Which one of the following IoT components contains hardware that can be dynamically reprogrammed by the end user?
A. RTOS(Real-time OS)
B. SoC(System on a Chip)
C. FPGA
D. MODBUS
Answers
The IoT components that contain hardware that can be dynamically reprogrammed by the end user are C) FPGAs.
IoT components can be broken down into the following categories: Hardware components and Software components. There are several hardware components that make up the IoT system, including:
1. Microcontrollers
2. Single-board computers
3. SoC (System on a Chip)
4. Sensors and actuators
5. Memory
6. FPGA (Field Programmable Gate Array)
The following are some of the software components that make up the IoT system:
1. Operating Systems
2. Analytic tools
3. Communication protocols
4. Machine learning algorithms
5. Cloud computing platforms
6. Firmware
7. Device management
FPGA stands for Field Programmable Gate Array. It is a programmable integrated circuit, which means it can be reprogrammed after being manufactured. This implies that the user can reprogram an FPGA chip to suit a specific application. FPGA can be used to develop and deploy digital circuits, as well as to prototype new hardware designs. C) FPGA is the correct answer.
Learn more about FPGA visit:
https://brainly.com/question/30434774
#SPJ11
Related Questions
You have a small home network that uses 192.168.1.0 with the default subnet mask for the network address. The default gateway address is 192.168.1.254, and the router is providing DHCP on the network. The Wrk2 computer has been assigned the IP address of 192.168.1.55. Which of the following is considered the loopback address for the Wrk2 computer
Answers
In this scenario, the loopback address for the Wrk2 computer is 127.0.0.1. It is used for local network testing and communication within the device itself.
The loopback address for the Wrk2 computer in the given scenario is 127.0.0.1.
The loopback address is a special IP address used to test network connectivity on a local machine without actually sending data over a physical network. It allows a device to communicate with itself.
In IPv4, the loopback address is defined as 127.0.0.1 and it is reserved for this purpose. When a device sends data to the loopback address, it is looped back to the device itself without going out to the network.
In the given scenario, the Wrk2 computer has been assigned the IP address 192.168.1.55. This IP address belongs to the local network, and it can be used to communicate with other devices on the same network. However, if the Wrk2 computer wants to test its own network connectivity, it can use the loopback address 127.0.0.1.
For example, if the Wrk2 computer wants to check if its network stack is functioning properly, it can ping the loopback address. By sending a ping to 127.0.0.1, the Wrk2 computer will receive a response from itself, confirming that its network stack is working correctly.
Learn more about local network testing here:-
https://brainly.com/question/31106950
#SPJ11
while t >= 1 for i 2:length(t) =
T_ppc (i) (T water T cork (i- = - 1)) (exp (cst_1*t)) + T cork (i-1);
T cork (i) (T_ppc (i) - T pet (i- = 1)) (exp (cst_2*t)) + T_pet (i-1);
T_pet (i) (T cork (i)
=
T_air) (exp (cst_3*t)) + T_air;
end
T final ppc = T_ppc (t);
disp (newline + "The temperature of the water at + num2str(t) + "seconds is:" + newline + T_final_ppc + " Kelvin" + newline + "or" + newline +num2str(T_final_ppc-273) + degrees Celsius" + newline newline);
ansl = input (prompt, 's');
switch ansl case 'Yes', 'yes'} Z = input (IntroText); continue case {'No', 'no'} break otherwise error ('Please type "Yes" or "No"')
end
end
Answers
The given code describes a temperature change model that predicts the final temperature of water based on various input parameters such as the temperatures of cork, pet, and air.
It appears that you are providing a code snippet written in MATLAB or a similar programming language. The code seems to involve a temperature calculation involving variables such as T_ppc, T_water, T_cork, T_pet, and T_air. The calculations involve exponential functions and iterative updates based on previous values.
The model uses a set of equations to calculate the temperature changes for each component.
The equations used in the model are as follows:
T_ppc(i) = (T_water – T_cork(i-1)) * (exp(cst_1 * t)) + T_cork(i-1)T_cork(i) = (T_ppc(i) – T_pet(i-1)) * (exp(cst_2 * t)) + T_pet(i-1)T_pet(i) = (T_cork(i) – T_air) * (exp(cst_3 * t)) + T_airThese equations are implemented within a for loop, where the input variables t, T_water, T_cork, T_pet, cst_1, cst_2, cst_3 are provided, and the output variable T_final_ppc represents the final temperature of the water after the temperature change.
Additionally, the code includes a prompt that allows the user to enter "Yes" or "No." Choosing "Yes" continues the execution of the code, while selecting "No" stops the code.
Overall, the code simulates and predicts the temperature changes of water based on the given inputs and equations, and offers the option to continue or terminate the execution based on user input.
Learn more about MATLAB: https://brainly.com/question/13715760
#SPJ11
In January, a company pays for advertising space in the local paper for ads to be run during the months of January, February, and March at $1,600 a month. The journal entry to record the payment would debit:
Answers
The journal entry to record the payment made by the Company for advertising space in the local paper for ads to be run during January, February, and March at $1,600 a month would be as follows:
Debit: Prepaid Advertising Expense - $4,800
Credit: Cash - $4,800
This journal entry reflects the fact that the Company has paid for the advertising space in advance and is therefore entitled to the use of this space for the next three months. The Prepaid Advertising Expense account represents the amount of the payment that has not yet been used up and will be recognized as an expense in the appropriate months.
As each month passes, the Company will recognize a portion of the Prepaid Advertising Expense as an expense on its income statement. For example, in January, the Company will recognize $1,600 of the prepaid expense as an expense, and the following journal entry will be recorded:
Debit: Advertising Expense - $1,600
Credit: Prepaid Advertising Expense - $1,600
This process will be repeated in February and March until the entire prepaid expense has been recognized as an expense.
To learn more about payment:
https://brainly.com/question/32320091
#SPJ11
PLEASE HURRY! Match terms in the first column with the order descriptions in column two.
1. Megabytes, gigabytes, terabytes
2. Petabytes, terabytes, kilobytes
3. Exabytes, zettabytes, megabytes
1. ordered from largest to smallest
2. in no apparent order
3. ordered from smallest to largest
Answers
Megabytes gigabytes terabytes - from smallest to largest
Petabytes terabytes kilobytes - largest to smallest
Exabytes zettabytes megabytes - in no apparent order
Explanation:
The matching of the first column with the order descriptions in column two is as follows:
Megabytes, gigabytes, terabytes: from smallest to largest.Petabytes, terabytes, kilobytes: largest to smallest.Exabytes, zettabytes, megabytes: in no apparent order. What are the units of storage capacity in computers?Decimal units such as kilobytes (KB), megabytes (MB), and gigabytes (GB) are commonly used to express the size of data. Binary units of measurement include kibibyte (KiB), mebibyte (MiB), and a gibibyte (GiB).
These units are categorized as follows:
Kilobyte: 1 thousand or, 1,000 bytes.Megabyte: 1 million, or 1,000,000 bytes.Gigabyte: 1 billion, or 1,000,000,000 bytes.Terabyte: 1 trillion, or 1,000,000,000,000 bytes.Petabyte: 1 quadrillion, or 1,000,000,000,000,000 bytes.Therefore, the matching of the first column with the order descriptions in column two is well mentioned above.
To learn more about Storage units, refer to the link:
https://brainly.com/question/232506
#SPJ2
Project manager Kevin has to create a project team organizational chart. Which activity should he perform before creating this chart?

Answers
Answer: C
Explanation: Allocating roles to project team members.
Ballet was originally created for the wedding celebration of Louis XVI and Marie Antoinette. (True or False)
Answers
Answer:
true
Explanation:
Which PowerPoint feature will you use to apply motion effects to different objects of a slide? A. Slide transition B. Slide design C. Animation movement D. Animation effects
Answers
Answer:
D. animation effects
firewall rules evaluate from top to bottom. the rule creators intended to block access to a website hosted at 10.15.1.2, except from hosts located on the 10.20.0.0/16 subnet. however, users on that subnet report that they cannot access the site. what is wrong?
Answers
The reason users cannot access the site is: The rules are misordered.
About Firewall:
A firewall is a type of network security device used in computing that keeps track of and regulates incoming and outgoing network traffic according to pre-set security criteria. A firewall often creates a wall between a reliable network and an unreliable network, like the Internet.
Firewall Rules:
The access control method employed by firewalls to protect your network from malicious apps and illegal access is called the firewall rules. Your firewall's acceptance and denial of different types of traffic are controlled by firewall rules. The firewall access policy is a set of firewall rules. Each network packet's control information is examined, and based on the standards you specify, they are either blocked or allowed. Each package is first assessed from top to bottom, and its constituent parts are contrasted with those of the policy regulations. Then, all of the steps specified in the stated parameters of the first matching rule's configured action are carried out.
Every firewall rule matches packet characteristics against a collection of shared rule elements. The packet's source address (Source), destination address (Destination), protocol and port numbers (Service), the interface it travels across (Interface), the direction it is traveling in (Direction), and the time of arrival are among the rule components that are displayed as fields (Time).
User can fix this mistake by reversing the order of rules 2 and 3. Any communication from the network 10.20.0.0/16 also matches rule 2, which blocks it, thus rule 3, which allows access, will never be activated.
To learn more about firewall rules visit:
https://brainly.com/question/13132276
#SPJ4
The question is incomplete. Below is the complete question:
The firewall rule creators intended to block access to a website hosted at 10.15.1.2 except from hosts located on the 10.20.0.0/16 subnet. However, users on that subnet report that they cannot access the site. What is wrong?
A.The protocol is incorrect.
B.The rules are misordered.
C.The source port is not specified.
D.There is no error in the rule, and Travis should check for other issues.
WHO IS YOUR FAVORITE FNAF CHARACTER?
Pick at least since there’s a lot-
Ill go first!
1: lolbit ofc
2: Roxanne
3: lefty
4: spring trap
5: Funtime foxy<3
6: foxy (og)
7: SHADOW FREDDY
Answers
Answer:
I really like rockstar freddy, toy bonnie, mangle and balloon boy.
Explanation:
How do I create a for loop in MATLAB?
Answers
There is one additional approach to retrieve array elements using the for loop. Here, we immediately add an array to the for loop so that the iterator variable can access its elements (i.e., I or j etc).
How is a for loop used?To repeat a certain block of code a predetermined number of times, use a "For" loop. We loop from 1 to that number, for instance, to verify each student's grade in the class. We utilize a "While" loop when it is unknown how many times something will happen.
In MATLAB, how do you repeat a function?action is repeated n times by the function repeat(action, n). The input arguments can be specified in any order. The action is repeated n times using the functions repeat(action,n) and repeat(n,action).
To learn more about iterator variable here:
https://brainly.com/question/12475735
#SPJ4
Acquiring new knowledge and skills at every stage of life:
A. internship
B. apprenticeship
C. job shadow
D . lifelong learning
Answers
d. lifelong learning
Answer:
D . lifelong learning
Explanation:
Lifelong learning is acquiring new knowledge and skills at every stage of life. Internship, apprenticeship, and job shadowing are all forms of learning, but they are not the same as lifelong learning. Lifelong learning is a continuous process of learning throughout one's life, while internship, apprenticeship, and job shadowing are typically limited to a specific period of time or job.
What is the output?
a = []
a.append([2, 4, 6, 8, 10])
a.append(['A', 'B' , 'C', 'D', 'E'])
a.append([111, 222, 333, 444, 555])
a.append(['roses', 'daisies', 'tulips', 'clover', 'zinnias'])
print(a [2] [4])
555
E
D
444
Answers
Note that the output of the code is: 555
What is the explanation for the above response?The list a has four elements, each of which is a list itself. The expression a[2] accesses the third element of a, which is the list [111, 222, 333, 444, 555].
The expression a[2][4] accesses the fifth element of that list, which is 555. Therefore, the output of the code is 555.
A computer code is a set of instructions written in a specific programming language that can be executed by a computer to perform a particular task or achieve a specific goal.
Learn more about code at:
https://brainly.com/question/28848004
#SPJ1
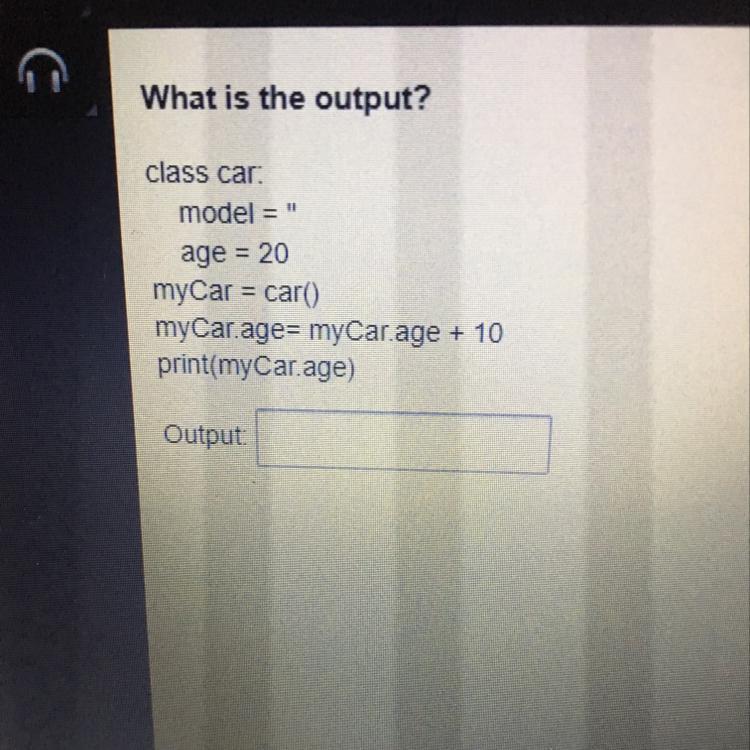
What is the output?
class car:
model = "
age = 20
myCar = car()
myCar.age= myCarage + 10
print(myCarage)
Output:
Answers
Answer:
Following are the modified code to this question:
class car:#defining a class car
model = ""#defining a class
age = 20#defining an integer variable that hold a value
myCar = car()#creating reference of class
myCar.age= myCar.age+ 10#Use reference to add value in age variable
print(myCar.age)#print age value
Output:
30
Explanation:
In the above code class care is defined, inside the car a string variable "model", and an integer variable "age" is defined that hold a value, in the next step, class reference myCar is defined, that used to add value in age variable an at the last we use print method to print age variable value.
which of the following is not a typical role for a computer scientist on a development team? a.) systems administrator b.) database administrator c.) computer engineer d.) programming language specialist
Answers
Computer Engineer is not a typical role for a computer scientist on a development team.
What is a Computer Engineer?
A computer engineer is someone who combines electrical engineering and computer science to create new technology. Modern computers' hardware is designed, built, and maintained by computer engineers.
These engineers are concerned with safely and efficiently integrating hardware and software in a unified system. Computer engineers, cybersecurity professionals, and systems analysts are the second-largest category of tech jobs, according to CompTIA.
In addition to personal devices, computer engineers contribute to the development of robotics, networks, and other computer-based systems. This position entails a significant amount of research and development, testing, and quality assurance. Problem solvers and technology enthusiasts may be drawn to computer engineering.
Computer engineers collaborate with software developers and other tech professionals as part of a team. The field necessitates strong foundations in science and mathematics, and the majority of employees have a related bachelor's degree. Certifications in software, programming languages, or hardware systems can open up new doors for employment.
To learn more about Computer Engineering, visit: https://brainly.com/question/24181398
#SPJ1
What is the process of displaying large quantities of data in a meaningful way called?
Answers
what is the essence of proper nutrition?
Answers
Answer:
Proper nutrition is about balance, and that means not getting too much of certain ingredients, such as sodium, or salt. Sodium increases blood pressure, which raises the risk of heart disease and stroke.
Explanation:
Answer:
Explanation:
Most people know good nutrition and physical activity can help maintain a healthy weight. But the benefits of good nutrition go beyond weight. Good nutrition can help: Reduce the risk of some diseases, including heart disease, diabetes, stroke, some cancers, and osteoporosis.
convert 4.75 base 10 to binary equivalent
Answers
Answer:
100
Explanation:
write a function which takes a pointer to the beginning of a linked list of integers (that is, a pointer to the first node) and an integer d > 0 and returns a pointer to a new list whose nodes have only integers from the original list which were divisible by d
Answers
An number d > 0 and a pointer toward the first node of a linear search of integers are both required by C++ code.
Is C++ coding simple?Compared to other widely used programming languages including Python and Java, C++ is regarded as one of the hardest to master. C++ is difficult to master because of its complex structure and more sophisticated syntax.
Briefing:
C++ Code:
#include <iostream>
using namespace std;
// Create a node
struct Node {
int item;
struct Node* next; // points to the next node
};
void printList(struct Node*);
void insert(struct Node** , int );
struct Node* divisibleBy(struct Node** , int);
struct Node* divisibleBy(struct Node** ref, int d) {
struct Node* newListHead = NULL; // head of the new linked list
struct Node* temp = *ref; // temporary reference to iterate throught the linked list
if(d == 1) { // if d = 1 then
newListHead = temp; //copy the linked list to an new linked and return
return newListHead;
}
else {
while(temp != NULL) {
if(temp->item % d == 0) { // if the reminder is 0
insert(&newListHead,temp->item); // insert that particular element to the new linked list
}
temp = temp->next; // increment the reference to the next node
}
}
return newListHead; // returning the referece of an new linked list
}
void insert(struct Node** ref, int data) {
struct Node* new_node = (struct Node*)malloc(sizeof(struct Node)); // dynamic memeory allocation for node
struct Node* last = *ref; //temporary reference of node
new_node->item = data;
new_node->next = NULL;
if (*ref == NULL) { // if the ref is null then new_node will be head
*ref = new_node;
return;
}
while (last->next != NULL)
last = last->next; // reaching the last node in the linked list
last->next = new_node; // assigning the new node at the last of new Linked list
return;
}
// Print the linked list
void printList(struct Node* node) {
if(node == NULL) {
cout<<"Empty List!!!";
return;
}
while (node != NULL) {
cout << node->item << " ";
node = node->next;
}
}
// Driver program
int main() {
struct Node* head = NULL; // head of the linked list
insert(&head, 1); // inserting the elements to the linked list
insert(&head, 2);
insert(&head, 4);
insert(&head, 5);
insert(&head, 8);
insert(&head, 3);
insert(&head, 12);
insert(&head, 9);
insert(&head, 6);
insert(&head, 15);
insert(&head, 10);
cout << "Linked list: ";
printList(head); // printing the inital linked list
cout<<endl;
int d;
cout << "Enter the value of d : "; // user input for d
cin >>d;
cout<<endl;
struct Node* newList = divisibleBy(&head, d); // calling the divisibleBy method
cout <<"New Linked list : ";
printList(newList);
}
To know more about C++ Code visit:
https://brainly.com/question/17544466
#SPJ4
the processing is done in the
Answers
Answer:
CPU Central Processing Unit
Answer:
CPU.... I'm not sure but it might be right or can u put the full question because it sorta don't make any sense
2. Say whether these sentences are True or False. a. Input is the set of instructions given to a computer to change data into information. the form of words numbers, pictures, sounds .it is true or false
Answers
Answer:
I think it is false bcz the set of instruction given to computer is program.
Why is ROM used for in modern computers?
Answers
Answer:
Because ROM saves even after the computer is turned off
Explanation:
RAM doesnt function when the computer is off, ROM does.
A collection of wiress connecting the CPU with main memory that is used to identify particular location is called
Answers
Answer:
Address buses are made up of a collection of wires connecting the CPU with main memory that is used to identify particular locations (addresses) in main memory. The width of the address bus (that is, the number of wires) determines how many unique memory locations can be addressed.
Explanation:
Address buses are made up of a collection of wires connecting the CPU with main memory that is used to identify particular locations (addresses) in main memory.
What is CPU?
The electronic equipment that carries out the instructions included in a computer program is known as a central processing unit (CPU), sometimes known as a central processor, main processor, or simply processor.
The CPU executes fundamental mathematical, logical, controlling, and input/output (I/O) activities as directed by the program's instructions. In contrast, specialized processors like graphics processing units and external components like main memory and I/O circuitry (GPUs).
Although CPUs' shape, design, and implementation have evolved throughout time, their basic function has remained mostly same. The arithmetic-logic unit (ALU), which performs arithmetic and logic operations, processor registers.
Therefore, Address buses are made up of a collection of wires connecting the CPU with main memory that is used to identify particular locations (addresses) in main memory.
To learn more about CPU, refer to the link:
https://brainly.com/question/16254036
#SPJ5
Rate these 3 fnaf characters from 1-3 tell me who you find the scariest as well
MICHEAL AFTON CIRCUS BABY GOLDEN FREDDY
Answers
Answer:
Golden Freddy is the scariest in my opinion
Answer:
Micheal Afton=3/3
Circus Baby=3-3
Golden Freddy=2/3
In my opinion, I'd say Circus Baby because of how her voice sounds like.
Genghis wants to develop a new application that requires a database. He does not, however, want to be responsible for managing the patching and security of the operating system for yet another server. Which of the following would best serve his needs? a. SaaS b. DaaS c. IaaS d. PaaS
Answers
Since Genghis wants to develop a new application that requires a database, the option that would best serve his needs is option a. SaaS.
What are platforms for SaaS?
SaaS, or "Software as a Service," is an acronym. Customers can access their apps remotely using this type of cloud-hosted software, frequently by purchasing a subscription package. The SaaS platform functions as a crucial component of the technical infrastructure in this situation.
Therefore, A software licensing and delivery strategy known as "software as a service" involves centrally hosting software that is subscriber-basedly licensed. On-demand software and Web-based/Web-hosted software are other names for SaaS.
Learn more about SaaS from
https://brainly.com/question/13615203
#SPJ1
Which of the following is used to make Artificial intelligence and Machine Learning possible?
a. Oracle b. PyTorch c. TensorFlow.js
Answers
One of the popular tools used in AI and ML is PyTorch, which is indicated in option b. PyTorch is a deep learning framework that provides a wide range of functions and capabilities to build and train neural networks.
Artificial intelligence (AI) and machine learning (ML) are made possible through the use of various tools and frameworks. One of the popular tools used in AI and ML is PyTorch, which is indicated in option b. PyTorch is a deep learning framework that provides a wide range of functions and capabilities to build and train neural networks. It offers a flexible and intuitive interface for researchers and developers to experiment and implement their models.
Another tool mentioned in the options is TensorFlow.js, which is indicated in option c. TensorFlow.js is a JavaScript library that allows developers to run machine learning models in the browser or on Node.js. It provides a way to deploy and execute models on a variety of platforms, making it convenient for web-based applications or environments where JavaScript is the primary programming language.
Oracle, indicated in option a, is not typically used directly for building AI or ML models. However, Oracle does offer various technologies and services that can be utilized in AI and ML projects. For example, Oracle provides databases and cloud infrastructure that can support the storage and processing of large amounts of data used in AI and ML.
In summary, PyTorch and TensorFlow.js are commonly used tools for building AI and ML models. While Oracle may not be directly used for AI or ML model development, it does offer technologies and services that can support these projects.
To know mor about framework visit:
https://brainly.com/question/32085910
#SPJ11
Someone calls you and gives you a phone number. You don't have any paper or pencil to write the number down so you repeat the number until you are able to write it down. This is an example of
Answers
Someone calls you and gives you a phone number. You don't have any paper or pencil to write the number down so you repeat the number until you are able to write it down. This is an example of rehearsal.
What is practice session learning?A practice session approach makes use of repeated exercise of statistics to analyze it. When a pupil is supplied with unique statistics to be learned, together with a list, regularly he's going to try to memorize the statistics via way of means of repeating it over and over.
The definition of a practice session is an exercise consultation or exercise overall performance completed previous to a actual occasion or earlier than viewing via way of means of an audience. When actors who're set on a play get collectively each day to move over their strains and plan out how the play could be performed, those exercise periods are an instance of a practice session.Read more bout the practice:
https://brainly.com/question/12555695
#SPJ1
In the data view of SPSS, each row shows the values of the same
variable, while each column shows the values of the same
observation (consumer, survey respondent, salesperson, etc).
True
False
Answers
False. In the data view of SPSS (Statistical Package for the Social Sciences), each row represents a separate observation (e.g., individual, respondent, case) in the dataset, while each column represents a variable.
Typically, a dataset in SPSS consists of multiple variables that capture different aspects of the observations. For example, if you have survey data on consumer preferences, each row would represent a different respondent, and each column would represent a different variable, such as age, gender, income, and product preference.
By organizing the data in this way, SPSS allows for easy analysis and manipulation of the dataset. Researchers can apply various statistical procedures, run tests, generate descriptive statistics, and explore relationships between variables.
It's essential to understand the structure of the data view in SPSS to correctly input, manage, and analyze data. Remember, each row represents a different observation, and each column represents a different variable.
This organization facilitates data analysis and ensures accurate interpretation of results.
For more such questions on SPSS,click on
https://brainly.com/question/30929074
#SPJ8
How big of a role does social media play in the mental health of people? Does it do more harm or good? Explain why. in 400 words
Answers
The role that social media play in the mental health of people is big. The use of social media is one that is known to have c positive effects for example connecting people, giving a platform for self-expression, and others.
What is the role that social media?The key bad impacts of social media on mental health is one that is known to have the potential for addiction. Social media platforms are said to be set up to be a form of engaging, which can result to individuals spending excessive amounts of time going through their feeds and this may lead to depression.
Hence the negative impact of social media on mental health is the one that can also lead to cyberbullying that is Online harassment.
Learn more about role that social media from
https://brainly.com/question/1163631
#SPJ1
When attaching a file or files in outlook 365 you select the attach command and then select the files location
Answers
Answer:
When you click the attachment button a window pops up allowing you to select the file/s you want to upload
You can also drag and drop file/s this is an alternative method
Explanation:
Microsoft Outlook is a personal information manager software system from Microsoft.
Though primarily an email client, Outlook also includes such functions as calendaring, task managing, contact managing, note-taking, journal logging, and web browsing. Wikipedia
What do you like least about coding in python?