why do maxima (bright spots) and minima (dark spots) appear when light is reflected back from the cd?
Answers
Maxima (bright spots) and minima (dark spots) appear when light is reflected back from the CD due to the interference of the reflected waves.
When light falls on the surface of the CD, it reflects back in all directions. As a result, multiple waves are created, each having a slightly different path length. These waves interfere with each other constructively and destructively. Constructive interference occurs when waves add up, resulting in brighter spots or maxima. Destructive interference occurs when waves cancel each other out, resulting in darker spots or minima.
The distance between these spots is determined by the wavelength of the incident light and the spacing of the tracks on the CD. The track spacing on a CD is uniform, so the distance between the spots is directly proportional to the wavelength of the incident light. This phenomenon is called diffraction grating and is used in many applications, including spectroscopy and optical communication.
To know more about reflected visit:
https://brainly.com/question/29235982
#SPJ11
Related Questions
What are some good websites to post my art on
Answers
Answer:
Explanation:
Good questions
I think Etsy
explain what the hexadecimal code in a MAC address represents
Answers
Answer:
An Ethernet MAC address consists of a 48-bit binary value. Hexadecimal is used to identify an Ethernet address because a single hexadecimal digit represents 4 binary bits. Therefore, a 48-bit Ethernet MAC address can be expressed using only 12 hexadecimal values.
which digits are used in digital computer?
Answers
Answer:
binary digits i.e. 0s and 1s
how can we modify almost any algorithm to have a good best-case running time?
Answers
To modify almost any algorithm to have a good best-case running time, we can follow these three steps:
Analyze the algorithm to identify the best-case scenario.Optimize the algorithm for the best-case scenario by modifying the code or data structures.Verify that the modifications do not worsen the worst-case scenario.How can algorithmic modifications lead to better best-case running times?In order to modify an algorithm to have a good best-case running time, it is important to identify specific inputs that have faster processing times than the general case. By adding special cases or checks in the algorithm to handle these inputs, we can reduce the overall running time of the algorithm.
For example, if we are sorting an array and we know that the array is already sorted, we can add a check to skip the sorting process and return the array as is. Similarly, if we are searching for an element in a sorted array, we can add a check to see if the element is the first or last element of the array, which would be faster than performing a binary search.
It is important to note that adding special cases or checks can increase the complexity and code size of the algorithm, and may not always be worth the effort. It is also important to thoroughly test the algorithm with different inputs to ensure that the modifications do not introduce any bugs or errors.
Learn more about Algorithm
brainly.com/question/21172316
#SPJ11
Select the correct answer,
Which component manages the flow of data between the parts of a computer?
A ALU
B.control unit
C. RAM
D ROM
Answers
Answer:
the answer is B the control unit
A data analyt add decriptive header to column of data in a preadheet. How doe thi improve the preadheet?
Answers
A data analyst add descriptive header to column of data in a spreadsheet. By doing this, the data analyst is adding context to their data.
What is spreadsheet?The term "spreadsheet" refers to a computer program that displays data in a two-dimensional grid along with formulas that link the data. An accounting ledger page that displays various quantitative data useful for managing a business is what a spreadsheet has traditionally been known as.
In the later 20th century, electronic spreadsheets took the place of paper ones. Spreadsheets, however, can be used for more than just financial data; they are frequently employed to represent and perform calculations on scientific data as well.
VisiCalc, created for the Apple II computer in 1979, was the first spreadsheet program. This application, which in some cases reduced a 20-hour per week bookkeeping task to a few minutes of data entry, served as the best example for many users of the practicality of personal computers for small businesses.
Learn more about spreadsheet
https://brainly.com/question/26919847
#SPJ4
which format is best for photos?
JPEG
DOC
GIF
Wav
Answers
Which of the following is the correct way for writing JavaScript array?
A. var salaries = new Array(1:39438, 2:39839 3:83729)
B. var salaries = new (Array1=39438, Array 2-39839 Array 3=83729)
C. var salaries = new Array(39438, 39839,83729)
D. var salaries = new Array() values= 39438, 39839 83729
Answers
The correct way for writing a JavaScript array is given in option C. var salaries = new Array(39438, 39839, 83729).
Explanation:
In JavaScript, arrays are objects used to store multiple values in a single variable. They can be created using various methods, but the most common way is by using the Array() constructor.
