write a function that will accept a complex number c, and plot at point on a cartesian coordinate system with a circular marker. the plot should include both the x and y axes, plus a vector drawn from the origin to the location of c. include a test script and the input and output.
Answers
Using the knowledge in computational language in MATHLAB it is possible to write a code that write a function that will accept a complex number c, and plot at point on a cartesian coordinate system with a circular marker.
Writting the code:clc;
clear all;
format compact
Myplot(4+5i) %Plotting the number 4+5i
function Myplot(c)
x=real(c); %Real part
y=imag(c); %Imaginary part
xp=0:0.01:x; %Value of x
yp=(y/x).*xp; %Value of y for plotting vector
plot(x,y,'or',xp,yp,'-b','LineWidth',2); %Plots both
xlabel('x');ylabel('y') %Adds label
end
Is matplotlib same as MATLAB?Matplotlib is a library for making 2D plots of arrays in Python. Although it has its origins in emulating the MATLAB graphics commands, it is independent of MATLAB, and can be used in a Pythonic, object-oriented way.
See more about MATHLAB at brainly.com/question/18502436
#SPJ1

Related Questions
having a legitimate reason for approaching someone to ask for sensitive information is called what?
Answers
Who do many employees think is responsible for safety in the workplace
Answers
Answer:
Supervisors.
Explanation:
Supervisors have an overall responsability to ensure the safety of the workers. They must take every precaution reasonable in the circumstances the worker is found in.
A brief history of HCI (human-computer interaction). No
plagiarism
Answers
Human-Computer Interaction (HCI) is a field that focuses on the design, evaluation, and implementation of interactive computing systems for human use. It involves studying how users interact with computers and improving the usability and user experience of technology. The history of HCI can be traced back to the emergence of computers in the mid-20th century.
In the early days, computers were primarily used by scientists and engineers, and the interaction was limited to programming and command-line interfaces. However, with the advent of graphical user interfaces (GUIs) in the 1970s, HCI took a significant leap forward. The Xerox PARC research center played a crucial role in developing GUIs, introducing concepts like windows, icons, menus, and pointing devices.
The 1980s saw the rise of personal computers, and HCI became more mainstream. Researchers started exploring human factors, cognitive psychology, and usability engineering to enhance user interfaces. The field gained further recognition in the 1990s with the widespread adoption of the World Wide Web, which brought new challenges and opportunities for HCI professionals.
In the 21st century, HCI expanded its scope to encompass various domains, including mobile devices, wearable technology, virtual reality, and smart environments. Design principles such as user-centered design, user experience (UX) design, and iterative prototyping gained prominence. HCI researchers and practitioners continue to explore innovative interaction techniques, such as touchscreens, gesture recognition, voice interfaces, and natural language processing.
HCI has evolved into a multidisciplinary field, drawing insights from computer science, psychology, design, anthropology, and other disciplines. It emphasizes the importance of understanding user needs, preferences, and capabilities to create technology that is intuitive, efficient, and enjoyable to use.
Overall, the history of HCI reflects the continuous efforts to improve the interaction between humans and computers, with a focus on making technology more accessible, usable, and meaningful to people in various contexts of their lives.
Learn more about Human-Computer Interaction here: brainly.com/question/30456694.
#SPJ11
If you think about designing a really complicated webpage with HTML, what are some challenges that you could face?
Answers
Answer:
Some challenges you could face when designing a really complicated web page with HTML are that the functions are different and if you don't know the code or there isn't any code for what you want to do you would need to find another way to get the result you want.
Explanation:
it's what i put down (i got it right so i hope this can help)
Answer:
I'm just here so the other person can get brainliest <3
Explanation:
What are the three main elements common to all radio ads?
Answers
If my answers wrong please tell me :D
Who paid for the development of the internet, and why?.
Answers
Computer scientists whose research was heavily financed by the federal government, most notably through Darpa, the research arm of the Defense Department
Which layer in the Transmission Control Protocol/Internet Protocol (TCP/IP) model is responsible for delivering data between two nodes?
Answers
Answer:
Network.
Explanation:
The Transmission Control Protocol/Internet Protocol (TCP/IP) model is a standard networking protocol which allows network devices such as routers, switches, and host computers to interconnect and communicate with one another over a network. The Transmission Control Protocol/Internet Protocol (TCP/IP) model comprises of four (4) layers and these includes;
I. Application layer.
II. Transport layer.
III. Internet layer.
IV. Network layer.
The network layer in the Transmission Control Protocol/Internet Protocol (TCP/IP) model is responsible for delivering data between two nodes.
