Which of the following is true? Group of answer choices worst case time of Heapsort is better than worst cast time of Quicksort average case time of Quicksort is better than average case time of Heapsort best case time of Quicksort is worse that best case time of Heapsort both a) and b)
Answers
Answer:
Worst case time of Heapsort is better than worst case time of Quicksort.
Explanation:
Worstcase of Heapsort is nlog(n). Worstcase time of Quicksort is (n^2). Heapsort is comparison based sorting algorithm. Heapsort divides input into sorting. It is a selection sort in which we send maximum inputs for maximum elements at end. Quicksort is divide and conquer algorithm. It is considered as efficient sourcing algorithm.
Related Questions
Need answer quick
In windows, the desktop is simply a folder that resides in your main user folder.
true or false?
Answers
Answer:
true
Explanation:
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
3X5
0
Problem 12:
Write a function problemi_2(x,y) that prints the sum and product of the
numbers x and y on separate Lines, the sum printing first.
Nam
RAN
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
def problemi_2(x,y):
X es 2
In
y en 5
print()
print("* + y
print("* * y
In
Trac
Fi
Name
In [C
Answers
Answer:
15
Explanation:
cause when you multiply three by five it will give u 15
You have been called in to consult on a new network design for CNT Books. The requirements of this design are summarized as follows: The building has three floors. There are 300 user workstations and 10 servers. Users must be grouped according to the projects they’re working on, but the users for each project are located on all three floors. There must be fault tolerance for communicating between the floors. >What features would you look for on the switches you purchase for this design? Explain why you would want each feature. Do you need to include any other devices in this design? Write a memo to me as if I were you boss with the answers to these questions and explain your choices.
Answers
Note that the Memo for the above scenario is given below.
What is a Memo that answers the above questions?The sample memo is given as follows:
Memo
To: [Your Boss]
Subject: Network Design for CNT Books
Based on the requirements for the new network design for CNT Books, the following features should be considered when purchasing switches:
VLANs - To group users based on their projects and segregate their network traffic to improve network performance and security.
Quality of Service (QoS) - To prioritize traffic and ensure that critical traffic, such as VoIP or video conferencing, receives higher priority over other traffic.
Link Aggregation Control Protocol (LACP) - To bundle multiple physical links between switches to increase bandwidth and provide redundancy in case of link failure.
Spanning Tree Protocol (STP) - To prevent network loops and ensure redundancy without causing broadcast storms.
Layer 3 routing - To route traffic between VLANs and provide fault tolerance for communicating between floors.
In addition to switches, it is recommended to include routers to provide inter-VLAN routing and connect the network to the internet. It is also recommended to include firewalls to provide network security.
Please let me know if you have any questions or concerns.
Best regards,
[Your Name]
Learn more about IT Memos at:
https://brainly.com/question/25130307
#SPJ1
Drag each label to the correct location on the table.
Match the correct features to virtualization and cloud computing.
allows multiple operating systems
to run on a single machine
consolidates hardware devices into
a physical server
allows users to access data from anywhere
includes services such as platform
as a service and desktop as a service
uses a hypervisor that can be type 1 or type 2
allows users to run software applications
on web browsers without installing
the application locally
Answers
Match the correct features to virtualization and cloud computing is allows multiple operating systems to consolidates hardware and uses a hypervisor to allows users to access
Divide the statement in virtualization and cloud computing ?
sing virtualization, different operating systems can operate on a single machine using a type 1 or type 2 hypervisor.
Users can access data from anywhere using cloud computing, which combines hardware devices into a physical server and offers services like platform as a service and desktop as a service. Users can execute software applications on web browsers without having to install them locally.
Know more about virtualization Visit:
brainly.com/question/31037702
#SPJ1
Which graphics element loads faster when used with text or audio on a web page?
Answers
Answer:
A slideshow uses still images that shift through a desired orderThe graphical user interface (GUI) was pioneered in the mid-1970s by researchers at:
A) Apple Computer
B) Microsoft
C) Xerox
D) IBM
Answers
Answer:
its C actually
Explanation:
C) Xerox plus i had a quiz
Answer:
xerox
Explanation:
Which is a conditional statement?
If it is sunny, we can play ball.
It is sunny today.
It is sunny or rainy.
It is sunny across the street, but not sunny here.
Answers
Answer:
it is 1, I know this because i got 100% on my quiz
Explanation:
Your agile team only has one database developer. So the other developers finish their tasks and then wait for their work to be Integrated into the database. This creates a backup for the database developer. But it also means that the other developers must either wait or add to a growing pile of database work. What's one possible solution to this challenge?
Answers
Members of an Agile development team often agrees on what tasks to work on and they do it together. The one possible solution to this challenge is to Have the database developer train the rest of the team so there are fewer handoffs.
Agile development team often works together as a team. They as team discuss the task yo take, when it will take place etc.
This team is all about communication, teamwork, problem-solving etc.
Conclusively, A task should be completed by one member on the team, but the team may choose to pair up when doing the work.