Option A is incorrect as it uses a colon instead of a comma to separate the values in the array, which is not valid syntax in JavaScript.
Option B is also incorrect as it uses an unconventional way of assigning values to the array by using equal and minus signs instead of commas.
Option D is also incorrect as it uses an invalid syntax to assign values to the array by using an equal sign after the Array() constructor and not using commas to separate the values.
Option C is the correct way to create an array in JavaScript, where the values are enclosed in parentheses and separated by commas within the Array() constructor. For example, the code "var salaries = new Array(39438, 39839, 83729);" creates an array called "salaries" with three values: 39438, 39839, and 83729.
To learn more about JavaScript click here:
https://brainly.com/question/28448181
#SPJ11
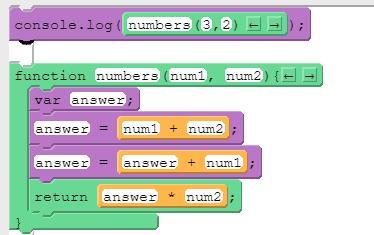
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
50 POINTS
1. int f = 8;
out.println("$"+f+10);
what is the output and how did you get that?
2. int e = 12;
e = 15;
out.println(e);
what is the output and how did you get that?
3. int i =7, j = 10;
j *=i+2;
out.println( i+" "+j);
what is the output and how did you get that?
THOUGHTFUL ANSWER OR NOT REPORT
Answers
The output of the code is "$810".
The expression "$" + f + 10 is evaluated as follows:
' f ' is an integer with the value of 8, so f + 10 evaluates to 18.
The string "$" is concatenated with the result of f + 10, resulting in the string "$18".
The final result is printed to the console using the println method, so the output is "$810".
The output of the code is "15".
The code sets the value of ' e ' to ' 12 ' in the first line, then re-assigns it to ' 15 ' in the second line. The final value of ' e ' is ' 15 '.
In the third line, the value of ' e ' is printed to the console using the ' println ' method, so the output is "15".
The expression j *= i + 2 means to multiply j by the value of i + 2 and assign the result back to j. So in this case, j becomes j * (i + 2) = 10 * (7 + 2) = 10 * 9 = 90.
In the third line, the values of i and j are concatenated with a space in between and printed to the console using the println method, so the output is "7 29".
"write a program to play and score the paper-rock-scissor game. each of two users types in either p, r, or s. the program then announces the winner as well the basis for determining the winner: paper covers rock, rock breaks scissors, scissors cut paper, or nobody wins. be sure to allow the users to use lowercase as well uppercase letters. your program should include a loop that lets the user play again until the user says she or he is done."
Answers
The program is an illustration of conditional statements.
Conditional statements are used to execute instructions, if and only if certain condition or conditions are met.
Take for instance: If b = 5, print "ab"
The above print statement will only be executed, if the value of b is 5
The paper-rock-scissor program in Python where comments are used to explain each line is as follows,
#This imports the random module
import random
#This is used to control the repetition of the game
playagain ="T"
#The following is repeated until the user chooses not to play again
while(playagain == "T"):
#This generates a random choice for the computer
computer = random.choice(['Rock', 'Paper', 'Scissors'])
#This gets input for the player
player = input('Choose: ')
#If the player and computer choose the selection
if player == computer:
#Then, it's a tie
print('A tie - Both players chose '+player)
#If the player wins
elif (player.lower() == "Rock".lower() and computer.lower() == "Scissors".lower()) or (player.lower() == "Paper".lower() and computer.lower() == "Rock".lower()) or (player == "Scissors" and computer.lower() == "Paper".lower()):
#This prints "player won" and the reason
print('Player won! '+player +' beats '+computer)
#If otherwise,
else:
#This prints "computer won" and the reason
print('Computer won! '+computer+' beats '+player)
#This asks if the player wants to play again
playagain = input("Play again? T/F: ")
At the end of each round,
The program displays the winnerOr prints a tie, if there's a tieSee attachment for sample run
Read more about conditional statements at:
https://brainly.com/question/22078945
how to get gale to fix the pedestals in prodigy 2023
Answers
Answer:
Explanation:
he ate food
The ability for new computers to be automatically connected to the network is provided by the:________
Answers
Answer:
DHCP server
Explanation:
Which of the following actions directly improves system security on a Windows workstation?
Disable automatic reboot on error.