Basically, this layer known as network layer is the fourth layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model and it is typically responsible for the transmission of packets from one network device to another.
N an AWS design template, the "depends on" property of a resource is represented by an _________ color dot. Red Orchid Blue Black
Answers
Answer:
Black
Explanation:
Explicit dependencies in Amazon Web Services are used to determine the order in which resources are added or deleted on AWS Cloud Formation. If a user wishes to create explicit dependency, a line from the "dependson" dot located at the route is moved to the gateway-VPC attachment.
The "dependson" dot helps to specify which resource is created before another. It is signified by a black dot (*). It can be used to override parallelisms and also to determine when a wait condition becomes activated.
What would be the output for the following block of code?
price = 39.99
if price < 40 or price > 30:
print(“You qualify for a special discount!”)
else:
print(“Sorry, no discount for you.”)
A.
You qualify for a special discount!
B.
Sorry, no discount for you.
C.
Nothing would print.
D.
A syntax error would occur.
Answers
The output for the given block of code would be: A. You qualify for a special discount.
What is block of code?A block of code in computer programming refers to a cohesive lexical structure within source code that is clustered together. Blocks are composed of declarations and statements, either singularly or in multiples.
The Boolean condition, which states that price should be less than 40 or greater than 30, is found to be true as the current price of 39.99 satisfies both the criteria. Thus, the code enclosed in the if condition will run, displaying the message "You are entitled to a unique discount.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1
l
What do we call a statement that displays the result of computations on the screen?
ОА.
result statement
ов.
screen statement
OC output statement
OD
answer statement
OE.
input statement
Answers
Answer:
Output statement. The others do not make sense.
Color codes are stored as:
A) int
B) float
C) dec
D) Strings
Answers
Answer:
the correct answer is Strings, have a great evening yall
Explanation:
Which correctly calls the add() function?
def add(a, b, c):
print(a + b + c)
add(2; 4; 6)
add(2 4 6)
add(2, 4, 6)
add(2 + 4 + 6)
Answers
The correct option is add(2, 4, 6) ,it is a correct function call to the add() function.
How to correctly call a function?The correct function call to the add() function is add(2, 4, 6). In this call, the function is invoked with three arguments: 2, 4, and 6, which are separated by commas.
This syntax follows the standard convention for passing multiple arguments to a function in many programming languages.
The semi-colon (;) is not used to separate arguments in a function call. It is a syntax error to write add(2; 4; 6) as shown in the second option.
Similarly, in the third option add(2 4 6), the absence of commas between the arguments is incorrect and would result in a syntax error.
The fourth option add(2 + 4 + 6) is also incorrect because it attempts to perform addition within the function call itself.
Instead, the individual values should be passed as separate arguments to the function, as shown in the correct function call example.
Learn more about function
brainly.com/question/31062578
#SPJ11
In a day, a car passes n
kilometers. How many days does it take to travel a route of length m
kilometers?
The program receives as input in the first line a natural number n
and in the second line a non-negative integer m
. Python code
Answers
#Calculate days.
def calculateDay(m, n):
assert isinstance(m, int) and m >= 0, "m should be a natural number."
assert isinstance(n, int) and n > 0, "n shouldn't be negative."
return m/n
#Main function
def Main():
m, n = input().split()
print(f'Result: {calculateDay(int(m),int(n)):.2f} days.')
#Point.
if(__name__ == "__main__"):
Main()

power point cannot use

Answers
where can I go to follow other people on brainly?
Answers
Answer:
You have to send them a friend request. Click on their profile and that will take you to another link, with their info. Click add friend there.
Hope this helps.
Good Luck
Ashanti is using the PC version of Word, and she wants to create an interactive table of contents—pages that, when the user clicks on them, will take the user to that section of her document. Describe the exact process by which Ashanti could accomplish this task.
Answers
Answer:
Using some sort of link or hyperlink connected to the text would be a great way to do this, just highlight the text with your cursor and right click and click on hyperlink then set it up to go to the designated page.
Absolutely Brilliant if you to ask me!
what is the difference between windows 10 and windows 11
Answers
Answer: Windows 11 brings a brand-new, more Mac-like interface to the OS. It features a clean design with rounded corners and pastel shades. The iconic Start menu also moves to the centre of the screen along with the Taskbar. But you can move those back to the left, as they are in Windows 10, if you prefer.
