Write a public int indexOf(String s) method that searches the list for the first occurrence of a value equivalent to s
Answers
This function iterates over the list's items, assuming that list is the name of the list you are searching through, and uses the equals() method to determine whether each element is equal to the supplied string s. In the event that a match is discovered , the procedure returns the index of the first occurrence. If no match is discovered, -1 is sent back to show that the value was not included in the list.
A string is a one-dimensional array of characters in the C programming language that is ended by the null character ('0'). A character array that is not ended with a null value is not a valid C string. Each character in a C string takes up one byte of memory, even the null character.
The string's end is indicated by a null character, which is also the sole method for the compiler to understand where the string ends. When dealing with text such as names of people function, addresses, and error messages, strings come in handy.
Learn more about String, from :
brainly.com/question/32338782
#SPJ4
Related Questions
Match the following.A. URL B. Web browserC. Web hostingD. Web pageE. World Wide Web1. A subset of the Internet where Web pages written using HTML can link together and can be displayed by a Web browser.2. A type of software that is capable of searching and retrieving web pages through the World Wide Web on the Internet.3. Uniform Resource Locator; an identifier that combines the domain name and the server location to tell the Web browser where the specific web page is located.4. A service where server stores all the information for a Web page and makes it available for other computers to access.5. A document that is create in Hypertext Markup Language or Extensible Hyper Text Markup Language that can be located by a Web browser and accessed through the World Wide Web.
Answers
Answer:
The answer to this question can be defined as follows:
A = 3
B= 2
C= 4
D= 5
E= 1
Explanation:
In this question, the matched point is defined in the attached file. please find it.

Exercise 1.7.11: Integer Overflow points Let's Go! If an expression would evaluate to an int value outside of the allowed range, an integer overflow occurs. This could result in an incorrect value within the allowed range. In this program you will test for underflow and overflow in Java by adding 1 to the maximum value and subtracting 1 from the minimum value to see what happens to the output. Your output should include 4 items: • The minimum value for an integer. • The maximum value for an integer. • The minimum value subtracted by 1. • The maximum value with 1 added. What do the last two lines print out? Did this surprise you? What do you think it happening here? NOTE: Refer back to the previous example on Min and Max Values of Integers if you need to.
Answers
An integer overflow can result in the value wrapping and become negative, which goes against the program's premise and could produce unanticipated results.
Is there a fix for integer overflow?Using larger integer types, such as Java's long or C's long long int, can lessen the risk of integer overflow occurring in languages where it is possible. There are libraries made to handle arbitrary large numbers if you need to store anything even greater.
What would happen with a Java integer overflow?If it exceeds, it returns to the lowest value before continuing. If it falls below the maximum value, it returns there and continues. If you anticipate that this will happen frequently, think about utilising a datatype or object that can.
To know more about Java's visit:-
https://brainly.com/question/29897053
#SPJ4
what is the intent of bacnet when it states that the path or chain of segments connected by routers can never be circular?
Answers
The intent of BACnet when it states that the path or chain of segments connected by routers can never be circular is to ensure efficient and reliable communication of data between devices in a building automation and control network. By prohibiting circular paths, BACnet ensures that there is always a clear and defined path for data to travel, and that information does not get trapped in an endless loop, which could cause confusion and potential data loss.
1. BACnet is a standard protocol used for building automation and control networks. It ensures that devices from different manufacturers can communicate with each other using a common language.
2. BACnet requires that the network topology be designed in a way that avoids circular paths. This means that the path or chain of segments connected by routers must always be linear, and there should be no loops or circular paths in the network.
3. Circular paths in the network could cause confusion and potential data loss, as information could get trapped in an endless loop. This can lead to network congestion, slow communication, and even network malfunction.
4. By prohibiting circular paths, BACnet ensures that there is always a clear and defined path for data to travel between devices. This helps to ensure efficient and reliable communication of data, as there is no chance for data to get stuck in a loop or take a longer route than necessary.
