While browsing the Internet, You notice that your browser displays pop-ups containing advertisements that are related to recent keywords searches you have performed.
What is this an example of?
Adware.
Answers
The advertisements that are related to recent keywords searches that performed before is adware.
What is adware?Adware is a software to create and display the pop-ups advertisement that have potential to carry malware. Adware is capable to tracking your search history and online activity to get the relevant keywords in order to be able to personalize ads that are more relevant to you.
Adware that carries malware hides in your computer system and runs in the background to monitor all your online activity so that it can provide personalized advertisements for you.
Learn more about malware here:
brainly.com/question/29650348
#SPJ4
Related Questions
You are troubleshooting an issue where a PC can reach some hosts on the Internet (using either DNS name or IP address), while several other hosts on the Internet are not reachable. From the PC you can Ping all devices on your local subnet. What is most likely causing the problem?
Answers
The options are missing from the question,below are the options to choose from;
A) incorrect (or missing) routes in a routers routing table
B) incorrect DNS configuration on the PC
C) incorrect default gateway configuration on the PC
D) duplicate IP addresses on your LAN
Answer: The correct answer to the question is option A
INCORRECT (OR MISSING) ROUTES IN A ROUTERS ROUTING TABLE.
Explanation: When it is possible for a PC to ping some devices but not actually all,we can then make an assumption that either it has a wrong subnet that is configured or the router from the path to the remote device actually has an incorrect or a missing routes to the device.
Cybersecurity is defined as the set of techniques to protect the secrecy, integrity, and availability of computer systems and data against threats. (true or false)
Answers
Answer:
The answer is true because it protects our secret accountIn this c++ assignment, add an undo feature to a list of strings.
Here's a working class called Stringlist that implements a simple string list as a dynamic array. Stringlist_test.cpp has tests for all the methods in Stringlist.
Stringlist has one unimplemented method:
// Undoes the last operation that modified the list. Returns true if a
// change was undone, false otherwise.
//
bool undo()
{
cout << "Stringlist::undo: not yet implemented\n";
return false;
}
Your job is to implement undo, thus making Stringlist an undoable list.
Your implementation must follow these rules:
Do not delete any methods, or change the signatures of any methods, in Stringlist. You can change the implementation of existing methods if necessary. But they should still work the same way: your finished version of Stringlist with undo implement must still pass all the tests in Stringlist_test.cpp.
You can add other helper methods (public or private), functions, and classes/structs to Stringlist.h if you need them.
You must implement undo() using a private stack that is accessible only inside the Stringlist class. Implement the stack yourself as a linked list. Do not use arrays, vectors, or any other data structure for your stack.
Do not use any other #includes or #pragmas in Stringlist.h other than the ones already there.
When it's done, you'll be able to write code like this:
#include "Stringlist.h"
#include
using namespace std;
int main() {
Stringlist lst;
cout << lst << endl; // {}
lst.insert_back("one");
lst.insert_back("two");
lst.insert_back("three");
cout << lst << endl; // {"one", "two", "three"}
lst.undo();
cout << lst << endl; // {"one", "two"}
lst.undo();
cout << lst << endl; // {"one"}
lst.undo();
cout << lst << endl; // {}
}
Designing the Undo Stack
As mentioned above, you must implement undo() using at least one private stack implemented as a linked list inside the Stringlist class. You can modify Stringlist only as described at the start of this assignment.
examples of how specific methods should work.
Undoing insert_before
In code:
// lst == {"dog", "cat", "tree"}
lst.insert_before(3, "hat");
// lst == {"dog", "cat", "tree", "hat"}
lst.undo();
// lst == {"dog", "cat", "tree"}
lst.insert_before(1, "shoe");
// lst == {"dog", "shoe", "cat", "tree"}
lst.undo();
// lst == {"dog", "cat", "tree"}
Undoing set
For set, suppose that lst is {"yellow", "green", "red", "orange"}, and so lst.get(2) returns "red". If you call lst.set(2, "cow"), then you should push the operation set location 2 to "red" onto the undo stack, and then over-write location 2 with "cow".
