You are in charge of installing a remote access solution for your network. You decide you need a total of four remote access servers to service all remote clients. Because remote clients might connect to any of the four servers, you decide that each remote access server must enforce the exact same policies. You anticipate that the policies will change frequently. What should you do?
Answers
Configure one of the remote access servers as a RADIUS server and all other servers as RADIUS clients and configure network access policies on the RADIUS server.
Any Internet-connected device that can run the Remote Desktop Connection (RDC) client can be used to connect to resources on an internal or private network via the Remote Desktop Gateway, also known as RD Gateway.
To launch the Routing and Remote Access Server Setup Wizard, right-click the server and select Configure and Enable Routing and Remote Access. Choose Next. To allow remote computers to dial into or connect to this network through the Internet, choose Remote access (dial-up or VPN).
Learn more about Remote Access, here;
https://brainly.com/question/29850968
#SPJ4
Related Questions
Once a business determines that change needs to occur, what ahould the
business create?
A. Business operation
B. Business analysis
C. Business model
D. Business strategy
Answers
Answer:
D. Business strategy
Explanation:
Kono Dio Da!!
how are areas of low pressure created?
Answers
Answer:
A low pressure area usually begins to form as air from two regions collides and is forced upward.
Add to brainliest please
1. Write a String constant that is the empty string .
2. Assume that message is a String variable . Write a statement to display its value on standard output .
3.Given a String variable word , write a String expression that parenthesizes the value of word . So, if word contains "sadly", the value of the expression would be the String "(sadly)"
Answers
1. Code String constant that is the empty string="";*************************** 2. A statement on standard output is System.out.println(message) 3. String expression that parenthesizes the value of word is "("+word+")".
What does Java's string class do?Character strings are represented by the String class. Java applications implement all string literals as instances of this class, including "abc." Strings are immutable; once they are generated, their values cannot be altered. Mutable strings are supported via string buffers.
What is a string's function in Java?In Java, a string is an object that represents different character values. Each letter in the string is represented by a unique character value in the Java string object. Java uses the char class to represent characters. A user-entered array of char values will have the same significance as a string.
To know more about String visit-
brainly.com/question/13262184
#SPJ4
Code String constant "";***************************; the empty string 2. The usual output statement is System.out.println(message). 3. The string expression "("+word+")" parenthesizes the value of the word.
The String class represents character strings. Java programs implement this class as an instance for each string literal, including "abc." Strings are immutable; their values cannot be changed after they have been formed. String buffers can handle mutable strings.
A string is an object that represents various character values in Java. The Java string object's representation of each letter in the string uses a different character value. The char class is used by Java to represent characters. An array of char values supplied by the user will have the same importance as a string.
Learn more about Java string here:
https://brainly.com/question/13262184
#SPJ6
you manage a network with two locations (portland and seattle). both locations are connected to the internet. the computers in both locations are configured to use ipv6. you'd like to implement an ipv6 solution to meet the following requirements: hosts in each location should be able to use ipv6 to communicate with hosts in the other location through the ipv4 internet. you want to use a site-to-site tunneling method instead of a host-to-host tunneling method. which ipv6 solution should you use? answer isatap 4to6 tunneling 6to4 tunneling teredo tunneling
Answers
In this situation, 6to4 tunnelling is the appropriate IPv6 approach. Site-to-site tunnelling is possible with 6to4 tunnelling, which may be used to link IPv6 networks via an IPv4 infrastructure.
Using 6to4 tunnelling, it is feasible to connect IPv6 networks over an IPv4 infrastructure and perform site-to-site tunnelling. In order to allow IPv6 hosts to interact across an IPv4 network, it works by enclosing IPv6 packets inside IPv4 packets. The best IPv6 solution in this scenario is 6to4 tunnelling. Using 6to4 tunnelling, it is feasible to connect IPv6 networks over an IPv4 infrastructure and perform site-to-site tunnelling. ISATAP or Teredo tunnelling are two options for host-to-host communication over the IPv4 internet. 6to4 tunnelling is the best choice in this scenario because it fits the requirement of allowing hosts in one area to communicate with hosts in the other location over the IPv4 internet.
learn more about IPv6 here:
https://brainly.com/question/15733937
#SPJ4
hash function takes a string of any length as input and produces a fixed length string which acts as a kind of signature for the data provided.
t
f
Answers
It is true to state that hash function takes a string of any length as input and produces a fixed length string which acts as a kind of signature for the data provided.
