Write a C program that calculates the users phone bill each month. The phone company charges all users a flat rate of $70 for their unlimited text, data and call plan for a single line. Each additional line is $35 more. Prompt the user to input the total number of phones on their account. Then, calculate and print their total due each month. For example, one line would be $70, two lines would be $105, and three lines would be $140
Answers
the program includes a check to ensure that the total number of lines is a positive integer.
Certainly! Here's an example of a C program that calculates the monthly phone bill based on the number of lines:
```c
#include <stdio.h>
#define BASE_PRICE 70
#define ADDITIONAL_PRICE 35
int main() {
int totalLines;
int totalDue;
printf("Enter the total number of phones on your account: ");
scanf("%d", &totalLines);
if (totalLines <= 0) {
printf("Invalid input. Number of lines must be a positive integer.\n");
return 1; // Exit the program with an error status
}
totalDue = BASE_PRICE + (totalLines - 1) * ADDITIONAL_PRICE;
printf("Your total monthly bill is: $%d\n", totalDue);
return 0;
}
```
In this program, we use `BASE_PRICE` to represent the flat rate of $70 for the first line, and `ADDITIONAL_PRICE` to represent the additional cost of $35 for each additional line. The user is prompted to input the total number of phones on their account using `scanf()`, and the program calculates the total due by applying the appropriate pricing logic.
Note that the program includes a check to ensure that the total number of lines is a positive integer. If the user enters a non-positive value or a non-integer value, an error message is displayed, and the program exits with an error status.
You can compile and run this program using a C compiler to test it with different input values.
To know more about Coding related question visit:
https://brainly.com/question/17204194
#SPJ11
Related Questions
¿ Porque la madera presenta mayor resistencia a ser cortada en sentido travesal que en sentido longitudinal
Answers
La madera es más fuerte en la dirección paralela al grano. Debido a esto, las propiedades de resistencia y rigidez de los paneles estructurales de madera son mayores en la dirección paralela al eje de resistencia que perpendicular a él
3 things in terms of photography to learn about.
Answers
The three important principle in photography are;
Photography is about light. Without it, you couldn't even take images, let alone excellent ones.
The quality of light varies from one to photograph, yet it is always what gives your photographs their underlying structure. It doesn't get any more basic than that.
Most of us snap photos because something catches our attention.
Unsurprisingly, that "something" is your subject.
If you're explaining a photograph to someone else, the topic is most likely the first thing you'll mention.
Finally, the composition is the third and most important aspect of every shot.
Simply said, composition is the arrangement of the things in your shot. It includes your camera position, the connections between photo elements, and the things you accentuate, deemphasize, or altogether eliminate. Composition is the method through which you communicate your tale.
Learn more about photography:
https://brainly.com/question/30685203
#SPJ1
compare and contrast peer-to-peer and master-slave replication models from the perspective of the cap theorem. why is it easier to maintain higher degrees of availability in a peer-to-peer replicated data model?
Answers
In the CAP theorem, consistency, availability, and partition tolerance are the three characteristics that must be balanced when designing distributed systems. It is easier to maintain higher degrees of availability in a peer-to-peer replicated data model because it does not depend on a single node to process write requests.
This theorem states that any distributed system can only have two of these three attributes at a time. Therefore, while evaluating a replication model, we must consider which attribute is more important. Two types of replication models are Master-Slave and Peer-to-Peer replication models. Let us compare and contrast the two models from the perspective of the CAP theorem.
Master-Slave replication model: Consistency and Partition tolerance are the two most important attributes in the Master-Slave replication model. It is the most popular replication model used by relational database management systems. It follows a strict, centralized approach that allows one machine to serve as the master node, which is in charge of processing all write requests. The slave nodes, on the other hand, only accept read requests. This creates a bottleneck since only the master node can process write requests, causing the entire system to be unavailable in the event of a failure.
