Write a function addUpSquaresAndCubes that adds up the squares and adds up the cubes of integers from 1 to N, where N is entered by the user. This function should return two values - the sum of the squares and the sum of the cubes. Use just one loop that generates the integers and accumulates the sum of squares and the sum of cubes. Then, write two separate functions sumOfSquares and sumOfCubes to calculate and return the sums of the squares and sum of the cubes using the explicit formula below.
Answers
Answer:
All functions were written in python
addUpSquaresAndCubes Function
def addUpSquaresAndCubes(N):
squares = 0
cubes = 0
for i in range(1, N+1):
squares = squares + i**2
cubes = cubes + i**3
return(squares, cubes)
sumOfSquares Function
def sumOfSquares(N):
squares = 0
for i in range(1, N+1):
squares = squares + i**2
return squares
sumOfCubes Function
def sumOfCubes(N):
cubes = 0
for i in range(1, N+1):
cubes = cubes + i**3
return cubes
Explanation:
Explaining the addUpSquaresAndCubes Function
This line defines the function
def addUpSquaresAndCubes(N):
The next two lines initializes squares and cubes to 0
squares = 0
cubes = 0
The following iteration adds up the squares and cubes from 1 to user input
for i in range(1, N+1):
squares = squares + i**2
cubes = cubes + i**3
This line returns the calculated squares and cubes
return(squares, cubes)
The functions sumOfSquares and sumOfCubes are extract of the addUpSquaresAndCubes.
Hence, the same explanation (above) applies to both functions
Related Questions
I lost the charger. How do I charge this camera without the charger?

Answers
Answer:
possibly a new battery????
Answer:
See below
Explanation:
This is from the manual for your camera:
(just plug the larger USB into a USB power source/brick/computer to charge the battery )

Matt is working with the business analysts to create new goals for his corporation. He does not agree with the way they make decisions in his company and is facing an issue of ______ with his work.
Answers
Matt is facing an issue of misalignment or disagreement with his work.
How can this be explained?Matt is facing considerable work-related difficulties due to a fundamental mismatch in decision-making within his company. He is in a conflicting position with the corporate analysts who are accountable for establishing fresh objectives for the company. The root of this argument could be attributed to variances in viewpoints, beliefs, or methods of reaching conclusions.
Matt is experiencing frustration as a result of facing challenges when it comes to collaborating effectively with the analysts due to their differing views. The problem of being misaligned not only affects his capability of making valuable contributions to goal-setting but also presents a more sweeping obstacle to the organization's cohesiveness and overall effectiveness.
Read miore about work problems here:
https://brainly.com/question/15447610
#SPJ1
Zoe wants to use an image file that will allow her to preserve all of the original
information. What file format should she use?
doc files
JPEGs
RAW files
MP3s
Answers
Since Zoe wants to use an image file that will allow her to preserve all of the original information. the file format should she use is known to be RAW files.
What are RAW files?A RAW file is known to be a term that is used for files that are uncompressed or those that are unprocessed image data taken by a digital camera or scanner's sensors.
Therefore, Since Zoe wants to use an image file that will allow her to preserve all of the original information. the file format should she use is known to be RAW files.
Learn more about RAW files from
https://brainly.com/question/27139052
#SPJ1
Answer:
Explanation:
I took the test

How to make a Java GUI application? Discuss each step needed.
Answers
Explanation:
Create a JFrame container
1- In the Projects window, right-click the NumberAddition node and choose New > Other .
2- In the New File dialog box, choose the Swing GUI Forms category and the JFrame Form file type. Click Next.
3- Enter NumberAdditionUI as the class name.
4- Enter my. numberaddition as the package.
5- Click Finish.
Which programming language uses objects? C++ ALGOL Pascal BASIC
Answers
Answer:
C++
Explanation:
I am a c++ dev
Answer:
its A
C++
Explanation:
Youre amazing
Assign 75 to number_of_minutes and convert the number of minutes to hours and minutes. In your program you must use the variable number_of_minutes, module and integer division operators. Your output should display as: 75 minutes is 1 hours and 15 minutes.