In code:
// lst == {"yellow", "green", "red", "orange"}
lst.set(2, "cow");
// lst == {"yellow", "green", "cow", "orange"}
lst.undo();
// lst == {"yellow", "green", "red", "orange"}
Undoing remove_at
For remove_at
In code:
// lst == {"dog", "cat", "tree"}
lst.remove_at(1);
// lst == {"dog", "tree"}
lst.undo();
// lst == {"dog", "cat", "tree"}
Undoing operator=
For operator=,
In code:
// lst1 == {"dog", "cat", "tree"}
// lst2 == {"yellow", "green", "red", "orange"}
lst1 = lst2;
// lst1 == {"yellow", "green", "red", "orange"}
// lst2 == {"yellow", "green", "red", "orange"}
lst1.undo();
// lst1 == {"dog", "cat", "tree"}
// lst2 == {"yellow", "green", "red", "orange"}
As this shows, when you undo operator=, the entire list of strings is restored in one call to undo().
Important notes:
If lst1 and lst2 are different objects, then when lst2 is assigned to lst1 just the underlying string array of lst2 is copied to lst1. The lst1 undo stack is updated so that it can undo the assignment. The undo stack of lst2 is not copied, and lst2 is not modified in any away.
Self-assignment is when you assign a list to itself, e.g. lst1 = lst1;. In this case, nothing happens to lst1. Both its string data and undo stack are left as-is.
Undoing remove_all
For remove_all,
In code:
// lst == {"dog", "cat", "tree"}
lst.remove_all();
// lst == {}
lst.undo();
// lst == {"dog", "cat", "tree"}
Note that it should work the same way when lst is empty:
// lst == {}
lst.remove_all();
// lst == {}
lst.undo();
// lst == {}
Undoing Other Methods
undo() should undoall the other methods in Stringlist that are marked as "undoable" in the source code comments.
As mentioned above, undo() is not undoable. There is no "re-do" feature in this assignment.
Each method in Stringlist.h marked "undoable" should work correctly with undo(). This also includes the correct behaviour for the Stringlist copy constructor (which should not copy the undo stack).
The markers tests should run correctly, including with no memory leaks according to valgrind.
Answers
To implement the undo feature in the Stringlist class, you will need to modify the existing class and add a private stack implemented as a linked list. Here are the steps to follow:
How to write the program code1. In the Stringlist class in Stringlist.h, add a private struct called `UndoNode` to represent each node in the undo stack. Each node should store the necessary information to undo an operation (e.g., the method name, the arguments, and any other relevant data).
```cpp
private:
struct UndoNode {
std::string method; // The method name
// Add other necessary data for the specific method being undone
// ...
UndoNode* next; // Pointer to the next node in the stack
UndoNode(const std::string& m) : method(m), next(nullptr) {}
};
```
2. Add a private member variable `undoStack` of type `UndoNode*` to the Stringlist class to keep track of the undo stack.
```cpp
private:
// Other private member variables
UndoNode* undoStack;
```
3. Modify the undoable methods in the Stringlist class to push the necessary information onto the undo stack before performing the operation. For example, in the `insert_before` method:
```cpp
void insert_before(size_t index, const std::string& str) {
// Push the operation onto the undo stack
UndoNode* undoNode = new UndoNode("insert_before");
// Add necessary data to the undoNode (e.g., index and str)
// ...
// Perform the actual operation
// ...
// Add the undoNode to the top of the stack
undoNode->next = undoStack;
undoStack = undoNode;
}
```
4. Implement the `undo` method to pop the top node from the undo stack and perform the undo operation based on the stored information. You will need to handle each operation individually in the `undo` method.
```cpp
bool undo() {
if (undoStack == nullptr) {
std::cout << "Undo stack is empty." << std::endl;
return false;
}
UndoNode* undoNode = undoStack;
undoStack = undoStack->next;
// Perform the undo operation based on the stored information in undoNode
if (undoNode->method == "insert_before") {
// Undo the insert_before operation
// ...
} else if (undoNode->method == "set") {
// Undo the set operation
// ...
}
// Handle other operations...
delete undoNode;
return true;
}
```
Remember to handle memory deallocation appropriately and update other methods marked as "undoable" accordingly.
