write a program that adds each of the numbers stored in memory locations d through e, inclusive, and stores the result in register r2. assume that address d can be found in register r3 and address e can be found in register r4. to receive credit, you can only modify the contents of r2, r3, r4, r5, and no other registers, and your solution should have no more than 12 lines of code. note: you do not need to consider the case when d is greater than e.
Answers
If the address in the MAR points to a device register, the output is a 1. (KBSR, KBDR, DDR, DSR). The address control logic handles this.
MANDATORY ADDITIONAL POINTS is referred to as MAR. This is a measure that MAKAUT probably launched in 2018–19 to encourage students to participate in extracurricular activities. The extracurricular activities ranged widely, from taking part in and organizing campus events to creating new initiatives and even studying things that weren't on the course syllabus through MOOCs system.
The main objective was to make sure that the students developed their skills and gained some first-hand experience with social work. MAKUT sought to make the students' involvement in the aforementioned activities voluntary. Its grading system, however, contradicted that. Currently, each student from the first to fourth years must receive 100 marks in order to receive the certificate of course completion.
To know more about system click here:
https://brainly.com/question/27148473
#SPJ4
Related Questions
Microsoft is no longer the market leader in client/server networking.
a. True
b. False
Answers
The statement is false. Microsoft is no longer the client/server networking market leader. Mobile computing is the most rapidly growing type of computing.
Cloud computing is the most rapidly growing type of computing. In the near future, exponential growth in the number of transistors and processor power is expected to slow. Cisco is a market leader in networking hardware. Cisco has been designing and manufacturing computer networking products for over 30 years. A host is any computer that is linked to a network. Unlike server and client, which can refer to either a computer or a computer program, server-host and client-host always refer to computers. The host is a multipurpose computer; clients and servers are simply programs that run on the host.
Learn more about client/server networking here-
https://brainly.com/question/3443368
#SPJ4
Should Microsoft bring paid ads to its X-Box gaming space in light of the new activision deal? Is Microsoft moving to slow with it acquisition based strategy and should they look to develop solutions in house?
Answers
Key factors to keep in mind when utilizing paid advertisements within the box gaming domain, as well as effective methods for gaining new customers is User Experience.
What is the gaming spaceThe addition of advertisements that require payment within the box gaming world has the potential to adversely affect the user experience. Most gamers usually desire unbroken gaming and might react unfavorably towards advertisements that are intrusive or that cause disruptions.
To increase revenue on the box platform, Microsoft may consider implementing paid advertisements as a form of monetization. By making use of advertising income, there is a potential to acquire additional funds that can be utilized for various endeavors such as enhancing platform development, etc.
Learn more about gaming space from
https://brainly.com/question/24855677
#SPJ4
Explain how SEO impacts the way you should interpret search engine results ???
Answers
Answer:
For the majority of businesses, the goal of SEO is to gain leads from search engines, by:
Increasing organic traffic. Increasing keyword rankings. Ranking for more keywords.3-46. Indicate the importance of APIs. What have been the advantages of DBS in creating a developer platform?
3-47. Explain what it means to think "outside of the box" in the context of DBS.
3-48. How well is DBS prepared for the future? Based on: API University. What are APIs and how do they work?
Answers
APIs or Application Programming Interfaces are crucial for businesses that want to interact with other businesses or software and allow developers to create new applications by integrating existing services and data.
DBS has found several advantages in creating a developer platform, which include the following:Advantages of DBS in creating a developer platform: Creating a developer platform has several advantages for DBS. Firstly, DBS has access to a range of developers who can create new applications using DBS's APIs.
This can create new revenue streams for the bank and give customers more options for banking services.Secondly, a developer platform can help the bank increase its brand recognition and visibility among potential customers.
To know more about Programming visit :
https://brainly.com/question/14368396
#SPJ11
what is the term for the era created by the digital revolution?
Answers
Answer:
The Digital Revolution also marks the beginning of the Information Era. The Digital Revolution is sometimes also called the Third Industrial Revolution.
Explanation:
Hope this Helps.
a two-digit code used in addition to the procedure code to indicate circumstances in which the procedure differs in some way from that described is called a
Answers
The two-digit code used in addition to the procedure code is called a modifier. It is used to indicate that the procedure performed had some special circumstances that set it apart from the standard procedure code description.