Peer-to-Peer replication model: Availability and partition tolerance are the two most important attributes in the Peer-to-Peer replication model. It is a decentralized method that allows nodes to communicate directly with one another without the need for a centralized control system. Each node in the network acts as both a producer and a consumer of data, allowing for peer-to-peer interaction. This replication model is self-healing and can recover from failures quickly, making it more reliable than the Master-Slave replication model. Since all nodes can process both read and write requests, there is no bottleneck, making it easier to maintain higher degrees of availability.
It is highly resilient to failure since it is a decentralized method that allows nodes to communicate directly with each other. Therefore, the data is replicated across many nodes in the network, making it highly available.
Learn more about peer-to-peer and master-slave replication :https://brainly.com/question/28474766
#SPJ11
The owner tells you that in the future, CSM Tech Publishing might need system fault tolerance to ensure that there's little or no downtime because this critical application will eventually be accessed at all times of the day and night. For now, he's just concerned about getting the system up and running. You check the existing server's capacity and determine that the new application's memory and disk requirements will likely exceed the existing server's 4 GB capabilities. The owner explains that there's enough budget for a new server, so you should plan for growth. As an aside, he mentions that because all his employees sign in at about the same time, the time it takes to sign in has been increasing. You need to come up with specifications for a new server. Describe some hardware features you plan to recommend for this new server, in particular the CPU architecture, number of CPUs, amount of RAM, and disk system. Explain your answers.
Answers
Answer:
Follows are the solution to this question:
Explanation:
New useful server specifications can be defined as follows:
Space planning is enough to store units should also be available to handle the current load. The goals shall become converted through strategies Security was its key problem, thus the technology must at least be safeguarded by good chemical stability as well as virus protection.
RAM is also to be improved. Its 8 GB is viewed as good. The amount of redskins would increase performance if they had been increased. Numerous CPUs will be connected to a system for the procedure and is as required.
Its hard drive must be linked to structures with such a temperature of 1-2 TB more than. Besides that, the fault-tolerant equipment, tracking tools, reporting tools, audit tools, and data centers are frequently used.
Tom wants to send some songs to one of his friends by short-range wireless connection in his home. Which technology would suit this task?
a. Wifi
b. WLAN
c. Bluetooth
d. PAN
Answers
Answer:
a
Explanation:
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
the primary reason for data normalization is to: group of answer choices optimize access or processing speed for quicker reports better communicate requirements to the users optimize storage requirements by reducing data redundancy test the efficiency and effectiveness of database designers
Answers
When a relational database's attributes and tables are organized to reduce data redundancy, this process is known as database normalization.
Why does normalization exist in the first place?Reducing or getting rid of redundant data storage is referred to as normalization. Avoiding issues resulting from updating redundant data is normalization's main goal. The 3NF-3rd Normal Form, for instance, uses a design approach to normalization that could lead to a lot of tables.
What could normalizing a database be used for?The purpose of normalizing a database is to reduce redundancy (duplicate data) and make sure that only related data is kept in each table. Additionally, it stops any problems brought on by updates, insertions, and deletions in the database.
To know more about database visit :-
https://brainly.com/question/6447559
#SPJ4
1. What is material science?
Answers
Answer:
Explanation:
The study of the properties of solid materials and how those properties are determined by a material’s composition and structure is material science.
Answer:
The scientific study of properties and applications of materials of construction or manufacture.