Create a password reset disk.
Create regular restore points.
Install the latest updates.
Answers
Installing the latest updates is the action that directly improves system security on a Windows workstation.
Installing the latest updates is crucial for improving system security on a Windows workstation. Updates often include patches for security vulnerabilities that have been identified, and failing to install updates can leave the system open to attacks. Therefore, it is important to ensure that updates are regularly installed, either manually or by enabling automatic updates. Disabling automatic reboot on error can help prevent data loss in the event of a system crash, but it does not directly improve system security. Creating a password reset disk is a useful precautionary measure, but it does not directly improve system security. Similarly, creating regular restore points is helpful for recovering from system errors, but it does not directly improve system security. Therefore, of the given options, installing the latest updates is the action that directly improves system security on a Windows workstation.
Learn more about workstation here:
https://brainly.com/question/32178463
#SPJ11
Construct a Huffman tree for the five-symbol alphabet (A, B, C, D, ) with the following occurrence frequencies in a text made up of these symbols. Also, show the resulting codewords for each character. A B с D symbol frequency 0. 35 0,1 0. 15 0. 2 0. 2
Answers
The Huffman tree is a binary tree used for data compression. To construct the tree, we start by assigning each symbol a node with its frequency. Then, we merge the two nodes with the lowest frequencies into a new node, summing their frequencies. We repeat this process until we have a single tree.
The resulting Huffman tree for this alphabet is:
B + C + D + A + E
/ \
B + C + D A + E
/ \ / \
B + C D A E
/ \ / \
B C A E
Now, let's assign codewords to each character based on their position in the tree:
A: 10
B: 00
C: 01
D: 11
E: 1
To know more about Huffman tree visit :-
https://brainly.com/question/33481945
#SPJ11
in a ____, all rows from the table on the right will be included regardless of whether they match rows from the table on the left.
Answers
In a LEFT OUTER JOIN, all rows from the table on the left will be included and only matching rows from the table on the right will be included. However, any rows from the table on the right that do not have a matching row in the table on the left will also be included.
1.With a keyboard, a row is several keys going horizontally from the left-side to the right-side of the keyboard. Most keyboards have six rows of keys with the fingers resting on the home row. Other keyboard rows include the function keys, number keys, top row, bottom row, and spacebar row.
2. In a database, a row in a table is called records.
3. A row is several data banks (cells) laid out horizontally in a table or spreadsheet. For example, in the picture below, the row headers (row numbers) are numbered 1, 2, 3, 4, 5, etc. Row 16 is highlighted in red and cell D8 (on row 8) is the selected cell.
To know more about rows refer https://brainly.com/question/29524249
#SPJ11
Who is the prince of math?
Answers
Answer:
Johann Carl Friedrich Gauss
Explanation:
what is shortcuts to launch spelling in
Answers
Answer:
Just hit Alt + F7 on your keyboard and it will start with the first misspelled word. If the first highlighted word at the top of the list is correct, just hit Enter. Or you can arrow to the correct one, ignore it, or Add to Dictionary.
what is the minimum number of drives required for disk striping with distributed parity?
Answers
The minimum number of drives required for disk striping with distributed parity is three, with two drives for storing data and one drive for storing parity information. This configuration provides fault tolerance and data recovery capabilities in case of drive failure.
The minimum number of drives required for disk striping with distributed parity is three.
In disk striping with distributed parity, data is distributed across multiple drives (stripes), and parity information is also distributed across the drives to provide fault tolerance. The distributed parity helps in reconstructing data in case of drive failure.
For this technique to work, at least three drives are needed: two drives for storing data and one drive for storing parity information. The parity information is calculated and distributed across the drives in a way that allows for the recovery of data if one of the drives fails. This provides a level of data redundancy and fault tolerance in the disk storage system.
To know more about drives fails, visit:
https://brainly.com/question/32874811
#SPJ11
ProjectStem 7.5 practice
Use the function written in the last lesson to calculate the gold medalists’ average award money for all of their gold medals. Define another function in your program to calculate the average.
Your program should then output the average award money, including the decimal place. Your program should use a total of two functions. You may assume that the user will provide valid inputs.
