You have been experiencing a slowdown when you connect to your corporate intranet from outside the office. Which command should you run from your Windows workstation if you need to determine which router is having problems
Answers
When experiencing a slowdown connecting to your corporate intranet from outside the office, you should run the "tracert" command from your Windows workstation.
How does "tracert" command identify problematic routers?To determine which router is causing problems when experiencing a slowdown connecting to your corporate intranet from outside the office, you can use the "tracert" (short for "trace route") command on your Windows workstation.
The "tracert" command is a network diagnostic tool that traces the route taken by packets from your computer to the destination IP address. It sends a series of ICMP (Internet Control Message Protocol) echo request packets with gradually increasing Time-To-Live (TTL) values.
Each router along the path decrements the TTL value, and when it reaches zero, the router discards the packet and sends an ICMP time exceeded message back to the sender. By analyzing these responses, the "tracert" command determines the IP addresses and round-trip times of each router encountered along the route.
By running the "tracert" command and examining the output, you can identify the routers that are causing delays or packet loss, as well as the overall path taken by your connection.
This information can help pinpoint the specific router or network segment that is experiencing issues, allowing you to troubleshoot or report the problem to your network administrators for further investigation and resolution.
Learn more about router
brainly.com/question/32317464
#SPJ11
Related Questions
which gallery will allow a user to access a variety of preconfigured formatting styles for images that are added to a PowerPoint presentation
Answers
Answer:
Picture Effects gallery.
Explanation:
PowerPoint application can be defined as a software application or program designed and developed by Microsoft, to avail users the ability to create various slides containing textual and multimedia informations that can be used during a presentation. Some of the features available on Microsoft PowerPoint are narrations, transition effects, custom slideshows, animation effects, formatting options etc.
To format an image on PowerPoint, you can either use the Artistic Effects or Picture Effects.
The Picture Effects gallery allows a user to access a variety of preconfigured formatting styles for images that are added to a PowerPoint presentation.
Basically, the Picture Effects consist of the following preconfigured formatting styles; transparent shadow, soft edge, reflection, glow, 3-D rotation, metal frame, bevels, perspectives etc.
Answer: Picture Styles gallery
Explanation: He is correct he just typed it wrong.
which ieee standard defines improved encryption for wireless networks, including aes?
Answers
The IEEE standard 802.11i-2004, also known as WPA2 (Wi-Fi Protected Access II), defines improved encryption for wireless networks, including AES (Advanced Encryption Standard).
The WPA2 standard was developed to address the weaknesses in the previous WPA standard. WPA2 uses the CCMP (Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) encryption method, which is based on the AES encryption algorithm, for secure data transmission over wireless networks. This standard provides better security by using longer keys, stronger encryption algorithms, and improved message integrity checks.AES is a symmetric encryption algorithm that provides high-level security, confidentiality, and integrity of data over a wireless network.
AES uses a block cipher to encrypt data, and the length of the key used for encryption can be 128, 192, or 256 bits. The AES algorithm is considered to be secure and is widely used in many applications to protect data, including wireless networks.
To know more about networks visit:
https://brainly.com/question/29350844
#SPJ11
What is the common term used to describe a single computer document?
A.Screenshot
B. Driver
C. File
D. Icon
Answers
Decimal numbers are based on __________.
letters (a and b)
16 digits
10 digits
two digits (1s and 0s)
Answers
I’m not sure.
Answer:
They are based on 10 digits.
Explanation:
I just did the test and got the answer right.
What is the name of the process that basically takes a snapshot of the current security of an organization
Answers
The name of the process that takes a snapshot of the present security of an organization is refereed to as: Vulnerability assessment.
What is Vulnerability Assessment?Vulnerability assessment can be defined as the process whereby risk and vulnerability of computer networks, systems, applications or other part of an IT ecosystem is identified.
Vulnerability assessment, as an important component of vulnerability management, involves providing security teams and stakeholders with necessary information that can aid analysis and prioritizing of risk for proper remediation.
Therefore, the name of the process that takes a snapshot of the present security of an organization is refereed to as: Vulnerability assessment.
Learn more about Vulnerability assessment on:
https://brainly.com/question/25633298
describe the process of stp from implementation to convergence.
