tasks, which can displace jobs, and its usage can be used for malicious intent like spreading misinformation, hacking and surveillance.
It's important to keep in mind that these are not exhaustive lists, and there are other risks associated with these technologies. It is crucial to be aware of these risks and to take the appropriate measures to mitigate them.
nts/viewer/classes/289ef1a5d7c341c284010 Select the compound inequality shown on the graph. 5 4 3 2 1 0 1 2 를 4
Answers
What operating system are you using? On most computers, you can answer this question by right-clicking on the "My Computer" icon on the desktop and selecting Properties from the menu. The line under System: tells you the name of your operating system. Enter the name of your OS in the space provided
Answers
Answer
Chrome OS
Explanation:
i cant tell whether this is a question you c&p'd or if your genuinely asking people what os they're running
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
Describe the impact of a company’s culture on its success in a customer-focused business environment. Discuss why each is important.
Answers
The influence of a corporation's culture cannot be underestimated when it comes to achieving success in a customer-centric commercial landscape.
The values, beliefs, norms, and behaviors that constitute a company's culture have a major impact on how its employees engage with customers and prioritize their requirements.
Having a customer-centric mindset means cultivating a culture that places a strong emphasis on satisfying and prioritizing customers' needs and desires, resulting in employees who are aware of the critical role customer satisfaction plays in ensuring success.
Learn more about company’s culture from
https://brainly.com/question/16049983
#SPJ1
Zeke is working on a project for his economics class. He needs to create a visual that compares the prices of coffee at several local coffee shops. Which of the charts below would be most appropriate for this task?
Line graph
Column chart
Pie chart
Scatter chart
Answers
Opting for a column chart is the best way to compare prices of coffee at various local coffee shops.
Why is a column chart the best option?By representing data in vertical columns, this type of chart corresponds with each column's height showing the value depicted; facilitating an efficient comparison between different categories.
In our case, diverse branches of local coffee shops serve as various categories and their coffee prices serve as values. Depicting trends over time suggested usage of a line graph. Pie charts exhibit percentages or proportions ideally whereas scatter charts demonstrate the relationship between two variables.
Read more about column chart here:
https://brainly.com/question/29904972
#SPJ1
What is the default location for saving a template in Word
D Custom Templates
D Created Templates
D Created Office Templates
D Custom Office Templates
Answers
The default location for saving a template in Word is Custom Office Templates. The correct option is D.
What is a template?When used in the context of word processing software, the term template refers to a sample document that already has some details in place.
These can be done by hand or through an automated iterative process, such as with a software assistant.
Templates are pre-formatted documents that are designed to speed up the creation of common document types such as letters, fax forms, and envelopes.
The default location for new templates is a subfolder named "Custom Office Templates" in the user's documents folder.
Thus, the correct option is D.
For more details regarding template, visit:
https://brainly.com/question/13566912
#SPJ1
Answer:
the correct option is D
Explanation:
Main Difference between Excel and word application
programs
Answers
Answer:
See explanation
Explanation:
Word documents are mainly for typing papers and documents. This is useful for writing a report or making a book.
Excel is for writing spreadsheets and doing math equations within the program. This is useful for having budget calculators and math equations.
Hope this helped!
Keisha is creating an input mask and needs to ensure that the user will only enter digits into the field. Which two
characters do NOT enforce this rule?
0 0 and 9
09 and ?
O ? and L
O Land 0
Answers
Answer:
? and L
Explanation:
12. What separated Grand turismo from other racing games was its focus on ______.
a) Your audiences and females in particular
b) Fantasy graphics and visuals
c) Pure simulation and ultrarealistic features
d) All of the above
Answers
Answer:
c) Pure simulation and ultrarealistic features
Explanation:
The main difference between Grand Turismo and other racing games was its focus on Pure simulation and ultrarealistic features. The Grand Turismo series has always been a racing simulation, which was made in order to give players the most realistic racing experience possible. This included hyperrealistic graphics, force feedback, realistic car mechanics, realistic weather, and wheel traction among other features. All of this while other racing games were focusing on the thrill of street racing and modifying cars. Therefore, it managed to set itself apart.
Which of the following BEST describes an inside attacker?
An agent who uses their technical knowledge to bypass security.
An attacker with lots of resources and money at their disposal.
A good guy who tries to help a company see their vulnerabilities.
An unintentional threat actor. This is the most common threat.
Answers
The inside attacker should be a non-intentional threat actor that represents the most common threat.
