Write 4 types of viruses , explain them briefly.
Answers
I can help with two.
Web Scripting Virus, A sneaky virus that targets popular websites. What this virus does is overwrite code on a website and insert links that can install malicious software on your device. Web scripting viruses can steal your cookies and use the information to post on your behalf on the infected website.
FILE INFECTOR, targeting executable files (.exe), file infector viruses slow down programs and damage system files when a user runs them.
Related Questions
Calculate the formula unit mass if Al(NO3)3.(Al=27,N=14,O=16)
Answers
Answer:
Explanation:
EMAIL query ? comment or request a type of GCSE calculation not covered? ... atomic masses are Al = 27 and O = 16; so the relative formula mass RFM or Mr = (2 x 27) + (3 x 16) = 102
What will you see on the next line?
int(200.9123)
Answers
Answer:
200
Explanation:
Because int number can not carry decimal point.
Write a program that prompts the user to input two POSITIVE numbers — a dividend (numerator) and a divisor (denominator). Your program should then divide the numerator by the denominator. Lastly, your program will add the quotient and the remainder together.
Sample Run:
Input the dividend: 10
Input the divisor: 4
The quotient + the remainder is 4.0
Hint: If you use division (/) to calculate the quotient, you will need to use int() to remove the decimals. You can also use integer division (// ), which was introduced in Question 10 of Lesson Practice 2.3.
Once you've calculated the quotient, you will need to use modular division (%) to calculate the remainder. Remember to clearly define the data types for all inputs in your code. You may need to use int( ) and str( ) in your solution.
int( ): When you divide the numerator and the divisor using /, make sure that the result is an integer.
str( ): After using modular division, you can transform the quotient and remainder back into strings to display the result in the print() command.
Answers
here gang,
dividend = int(input("Input the dividend: "))
divisor = int(input("Input the divisor: "))
quotient = int(dividend/divisor)
remainder = dividend%divisor
answer = quotient+remainder
print("The quotient + the remainder is " + str(answer))
this gave me 100%
Write a program to find the sum of first 10 even numbers in qbasic
Answers
Answer:
CLS. FOR I = 1 TO 10. INPUT "ENTER THE NUMBERS"; N(I) IF N(I) MOD 2 = 0 THEN S = S + N(I) ...
Your friend decides to create a spreadsheet containing vocabulary terms and their definitions to help prepare for the unit test in Spanish class. If your friend wants to organize the terms alphabetically from A to Z, which spreadsheet tool should be used?
filter
sort
locate
replace
Answers
Answer:
The answer is SORT
Explanation:
Just did the test :)
Answer:
its B (sort)
Explanation:
Joe wants to copy the formatting of cells A1 through C1 in his workbook to use in another location. Which of the following commands should he use?
Cut Painter
Copy Painter
Paste Painter
Format Painter
Answers
Copy Painter
Copy Painter is the commands should he use. Hence, option B is correct.
What is Copy Painter?Think of it as copying and pasting for formatting. With format painter, you may copy all of the formatting from one object and apply it to another. Choose the text or image that has the desired formatting. Note: Choose a section of a paragraph to duplicate the formatting of.
Character and paragraph formats can be copied and pasted into text using the Format Painter tool. This tool can make organizing and reformatting documents simpler and more effective when used in conjunction with styles.
Explore the home menu ribbon to find the "Clipboard" category of tools. Usually, this can be found in the top left corner of your screen. The "Format Painter" button should be clicked. The paintbrush icon next to this button
Thus, option B is correct.
For more information about Copy Painter, click here:
https://brainly.com/question/1451042
#SPJ6
Omar wants to research additional information about asteroids. Complete the sentences to describe how he should use the Smart Lookup feature in PowerPoint. Step 1: He should ____________ the word asteroid. Step 2: He should navigate to the _________ tab. Step 3. He should go to the __________ command group. Step 4: He should turn on the Intelligent Services of PowerPoint in the pane. Step 5: He should click the ________ option to open links that contain information about asteroids. Please answer quickly! It is quite urgent
Answers
Answer:
Step 1: He should
✔ select
the word asteroid.
Step 2: He should navigate to the
✔ Review
tab.
Step 3. He should go to the
✔ Insights
command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the
✔ Explore
option to open links that contain information about asteroids.
Explanation:
Edg2020
Omar should use the Smart Lookup feature in PowerPoint in several steps 1. Select, 2. Review, 3. Insights, 4. Explore.
What is the Smart Lookup feature in PowerPoint?The new Smart Lookup feature in PowerPoint 2016 for Windows is an option that shows up definitions, images, and other results from various online platforms about a word or phrase, right within PowerPoint.