Explanation:
Information below:

Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
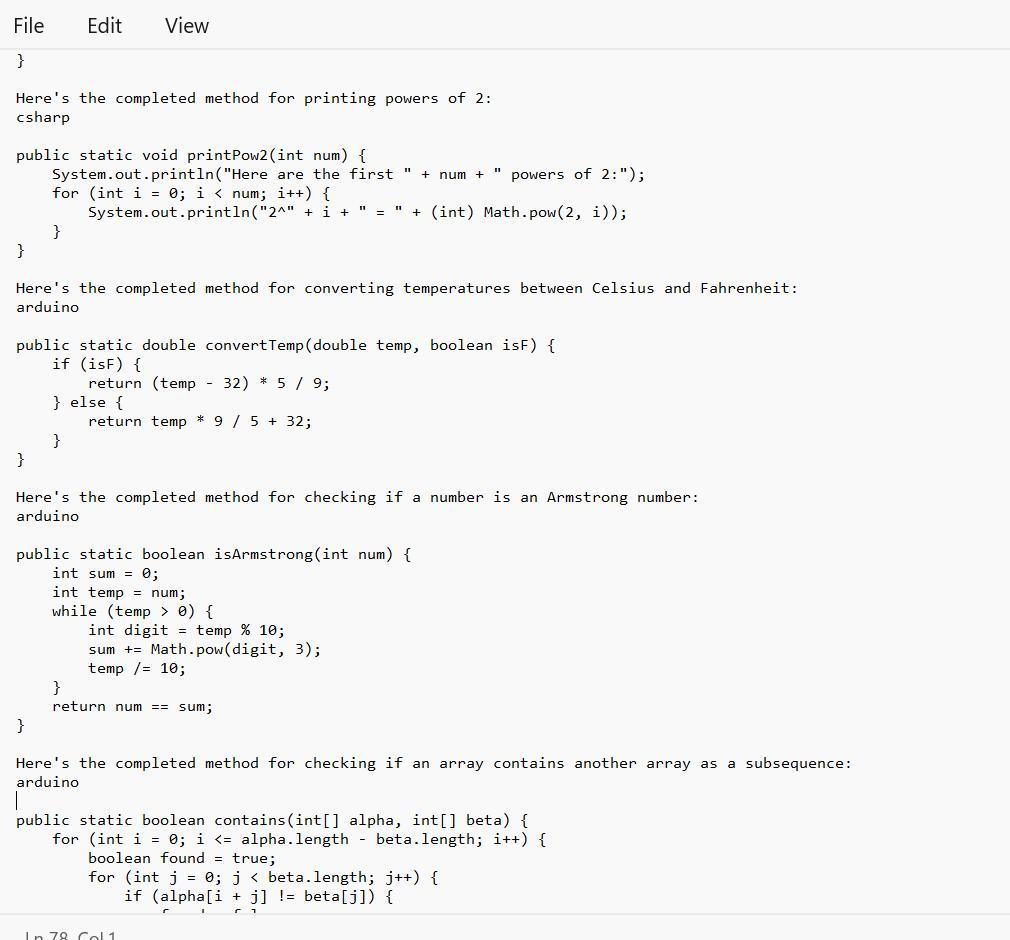
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


Ayy so in your opinion what is they best XXL freestyle no wrong answers except for Coi Leray and YK Osiris, my personally favorite is Denzel Curry's.
Answers
What is the value of z after the following statements have been executed? int x = 4, y = 33; double z; z = (double) (y / x); group of answer choices
Answers
The value of z after the below statements have been executed: int x = 4, y = 33; double z; z = (double) (y / x) is 8.0
What is coding?The term Coding is known to be often called called computer programming, and it is said to be the ways that people do talk or communicate with computers.
Note that Code tells a computer the right actions to take, and based on the above, the value of x is doubled and so it will be 8.
Therefore, The value of z after the below statements have been executed: int x = 4, y = 33; double z; z = (double) (y / x) is 8.0
Learn more about coding from
https://brainly.com/question/22654163
#SPJ1
Write code that sets the value of the variable num_cards to seven if its current value is less than seven. otherwise, don't change the value. assume that num_cards already has an initial value.
Answers
The program to illustrate the information is given below.
How to express the code?num_cards = 5 #Assuming value of num_cards is 5 (You can take any value you want)
if num_cards<7 :
num_cards=7
print(num_cards)
def dice_eval(x,y):
if (x+y== 7)|(x+y== 11) :
return "Winner!"
elif (x+y== 2)|(x+y== 3)|(x+y== 12) :
else:
a = x+y
if a<10:
return "Point is 0"+ str(a)
else :
return "Point is " + str(a)
Example -
dice_eval(0,8) returns 'Point is 08'
Learn more about programs on:
https://brainly.com/question/26642771
#SPJ1
pls help ASAP!! will give brainliest

Answers
Answer:
a is the CPU
b is the ram
c is the mother board
d is the power supply
e is the hard drive
Explanation:
a is the brain of the computer it directs things
b is the temporary storage
c the mother board processes things
d this gives the computer power
e is the long storage
why is this python code giving me problems?