The following information related to the inside attacker is:
It is introduced by the internal user that have authorization for using the system i.e. attacked.It could be intentional or an accidental.So it can be non-intentional threat.Therefore we can conclude that The inside attacker should be a non-intentional threat actor that represents the most common threat.
Learn more about the threat here: brainly.com/question/3275422
Highlight three (3) typical User Requirements and three (3) typical System
Requirements of the ATM system. Use both Natural Language and Form-Based
Specifications to illustrate the typical requirements
Answers
As part of each transaction, an user will be obligated to insert an ATM card and enter a personal identification number (PIN), both of which will be sent to the bank for validation.
What is ATM?ATMs are convenient because they allow consumers to perform quick self-service transactions such as deposits, cash withdrawals, bill payments, and account transfers.
Fees for cash withdrawals are frequently charged by the bank where the account is held, the operator of the ATM, or both.
A user will be required to insert an ATM card and enter a personal identification number (PIN) as part of each transaction, both of which will be sent to the bank for validation.
The customer's unique ID must be accepted by the ATM system. The ATM system must accept the customer's choice for a variety of banking transactions.
The ATM system must accept the customer's account type for deposits, balance inquiries, and payments on account.
Thus, these are some of the requirements for ATM.
For more details regarding ATM, visit:
https://brainly.com/question/3450346
#SPJ1
Which of the following represents an input on a smartphone?
A pressing the volume key
B an appointment displayed by your calendar
C your phone ringing
D your screensaver turning on
Answers
Answer:
Pressing the volume key.
Explanation:
The appointment is and output. It is being shown to you from the smartphone.
The volume key is an input. Your telling the smartphone to raise its volume.
The phone ringing is also an output, and so is the screensaver turning on.
Answer:
A. Pressing the Volume Key
Hope this helped (~0>0)~What is weather in mexico today
Answers
In Mexico, the dry season is between the middle of November and April, and the rainy season is from May through October.
Mexico has a distinct transition between its desert and tropical climates. The country is split in two by the Tropic of Cancer, with one region being tropical and the other being temperate.
As a result, the northern lands have colder winter temperatures than the southern parts, where temperatures are stable throughout the year.
Mexico City experiences very consistent weather all year long, with daily highs of 71 degrees Fahrenheit (22 °C) and lows of 38 °F (3 °C) in the winter. Summers are only somewhat hotter, with normal daytime highs of 76 °F (25 °C) and nighttime lows of 44 °F (7 °C).
To learn more about Mexico, follow the link:
https://brainly.com/question/10938609
#SPJ1
Write a single statement that assigns avg_sales with the average of num_sales1, num_sales2, and num_sales3. Sample outputs with: 3 4 8
Average sale: 5
Answers
Here is an example of a single statement that assigns the variable avg_sales with the average of num_sales1, num_sales2, and num_sales3 in Java:
avg_sales = (num_sales1 + num_sales2 + num_sales3) / 3.0;
This statement uses the addition operator (+) to sum the values of num_sales1, num_sales2, and num_sales3, and then divides the result by 3 using the division operator (/) to find the average. The division operator is used with a floating-point number (3.0) to ensure that the result is also a floating-point number.
For example, if num_sales1 = 3, num_sales2 = 4, num_sales3 = 8, the statement
avg_sales = (num_sales1 + num_sales2 + num_sales3) / 3.0;
will assign the value 5.0 to avg_sales.
Explain the five most important things that should be taken into consideration when designing a computer network.
Answers
Explanation:
Many computer experts (networkers) believe that you consider the following when designing a computer network:
Budget: By considering the amount available to be spent on setting up the computer network, it allows buying the best quality equipment considering the available funds.Type of network connectivity: This involves determining whether the network would only be a wireless connection or wired connection using cables, or involves both combinations.Type of security: This involves deciding the type of network security to be installed. Answering: Would it cloud systems be used? What type of firewall systems to use, etc?The type of hardware and software: This is very important in other to determine how optimal the network would be.Disaster recovery plan: For example, what type of back-up power would be required or affordable, solar power, or generator?Write a program to print a vampire number in java
Answers
Here's a program in Java to print a vampire number:
The Programpublic class VampireNumber {
public static boolean isVampire(int num) {
int len = String.valueOf(num).length();
int[] digits = new int[len];
int i;
for (i = 0; i < len; i++) {
digits[i] = num % 10;
num /= 10;
}
for (int x = 0; x < len / 2; x++) {
for (int y = 0; y < len / 2; y++) {
int fang1 = digits[x] * 10 + digits[y];
int fang2 = digits[len - x - 1] * 10 + digits[len - y - 1];
if (fang1 * fang2 == num) {
return true;
}
}
}
return false;
}
public static void main(String[] args) {
for (int i = 10; i <= 100; i++) {
if (isVampire(i)) {
System.out.println(i + " is a vampire number.");
}
}
}
}
This program first checks if a given number is a vampire number by checking all possible combinations of its digits and returning true if it is. The main method then loops through all numbers between 10 and 100 and calls the isVampire method on each to determine if it is a vampire number.