There are four steps to use the Smart Lookup feature in PowerPoint:
Step 1: He should select the word asteroid.
Step 2: He should navigate to the Review tab.
Step 3. He should go to the Insights command group.
Step 4: He should turn on the Intelligent Services of PowerPoint in the pane.
Step 5: He should click the Explore option to open links that contain information about asteroids.
Therefore, he should use 1. Select, 2. Review, 3. Insights, 4. Explore.
Learn more about PowerPoint, here:
https://brainly.com/question/19238885
#SPJ2
Why do you need to look out for others' safety as well as your own in the metaverse?
Answers
In the metaverse, just like in the real world, it's important to consider the safety and well-being of others as well as your own for several reasons:
Respect for others - The metaverse is a shared digital space, and it's essential to show respect for others and maintain a safe environment for all users.Legal and ethical considerations - Certain activities in the metaverse, such as harassment or theft, may be illegal or unethical and can have consequencesWhat is the Metaverse?The metaverse is a computer industry concept of the next version of the internet: a single, shared, immersive, permanent, 3D virtual place where humans may experience life in ways they cannot in the physical world.
The word metaverse is coined by American sci-fi writer Neal Stephenson in his book Snow Crash, which describes a dismal future society in which affluent individuals escape into an other 3D, networked reality.
Learn more about Metaverse:
https://brainly.com/question/29340413
#SPJ1
Oh... what I got was: myPetA.changeName('Tiger')
Answers
Answer: monke
Explanation:
has honda made enough improvements to their1.5 liter 4 cyl. turbo engine so that its reliability matches that which honda engines are known for___
Answers
has honda made enough improvements to their1.5 liter 4 cyl. turbo engine so that its reliability matches that which honda engines are known for being easy to start.
What makes Honda engines unique?
Consistently, Honda engines are known for being simple to start. Our engines are made with quick, simple starts in mind, from the innovative variable ignition timing to our one-of-a-kind automatic mechanical decompression system to heavy-duty recoil ropes.
What four-cylinder Honda engine is the best?
The K20 and K24 have both established themselves as two of the best four-cylinder engines ever created. They have inexpensive parts with enormous potential and a devoted fanbase that has encouraged individuals to install them in virtually any type of vehicle.
Since they only employ parts from the finest manufacturers and evaluate each component for longevity before using it on a car, they use only the best components.
Learn more about Honda engines
brainly.com/question/14987584
#SPJ4
Based on your answer in task 3, identify skills and competencies required for a
programmer.
Answers
The field of programming requires a range of skills and competencies to be successful like Coding Skills, Problem-Solving Skills, Logical and Analytical Thinking and many more.
Here are some key skills and competencies that are important for programmers:
Proficient Coding Skills: Strong programming skills in languages such as Python, Java, C++, or JavaScript are crucial. This includes understanding syntax, data structures, algorithms, and problem-solving techniques.Logical and Analytical Thinking: Programmers need to possess strong logical and analytical thinking abilities to break down complex problems into smaller, manageable components and develop efficient solutions.Attention to Detail: Programming often involves working with intricate code, and even minor errors can lead to significant issues. Attention to detail is essential to catch bugs, troubleshoot problems, and ensure code accuracy.Problem-Solving Skills: Programmers are constantly faced with challenges and need to be adept at problem-solving. This involves analyzing problems, identifying solutions, and implementing effective strategies to overcome obstacles.Collaboration and Communication: Programmers often work in teams and need to effectively communicate and collaborate with others. This includes sharing ideas, discussing requirements, and providing clear documentation.Continuous Learning: The programming field is dynamic, with new technologies and frameworks emerging regularly. Programmers should have a thirst for learning and staying updated with the latest trends to adapt to changing requirements.Debugging and Testing: Identifying and fixing errors in code is an essential skill for programmers. They need to be proficient in debugging techniques and conducting thorough testing to ensure the quality and functionality of their programs.These are just a few of the key skills and competencies required for programmers. The field is broad, and different programming roles may require additional specialized skills based on specific technologies or industries. Continuous self-improvement and a passion for coding are also crucial traits for success in programming.For more such questions on programming
https://brainly.com/question/23275071
#SPJ8
type of report that useful when the user wants only total figures and does not need supporting details
Answers
A summary report is useful for total figures only.
What is a summary report?The type of report that would be useful when the user only wants total figures and does not need supporting details is a summary report.
A summary report is a condensed version of a larger report that presents only the most important information, such as total figures or key findings, without providing any supporting details.