5. In summary, BACnet's requirement to avoid circular paths in the network topology contributes to a stable, efficient, and reliable building automation and control network. It ensures that data packets can travel between devices with a clear and defined path, avoiding potential data loss, and network congestion.
Learn more about network topology:
https://brainly.com/question/30672019
#SPJ11
PLS WILL GIVE BRAINLEST What eventually led to the abandonment of Jamestown?
malaria-carrying mosquitoes
a civil war
riots started by slaves
famine
Answers
Answer:
famine is the answer I believe
Answer:
D. Famine
Explanation:
Sir Thomas Gates, the newly named governor, found Jamestown in shambles with the palisades of the fort torn down, gates off their hinges, and food stores running low. The decision was made to abandon the settlement.
ways you will use to reach all pupils who are living at a
disadvantaged area
Answers
Answer:
?
im confused
Explanation:
Chapter 1: Case Study Activity QuestionsCase Study-1: Identify Security Control Types1. Despite operating a patch management program, your company has been exposed to severalattacks over the last few months. You have drafted a policy to require a lessons- learnedincident report be created to review the historical attacks and to make this analysis arequirement following future attacks. How can this type of control be classified?2. A bespoke application used by your company has been the target of malware. The developershave created signatures for the application's binaries, and these have been added to endpointdetection and response (EDR) scanning software running on each workstation. If a scan showsthat a binary image no longer matches its signature, an administrative alert is generated. Whattype of security control is this?3. Your company is interested in implementing routine backups of all customer databases. This willhelp uphold availability because you will be able to quickly and easily restore the backed-upcopy, and it will also help uphold integrity in case someone tampers with the database. Whatcontrols can you implement to round out your risk mitigation strategy and uphold thecomponents of the CIA triad?
Answers
The control in question can be classified as a "lessons-learned incident reporting" control. This control involves creating a policy that requires the development of incident reports to review historical attacks and analyze them.
By implementing this control, your company aims to learn from past incidents and apply those lessons to future attacks, thereby improving security. The security control described here is an example of "endpoint detection and response (EDR) scanning" control. In this case, the developers have created signatures for the application's binaries, and these signatures are used by the EDR scanning software installed on each workstation. The software compares the binary image with its signature during scans and generates an administrative alert if a mismatch is detected. This control helps identify any changes or anomalies in the application's binaries, which can indicate the presence of malware.
To round out your risk mitigation strategy and uphold the components of the CIA triad (confidentiality, integrity, and availability), you can implement the following controls for routine backups of customer databases: Encryption: Implement encryption measures to protect the confidentiality of the backed-up copies of the databases. This can involve using strong encryption algorithms and secure key management practices. Access controls: Implement appropriate access controls to ensure that only authorized personnel can access and restore the backed-up copies of the databases. This helps maintain confidentiality and integrity by preventing unauthorized tampering with the backups. Testing and validation: Regularly test and validate the backup and restoration processes to ensure that the backed-up copies are accurate, complete, and can be successfully restored when needed.
To know more about policy visit :
https://brainly.com/question/31951069
#SPJ11
give several examples where you need to use clustering instead of classification in business. what do you think the issues are in clustering algorithms? e.g., are they difficult to validate?
Answers
Classification techniques include support vector machines, naive bayes classifiers, and logistic regression. The k-means clustering algorithm, the Gaussian (EM) clustering algorithm, and others are instances of clustering.
Two methods of pattern recognition used in machine learning are classification and clustering. Although there are some parallels between the two processes, clustering discovers similarities between things and groups them according to those features that set them apart from other groups of objects, whereas classification employs predetermined classes to which objects are assigned. "Clusters" are the name for these collections.
Clustering is framed in unsupervised learning in the context of machine learning, a branch of artificial intelligence. For this kind of algorithm, we only have one set of unlabeled input data, about which we must acquire knowledge without knowing what the outcome will be.
