Write a program named Deviations.java that creates an array with the deviations from average of another array. The main() method
Answers
Answer:
hello your question is incomplete attached is the complete question and solution
answer : The solution is attached below
Explanation:
Below is a program named Derivations.java that creates an array with the deviations from average of another array.
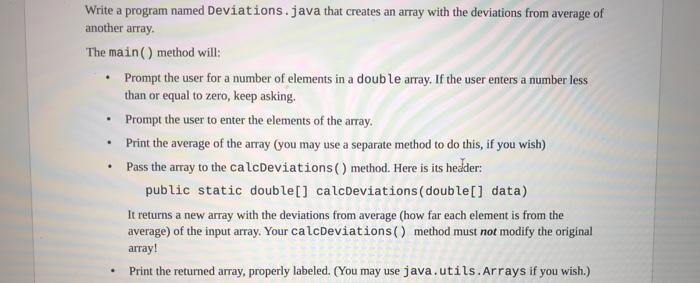
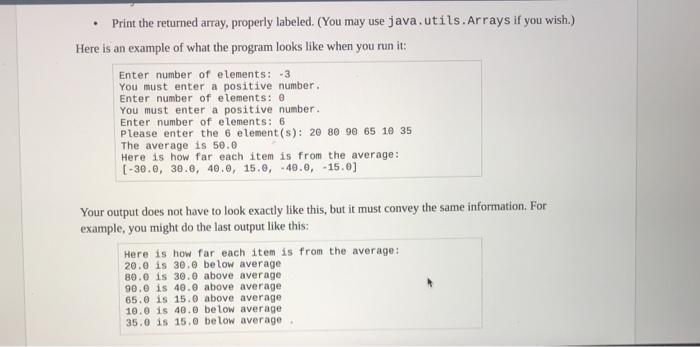
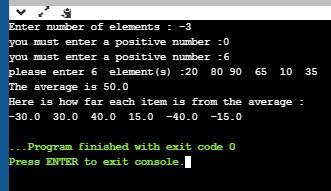
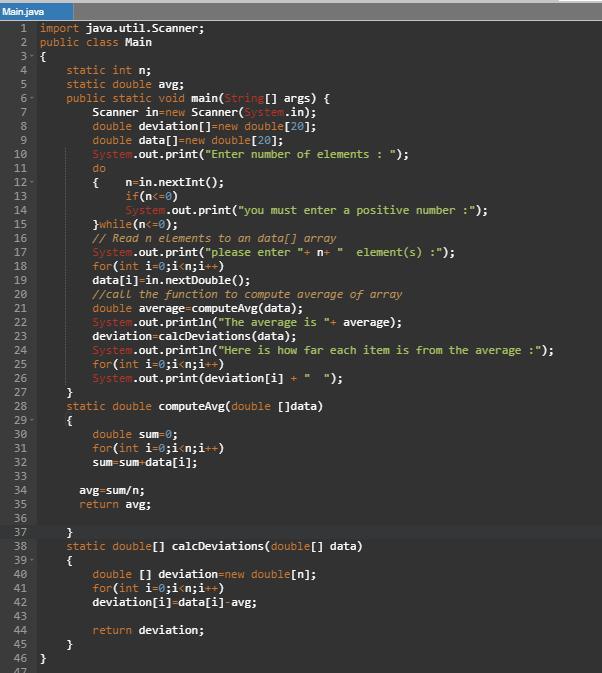
Related Questions
hurry i need help swear to god i will give brainliest not lying

Answers
Answer:
finding area of a circle
def area(radius):
int(radius)
formula = radius * radius * 3.14
print(formula)
radius_input = int(input('Insert the radius of your circle: '))
area(radius_input)
hope this helped :D
Select 3 true statements about Python primitive types.
32-bit integer type (a.k.a. int32) can represent integer value from -2^31 (-2,147,483,648) to 2^31-1 (2,147,483,647)
The int type in Python3 cannot represent a number greater than 2^31-1.
A binary floating-point method is used to represent fractions in binary numbers.
