Write, compile and test (show your test runs!) program that calculates and returns the fourth root of the number 81, which is 3. Your program should make use of the sqrt() method. Math.sqrt(number).
Answers
Answer:
I am writing a JAVA program. Let me know if you want the program in some other programming language.
public class FourthRoot{ //class to calculate fourth root of 81
public static void main(String[] args) { //start of main() function body
double square_root; //declares to hold the fourth root of 81
double number=81; // number is assigned the value 81
/* calculates the fourth root of number using sqrt() method twice which means sqrt() of sqrt(). This is equivalent to pow(number,(0.25)) where pow is power function that computes the fourth root by raising the number 81 to the power of 0.25 which is 1/4 */
square_root=Math.sqrt(Math.sqrt(number));
//displays the fourth root of 81 i.e. 3
System.out.println("Fourth Root of 81 is "+ square_root); } }
Explanation:
The program is well explained in the comments given along with each statement of the program . Since it was the requirement of the program to user Math.sqrt() method so the fourth root of number= 81 is computed by taking the sqrt() of 81 twice which results in the fourth root of 81 which is 3.
So the first sqrt(81) is 9 and then the sqrt() of the result is taken again to get the fourth root of 81. So sqrt(9) gives 3. So the result of these two computations is stored in square_root variable and the last print statement displays this value of square_root i.e. the fourth root of number=81 which is 3.
Another way to implement the program is to first take sqrt(81) and store the result in a variable i.e. square_root. After this, again take the sqrt() of the result previously computed and display the final result.
public class FourthRoot{
public static void main(String[] args) {
double square_root;
double number=81;
square_root=Math.sqrt(number);
System.out.println("Fourth Root of 81 is: "+ Math.sqrt(square_root)); } }
The program along with its output is attached in a screenshot.
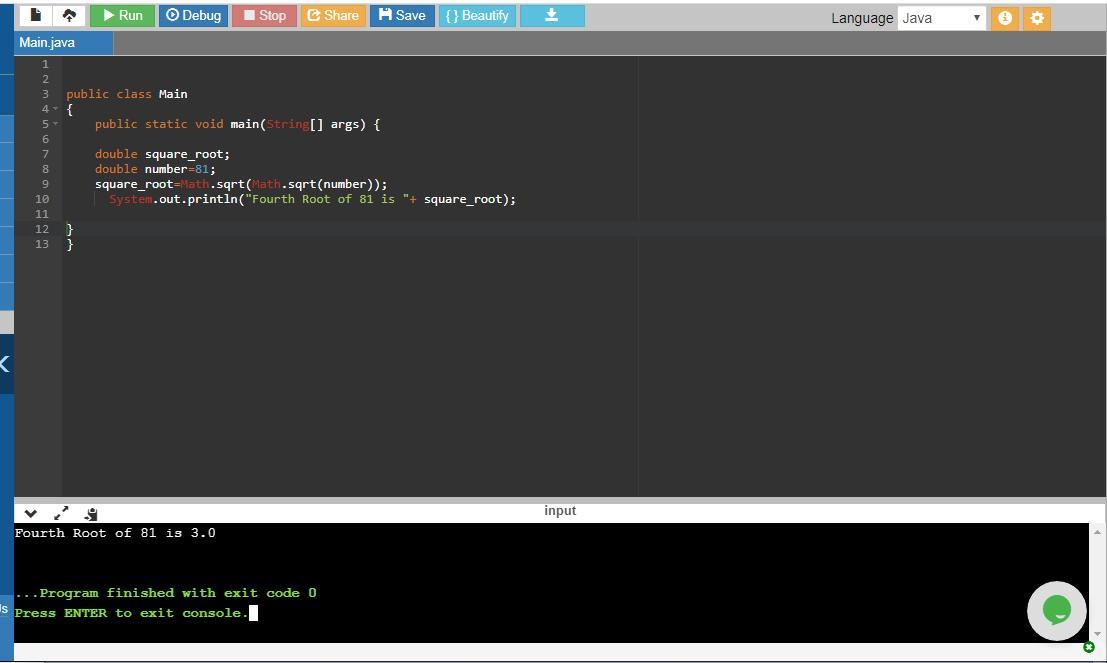
Related Questions
_ is unsolicited junk mail. It can overcrowd your mailbox and deliver malware.