This type of report is useful for decision-makers who need to quickly understand the overall picture without getting bogged down in details.
Summary reports are often used in financial reporting, where executives may only be interested in the bottom-line figures, or in market research, where only the key takeaways need to be presented.
Learn more about Summary reports
brainly.com/question/31669908
#SPJ11
help please give me the correct ans....
write a qbasic program to print the word "hello" 10 times [by using for next]
Answers
http://www6.uniovi.es/qbasic/qtutor1.html
go to this link and it will show you how to solve your problem
In reality, the page fault handler code must also reside in pages in memory, and might, under some circumstances (e.g., FIFO page replacement policy) itself be removed. what could be done so that the page fault handler could not be removed?
Answers
To prevent the page fault handler from being removed under certain circumstances such as FIFO page replacement policy, it could be added to a list of kernel processes that should always remain in memory.
This list is known as the "swapper space".In reality, the page fault handler code must also reside in pages in memory, and might, under some circumstances (e.g., FIFO page replacement policy) itself be removed.
To prevent the page fault handler from being removed under certain circumstances such as FIFO page replacement policy, it could be added to a list of kernel processes that should always remain in memory. This list is known as the "swapper space". This is an area of memory that is never swapped out to disk and is always kept in RAM.
Learn more about memory at:
https://brainly.com/question/30886136
#SPJ11
what are six examples of information technologies that could be used in computer crimes?
Answers
The use of spyware, adware, phishing, keystroke loggers, pharming, and baiting are example how these practices can be used to perpetrate fraud and other illegal goods, steal identities, and violate people's privacy.
What does computer crime taping entail?Either a monitoring device, known as a "bug," is placed on the targeted cable or special features built into other communication technologies are used to conduct a wiretap.
How can criminals take advantage of technology?Regrettably, technology has also made it possible for people to conduct crimes in secret from the comfort of their own homes. Cybercrime is what happens when someone commits a criminal act online while utilising a computer or another electronic device to damage someone else.
To know more about people's privacy visit:-
brainly.com/question/29095928
#SPJ1
_______ are malicious programs that come into a computer system disguised as something else such as a free computer game or screen saver.
Answers
Answer:
Trojan horses
Explanation:
this is a special built-in pointer that is available to a class's member functions.
Answers
The special built-in pointer that is available to a class's member functions is commonly known as "this".
This pointer points to the object that the member function is being called on and allows the function to access the object's data members and other member functions. When a member function is called, the "this" pointer is automatically passed as a hidden argument to the function. This allows the function to know which object it is operating on. By using the "this" pointer, member functions can avoid naming conflicts with local variables or parameters that have the same name as the object's data members. Overall, the "this" pointer is a powerful tool that allows for efficient and effective implementation of member functions within a class.
learn more about built-in pointer here:
https://brainly.com/question/31922659
#SPJ11
As a network administrator, Lea helps a small start-up set up a temporary network at a rented space. She configures a host computer with the IP address provided by the ISP to act as a router. Other computers in the network share the Internet connection through the host computer. After few hours, the owners of the start-up complain that they are not able to connect to the Internet.
Required:
What would Lea do to resolve the problem?
Answers
Business often needs internet connections to run their businesses online. What Lea should do to resolve the problem is that since the host computer was manually configured using ICS which was one of the major cause of the internet sharing. The best thing to do is to disable the ICS and then there will be no internet sharing.
Internet Connection Sharing (ICS) is known as a Windows service that helps an individual in their Internet-connected computer so as to share its Internet connection with other computers on a Local area network (LAN).
The Host computer often shares its Internet connection and acts as a gateway means. All traffic between other computers and the Internet go through this computer due to this connection. It gives Dynamic Host Configuration Protocol (DHCP) and network address translation (NAT) services for the LAN computers.
Conclusively, ICS enable a host computer to share the internet connection with other computer within the area and as such it's internet connection make have issues when a lot of other connects to it.
Learn more from
https://brainly.com/question/18543195
you want to see the filesystems that are presently in use on the system. what command could you use?
Answers
You can use the df command to see the file systems that are currently in use on the system. The df command displays the amount of disk space available on the file system containing each file name argument.
What is df command?
The df command is a useful tool for system administrators and users to check the utilization of disk space on a system. By default, df shows information about the available disk space and the space used by each file system in kilobytes.
The -h option makes the output more readable by using units such as MB and GB, making it easier to understand how much disk space is being used. The output of the df command shows the file system, total size, used space, available space, and the percentage of disk space used for each file system on the system.