Answers
To write a program to find hours and minute we divide the number with 60 and the find the remainder.
Code:
number_of_minutes = 75
# Calculate hours and minutes
hours = number_of_minutes // 60 # Integer division operator to get the number of hours
minutes = number_of_minutes % 60 # Module operator to get the remaining minutes
# Display the result
print(f"{number_of_minutes} minutes is {hours} hours and {minutes} minutes.")
In the above program, we first assign the value 75 to the variable number_of_minutes.
Then, we use the integer division operator (//) to divide number_of_minutes by 60, which gives us the number of hours. This value is stored in the variable hours.
Next, we use the module operator (%) to calculate the remaining minutes after dividing by 60, which are stored in the variable minutes.
Finally, we use the print function to display the output in the desired format, using f-strings (formatted strings) to incorporate the variables into the output message.
When you run this program, the output will be: "75 minutes is 1 hour and 15 minutes."
This indicates that 75 minutes can be expressed as 1 hour and 15 minutes.
For more questions on program
https://brainly.com/question/26134656
#SPJ8
what gases are involved in the process of respiration
Answers
Answer: (O(2)), nitric oxide (NO), and carbon dioxide (CO(2))
Explanation:
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
Why is it important to use a high sample rate when recording sound?
OA. It allows the computer to convert the sound wave into binary code.
OB. It means that the sound wave is making more vibrations per second.
C. It produces a more accurate copy of the sound wave.
D. It improves the original sound wave coming from the sound source.
Answers
The correct answer is C. It produces a more accurate copy of the sound wave.
When recording sound, the sample rate refers to the number of times per second that the audio signal is measured and converted into a digital value. A higher sample rate means that the audio signal is being measured and digitized more frequently, which produces a more accurate representation of the original sound wave.
Using a high sample rate is important because it allows for a more precise representation of the audio signal. If the sample rate is too low, some of the audio signal may be lost or distorted, which can result in poor sound quality or artifacts such as aliasing.
It is worth noting that a high sample rate also requires more storage space and processing power, so there is a tradeoff between the quality of the audio and the resources required to store and process it.
Answer: it produces a more accurate copy of the sound wave
Explanation: I took the test
To classify wireless networks by coverage, which of the following are wireless networks?
A- WPAN
B-WLAN
C- WMAN
D- WWAN
Answers
Answer:
B -WLAN
Explanation:
Use the edit icon to pin, add or delete clips.
You are given an array of integers, each with an unknown number of digits. You are also told the total number of digits of all the integers in the array is n. Provide an algorithm that will sort the array in O(n) time no matter how the digits are distributed among the elements in the array. (e.g. there might be one element with n digits, or n/2 elements with 2 digits, or the elements might be of all different lengths, etc. Be sure to justify in detail the run time of your algorithm.
Answers
Answer:
Explanation:
Since all of the items in the array would be integers sorting them would not be a problem regardless of the difference in integers. O(n) time would be impossible unless the array is already sorted, otherwise, the best runtime we can hope for would be such a method like the one below with a runtime of O(n^2)
static void sortingMethod(int arr[], int n)
{
int x, y, temp;
boolean swapped;
for (x = 0; x < n - 1; x++)
{
swapped = false;
for (y = 0; y < n - x - 1; y++)
{
if (arr[y] > arr[y + 1])
{
temp = arr[y];
arr[y] = arr[y + 1];
arr[y + 1] = temp;
swapped = true;
}
}
if (swapped == false)
break;
}
}
The greater than sign(>) is an example of
Answers
Answer:
charactor
Explanation:
It's used in arythmetic calculation
Which of the following functions will correctly return True if it is passed an odd integer value for x?