Read more on Java codes here https://brainly.com/question/25458754
#SPJ1
Which of the following would be used to communicate a high level description of a major change
Answers
A Change Proposal would be used to communicate a high-level description of a major change that involved significant cost and risk to the organization. Thus option D is correct.
What are a cost and risks?The price of mitigating risk and suffering losses. The sum of all costs associated with a firm's activities that are linked to risk, such as retention costs and associated less any charges
To convey a high-level summary of a patch, utilize a change proposal. Typically, the service portfolio method produces this encouragement and inspiration, which is then forwarded to deal with different situations for approval.
Therefore, option D is the correct option.
Learn more about cost and risks, Here:
https://brainly.com/question/2149007
#SPJ1
The question is incomplete, the complete question will be :
Which of the following would be used to communicate a high-level description of a major change that involved significant cost and risk to the organization?
1) Service Request
2) Change Policy
3) Risk Register
4) Change Proposal
Solving Systems of Equations by Substitution
pdf

Answers
Summary of Activities: Learning/Insights:

Answers
Summary of Activities:
Gathering Information: Researching, collecting data, and gathering relevant information from various sources such as books, articles, websites, or experts in the field.
What is the Summary about?Others are:
Analysis: Reviewing and analyzing the gathered information to identify patterns, trends, and insights. Extracting key findings and observations from the data.Synthesis: Organizing and synthesizing the gathered information to create a coherent and structured overview of the topic or subject.Reflection: Reflecting on the findings and insights obtained from the research and analysis. Considering their implications, relevance, and potential applications.Evaluation: Assessing the quality, reliability, and validity of the information and insights obtained. Evaluating the strengths and weaknesses of the findings and the research process.Lastly, Application: Applying the obtained knowledge and insights to real-life situations, problem-solving, decision-making, or creative ideation.
Read more about Summary here:
https://brainly.com/question/27029716
#SPJ1
How many steps are in the SECRET to keyboarding success video?
4
5
6
7
Answers
Answer:
5
Explanation:
Answer:
there is 6 secrets
Explanation:
1. sit up straight
2.keep eyes on the txt
3.use the correct finger
4. keep a reasonable rhythm
5.erase your errors
6.tap the keys quickly
Suppose that i and j are both of type int. What is the value of j after the following statement is executed?
for (i = 0, j = 0; i < 10; i++)
j += i;
Answers
Answer:
The value of j after the above statement is executed would be 45.
The for loop initializes both i and j to 0, and then runs a loop that executes 10 times. Each time the loop runs, i is incremented by 1. The statement j += i adds the current value of i to j.
Since i starts at 0 and is incremented by 1 each time the loop runs, the values of i in each iteration of the loop are 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9. The statement j += i adds these values to j in each iteration, so the final value of j after the loop is finished running is 0 + 1 + 2 + 3 + 4 + 5 + 6 + 7 + 8 + 9 = 45.
While setting up annetwork segment you want to check the functionality cable before putting connectors on them. You also want to meaure the termination point or damange in cable which tool used
Answers
A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
What is network Segementation?Segmentation works by regulating the network's traffic flow. The term "network segmentation" should not be confused with "microsegmentation," which limits east-west communication at the workload level in order to lower an organization's network attack surface.
Despite having some uses, microsegmentation should not be confused with standard network segmentation.
A network is divided into several zones via network segmentation, and each zone or segment is independently managed. To regulate what traffic is allowed to pass through the segment and what is not, traffic protocols must be used.
Dedicated hardware is used to create network segments that are walled off from one another and only permit users with the proper credentials to access the system.
Therefore, A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
To learn more about network, refer to the link:
https://brainly.com/question/15088389
#SPJ1
You are working for a government contractor who requires all users to use a PIV device when sending digitally signed and encrypted emails. Which of the following physical security measures is being implemented?
Options are :
Smart card
Key fob
Biometric reader
Cable lock
Answers
Answer: Smart Card.
Explanation: A Personal Identity Verification device is a smart card that is used to store a user's digital identity and provide secure access to government computer systems. By requiring users to use a PIV device when sending digitally signed and encrypted emails, the government contractor is implementing the use of smart cards as a physical security measure. Smart cards are secure, portable, and can be used to provide strong authentication and encryption for a wide range of applications, including digital signatures and encrypted emails. They offer a high level of security by requiring a user to physically possess the card in order to access its stored information.