Here's an example of how to use the df command:
df -h
The -h option is used to display the sizes in "human-readable" format (i.e., using units of KB, MB, GB, etc.).
To learn more about file systems, visit: https://brainly.com/question/30019616
#SPJ4
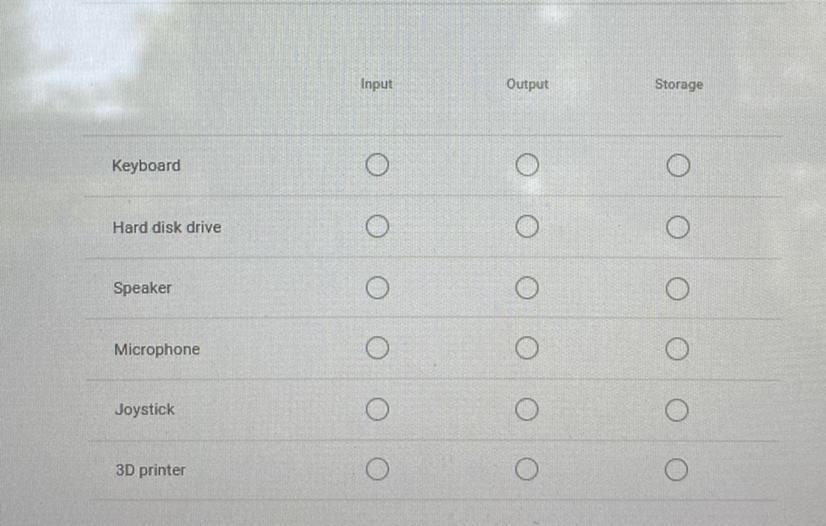
Determine whether each device is an input device, an output device, or a storage device.
Answers
What do devices provide? A.data to be processed B. Software code C.text and images only D.results of processing.
Answers
A is the correct answer!
which character formatting tool appears only when you select text?
Answers
'The mini toolbar' is the character formatting tool that appears only when a user selects text.
In Microsoft Word, Excel, Outlook, and PowerPoint the mini toolbar is a smaller version of the full toolbar placed near the top of the application window. The mini toolbar displays when a user highlights or selects text and either moves the mouse cursor over the selected text or right-clicks the selected text.
Thus, the character formatting tool that appears only when some text is selected is known as the mini toolbar.
You can learn more about the mini toolbar at
https://brainly.com/question/14580960
#SPJ4
Which combination of options is the keyboard shortcut to access the find dialog box and search a worksheet for particular values? ctrl h ctrl r ctrl f ctrl e
Answers
A hot key is a key or group of keys on a computer keyboard that, when pressed simultaneously, carry out a task (such launching an application) more quickly than a mouse or other input device.
What is the uses of shortcut keys ?The Find and Replace dialog box, which enables you to look for a specific value in your worksheet and replace it with another value, is opened by pressing the keyboard shortcut Ctrl + F. Additionally, formatting can be found and changed with this shortcut.The function keys and keyboard shortcuts in Word for Windows are discussed in this article.
The Find tab appears in place of the Replace tab when using the CTRL+H keyboard shortcut or the Replace button on the ribbon to open the Find and Replace dialog box.Pressing Ctrl + R will refresh (reload) the current web page in all popular Internet browsers, including Chrome, Edge, Firefox, and Opera.To choose the search box, use Ctrl + E.
To learn more about shortcut key refer to :
https://brainly.in/question/135577
#SPJ4
The feature that modifies text to include special effects, such as color, shadow, and gradients, is__________
Answers
The feature that modifies text to include special effects, such as color, shadow, and gradients, is called text formatting.
This feature allows you to enhance the appearance of your text and make it more visually appealing. Text formatting options can include changing the font, size, color, and style of the text, as well as adding special effects like shadows and gradients.
These options are typically found in the toolbar of word processing or graphic design software. Text formatting can also help to make your text more legible, such as by increasing the font size or changing the font to one that is easier to read. Text formatting can also be used to create a unique, eye-catching style that stands out from the crowd.
Learn more about text formatting:
https://brainly.com/question/766378
#SPJ11
The feature that modifies text to include special effects, such as color, shadow, and gradients, is called text formatting.
This feature allows you to enhance the appearance of your text and make it more visually appealing. Text formatting options can include changing the font, size, color, and style of the text, as well as adding special effects like shadows and gradients.
These options are typically found in the toolbar of word processing or graphic design software. Text formatting can also help to make your text more legible, such as by increasing the font size or changing the font to one that is easier to read. Text formatting can also be used to create a unique, eye-catching style that stands out from the crowd.