Modifiers provide additional information to payers and coders regarding the nature of the procedure performed. They are necessary to ensure accurate payment and prevent fraudulent billing. Common modifiers include those indicating a procedure was performed on multiple sites, with a different technique, or by a different provider. The two-digit code used in addition to the procedure code is called a modifier. Modifiers are typically added to the end of the procedure code and are an essential component of the medical coding and billing process.
Learn more about code here:
https://brainly.com/question/17204194
#SPJ11
a two-digit code used in addition to the procedure code to indicate circumstances in which the procedure differs in some way from that described is called a________.
write a paragraph on plastic and pollution within 100 words
Answers
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
Most importantly, plastic pollution harms the Marine life. The plastic litter in the water is mistaken for food by the aquatic animals. They eat it and die eventually. For instance, a dolphin died due to a plastic ring stuck in its mouth. It couldn’t open its mouth due to that and died of starvation. Thus, we see how innocent animals are dying because of plastic pollution.
In short, we see how plastic pollution is ruining everyone’s life on earth. We must take major steps to prevent it. We must use alternatives like cloth bags and paper bags instead of plastic bags. If we are purchasing plastic, we must reuse it. We must avoid drinking bottled water which contributes largely to plastic pollution. The government must put a plastic ban on the use of plastic. All this can prevent plastic pollution to a large extent.
Answer:
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Uprise of Plastic Pollution
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
Read the scenario below, and then choose the right type of computer for each person from the drop-down menus. Three of your friends are in the market to purchase a new computer. Sera does not have a big budget, but she needs a portable computer. Arturo is worried about viruses and has a high budget. Portability is not an issue. Kazuma wants a computer that does not cost too much and is easy to upgrade.

Answers
Answer:
- laptop running Windows
- desktop computer running a Mac OS
- desktop computer running Windows
Explanation:
just took it on edg
Answer:
1. Laptop Running Windows
2. Desktop Computer Running a Mac OS
3. Desktop Computer Running Windows
Explanation:
1. Sera does not have a big budget, but she needs a portable computer. Laptop Running Windows
2. Arturo is worried about viruses and has a high budget. Portability is not an issue. Desktop Computer Running a Mac OS
3. Kazuma wants a computer that does not cost too much and is easy to upgrade. Desktop Computer Running Windows
I hope this helps.<3
Have a nice day.<3
Whats the overall mood of the song Rags2Riches by rod wave
Answers
Answer:
9.5/10
Explanation: Because you can vibe with the muisc but i just dont like the name so with out the name 10/10
Answer:
it would be a sad/get turnt
4:16 decoder using a decoder tree of sizes using 1:2 with active
low enables and outputs
Answers
A 4:16 decoder tree can be constructed using four 2:4 decoder circuits. The inputs are labeled as D0 to D3, while the outputs are labeled as Y0 to Y15. In each of the four 2:4 decoders, the active low enable input, EN, is connected to a different combination of input bits,
as follows:Decoder 1: EN = D0' · D1'Decoder 2: EN = D0' · D1Decoder 3: EN = D0 · D1'Decoder 4: EN = D0 · D1The outputs of the four 2:4 decoders are combined using AND gates to produce the 16 decoder outputs. Each output is the logical AND of a combination of input bits that corresponds to its binary code.The AND gates used to combine the outputs are shown in the following figure.The decoder is considered to be active low because the enable inputs are active low. The output of each AND gate is high only when its corresponding 2:4 decoder is enabled and its corresponding input combination is present. This is illustrated in the truth table below:EN D0 D1 Y0 Y1 Y2 Y3 Y4 Y5 Y6 Y7 Y8 Y9 Y10 Y11 Y12 Y13 Y14 Y150 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 01 0 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 01 1 0 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 0 01 1 1 0 0 0 1 0 0 0 0 0 0 0 0 0 0 0 0 01 1 1 1 0 0 0 1 0 0 0 0 0 0 0 0 0 0 0 01 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 0 0 0 01 1 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 0 0 01 1 1 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 0 01 1 1 1 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 01 1 1 1 1 1 1 1 1 0 0 0 1 0 0 0 0 0 0 01 1 1 1 1 1 1 1 1 1 0 0 0 1 0 0 0 0 01 1 1 1 1 1 1 1 1 1 1 0 0 0 1 0 0 0 01 1 1 1 1 1 1 1 1 1 1 1 0 0 0 1 0 0 1 01 1 1 1 1 1 1 1 1 1 1 1 1 0 0 0 1 0 1 01 1 1 1 1 1 1 1 1 1 1 1 1 1 0 0 1 01 1 1 1 1 1 1 1 1 1 1 1 1 1 1 0 1 01 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 01 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 Since the enable inputs are active low, the circuit is a 4:16 decoder with active low enables and outputs.
