A networking instructor is demonstrating the use of a device that, when making a connection to the Internet, issues a series of alternating tones, and is used to translate the digital signals from computers to analog signals used on traditional telephone lines. Although the name is familiar to the students, this particular device is no longer in common use. What is the instructor demonstrating
Answers
A networking instructor is demonstrating the use of a device. Although the name is familiar to the students, this particular device is no longer in common use. A modem is the instructor demonstrating.
The modem is being used as an example by the networking instructor. With the aid of a modem, a computer can transmit digital signals over the internet by connecting to a phone line.
The modem modifies (or converts) the digital signal coming from the computer into analogue signals that may be transmitted over regular phone lines. Additionally, the modem demodulates incoming telephone line signals into digital signals the computer can use.
Learn more about on modem, here:
https://brainly.com/question/14208685
#SPJ4
Related Questions
Vicky is investigating multiple hacking attempts on her cloud-based e-commerce web servers. She wants to add a front-end security system that can actively deploy countermeasures that shuts down the hacking attempts. What application would you suggest that Vicky deploy?
Answers
Answer:
IPS
Explanation:
Intrusion Prevention System can track suspicious activities such as policy violation and actively take preventive measures to prevent and minimize the intrusion impact. It is referred to the network protection technology that analyses the flows of network traffic to identify and mitigate exploits of vulnerability. Vulnerabilities generally come to a specific service in the form of malicious inputs, which attackers use to disrupt and seize the power of a particular application. As per the question, Vicky needs an IPS to counter the hacking attempts.
Casting is one of the oldest known manufacturing processes.
True or false
Answers
in which type of computer parallel processing is possible
Answers
Answer:
(Hope this helps can I pls have brainlist (crown)☺️)
Explanation:
Parallel processing may be done on any system with more than one CPU, including multi-core processors, which are prevalent in today's computers. Multi-core processors are integrated circuit chips with two or more processors for improved performance, lower power consumption, and more efficient multitasking.
We take in numerous distinct types of information at the same time in parallel processing. This is especially true when it comes to vision. When you see a bus approaching, for example, you can perceive its colour, form, depth, and velocity all at once. It would take far too long if you were to evaluate each item individually.
How should I do it Please code for Java

Answers
Answer:
class Main {
public static void printPattern( int count, int... arr) {
for (int i : arr) {
for(int j=0; j<count; j++)
System.out.printf("%d ", i);
System.out.println();
}
System.out.println("------------------");
}
public static void main(String args[]) {
printPattern(4, 1,2,4);
printPattern(4, 2,3,4);
printPattern(5, 5,4,3);
}
}
Explanation:
Above is a compact implementation.
for a given system:- virtual addresses are 40 bits.- physical addresses are 30 bits.- 8 kbytes of addressable entries per page.- the tlb in the address translation path has 128 entries.how many virtual addresses can be quickly translated by the tlb? would changing the page size makeyour answer better or worse?- virtual addresses are 40 bits.- physical addresses are 30 bits.- 8 kbytes of addressable entries per page.- the tlb in the address translation path has 128 entries.how many virtual addresses can be quickly translated by the tlb? would changing the page size makeyour answer better or worse?
Answers
Given the system with 40-bit virtual addresses, 30-bit physical addresses, 8 Kbytes of addressable entries per page, and a TLB with 128 entries, the number of virtual addresses that can be quickly translated by the TLB is 128 x 8 Kbytes = 1 Mbyte. This means that the TLB can store the translations for 1 Mbyte of virtual memory addresses, allowing for fast and efficient address translation.
Changing the page size can affect the number of virtual addresses that can be quickly translated by the TLB. If the page size is increased, there will be fewer entries in the page table and fewer translations needed, which can lead to better TLB performance. However, if the page size is decreased, there will be more entries in the page table and more translations needed, which can lead to worse TLB performance. The optimal page size depends on the specific characteristics of the system and workload, and may require experimentation and tuning to determine the best configuration.
To learn more about memory click on the link below:
brainly.com/question/31382063
#SPJ11
It is necessary for us to verify and checked information before we shared online? Explain
Answers
Answer:
The answer is yes.