Explanation:
Windows 11 will be a better operating system than Windows 10 when it comes to gaming. ... The new DirectStorage will also allow those with a high-performance NVMe SSD to see even faster loading times, as games will be able to load assets to the graphics card without 'bogging down' the CPU.
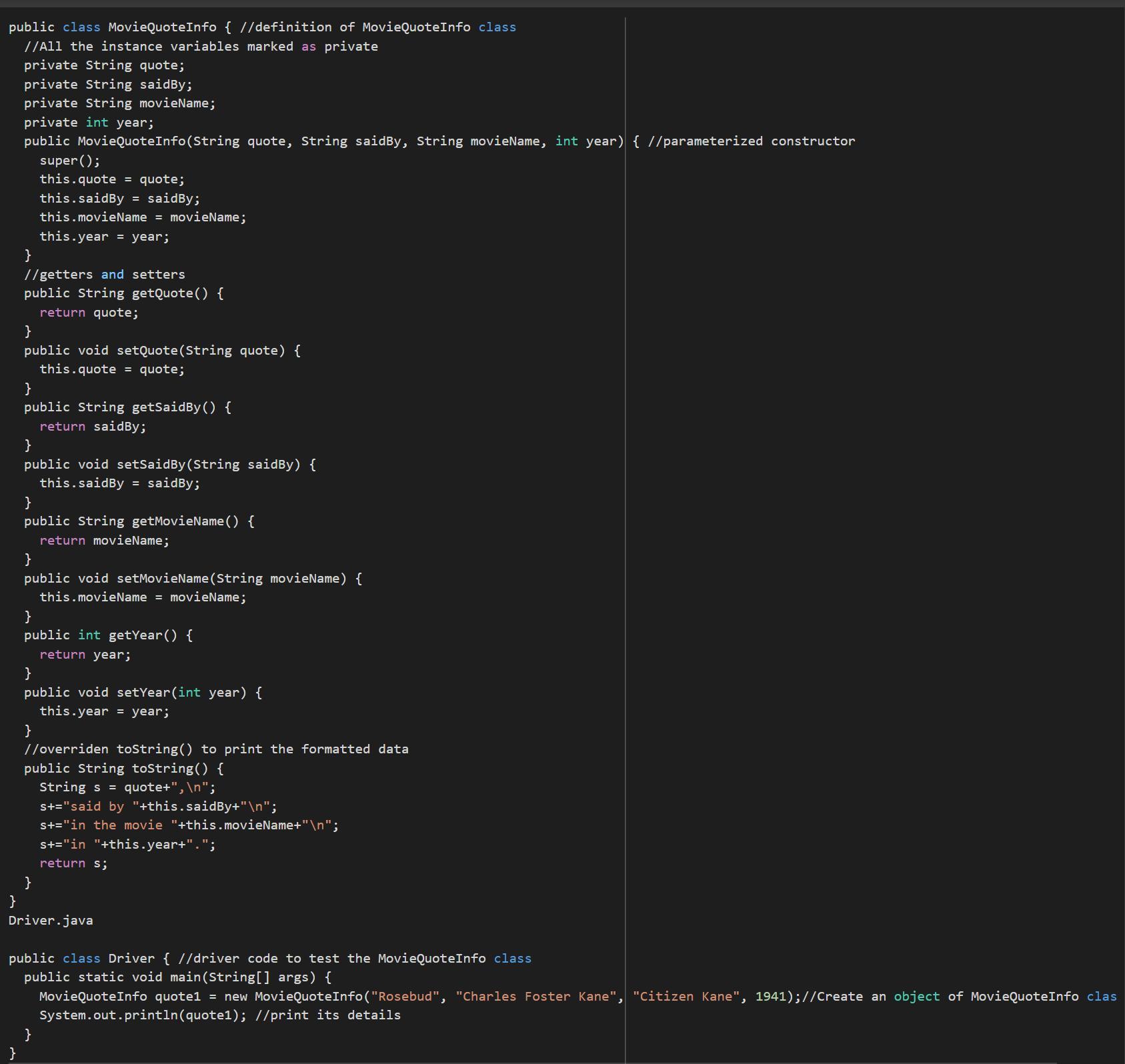
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
What would be the best command for a student to use to show their work on a math problem?