How is this so?A hash function is a mathematical algorithm that takes an input of any length, such as a string, and produces a fixed-length string of characters called a hash value or hash code.
This hash value acts as a unique identifier or signature for the input data. It is used in various applications, including data integrity checks, password storage, and digital signatures,where the fixed-length hash provides a concise representation of the input data.
Learn more about hash function at:
https://brainly.com/question/13164741
#SPJ4
6. When working with a file,
__________ the blades in a vise or against a solid surface such as a work bench to
avoid injury and ensure an even stroke.
Answers
Answer:
When working with a file, stabilize the blade in a vis or against a solid surface such as a work bench to avoid injury and to ensure an even stroke
Explanation:
The file can be used to sharpen a blade to increase the effectiveness of the blade. In order to properly sharpen a file in a safe manner, the blades to be sharpen, which ae usually relatively flexible as compared to the file, should be made stable during the repetitive forward and backward notion of the file, for safety, to avoid being injured by the recoil of the blade, and also to ensure that the stroke is evenly applied to the blade.
Which term describes a VPN created between two individual hosts across a local or intermediary network?VPN applianceHost-to-host VPNHashSite-to-site VPN
Answers
A Host-to-host VPN describes a virtual private network created between two individual hosts across a local or intermediary network.
So, the correct answer is A.
This type of VPN allows secure communication between the two hosts by establishing a direct, encrypted connection. Unlike a site-to-site VPN, which connects entire networks together, a host-to-host VPN focuses specifically on connecting the two individual devices.
VPN appliances are hardware devices that facilitate VPN connections, while a hash is a cryptographic function used to ensure data integrity and security. In summary, a host-to-host VPN provides a secure communication channel between two individual hosts on a network
Hence, the answer of the question is A.
Learn more about VPN at https://brainly.com/question/32241371
#SPJ11
rotate object while holding the shift key. what does it do?
Answers
Answer:
It rotates it 45 degrees in a direction
construction companies use specialized technicians to do which step in the maintenance prosses
Answers
Construction companies use specialized technicians to perform the step of maintenance known as repairs and troubleshooting.
These technicians are skilled professionals who possess expertise in diagnosing and fixing issues in various construction systems, equipment, and structures. They play a crucial role in ensuring that maintenance activities are carried out effectively and efficiently.
These technicians are trained to identify and rectify problems related to electrical systems, plumbing, HVAC (heating, ventilation, and air conditioning), structural integrity, and other construction-related components. They use specialized tools, equipment, and techniques to diagnose and repair faults, perform routine maintenance tasks, and ensure the smooth operation of construction projects.
Their expertise and technical knowledge enable them to troubleshoot issues, identify potential hazards, and implement necessary repairs or replacements. By employing specialized technicians, construction companies can maintain the functionality, safety, and longevity of their projects, minimizing downtime and ensuring optimal performance.
Learn more about troubleshooting here:
https://brainly.com/question/29736842
#SPJ11
Most wires are covered in rubber to insulate them and keep people safe from electricity and heat true of false
Answers
Answer:
I think it is true...
Explanation:
Hope its right
En la historia del Computador porque se caracteriza la primera generación? *
1 punto
a.Por que se reemplazo el ábaco
b.ninguna de las anteriores
c.Por la implementación del calculo
d.Por el uso de tubos de vacío
Answers
D. Por el uso de tubos de vacio.
hy does payments constitute such a large fraction of the FinTech industry? (b) Many FinTech firms have succeeded by providing financial services with superior user interfaces than the software provided by incumbents. Why has this strategy worked so well? (c) What factors would you consider when determining whether an area of FinTech is likely to tend towards uncompetitive market structures, such as monopoly or oligopoly?
Answers
(a) lengthy and complex processes for making payments (b) legacy systems and complex interfaces (c) regulatory requirements and substantial initial investment, can limit competition
(a) Payments constitute a significant portion of the FinTech industry due to several factors. First, traditional banking systems often involve lengthy and complex processes for making payments, leading to inefficiencies and higher costs. FinTech firms leverage technology and innovative solutions to streamline payment processes, providing faster, more secure, and convenient payment options to individuals and businesses. Additionally, the rise of e-commerce and digital transactions has increased the demand for digital payment solutions, creating a fertile ground for FinTech companies to cater to this growing market. The ability to offer competitive pricing, improved accessibility, and enhanced user experience has further fueled the growth of FinTech payment solutions.