Explanation:
If you don’t check where the source is from and if it is verified, you may share an incorrect and false answer. Also, you may type in your personal information. This is VERY risky. Do NOT share your private information to strangers!
You can check your information by searching it up online or asking a teacher! There! I hope this helps! ;)
To insert a row, right-click the row below where you want to insert a row and then click on ____ the shortcut menu. A. Columns B. Insert C.Rows D.Cells
Answers
Answer:
I think it's insert. (It's the only one that actually makes sense).
Explanation:
Hope that helps. x
Josh is learning about hackers known for causing damage and altering functions of websites. Which type of hacker is he learning about?
A. Brown hat hacker
B. Black hat hacker
C. White hat hacker
D. Gray hat hacker
Answers
Answer:
WHITE HACKERS
Explanation: When a white hat hacker discovers a vulnerability, they will exploit it only with permission and not tell others about it until it has been fixed. In contrast, the black hat will illegally exploit it or tell others how to do so. The gray hat will neither illegally exploit it nor tell others how to do so.
Answer:white hat hacker's
Explanation The white hat hacker is one who is an ethical hacker.
model of social relations, individuals go through life embedded in a personal network of individuals to whom they give and from whom they receive social support.
Answers
According to the social convoy theory of social relationships, people live their lives as part of a personal network of people to whom they provide support and from whom they receive it.
What is the meaning of social convoy?The people that travel with us on the road of life are referred to as the social convoy. At every stage of development, this social grouping is a crucial component of successful adjustment and wellbeing.
As one matures and develops, they rely on these interactions and connections because all are social beings. Social convoy is a network of friends that travel through life with us and support us through both good and difficult times.
Learn more about social convoy from here:
https://brainly.com/question/7318152
#SPJ1
The complete question has been attached in text form:
In the social ______ model of social relations, individuals go through life embedded in a personal network of individuals to whom they give and from whom they receive social support.
TRUE/FALSE. a game writer and a game designer are two distinctly different jobs that require different skill sets.
Answers
True. Writing the game and actually developing is completely different. Think of it as a coloring page: you could color it in, sure, but could you redraw the image?
2 WAp to input the radius and print
the area of circle
Answers
\(\tt r=float(input("Enter\:the\:value\:for\:radius\:of\:circle"))\)
\(\tt x=3.14*\:r**2\)
\(\tt print("Area\:of\:Circle=\{x\}")\)
Sample run:-\(\tt r=3\)
\(\tt Area\:of\:the\:circle=28.26\)
Janae started an essay on the computer at school. She would like to work on it when she gets home, but she does not have a flash drive. What technology would allow her to work on the essay on any device as long as there is internet access?
Answers
Answer:
The answer is "Cloud Computing".
Explanation:
The term, cloud computing also is known as accessible on-demand, it uses central computer services through specific active user management, especially for cloud services.
It is used to define storage systems accessible through the Internet for several users. It offers rapid innovation, scalable resources, or advantages of scale to computing resources, that's why she uses cloud computing technology.what do most large corporations use to consolidate internal and external data?
Answers
Answer:
Most large corporations use Enterprise Resource Planning (ERP) systems to consolidate internal and external data. These systems integrate various business functions such as finance, accounting, human resources, supply chain management, and customer relationship management into a single, comprehensive database. The goal is to provide accurate and timely information to support decision-making and streamline business processes.
Explanation:
Some one help pls will mark brainless !!!!!