Learn more from
https://brainly.com/question/24383225
See full question below:
Your agile team only has one person who knows how to develop database software. So the other developers finish their tasks and then wait for their work to be Integrated into the database. This creates a pile of backed up work for the database developer. But it also means that the other developers must either wait or add to the growing pile of database work. What's one possible solution to this challenge?
Select an answer:
Have the database developer train the rest of the team so there are fewer handoffs.
Have the software developers split their time between other teams so they're not as productive
Encourage the database developer to work overtime to catch up with their work.
Create a large batch of work so the database developer can focus on finishing
You work as a network administrator for a company with 100 employees. Your company need all the employees should have a separate computer and connected to the network. (a) What is the smallest size address block that can support the all the 100 computers servers and routers in your perimeter network? (Express the network size in slash notation and dotted-decimal notation.) (b) You have decided to deploy three new servers in the perimeter network and assign them each a public IP address. If your provider sells addresses in blocks only, what size block should you request to enable you to host all of your public servers on a single subnet?(c) Are the IPv4 address 192.158.1.14 and 192.158.1.127 on the same subnet? Both have a subnet mask of 255.255.255.0
Answers
Answer:
gdghfhffhgcgchchghvb. bvhvhhvhvhgcgfhsufsjtstjsfsfshrs
Which of the following guidelines about the subject line of e-mail messages is most appropriate?
1: Avoid using a subject line unless the e-mail is very important.
2: Use the subject line wisely to let your reader know the main purpose of the e-mail.
3: Try to keep the subject line very short, such as just one or two words.
4: Make sure you provide all the details in the subject line in case the receiver does not have time to read the whole e-mail.
Answers
Answer: 2: Use the subject line wisely to let your reader know the main purpose of the e-mail.
============================================================
Explanation:
The subject line is like the title of a book. You want to give a quick sense of what the email is about, but you also don't want to put the entire contents of the book in the title. The subject line only has so much room. Even less room is available if the reader is checking their email on their mobile device.
Choice 1 is false because subject lines are important. I can't think of a case where you can omit the subject line entirely (ie leave it blank), unless it's a situation where the recipient knows in advance what the topic is about. Though that may be rare.
Choice 3 is false. Yes you want to keep the subject line short, but you also don't want to be cryptic or confusing. If you can get away with using 1 or 2 words, then go ahead and do so. However, you may need more words to convey the topic of the email. Go with what feels right and try to put yourself in the shoes of the person reading your email. Ask yourself "Does this convey the message I want to send?"
Choice 4 is false. As mentioned, you do not want to put the entire email in the subject line. The exception of this rule is that if the email is really really short. For every other case, you should have a fairly short title and then go over the details in the email main body itself.
Answer:
Use the subject line wisely to let your reader know the main purpose of the e-mail.
Explanation:
i got it right on edge 2021
In recent years there has been a trend to represent traditional relational data in a semi structured data format such as XML.
a) List and explain three of the main motivations for this trend over recent years.
b) State an application and explain why the stated application warrants the need to store and process semi-structured data.
c) Explain the support required for storing semi-structured data in a relational database
d) Discuss the performance implications for retrieving a particular XML element from a XML file.
(Advanced Database Systems Course)
Answers
a) Three main motivations for representing traditional relational data in a semi-structured data format such as XML in recent years include:
Flexibility: XML is a flexible data format that allows for the representation of complex data structures, such as hierarchical or nested relationships, that are difficult to represent in a traditional tabular format.Interoperability: XML is a widely-supported data format that is used by many different systems and applications, making it easy to exchange data between different platforms.Extensibility: XML allows for the creation of custom tags and attributes, making it easy to add new information to a data structure without changing its overall structure.What are the others about?b) One application that warrants the need to store and process semi-structured data is a content management system (CMS). A CMS is a system used to create, edit, and manage digital content, such as websites or online documents. Because digital content can be highly varied and complex, a CMS must be able to handle a wide range of data types and structures. Using a semi-structured data format like XML allows a CMS to represent and manage this complex data in a flexible and extensible way.
c) In order to store semi-structured data in a relational database, the database must have support for storing and manipulating XML data. This may involve adding specific data types for storing XML documents or elements, as well as supporting functions and operators for querying and manipulating XML data.
Lastly d) Retrieving a particular XML element from a XML file can have performance implications, especially if the file is large or the element is deeply nested within the file's structure. To optimize performance, it may be necessary to index the XML data in order to speed up element retrieval, or to use specialized XML processing tools that are optimized for this task. Additionally, the use of a database system that has built-in support for handling XML data can also help to improve performance when working with semi-structured data.
Learn more about relational data from
https://brainly.com/question/13262352
#SPJ1
lan is working on a project report that will go through multiple rounds of
revisions. He decides to establish a file labeling system to help keep track of
the different versions. He labels the original document
ProjectReport_v1.docx. How should he label the next version of the
document?
A. ProjectReport_revised.docx
B. ProjectReport_v1_v2.docx
C. Report_v2.docx
D. ProjectReport_v2.docx
Answers
Answer:It’s D
Explanation:
APEVX
The label of the next version of the document can probably be ProjectReport_v2.docx. The correct option is D.