To know more about decoder visit:
brainly.com/question/33548572
#SPJ11
I request that it is done in C++. Giving 100 points. To find the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
Sample Output:
Enter Amount: 489.98
The number of 100 dollar bills: 4
The number of 20 dollar bills: 4
The number of 10 dollar bills: 0
The number of 5 dollar bills: 1
The number of 1 dollar bills: 4
The number of Quarters: 3
The number of Dimes: 2
The number of Nickels: 0
The number of Pennies: 3
I have this so far.(look at attachment)
Answers
A program that finds the number of 100 dollar bills, 20 dollar bills, 10 dollar bills, 5 dollar bills, 1 dollar bills, quarters, dimes, nickels, and pennies that will make up an amount entered by the user.
The Program#include<iostream>
using namespace std;
int main () {
double bill=0.0, twenty=0.0, ten=0.0, five=0.0, one=0.0, quarter=0.0, dime=0.0, nickel=0.0, penny=0.0, payment=0.0, cashBack=0.0;
// We need to gather a value for the bill.
while (bill==0) {
cout << "Please enter the amount of the bill (ex. $15.67): \n";
cin >> bill;
cout << "Your bill is "<< bill << ".\n";
}
do {
cout << "Please pay for bill by entering \nthe count of each dollar bill denomination and coin denomination.\n";
// Gathers an amount for each denomination and then gives it a value equal to its monetary value.
cout << "\nTwenty dollar bills:"; cin >> twenty;
twenty *= 20.00;
cout << "\nTen dollar bills:"; cin >> ten;
ten *= 10.00;
cout << "\nFive dollar bills:"; cin >> five;
five *= 5.00;
cout << "\nOne dollar bills:"; cin >> one;
one *= 1.00;
cout << "\nQuarters:"; cin >> quarter;
quarter *= .25;
cout << "\nDimes:"; cin << dime;
dime *= .10;
cout << "\nNickels:"; cin >> nickel;
nickel *= .05;
cout << "\nPennies:"; cin >> penny;
penny *= .01;
// Add the money together and assign the value to payment.
payment = twenty + ten + five + one + quarter + dime + nickel + penny;
cout << "\nYour payment totals: $" << payment << "\n";
if (payment < bill) {
cout << "\nYou didn't pay enough money to cover the bill. \nPlease re-enter your amount.\n";
// If payment isn't greater than bill then they're asked to reenter their money.
}
// Determine the amount of cash to give back and assign the value to cashBack.
cashBack = payment - bill;
} while (cashBack <= 0);
cout << "\nI owe you $" << cashBack <<"\n";
// Reset the values of each denomination to 0
twenty = 0;
ten = 0;
five = 0;
one = 0;
quarter = 0;
dime = 0;
nickel = 0;
penny = 0;
// These while loops will subtract the monetary value from cashBack and add a value of 1 each time it is looped.
while (cashBack >= 20) {
cashBack -= 20;
twenty += 1;
}
while (cashBack >= 10) {
cashBack -= 10;
ten += 1;
}
while (cashBack >= 5) {
cashBack -= 5;
five += 1;
}
while (cashBack >= 1) {
cashBack -= 1;
one += 1;
}
while (cashBack >= .25) {
cashBack -= .25;
quarter += 1;
}
while (cashBack >= .10) {
cashBack -= .10;
dime += 1;
}
while (cashBack >= .05) {
cashBack -= .05;
dime += 1;
}
while (cashBack >= .01) {
cashBack -= .01;
penny += 1;
}
// For each denomination that has a value greater than 0, the person is payed back the amount.