PLEASE HELP ASAP!!
Answers
Answer:
Spam
Explanation:
Spam has been a long term issue with technology, it is unsolicited and can overfill your mailbox. It is called spam because you receive much of it.
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

How to edit the copied formula and return to value in the 3rd column
Answers
To edit the copied formula and return to value in the 3rd column, the process is given below:
What is formula?Formulas are mathematical expressions used to calculate values or make predictions. They are typically composed of mathematical symbols, such as numbers, variables, and operators, and can be used to solve equations or model complex systems. Formulas can be used for a variety of applications, such as predicting the outcomes of experiments, determining the cost of products, or analyzing the relationships between variables. Many formulas are based on the laws of physics, and can be used to describe the behavior of physical phenomena, such as motion or electrical current. Formulas can also be used to analyze data and draw conclusions about trends and relationships.
1. Select the cell containing the formula.
2. Right-click on the cell and select "Edit Formula" from the menu that appears.
3. Edit the formula as desired.
4. Press Enter to calculate the new value and return it to the 3rd column.
To learn more about formula
https://brainly.com/question/29605414
#SPJ1
An array of integers can be assigned to a memory address in the ...
An array of integers can be assigned to a memory address in the .datanumbers
section of a MIPS assembly language program as show below. Here the length of the array is stored first, and then the elements of the array next.
Implement a MIPS assembly language program to perform the functionality of the following C program and print the updated array content, by listing each integer in it.
It should ask a user to enter three integers, a starting index, an ending index, and an integer to use for a comparison. It should examine only the elements in the array located from the entered starting index, to the entered ending index to check if each of them is greater the last entered integer, then if it is, subtract 3*the last entered integer to each such element in the array.
For instance, if a user enters 2, enters 9, then enters 3, then the output will be the following:
45
-6
14
-7
6
-17
2
-4
14
-26
2
19
i.e., the numbers that are located between the index 2 and 9 are examined to see if each of them is greater than the last entered number (3 in this case),
then each of such element is subtracted with 3 times that number (3 in this case) if it is.
If the entered ending index is larger than 11, then the program should exam elements in the array until the end, and if the entered starting index is less than 0, then it should start examining elements from the first one in the array.
.data
numbers_len: .word 12
numbers: .word 45, -6, 23, -7, 15, -17, 11, -4, 23, -26, 2, 19}
The following shows how it looks like in a C program:
int numbers[12] = {45, -6, 23, -7, 15, -17, 11, -4, 23, -26, 2, 19};
int startIndex, endIndex, num1;
int j;
printf("Enter a starting index:n");
//read an integer from a user input and store it in startIndex
scanf("%d", &startIndex);
printf("Enter an ending index:n");
//read an integer from a user input and store it in endIndex
scanf("%d", &endIndex);
printf("Enter an integer:n");
//read an integer from a user input and store it in num1
scanf("%d", &num1);
if (startIndex < 0)
startIndex = 0;
for (j = startIndex; j <= endIndex && j < 12; j = j+1)
{
if (numbers[j] > num1)
{
numbers[j] = numbers[j] - (3 * num1);
}
}
printf("Result Array Content:n");
for (j = 0; j < 12; j = j+1)
{
printf("%dn", numbers[j]);
}
The following is a sample output (user input is in bold):
Enter a starting index:
2
Enter an ending index:
9
Enter an integer:
3
Result Array Content:
45
-6
14
-7
6
-17
2
-4
14
-26
2
19
Please make sure it can output like the sample above
Answers
Answer:
A :)
Explanation:
when should you stop where you are, drop to the
cover your face with your hands, and roll over and over?
A
if you burn a stump
B
if your clothes catch fire
if you draw a cool bath
if your top layer of skin is damaged
Answers
Answer:
A . if you burn a stump because if u roll over the fire will have a 90% chance of going out
With clear examples, describe how artificial intelligence is applied in fraud detection
Answers
Answer:
AI can be used to reject credit transactions or flag them for review. Like at Walmart
Explanation:
I work with AI, i know what i'm talking about.
How many clients has
Accenture engaged globally on blockchain?
Answers
- blockchain network technology by Accenture creates a database and allows the different organizations to access it in real-time without privacy issues
- For this Blockchain project, Accenture has employed 3,84,000 people approximately all over the world.