(b) FinTech firms have succeeded by providing financial services with superior user interfaces compared to incumbents for several reasons. Firstly, traditional financial institutions often have legacy systems and complex interfaces that can be challenging for users to navigate. FinTech companies capitalize on this opportunity by designing user-friendly interfaces that are intuitive, visually appealing, and provide a seamless user experience. By prioritizing simplicity, convenience, and accessibility, FinTech firms attract and retain customers who value efficiency and ease of use. Moreover, FinTech companies leverage technological advancements such as mobile applications and digital platforms, allowing users to access financial services anytime, anywhere, further enhancing the user experience.
(c) Several factors contribute to the likelihood of an area of FinTech tending towards uncompetitive market structures such as monopoly or oligopoly. Firstly, high barriers to entry, including regulatory requirements and substantial initial investment, can limit competition, allowing a few dominant players to establish market control. Additionally, network effects play a significant role, where the value of a FinTech service increases as more users adopt it, creating a competitive advantage for early entrants and making it challenging for new players to gain traction. Moreover, data access and control can also contribute to market concentration, as companies with vast amounts of user data can leverage it to improve their services and create barriers for potential competitors. Lastly, the presence of strong brand recognition and customer loyalty towards established FinTech firms can further solidify their market position, making it difficult for new entrants to gain market share.
To learn more about technology click here: brainly.com/question/9171028
#SPJ11
Please answer quick:))))

Answers
Given the table of C Code Statements, variable names and variable values, determine
the variable values after each code statement is executed.
*Image is below*
Thank you!!

Answers
The variable values after each code statement is executed goe the num1 is -2 and num2 is 1.25.
How variables are declared in C deliver an example?You will use the key-word extern to claim a variable at any place. Though you could claim a variable a couple of instances on your C program, it may be described most effective as soon as in a file, a function, or a block of code.
The = image is referred to as the undertaking operator. It is likewise viable to claim a variable and assign it a fee withinside the equal line, so in place of int i after which i = 9 you could write int i = 9 multi functional go. If you've got got multiple variable of the equal kind you could additionally claim them collectively e.g.
Read morea bout the Code :
https://brainly.com/question/4514135
#SPJ1
What are slicers used for?
O checking the accuracy of data
O accurately charting data
O adding data to a table
O quickly filtering data
Answers
Answer:
D: Quickly Filtering Data
Explanation:
Slicers are a feature in Microsoft Excel and Power BI used for filtering and segmenting data in a pivot table. They allow users to quickly filter and view a subset of data by selecting one or more items from a list, without having to manually create complex filter criteria. Slicers are used to quickly filter data and segment it by specific fields or dimensions. They do not check the accuracy of data, accurately charting data or adding data to a table.
Answer:
D) Quickly Filtering Data
Explanation:
got it right on edge
Witch icon allows you to see paragraph formatting feature
Answers
I need help I’m behind

Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
You use a really long cable to connect the desktop computer in your bedroom to the router on the other side of your house. Which of these may be a problem?
IP/MAC confusionLack of input deviceAttenuationAdaptationThe correct answer to this question is Attenuation.
Attenuation is the loss of signal strength in networking cables or connections. This may occur when the cable is spread over a long distance. Attenuation is typically measured in (dB) decibels or voltage and can occur due to a variety of factors. Attenuation occurs in the cable when there is a reduction in power of the light signal as it is transmitted.
Other options are not correct because IP/MAC confusion will not occur due to long-distance cable. Lack of input device may not create the problem and adaptation also.
Write a definition in your own words for intranet. Please don't copy and paste.
Answers
Answer:
An Intranet is a communication network, usually, a private network that was created using the World Wide Web software.
Explanation:
An Intranet is an private Network based on internet standards but only available within a business or other organizations.
Thinking about the operations needed in these games, which game is likely to be one of the oldest games in the world?
tag
dice throwing
jump-rope
tic-tac-toe
Answers
Answer:
Most likely tag because it doesn't require anything except legs and running had been around since like forever
Explanation:
Does each box at the fruit stand contain a different fruit?
In [164]:
# Set all_different to "Yes" if each box contains a different fruit or to "No" if multiple boxes contain the same
fruit all_different = "No" all_different
Out[164]: 'No' In [165]: _
= ok.grade('q6_3')
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Running tests
Answers
Answer:
yes
Explanation:
The value of the variable all_different is: all_different = No
Complete questionDoes each box at the fruit stand contain a different fruit? Set all_different to True if each box contains a different fruit or to False if multiple boxes contain the same fruit.