if (twenty > 0) {
cout << "\n" << twenty << " Twenty dollar bills.\n";
}
if (ten > 0) {
cout << "\n" << ten << " Ten dollar bills.\n";
}
if (five > 0) {
cout << "\n" << five << " Five dollar bills.\n";
}
if (one > 0) {
cout << "\n" << one << " One dollar bills.\n";
}
if (quarter > 0) {
cout << "\n" << quarter << " Quarters.\n";
}
if (dime > 0) {
cout << "\n" << dime << " Dimes.\n";
}
if (nickel > 0) {
cout << "\n" << nickel << " Nickels.\n";
}
if (penny > 0) {
cout << "\n" << penny << " Pennies.\n";
}
}
Read more about C++ programming here:
https://brainly.com/question/20339175
#SPJ1
The perusal activity is individual work. The activity must be submitted in the drop box through TURN-IT-IN. Note the key aspects which is the rubric/criteria below, for which the activity marks will be allocated. Activity Objectives: Address all key aspects of the activity: a. Summarize global growth scenario 2020 and 2022 b. Identify key events that have contributed to global growth scenario. c. Explain macroeconomic actions countries have taken in response Note: That you must adhere to proper referencing (APA style). Activity must be typed in WORD format, Times New Roman, 1.5 line spacing and 12 font) Resources: World Economic Outlook Update Jan 2020 World Economic Outlook Update July 2022 Other credible sources) Global growth had been revised downwards for 2019-2020 and for 2021-2022. Peruse through Jan 2020 Economic Outlook Update and the July 2022 Economic Outlook Update and do the following: i) Write a paragraph each explaining global growth scenario for 2020 and 2022 (100 words each) [12 marks] ii) For each Economic Outlook: a) Cite three key events that have impacted global growth potential. [24 marks] b) Discuss three actions major countries have taken and are taking in response [24 marks]
Answers
General understanding of global growth scenarios and some examples of key events and macroeconomic actions that have influenced them. You can use this information as a starting point and conduct further research to complete the activity.
Global Growth Scenario:
In the January 2020 Economic Outlook Update, the global growth scenario for 2020 was revised downwards due to various factors such as trade tensions, geopolitical uncertainties, and subdued investment. Economic growth was expected to be moderate, with risks tilted to the downside.
In the July 2022 Economic Outlook Update, the global growth scenario for 2022 had also been revised downwards, primarily due to the impact of the COVID-19 pandemic. The pandemic led to disruptions in global supply chains, reduced consumer spending, and weakened business investments, contributing to a decline in global growth prospects.
Key Events Impacting Global Growth:
1. Trade Wars: The ongoing trade tensions between major economies, such as the United States and China, have had a significant impact on global growth. Tariffs and trade restrictions have disrupted international trade, leading to reduced business confidence and investment.
2. COVID-19 Pandemic: The emergence of the COVID-19 pandemic in 2020 had a profound impact on the global economy. Lockdown measures, travel restrictions, and reduced consumer activity resulted in a sharp contraction in economic activity across various sectors.
3. Policy Responses to the Pandemic: Governments and central banks implemented various fiscal and monetary policies to mitigate the economic impact of the pandemic. These measures included stimulus packages, interest rate cuts, and liquidity injections to support businesses, households, and financial markets.
Macro-economic Actions by Major Countries:
1. Fiscal Stimulus: Governments implemented expansionary fiscal policies by increasing public spending, providing financial assistance to affected industries, and implementing tax relief measures to stimulate economic growth.
2. Monetary Policy Easing: Central banks employed accommodative monetary policies by reducing interest rates, implementing quantitative easing programs, and providing liquidity support to banks to encourage borrowing, investment, and lending.
3. Structural Reforms: Some countries initiated structural reforms aimed at improving competitiveness, attracting investments, and enhancing productivity. These reforms focused on areas such as labor market flexibility, taxation, regulatory frameworks, and infrastructure development.
Remember to reference your sources using APA style and ensure that the content you provide aligns with the specific resources mentioned in your assignment instructions.
Learn more about macroeconomic here:
https://brainly.com/question/28489802
#SPJ11
What is a “backdoor”
Answers
Answer:
A backdoor refers to any method by which authorized and unauthorized users are able to get around normal security measures and gain high level user access (aka root access) on a computer system, network or software application.