- The motto of Accenture’s Blockchain project is “Enable and empower multiparty systems to accelerate transformation”
help pls asaap why do teens spend to much time on electronics
Answers
Answer:
Becuase we want to cause it fun and because of classes
Explanation:
A digital pen is an example of what type of device used in the information processing cycle ?
Answers
Answer:
Input is the answer
Answer:
im pretty sure its input..
Explanation:
which native Windows application allows you to access basic PC settings and controls such as system information, controlling user accounts, and unnistalling programs
Answers
The native Windows application that allows you to access basic PC settings and controls such as system information, controlling user accounts, and uninstalling programs is the "Control Panel."
What is the Control PanelThe Control Panel provides a centralized location for managing various aspects of your Windows computer, including hardware and software settings, user accounts, security settings, and more.
It allows you to customize and configure your system according to your preferences and needs.
Read more on Control Panel here https://brainly.com/question/1445737
#SPJ1
What don’t colleges consider when deciding whether to accept you as a student?
Answers
Awnser: Your skills, compatibilities, grades in highschool, and criminal record would most likely be a helping key for deciding who will be accepted into the college.
(This is a guess, and could completely have been wrong, concluding that I have never been in a college.)
Encircle the ANIMALS WHICH DONOT BELONG TO THE GROUP

Answers
Answer:
Get lost kid..............................................................
Explanation:
An e-commerce company is collaborating with our artisans from all over the world to sell the artisans products. Accenture is helping the client build a platform that will maintain the integrity of the artisans credentials by creating digital identities for them. This creates a privacy preserving link between the products and the artisans unique identities. How will these digital identities help these artisans?
Answers
The given digital identities help these artisans by individually recognizing and rewarding them for using methods and materials that align with buyers’ values such as sustainability and labor practices.
What is the collaboration of e-commerce companies?The collaboration of e-commerce companies typically describes electronically enabled business interactions among an enterprise's internal personnel, business partners, and customers throughout a trading community.
The strategy of collaboration in the business allows exchanging of information, such as inventory and product specifications, using the web as an intermediary. Fast food companies may pair up with food delivery services as a form of C-commerce.
By collaborating, companies can become more profitable and competitive by reaching a broader audience.
To learn more about E-commerce, refer to the link:
https://brainly.com/question/23369154
#SPJ1
Keisha has a worksheet with a range of cells using the following columns: Name, Score, Group, Study Group, and Date. Keisha needs to sort the worksheet on the Date field. Which option should she use to most efficiently complete this task?
A: Use the Cut and Paste option to reorganize the data to fit that order.
B: Use the Filter function to organize the data based on the date.
C: Use the Order function to organize the data based on the date.
D: Use the Sort function to organize the data based on date order.
Answers
Answer:
The answer is
d. Use the Sort function to organize the data based on date order.
Explanation:
Most accurate one.
The option that she should use to most efficiently complete this task is to use the Sort function to organize the data based on date order. The correct option is D.
What is a worksheet?It is "a piece of paper used to record work schedules, working hours, special instructions, etc. a sheet of paper used to jot down problems, ideas, or the like in draft form." A worksheet used in education could have questions for pupils and spaces for them to record their responses.
A single spreadsheet called an Excel Worksheet is made up of cells arranged in rows and columns. A worksheet always starts in row 1 and column A. A formula, text, or number can be entered into each cell. Additionally, a cell can point to a different cell on the same worksheet, in the same workbook, or in a different workbook.
Therefore, the correct option is D. Use the Sort function to organize the data based on date order.
To learn more about the worksheet, refer to the link:
https://brainly.com/question/1024247
#SPJ6
The
tests the ability of a networking technician to install,
maintain, troubleshoot, and support a network, and understand various aspects of
networking technologies, including TCP/IP and the OSI models.
COMPTIA NETWORK+
COMPTIA A+
COMPTIA ACCESS
COMPTIA A+
Answers
The COMPTIA NETWORK+ tests the ability of a networking technician to install, maintain, troubleshoot, and support a network, and understand various aspects of networking technologies, including TCP/IP and the OSI models.
Who is a Network Technician?This refers to a person that oversees a network to check and control the vulnerabilities in it.