Answers
Spanning Tree Protocol (STP) is a networking protocol that was created to prevent network loops in a Layer 2 switched network. STP helps in controlling the flood of traffic in a switched network by organizing the network topology. In this regard, the process of STP from implementation to convergence involves a series of steps as described below:
Step 1: STP Implementation
The first step in the process of STP implementation is to enable STP on all switches in the network. This ensures that all switches can participate in the STP process. After enabling STP on all switches, the switches must then be configured with a unique Bridge ID.
Step 2: Root Bridge Election
The next step is to elect a Root Bridge. The Root Bridge is the most important bridge in the STP topology as it provides the basis for the entire network's logical topology. To elect the Root Bridge, the switches compare their Bridge IDs, with the switch with the lowest Bridge ID being elected as the Root Bridge.
Step 3: Calculating Path Costs
The next step is to calculate the path costs from each switch to the Root Bridge. Path costs are calculated by adding the cost of each link between a switch and the Root Bridge.
Step 4: Determining the STP Topology
Using the Root Bridge and the path costs, STP then determines the topology of the network. STP calculates the shortest path from each switch to the Root Bridge, and blocks any redundant links.
Step 5: STP Convergence
After STP has determined the topology of the network, it then begins to converge. During convergence, switches change their port states until all ports are either in the forwarding or blocking state.
In conclusion, STP is an essential protocol for maintaining a stable and efficient network. By following the above process, STP helps prevent network loops and ensures that traffic flows efficiently throughout the network.
To know more about maintaining visit:
https://brainly.com/question/28341570
#SPJ11
A Career Cluster is a group of related careers true or false
Answers
Answer:
true
Explanation:
there are 16 different types so each cluster is related in some way.
A Career Cluster is a group of related careers or occupations that share common skills, knowledge, and pathways. This statement is true
These clusters are used in career exploration and education to organize and categorize careers based on similarities in the types of work they involve.
Each cluster encompasses a range of careers that share similar attributes and can be connected through similar educational pathways or skill sets.
For example, the STEM (Science, Technology, Engineering, and Mathematics) cluster includes careers such as biologist, software developer, engineer, and mathematician, all related to science and technology fields.
Career Clusters provide a useful framework for students and job seekers to explore and navigate various career options effectively.
Know more about Career Cluster:
https://brainly.com/question/8825832
#SPJ6
, , ,g d,t ,dt m,dt ymtd
Answers
Answer:ummm me confused
Explanation:
What are Apps?
How do we interact with them?
Answers
Answer:
Sliding elements in list format.
Cards.
Images.
Buttons.
Overflow screens.
Multiple selection app interactions.
Text input fields.Explanation:
In the current situation, how do you access information as a student? How will you integrate the use of ICT in your daily life and your chosen track?
Answers
Answer:
Explanation:
As a computer science student information is accessed in every possible way. This can be through a local school lan network, mobile devices, e-mail, etc. All of these help information flow to and from various people and makes obtaining this information incredibly simple as a student. Especially in the field of computer science, I need to integrate as many ICT devices with me in my everyday life, to send emails, check calendar updates, research information on the web, check school reports, and even speak with clients.
Which of the following led to the decline in production of LPs?
quality of LPs
appearance of LPs
cost of LPs
size of LPs
i will mark brainlist
Answers
But SIZE, was major downfall as portable cassette/ boom boxes, CD and mp3, etc became available.
Which two of these should a website’s privacy policy created under California Online Privacy Protection Act describe?
A third parties that may view the information
B name and designation of the author of the policy
C effective date and expiration date of the policy
D links to third-party policies, if any
E approvals necessary to bypass the policy
Answers
Answer:
E approvals necessary to bypass the policy
Questions- Which two of these should a website’s privacy policy created under the California Online Privacy Protection Act describe?
The correct answer is third parties that may view the information.
effective date and expiration date of the policy.
Explanation:

Which of these about non-disclosure agreements is accurate?

Answers
Answer: number 2
Explanation: number 2
Answer: B) Employers often require their employees to sign them.
Non-disclosure agreements (abbreviated NDA) are documents in which the person signing said agreement must keep certain information from being spread. For instance, if a company has a policy or formula they wish to keep secret, then they would require the proper employees working with this aspect to sign NDA's keeping the items secret. NDA's also extend to things like doctor-patient confidentiality, attorney-client privilege's, and so on.
In your own words and in great detail explain the characteristics of the image types listed below. Give an example of when would be best to use each image file type.