I.
def is_odd (int x) :
return x % 2 == 1
II.
def is_odd (int x) :
return x / 2 == 1
III.
def is_odd (int x) :
if x % 2 == 1:
return True
else:
return False
Answers
Your computer is on a Public Network if it has an IP address of 161.13.5.15.
What is a Private Network?A private network on the Internet is a group of computers that use their own IP address space. In residential, business, and commercial settings, these addresses are frequently used for local area networks.
Private Network IP address ranges are defined under IPv4 and IPv6 standards, respectively. Private IP addresses are used in corporate networks for security since they make it difficult for an external host to connect to a system and also limit internet access to internal users, both of which contribute to increased security.
Therefore,Your computer is on a Public Network if it has an IP address of 161.13.5.15.
To learn more about Private Network, use the link given
brainly.com/question/6888116
#SPJ1
Which function deletes the first occurence of 3 in a list named listB ?
listB.clear(3)
listB(3)
listB delete(3)
listB.remove(3)
Answers
Answer:
\(listB.remove(3)\)
Explanation:
Given
Options A to D
Required
Which deletes the first occurrence of 3
The options show that the question is to be answered using the knowledge of Python.
So, we analyze each of the options using Python syntax
(a) listB.clear(3)
In python, clear() is used to delete all elements of a list, and it does not take any argument i.e. nothing will be written in the bracket.
Hence, (a) is incorrect
(b) listB(3)
The above instruction has no meaning in Python
(c) listB delete(3)
The above instruction as written is an invalid syntax because of the space between listB and delete.
Also, it is an invalid syntax because lists in Python do not have the delete attribute
\((d)\ listB.remove(3)\)
This removes the first occurrence of 3
Answer: listB delete(3)
Explanation: got it right on edgen
write a function insert_string_multiple_times() that has four arguments: a string, an index into the string, a string to insert, and a count. the function will return a string with count copies of the insert-string inserted starting at the index. note: you should only write the function. do not put any statements outside of the function. examples: insert_string_multiple_times('123456789',3,'xy',3) '123xyxyxy456789' insert_string_multiple_times('helloworld',5,'.',4) 'hello....world' insert_string_multiple_times('abc',0,'a',2) 'aaabc' insert_string_multiple_times('abc',0,'a',0) 'abc'
Answers
Answer:
Written in Python:
def insert_string_multiple_times(str1,indto,str2,count):
splitstr = str1[:indto]
for i in range(count):
splitstr+=str2
splitstr +=str1[indto:]
print(splitstr)
Explanation:
This line defines the method
def insert_string_multiple_times(str1,indto,str2,count):
In the above definition:
str1 represents the string
indto represents index to insert a new string
str2 represents the new string to insert
count represents the number of times str2 is to be inserted
This gets the substring from the beginning to indto - 1
splitstr = str1[:indto]
This performs an iterative operation
for i in range(count):
This appends str2 to the first part of the separated string
splitstr+=str2
This appends the remaining part of the separated string
splitstr +=str1[indto:]
This prints the new string
print(splitstr)
What is the difference between a prefix and postfix in Java?
Answers
Answer:
prefix comes first
Explanation:
pre means before, and post means after.
Chinh wants to have a program print, "Sorry, but that isn’t one of your options" until the user enters the correct information. What should be used to do this?
a database
import
a while loop
a for loop
Answers
Answer:
I really beleive its a while loop
Explanation:
Chinh wants to have a program print, "Sorry, but that isn’t one of your options" until the user enters the correct information so a while loop should be used to do this.
What is a while loop ?A "While" Loop is used to copy a selected block of code an unknown range of instances, till a circumstance is met. For example, if we need to invite a person for a variety of among 1 and 10, we do not know how in many instances the person can also additionally input a bigger range, so we preserve asking "whilst the range isn't among 1 and 1.
The whilst loop is used whilst we do not know the range of instances it's going to repeat. If that range is infinite, or the Boolean circumstance of the loop by no means receives set to False, then it's going to run forever.