This is having the user input a decimal number and the code has to round it up to the 2nd decimal place. This code is giving me problems, please fix it.
num3 = int(input("Please input a decimal number:")
num3 = int(round(num3, 2))
print ("your decimal rounded to the 2nd decimal place is:", x)
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The given code in this program has syntax errors.
In the given code, at line 1, input will cast or convert to int. It will generate an error on the second line because integer numbers can't be rounded. In simple, integer numbers don't have decimals. So, to correct the line you must use float instead of int.
In the second line, you need also to emit the int casting (data type conversion), because you have already converted the input into the float. In line 3, the second parameter to print function is num3, not x.
So the correct lines of the python code are given below:
num3 = float(input("Please input a decimal number:"))
num3 = (round(num3, 2))
print ("your decimal rounded to the 2nd decimal place is:", num3)
When you will run the above bold lines of code, it will run the program successfully without giving you any syntax and semantic error.
In a partially filled array, the number of slots in the array that are not currently used is the?
Answers
Answer:
Can you please explain more
Explanation:
what is constant layout in android studio
Answers
"A ConstraintLayout is a ViewGroup allows you to position and size widgets in a flexible way. Note: ConstraintLayout is available as a support library that you can use on Android systems starting with API level 9 (Gingerbread)"
Which practice has a purpose that includes restoring normal service operation as quickly as possible
Answers
The practice that has a purpose that includes restoring normal service operation as quickly as possible is the Incident Management practice.
The purpose of the Incident Management practice is to restore normal service operation as quickly as possible and reduce the negative impact of incidents on business operations, thus ensuring that the best possible levels of service quality and availability are maintained. Incident management refers to the practice of minimizing downtime and disruptions caused by a specific event or incident.
The incident management process's purpose is to resolve an issue quickly and effectively while also minimizing the impact on the organization's day-to-day operations.The Incident Management process can be used to restore a failed configuration item (CI) to a fully operational state in the minimum amount of time possible. The objective of this process is to restore normal operations to the smallest number of people and companies affected by the incident with the least amount of disruption possible to the business.
To know more about operation visit:
https://brainly.com/question/28335468
#SPJ11
A programmer used Scratch to create a program with three frog sprites. If a
user clicks any of the frogs, they make a "boing" sound and glide to a random
position in the stage panel.
In this scenario, what are two examples of an algorithm?
A. The combination of panels that compose the Scratch interface
B. The code that instructs the computer to move the sprite after it is
clicked
C. The user's decision about which frog to click
D. The code that generates a random location each time.
Answers
Answer:
D. The code that generates a random location each time.
Explanation:
An algorithm is a process or set of rules to be followed in calculations or other problem-solving operations, especially by a computer.
An algorithm is needed to get a random location.
The code that instructs the computer to move the sprite after it is clicked and the code that generates a random location each time are examples of an algorithm in this scenario. The correct options are B and D.
What is algorithm?A set of instructions or rules that must be followed in order to complete a task or solve a problem is referred to as an algorithm.
The programmer in this scenario used Scratch to create a programme with three frog sprites that respond to user input by making a "boing" sound.
In this scenario, the combination of panels that comprise the Scratch interface and the user's decision about which frog to click are not examples of algorithms.
The panels that make up the Scratch interface are part of the programming environment, but they have no effect on the program's behaviour.
Similarly, the user's choice of which frog to click is a user input, but it does not form part of the algorithm that governs the program's behaviour.
Thus, the correct options are B and D.
For more details regarding algorithm, visit:
https://brainly.com/question/22984934
#SPJ7
Please help!!!! 100 points!!

Answers
Answer:
I DONT GET IT
Explanation:
I was also looking for an answer for the same question lo
What are the best Aviation Schools?