1. JPG
2. PNG
3. GIF
4. PDF
5. SVG
Answers
Answer:
JPG It's a standard image format for containing lossy and compressed image data. PNG “Portable Graphics Format”. It is the most frequently used uncompressed raster image format on the internet .GIF is a lossless format for image files that supports both animated and static images. It was the standard for 8-bit color images on the internet until PNG became a viable alternativePDF Portable Document SVG scalable vector graphics, and it is a file format that allows you to display vector images on your website.Explanation:
Despite the huge reduction in fil e size JPEG images maintain reasonable image quality. This lossless data compression format was created to replace the Graphics 2.Interchange Format (GIF) Like GIF images, PNG also have the ability to display transparent backgrounds.You may have seen them used often in email signatures. Animated GIFs are several images or frames combined inUsed to display documents in an electronic form independent of the software, hardware or operating systemThis means that you can scale an SVG image up and down as needed without losing any quality, making it a great choice for responsive web design they are viewed onto a single fileFill in the blank
A colleague excitedly tells you she has created an interface component for SPSS, a statistics software program. She has created a ______.
Answers
Answer:
Software
Explanation:
because softwares are always created to solve a particular problem or challenges
Given the following list, what is the value of ages[5]?ages = [22, 35, 24, 17, 28]221728None: Index errorFlag this QuestionQuestion 21 ptsGiven the following list, what is the value of names[2]?names = ["Lizzy", "Mike", "Joel", "Anne", "Donald Duck"]MikeJoelAnneNone, improper assignment of "Donald Duck" due to space in the nameFlag this QuestionQuestion 31 ptsGiven the following code, what would the list consist of after the second statement?ages = [22, 35, 24, 17, 28]ages.insert(3, 4)ages = [22, 35, 24, 4, 17, 28]ages = [22, 35, 3, 24, 17, 28]ages = [22, 35, 24, 17, 3, 28]ages = [22, 35, 24, 17, 4, 28]Flag this QuestionQuestion 41 ptsThe __________ method adds an item to the end of a list.pop()append()insert()index()Flag this QuestionQuestion 51 ptsThe primary difference between a tuple and a list is that a tuplehas a limited rangeis indexed starting from 1is mutableis immutableFlag this QuestionQuestion 61 ptsTo refer to an item in a list, you code the list name followed byan index number in brackets, starting with the number 1an index number in parentheses, starting with the number 1an index number in brackets, starting with the number 0an index number in parentheses starting with the number 0Flag this QuestionQuestion 71 ptsWhen a function changes the data in a list, the changed listdoes not need to be returned because lists are mutable.is only available within that function.needs to be returned because lists are immutable.does not need to be returned because lists are immutable.Flag this QuestionQuestion 81 ptsWhich of the following is not true about a list of lists?You can use nested for statements to loop through the items in a list of lists.You can refer to an item in an inner list by using two indexes.To delete an item in the outer list, you first have to delete the list in the item.The inner lists and the outer list are mutable.Flag this QuestionQuestion 91 ptsWhich of the following would create a list named numbersconsisting of 3 floating-point items?numbers[1] = 5.3numbers[2] = 4.8numbers[3] = 6.7numbers = [5.3, 4.8, 6.7]numbers = [0] * 3numbers[3] = (5.3, 4.8, 6.7)Flag this QuestionQuestion 101 ptsWhich of the following creates a tuple of six strings?vehicles = ("sedan","SUV","motorcycle","bicycle","hatchback","truck")vehicles = ["sedan","SUV","motorcycle","bicycle","hatchback","truck"]vehicles = (sedan, SUV, motorcycle, bicycle, hatchback, truck)vehicles = "sedan","SUV","motorcycle","bicycle","hatchback","truck"
Answers
vehicles = ("sedan","SUV","motorcycle","bicycle","hatchback","truck")
1. The value of ages[5] is None: Index error, since the list has only 5 elements and the index starts from 0.
2. The value of names[2] is Joel.
3. After the second statement, the list would be: ages = [22, 35, 24, 4, 17, 28].
4. The append() method adds an item to the end of a list.
5. The primary difference between a tuple and a list is that a tuple is immutable.
6. To refer to an item in a list, you code the list name followed by an index number in brackets, starting with the number 0.