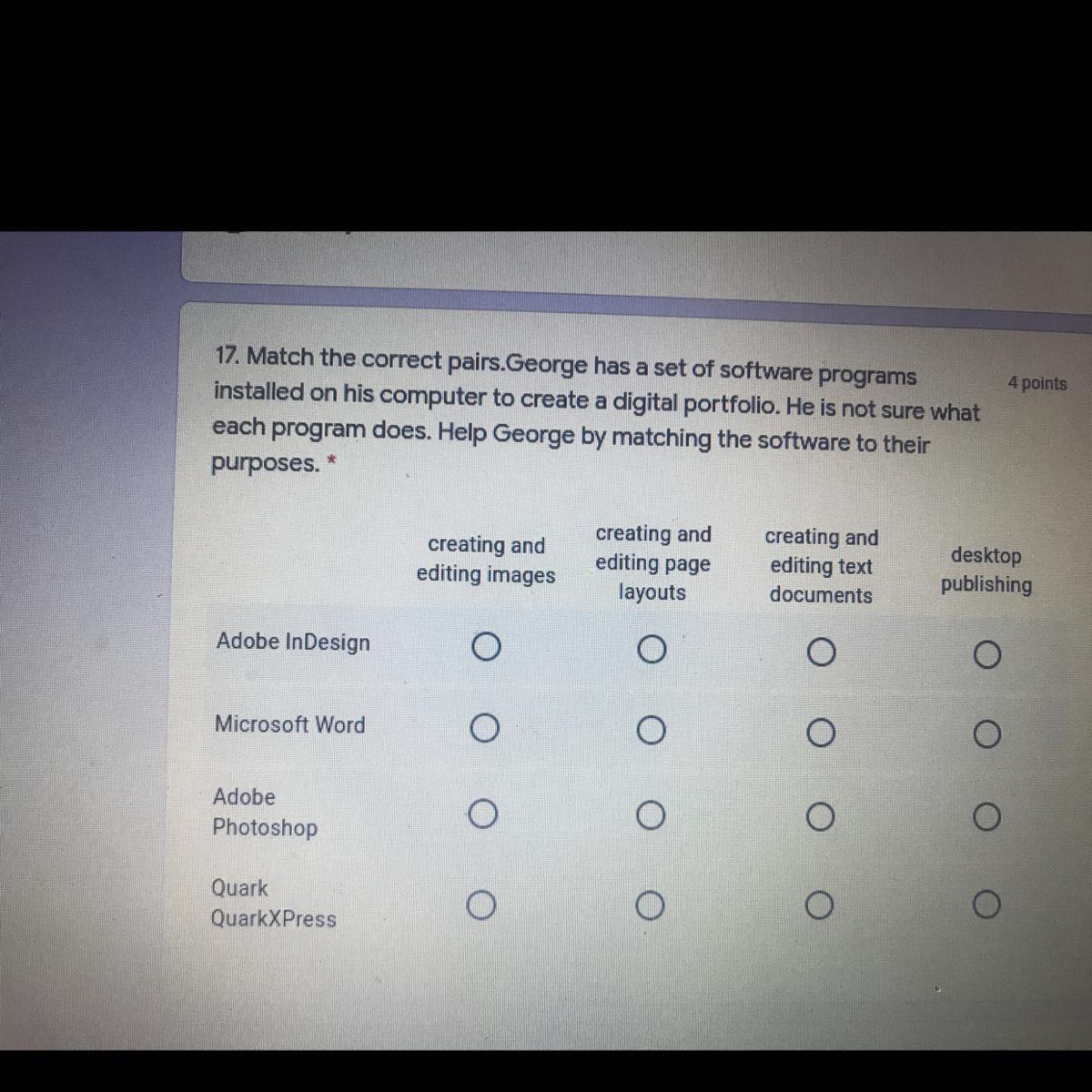
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
2) Prompt the user for his/her favorite 2-digit number, and the output is the square root of the number.
Answers
num = int(input("What's your favorite 2-digit number? "))
print("The square root of {} is {}".format(num, (num**0.5)))
I hope this helps!
to show the year using four digits, such as 2021, you would enter ________ for the custom code format.
Answers
To show the year using four digits, such as 2021, you would enter "yyyy" for the custom code format.
The "yyyy" format code is used to represent the year with four digits. Each "y" represents a digit of the year. By entering "yyyy" as the custom code format, it instructs the system to display the year in a four-digit format. For example, if the current year is 2023, using this format will display "2023". This is commonly used in programming, spreadsheets, and various software applications where the year needs to be presented in a specific format.
Learn more about software here:
https://brainly.com/question/985406
#SPJ11
If you want to connect a TV to your computer, you need to use the:
video port.
DVI port.
S-video port.
sound port.
Answers
In your own words! Give me an example of Digital Literacy? (50 words
No links or I will report!!!!!!!
Answers
Answer: See explanation
Explanation:
Digital literacy is when an individual can compose, find, and evaluate, a clear and composed information on digital platforms.