Read more about the a database
https://brainly.com/question/26096799
#SPJ2
Which of the following does PXE use?
a) USB
b) DVD-ROM
c) CD-ROM
d) NIC
Answers
Answer:
The answer is d) NIC.
Explanation:
PXE Stands for Preboot Execution Environment and a PXE uses an NIC also know as Network Interface Controller. For an example: If you have a DELL Inspiron 8500 and you couldn't get it to work you would need to go through all boot-up system including a Preboot Execution Environment in the booting code protocols it would say connecting to NIC after 6 seconds it would say NIC connected then it would search for a boot device after a few munities since the DELL Inspiron 8500 is obsolete you would get this message:
No Boot Device found
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least 65 percent transfer efficiency.
What is the transfer efficiency
EPA lacks transfer efficiency requirement for auto refinishing spray guns. The EPA regulates auto refinishing emissions and impact with rules. NESHAP regulates paint stripping and coating operations for air pollutants.
This rule limits VOCs and HAPs emissions in automotive refinishing. When it comes to reducing overspray and minimizing wasted paint or coating material, transfer efficiency is crucial. "More efficiency, less waste with higher transfer rate."
Learn more about transfer efficiency from
https://brainly.com/question/29355652
#SPJ1
your own choice Identify an organisation of whether factual of fiction with the following Consideration:The three best os to intergrate with the advantages and disadvantages
Answers
Answer:
sorry dont know
Explanation:
Which option of the auto correct to enables you to add and delete words that do not follow abbreviation rules
Answers
It is possible to add or remove words that do not adhere to abbreviation rules by using the replace text as you write feature in the AutoCorrect tool.
What purposes does AutoCorrect serve?
The AutoCorrect tool allows you to repair typos, capitalization mistakes, and misspelt words as well as automatically insert symbols and other content. You can change the entries in this list, but by default, AutoCorrect utilises a standard list of frequent misspellings and symbols. Autocorrection, often known as text replacement, replace-as-you-type, or just autocorrect, is an automatic data validation feature that is frequently seen in word processors and text editing interfaces for smartphones and tablet computers.
To know more about using visit:-
https://brainly.com/question/8723368
#SPJ1
Advanced Sounds is engaging in a full upgrade of its Windows Server 2003 network to Windows Server 2008. The upgrade includes using Windows Server 2008 Active Directory. Advanced Sounds has pioneered many technological innovations and is very concerned about keeping its network and computer systems secure. Advanced Sounds Information Technology (IT) Department hires you to help them implement Windows Server 2008 Active Directory. Assume the following:
All email servers have been consolidated back in the New York City Complex.
Most all the other applications running on Windows Servers are distributed at all sixteen locations.
Each location at minimum has a file server, a print server and a local application server.
All locations have adequate Wide Area network connections with available capacity; 10 Mbps links
The New York location has enough network capacity to serve all 16 locations.
There are 500 people at the New Your City complex.
There are 200 people at the Quebec City location and 200 at the Montreal location.
There are 40-50 people at each outlet store.
Advanced Sounds IT Department has formed a small installation planning committee consisting of the IT server operations manager, two system programmers, the current Active Directory administrator, and you. After the first meeting they have asked you to prepare a small report to address the following questions:
A. What information is required as input to the initial installation involving Active Directory? a=
B. How many Active directory servers do you propose?
C. Where will the Active directory server(s) be located?
Answers
Answer:
cs
Explanation:
Write a 250-word essay on the benefits and dangers of collecting and storing personal data on online databases. Things to consider:
Does the user know their data is being collected?
Is there encryption built into the system?
Is that encryption sufficient to protect the data involved?
Does collecting the data benefit the end user? Or just the site doing the collecting?
Answers
Answer:
The collection and storage of personal data on online databases has both benefits and dangers. On the one hand, collecting and storing data can be incredibly useful for a variety of purposes, such as personalized recommendations, targeted advertising, and improved user experiences. However, it's important to consider the risks and potential consequences of this practice, particularly in regards to privacy and security.