The decimal number 0.1 cannot be expressed without error in binary floating-point format.
The float type in Python3 can represent decimal 0.1 without error.
Answers
The true statements about Python primitive types are:
32.bit integer type (a.k.a. int32) can represent integer value from -2 31 (-2.147,483,648) to 2"31-1 (2,147,483,647) A binary floating point method is used to represent fractions in binary numbers. The decimal number 0.1 cannot be expressed without error in binary floating-point format.What are the Python primitive types?
The Python is known to be made up of four primitive data types which are said to be:
Integer.Float.String.Boolean.Note therefore that The true statements about Python primitive types are:
32.bit integer type (a.k.a. int32) can represent integer value from -2 31 (-2.147,483,648) to 2"31-1 (2,147,483,647) A binary floating point method is used to represent fractions in binary numbers. The decimal number 0.1 cannot be expressed without error in binary floating-point format.Learn more about Python from
https://brainly.com/question/26497128
#SPJ1
public class Dog
{
/* code not shown */
}
public class Dachshund extends Dog
{
/* code not shown */
}
Assuming that each class has a default constructor, which of the following are valid
declarations?
I. Dog sadie = new Dachshund();
II. Dachshund aldo = new Dachshund();
III. Dachshund doug = new Dog();
Answers
Answer:
dog=1/3=1/4
Explanation:
Accessing disk is much slower than accessing memory. As a result, many file systems have been designed with various optimizations to improve performance. What is an example of file system performance optimization
Answers
Answer:
An example of file system performance optimization is Caching - i.e. keep in memory a collection of blocks that logically belong on the disk, for performance reasons.
Explanation:
Caching - i.e. keep in memory a collection of blocks that logically belong on the disk, for performance reasons.
The ultimate frequent method employed to decrease the duration of disk elucidated as a collection of books i.e similar kind that is preserved in invisible area.
why concurrency control is needed in transaction.
And why Acid properties in transaction is important.
Answers
Explanation:
Concurrency Control in Database Management System is a procedure of managing simultaneous operations without conflicting with each other. It ensures that Database transactions are performed concurrently and accurately to produce correct results without violating data integrity of the respective Database.And The ACID properties, in totality, provide a mechanism to ensure correctness and consistency of a database in a way such that each transaction is a group of operations that acts a single unit, produces consistent results, acts in isolation from other operations and updates that it makes are durably stored.
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
write an algorithm of telephone call system
Answers
Answer:
this is the correct answer

Step 2 : Pick up the phone.
Step 3 : Search for friend’s phone number in the contact list
Step 4 : Select the number and dial it by clicking on the dial button.
Step 5 : Wait for the network to connect.
Step 6 : If connection is successful, you will hear the dialer tone,
Else if network connection failure, number will not be dialled
Else if number is busy, hear busy tone
Else if number is not reachable, hear number not reachable message.
Step 7 : End procedure.
One advantage of the Second generation of programming language is that it is machine dependent. True or False
Answers
Answer:
I THINK FALSE
Explanation:
A local company is expanding its range from one state to fifteen states. They will need an advanced method of online communication and someone to design an advanced and thorough database to store a lot of information. Who should they hire to assist with both these goals?
a Database Architect and a Computer System Analyst who focuses in interactive media
a Computer Hardware Engineer and a Software Developer who focuses in interactive media
a Software Developer and a Web Developer who focuses in programming and software development
a Web Administrator and a Computer System Analyst who focuses in information support and services
Answers
Answer:
the answer is C,a a Software Developer and a Web Developer who focuses in programming and software
Brainlist me if im right
Answer:
C is correct
Explanation:
True
Question # 21
Dropdown
You shouldn’t use more than ____ fonts on a slide.
Answers
Answer:
You should use no more than two fonts on a slide.
Answer:
Well the correct answer is 3 or less, but for this question its not an answer so the correct answer for this is 2
Explanation:
Describe producing any four (4) methods output. o
Answers
Outputs are final products or services that are given to the client. These outputs come from the processes that are used to transform the inputs into a business.