Hint: You don't have to write code to calculate the True/False value for all_different. Just look at the inventory table and assign all_different to either True or False according to what you can see from the table in answering the question.
box ID fruit name count
53686 kiwi 45
57181 strawberry 123
25274 apple 20
48800 orange 35
26187 strawberry 255
57930 grape 517
52357 strawberry 102
43566 peach 40
all_different = ...
How to determine the true statement?From the hint given, we can see that writing a code is not necessary.
All we need to do is to scan through the table.
From the given table, we can see that there are several fruits on the table.
These include peach, kiwi, grape, strawberry, etc.
Since the fruits are different, then the value of the variable all_different is:
all_different = No
Read more about boolean variables at:
https://brainly.com/question/18089222
#SPJ2
1-the principle of recycling applies only to open systems
True/False
2-It is important that measurements be consistent in engineering because
A-There is only one established system of measurement available
B-there is one unit that is used to measure weight, length and distance
C-engineers often work together internationally and replicate each others' results
Answers
Answer:
The answer to this question can be described as follows:
In question 1, the answer is False.
In question 2, Option C is correct.
Explanation:
Recycling seems to be the concept of organizing life by making use of as little resources as possible. The recycling approach enables us to live and reconstruct in modules that are closed, it use everywhere not only in the open system. Measurements must be accurate in engineering because engineers often operate independently globally and repeat the findings of one another.It can be said that the lowest two layers of the OSI operate somewhat like Morse code.
Select the correct answer.
O False
0 True
Answers
Answer:
o
Explanation:
because of the different function in the computer
Which one of these 3 Apple products is the best one?

Answers
Answer:
First one
Explanation:
Because it is expensive
I need some help with this project. The picture of the assignment is above

Answers
Answer:
sorry
Explanation:
you need to do this on your own Wahhabi
but if you sub to my you-tube channel at chris got ha,x i will help you out
1. Select and open an appropriate software program for searching the Internet. Write the name of the program.
Answers
An appropriate software program for searching the Internet is known as Web browser.
What is the software that lets you search?A browser is known to be any system software that gives room for a person or computer user to look for and see information on the Internet.
Note that through the use of this browser, one can easily look up information and get result immediately for any kind of project work.
Learn more about software program from
https://brainly.com/question/1538272
What is the most popular example of specialized software for managing projects?.
Answers
The most popular example of specialized software for managing projects is Microsoft Project.
Specialized software is a software that caters to the specific needs of a specific field.