Answers
Answer:
air force ⭐
Explanation:
Answer:
ATP, if not your local flight school
Explanation:
ATP is a extreamly regimented program (like a intense college) and will not let you have a job on the side; if you do and they find out you will be kicked out of the program and get NONE of your money back. You will learn alot very quickly but if you are not ready to be at your local ATP everyday for at least 8 hours I suggest going to your local flight school.
Hope this helped :)
Please label the parts its urgent Best answer receives a brainliest and 20 points please i need it :) :)

Answers
Answer:
B: Floppy Drive
C: Power Button
D: Power Indicator
E: USB Port
F: Headphone port
Answer:
A. hard disk
B. floppy disk
C. power button
D. reset button
E. USB ports
F. mic port
Explanation:
hope it helps .
What is the difference between basic auth and oauth.
Answers
Answer:
Basic auth is an authentication where username and password are sent with an HTTP request unencrypted (just base64 encoded).
OAuth is a scheme whereby you perform a login at an IAM server, which gets you a token, and then you provide the token with requests to another server.
elecrrib is it possible to hide this desktop applications window to people viewing on share screen but still show it to the person sharing their screen?
Answers
Yes, it is possible to hide the desktop applications window from people viewing on share screen but still show it to the person sharing their screen.
This is done through screen-sharing settings. How to hide desktop applications window to people viewing on share screen but still show it to the person sharing their screen? To hide the desktop applications window to people viewing on share screen but still show it to the person sharing their screen, follow the steps below:Launch the screen share feature in your preferred video conferencing application or platform; the method for starting screen sharing varies depending on the platform being used.Click the Advanced Sharing Options button at the bottom of the screen sharing settings pop-up window; this opens a new pop-up window containing a variety of sharing choices.Under the Who Can Share drop-down menu, choose Only Host; this will prevent other participants from sharing their screens on the call.To keep the desktop applications window visible on the presenter's desktop while keeping it hidden from the view of the other call participants, go to the 'App/Window Sharing' section of the Advanced Sharing Options pop-up window.Click the 'Share' button next to the app or window that you want to share and keep visible to only the presenter. The selected app or window will appear on the presenter's screen while being hidden from the view of the other participants.
Learn more about screen-sharing here:
https://brainly.com/question/31165735
#SPJ11
3. what are two reasons why you might want to delete the drivers and driver package when you uninstall a device?
Answers
1. To reduce clutter on the computers and improve performance.
2. To ensure the device is completely uninstalled and no remnants remain.
When uninstalling a device from a computer, it is usually necessary to delete the drivers and driver package associated with the device as well. This is important for a few reasons. Firstly, deleting the drivers and driver package helps to reduce clutter on the system, as the system no longer needs to keep the files associated with the device. This helps to improve system performance, as the system is no longer trying to use unnecessary files. Secondly, deleting the drivers and driver package helps to ensure the device is completely uninstalled and no remnants remain. If the drivers and driver package were not deleted, they could potentially interfere with the operation of other devices or cause compatibility issues. Therefore, it is important to delete the drivers and driver package when uninstalling a device in order to keep the system running smoothly.
Learn more about computers here:
brainly.com/question/30206316
#SPJ4
what is the predefined business logic within a blockchain called?
Answers
Smart contracts: With so much being said and published about blockchain, it appears that the technology may be misunderstood by the general public. They see it as a one-man band that can do everything, including enabling bitcoin, safeguard data, brew coffee, and more, rather than a technology.
Blockchain is a distributed, immutable database that simplifies the tracking of assets and the recording of transactions inside a business network. An asset may be tangible (such a home, automobile, sum of money, or plot of land) or intangible (intellectual property, patents, copyrights, branding). A blockchain network allows for the recording and trading of practically everything of value, lowering risk and increasing efficiency for all parties. Business depends heavily on information, which is why blockchain technology is significant. It is preferable if it is received promptly and accurately.Because it provides real-time, shareable, and fully transparent data that is recorded on an immutable ledger and only available to users of a permissioned network, blockchain is the perfect technology for delivering such information.