Thus, In other words, the output method counts the accomplishments. An entity must first estimate how many outputs will be required to fulfill the contract before implementing the output method.
The entity then monitors the development of the contract by comparing the total estimated outputs required to fulfill the performance obligation with the outputs that have already been produced and Bussiness.
Quantifying outputs can be done in a variety of ways and is easily adaptable to a contract. Examples of production measures are finished tables, units delivered, homes built, or miles of track constructed and outputs.
Thus, Outputs are final products or services that are given to the client. These outputs come from the processes that are used to transform the inputs into a business.
Learn more about Bussiness, refer to the link:
https://brainly.com/question/30762888
#SPJ1
you work as a network administrator for a small company. you are asked by your manager to ensure that the technical requirements for efs (encrypting file system) on computer1 are met. which of the following commands will you use to accomplish this?
Answers
The answer is Cipher.exe, meaning that the Cipher.exe command is used, in accordance with the information provided in the question.
What is the purpose of encrypting file systems?Encrypting File System (EFS): What is it? By encrypting folders or files on various variants of the Windows OS, the Encrypting File System adds an extra degree of security. EFS is an NTFS feature that is integrated into a device's operating system (OS).
Which is better, BitLocker or EFS?In contrast to EFS, which can add additional consumer file level encrypting for security isolation between many users of a single computer, BitLocker helps defend the complete operating system drive from offline attacks. Files on other disks that aren't secured by Boot loader can likewise be encrypted in Windows using EFS.
To know more about encrypting file system visit:
https://brainly.com/question/10410730
#SPJ4
What is the stdio.h header file ?
Answers
Write Java statements to declare another array and initialize it with the names of the months of the year.
Answers
Answer:
SEE CODE IN BELOW AND GIVE ME BRAINLEST
Explanation:
String[] months = {"January", "February", "March", "April", "May", "June", "July", "August", "September", "October", "November", "December"};
Heads of DoD Components are responsible for establishing component specific procedures regarding transmission and transportation of classified material. Select items that must be considered when establishing these procedures.
a. Achieve declassification goals(not sure)
b. Identify local authorized couriers (selected but incorrect)
c. Promote the most cost-effectiveness method (not sure )
d. Aim to minimize the risk of compromise (selected and correct)
answer was incorrect
Answers
The correct answer is b. Identify local authorized couriers. When establishing procedures regarding transmission and transportation of classified material,
What is transmission ?Transmission is the process for transferring data from one point to another. This process can involve the transmission of information through a variety of media, such as electrical cables, wireless networks, satellite signals, and optical fibers. Transmission can be used to exchange a variety of data including texts, images, audio, and video. It is important to note that transmission is not the same as communication, as communication involves the exchange of data as well as the interpretation of the data.
it is important to identify local authorized couriers who will be responsible for securely transporting the material. This helps to ensure that the material is handled securely and that only authorized personnel have access to it. Additionally, other items that must be considered when establishing these procedures include the type of security measures needed for the material, the frequency of transportation, and the type of container used to transport the material.
To learn more about transmission
https://brainly.com/question/30557689
#SPJ1
What common feature of well-made web apps helps them stand out from static email advertisements?
Answers
Answer:
For the test, I litterally came here while taking it and couldn’t find an answer, I got a horrible 70.. but all I know it’s not C or D
Explanation:
I took the test, sorry I don’t have an actual answer
A software repository, also known as a 'repo'
Answers
I hope this helps
The term management information systems refers to a specific category of
information system serving. Discuss
Answers
Information systems specifically designed to support management-level tasks are referred to as management information systems (MIS).
What is meant by a management information system?Management information systems is the study of people, organizations, technology, and their relationships (MIS). The return on investments in people, equipment, and company operations are maximized by businesses with the help of MIS specialists. MIS is a people-oriented field with a focus on providing technology-enabled services.
How crucial is a management information system?A management information system boosts an organization's competitiveness. What is working and which isn't is reported and identified. Owners can use these reports to get the data they require to make decisions and raise employee and company performance.