Hence, we can see that The COMPTIA NETWORK+ tests the ability of a networking technician to install, maintain, troubleshoot, and support a network, and understand various aspects of networking technologies.
Read more about network certifications here:
https://brainly.com/question/14472075
#SPJ1
Answer:compita network+
Explanation:I just did it and got it right big w
An internet filter is firewall software used to block a users access to specific internet content. An internet filter can be installed on which three of the following
Answers
An internet filter can be installed on a variety of devices, including:Computers: Internet filters can be installed on individual computers, whether they are desktops, laptops, or tablets.
This allows users to control their own access to certain websites or types of content.Routers: Some routers have built-in internet filtering capabilities, which allow network administrators to control access to specific websites or types of content for all devices connected to the network.Mobile devices: Internet filters can also be installed on smartphones and other mobile devices, which can be particularly useful for parents who want to restrict their children's access to certain types of content while using their mobile devices. internet filters can be installed on a range of devices, depending on the specific needs of the user or organization. By blocking access to certain websites or types of content, internet filters can help to protect users from harmful or inappropriate content, and promote responsible internet use.
To learn more about laptops click the link below:
brainly.com/question/30551024
#SPJ1
Which of the following is the best example of a purpose of e-mail?
rapidly create and track project schedules of employees in different locations
easily provide printed documents to multiple people in one location
quickly share information with multiple recipients in several locations
O privately communicate with select participants at a single, common location
Answers
Answer:
The best example of a purpose of email among the options provided is: quickly share information with multiple recipients in several locations.
While each option serves a specific purpose, the ability to quickly share information with multiple recipients in different locations is one of the primary and most commonly used functions of email. Email allows for efficient communication, ensuring that information can be disseminated to multiple individuals simultaneously, regardless of their physical location. It eliminates the need for physical copies or face-to-face interactions, making it an effective tool for communication across distances.
Explanation:
1.2.1 Write the design brief. Write the design brief: Remember to analyse the problem first: consider the following points; what is the problem, when and how often does it occur? where does it occur? why does it cause a problem? Who does it affect? where will the product be used? will it be safe to use?
Answers
Answer:
The design brief is to create a product that solves a specific problem. The problem is that people are having difficulty carrying items while walking or running. This problem occurs frequently and affects people of all ages. The product should be lightweight, portable, and safe to use. It should be able to be used in multiple environments, such as on the street, in the park, and in the home. The product should also be able to carry items weighing up to 10kg. It should be able to be used in any weather conditions, and should be ergonomically designed for comfort and ease of use. Finally, the product should be aesthetically pleasing and made with durable materials.
A size of a jumbo candy bar with rectangular shape is l x w x h. Due to rising costs of cocoa, the volume of the candy bar is to be reduced by p%.
To accomplish this, the management decided to keep the height of the candy bar the same, and reduce the length and width by the same amount.
For example, if l = 12, w = 7, h = 3, and p = 10, then the new dimension of the candy bar is 11.39 x 6.64 x 3.
Below is an example of how the completed program should work:
Enter the length, width, and height of the candy bar separated by space(s): 12 7 3
Enter the amount of the reduced volume as a percentage: 10
The new dimensions of the candy bar is: 11.38 x 6.64 x 3.00
Format your output with setprecision(2) to ensure the proper number of decimals for testing!
Answers
Question
A size of a jumbo candy bar with rectangular shape is l x w x h. Due to rising costs of cocoa, the volume of the candy bar is to be reduced by p%.
To accomplish this, the management decided to keep the height of the candy bar the same, and reduce the length and width by the same amount.
For example, if l = 12, w = 7, h = 3, and p = 10, then the new dimension of the candy bar is 11.39 x 6.64 x 3.
Below is an example of how the completed program should work:
Enter the length, width, and height of the candy bar separated by space(s): 12 7 3
Enter the amount of the reduced volume as a percentage: 10
The new dimensions of the candy bar is: 11.38 x 6.64 x 3.00
Format your output with setprecision(2) to ensure the proper number of decimals for testing!
WORTH 75 POINTS!!
Which best describes the video encoding process?
converting analog video into digital video
filming a video at 30 frames per second
saving a digital video in a specific file format
watching a video while the file downloads
Answers
Answer:
To watch a digital video, you must use the codec that was used to encode the video file. Most videos are compressed.