7. When a function changes the data in a list, the changed list does not need to be returned because lists are mutable.
8. The statement "To delete an item in the outer list, you first have to delete the list in the item" is not true about a list of lists.
9. To create a list named numbers consisting of 3 floating-point items: numbers = [5.3, 4.8, 6.7].
10. To create a tuple of six strings: vehicles = ("sedan","SUV","motorcycle","bicycle","hatchback","truck").
Learn more about vehicles here:-
https://brainly.com/question/13390217
#SPJ11
5.16 LAB: Output numbers in reverse
Answers
In Excel, which direction does a Row go and does it use letters or numbers to track the cells? A. Vertical and Letters B. Vertical in numbers C. Horizontal and numbers D. Horizontal and Letters
Answers
Answer:
In Excel, a Row goes horizontally and uses numbers to track the cells. (Option D. Horizontal and Numbers)
Which expression is equivalent to 5(s + 6)?
Answers
steps: distribute 5 to s and 6
Write a white paper or PowerPoint presentation demonstrating that you understand the essential elements of a patch
management program. Evaluate at least three patch management software solutions, recommend one, and describe why
you are making this recommendation
Use the list provided in the lesson as your template and search the Internet for information on patch management
concepts and vendor solutions to help create your plan.
Answers
Answer:
When is this due?
Explanation:
I will write it
let ee be the set of even integers and let oo be the set of odd integers. suppose that a computer is programmed to input a sequence of elements of ee and output a sequence of elements of oo according to some rule. you run a test of this program using 12,6,8,10,212,6,8,10,2 as input, and the computer outputs 81,9,25,49,181,9,25,49,1. what rule does the computer appear to be using?
Answers
The rule computer appears to be using is f(n) = (n-3)²
what rule computer is using?EE be the set of even integers
OO be the set of odd integers
we have to form a function f: EE--> OO such that we receive the following result
Domain 12 6 8 10 2 12 6 8 10 2
co-Domain 81 9 25 49 181 9 25 49 1
so, the function is f(n) = (n-3)² where N ∈ OO
So the required rule is f(n) = (n-3)²
Note: Notice the fifth position. There is some mistake. it is not 212, it will be 2 and 12 Separately
f(2) = (2-3)² = (-1)² = 1
f(12) = (12-3)² = 9² = 81
to know more about computers, visit
https://brainly.com/question/24540334
#SPJ4
Select three areas that should be included in a contract consultant’s business expense model.
Answers
Answer:
i dont really know but i tried
Explanation:
Fixed price contracts. With a fixed price contract the buyer (that's you) doesn't take on much risk. ...
Cost-reimbursable contracts. With a cost-reimbursable contract you pay the vendor for the actual cost of the work. ...
Time and materials contracts
An installation is:
please help asap
Answers
Answer: an installation is the act of putting something in, a device that stays in one place, a military base, or an art piece that often involves building and different types of materials.
Explanation:
Getting your new air conditioner put in is an example of an installation.
wants to redesign the user interface. The customer service agents use ________ to enter explicit statement to invoke operations within the system and cannot always remember the commands.
Answers
Answer:
The correct answer to use in filling in the gap is "Command languages interaction".
Explanation:
Command languages interaction occurs when the user enters command which are not always remembered, the computer executes it (with feedback if necessary), then requests next command.
This implies that under command languages interaction, "Command prompts" are employed by users who enter in commands and maybe certain parameters that impact how the command is executed.
Therefore, the correct answer to use in filling in the gap is "Command languages interaction".