Ink Equation
Add Equation
Insert Symbols
Create Structures
Answers
Answer:
A, ink equation
Explanation:
Answer:
it is A, ink equation
Explanation:
In a single paragraph, write about the connections between web servers and web pages. Select and differentiate between their various characteristics and how they work together.
Edge please don't copy paste, 20 points
Answers
Answer:
web servers hold all the info that the website has on it, most servers hold multiple websites
Explanation:
Answer:
web servers hold all the info that the website has on it, most servers hold multiple websites
Explanation:
Question 2: John is 40 years old today (this is time 0). He is hoping to retire at age 65 (exactly on his 65th birthday) and actuarial tables suggest that he is likely to live until the age of 85. He wants to move to a Caribbean Island when he retires at age 65 (on his 65th birthday). He estimates that it will cost him $50,000 to make the move on his 65th birthday. Starting on his 65th birthday and ending on his 84th birthday (all withdrawals are at the beginning of the year), he will withdraw $40,000 per year for annual living expenses. Assume interest rate to be 5.5% for all calculations.
Use the timeline method to solve this question. (16)
What is the total amount required on the 65th birthday so that this amount can be used to make all the expenditures in retirement?
Answers
The total amount required on the 65th birthday so that this amount can be used to make all the expenditures in retirement is $568,596.99.
From his 65th birthday to his 84th birthday, he will withdraw $40,000 per year for annual living expenses. The interest rate is 5.5% for all calculations.
To calculate the total amount required on the 65th birthday, we need to find out the Present Value of all the future cash flows in today's dollars. This can be done using the PV function in Excel.
The cash flows can be divided into three parts:
1. Move to the Caribbean Island = $50,000 (one-time payment)
2. Annual living expenses from age 65 to age 84 = $40,000 x 20 = $800,000
3. Remaining balance at age 84 = $0 (since all the money will be spent by age 84)
Therefore, the total cash flows are $50,000 + $800,000 + $0 = $850,000.
To calculate the Present Value of these cash flows, we can use the following formula:
PV = CF1 / (1 + r)^1 + CF2 / (1 + r)^2 + ... + CFn / (1 + r)^n
Where,CF1 = Cash flow in year 1
CF2 = Cash flow in year 2
CFn = Cash flow in year n
PV = Present value of all cash flows
r = Interest rate (5.5%)
n = Number of years
To calculate the Present Value of all cash flows, we can use the PV function in Excel. The formula for the PV function is as follows:
PV(rate, nper, pmt, [fv], [type])
Where,rate = Interest rate
nper = Number of periods (years)
pmt = Payment per period
fv = Future value (optional, default is 0)
type = Timing of payment (optional, 0 or 1, default is 0)
Using this formula, we get:
PV(5.5%, 20, 40000, 0, 0) = $518,596.99
Therefore, the total amount required on the 65th birthday so that this amount can be used to make all the expenditures in retirement is $50,000 + $518,596.99 = $568,596.99 (rounded to the nearest cent).
Hence, the required amount is $568,596.99.
Learn more about present value at
https://brainly.com/question/32720837
#SPJ11
Lambda calculus for programming constructs 1. In the basic untyped lambda calculus, the boolean "true" is encoded as λx.λy.x, and "false" is encoded as λx. λy. y. That is, "true" takes in two arguments and returns the first, while "false" takes in two arguments and returns the second. These definitions of the boolean constants may seem strange, but they are designed to work with the "if-then-else" expression. The if-then-else expression is defined as λx. λy. λz. ((xy)z). Verify that these definitions do, indeed, make sense, by evaluating the following: a. (((λx.λy.λz.((xy)z)λu.λv.u)A)B) b. (((λx⋅λy⋅λz⋅((xy)z)λu⋅λv⋅v)A)B) Ocaml 2. Suppose a weighted undirected graph (where each vertex has a string name) is represented by a list of edges, with each edge being a triple of the type String ∗String ∗int. Write an OCaml function to identify the minimum-weight edge in this graph. Use pattern matching to solve this problem. 3. Solve the above problem by using the List.fold_left higher-order function.
Answers
Lambda calculus provides a formal system for expressing computations and programming constructs. The given questions involve verifying lambda calculus definitions and solving programming problems using OCaml.