Know more about machine learning here:
https://brainly.com/question/16042499
#SPJ4
The owner of an organic pet food store would like to analyze the sales data to determine if the
business is growing, declining or remaining flat. The owner has the following data:
Sales Revenue Last Year = $350,000
Sales Revenue Current Year = $402,500
What is the sales growth?
0000
13%
10%
15%
17%
Answers
Answer:
Growth sales 15%
Explanation:
Let's make a proportion:
$350,000 - 100%
$402,500 - X%
X = $402,500 * 100% / $350,000 ≈ 115%
Growth sales:
115% - 100% = 15%
how to explain if the following is a valid set of java instructions: int mygrade = (assignment1 * 10); int assignment1 = 10;
Answers
Yes, this is a valid set of Java instructions. The first line declares a variable called mygrade' and assigns it the value of the product of the two variables 'assignment1' and 10. The second line declares a variable called 'assignment1' and assigns it the value of 10.
What is Java ?Java is a programming language and computing platform first released by Sun Microsystems in 1995. It is used to develop and run programs on a variety of hardware, including desktop computers, servers, and mobile devices. Java has become one of the most popular programming languages due to its versatility, allowing developers to write code that can be used on different platforms. Java is a class-based, object-oriented language,
which means it is composed of classes that define objects and the methods that can be used to manipulate them. It is an interpreted language, meaning that the code is compiled into bytecode and then executed by the Java Virtual Machine (JVM). Java also has features such as garbage collection and memory management, which make it easier for developers to create reliable, efficient applications. Java is used in many applications, from web applications to enterprise software to Android apps.
To learn more about Java
https://brainly.com/question/26789430
#SPJ1
What characteristic of a monitor is calculated by multiplying the number of horizontal pixels and the number of vertical pixels
Answers
Resolution is the total number of pixels, that is, the number of horizontal pixels and the number of vertical pixels that make up the image on a monitor screen.
What is resolution?It refers to the number of pixels a device is capable of displaying, expressed as a function of its width and height.
Characteristics of resolutionIt describes the visual dimensions of any given screen, the clarity of the text and images on the screen.At higher resolutions, elements appear sharper, which means the image can be more detailed.Therefore, we can conclude that resolution is the total number of pixels, a higher resolution equals a higher number of pixels on a monitor screen.
Learn more about characteristic of a monitor here: brainly.com/question/14294025
Challenge Asteroid Mining Programming challenge description: You are starting an asteroid mining mission with a single harvester robot. That robot is capable of mining one gram of mineral per day. It also has the ability to clone itself by constructing another harvester robot. That new robot becomes available for use the next day and can be involved in the mining process or can be used to construct yet another robot Each day you will decide what you want each robot in your fleet to do. They can either mine one gram of mineral or spend the day constructing another robot. Write a program to compute a minimum number of days required to mine n grams of mineral. Note that you can mine more mineral than required. Just ensure that you spent the minimum possible number of days to have the necessary amount of mineral mined. Input: A single integer number n, which is the number of grams of mineral to be mined. The value of n will be between 1 and 1000000 (inclusive). For example: Output: A single integer, the minimum number of days required to mine n grams of mineral. For example: Your 2020 Early Career Tale. Time Remaining: E Challenge <> Editor Output A single integer, the minimum number of days required to mine n grams of mineral. For example: 1 import 2 import 3 import 4 import 5 6 public 7 8 * It 9 +/ 10 publi 11 Ing 12 Buf 13 Str 14 Test 1 Test Input Expected Output >_Test Cas Test 2 Test Input No result test your Expected Output 3 E Challenge Expected Output 1 21 314 Test 3 JOUWN Test Input 99 Expected Output 10 11 12 13 Test 4 >_1 Test Input 1000000 No test Expected Output 21
Answers
Given Below is a possible way to the Asteroid Mining Programming challenge in Python.