It involves possessing the skills that one need to live, and learn, through the use of digital platforms such as social media, mobile
Example of digits literacy is the use of search engines, understanding how web browser can be used or sending of emails. etc
what do you mean by networking devive?
Answers
Answer:
Networking Device are Those Device which are required for communicating and interacting between device and a computer network.
Explanation:
.Choose the extention of Scratch Project
.sb2
jpeg
.exls
Answers
Answer:
I know about .sb3, and it similar to .sb2
that might be your answer.
Explanation:
jpeg is for pictures and .exls is Microsoft's excel
extension.
Can anyone help me on assignment 8: personal organizer on edhesive?
Answers
Open the PDF attached and it has the code I used to answer it. It got me 100%. Hope it works for you <3
Help pls due today
Select the correct answer. Mike needs to export some animation videos
from his smartphone to an online platform. Which common file format can
he use for this purpose?
1) .swf
2 ) flv
3) .mov
4) .3gp
Answers
The Correct Answer:
3) .mov
Answer:
D. .3gp
Explanation:
You've just received an e-mail message that indicates a new serious malicious code threat is ravaging across the Internet. The message contains detailed information about the threat, its source code, and the damage it can inflict. The message states that you can easily detect whether or not you have already been a victim of this threat by the presence of the three files in \Windows\System32 folder. As a countermeasure, the message suggests that you delete these three files from your system to prevent further spread of the threat. What should your first action based on this message be?a. Perform a complete system backup.b. Verify the information on well-known malicious code threat management web sitesc. Distribute the message to everyone in your address book.d. Reboot the system.e. Delete the indicated files if present
Answers
Answer:
B.) Verify the information on well-known malicious code threat management web sites
Explanation:
Of course, you should verify the message with reliable sources before taking any actions that could impact your computer. Even if the message seemed legit, it telling you to fiddle with the Windows system folder is a red flag.
Verify the information on well-known malicious code threat management web sites. The correct option is b.
What is malicious code threat?The threat posed by malicious code to application security cannot be effectively addressed by traditional antivirus software on its own.
Attack scripts, viruses, worms, Trojan horses, backdoors, and malicious active content are all examples of the broad category of system security words known as harmful code.
Malware attacks are frequent cyberattacks in which the victim's system is compromised by malware, which is typically malicious software.
Ransomware, malware, command and control, and other specialised sorts of attacks are all included in malicious software, sometimes known as viruses.
The notification advises you to remove these three files from your system as a countermeasure to stop the threat from spreading further, but you should first double-check the information on reputable harmful code threat management websites.
Thus, the correct option is b.
For more details regarding malicious attacks, visit:
https://brainly.com/question/13137381
#SPJ5
How does your phone work?
Answers
Answer:
Radiation and enjoyment
Explanation:
In the most basic form, a cell phone is essentially a two-way radio, consisting of a radio transmitter and a radio receiver. When you chat with your friend on your cell phone, your phone converts your voice into an electrical signal, which is then transmitted via radio waves to the nearest cell tower.
Stress and anxiety. Excessive use of mobile phones is bad for your psychological health. Constant over-use of mobile phones leads to increased anxiety, feelings of loneliness, and low self-esteem. Reliance on mobile phones can also cause irritation, frustration, and impatience when they cannot be used.
Even when you can't talk, cell phones make communication easy with the use of text messaging. With more sophisticated cell phones, you can also send pictures, video clips, listen to music, and even access the Internet. Some cell phones also provide access to calculators, maps, GPS devices and television.
Which of the following is not a characteristic of a large database?
a) Optstore items in a filing cabinet.
b) Stores items in a computer such as music.
c) stores large amounts of items such as an online store.
d) can be used as a small recipe book.
Answers
find the binary representation of each of the following positive integers by working through the algorithm by hand. you can check your answer using the sage cell above.
Answers
the binary representation of 13 is 1101. To find the binary representation of a positive integer, you can follow the algorithm below:
Start with the given positive integer. Divide the number by 2 and write down the remainder. Continue dividing the quotient obtained in step 2 by 2, writing down the remainders each time, until the quotient is 0. The binary representation is the sequence of remainders obtained in reverse order.