How can we verify lambda calculus definitions and solve programming problems using OCaml?In lambda calculus, the given definitions of boolean constants and the "if-then-else" expression can be verified by evaluating expressions. For example, in part (a), we substitute the arguments A and B into the "if-then-else" expression and perform the required reductions step by step to obtain the final result.
For the weighted undirected graph problem in OCaml, we can define a function that takes the list of edges and uses pattern matching to find the minimum-weight edge. By comparing the weights of each edge and keeping track of the minimum, we can identify the edge with the smallest weight.
Alternatively, the List.fold_left higher-order function in OCaml can be used to solve the minimum-weight edge problem. By applying a folding function to accumulate the minimum weight while traversing the list of edges, we can obtain the minimum-weight edge.
By applying lambda calculus evaluation and utilizing the programming features of OCaml, we can verify definitions and solve problems effectively.
Learn more about solving programming
brainly.com/question/28569540
#SPJ11
When you try to run a SQL statement that contains a coding error, SQL Developer displays an error message that includes
an explanation of what you did wrong
the line and column number for the start of the error
the likely cause of the error
Answers
When we try to run a SQL statement that contains a coding error, SQL Developer displays an error message that includes an explanation of what you did wrong, as well as the line and column number for the start of the error.
SQL Developer is an integrated development environment (IDE) for working with SQL databases. It provides a user-friendly interface for writing and executing SQL statements, as well as debugging and error-handling capabilities. When a coding error is encountered, SQL Developer's error message provides valuable information to help identify and fix the issue. The message typically includes an explanation of the error, which helps you understand what went wrong in your SQL statement. It may indicate syntax errors, missing or incorrect keywords, or invalid data types, among other things. Additionally, the error message specifies the line and column number where the error was detected. This allows you to quickly locate the problematic section of your SQL statement and make the necessary corrections. By providing the exact position of the error, SQL Developer helps streamline the debugging process and facilitates efficient troubleshooting.
Overall, SQL Developer's error messages play a crucial role in assisting developers in identifying and resolving coding errors in their SQL statements, promoting more accurate and robust database programming.
Learn more about SQL Developer here:
https://brainly.com/question/30552602
#SPJ11
Write an assembly program to find the largest item in an array and store it in a variable named MAXIMUM. Hint: Use both Jump and loop instructions to write the program. Logic: Assume that the first item of the array is the minimum and store it in variable MAXIMUM Write a loop. Inside the loop, compare the each array item with the minimum If the array item is less than the MAXIMUM, update MAXIMUM with that array item. . Data Array WORD 10, 2, 23, 45, 21, 11 MAXIMUM WORD
Answers
Use the knowledge of computational language in C++ to write the a code assembly program to find the largest item.
How to write a maximum function in C++?To make it simpler the code is described as:
#include<bitd/stdc++.h>
Using namespace std;
Int main(){
Int arr[10]={10, 2, 23, 45, 21, 11};
Int min=INT_MAX;
Int max=INT_MIN;
for(int i=0;i<10;i++)
If(min<arr[i])min=arr[i];
for(int j=0;j<10;j++)
if(max>arr[j])max=arr[j];
Cout<<max<<” “<<min<<endl;
return 0;
See more about C++ code at brainly.com/question/19705654

Technician A states that in a brake-by-wire system, the computer detects a
panic stop if the driver quickly releases the accelerator. Technician B states
that brake-by-wire systems are not efficient in detecting panic stops. Who is
correct?
O a. Technician A
O b. Technician B
O c. Both Technician A and Technician B
O d. Neither Technician A nor Technician B
Answers
The brake-by-wire system can detect panic stops if the driver abruptly releases the accelerator, so Technician A is only partly accurate. Technician B is mistaken because panic stops can be accurately detected by brake-by-wire devices.
How well do brake-by-wire devices work at spotting panic stops?That period of time and distance can be cut down in a brake-by-wire device. The driver's abrupt release of the accelerator can be detected by the computer, which could be a sign of a panic halt.
What does an anti-lock braking device (MCQ) do?In order to keep tractive contact with the road surface and give the driver more control over the car, ABS works by preventing the wheels from locking up when braking.
To know more about panic stops visit:
https://brainly.com/question/28779956
#SPJ9
Which line of code will create an instance of the pet class?
class pet:
def __init__(self,strSpecies,strName):
self.species = strSpecies
self.petName = strName
myPetA = pet('dog', 'Spot'), myPetA = pet(self, 'dog', 'Spot'), myPetA = new pet('dog', 'Spot'), myPetA .pet() = 'dog', 'Spot'
Answers
Answer:
myPetA = pet(self, 'dog', 'Spot')
Explanation:
I mite be wrong
The line of code that will create an instance of the pet class is myPetA = pet (self, 'dog', 'Spot'). Option B is correct.