What is the Programming about?In the code given, we start with a sole harvester robot and keep track of the number of machines and minerals mined before this time. We loop through each day and either mine individual gram of not organic or construct a new android.
o construct a new android, we simply augmentation the harvester_count changing.We continue circling until we've mined the necessary number of minerals. Once we have attained that point, we return the number of days it took to mine the mineral.
Learn more about Programming from
https://brainly.com/question/26134656
#SPJ4

when would instant messaging be the least effective means of communication
Answers
Instant messaging would be least effective means of communication when you have a series of complex questions to ask your colleague.
What is the aim of instant messaging?Instant messaging is often used as a means of sending textual messages, It is known to be a short one and also quick in nature. It can occur between business colleagues and friends.
Its disadvantages is that its is an Ineffective tool for mass communication and also has issues when used for system for archiving.
See options below
A. When you want your colleague to let you know if the hyperlink you sent her is working
B. When you want to tell someone "Happy Birthday!"
C. When you have a series of complex questions to ask your colleague
D. When you want to call an impromptu meeting between some of the people in your office
Learn more about instant messaging from
https://brainly.com/question/26271202
Answer:
When you have a series of complex questions to ask your colleague.
Explanation:
Asking these questions on instant messaging is the least professional way you can ask a colleague about series topics that involve your job, it would be more professional to ask this at work rather than on via message.
Write a half page summary on how to clean a Gaming PC properly.
Answers
Answer:
As a responsible PC gaming enthusiast, you simply cannot wait for spring to do a little routine cleaning on your PC. Regardless of whether you casually play or professionally game, all gaming computers are susceptible to dirt, dust, and other contaminants that can severely impact performance. Dust buildup can cause PC components to retain heat, making it difficult for internal fans to keep the system cool. As a result, the system can become less efficient and unusually slow. However, there are steps you can take to keep your gaming computer in great condition. In this article, we explain how to clean the inside of your gaming computer, so you can keep on fighting the good fight in digital worlds.Assemble the Right ToolsGaming desktops are very complex pieces of technology. Be smart by assembling the necessary tools and supplies before you begin the deep-clean process. Most of the products you need might already be sitting around the house, including compressed air cans, rubbing alcohol, white vinegar, distilled water, microfiber cloths, ear swabs, and tape.How to Clean a Gaming PCFollow these 10 steps to get back on good terms with your gaming rig.1. Disconnect the power cable, USB peripherals, as well as any audio equipment attached to your computer and safely discharge the remaining power.2. Take the computer case outside, so the dust doesn’t settle in the same room that your gaming setup is located.3. Wipe the exterior and interior of the computer case.4. Detach the dust filters and wipe away any accumulated dust. We recommend using compressed air for full coverage. If you have foam filters, gently rinse with water and leave them to dry.5. Wipe down the inside of the case by hand after disconnecting the graphics cards and RAM modules.6. If possible, remove the heatsink entirely to scrub away any gunk or debris.7. Clean off any dust hidden between the cracks of the graphics cards, so you can easily clean the motherboard.8. Remove any big clumps of dust by using a cloth dampened with rubbing alcohol.9. Use the compressed air can to clean nooks, crannies, and the motherboard. For stubborn dust spots, just dampen an ear swab with rubbing alcohol or use a gentle toothbrush to clean.10. Once the case interior is completely clean and free of dust, you can put each component back where it belongs.Routine cleaning and maintenance are important to the health of your gaming PC. We recommend using compressed air every three to six months to prevent dust buildup from impacting your PC components. You should also make an effort to clean your mouse, headphones, keyboard, and monitor to keep your gaming setup looking like new.
Explanation:
what's your opinion on Pokemon and pixeldip
Answers
Answer:
Its a good game but an amazing show. 10/10
Explanation:
what is network topology
Answers
Task
Ask for the total price of the bill, then ask how many diners there are. Divide the total bill by the number of diners and show how much each person must pay.