Briefing:Information systems specifically designed to support management-level tasks are referred to as management information systems (MIS). In most cases, MIS generates summary reports from enormous amounts of input data. MIS are virtually entirely focused on internal events rather than environmental or outside ones.
To know more about Management information systems (MIS) visit:
https://brainly.com/question/16131934
#SPJ10
how to power clip in corel draw
Answers
Answer:
Open CorelDRAW and create a new document or open an existing one.Select the object or shape that you want to use as the container for the PowerClip. This object will act as the frame or mask that holds the content.Go to the "Arrange" menu at the top of the screen and choose "PowerClip" from the dropdown menu. Alternatively, you can use the keyboard shortcut Ctrl + K.A PowerClip dialog box will appear. Click on "Place inside container" and then "OK."You will notice that the cursor changes to a small arrow. Click on the object or shape that you want to insert or clip inside the container.The selected object or shape will now be inserted into the container and clipped according to its boundaries.To edit the contents of the PowerClip, double-click on the container object. This will enter the editing mode, where you can move, resize, or modify the clipped object.To exit the editing mode and return to the regular workspace, click outside the container object or press Esc on your keyboard.Explanation:
hope this helps
Emerson needs to tell his browser how to display a web page. Which tool will he use?
Group of answer choices
HTML
Web viewer
Operating system
Translator
Answers
Answer:
HTML
Explanation:
HTML stands for "Hypertext Markup Language." It allows the creation of electronic documents which use semantics to indicate a particular text. The different HTML elements are being separated by "angle brackets" in order to make up a tag. These tags are not visible, but they make it possible for the browser's page to be interpreted.
Answer:
HTML
Explanation:
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
Give atleast 10 examples of wearable technologies and its functions
Answers
Answer:
Wearable technologies are a form of technology designed and manufactured in such a way that people can wear them around.
Explanation:
Examples of smart wearable technologies and their functions are:
1. Smart wrist watch: this serves as both wrist watch and mobile gadgets that can make calls and some other functions like calculator, calendar, etc.
2. Fitness tracker: this helps in monitoring body activity level
3. Smarts clothIng: this can work with smart watch or phones to monitor the body activity
4. Smart headset: asides from using it to listen to music, it can also filter then the information within the environment
5. Artificial Intelligence hearing aid: this can help remove unnecessary noise level
5. Artificial Intelligence hearing aid: this can help remove unnecessary noise level
6. Smart jewelry: just like smart watches, it helps in measuring health activities in the human body system.
7. Implantable: this is for internal use and can also monitor the functioning rate of the body.
8. Head Mounted display: this is attached to the head, but one will be able to see the things the device is seeing.
9. Smart Chést stràp: this measures the level of heart rate in the body
10. Goógle glass: a user to make a call or browse the intérnet, and easily share what you ve seen
Wearable are part of the technology that is made to wear and use.
technology also includes activity trackers and skin electronics. The electronics such as software sensors and other things enable them to exchange quality data.They include rings, pens, watches, bracelets, trackers, earbuds, lens and contact less devices.Hence the above mentioned are some of the examples of wearables technologies.
learn more about at least 10 examples of wearable technologies and their functions.
brainly.ph/question/11249287.
match the unhealthy food choice with its long-term effects
Answers
Could you please elaborate this question by attaching a file to support it?
A(n) ___loop is a special loop that is used when a definite number of loop iterations is required.
O a. for
O b. do...while
O c. else
O d. while
Answers
Answer: A
Explanation:
for is used when you're talking in terms of repeating loops for a finite number of times.
do... while is used when describing something to do while a variable is equal to something, else is used when a variable isn't what was defined in a while statement, and while is used when you want something to repeat while a variable is equal to something.