BRAINLIEST AND 50 POINTS PLEASE AND FAST FAST FAST FAST FAST!!!!!!
What are three things that the use of color on a website do?
Answers
Answer: Colors can attract the attention of others, create the environment for a website, and it has an impact on how people feel about that website. When you dig into the psychology part of it, there is a variety of different things you can do with color on a website.
1.
Question 1
An online gardening magazine wants to understand why its subscriber numbers have been increasing. What kind of reports can a data analyst provide to help answer that question? Select all that apply.
1 point
Reports that examine how a recent 50%-off sale affected the number of subscription purchases
Reports that describe how many customers shared positive comments about the gardening magazine on social media in the past year
Reports that compare past weather patterns to the number of people asking gardening questions to their social media
Reports that predict the success of sales leads to secure future subscribers
2.
Question 2
Fill in the blank: A doctor’s office has discovered that patients are waiting 20 minutes longer for their appointments than in past years. To help solve this problem, a data analyst could investigate how many nurses are on staff at a given time compared to the number of _____.
1 point
doctors on staff at the same time
negative comments about the wait times on social media
patients with appointments
doctors seeing new patients
3.
Question 3
Fill in the blank: In data analytics, a question is _____.
1 point
a subject to analyze
an obstacle or complication that needs to be worked out
a way to discover information
a topic to investigate
4.
Question 4
When working for a restaurant, a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions. What is this an example of?
1 point
An issue
A business task
A breakthrough
A solution
5.
Question 5
What is the process of using facts to guide business strategy?
1 point
Data-driven decision-making
Data visualization
Data ethics
Data programming
6.
Question 6
At what point in the data analysis process should a data analyst consider fairness?
1 point
When conclusions are presented
When data collection begins
When data is being organized for reporting
When decisions are made based on the conclusions
7.
Question 7
Fill in the blank: _____ in data analytics is when the data analysis process does not create or reinforce bias.
1 point
Transparency
Consideration
Predictability
Fairness
8.
Question 8
A gym wants to start offering exercise classes. A data analyst plans to survey 10 people to determine which classes would be most popular. To ensure the data collected is fair, what steps should they take? Select all that apply.
1 point
Ensure participants represent a variety of profiles and backgrounds.
Survey only people who don’t currently go to the gym.
Collect data anonymously.
Increase the number of participants.
Answers
The correct options are:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasespatients with appointmentsa way to discover informationA business taskData-driven decision-makingWhen conclusions are presentedFairnessa. Ensure participants represent a variety of profiles and backgrounds.c. Collect data anonymously.d. Increase the number of participants.What is the sentences about?This report looks at how many people bought subscriptions during a recent sale where everything was half price. This will show if the sale made more people subscribe and if it helped increase the number of subscribers.
The report can count how many nice comments people said and show if subscribers are happy and interested. This can help see if telling friends about the company has made more people become subscribers.
Learn more about gardening from
https://brainly.com/question/29001606
#SPJ1
Reports, investigating, fairness, data-driven decision-making, gym classes
Explanation:Question 1:A data analyst can provide the following reports to help understand why the subscriber numbers of an online gardening magazine have been increasing:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasesReports that describe how many customers shared positive comments about the gardening magazine on social media in the past yearReports that compare past weather patterns to the number of people asking gardening questions on their social mediaReports that predict the success of sales leads to secure future subscribersQuestion 2:A data analyst could investigate the number of patients with appointments compared to the number of doctors on staff at a given time to help solve the problem of longer waiting times at a doctor's office.
Question 3:In data analytics, a question is a topic to investigate.
Question 4:When a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions for a restaurant, it is an example of a business task.
Question 5:The process of using facts to guide business strategy is called data-driven decision-making.
Question 6:A data analyst should consider fairness when conclusions are being presented during the data analysis process.
Question 7:Transparency in data analytics is when the data analysis process does not create or reinforce bias.