Let's work through an example with the positive integer 13
Start with 13. Divide 13 by 2 to get a quotient of 6 and a remainder of 1. Divide 6 by 2 to get a quotient of 3 and a remainder of 0. Divide 3 by 2 to get a quotient of 1 and a remainder of 1 Divide 1 by 2 to get a quotient of 0 and a remainder of 1.
To know more about binary representation visit :-
https://brainly.com/question/30871458
#SPJ11
in a dark place you have only a match , a twig , campfire logs , and oil lamp and a candle which do you literally first /
a twig
a campfire
none of the above
Answers
Answer:
You would use a twig first :)
Explanation:
Answer:
The glowing embers from the crackling campfire lit up the nighttime sky.
Explanation:
Technological progress is affected by (check all that apply) a. population growth b. new software developments c. investment in capital d. private property rights e. entrepreneurship
Answers
Technological progress is affected by,
a. population growth
c. investment in capital
d. private property rights
e. entrepreneurship
What is Entrepreneurship?
Entrepreneurship exists in the process of discovering new ways of combining resources. When the market value generated by this new variety of resources is greater than the market value these resources can cause elsewhere individually or in some other assortment, the entrepreneur makes a profit.
Entrepreneurship stands for the creation or extraction of economic value. With this definition, entrepreneurship is viewed as change, generally entailing risk above what is normally experienced in starting a business, which may contain other values than simply economic ones. Population growth stands for the increase in the number of individuals in a population or dispersed group.
Property rights have evolved over ancient and modern history, from Abrahamic law to today's Universal Declaration of Human Rights article 17. Property rights can be comprehended as constructs in economics for resolving how a resource or economic good exists used and is owned.
Technological progress guides the discovery of new and improved methods of producing goods. Differences in technology lead to an increase in the productivity of labor, capital, and other factors of production. Technology guides the process through which inputs exist transformed into outputs.
Hence, Technological progress is affected by,
a. population growth
c. investment in capital
d. private property rights
e. entrepreneurship
To learn more about Entrepreneurship refer to:
https://brainly.com/question/353543
#SPJ4
A 4"x6" photo is digitized using 10,000 pixels. An 11"x7" photo is digitized using 30,000 pixels. Which image will have the better resolution?
the 11"x7" photo
the 4"x"6 photo
the photos will have the same resolution
Answers
An image which will have the better resolution is: A. the 11"x7" photo.
What is a camera lens?A camera lens can be defined as a transparent optical instrument that is used in conjunction with a digital camera, so as to refract rays of light coming into the lens.
What is a resolution?A resolution can be defined as the number of pixels that are contained in an image (picture or photo) or on a display monitor of a computer system such a laptop.
In this scenario, we can infer an logically deduce that an image which will have the better resolution is the 11"x7" photo because it has a higher number of pixel (30,000 pixels) than the 4"x"6 photo.
Read more on resolution here: https://brainly.com/question/14294025
#SPJ1
focus in regards to the use of network load balancing clusters, what statement is not accurate?
Answers
The statement "Load balancing ensures that all nodes in the cluster handle the same amount of traffic" is not accurate in regards to the use of network load balancing clusters.
Network load balancing is a method for distributing network traffic across multiple servers or network resources in order to maximize resource utilization, minimize latency, and improve redundancy. It can also be used to improve network performance and scalability by distributing incoming traffic across multiple resources, such as servers, switches, or routers.Load balancing clusters of servers require specific hardware, software, and configurations that allow them to work together as a single system.
These clusters are designed to handle heavy traffic loads, provide redundancy, and improve the performance of applications and services by distributing traffic across multiple servers and network resources.Each node in a load balancing cluster has a unique IP address and hostname, but the cluster itself is represented by a single virtual IP address and hostname that is used to represent all nodes in the cluster.
The statement "Load balancing ensures that all nodes in the cluster handle the same amount of traffic" is not accurate in regards to the use of network load balancing clusters. This is because the amount of traffic handled by each node is not necessarily the same. In fact, the amount of traffic handled by each node will depend on a number of factors, including the load balancing algorithm used, the capacity of each node, and the amount of traffic being processed by each node at any given time.
To learn more about "Network Traffic" visit: https://brainly.com/question/29039902
#SPJ11