To learn more about " database " Click on below link brainly.com/question/28391263
#SPJ4
Which of the following is not true when viewing events collected by an IPAM server?
a. Events related to DHCP scope changes can be viewed.
b. Events in the detail pane can be clicked for more information.
c. Events are visible in real time.
d. Events related to DHCP policies changes can be viewed.
Answers
When viewing events collected by an IPAM (IP Address Management) server, it is not true that events related to DHCP policies changes can be viewed.d. Events related to DHCP policies changes can be viewed.
When viewing events collected by an IPAM (IP Address Management) server, it is not true that events related to DHCP policies changes can be viewed. DHCP (Dynamic Host Configuration Protocol) policies define the configuration settings and rules for IP address assignment and management within a network. While IPAM servers can track and manage IP addresses and DHCP scopes, they typically focus on monitoring and managing IP address allocations and related events rather than DHCP policies.
a. Events related to DHCP scope changes can be viewed: This is true. IPAM servers track and log events related to changes in DHCP scopes, such as modifications to the range of IP addresses allocated to a particular scope.
b. Events in the detail pane can be clicked for more information: This is true. IPAM servers usually provide a detailed view of events, and clicking on an event in the detail pane often provides additional information or context about that specific event.
c. Events are visible in real time: This is true. IPAM servers generally display events in real time, allowing administrators to monitor changes and activities as they occur.
Therefore, the correct answer is d. Events related to DHCP policies changes can be viewed.
To know more about IPAM server visit:
brainly.com/question/32178052
#SPJ11
Which of the following is not a key component of a structure?
A. Name
B. Properties
C. Functions
D. Enumerations
Answers
Answer:
D i think
Explanation:
Janelle wants to research information about a local politician's recent public appearances. Which tool should she use for this?
A printed newspaper with a local news section.
A digital library that has a section on politics.
A physical library where the politician has appeared.
Search engines filtered to only show news sites.
Answers
Answer:
Search engines filtered to only show news sites.
Explanation:
A printed newspaper could have come from any time
A digital library barely gets updated
I'm pretty sure I saw those same books 3 years ago
Yeah you get the jig
The refine area in the search tab of the ribbon provides quick options for the refining your search including?
Answers
The refine area in the search tab of the ribbon provides quick options for refining your search including Advanced Search, filter option, Outlook ribbon, etc.
What is the process of refining your search results?The process of refining your search results describes the methodology through which you can also select a category within the Refine group to further filter your search results:
From, only shows results from a specific person. The subject only shows results based on the subject. Has Attachment – only shows emails that have attachments.
Based on your preference, you can use Advanced Search by clicking the filter button on the right side of the search box. Alternatively, the Outlook ribbon will change to show the Search tab and you use any of the options in the Refine group to refine your search results.
Therefore, the refine area in the search tab of the ribbon provides quick options for refining your search including Advanced Search, filter option, Outlook ribbon, etc.
To learn more about Outlook search, refer to the link:
https://brainly.com/question/24165533
#SPJ1
the following array is to be sorted biggest to smallest using insertion sort. [10, 40, 50, 30, 20, 60] what will the array look like after the third pass of the for loop?
Answers
Answer:
After the third pass of the for loop, the array will look like this: [10, 30, 40, 50, 20, 60].
Explanation:
Insertion sort works by dividing the array into two parts: a sorted part and an unsorted part. The algorithm iterates through the unsorted part and for each element, it compares it with the elements in the sorted part and inserts it in the correct position such that the sorted part remains sorted.
In this case, the array [10, 40, 50, 30, 20, 60] needs to be sorted in decreasing order. After the first pass, the first element (10) will be in its correct position in the sorted part and the unsorted part will contain the rest of the elements [40, 50, 30, 20, 60].
After the second pass, the second element (40) will be inserted in the correct position in the sorted part, which will now be [10, 40], and the unsorted part will contain the rest of the elements [50, 30, 20, 60].
After the third pass, the third element (50) will be inserted in the correct position in the sorted part, which will now be [10, 30, 40], and the unsorted part will contain the rest of the elements [20, 60].
So, after the third pass, the array will look like this [10, 30, 40, 50, 20, 60].