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
NEED HELP
In a worksheet with the ages of 20 people listed in a column, what could you do to easily identify the oldest person?
A.
format the numbers as text
B.
filter the data in that column
C.
paste that column of data in a new worksheet
D.
sort the data in that column
Answers
Answer: the correct answer is D) sort the data in that column
Explanation: got the question right
how i want to be good in coding for subject c programming? anyone has a suggestion?
Answers
Answer:
Get more details about Standard Library Functions in C.
Use logical variable names to avoid any confusion.
Don't forget to check a complete guide for Variables in C.
Explore how Escape Sequence in C make your coding better.
So, I have strict parents & need help, if u don’t know how to fix this after u read it, leave. I don’t want u getting points for nothing I’m deleting ur answer if u do it for points. Anyways, I want to get Spotify on my phone, but it says “Enter the password for (my email)”. How do I sign back into it if I don’t know the password. My dad has the password, but I don’t want to get in trouble for stealing his phone to fix mine. Please help, I’ll give the brainliest!
Answers
Well if you forgot your password you can click "Forgot Password" at the bottom and it should ask you some questions and send you an email with the password
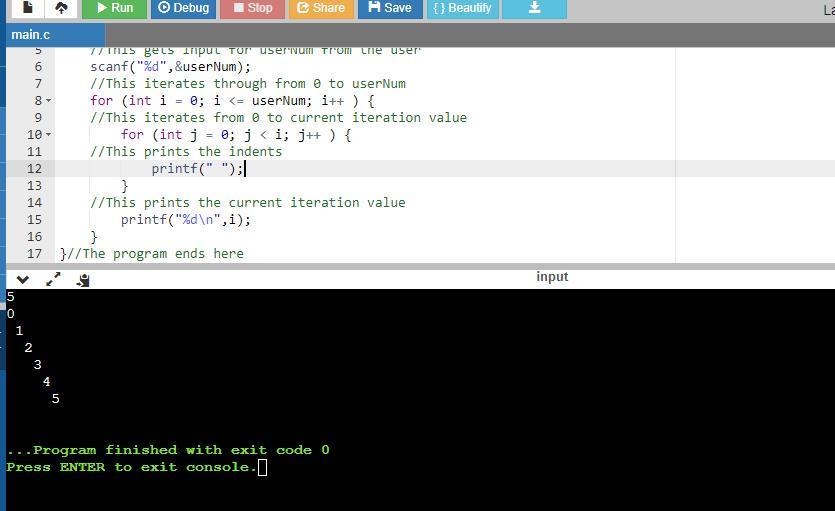
In C language. Print numbers 0, 1, 2, ..., userNum as shown, with each number indented by that number of spaces. For each printed line, print the
leading spaces, then the number, and then a newline. Hint: Use i and j as loop variables (initialize i and j explicitly). Note: Avoid any
other spaces like spaces after the printed number. Ex: userNum = 3 prints:
Answers
The program uses loops to print the numbers from 0 to the user input.
It also uses loops to print the indented space before each iteration value.
The program in C where comments are used to explain each line is as follows:
#include <stdio.h>
int main(){
//This declares userNum as integer
int userNum;
//This gets input for userNum from the user
scanf("%d",&userNum);
//This iterates through from 0 to userNum
for (int i = 0; i <= userNum; i++ ) {
//This iterates from 0 to current iteration value
for (int j = 0; j < i; j++ ) {
//This prints the indents
printf(" "); }
//This prints the current iteration value
printf("%d\n",i); }
}//The program ends here
At the end of the program, the program outputs the indent, followed by the iteration value and a new line.
See attachment for the program sample run
Read more about loops at:
https://brainly.com/question/21751160
survey and describe the system
Answers
Survey systems help create, distribute, and analyze surveys by providing a framework for designing questionnaires, managing respondents, and analyzing data.
What is survey?A survey system lets users create surveys with different question types and response options. The system offers multiple ways to distribute surveys, including sharing a web link, email invites, website embedding, and social media.
Data is collected from respondents and stored accurately and securely, with error checking and validation in place. After survey completion, analyze data with summary stats, visualizations, filters, and cross-tabulations for identifying patterns. Survey systems have reporting features to generate detailed reports based on its data, including statistics, graphs, etc.