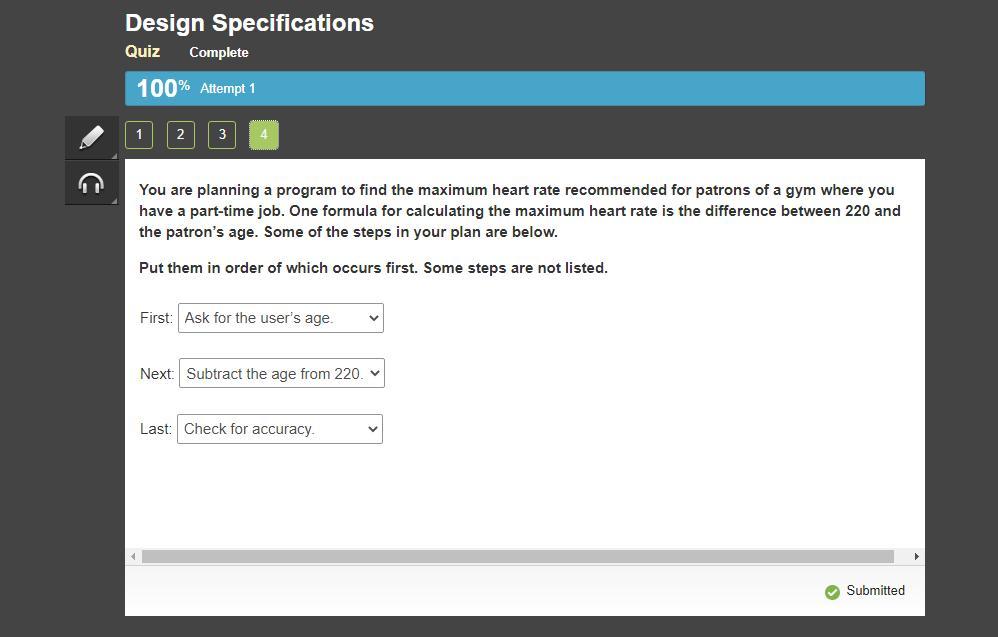
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
a(n) ____ links each page with the pages that follow and precede it.
Answers
linear structure links each page with the pages that follow and precede it.
What tag is employed to specify a link*?
a link that connects two pages together, or a hyperlink. The href attribute, which denotes the location of the link, is the most significant attribute of the element. In all browsers, links will typically show up as follows: An unclicked link is blue and underlined.
Use a relative link if the document you are linking to is located on a different drive. Each page in an augmented structure is connected to the pages that come before and after it.
How do links normally show up in a quizlet in a web browser?Nearly all Web pages contain hyperlinks, allowing visitors to navigate between them by clicking. Text connections are frequently.
To know more about linear structure visit:-
https://brainly.com/question/13898701
#SPJ4
How many different name servers need to be visited in order to find location of www.flamingflamingo.eu including ROOT server
Answers
Answer:
10
Explanation:
Which of the following commands can an administrator run to quickly locate and determine the TTL of the further reachable node? A. route. B. ping. C. traceroute
Answers
An administrator can run the command `traceroute` to quickly locate and determine the TTL of the further reachable node. So the correct option is C. traceroute.
This command is also known as `tracert` on Windows and it is used to track the path of network packets and display them on a map of hops between the client and server. The command provides a list of all the network nodes that packets travel through to get to their destination and shows the time it takes for each hop.Traceroute is commonly used to troubleshoot network problems and to determine the exact location of an issue.
The TTL is the maximum number of hops that a packet can travel before it is discarded. The traceroute command sends packets with increasing TTL values until it reaches the destination, at which point the host returns an ICMP Time Exceeded message that contains the TTL value.
To know more about administrator visit:-
https://brainly.com/question/32491945
#SPJ11
explain whether the information in the microsoft office file properties is reliable for forensic purposes.
Answers
The information found in Microsoft Office file properties may not always be reliable for forensic purposes.
While these properties can provide valuable information such as the file creator, creation and modification dates, and version, they can also be easily manipulated or deleted. In addition, metadata stored in file properties may not be comprehensive and may not capture all actions taken on the file.
Therefore, it is important to supplement the information found in file properties with other forensic techniques and tools to ensure the accuracy and reliability of the evidence collected.
You can learn more about Microsoft Office at: brainly.com/question/14984556
#SPJ11
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
b. false
Answers
Answer:
A threat vector is an item of code on a distributed device that reports the condition of the device to a central server.
a. true
It is true that a threat vector is an item of code on a distributed device that reports the condition of the device to a central server. The correct option is a.
What is a threat vector?The total number of attack vectors that an attacker can use to manipulate a network or computer system or extract data is referred to as the attack surface.
Threat vector and attack vector are interchangeable terms that describe the various ways a hacker can gain access to data or other confidential information.
The methods used by adversaries to breach or infiltrate your network are referred to as attack vectors.
Malware and ransomware, as well as man-in-the-middle attacks, compromised credentials, and phishing, are all examples of attack vectors.
A threat vector is a piece of code on a distributed device that reports the device's status to a central server.
Thus, the correct option is a.
For more details regarding a threat vector, visit:
https://brainly.com/question/28558110
#SPJ2