I need code for this on Repl.it python
Answers
Answer:
Please see the full code in explanation
Explanation:
#This is a console program
def bill_calculator():
print("Enter the Total value of the bill:\n")
bill_total = float(input())
print("Enter total number of dinners:\n")
total_dinner = int(input())
bill_per_person = bill_total / total_dinner
result = ("Bill total: {} \n"
"Total dinners: {} \n"
"Bill per person: {} ").format(bill_total,total_dinner, bill_per_person)
print(result)
if __name__ == '__main__':
bill_calculator()
1.
Which of the following is NOT caused by alcohol?
Answers
Answer:
What are the choices
Answer:
Explanation:reduced concentratjon
inhibited comprehension
decreased coordination
increased heart rate
I need somebody to help me with this question I’ll give points!
Please help no funny business
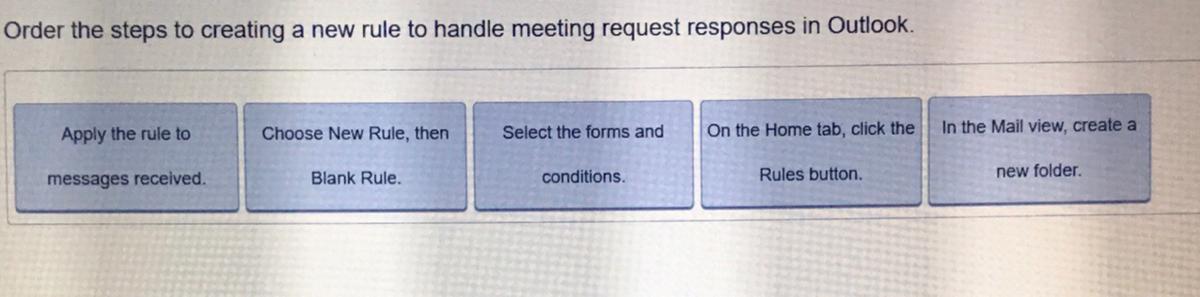
Answers
Answer:
create a new folder (you need that in order to choose it as a destination)
click the rules button
new rule; blank rule
select forms and conditions
apply the rule to messages received
A system has defined specifications that describe how signals are sent over connections. Which layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model provides this function?TransportNetworkData linkPhysical
Answers
The Physical layer of the TCP/IP model plays a critical role in ensuring that signals are sent over connections in a reliable and efficient manner, and that the data transmitted between devices is accurate and secure.
The layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model that provides the function of defining specifications for sending signals over connections is the Physical layer.
The Physical layer is the lowest layer of the TCP/IP model and is responsible for transmitting bits between devices over a physical medium, such as a copper wire or fiber optic cable. It defines the electrical, mechanical, and procedural specifications for transmitting data, including the encoding and modulation of signals, the types of cables and connectors used, and the physical characteristics of the transmission medium.
The Physical layer ensures that data is transmitted accurately and reliably by providing error detection and correction mechanisms, as well as mechanisms for handling signal attenuation, interference, and other factors that can affect the quality of the transmission.
For such more questions on TCP:
https://brainly.com/question/14280351
#SPJ11
How to Fix ""Your PHP Installation Appears to Be Missing the MySQL Extension Which Is Required by WordPress"" Error?
Answers
Update WordPress, Check your PHP version, Ensure the MySQL extension is installed, Verify that the PHP extension is properly configured.
What does a computer install?Making a computer software (including peripherals and plugins) ready for use involves installing (or setting up) the application. Installation is the process of specifically configuring hardware or software so that it may be used with a computer.
How do I install a device?This occurs when the user plugs on (or explicitly installs) a Plug- and-Play (PnP) device, as well as when the system boots for all currently connected devices. Windows is able to identify the devices that are there thanks to drivers like the ACPI driver as well as other PnP bus drivers.
To know more about Installation visit:
https://brainly.com/question/13267432
#SPJ4
The ___ function creates the frame that holds the drawing
Code: Python
Answers
Answer:
create_frame
Explanation:
the answer
The name of the function that is used to create frames that holds the drawing is called;
create_frame
In python, there are different terminologies such as range, frame, draw line, def function e.t.c.