Question 8:To ensure the collected data is fair when surveying 10 people to determine popular classes for a gym, a data analyst should: ensure participants represent a variety of profiles and backgrounds, collect data anonymously, and increase the number of participants.
Learn more about Data analysis here:https://brainly.com/question/33332656
Write a partial class that shows a class constant and an instance method. Write an instance method that converts feet to inches using a class constant representing the number of inches in one foot. The value passed to the method represents the distance in feet.
Answers
Answer:
Please the code snippet below, the code was writen in Kotlin Language
Explanation:
const val inches:Int= 12 . //This is the const value
fun main(args: Array<String>) {
//this will ask the user for input
print("Enter a number")
//this will do the conversion
var valueInFeet= Integer.valueOf(readLine())*inches
print("The value in feet is $valueInFeet feet(s)")
}
discuss 5 features of mobile phones and how it can help play in a holistic digital marketing strategy
Answers
Answer:
1. Mobile Friendly Website
Statistics claim that by 2013 more people will be accessing websites via their cell phones as opposed to desktops and laptops. This means that mobile optimized websites are more important now more than ever before.
2. SMS (Text) Alerts/Reminders
SMS has many useful applications in the mobile technology realm, one of which is alerts and reminders. Having the ability to contact your customers with simple text messages is non-intrusive and convenient. Two current examples of industries utilizing SMS alerts and reminders are banks and retail chains. Banks use this technology to alert customers of balances on their accounts. Retails chains can alert customers when certain products are discounted or available.
3. SMS Voting/Polling
Many of you may be familiar with this technology already. Television shows like American Idol and America’s Got Talent already utilize this technology to rank contestants. However, this technology is also helpful in the business world, where users can poll or vote on various products and services. What a great way to get valid feedback on your business!
4. Mobile Commerce
60% of consumers are purchasing goods and services on their mobile phones. They are also able to compare prices with competing vendors.
The invention of Near Field Communications (NFC) in the mobile commerce arena is going to explode. NFC allows you to wave your phone over a compatible device at your retailer to purchase goods or services. This ability to purchase products with your smartphone is a convenient technology that may one day “eliminate” the need for a wallet.
5. Mobile Applications
There’s an app for that, and that’s no joke. Companies and organizations worldwide have adopted the use of mobile apps to help increase awareness and revenue streams. Mobile apps can provide data such as product information, account information, games, scores to a sporting event, streaming audio, and this goes on and on.
Studies show that users prefer mobile games, social media, maps and music in the form of an app, as opposed to a web based interaction. There is a sense of security with an application that is installed and trusted by a relevant source on your mobile phone. This does not mean that mobile websites do not have their place, they do, and it’s up to the organization to determine the best use of a mobile web or mobile app.
Explanation:
Classify the following attributes as binary, discrete, or continuous. Also classify them as qualitative (nominal or ordinal) or quantitative (interval or ratio). Some cases may have more than one interpretation, so briefly indicate your reasoning if you think there may be some ambiguity. Example: Age in years. Answer: Discrete, quantitative, ratio
a)Time in terms of AM or PM.
b)Brightness as measured by a light meter.
c)Brightness as measured by people's judgments.
d)Angles as measured in degrees between 0 and 360.
e)Bronze, Silver, and Gold medals as awarded at the Olympics.
f)Height above sea level.
g)Number of patients in a hospital.
h)ISBN numbers for books. (Look up the format on the Web.)
i)Ability to pass light in terms of the following values: opaque, translucent' transparent.
j)Military rank.
k)Distance from the center of campus.
l)Density of a substance in grams per cubic centimeter.
m)Coat check number. (When you attend an event, you can often give your coat to someone who, in turn, gives you a number that you can use to claim your coat when you leave.)
Answers
Answer:
is A
Explanation:
With the development of the sundial in Ancient Egypt around 1500 B.C., the terms a.m. and p.m. were first used. The concept of 24 “hours” per day originated with the Egyptians. Thus, option A is correct.
What Time in terms of AM or PM?These Latin terms are used to describe time. Ante Meridian and Post Meridian are Latin terms that indicate “before noon” and “after midday,” respectively. Post Meriden, which means afternoon or after noon, is abbreviated as “P.M.”