Explanation:
You are the network administrator for a city library. Throughout the library, there are several groups of computers that provide public access to the internet. Supervision of these computers has been difficult. You've had problems with patrons bringing personal laptops into the library and disconnecting the network cables from the library computers to connect their laptops to the internet. The library computers are in groups of four. Each group of four computers is connected to a hub that is connected to the library network through an access port on a switch. You want to restrict access to the network so only the library computers are permitted connectivity to the internet. What can you do to fix this problem
Answers
Answer: Configure port security on the switch
Explanation:
Since there need to be a restriction on access to the network so that the library computers will be the only ones that are allowed connectivity to the internet, the thing that can be done to fix the problem is to configure a port security on the switch.
When a port security is configured, it helps in securing the network and this will in the prevention of unknown devices from being connected to the network.
You are working on a home office network. Recently, you added a cable modem to the network so the computer named home-pc could connect to the internet. You also added the computer named home-pc2 to your network, but your networking configuration only allows home-pc to connect to the internet. To save on cost, you want to add a hub to the network so that both computers can communicate with each other and connect to the internet. The computers do not need to have guaranteed bandwidth for their network connections
Answers
Answer:
connect the ethernet
Explanation:
What are some useful applications of video games?
Answers
Answer:
Steam, Origin, Uplay and epic games
Explanation:
Advertisers pay ad partners for _______________ whenever a user responds to an ad by performing a specified activity such as signing up for a service, requesting material, or making a purchase. Group of answer choices
Answers
Advertisers pay ad partners for "cost per action" (CPA) whenever a user responds to an ad by performing a specified activity such as signing up for a service, requesting material, or making a purchase.
When advertisers partner with publishers, networks, or other advertising platforms to promote their products or services, they may agree to a cost-per-action (CPA) payment model. In this model, advertisers pay their partners each time a user responds to an ad by performing a specific action, such as signing up for a service, requesting material, or making a purchase. This payment model is attractive to advertisers because it focuses on results rather than impressions, clicks, or views, making it easier to measure the effectiveness of their campaigns. It also benefits publishers and networks, as they can earn revenue for driving valuable user actions, rather than just displaying ads to their audience.
To know more about advertisers visit:
brainly.com/question/3163475
#SPJ11
1. Access Control is the central element of computer security because access control systems provide the essential services of identification and authentication, authorization, access approval, and accountability. Is this statement true?
2. The main function of Access control is to allow authorized access to resources. Do you agree with this statement?
Justify your answers
Answers
Authorization , The system responds to these queries during the authorization phase of access control: "What precisely can the requestor access?" and "What can they do?"
In computer security, what does access control mean?Access control is a key element of data security that establishes who is permitted access to and usage of the resources and information of the firm. Access control rules use authentication and authorization to ensure users are who they claim to be and have authorized access to company data.
What makes access control crucial to security?Access restrictions restrict who has access to data and information processing systems. When properly implemented, they reduce the chance of information being accessed illegally, without the proper authorization, and risk of a data breach.
To know more about Authorization visit :-
https://brainly.com/question/9560827
#SPJ4
Plz I need the answer ASAP. I’ll mark brainliest

Answers
Answer:
A string containing all lowercase letters and numerals and ending with a- Or D
Question #5
Multiple Choice
What is used within an HTML tag for additional information?
O attribute
O anchor
O hyperlink
metadata
Answers
Answer: Attribute
Explanation: Attribute is used in HTML tags for additional information. Correct on Edg 2021.
Answer: attribute
Edge '23
How a Programmatic NEPA Review (for our purposes this will be a
Programmatic EIS) differs from an EIS (referred to as a project
level EIS)?
Answers
A Programmatic NEPA Review, or Programmatic Environmental Impact Statement (PEIS), differs from a project-level Environmental Impact Statement (EIS) in several ways. The main differences include the scope and level of detail involved in each type of analysis.
The key differences between a Programmatic NEPA Review (Programmatic EIS) and a project-level EIS are as follows:
1. Scope: A Programmatic NEPA Review (Programmatic EIS) examines the impacts of an entire program, policy, or regulatory decision and covers a wide range of potential future actions, while a project-level EIS is site-specific and focuses on the impacts of a specific project.