One concern is whether or not users are aware that their data is being collected. In some cases, this information may be clearly disclosed in a site's terms of service or privacy policy, but in other cases it may not be as transparent. It's important for users to be aware of what data is being collected and how it is being used, so that they can make informed decisions about whether or not to share this information.
Another important factor is the level of encryption built into the system. Encryption is a way of encoding data so that it can only be accessed by authorized parties. If a system has strong encryption, it can help to protect the data involved from being accessed by unauthorized users. However, if the encryption is weak or flawed, it may not be sufficient to protect the data. It's important to carefully consider the strength and reliability of any encryption used on a system that stores personal data.
Ultimately, the benefits and dangers of collecting and storing personal data on online databases will depend on the specific context and how the data is being used. It's important to weigh the potential benefits and risks, and to carefully consider whether the collection and storage of this data is truly in the best interests of the end user, or if it is primarily benefiting the site doing the collecting.
Explanation:
Difference between Python vs Pandas?
Answers
Python and Pandas are not directly comparable as they serve different purposes. Here's an explanation of each:
Python:
Python is a general-purpose programming language known for its simplicity and readability. It provides a wide range of functionalities and can be used for various tasks, including web development, data analysis, machine learning, and more. Python has a large standard library and an active community, making it versatile and widely used in different domains.
Pandas:
Pandas, on the other hand, is a powerful open-source library built on top of Python. It is specifically designed for data manipulation and analysis. Pandas provides easy-to-use data structures, such as Series (one-dimensional labeled arrays) and DataFrame (two-dimensional labeled data tables), along with a variety of functions for data cleaning, transformation, filtering, grouping, and aggregation.
In essence, Python is the programming language itself, while Pandas is a Python library that extends its capabilities for data analysis and manipulation. You can use Python to write code for a wide range of purposes, while Pandas is focused on providing efficient and convenient tools for working with structured data.
for similar questions on Python.
https://brainly.com/question/26497128
#SPJ8
Are AWS Cloud Consulting Services Worth The Investment?
Answers
AWS consulting services can help you with everything from developing a cloud migration strategy to optimizing your use of AWS once you're up and running.
And because AWS is constantly innovating, these services can help you keep up with the latest changes and ensure that you're getting the most out of your investment.
AWS consulting services let your business journey into the cloud seamlessly with certified AWS consultants. With decades worth of experience in designing and implementing robust solutions, they can help you define your needs while executing on them with expert execution from start to finish! AWS Cloud Implementation Strategy.
The goal of AWS consulting is to assist in planning AWS migration, design and aid in the implementation of AWS-based apps, as well as to avoid redundant cloud development and tenancy costs. Project feasibility assessment backed with the reports on anticipated Total Cost of Ownership and Return on Investment.
Learn more about AWS consulting, here:https://brainly.com/question/29708909
#SPJ1
hello hello . please help me
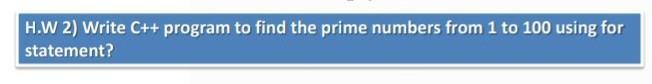
Answers
Answer:
#include <iostream>
using namespace std;
int main() {
int num, check=0;
for(int num = 1; num<=100;num++){
for(int i = 2; i <= num/2; i++) {
if(num % i == 0) {
check=1;
break; } }
if (check==0) { cout <<num<<" "; }
check = 0;
}
return 0;
}
Explanation:
This line declares num as integer which represents digits 1 to 100.