Learn more about text formatting:
brainly.com/question/766378
#SPJ11
How can I input the answers using Simul8 app?
Answers
To input s in Simul8, you can use various methods such as data entry forms, external data sources, or programming interfaces.
Simul8 offers flexibility in gathering inputs based on your specific requirements.
Simul8 is a simulation software used for modeling and analyzing processes. When it comes to inputting s, Simul8 provides several s to accommodate different scenarios and data sources.
1. Data Entry Forms: Simul8 allows you to create custom data entry forms within the simulation model. Users can input values directly into the form, which are then used as inputs for the simulation.
2. External Data Sources: You can import data from external sources such as spreadsheets, databases, or text files. Simul8 supports various file formats and provides tools to map the imported data to the appropriate simulation variables.
3. Programming Interfaces: Simul8 offers programming interfaces like Visual Logic (a visual programming language) and COM/OLE automation. These interfaces allow you to write scripts or code to input s dynamically or fetch data from external systems during the simulation.
By utilizing these methods, you can effectively input s into Simul8 to drive your simulations and obtain meaningful results. The choice of method depends on the nature of your inputs and the integration requirements with other systems or data sources.
Learn more about programming here:
https://brainly.com/question/14368396
#SPJ11
how can an administrator retrieve the ip address settings of a computer using powershell?
Answers
To retrieve the IP address settings of a computer using PowerShell, an administrator can utilize the built-in cmdlets that come with the Windows operating system. These cmdlets provide an easy way to gather information about the network configuration of a machine, including its IP address settings.
To get started, open up PowerShell on the computer you want to retrieve the IP address settings from. Then, run the following command: Get-NetIPAddress This command will display a list of all IP addresses associated with the computer, including the IPv4 and IPv6 addresses. If you only want to view the IPv4 address, you can run the following command instead: Get-NetIPAddress -AddressFamily IPv4
This will only display the IPv4 address associated with the computer. In addition to the IP address settings, an administrator can also use PowerShell to retrieve other network-related information, such as the default gateway, DNS server, and subnet mask. For example, to view the default gateway, run the following command: Get-NetRoute -DestinationPrefix 0.0.0.0/0 | Select-Object -ExpandProperty NextHop This command will display the IP address of the default gateway configured on the computer. In summary, PowerShell provides a simple and efficient way for administrators to retrieve the IP address settings of a computer. By leveraging the built-in cmdlets, an administrator can quickly gather the information they need to troubleshoot network-related issues and ensure that the computer is properly configured for its intended use.
Learn more about IP address here-
https://brainly.com/question/31453021
#SPJ11
wyd...tmr no school so happy(:
Answers
Answer:
Just writing, there's no school today either, well at least for me
Explanation:
You're welcome.
Answer: Nothing much, probably just homework and softball practice. I was also off today because of the snow.
Explanation: Have a good day!
What is Communication
Answers
____ record the keystrokes of a user into a text file that is sent back to the attacker for a specific period of time and frequency.
Answers
logic bombs are dormant and will only be activated by the fulfillment of specific conditions when they will deliver a malicious payload to unsuspecting computer users.
What is a logic bomb?A logic bomb is a series of codes that have been intentionally introduced into a software system and which will set off a malicious function when some specific conditions are met.
In other words, logic bombs are dormant and will only be activated by the fulfillment of specific conditions, when they will deliver a malicious payload to unsuspecting computer users.
An example is when a programmer in a company hides pieces of code that will start to delete files in the company, in the event of him/her getting fired from the company.
To know more about logic bomb follow
https://brainly.com/question/13993673
#SPJ4
how can computers and technology help in investigating a fraud? what kinds of challenges can the involvement of technology present to a case?
Answers
Today's computer forensic analysts can recover data that has been deleted, encrypted, or hidden within the folds of mobile device technology; they can be called to testify in court and relate the evidence discovered during investigations.
The computer forensic process:
A computer forensic examination is performed to recover data from computers that have been seized as evidence in criminal investigations. Experts examine evidence that may be presented in court during proceedings in a systematic manner. Forensic experts should be involved early in an investigation because they can assist in properly collecting technical material in a way that allows the content to be restored without compromising its integrity.
Many (or all) of the following steps can be included in forensic investigation efforts:
Collection entails the search for and seizure of digital evidence, as well as the acquisition of data.Examining entails using techniques to identify and extract data.Analysis is the process of using data and resources to prove a point.Reporting entails presenting the information gathered.To know more about computer forensic, visit: https://brainly.com/question/14405745?referrer=searchResults
#SPJ4