Sample Run
Enter Gold Medals Won: 3
How many dollars were you sponsored in total?: 20000
Your prize money is: 245000
Your average award money per gold medal was 81666.6666667
Answers
Below is Python program that calculates the average award money per gold medal using two functions:
python
def calculate_average_award(total_award_money, gold_medals):
"""Calculates the average award money per gold medal"""
return total_award_money / gold_medals
def main():
"""Main function to get user input and output the result"""
gold_medals = int(input("Enter Gold Medals Won: "))
total_award_money = float(input("How many dollars were you sponsored in total?: "))
prize_money = float(input("Your prize money is: "))
average_award_money = calculate_average_award(prize_money + total_award_money, gold_medals)
print("Your average award money per gold medal was", round(average_award_money, 10))
if __name__ == "__main__":
main()
Sample run:
yaml
Enter Gold Medals Won: 3
How many dollars were you sponsored in total?: 20000
Your prize money is: 245000
Your average award money per gold medal was 81666.6666666667
What is the Python program about?The calculate_average_award function takes two arguments, the total award money and the number of gold medals, and returns the average award money per gold medal.
The main function gets the user input for the number of gold medals, the total award money, and the prize money. It then calculates the total award money for all gold medals by adding the total award money and the prize money, and passes the values to the calculate_average_award function to get the average award money per gold medal.
Therefore, The program then outputs the result using the print function, rounding the value to 10 decimal places using the round function.
Learn more about Python program from
https://brainly.com/question/27996357
#SPJ1
kadijah is concerned about her geolocation getting tracked and stored in a database. to avoid her geolocation being tracked, which computing devices should she avoid using? i istart text, i, end text. devices on a wired internet connection ii iistart text, i, i, end text. devices on a wireless internet connection iii iiistart text, i, i, i, end text. devices with a gps receiver
Answers
To avoid kadijah's geolocation being tracked and stored in a database, Khadijah should avoid using the following computing devices: (i) devices on a wired internet connection, (ii) devices on a wireless internet connection, and (iii) devices with a GPS receiver.
If Kadijah is concerned about her geolocation getting tracked and stored in a database, she should avoid using devices with a GPS receiver.
These types of devices are designed to track and store location data, which could be used to identify her movements and activities. However, it's worth noting that many other devices can also be used to track geolocation data, including those on a wired or wireless internet connection. In general, the best way to avoid being tracked is to be aware of the data that you are sharing and take steps to limit it as much as possible. This may include using privacy-focused software and tools, avoiding sharing sensitive information online, and being cautious about the devices and services that you use.(i) devices on a wired internet connection,
(ii) devices on a wireless internet connection, and
(iii) devices with a GPS receiver.
These devices can track and store her geolocation, which she is concerned about.
Know more about the geolocation
https://brainly.com/question/30670654
#SPJ11
cloud kicks needs to change the owner of a case when it has been open for more than 7 days. how should the administrator complete this requirement?
Answers
To change the owner of a case when it has been open for more than 7 days, an administrator on Cloud Kicks can complete the requirement by creating a Workflow Rule that automatically assigns the case to a different owner after 7 days have passed.
Here's how the administrator can create this Workflow Rule on Cloud Kicks:
1: Navigate to Workflow Rules
Go to Setup > Create > Workflow Rules. Click on the 'New Rule' button to create a new rule.
2: Choose Object
Select the object on which the rule is to be created. In this case, it's the 'Case' object. Click on the 'Next' button.
3: Set Rule Criteria
Set the rule criteria to "Case: Date/Time Opened greater than 7 days" to ensure that the rule only applies to cases that have been open for more than 7 days.
4: Add Workflow Action
Click on the 'Add Workflow Action' button and select 'New Field Update.'
5: Define Field Update
In the 'New Field Update' dialog box, define the field update as follows:Field to Update: OwnerID
New Owner: [Enter the name of the new owner here]
6: Save Field Update
Click on the 'Save' button to save the field update.
7: Activate Workflow Rule
Click on the 'Activate' button to activate the workflow rule. Once activated, the rule will automatically assign cases to a new owner after they have been open for more than 7 days.
Learn more about workflow rules at:
https://brainly.com/question/16968792
#SPJ11
The experimental Synthesis operating system has an assembler incorporated in the kernel. To optimize system-call performance, the kernel assembles routines within kernel space to minimize the path that the system call must take through the kernel. This approach is the antithesis of the layered approach, in which the path through the kernel is extended to make building the operating system easier. Discuss the pros and cons of the Synthesis approach to kernel design and system-performance optimization.