2. Level of Detail: A Programmatic NEPA Review (Programmatic EIS) provides a broader analysis of environmental impacts .
3. Timeframe: A Programmatic NEPA Review (Programmatic EIS) covers a longer time frame and is typically completed before any specific projects are proposed .
4. Decision-Making: A Programmatic NEPA Review (Programmatic EIS) can help inform decision-making at a higher level .
5. Flexibility: A Programmatic NEPA Review (Programmatic EIS) provides greater flexibility in the implementation of future projects .
To know more about Programmatic visit:-
https://brainly.com/question/30778084
#SPJ11
Greg is looking around an art exhibition displaying American art from different ages. He spots the works of some famous artists. Match the
artists to the era of which they belong.
Benjamin West
Georgia O'Keeffe
Native Americans
Thomas Crawford
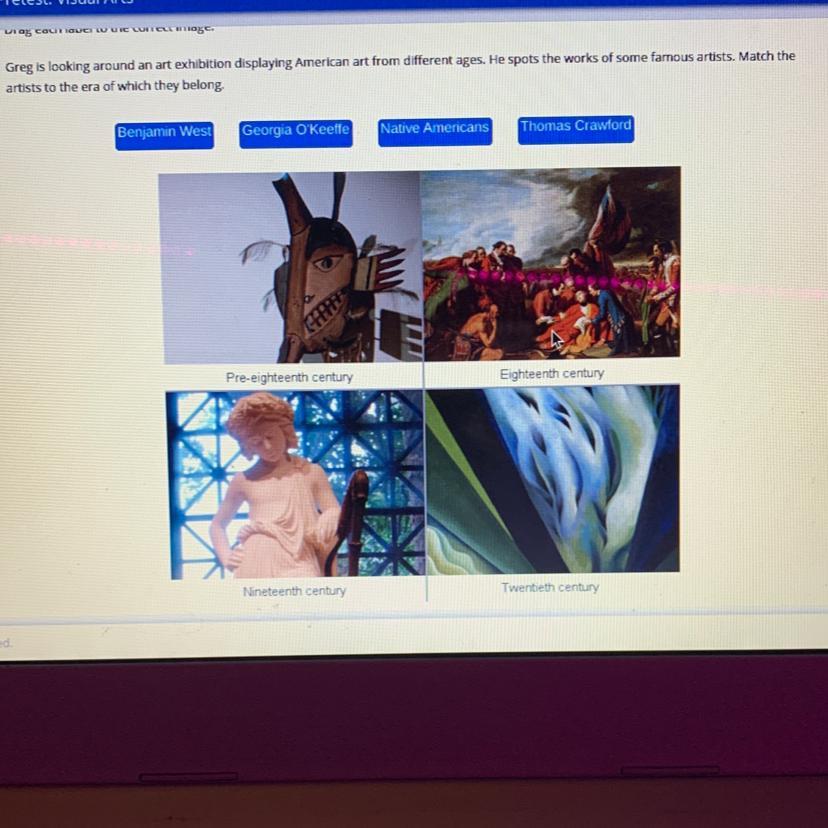
Answers
Answer:
Benjamin west is 18th century
Thomas Crawford is 19th century
Native Americans is pre-18th century
Georgia O'Keeffe is 20th century
Explanation:
To view the Picture tools tab, a user must first _____.
A.select the picture
B.navigate to the View tab
C.place the cursor in the right margin
D.select the picture style
Answers
Critical Thinking Questions
You learned that there are many different programming languages, just like there are many different spoken languages throughout the world. And programming languages have certain syntax, or rules, they have to follow in order for the computer to understand the commands. Give one example of syntax for one of the programming languages listed in the unit. Then give two examples of syntax from a language you know. Describe what will happen if you do not follow these rules in your language.
What are the four main components of programming languages, and why is each one needed?
Give your own examples for how list and dictionary data structures could keep track of some common information you might need. Your examples should be different from the ones in the unit.
Why would a programmer use a flowchart?
Finish identifying the data types of each of the following pieces of data:
TABLE Identify data types
Data Data Type
“Hermione” String
13.5
-6
“18 Mingle Lane”
False
-20.4
“Bonjour”
12345
Answers
Answer:
I only have three answered but I hope this helps.