Write a program that uses the Purchase class in 5.13. Set the prices to the following: Oranges: 10 for $2.99 Eggs: 12 for $1.69 Apples: 3 for $1.00 Watermelons: $4.39 each Bagels: 6 for $3.50 Set the purchased quantity to the following: 2 dozen oranges, 2 dozen eggs, 20 apples, 2 watermelons, 1 dozen bagels Display the total cost of the bill
Answers
Answer:
Explanation:
The following program is written in Java. Using the program code from Purchase class in 5.13 I created each one of the fruit objects. Then I set the price for each object using the setPrice method. Then I set the number of each fruit that I intended on buying with the setNumberBought method. Finally, I called each objects getTotalCost method to get the final price of each object which was all added to the totalCost instance variable. This instance variable was printed as the total cost of the bill at the end of the program. My code HIGHLIGHTED BELOW
//Entire code is in text file attached below.
//MY CODE HERE
DecimalFormat df = new DecimalFormat("0.00");
oranges.setPrice(10, 2.99);
oranges.setNumberBought(2*12);
eggs.setPrice(12, 1.69);
eggs.setNumberBought(2*12);
apples.setPrice(3, 1);
apples.setNumberBought(20);
watermelons.setPrice(1, 4.39);
watermelons.setNumberBought(2);
bagels.setPrice(6, 3.50);
bagels.setNumberBought(12);
totalCost = oranges.getTotalCost() + eggs.getTotalCost() + apples.getTotalCost() + watermelons.getTotalCost() + bagels.getTotalCost();
System.out.println("Total Cost: $" + df.format(totalCost));
}
}

d' Explain each of the following i 100 Base-CX (10GBase-T Ethernet standards
Answers
Note that 100Base-CX is an Ethernet standard for 100 Mbps over short distances. While,
10GBase-T - Ethernet standard for 10 Gbps over copper cables up to 100 meters.
How do they work?1. 100Base-CX - It is an Ethernet standard that defines the specifications for transmitting data at a rate of 100 Mbps over a short distance using copper twisted pair cables with a maximum segment length of 25 meters.
It uses a balanced signaling scheme and is commonly used for connecting devices within a confined area, such as in-building networks.
2. 10GBase-T - It is an Ethernet standard that allows for data transmission at a rate of 10 Gbps over twisted pair copper cables. It utilizes advanced signaling techniques and supports a maximum cable length of 100 meters.
10GBase-T is widely used for high-speed network connections in data centers, enterprise networks, and other applications requiring high bandwidth.
Learn more about Ethernet standards at:
https://brainly.com/question/31063222
#SPJ1
Could YOU Please help me out of this question This is how I started typing but at the end I got stuck My half of the answers I attached. please Help I will give you brainiest
we will work on text processing and analysis. Text analyzers could be used to identify the language in which a text has been written (language detection), to identify keywords in the text (keyword extraction) or to summarize and categorize a text. You will calculate the letter (character) frequency in a text. Letter frequency measurements can be used to identify languages as well as in cryptanalysis. You will also explore the concept of n-grams in Natural Language Processing. N-grams are sequential patterns of n-words that appear in a document. In this project, we are just considering uni-grams and bi-grams. Uni-grams are the unique words that appear in a text whereas bi-grams are patterns of two-word sequences that appear together in a document.
Write a Java application that implements a basic Text Analyzer. The Java application will analyze text stored in a text file. The user should be able to select a file to analyze and the application should produce the following text metrics:
1. Number of characters in the text.
2. Relative frequency of letters in the text in descending order. (How the relative frequency that you calculated compares with relative letter frequencies in English already published?)
3. Number of words in the text.
4. The sizes of the longest and the shortest word.
5. The twenty most repeated uni-grams (single words) in the text in descending order.
6. The twenty most repeated bi-grams (pairs of words) in the text in descending order.
Test your program in the file TheGoldBug1.txt, which is provided.