Although early mechanical clocks displayed all 24 hours, clockmakers eventually discovered that the 12-hour method was easier and more affordable. A.M., or ante meridiem, is of course Latin for “before midday.
Therefore, A sundial uses the sun's location in the sky to tell the time, as its name suggests.
Learn more about Time here:
https://brainly.com/question/28050940
#SPJ5
warning 1 a reference was created to embedded interop assembly 'interop.acropdflib' because of an indirect reference to that assembly from assembly 'axinterop.acropdflib'. consider changing the 'embed interop types' property on either assembly. es-software v3.0
Answers
Because assembly2 and assembly1 both reference one other and have the Embed Interop Types property set to False, the compiler is unable to integrate interop type information from assembly1.
Meaning of embed interop typesUsing COM interop, such as in an application that makes use of automation objects from Microsoft Office, type embedding is widely employed. The same build of a software can be used with several machines' installations of Microsoft Office thanks to type information embedded in it.
What is cs1026 error?The statement was judged to be unfinished. Placing a statement within an inline expression on an ASP.NET website rather than an expression is a common reason for this problem.
To know more about compiler visit:-
https://brainly.com/question/28232020
#SPJ4
What is write the technical terms for the following statements. 3. A computer program that can hide and transfer from one computer to another without the notice of the user.
Answers
Answer:
I think it is computer virus I don't surly know
what is the first things u do upon seeing this sheet?
Answers
Answer:
umm ok
Explanation:
plz mark brainlyest
any computer and technology experts?
1. what is a file
2. what is a folder
3. what is a subfolder
4. how files are organized in folders and subfolders
5. what is a file extension
6. types of file extensions
7.the importance of file extensions
Answers
Answer:
file is the common storage unit in a computer, and all programs and data are "written" into a file and "read" from a file. A folder holds one or more files, and a folder can be empty until it is filled. A folder can also contain other folders, and there can be many levels of folders within folders.
a subfolder is an organizational folder on a computer that is located within another folder
Explanation:
sorry i dont know all
Explain the different hardware used by local network
Answers
The different hardware used by local network are:
Routers hubsswitchesbridges, etc.What is the role of the hardware?The hardware are tools that aids in the act of connecting a computer or device to any form of local area network (LAN).
Note that hardware components needed also are:
A network interface card (NIC) A wireless network interface controller (WNIC) A transmission medium , wired or wireless.Learn more about local network from
https://brainly.com/question/1167985
#SPJ1
Olivia wants to change some settings in Outlook. What are the steps she will use to get to that function? open Outlook → File → Export open Outlook → View → Settings open Outlook → File → Options open Outlook → Home → Options
Answers
write a program to count the number of space present in a text file "python.txt"
Answers
Using the codes in computational language in python it is possible to write a code that write a program to count the number of space present in a text file "python.txt".
Writting the code:def countlines(fname,mode='r+'):
count=0
with open(fname) as f:
for _ in f:
count += 1
print('total number of lines in file : ',count)
countlines('file1.txt')
##########################
with open('file1.txt') as f:
print(sum(1 for _ in f))
###########################
'''You can use len(f.readlines()),
but this will create an additional list in memory,
which won't even work on huge files that don't fit in memory.
'''
See more about python at brainly.com/question/18502436
#SPJ1

How is a collapsed qubit similar to a bit?
Answers
The collapsed qubit similar to a bit as it has a single value of either 0 or 1.
What is the difference between a qubit and a bit?Note that a classical computer is one that has a memory composed of bits that is, each bit is known to hold a one or a zero.
Note also that a qubits (quantum bits) is one that can hold a one, a zero or can also superposition the both.
Hence, The collapsed qubit similar to a bit as it has a single value of either 0 or 1.
See full question below
How is a collapsed qubit similar to a bit? It can stay in a state of superposition. It is still dependent on its counterparts. It has a single value of either 0 or 1. It has numerous potential paths to follow.