Explanation:
1. You learned that there are many different programming languages, just like there are many different spoken languages throughout the world. And programming languages have certain syntax, or rules, they have to follow in order for the computer to understand the commands. Give one example of syntax for one of the programming languages listed in the unit. Then give two examples of syntax from a language you know. Describe what will happen if you do not follow these rules in your language.
In python, when we declare a float or an integer, we declare like this:
a=2 for int
b=2.0 for float
4. Why would a programmer use a flowchart?
Programmers use flowcharts because the help the programmer see where the data will end up. Flow charts help programmers figure out where a potential problem area is and helps them with debugging or cleaning up code that is not working.
5. Finish identifying the data types of each of the following pieces of data:
Data Data Type
“Hermione” String
13.5 Float
-6 Integer
“18 Mingle Lane” String
False Boolean
-20.4 Float
“Bonjour” String
12345 Integer
Select the correct answer.
Nancy wants to buy a cooking stove that’s electrically insulated and resistant to heat. What material should she choose for the cooktop?
A.
composite
B.
polymer
C.
metal
D.
ceramic
E.
semiconductor
Answers
Answer:
E I think is the best answer
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
With regarding to privacy settings, which statements are true?
Answers
Cookies are text files that a website sends to your computer or other device when you visit it.
What is the role of privacy settings in using technology?Cookies themselves are secure because the data they hold is constant. Computers cannot be infected with malware or viruses.
However, certain cyberattacks have the capacity to access your browsing sessions and commandeer cookies. They can track people's browsing histories, which is dangerous.
If you agree to them, these cookies are recorded on your device's web browser. The owner of the website can then be contacted by cookies to track and collect information from your browser.
The information you've placed into forms, your web search history, your browsing history, and even your location can all be revealed via cookies.
Therefore, When it asks if you’d like to accept cookies on a website
Learn more about privacy settings here:
https://brainly.com/question/13650049
#SPJ5
can you help me please can you unscramble this words for me
and the word list is on the bottom of the assignment




Answers
Answer:
1. Accountants and Auditors
2. Financial Managers
3. Teacher Assistants
4. Firefighters
5. Cashiers
6. Dental Assistants
7. Clergy
8. Registered Nurses
9. Computer User Support Specialists
10. Management Analysis
Explanation:
Hope this helps.
May I please have brainliest? :)
I NEED HELP!! THIS IS 3D COMPUTER MODELING COURSE IN CONNEXUS
the coordinate's that determine the position of an element in space are expressed as. Different shapes, 1,2, and 3/ x,y,z/l,t,p
refer to the pictures




Answers
6. x, y, and z (x is right, z is forward, and y is up)
7. true
8. plane
9. Cartesian grid
10. They describe a location using the angle and distance from the original.
11. effects that alter the look of an object.
12. true
13. true
14. (not sure, but I would go with conceptual)
15. 3-D elements
Hope this helps! Please let me know if you need more help, or if you think my answer is incorrect. Brainliest would be MUCH appreciated. Have a great day!
Stay Brainy!
eastern europe uses nuclear energy for electricity production at a higher proportion compared to other parts of the world.
Answers
Yes, that is correct that Eastern Europe has a high proportion of nuclear energy use for electricity production compared to other regions in the world.
What is energy?In the context of coding, energy typically refers to the amount of computational resources (such as CPU cycles, memory usage, or battery life) required to execute a program or perform a specific task. Energy efficiency is an important consideration in the design and development of software, particularly for mobile devices or other systems with limited resources. Improving the energy efficiency of code can help extend battery life, reduce operating costs, and improve performance. Techniques for optimizing energy efficiency include code optimization, reducing unnecessary computations, and minimizing data transfers.
Here,
According to the International Atomic Energy Agency, in 2020, the share of nuclear energy in electricity production was 47% in Eastern Europe, while the global average was 10%.
The countries in Eastern Europe with the highest proportion of nuclear energy use for electricity production include Ukraine, Slovakia, Hungary, and the Czech Republic.
To know more about energy,
https://brainly.com/question/21439267
#SPJ4