A check variable is declared as integer and initialized to 0
int num, m=0, check=0;
This for loop iterates from 1 to 100
for(int num = 1; num<=100;num++){
This iterates from 2 to half of current digit
for(int i = 2; i <= num/2; i++) {
This checks for possible divisors
if(num % i == 0) {
If found, the check variable is updated to 1
check=1;
And the loop is terminated
break; } }
The following if statement prints the prime numbers
if (check==0) { cout <<num<<" "; }
check = 0;
}
What is generated from the following HTML code:
Hello
Hello
Hello
Answers
Answer:
<h1>Hello</h1>
<h1>Hello</h1>
<h1>Hello</h1>
Explanation:
the h1 tag is depending on what size you want it to be. You can go from h1 to h6 and beyond
Answer: Hi, Hello, whatsup, konichiwa, sup,
what is the role of product management in agile safe
Answers
Product management plays a crucial role in Agile SAFe (Scaled Agile Framework) by defining desirable, viable, feasible, and sustainable solutions that meet customer needs and supporting development across the product life cycle.
In an Agile SAFe environment, product management acts as the bridge between the customer and the development teams. They are responsible for understanding customer needs, gathering feedback, and translating those needs into actionable requirements.
By collaborating with stakeholders, product management ensures that the product vision aligns with customer expectations.
To define desirable solutions, product management conducts market research, user interviews, and analyzes customer feedback. They identify market trends, user pain points, and prioritize features accordingly.
They work closely with customers to gather insights and validate product ideas through iterative feedback loops.
Viable solutions are determined by evaluating market demand, competitive landscape, and business objectives. Product management considers factors like revenue potential, market share, and return on investment to ensure the product is financially sustainable.
Feasible solutions require close collaboration with development teams. Product management works with engineering, design, and other teams to assess technical feasibility, define scope, and establish delivery timelines.
They engage in Agile ceremonies such as sprint planning, backlog refinement, and daily stand-ups to facilitate efficient development.
Sustainable solutions are designed with long-term success in mind. Product management focuses on creating scalable, adaptable products that can evolve with changing customer needs and market dynamics. They continuously monitor and analyze product performance, customer feedback, and market trends to make informed decisions and drive iterative improvements.
In summary, product management in Agile SAFe is responsible for understanding customer needs, defining desirable and viable solutions, ensuring technical feasibility, and supporting development teams throughout the product life cycle to deliver sustainable products that meet customer expectations.
For more such questions Product,click on
https://brainly.com/question/28776010
#SPJ8
Which statements are true about the OSI reference model? The OSI model developed in the 1970s and 1980s. OSI stands for Open Systems Interface. OSI developed as two independent projects. These projects merged in 1980. The OSI reference model consists of seven layers. The model numbers these layers from 0 to 6. A layer can communicate with the layer above and below it. However, any layer can communicate with any other layer on another device.
Answers
Regarding the OSI reference model, the following statements are accurate: The Open Systems Interconnection, not Open Systems Interface, concept was created in the 1970s and 1980s.
Which of the following statements on the differences between the TCP/IP reference model and the OSI reference model is true?Transmission Control Protocol/IP (TCP/IP) and Open Systems Interconnection (OSI) are acronyms for different protocols. Whereas OSI takes a vertical approach, TCP/IP uses a horizontal approach.
Which of the following claims about the OSI model is true?Application, Presentation, Session, Transport, Network, Data Link, and Physical Layer are the seven levels of the OSI reference model. Open System Interconnect, or OSI for short, is a generic model.
To know more about OSI visit:-
https://brainly.com/question/25404565
#SPJ1
Drag each statement to the correct location.
Determine which are system software and which are application software.
device drivers OS system utilities
graphics software
System Software
word processors
media players
Application Software.
Answers
Drag each statement to the correct location.
The system software
device drivers OS system utilitiesThe application software.
A graphics softwareword processorsmedia playersApplication Software.What is System Software?Software is known to be a term that connote a kind of an organized composition of computer data and instructions.
Note that There are two types of software which are said to be application software and system software.
Hence, Drag each statement to the correct location.
The system software
device drivers OS system utilitiesThe application software.
A graphics softwareword processorsmedia playersApplication Software.Learn more about software from
https://brainly.com/question/1538272
#SPJ1