Answers
Experimental Synthesis operating system's approach to kernel design and system-performance optimization have the following pros and cons:Pros:Reduced system call execution time: Because the kernel builds and assembles routines within kernel space, the system call path through the kernel is shortened, resulting in faster system call execution times.
Less overhead: The Synthesis approach reduces overhead by assembling routines within the kernel space rather than passing them through many layers. Less complex: By including an assembler in the kernel, Synthesis significantly reduces the number of layers involved in a system call, making the operating system less complicated and more efficient. A faster, smoother system: With less overhead and a simplified approach, Synthesis can optimize the performance of system calls, resulting in a quicker and smoother operating system experience. Cons:Less modular: The Synthesis approach is less modular than the layered approach since it reduces the number of layers and consequently the modularity. Limited flexibility: Synthesis has a limited ability to modify the operating system's behavior and features due to the simplified approach and reduced modularity.
More challenging to develop and debug: Due to the reduced modularity and increased complexity, the Synthesis approach can be more difficult to develop and debug than the layered approach.
To know more about optimization visit:-
https://brainly.com/question/28587689
#SPJ11
Which of the following statements is valid?SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal = MAX(InvoiceTotal)SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal = (SELECT MAX(InvoiceTotal))SELECT InvoiceNumber, VendorNameFROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorIDWHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)All of the above
Answers
Correct Answer:
c.
SELECT InvoiceNumber, VendorName
FROM Invoices JOIN Vendors ON Invoices.VendorID = Vendors.VendorID
WHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)
Explanation:
All options only differ on the WHERE clause:
a: WHERE InvoiceTotal = MAX(InvoiceTotal)
Fails because aggregate functions (like MAX, COUNT, etc) have to be used on the SELECT clause.
b: WHERE InvoiceTotal = (SELECT MAX(InvoiceTotal))
Fails because the SELECT clause is incomplete.
c: WHERE InvoiceTotal IN (SELECT MAX(InvoiceTotal) FROM Invoices)
This one is correct, and returns the InvoiceNumber and VendorName register with the largest value on the InvoiceTotal field.
state two reasons why you would upload and download information
Answers
Answer:
get a better understanding of the problem
Explanation:
to be able to understand what it means and to be able to remember it in the future
Which of the following are addressed by programing design? Choose all that apply.
Who will work on the programming
The problem being addressed
The goals of the project
The programming language that will be used
Answers
Answer:
Its B, D, and E
Explanation:
Hope this helps
Answer:
3/7
B
D
E
4/7
Just a page
5/7
B
C
6/7
Page
7/7
A
B
D
9. What command do you enter in the Explorer search box to access the Remote Admin share on the computer named Fin?
Answers
Answer:
\\computername\admin$
Explanation:
give three causes for a running process to relinquish the cpu. in each case, what state does the scheduler put the process in?
Answers
There are several reasons why a running process may relinquish the CPU.
Three common causes are:
1. I/O Wait: When a process is waiting for input or output to complete, it may relinquish the CPU to avoid wasting resources. In this case, the scheduler puts the process in the waiting state.
2. Preemption: When a higher-priority process becomes ready to run, it may preempt the currently running process to ensure that the system runs as efficiently as possible. In this case, the scheduler puts the preempted process in the ready state.
3. Completion: When a process finishes executing, it relinquishes the CPU to allow other processes to run. In this case, the scheduler puts the process in the terminated state.
In all three cases, the scheduler is responsible for managing the process and ensuring that it runs efficiently. By carefully managing the state of each process, the scheduler can ensure that the system operates smoothly and that each process receives the resources it needs to complete its work.
Learn more about CPU here:
https://brainly.com/question/16254036
#SPJ11
1. How do we know if the information in a websites is fake or not?
2. How important is respect for truth?
Answers
Answer: 1)Ingrese la URL del sitio web y podrá ver detalles como el nombre de la organización del propietario, el país de registro y la antigüedad del dominio
2)Como individuos, ser veraces significa que podemos crecer y madurar, aprendiendo de nuestros errores
Explanation:
The user is told to guess a number between one and 10.
Which responses from the user could cause the program to halt with an error statement? Choose two options.
two
2.5
12
-3
0
Answers
Answer:
0 and -3
Explanation:
These two options do not fall within 1 and 10.
Answer:
2.5 and two
are the answers