Answers
The given program based on the question requirements is given below:
The Programpublic static void analyzeChar(String text)
{
text = text.toLowerCase();
char [] characters = new char[26];
int [] rep =new int[26];
//populate the array of characters
char ch = 'a';
for (int i =0; i < characters.length; i++)
{
characters[i] = ch;
ch++;
}
itz72
//System.out.println(Arrays.toString(characters));
//System.out.println(Arrays.toString(rep));
//how many times each characters repeats
for (int i =0 ; i < text.length (); i++ )
{
ch = text.charAt(i);
if(ch>= 'a'&& ch<= 'z')
{
rep[(int)(ch-'a')]++;
}
itz72
}
//show the number of repetitions
for (int i = 0; i < rep.length; i++)
{
System.out.println("character" + characters[i] + "reapeats"+ rep[i]);
}
}
itz72
public static void calcNumChar(String text)
{
System.out.println("The number of characters is: " + text.length());
}
public static String getText(String fileName) throws IOException
{
String line = "", allText = "";
//open the file
File file = new File(fileName);
Scanner inputFile = new Scanner(file);
//read the file
while(inputFile.hasNext())
{
line = inputFile.nextLine();
//System.out.println(line);
allText=allText + (" " + line);
}
itz72
//close the file
inputFile.close();
return allText;
}
public static String getFilename()
{
String file;
Scanner kb = new Scanner(System.in);
System.out.print("Enter the name of the file: ");
file = kb.nextLine();
return file;
}
}
This script contains numerous functions that aid in the examination and manipulation of written materials. This program determines the incidence of every letter present in the supplied text, tallies the overall character count, and includes the ability to import text from a file.
Read more about programs here:
https://brainly.com/question/26497128
#SPJ1
pls answer fast. Deciding when to quote an original e-mail is one challenge of effective communication. In which of the following e-mails should you quote the original e-mail? (select all that apply)
You respond to a price quote from a sales representative to tell them you need to think about the price.
You want to schedule a new meeting with a group you met with last week.
A coworker wants you to review an e-mail she is sending to a vender for clarity.
You want to start a new discussion with a contact who e-mailed you a newsletter a couple months ago.
Answers
Answer:
A,C
Explanation:
Answer: A&C
Explanation:
The ethical and appropriate use of a computer includes_____. Select 4 options.
Answers
The ethical and appropriate use of a computer encompasses several key principles that promote responsible and respectful behavior in the digital realm.
Four important options include:
1. Always ensuring that the information you use is correct: It is essential to verify the accuracy and reliability of the information we use and share to avoid spreading false or misleading content.
Critical evaluation of sources and fact-checking are vital in maintaining integrity.
2. Never interfering with other people's devices: Respecting the privacy and property rights of others is crucial. Unauthorized access, hacking, or tampering with someone else's computer or devices without their consent is unethical and a violation of their privacy.
3. Always ensuring that the programs you write are ethical: When developing software or coding, it is important to consider the potential impact of your creations.
Ethical programming involves avoiding harmful or malicious intent, ensuring user safety, respecting user privacy, and adhering to legal and ethical standards.
4. Never interfering with other people's work: It is essential to respect the intellectual property and work of others. Plagiarism, unauthorized use, or copying of someone else's work without proper attribution or permission is unethical and undermines the original creator's rights and efforts.
In summary, the ethical and appropriate use of a computer involves verifying information accuracy, respecting privacy and property rights, developing ethical programs, and avoiding interference with other people's work.
These principles promote a responsible and respectful digital environment that benefits all users.
For more such questions on ethical,click on
https://brainly.com/question/30018288
#SPJ8
The probable question may be:
The ethical and appropriate use of a computer includes_____.
Select 4 options.
-always ensuring that the information you use is correct
-never interfering with other people's devices
-always ensuring that the programs you write are ethical
-never interfering with other people's work
Database systems are exposed to many attacks, including dictionary attack, show with implantation how dictionary attack is launched?(Java or Python) ?
Answers
A type of brute-force attack in which an intruder uses a "dictionary list" of common words and phrases used by businesses and individuals to attempt to crack password-protected databases.
What is a dictionary attack?
A Dictionary Attack is an attack vector used by an attacker to break into a password-protected system by using every word in a dictionary as a password for that system. This type of attack vector is a Brute Force Attack.
The dictionary can contain words from an English dictionary as well as a leaked list of commonly used passwords, which, when combined with common character replacement with numbers, can be very effective and fast at times.
To know more about the dictionary attack, visit: https://brainly.com/question/14313052
#SPJ1