Learn more about qubit from
https://brainly.com/question/24196479
#SPJ1
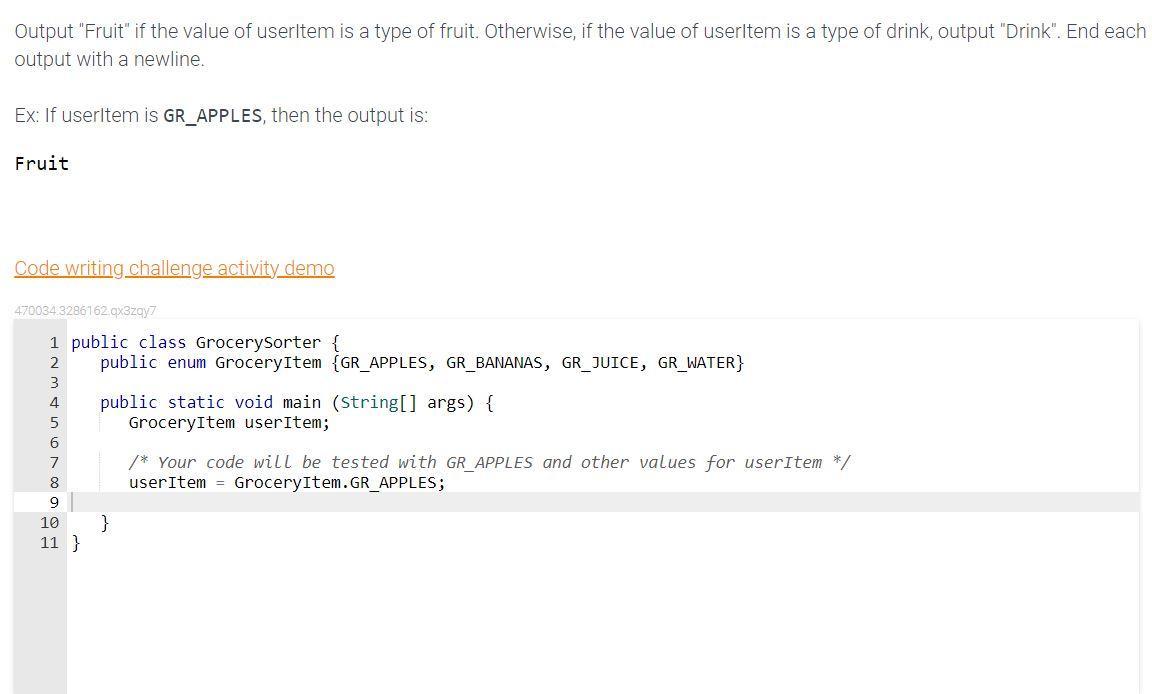
This is in Java.
Description:
Output "Fruit" if the value of userItem is a type of fruit. Otherwise, if the value of userItem is a type of drink, output "Drink". End each output with a newline.
Ex: If userItem is GR_APPLES, then the output is:
Fruit
Answers
Explanation:
public class GrocerySorter {
public static void main(String[] args) {
GroceryItem item = new GroceryItem("GR_APPLES", 1.99);
String itemName = item.getName();
if(itemName.startsWith("GR_")) {
System.out.println("Fruit\n");
} else {
System.out.println("Drink\n");
}
}
}
The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
What is program in Python?The program in Python, where comments are used to explain each line is as follows
#This gets input from the user
userItem = input("Item: ")
#This checks if user input is GR_APPLES or GR_BANANAS
if(userItem == "GR_APPLES" or userItem == "GR_BANANAS"):
#If yes, the program prints Fruit
print("Fruit")
#if otherwise, this checks if user input is GR_JUICE or GR_WATER
elif (userItem == "GR_JUICE" or userItem == "GR_WATER"):
#If yes, the program prints Drink
print("Drink")
#If otherwise
else:
#This prints Invalid
print("Invalid")
See attachment for sample run
Therefore, The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
Read more about conditional statements at:
brainly.com/question/4211780
#SPJ2
Write A C++ Program To Find If a Matrix Is a reflexive / irreflexive/Symmetric/Antisymmetric/Transitive.
Answers
A C++ Program To Find If a Matrix Is a reflexive / irreflexive/Symmetric/Antisymmetric/Transitive is given below:
Given the sample input:
0 1 2 3 //elements (A)
0 0 //relations (B)
1 1
2 2
3 3
x y z //elements (A)
x y //relations (B)
y z
y y
z z
x y z //elements (A)
x x //relations (B)
y z
x y
z y
x z
y y
z x
y x
z z
1 2 3 4 5 6 7 8 //elements (A)
1 4 //relations (B)
1 7
2 5
2 8
3 6
4 7
5 8
6 6
1 1
2 2
The Programbool pair_is_in_relation(int left, int right, int b[], int sizeOfB)
{
for(int i=0; i+1<sizeOfB; i+=2) {
if (b[i]==left && b[i+1]==right)
return true;
}
return false;
}
bool antiSymmetric(int b[], int sizeOfB)
{
bool holds = true;
for(int i=0; i+1<sizeOfB; i+=2) {
int e = b[i];
int f = b[i+1];
if(pair_is_in_relation(f, e, b, sizeOfB)) {
if (e != f) {
holds = false;
break;
}
}
}
if (holds)
std::cout << "AntiSymmetric - Yes" << endl;
else
std::cout << "AntiSymmetric - No" << endl;
return holds;
}
Read more about C++ programming here:
https://brainly.com/question/20339175
#SPJ1
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
Imagine that you have an image that is too dark or too bright. Describe how you would alter the RGB settings to brighten or darken it. Give an example.
Answers
This software agent helps people improve their work, assist in decision making, and facilitate their lifestyle. A) chatbot B) enterprise chatbot C) deep AI D) virtual personal assistant
Answers
The steps to follow in order to produce a Pivot table would be as mentioned below is Opting the columns for a pivot table. Now, make a click on the insert option.
What is pivot table?This click is followed by opting for the pivot table and the data columns that are available in it. After this, the verification of the range of the table is made and then, the location for the pivot table has opted.
After this, the column is formatted and the number option is selected followed by the currency option, and the quantity of decimal places. A Pivot table allows one to establish a comparison between data of distinct categories(graphic, statistical, mathematical) and elaborate them.
Therefore, The steps to follow in order to produce a Pivot table would be as mentioned below Opting the columns for a pivot table. Now, make a click on the insert option.
Learn more about 'Pivot Table' here:
brainly.com/question/13298479
#SPJ1
TWO (2) negative effects of how technology use in education affects students' learning. Your response should include a minimum of FIVE (5) credible sources.
Answers
Technological advancements have taken education to new heights, yet they have come with their fair share of drawbacks.
What is the explanation for the above response?Two such demerits of utilising technology in classrooms are distraction and lack of retention capacity among students.
Given the myriad choices provided by tech in terms of entertainment such as social networking sites or online games, students tend to lose focus and face negative consequences such as poor academic performance.
Technology dependency poses a vulnerability that can hinder student learning outcomes.
Students whose reliance rests solely on technology may face challenges related to critical thinking and problem-solving abilities - two necessary skills for achieving academic success.
Learn more about technology at:
https://brainly.com/question/28288301
#SPJ1
write an algorithm to determine the average of N numbers
Answers
Explanation:
STEP 1: START.
STEP 2: DEFINE n.
STEP 3: SET count = 1.
STEP 4: DEFINE xF, averageF.
STEP 5: SET sumF = 0.
STEP 6: ENTER n.
STEP 7: REPEAT STEP 8 to 10 UNTIL count<=n.
STEP 8: Enter xF.
An algorithm that is used to determine the average of N numbers is as follows:
Add all the numbers, and then divide their sum by N.What do you mean by Algorithm?An algorithm may be defined as a type of methodology that is significantly utilized for solving a problem or performing a computation. Algorithms act as an exact list of instructions that conduct specified actions step by step in either hardware- or software-based routines.
Following is the algorithm that represents the average of N numbers:
Step 1: Start.Step 2: Read the N number suppose "1, 2, 3, ....., N from the user.Step 3: Declared a variable "Avg".Step 4: sum of N numbers;Step 5: Avg=sum/N.Step 6:Display "Avg".Step 7 : End .Therefore, an algorithm that is used to determine the average of N numbers is well described above.
To learn more about the Algorithm, refer to the link:
https://brainly.com/question/24953880
#SPJ2