Now, frame is simply defined as the container that is used to hold the graphics while range is defined as a built-in function that returns a list of given numbers,However, in this question, we are dealing with a function that creates the frame holding drawing. We know that def function is used to create functions but the function in this question is called create_frame function.
Thus, in conclusion the function has a name called create_frame function.
Read more at; https://brainly.com/question/20474643
write around 600 words discussing the role of IT in Jumia operational applications
Answers
Jumia is an e-commerce platform that operates in various African countries, and it relies heavily on technology to run its operations. Information technology (IT) plays a critical role in enabling Jumia to process transactions, manage inventory, track deliveries, and provide customer support. In this essay, we will discuss the role of IT in Jumia's operational applications and how it helps the company to achieve its business objectives.
Jumia uses a range of IT systems and tools to support its operations, including its website, mobile application, customer relationship management (CRM) software, order management system (OMS), warehouse management system (WMS), and logistics management system (LMS). These systems work together seamlessly to provide a comprehensive end-to-end solution for Jumia's e-commerce operations.
One of the key roles of IT in Jumia's operational applications is to provide a platform for customers to browse and purchase products online. The Jumia website and mobile application are designed to be user-friendly and easy to navigate, with a search function that allows customers to find products quickly and easily. The website and mobile application also allow customers to view product details, check prices, and make payments securely using a range of payment options.
Another critical role of IT in Jumia's operational applications is to support order management and fulfilment. The order management system (OMS) allows Jumia to manage customer orders, allocate inventory, and track order fulfilment. The OMS also integrates with Jumia's warehouse management system (WMS), which helps Jumia to manage inventory levels, track product movement, and fulfil orders efficiently.
IT also plays a role in Jumia's customer support operations. Jumia uses a CRM system to manage customer interactions and provide support to customers. The CRM system allows Jumia to track customer orders, manage customer inquiries, and provide post-sale support. The CRM system also integrates with Jumia's website and mobile application, allowing customers to access support directly from these channels.
To know more about various visit:
https://brainly.com/question/32260462
#SPJ11
Which type of operating system is permanently programmed into a hardware device?
A. Embedded OS
B. Firmware
C. Mobile OS
D. Hypervisor
Answers
Answer:
B.FIRMWARE
Explanation:
An operating system that is permanently etched into a hardware device (such as a keyboard or a video card).
The type of operating system is permanently programmed into a hardware device is firmware. The correct option is B.
What is firmware?A platform's hardware components are configured and controlled by firmware, which is often computer code. As a result, firmware typically executes as the first piece of code when a device is turned on, serving as the cornerstone upon which system trust is based.
Firmware is a class of software that is permanently included in a device's read-only memory. It offers instructions on how to operate the device and reduces hardware-level security risks. Essentially, firmware refers to software that is integrated into a piece of hardware.
It is referred to as embedded software at times. A microcontroller, a component of the microprocessor that instructs the microprocessor on what to do, serves as an illustration.
Therefore, the correct option is B. Firmware.
To learn more about firmware, refer to the link:
https://brainly.com/question/28945238
#SPJ2
what is computer and its features
Answers
Answer:
A computer is a machine that can be programmed to manipulate symbols.
Explanation:
Following are the features of PC (computer)
Processor
speed
reliability
accuracy
automation
diligence
consistency
Random access memory (RAM)
Operating system
Graphics adapter and video RAM
Monitor
Answer:
Computer Is a Electronic Machine Used To Play Games and for school assigments
Mobile apps fall into two primary categories. What are they?
Engaging consumers and streamlining the purchasing process
Providing location-based promotions and providing streaming services
Engaging consumers and providing entertainment
Sharing data and e-commerce
Answers
The two primary categories of mobile apps are engaging consumers and providing entertainment. Engaging consumers and streamlining the purchasing process: Many mobile apps are designed to engage consumers and provide them with a purchasing experience.