What is code?Computer code, or a set of instructions or a system of rules defined in a specific programming language, is a term used in computer programming (i.e., the source code). It is also the name given to the source code after a compiler has prepared it for computer execution.
Code, often known as source code, refers to text that a computer programmer has created in a programming language. Programming languages like C, C#, C++, Java, Perl, and PHP are examples.
Another less formal term for text produced in markup or style languages, such as HTML and CSS, is code (Cascading Style Sheets)
Therefore Option B is correct.
Learn more about code:
https://brainly.com/question/17204194
#SPJ2
Alarmed by new information-security threats, the U. S. Army is updating its policies to add more security measures on the use and safeguarding of:
Answers
The U.S. Army is implementing updated policies to enhance information security measures. These measures aim to address new threats and strengthen the use and protection of sensitive data.
In response to evolving information-security threats, the U.S. Army recognizes the need to update its policies and procedures to bolster the security of its data. The rapid advancement of technology and the increasing sophistication of cyberattacks require a proactive approach to safeguarding sensitive information.
The updated policies will encompass various aspects of information security, including but not limited to access control, data encryption, network security, and incident response. These measures aim to minimize the risk of unauthorized access, data breaches, and information theft. The Army will likely enforce stricter protocols for user authentication and authorization, implement robust encryption mechanisms to protect data both at rest and in transit, and enhance network monitoring and intrusion detection systems.
Furthermore, the updated policies will emphasize the importance of personnel training and awareness regarding information security best practices. Education and ongoing training programs will equip Army personnel with the knowledge and skills needed to identify and mitigate potential threats. Additionally, the policies may incorporate stringent measures for the secure handling and disposal of classified or sensitive information.
By implementing these enhanced security measures, the U.S. Army aims to safeguard its critical data, maintain operational readiness, and ensure the protection of national security interests. Regular reviews and updates to the policies will be essential to adapt to emerging threats and stay ahead of potential vulnerabilities in an ever-evolving information-security landscape.
learn more about information security measures here:
https://brainly.com/question/31749616
#SPJ11
Which of the following commands allows the user to round the edges off the selected segments?
Rotate
Stretch
Linetype
Filet
Answers
Answer:
rotate
hope it helps
Explanation:
to round the edges off selected segment rotate can do it
assuming standard 1500 byte ethernet max payloads: how many ipv4 fragments will be needed to transfer 2000 bytes of user data with a single udp send? and, how do the 2000 bytes get split over the frags?
Answers
Assuming the standard 1500-byte Ethernet maximum payload.The first fragment will contain the first 1480 bytes of data, and the second fragment will contain the remaining data.
The data will be split over the two fragments as follows: the first fragment will contain 1480 bytes of user data (the maximum amount of data that can fit in a single IPv4 fragment), and the second fragment will contain the remaining 520 bytes of user data (2000 - 1480 = 520)Ethernet frames have a maximum payload size of 1500 bytes, which includes the Ethernet header and trailer. When a larger packet (such as an IP packet) needs to be sent over Ethernet, it must be fragmented into smaller pieces that can fit in multiple Ethernet frames.
IPv4 packets can be fragmented, but only at the source host (i.e. the sender of the packet). When a packet is fragmented, the IP layer breaks it up into smaller pieces (fragments), each of which is small enough to fit in a single Ethernet frame.Each IPv4 fragment has its own IP header, which includes information about the packet as a whole (such as the source and destination IP addresses), as well as information about the individual fragment (such as its offset within the original packet). The last fragment of a packet has a special flag set in its IP header to indicate that it is the last fragment.
To know more about payload visit:
https://brainly.com/question/31807729
#SPJ11
A computer would do a better job than a human at solving lengthy, complex math problems. True False
Answers
Answer:
I would say true
Explanation:
Humans, by contrast, can master many things, from tying our shoes to cooking an omelet to solving complex math equations. The best AI hardly comes close to the incredible creativity and design of any human, and it’s an open question whether AI can ever become what its prophets claim. Second, when we make AI, we are basically copying our Creator.
Answer:
Its true and give the man brainlyest! or me. that would be nice too!
Explanation: