you have been trying to troubleshoot a user's system all day when it suddenly becomes clear that the data is irretrievably lost. when you inform the customer, they become so angry that they shove you against a wall. what should you do?
Answers
You ought to make an effort to relax the user. If you are unable to accomplish this, you should immediately leave the area and wait until it's safe to do so before coming back.
By data, what do you mean?Data is data that has been transformed into a format that is useful for transfer or processing in computing. Data is information that has been transformed to binary pdf format for use with modern computers and communication mediums.
How does life use data?Tracking and keeping track of one's health habits, Epidemic and disease prediction, treatment regimens, and prospective treatments.
To know more about data visit:
https://brainly.com/question/13650923
#SPJ4
Related Questions
is it possible build a real time machine?
Answers
Answer:
An Iranian scientist has claimed to have invented a 'time machine' that can predict the future of any individual with a 98 percent accuracy. Serial inventor Ali Razeghi registered "The Aryayek Time Traveling Machine" with Iran's state-run Centre for Strategic Inventions, The Telegraph reported.
Explanation:
large carriers like sprint, at&t, and xo communications exchange internet traffic freely at physical locations called ________.
Answers
The answer is Internet Exchange
Need help with this please
4. Declare three variables and give them the names of three common grocery items. Assign to each variable a NUMBER value approximately its price. Don’t use $ sign, just the actual number.
5. Declare another variable, name it total, and assign to it the SUM of the three other variables, using the VARIABLE NAMES, not the value they contain. Hint - you’ll need to use an arithmetic operator to do this.
This is what my assignment looks like in the picture.
It’s for a coding class I’m taking.
I’m just super confused on how to do part B.

Answers
Answer:
4. let eggs = 5
let bread = 10
let soda = 6
5.
let total = eggs+bread+soda
the tool used to apply policy settings to multiple computers in an active directory domain is ________.
Answers
The tool used to apply policy settings to multiple computers in an Active Directory domain is Group Policy.
Group Policy allows administrators to manage and enforce configurations for users and computers within the domain. This centralized management approach simplifies administration tasks and ensures consistent settings across the network.
Through Group Policy Objects (GPOs), administrators can define settings such as security policies, software installation, and login scripts.
These settings are then applied to users and computers within specified Organizational Units (OUs) in the domain hierarchy. Group Policy streamlines the management of large networks and improves overall security and efficiency.
Learn more about group policy at https://brainly.com/question/30778834
#SPJ11
A framework for all of the entities involved in digital certificates for digital certificate management is known as:
Answers
Answer:
public key infrastructure
Explanation:
Public key infrastructure (PKI) refers to tools used to create and manage public keys for encryption, which is a common method of securing data transfers on the internet. PKI is built into all web browsers used today, and it helps secure public internet traffic. Organizations can use it to secure the communications they send back and forth internally and also to make sure connected devices can connect securely.
The most important concept associated with PKI is the cryptographic keys that are part of the encryption process and serve to authenticate different people or devices attempting to communicate with the network.
To identify the effect in a text, you can ask yourself which question?
A. What happened?
B. Why did this happen?
C. How did the person feel?
D. Where did this happen?
Answers
Answer:
why did this happen?
Explanation:
effect means what caused it so You should ask why did this happen or (what caused it)
4.2 Lesson Practice Edhisive

Answers
Answer:
10
Explanation:
What is phishing? Answer
Answers
Answer:
Phishing is a type of online scam where an attacker sends a fraudulent email purporting to be from reputable companies, designed to deceive a person into revealing sensitive and personal information (card numbers, passwords etc).
Hope this helps.
Describe the IT software that might be used by the Seller to summarize and analyze previous sales, which goods, which customers, etc. Explain the software and give examples of suggested information required by the seller.
Answers
Answer:
Explanation:
Customer Relationship Management (CRM) software presents a substantial step up over spreadsheet software in a number of ways. CRM software automatically records interactions with leads in your pipeline, saving your team time otherwise wasted on data entry and helping you make sure you never lose track of communications with your leads. Plus, with mobile app features and third-party integrations, CRMs expand the scope of what you can measure.
Were your automated email campaigns successful? How long was the average length of a successful cold call versus an unsuccessful one? Where are your most successful leads being generated?
Your CRM gives you reports on your winning sales patterns so you can reproduce and improve them.
On top of everything a spreadsheet can do, CRMs give you even more control of your data. Whether you’re reviewing your overall sales process for bottlenecks or looking at the most effective way to bring cold leads back into the pipeline, your CRM will have data to help.
Regardless of your software, once you’ve been collecting data for a few weeks you’ll have a pool of data, sales information and more you can draw from. The longer you keep reporting, the more data you’ll have and the more accurate it’ll be.
9. Which of the following is a disadvantage of cloud storage? * Accessibility (offline/without internet) Reduction of storage cost to organization, Increased possibility for disaster recovery, Efficient management of stored Data
Answers
Answer:
Accessibility offline
Explanation:
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

(Approximate pi) pi can be computed using the following formula
pi = 4* ( 1-1/3 + 1/5 - 1/7 +1/9 - 1/11+...)
Write a program that displays the result of 4* ( 1-1/3 + 1/5 - 1/7 +1/9 - 1/11)
and 4* ( 1-1/3 + 1/5 - 1/7 +1/9 - 1/11 + 1/13 - 1/15).
Code should be in python.
Answers
The python program to display the value of pi, define a variable pi and set it to 0. Iterate over a range of odd numbers starting from 1, adding or subtracting the inverse of the current number to pi based on the position in the series. Multiply the final value of pi by 4 to approximate π.
Here's a Python program that approximates the value of π using the provided formula:
def compute_pi(n):
pi = 0
sign = 1
for i in range(1, n+1):
term = 1 / (2*i - 1)
pi += sign * term
sign *= -1
return 4 * pi
# Compute pi with the first 6 terms
result1 = compute_pi(6)
print("Result with 6 terms:", result1)
# Compute pi with the first 8 terms
result2 = compute_pi(8)
print("Result with 8 terms:", result2)
This program defines a function compute_pi() that takes an integer n as input, representing the number of terms in the series. It iterates over the range of 1 to n and calculates each term in the series based on the formula.
The sign alternates between positive and negative for each term. Finally, the function returns the computed value of π.
In the main code, we call the compute_pi() function with n equal to 6 and 8, respectively, and store the results in result1 and result2. We then print the results to display the approximations of π using the given number of terms.
To learn more about python: https://brainly.com/question/26497128
#SPJ11
You are serving content from CloudFront. Which of the following happens to an end user's request?
-The user's request is routed to the origin server
-The user's request is routed to the nearest edge location.
-The user's requests are routed to the edge location in the country from which the request originates.
-For countries without edge location, requests are routed to the origin server.
Answers
When serving content from CloudFront, an end user's request is typically routed to the nearest edge location.
CloudFront automatically detects the end user's location and routes the request to the nearest edge location in order to reduce latency and improve performance. The edge location serves as a cache for the content, which means that subsequent requests for the same content can be served from the edge location rather than going all the way back to the origin server. If CloudFront does not have an edge location in the country from which the request originates, the request is routed to the origin server. However, with over 200 edge locations worldwide, CloudFront can typically serve content quickly and efficiently to users all over the globe.
To know more about CloudFront visit:
https://brainly.com/question/31712211
#SPJ11
draw the block diagrams of the four state elements of a risc-v microprocessor and describe their functionalities and operations.
Answers
The drawing of the of the four state elements of a risc-v microprocessor is :
+-------------+
| |
| Program |
| Counter (PC)|
| |
+-----+-------+
|
|
v
+-----+-------+
| |
| Instruction |
| Register (IR)|
| |
+-----+-------+
|
|
v
+-----+-------+
| |
| Register |
| File (RF) |
| |
+-----+-------+
|
|
v
+-----+-------+
| |
| Arithmetic |
| Logic Unit |
| (ALU) |
| |
+-------------+
These elements are commonly found in a RISC-V processor design are:
Program Counter (PC)Instruction Register (IRRegister File (RF)ALU (Arithmetic Logic Unit)What is the RISC-V processor designThe Program Counter, which maintains the memory address of the next instruction to be fetched. It's a register for the current instruction's memory address. After each fetch, the PC is incremented to the next instruction in memory.