Learn more about survey from
https://brainly.com/question/14610641
#SPJ1
Which alignment aligns text to the left and right side margins?
A) Centered alignment
B) Correct alignment
C) Horizontal alignment
D) Vertical alignment
Answers
Answer:
I have the same question but a little different I’m sorry that this is useless to you question but it’s not letting me ask my question. Sorry again-
Explanation:
What is a software system designed to locate information on the World Wide Web? Search browser Search engine Search keyword Search results
PLZ HELP THIS ENDS TODAY
During slide show mode, hitting the B key will do which of these?
End your presentation
Blank the screen with black screen
Move back one page
Move to the first page of your presentation
Answers
Answer:
B or Period. Pressing the B key or period key pauses the slideshow and displays a black screen, which you can write on. Press the B or period key again to resume the slideshow.
Answer: It blanks the screen black.
You should use the arrow keys.
Explanation:
I tried it.
The Car class will contain two string attributes for a car's make and model. The class will also contain a constructor.
public class Car
{
/ missing code /
}
Which of the following replacements for / missing code / is the most appropriate implementation of the class?
A.
public String make;
public String model;
public Car(String myMake, String myModel)
{ / implementation not shown / }
B.
public String make;
public String model;
private Car(String myMake, String myModel)
{ / implementation not shown / }
C.
private String make;
private String model;
public Car(String myMake, String myModel)
{ / implementation not shown / }
D.
public String make;
private String model;
private Car(String myMake, String myModel)
( / implementation not shown / }
E.
private String make;
private String model;
private Car(String myMake, String myModel)
{ / implementation not shown / }
Answers
Public Car(String myMake, String myModel), / implementation not shown / private String make, private String model
Which of the following best sums up what the arrayMethod () method does to the Nums array?Which statement best sums up what the arrayMethod() method does to the array nums? C. The method call, which was effective before to the update, will now result in a run-time error because it tries to access a character in a string whose last element is at index 7, which is where the problem will occur.
Is a function Object() { [native code] } a procedure that is invoked immediately upon the creation of an object?When a class instance is created, a function Object() { [native code] } method is automatically called. In most cases, constructors carry out initialization or setup tasks, like saving initial values in instance fields.
To know more about String visit:-
https://brainly.com/question/15243238
#SPJ1
what is the fnajofnjanfaofoafnka
Answers
Answer: that is the letter f,n,a,j,o,f,n,j,an,f,a,o,f,n,k,a
Which are ether random letters or….. it’s a word scramble.
I well now organize the letters.
1F 2F 3F 4F
1N 2N 3N 4N
1A 2A 3A 4A
1J 2J
1O 2O
1K
Words that can be written are
Fan four times there are other things such as names it can write such as Joan Jon or it could be abbreviations but I believe It’s just random letters you wrote to confuse the brainly community trust me you confused me lol.
Explanation:
Can someone tell me how to get rid of the the orange with blue and orange on the status bar
Please and thank you
Picture above

Answers
Answer:
Explanation:
i'm not sure how tho
Nia is editing a row in an Access table. The row contains the Pencil icon on the left end of the record
this icon indicate?
A. The record is committed.
B. The record has not been written.
C. The record has been written.
D. Nia is editing the record currently.
Answers
Answer:
The answer is D
Explanation:
That little pencil reminds you that you are entering or editing the current record, and that the changes you are making are not yet saved. The little pencil disappears as soon as you move off the current record. Take that as confirmation that Access has saved your new record, or the changes you made to an existing one.
In the case above, The row has the Pencil icon on the left end of the record this icon indicate Nia is editing the record currently.
What is record?A record is known to be the state or fact of an act been put down or is been recorded.
Note that In the case above, The row has the Pencil icon on the left end of the record this icon indicate Nia is editing the record currently as it shows the pen icon.
Learn more about record from
https://brainly.com/question/25562729
#SPJ9
The OSHA Publication
explains 8 rights that
workers have under the
OSH Act.
Answers
The OSHA Publication explains 8 rights that workers have under the OSH Act is known to be Workers' Rights - OSHA.
What is Workers' Rights - OSHA?This is known to be the making of the Occupational Safety and Health Administration (OSHA) and it is one that was said to be done in 1970
This is one that tends to provide all workers with their right to be in a safe and healthful work environment.
Hence, The OSHA Publication explains 8 rights that workers have under the OSH Act is known to be Workers' Rights - OSHA.
Learn more about OSHA Publication from
https://brainly.com/question/13708970
#SPJ1