Answer:
Why is compression important for video streaming?
to increase the number of frames per second so that motion appears smooth
to watch video without waiting for it to download(this one)
to improve image quality
to increase file size
Explanation:
how have computer affected banks
Answers
Answer:
people no longer have to visit the bank inorder for them to do tgeir banking.
Explanation:
they now do it online
What are the different options in a page layout feature ? Select three options
Answers
Answer:
Half Center Right Left, theres four
Explanation:
Prepare a document to list down at least 10 features/operations (on process and thread) you can do using Process Explorer.
Answers
Answer:
The operations that can be carried out using process explorer include but are not limited to:
Explanation:
Killing a Process TreeEnding or terminating a processSuspending a processExamining which process has locked a fileManually detecting a virusUnhiding a process. This can help to callup the window for a process that is not visible under normal explorer activitiesMonitor CPU usage setting the priority of a processchanging a service process's access securityMonitoring Graphics Processing Unit
Cheers
A PC that is communicating with a web server has a TCP window size of 6,000 bytes when sending data and a packet size of 1,500 bytes. Which byte of information will the web server acknowledge after it has received two packets of data from the PC
Answers
Answer: 3001.
Explanation:
The Server would acknowledge the 3001 information after it receives two packets of data from the personal computer, which is being used to communicate with the web server of the TCP (Transmission Control Protocol) with a window of 6000.
A TCP is the defined standard which is used for establishing and maintaining a network conversation. this is a medium from which applications programs exchange data.
The TCP is explicitly called the Transmission Control Protocol which allows computing devices to communicate and exchange information by sending packets over a network. Hence, the byte of information acknowledged after receiving 2 packets of data is 3001.
Size perpacket data = 1500 bytes Number of packets sent = 2The bytes of information acknowledged by the web server can be calculated thus :
Size per packet data sent × number of packets 1500 × 2 = 3000Therefore, the bytes of information that would be acknowledged by the web server is 3001.
Learn more : https://brainly.com/question/12191237
where can i learning cybersecurity for free
Answers
Answer:
You can learn cybersecurity for free on Coursera. They offer 90 cybersecurity courses from top universities and companies to help you start or advance your career skills in cybersecurity. You can learn online for free today!
Explanation:
Which of the following is the MOST important reason for creating separate users / identities in a cloud environment?
Answers
Answer:
Because you can associate with other
Answer:
Explanation:
To avoid cyberbully
c) Based on your own experiences, what are some symbols (e.g., letters of the alphabet) people use to communicate?
Answers
Based on my own experience, some symbols people use to communicate and they are:
Emojis/emoticonsGifshand gesturesWhat do people use to communicate?Individuals utilize composed images such as letters, numbers, and accentuation marks to communicate through composing.
For occasion, letters of the letter set are utilized to make words, sentences, and sections in composed communication. Individuals moreover utilize images such as emojis and emoticons in computerized communication to communicate feelings, expressions, and responses.
Learn more about communication from
https://brainly.com/question/28153246
#SPJ1
two things every professional PowerPoint presentation should have
Answers
-Simplify and limit the number of words on each screen. Use key phrases and include only essential information.
Sharon must give an informative presentation to a group of teenagers about cultivating earthworms for use in home gardening. Which of the following is the best approach she could take?
a.
She could begin with a funny story about her adventures as a young girl digging up worms with her father and all the wonderful things he taught her about gardening.
b.
She could give a lengthy and detailed lecture about all the major gardening techniques and show several graphs demonstrating the benefits of cultivating earthworms.
c.
She could bring in actual worms for the audience to handle and observe, and actual soil samples for them to touch and smell.
d.
Both a. and c. would be effective approaches for Sharon to take.
Answers
Answer:
D
Explanation:
edg2021
The best approach in the above scenario is to follow both option a. and c. as it would be the effective approaches for Sharon to take.
What is vital in a presentation?For one to be able to get the attention of the audience, the right thing to do is to have a good body language in any presentation.
Conclusively, Sharon could start with a funny story about her adventures as a young girl digging up worms with her father and all the wonderful things he taught her about gardening.
Learn more about presentation from
https://brainly.com/question/24653274
#SPJ2
If you wanted a computer that store a variable with the content of 110 maple street which datatype would be most appropriate