The IR is a storage element holding the current instruction being executed. It gets the instruction from memory, which the decoder uses to identify the instruction's type and required actions.
In RISC-V, register file has GPRs. These 32-bit registers store integer data. Register File serves as an operand provider and result storage for arithmetic and logical operations.
ALU performs math & logic ops on data. Gets input from Register File and performs arithmetic, bitwise, and comparison operations. ALU handles integer operations based on RISC-V ISA.
Learn more about RISC-V processor design from
https://brainly.com/question/29817518
#SPJ4
DUI manslaughter results in…
A. becoming a convicted felon.
B. a misdemeanor offense.
C. a third degree misdemeanor offense.
Answers
Answer:
a third degree misdemeanor offense.
I use the wrap text feature in Excel daily. What is the difference in how this behaves or is used in Excel versus Word? Please explain in detail the differences and similarities.
Answers
The wrap text feature is an essential tool used to format text, particularly long texts or data within a cell in Microsoft Excel. In this question, we need to explain the difference between how wrap text behaves in Microsoft Excel versus how it is used in Microsoft Word.
Wrap Text in Microsoft Excel: Wrap text in Excel is a formatting option that is used to adjust text or data within a cell. When the text entered exceeds the size of the cell, it can be hard to read, and this is where wrap text comes in handy. Wrap text in Excel automatically formats the data within the cell and adjusts the text size to fit the cell's width. If a cell contains too much data to fit in the column, the cell's text wraps to the next line within the same cell.
To wrap text in Excel, follow these simple steps:
Select the cell or range of cells containing the text that needs wrapping. Right-click on the selected cell and click Format Cells. In the Format Cells dialog box, click on the Alignment tab. Click the Wrap text option and then click OK.Wrap Text in Microsoft Word: In Microsoft Word, the Wrap Text feature is used to format text around images and graphics. It is used to change the way the text flows around the image, allowing users to position images and graphics in the document. Wrap Text in Microsoft Word does not adjust the font size of the text to fit the width of the cell like in Excel.
To wrap text in Microsoft Word, follow these simple steps:
Insert the image in the document. Select the image and go to the Picture Format tab. Click on Wrap Text, and you can choose how you want the text to wrap around the image.The main difference between the use of Wrap Text in Microsoft Excel and Microsoft Word is that Wrap Text in Excel is used to format long data and adjust text size to fit the width of the cell while Wrap Text in Microsoft Word is used to format text around images and graphics.
To learn more about wrap text, visit:
https://brainly.com/question/27962229
#SPJ11
What is a commerce platform?
Answers
Answer:
In basic terms, a commerce platform simply refers to technology that enables a transaction (the commerce bit). The platform part allows you to overlay that technology across various channels such as online and in-store.
Answer:
Explanation:
a commerce platform simply refers to technology that enables a transaction (the commerce bit). The platform part allows you to overlay that technology across various channels such as online and in-store.20 Feb 2017
which mode is required to install the license on a cisco device?
Answers
Answer:
EXEC modeExplanation:
I hope it's helpful for youAnswer:
sry I don't know the answer
Select the correct answer.
Which letter will be uppercase in the below sentence?
she will have exams next week.
A.
s in she
B.
h in have
C.
e in exams
D.
w in week
E.
n in next

Answers
Answer:D
Explanation:
I have no errors in the code but for some reason it doesn't work... what i'm missing?

Answers
The JavaScript code that you have written is one that tends to retrieves data from a table that is called "Busiest Airports" . The corrected code is given below.
What is the getColumn code about?In regards to the given code that was corrected, the user input is one that can be obtained from the text input element with the use of the ID "yearInputBox" via the act of getText function as well as been saved in a variable named inputYear.
Therefore, when there is a match that is found, the output is said to be made by the use of the corresponding elements that is obtained from the year, as well as country, and that of airport arrays, and later on set to the "outputBox" element via the use of the setText function.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1
See text below
1
var year getColumn("Busiest Airports", "Year");
var country = getColumn ("Busiest Airports", "Country");
var airport = getColumn("Busiest Airports", "Airport");
onEvent("goButton", "click", function() {
/*call the "calculateOutput" function here,
*passing in the user input as a paremeter 10 */
calculateOutput (getText("year InputBox"));
function calculateOutput (years){
var output="";
for (var i = 0; i < year.length; i++) { /*write the list element being accessed*/ if (years[i] == "inputYear"){ output "In "
=
+ year + "the busiest airport was
11
+ country + "
in "airport[i];
21
}
}
setText("outputBox", output );
}

print 3 numbers before asking a user to input an integer

Answers
Answer:
you can use an array to do this
Explanation:
(I've written this in java - I think it should work out):
Scanner input = new Scanner(System.in);
System.out.println("Enter an integer: ");
int userInt = input.nextInt();
int[] array = new int[userInt - 1];
for(int i = userInt-1; i < userInt; i--)
System.out.println(array[i]);
is spin to win paying or is a scam app
Answers
Answer:
scam bro.
Explanation:
Answer:
yes it's a scam app when I tried it and after a few days it hasn't been delivered to my house though
9. can you envision circumstances in which an assembly language permits a label to be the same as an opcode (e.g., mov as a label)? discuss.
Answers
No, there are no circumstances in which an assembly language permits a label to be the same as an opcode. It is not possible to use opcode as a label in assembly language.
This is because opcodes are reserved keywords and commands that are already used to perform certain operations. If you try to use an opcode as a label, the assembler will fail to identify the intended instruction and raise an error.
For example, in the following code, `mov` is an opcode:``` mov ax, bx ```In this instruction, `mov` copies the contents of the `bx` register into the `ax` register. If we try to use `mov` as a label like this:``` mov: mov ax, bx ```
This code will fail because `mov` is already reserved as an opcode and cannot be used as a label. Therefore, it is not possible to use an opcode as a label in assembly language.
Learn more about assembly language at:
https://brainly.com/question/31764413
#SPJ11
what do you mean by networking devive?
Answers
Answer:
Networking Device are Those Device which are required for communicating and interacting between device and a computer network.
Explanation:
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
What is the something in the computer can be in the form of a tables, reports and graphs etc.
Answers
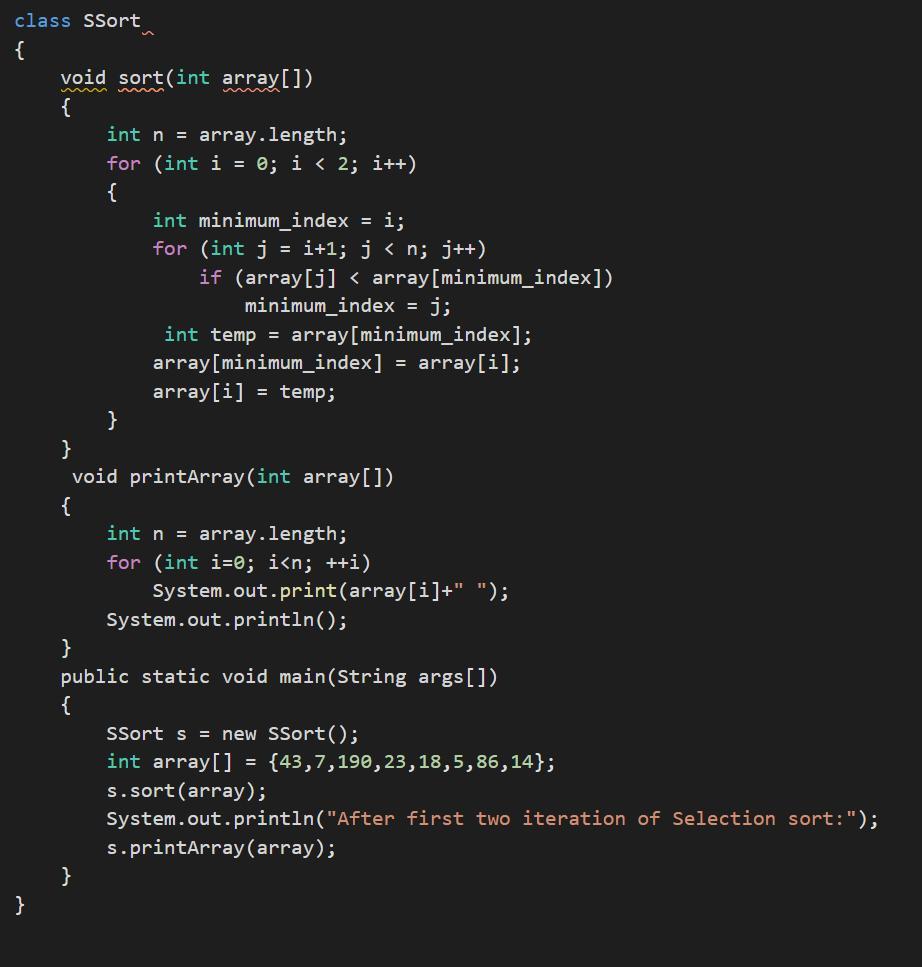
Show the contents of the array {43, 7, 190,23,18, 5,86,14} (sort in ascending order) after the first two iterations of Selection Sort. How many comparisons would be needed to sort an array containing 10 elements using Bubble sort in the worst case
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that organizes the values in larger and smaller in arguments.
Writing the code in JAVA we have:class SSort
{
void sort(int array[])
{
int n = array.length;
for (int i = 0; i < 2; i++)
{
int minimum_index = i;
for (int j = i+1; j < n; j++)
if (array[j] < array[minimum_index])
minimum_index = j;
int temp = array[minimum_index];
array[minimum_index] = array[i];
array[i] = temp;
}
}
void printArray(int array[])
{
int n = array.length;
for (int i=0; i<n; ++i)
System.out.print(array[i]+" ");
System.out.println();
}
public static void main(String args[])
{
SSort s = new SSort();
int array[] = {43,7,190,23,18,5,86,14};
s.sort(array);
System.out.println("After first two iteration of Selection sort:");
s.printArray(array);
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Which is the name of a note-taking method that can be used when watching a video? SQRW sticky notes charting highlighting
Answers
Answer:Charting!
Explanation:so I just came across this question on edgenuity and it’s C, Charting. Hope this helped
Answer:
C.
Explanation:
It’s right :D
Digital Dashboard Analytic Capabilities Drag the name of the digital dashboard analytical capabilities to match its definition Pivot Slice-and-Dice Consolidation Drill-Down The aggregation of data from simple roll-ups to complex groupings of interrelated information Enables users to view details, and details of details, of information The ability to look at information from different perspectives Rotates data to display alternative presentations of the data Reset
Answers
The digital dashboard analytic is the match on the terms are:
1. Pivot: rotates data to display alternative presentations of the data.
2. Consolidation: The aggregation of data from simple roll-ups to complex groupings of interrelated information.
3. Slice and dice: The ability to look at the data warehouse information from different perspectives.
4. Drill Down: enables users to view details of information.
What is Consolidation?The word consolidate is derived from the Latin word consolidates, which meaning "to merge into one body." To consolidate, in whatever context, means to combine numerous objects into a singular, smaller number.
According to the dash board as the match on the appropriate as the term.
1. Pivot: flips data to display alternate data presentations.
2. Consolidation: The process of aggregating data from basic roll-ups to complicated groups of interconnected information.
3. Slice and slices: The capacity to examine data warehouse material from many angles.
4. Drill Down: allows consumers to view information specifics.
As a result, the significance of the consolidation, are the aforementioned.
Learn more about on consolidate, here:
https://brainly.com/question/15296526
#SPJ4

A key component of the u. S. Government under the constitution is.
Answers
Answer:
a legislative, an executive, and a judicial branch