Microsoft Project is a project management software program designed, developed, and marketed by Microsoft. It assists project managers in creating plans, assigning resources to tasks, tracking progress, managing budgets, and analyzing workloads. It is also helpful in resource management, cost estimation, and communication. Project managers can use Microsoft Project software to break their projects down into different tasks, assign them to team members, and set deadlines for the same.
Therefore, the most popular example of specialized software for managing projects is Microsoft Project.
Learn more about Microsoft Project:
https://brainly.com/question/30086361
#SPJ11
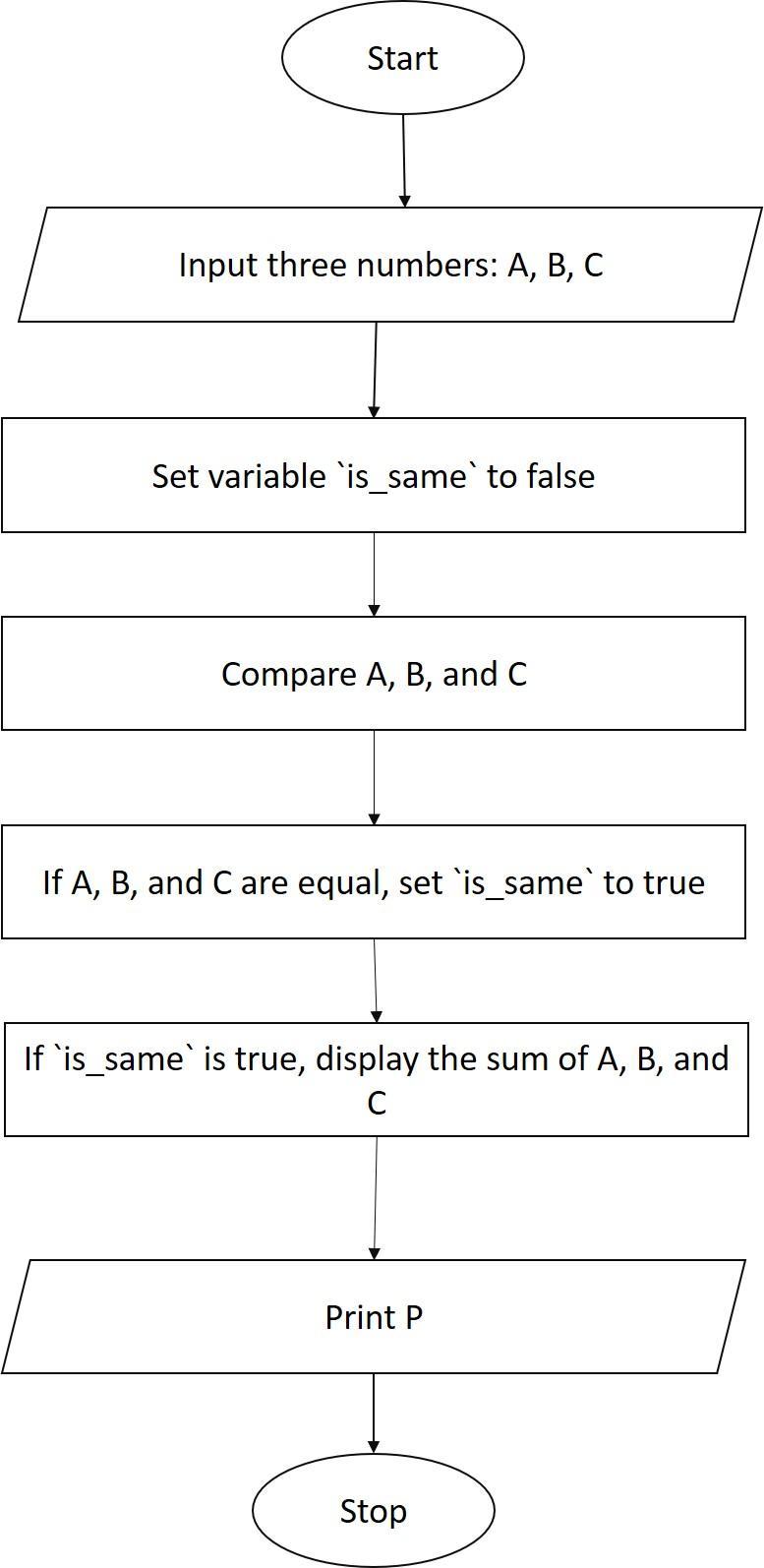
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
Sarah is working in Scratch and trying to access the code editor. What does Sarah need to click on in order to do this?
A.
the Code tab at the bottom right of the screen
B.
the Code tab at the top right of the screen
C.
the Code tab at the bottom left of the screen
D.
the Code tab at the top left of the screen
Answers
Answer: the Code tab at the bottom right of the screen
Explanation: Already did this and got it right !
Discuss, in your own words, the topic of cybersecurity management for both individuals and business. Briefly talk about the different threats, and then explain what cybersecurity management is, and what it could do against each common type of threat.
Answers
Cybersecurity management protects individuals and businesses from threats.
How does cybersecurity management safeguard individuals and businesses?Cybersecurity management is essential for both individuals and businesses to protect themselves from the ever-increasing threats in the digital landscape. In today's interconnected world, individuals face various cybersecurity risks, such as malware, phishing attacks, identity theft, and data breaches.
Similarly, businesses are vulnerable to targeted attacks, ransomware, insider threats, and intellectual property theft.
Cybersecurity management involves implementing proactive measures to prevent and mitigate these threats. It includes the use of robust security tools, regular software updates, strong passwords, and user awareness training.
Additionally, businesses should employ network monitoring, intrusion detection systems, and incident response plans to detect and respond to any security breaches promptly.
How cybersecurity management works by adopting a layered defense approach, combining technology, policies, and employee awareness. A comprehensive strategy should include firewalls, antivirus software, encryption, multi-factor authentication, and regular data backups.
It is crucial to continually assess and update security measures to stay ahead of evolving threats and ensure a secure digital environment.
Learn more about Cybersecurity
brainly.com/question/30902483
#SPJ11
After saving the changes she made, Sally notices that she used the word "home” too many times in her paragraph. She decides to make her paragraph more interesting by replacing "home” with "shelter” in a few places in the paragraph. How should Sally accomplish this task?
Answers
Answer:
c or a there both correct
Explanation: