Which of these plays an important role in keeping attack traffic off your systems and helps to protect users? Check all that apply.
Antivirus software
Antimalaware measures
Answers
Antivirus software and antimalware measures both play important roles in keeping attack traffic off your systems and help protect users. They work together to detect, prevent, and remove various types of malicious software, ensuring the security of your devices and data.
Antivirus software and antimalware measures are both designed to protect your devices and data from malicious software, such as viruses, spyware, and other types of malwares.
Antivirus software specifically focuses on detecting and removing viruses and other types of malicious software that are known to be harmful to your system. It typically works by scanning files and programs on your device to check for signs of infection and then removing any threats that are found.
Antimalware measures are a broader category of software tools and techniques that are designed to protect against a wide range of malicious software threats. This can include viruses, spyware, adware, and other types of malware that may be more difficult to detect and remove than traditional viruses.
Some common antimalware measures include firewalls, which can help block malicious traffic from entering your network, and intrusion detection and prevention systems, which can help detect and prevent attacks before they cause damage.
Together, antivirus software and antimalware measures provide a multi-layered defense against malicious software threats. By working together to detect, prevent, and remove malicious software, they help keep your devices and data safe from harm.
Know more about the Antivirus software click here:
https://brainly.com/question/17209742
#SPJ11
Related Questions
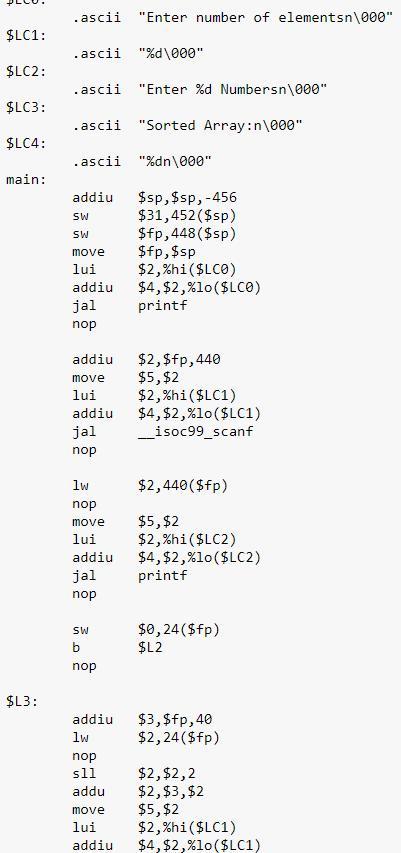
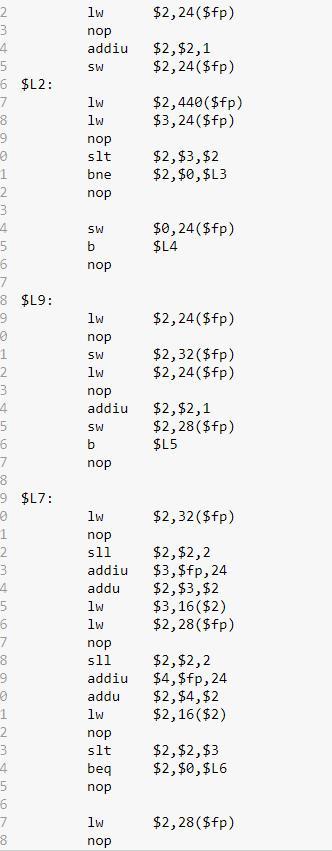
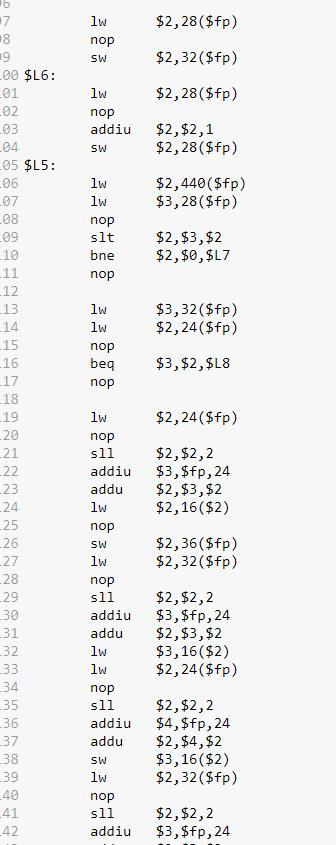
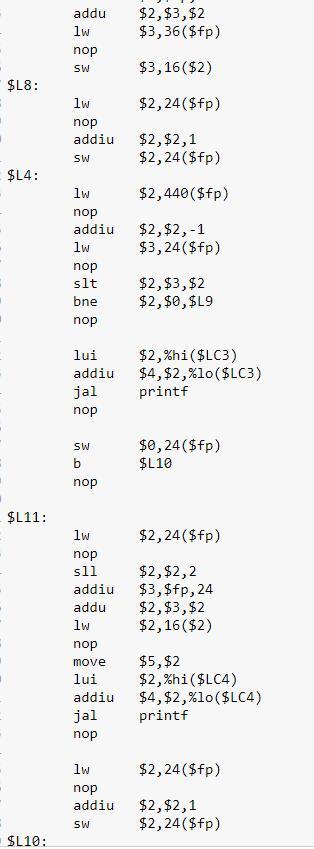
Need a Mips program for Selection sort.
Declare array, ask for values from user, and insert values into array
Run two for loops: outer loop start will with zero, will run the length of [values – 1] overall and will increment with each loop run, inner loop will start with [outer loop’s position + 1], run until the length of all of the values and increment with each loop run.
Declare a variable min to store the minimum value. Min is equal to outer loop’s value
Inner loop will have two functions:
IF function – compares the current value of the inner loop with the current value of the outer loop. If inner loop value is greater than outer loop value, min value is the current value
Swapping elements – use a temp variable to swap the new min with the value of the first element
Print array
Answers
A Unix text file with many lines that contains a MIPS Assembly program. Each line is formatted generally with labels, instructions, and comments. All three of these elements—labels, instructions, and comments—are optional; a line may have all three, any two, anyone, or none at all.
The MIPS program has been provided and attached below:
$LC0:
.ascii "Enter the number of elementsn\000"
$LC1:
.ascii "%d\000"
$LC2:
.ascii "Enter %d Numbersn\000"
$LC3:
.ascii "Sorted Array:n\000"
$LC4:
.ascii "%dn\000"
main:
addiu $sp,$sp,-456
sw $31,452($sp)
sw $fp,448($sp)
move $fp,$sp
lui $2,%hi($LC0)
addiu $4,$2,%lo($LC0)
jal printf
nop
addiu $2,$fp,440
move $5,$2
lui $2,%hi($LC1)
addiu $4,$2,%lo($LC1)
jal __isoc99_scanf
nop
lw $2,440($fp)
nop
move $5,$2
lui $2,%hi($LC2)
addiu $4,$2,%lo($LC2)
jal printf
nop
sw $0,24($fp)
b $L2
nop
The MIPS processor's assembly language is known as the MIPS assembly language. Microprocessor without Interlocked Pipeline Stages, or MIPS, is the abbreviation for this phrase. MIPS Technologies is a company that created the reduced-instruction set architecture.
Because so many embedded systems use the MIPS processor, learning the MIPS assembly language is tremendously beneficial. A fuller grasp of how these systems work may be gained by learning to code in this language.
Learn more about MIPS programming here:
https://brainly.com/question/14949519
#SPJ4
What do Cc and Bcc stand for?
O Clear Copy and Binary Clear Copy
O Counter Claim and Best Counter Claim
O Crystal Clear and Binary Crystal Clear
O Carbon Copy and Blind Carbon Copy
Answers
Thank You!
Who is the intended audience of a pseudocode document?
Answers
Answer and Example:
Pseudocode is an artificial and informal language that helps programmers develop algorithms.
Pseudocode is a "text-based" detail (algorithmic) design tool. The rules of Pseudocode are reasonably straightforward. All statements showing "dependency" are to be indented.
Pseudocode is understood by the programmers of all types. it enables the programmer to concentrate only on the algorithm part of the code development.
Java would use this.
As government debt increases, Group of answer choices Congress will reduce spending by an equal proportion. the government must spend more revenue on interest payments. a trade-off with government deficits is inevitable. tax rates must rise to cover the deficit.
Answers
As government debt increases, the government must spend more revenue on interest payments.
As government debt increases, the government is required to allocate more of its revenue towards servicing the interest on that debt. This means that a larger portion of the government's budget will be dedicated to making interest payments, reducing the available funds for other purposes such as public services, infrastructure development, or social programs. The increase in interest payments can put a strain on the government's financial resources and limit its ability to address other pressing needs.
When a government incurs debt, it typically borrows money by issuing bonds or securities to investors. These investors expect to receive interest payments as compensation for lending their funds to the government. As the debt accumulates, the government's interest obligations increase. Therefore, a growing portion of the government's budget must be allocated to interest payments, which can crowd out other areas of spending.
Learn more about interest payments here:
https://brainly.com/question/30408540
#SPJ11
how to add an excel formula to count every item added to inventory list and show the number of total number
Answers
To add an Excel formula to count every item in an inventory list and display the total number, you can use the COUNT or COUNTA functions.
To use COUNT for numerical values, enter this formula in an empty cell: =COUNT(range), where "range" represents the cells containing your inventory items.
For example, if your inventory list is in cells A1:A50, the formula would be =COUNT(A1:A50).
If your inventory list contains text, use COUNTA: =COUNTA(range).
For the same range as above, the formula would be =COUNTA(A1:A50).
These functions will calculate the total number of items in your inventory list, providing an accurate and efficient way to track your stock.
Learn more about Excel formula at
https://brainly.com/question/30324226
#SPJ11
Different countries in the world have launched their own navigation system why
Answers
Answer:
China, the European Union, Japan and Russia have their own global or regional navigation systems to rival GPS
Answer: The reason other countries made their own id because they don't trust the U.S the U.S gps listens to you talk and tracks you.
Explanation: Please give brainlist.
Hope this helps!!!!
Which computer component converts high-voltage AC current to low-voltage DC current?
speakers
power supply
motherboard
cooling unit
Answers
Answer:
Power supply
Explanation:
A Power supply unit (or PSU) converts high AC current to low-voltage regulated DC current for the internal components of a computer.
Now a days personal computers universally use switched-mode power supplies.
Some of the power supplies have a manual switch for selecting input voltage, while modern computers automatically adapt to the mains voltage.
Answer:
power supply
Explanation:
As the complexity of a network increases, the possibility of security breaches decreases.
Answers
False. As the complexity of a network increases, the possibility of security breaches can actually increase. Complexity often means more points of entry for malicious actors.
The Security Challenges of High Level NetworksOne of the main concerns regarding the security of high-level networks is the possibility of denial of service attacks. These attacks are performed when hackers bombard a server with malicious traffic to disrupt service for legitimate users.
Another security challenge for high-level networks is the possibility of infiltration attacks. This occurs when an attacker breaks into the system and accesses confidential or sensitive information.
High-end network security challenges also include the threat of viruses and malware:
Viruses can spread through the network and cause harm to end users. Malware can also be used to steal information, spy on users, or even control their computers.Learn more about High Level Network Security:
https://brainly.com/question/28581015
#SPJ4
which cellular network type can, theoretically, provide speeds up to 10gbps?
Answers
The cellular network type that can theoretically provide speeds up to 10Gbps is 5G.
5G, the fifth generation of cellular network technology, has the potential to deliver speeds up to 10Gbps (gigabits per second) in ideal conditions. This is a significant improvement over the previous generation, 4G LTE, which typically offers speeds in the range of 100Mbps to 1Gbps.
5G achieves these high speeds through the use of advanced technologies such as millimeter wave (mmWave) frequencies and massive multiple-input multiple-output (MIMO) antenna systems. MmWave frequencies have a larger bandwidth available, allowing for faster data transmission. Massive MIMO utilizes a large number of antennas to enhance capacity and improve network performance.
In addition to speed, 5G offers lower latency, which means there is less delay in data transmission, resulting in a more responsive network. This is especially crucial for applications like real-time gaming, autonomous vehicles, and remote surgeries, where even milliseconds of delay can have a significant impact.
However, it's important to note that the actual speeds experienced by users on a 5G network can vary depending on several factors. These factors include the distance from the cell tower, network congestion, signal interference, and the device being used. Additionally, the highest speeds are typically achieved in densely populated urban areas with extensive 5G infrastructure.
Learn more about Cellular network
brainly.com/question/32896643
#SPJ11
Using cell references enter a formula in B6 to calculate monthly payments for the loan described in this worksheet Omit the optional arguement use a negative value for pv
Answers
Answer:
= PMT(B4/B2, B2 * B3, B1)
Explanation:
The syntax to use is:
= PMT(Rate,NPER, PV)
To answer this question, the following assumptions will be made.
B1 = Present Value i.e. PV
B2 = Number of Payment Period i.e n
B3 = Duration (in years)
B4 = Rate
So, the formula to enter in B6 is:
= PMT(B4/B2, B2 * B3, B1)
The above formula will return the monthly payment in cell B6
suppose a large warehouse has 20% of the items (fast items) contributing to 80% of the movement in and out, and the other 80% of the items (slow items) contributing to the remaining 20% of the movement. which storage policy would you recommend? (check all answers) group of answer choices class-based storage policy for fast and random policy storage for slow dedicated storage policy for fast and slow class-based storage policy for fast and slow random storage policy for fast and random policy storage for slow dedicated storage policy for fast and random policy storage for slow
Answers
Based on the given information, a recommended storage policy would be a class-based storage policy for fast items and a random storage policy for slow items.
Since the fast items are responsible for 80% of the movement in and out of the warehouse, it would be beneficial to have them stored together in a designated area, such as a specific aisle or section of the warehouse. This would allow for faster and more efficient picking and replenishment processes, as well as potentially reducing the risk of errors or misplacements.
On the other hand, since the slow items only contribute to 20% of the movement, a random storage policy would be more suitable for them. This means that they can be stored in any available location throughout the warehouse, without being grouped together based on any specific criteria. This allows for more flexible use of the warehouse space and can potentially reduce the amount of time spent searching for specific items.
Alternatively, a dedicated storage policy for fast and slow items could also be considered. This would involve having separate areas or even separate warehouses for the two types of items. However, this approach may not be as cost-effective or practical for all warehouses.
Overall, the storage policy chosen should aim to optimize the efficiency and productivity of the warehouse, while also taking into account the specific characteristics and demands of the items being stored.
For such more question on dedicated
https://brainly.com/question/38521
#SPJ11
3. Describe at least THREE different kinds of networks present in your house or school and what devices are connected through each network. Which network do you personally use the most, and why? Should you be concerned about cybersecurity for that network?
Answers
Answer:
There are various networks in a typical house or school, including wired, wireless, and internet networks. Wired networks are used to connect devices such as desktop computers, printers, and servers using Ethernet cables. The wireless network connects devices such as laptops, smartphones, and tablets through a Wi-Fi signal. The internet network is used to connect to the internet, allowing devices to communicate and exchange data over the World Wide Web. I personally use the wireless network the most as it is the most convenient for my smartphone and laptop. Cybersecurity is a concern for all networks, especially for wireless networks as they are susceptible to hacking and unauthorized access. Therefore, it is crucial to use strong passwords, update software regularly, and limit access to the network to ensure cybersecurity.
How can you ensure that your internet search is happening over a secure network connection?.
Answers
A person can you ensure that your internet search is happening over a secure network connection by the use of:
By Renaming your Routers and Networks.The use of a strong passwords.Do Turn on encryption.The use of multiple firewalls.What is secure network connection?A secure connection is known to be a kind of a connection that is known to be one that is often encrypted by the use of a single or a lot of security protocols to make sure that the security of data that is known to be passing between two or more nodes.
Therefore, based on the above scenario, A person can you ensure that your internet search is happening over a secure network connection by the use of:
By Renaming your Routers and Networks.The use of a strong passwords.Do Turn on encryption.The use of multiple firewalls.Learn more about internet search from
https://brainly.com/question/20850124
#SPJ1
How are computer networks connected?
Answers
Answer:Computer networks connect nodes like computers, routers, and switches using cables, fiber optics, or wireless signals. These connections allow devices in a network to communicate and share information and resources. Networks follow protocols, which define how communications are sent and received.
Explanation.
hope this helped you find what your looking for
Which one of the following Python statements can be used to create the dataframe x ? Dataframe x :
A
a
NaN
b
NaN
c
NaN
alpha vantage pd. DataFrame(index =[ ' A '] , columns =[ ' a ', ' b ', ' c ' ] ) pd.DataFrame(index =[
′
a
′
,
′
', ' 'c' ], columns='A') pd.DataFrame(index =[ ' a ', ' b ', ' c ' ], columns =[
′
A
′
])
Answers
The correct statement to create the dataframe x is:
```python
x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])
The above code uses the pandas library in Python to create a dataframe named x. The `pd.DataFrame()` function is used to create the dataframe, with the specified index and columns. The `index` parameter specifies the row labels of the dataframe, while the `columns` parameter specifies the column labels. In this case, the index is set to ['A'] and the columns are set to ['a', 'b', 'c']. The values of the dataframe are set to NaN (Not a Number) for all the cells.To create the dataframe x with the specified structure, you can use the following Python statement: `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This statement uses the pandas library, which provides high-performance data manipulation and analysis tools. The `pd.DataFrame()` function is a constructor for creating dataframes in pandas. In this case, the `index` parameter is set to `['A']`, which specifies the row label for the dataframe. The `columns` parameter is set to `['a', 'b', 'c']`, which specifies the column labels for the dataframe. The resulting dataframe, x, will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c'. All the cells in the dataframe will have NaN (Not a Number) as their values. NaN is a special floating-point value that represents missing or undefined data. It is commonly used in data analysis to indicate the absence of a value. By creating the dataframe x using the specified index and columns, you can easily access and manipulate the data stored in the dataframe for further analysis and processing. To create the dataframe x with the specified structure, you can use the statement `x = pd.DataFrame(index=['A'], columns=['a', 'b', 'c'])`. This code utilizes the pandas library to construct the dataframe, specifying the row and column labels. The resulting dataframe will have one row labeled 'A' and three columns labeled 'a', 'b', and 'c', with NaN as the value for each cell. NaN is a special value used to represent missing or undefined data. Creating the dataframe in this way allows for easy data manipulation and analysis using the pandas library.
To know more about Dataframe , Visit:
https://brainly.com/question/32136657
#SPJ11
The first time you save a file, there is no difference between the Blank Space __________ and Save As commands.
Answers
I think the answer is save.
Hope that helps!
ok i need help my xdox one is making speaking noises even when its turned off what can i do?
Answers
Explanation:
that shi fkn possessed sell that h.o
HELP!!
A delivery of information from one person—or a small team of people—to an audience is called a ____________.
Question 8 options:
Presentation
Template
Speaker Notes
Slide Show Toolbar
Answers
Answer:
Presentation
Explanation:
Information is being presented to an audience (this makes sense).
A template can be used to organize the information that is to be given to the audience.
Speaker notes only help the speaker give the information to the audience.
Slide how toolbar is only for creating the slideshow that can be used to help the audience understand what the speaker is saying.
What is the process to correct a single spelling mistake that has been indicated by the spelling checker in PowerPoint Online?
Select the word, then double click.
Select the word, then left select.
Select the word, then right select.
Select the word, then single click.
YOU WILL GET BRAINLIEST FIRST PERSON IF RIGHT
Answers
Answer:
C!
Mark me as brainliest!!
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
When a television is turned on, it converts electrical energy into many other forms of energy. Which set of words correctly lists most of these forms?.
Answers
Light, sound, and heat comprise the group of words that accurately classifies the majority of these forms.
Describe energy.There are many different energy forms in the environment. These energies consist of kinetic, potential, and gravitational forces. Kinetic energy is created by converting the collected potential energy.
The action is carried out using kinetic energy. the energy that is converted into kinetic energy when work is completed. Other types of energy include light and heat.
Televisions are electronic devices with screens that show a variety of moving objects. The television therefore displays heat, sound, and light. It is powered by electricity, which is transformed into heat, sound, and light.
To know more about electrical energy visit:-
https://brainly.com/question/13077484
#SPJ4
I know how to do this but I'm struggling to make it appear on the screen am I doing it right? If I am please tell me that if not please tell me and explain to me how to do it also help me to understand by explaining it to me what I'm doing wrong so that in the future I will never ever make this mistake again.
Answers
Answer:
maybe you should try to copy the image then paste it, or save it to your files then go into your files and add it
Explanation:
Which mode would you use to take a photograph inside a cave in dim light?
A.
program mode
B.
aperture priority mode
C.
auto mode
D.
night mode
E.
sports mode
Answers
Answer:
I think B or A because when you go in a dark place you can use this
Answer:
D. Night Mode.
Explanation:
I am not 100% sure but it seems like since you are in a cave in dim light it would be like at night with the moon.
Will give brainliest if answered right

Answers
Answer:
control shift u
Explanation:
Answer:
I believe U is the answer.
Hurry please I’ll give Brainliest if you are right

Answers
Answer:
I think kevin?
Explanation:
Where do file name extensions appear?
(Select the best answer.)
O Above the file name
O Below the file name
O At the beginning of the file name
O At the end of the file name
Answers
Answer:
At the end of the file name
Explanation:
For this assignment, you will create a calendar program that allows the user
to enter a day, month, and year in three separate variables as shown below.
Day:
Month:
Year:
Then, your program should ask the user to select from a menu of choices
using this formatting
Menu:
1) Calculate the number of days in the given month.
2) calculate the number of days left in the given year.
I would really appreciate it if someone could help me on this.

Answers
Following are the program to the given question:
Program Explanation:
Defining three methods "leap_year, number_of_days, and days_left " is declared. In the "leap_year" method, it accepts the year variable, which calculates the year is the leap year and returns its value that is 1. In the next method "number_of_days", it is define which accepts the "year and month" variable in the parameter and calculate and returns its value. In the last "days_left" method, it calculates the left days and returns its value, and outside the method, two dictionary variable days_31 and days_30 is declared. It initilized a value by using 3 input variable "day, month, and year" variable which accepts user-input value. In the next step, a "c" variable is declared, that input values and calls and print its value accordingly.Program:
def leap_year(y):#defining a method leap_year that takes one parameter
l= 0#defining l variable that holds an integer
if y % 4 == 0:#using if block that check year value module by 4 equal to 0
l = 1#holding value in l variable
if y % 100 == 0:#using if block that check year value module by 100 equal to 0
l = 0#holding value in l variable
if y % 400 == 0:#using if block that check year value module by 400 equal to 0
l= 1#holding value in l variable
return l#return l value
def number_of_days(m, y):#defining a method number_of_days that takes two parameters
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
l = leap_year(y)#defining l variable that calls leap_year method and holds its value
if l == 1 and m == 2:#use if that check l value equal to 1 and 2
return 29#return value 29
if m == 2:#use if that check month value equal to 2
return 28#return value 29
return months[m]#return months value
def days_left(d, m, y):#defining a method days_left that takes three variable in parameter
l = leap_year(y)#defining l variable that hold leap_year method value
days = 0#defining days variable that hold integer value
months = {1: 31, 3: 31, 4: 30, 5: 31, 6: 30, 7: 31, 8: 31, 9: 30, 10: 31, 11: 30, 12: 31}#defining months variable that hold value in ictionary
if l== 1:#using if that check l equal to 1
if m > 2:#defining if that check m value greater than 2
days += (29 + 31)#using days variable that Calculate holds its value
i = m#defining i variable that holds months value
while i > 2:#defining while loop that checks other days
days += months[i]#defining a days variable that holds months value
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#defining elif block that checks m equal to 2
days += (29 - d) + 31#holding value in days variable
else:#defining else block
days = 31 - d#Calculating days value
return 366 - days#using return keyword that Calculates days value
else:#defining else block
if m > 2:#using if that checks m value greater than 2
days += (28 + 31)#Calculating and store value in days
i = m#holding months value in i
while i > 2:#defining while loop that checks i value greater than 2
days += months[i]#holding list value in days
i -= 1#decreasing i value
days -= (months[m] - d)#defining days that subtracts leap value
elif m == 2:#using elif block that checks m value equal to 2
days += (28 - d) + 31#Calculating and store value in days
else:#defining else block
days = 31 - d##Calculating and store value in days
return 365 - days#return total days
print("Please enter a date")#print message
day = int(input("Day: "))#input value
month = int(input("Month: "))#input value
year = int(input("Year: "))#input value
print("Menu: ")#print message
print("1) Calculate the number of days in the given month.")#print message
print("2) Calculate the number of days left in the given year.")#print message
c = int(input())#input value
if c == 1:#using if that checks c value equal to 1
print(number_of_days(month, year))#calling method and print its return value
elif c == 2:#using if that checks c value equal to 2
print(days_left(day, month, year))#calling method and print its return value
Output:
Please find the attached file.
Learn more:
brainly.com/question/16728668
Output from the print statement is usually written to the ______ in the form of ________
Answers
Answer:
Hope this helps :)
Explanation:
To the *processor* in the form of *binary* (or binary language)
Output from the print statement is usually written to the processor in the form of binary.
What is statement?The term statement was the based on the line are the perfectly in the arranged. The statement was the correct on the said by the famous in the personality. The statement was the line in the correct manner. There was the statement on the give to the situations.
The term “binary” refers to the smallest and minimum two-digit number stored on a computer device. The smallest binary codes are zero (0) and one (1). The use of storing numbers easily. The computer only understands the processor are the print statement.
As a result, the output from the print statement is typically written to the processor in the form of binary.
Learn more about on statement, here:
https://brainly.com/question/2285414
#SPJ2
True or false. The send e-mail feature, listed under tools, will allow you to send an e-mail to your instructor and to fellow students directly from your online course in blackboard.
Answers
Answer:
TRUEExplanation: please mark me brainliest
What is one major reason various industries have adopted the use of automated robotic assembly?.
Answers
The major reason various industries have adopted the use of automated robotic assembly is to increase manufacturing productivity.
What is automated robotic assembly?Automated robotic assembly is the use of automotive technology to operate different areas in the manufacturing industries.
Automated robotics are used to perform the following tasks:welding, assembly,shipping, handling raw materials, andproduct packing.The reason why various industries have adopted the use of automated robotic assembly is that it saves time and there is increase in the amount of products manufactured that when manually handled.
Learn more about automation here:
https://brainly.com/question/11211656