These apps often include features such as product catalogs, personalized recommendations, shopping carts, and secure payment options. They aim to create a convenient and user-friendly platform for users to browse, select, and purchase products or services. Examples of such apps include e-commerce apps, food delivery apps, ride-hailing apps, and banking apps.
Providing entertainment: Another major category of mobile apps is focused on providing entertainment to users. These apps are designed to offer a wide range of engaging and interactive content, such as games, social media platforms, streaming services, video-sharing platforms, and music apps. They aim to entertain users, provide them with engaging experiences, and keep them entertained while using their mobile devices.
While some mobile apps may offer location-based promotions or facilitate e-commerce transactions, these features are not the defining characteristics of the two primary categories. The key distinction lies in whether the app primarily focuses on engaging consumers and streamlining the purchasing process or providing entertainment.
Learn more about app here:
https://brainly.com/question/32284707
#SPJ11
You can use this keyboard shortcut to toggle the visibility of the command line. If for some reason your command line is hidden from the drawing area, then use this keyboard shortcut to bring it back *
Answers
Answer:
Ctrl + 9
Explanation:
You can use this keyboard shortcut to toggle the visibility of the command line
Is MOOC's potentially harmful to copyright? Why or why not ?
Answers
Answer:
Fair-use exceptions to traditional copyright protection face challenges as well, given a MOOC's potential for global reach. Nonetheless, fair use and MOOCs are not mutually exclusive ideas. MOOCs remain an experiment...
What is one possible use of the HASONEVALUE function?
A. Provide a test to determine if the PivotTable is filtered to one distinct value.
B. Use it to ignore any filters applied to a PivotTable.
C. Use it to ignore all but one filter applied to a PivotTable.
D. Use it to determine if a column has only one value.
Answers
A. Provide a test to determine if the PivotTable is filtered to one distinct value.
The correct answer is A. The HASONEVALUE function in Power BI is used to determine if a column in a PivotTable has only one distinct value. It returns a Boolean value indicating whether the column has a single value or multiple distinct values. In the context of a PivotTable, this function can be used to test if the table is filtered to a single value in a particular column. It is useful for creating conditional calculations or measures based on the presence or absence of multiple values in a column.
The HASONEVALUE function is particularly helpful in scenarios where you want to perform different calculations or apply specific logic based on whether a column has a single value or multiple distinct values. By using this function, you can customize the behavior of your calculations and visuals based on the filtered state of the PivotTable. It provides flexibility in creating dynamic reports and dashboards that respond to different filter selections.
To learn more about Boolean click here:
brainly.com/question/27892600
#SPJ11
(25 POINTS)Which statement best reflects the importance of following safety guidelines?
Workplace injuries can result in losses to an organization’s profits.
OSHA responds to complaints of unsafe work environments, and can fine or take negligent employers to court.
Every year, thousands of people die as a result of workplace injuries.
Using equipment safely is faster and makes work more efficient.
Answers
Answer:
I think, Every year, thousands of people die as a result of workplace injuries.
Answer:
B
Explanation:
in general, how much can a twisted-pair's cable be bent before data transmission may be impeded?
Answers
It depends on the specific type of twisted-pair cable being used and its maximum bend radius.
The maximum bend radius is the minimum radius at which a cable can be bent without damaging the inner conductors and insulation. If a cable is bent beyond this radius, it can cause signal loss, crosstalk, and attenuation. The specific maximum bend radius will vary depending on the cable's category and manufacturer, so it is important to consult the manufacturer's specifications for the specific cable being used.
Twisted-pair cables have a bending radius, which is the minimum radius around which the cable can be safely bent without causing damage or impacting data transmission. The industry-standard bending radius for twisted-pair cables is typically four times the diameter of the cable.
To know more about Bend radius visit:-
https://brainly.com/question/31256932
#SPJ11