What is a document?A document's purpose is to enable the transmission of information from its author to its readers.
It is the author's responsibility to design the document so that the information contained within it can be interpreted correctly and efficiently. To accomplish this, the author can employ a variety of stylistic tools.
Documentation can be of two main types namely, products and processes. Product documentation describes the product under development and provides instructions on how to use it.
A document file name is the name given to a document's electronic file copy.
The file name of the document does not have to be the same as the name of the document itself. In fact, you can use the shortest possible version of the name.
As the document here is second version of the previous one, so its name should be ProjectReport_v2.docx.
Thus, the correct option is D.
For more details regarding document, visit:
https://brainly.com/question/27396650
#SPJ2
program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
According to shared security model, which two are a customer's responsibilities in Oracle Cloud Infrastructure (OCI)?
Answers
Answer:
According to shared security model, a customer's responsibilities in Oracle Cloud Infrastructure (OCI) are:
1. Workloads security: The customer is responsible for protecting the work function or a distinct capacity, like a Hadoop node, a Web server, a database, or a container, that it puts on the cloud.
2. Services configuration: The customer is also responsible for securing the specifications that describe the different aspects of its managed service.
Explanation:
Responsibilities are shared between Oracle and the customers using the Oracle Cloud Infrastructure (OCI). Oracle is solely responsible for the security of the underlying cloud infrastructure (such as data-center facilities, hardware, and software systems), while the customer is responsible for securing the workloads and configuring their services to suit their individual needs.
explain the structure of c program with example
Answers
Answer:
A C program typically consists of a number of components, including preprocessor directives, function prototypes, global variables, functions, and a main function.
Explanation:
Here's an explanation of each component, followed by an example C program that demonstrates their usage:
Preprocessor Directives: Preprocessor directives are instructions to the C preprocessor, which processes the source code before compilation. They usually start with a '#' symbol. Some common directives are #include for including header files and #define for defining constants.
Function Prototypes: Function prototypes provide a declaration of functions that will be used in the program. They specify the function's name, return type, and the types of its parameters.
Global Variables: Global variables are variables that can be accessed by any function in the program. They are usually defined outside of any function.
Functions: Functions are blocks of code that can be called by name to perform specific tasks. They can accept input parameters and return a value. Functions are generally declared before the main function.
Main Function: The main function is the entry point of the program. It's where the execution starts and ends. It has a return type of int and typically takes command-line arguments via two parameters: argc (argument count) and argv (argument vector).
Here's an example C program that demonstrates the structure:
// Preprocessor directives
#include <stdio.h>
// Function prototypes
void print_hello_world(void);
// Global variable
int global_var = 10;
// Functions
void print_hello_world(void) {
printf("Hello, World!\n");
}
// Main function
int main(int argc, char *argv[]) {
// Local variable
int local_var = 20;
printf("Global variable value: %d\n", global_var);
printf("Local variable value: %d\n", local_var);
print_hello_world();
return 0;
}
This simple C program demonstrates the use of preprocessor directives, a function prototype, a global variable, a function, and the main function. When run, it prints the values of a global and a local variable, followed by "Hello, World!".
Lily is in her first year of undergraduate coursework and has not yet declared a major. She has attended a lot of career fairs and undergraduate major "open house" events to investigate her options. Marcia's theory of identity status suggests that the dimension Lily is most concerned with is the_____of 1 dimension.
Answers
Answer:
exploration
Explanation:
According to Marcia's theory of identity, the status suggests that the dimension Lily is most concerned with is the exploration dimension.
James E. Marcia who came up with the Marcia's theory of identity is a clinical and developmental psychologist. He also once taught at Simon Fraser University which is located in British Columbia, Canada and also in the State University of New York at Buffalo in Upstate, New York City.
James E. Marcia is also very much involved in clinical private practice, community consultation, clinical psychology supervision, and also in international clinical-developmental research and teaching.
If you are having trouble playing back a presentation smoothly, what should you try?
Answers
If a user has trouble playing back a presentation smoothly, the options are;
1. Copy the presentation to your internal hard drive.
2. Clear the Disable hardware graphics acceleration option.
3. Lastly, select the Show without animation option.
Microsoft PowerPoint is an application that can be used for presentations in offices, schools and other meetings. The issue of playback could occur when we want to replay a presentation but encounter difficulties along the way. To resolve the problem, each of the three steps above can be followed.
The particular presentation with the issue should be copied to the internal hard drive. Remove the option: Disable hardware graphics acceleration. Finally, select the option to play the presentation without animation.
Conclusively, the three listed options above, should be followed to resolve the problem of playing back a presentation smoothly.
Learn more about Microsoft PowerPoint presentations here:
https://brainly.com/question/24079115
5.19 LAB: Countdown until matching digits
PYTHON: Write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.

Answers
Using the knowledge of computational language in python it is possible to write a code that write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.
Writting the code:n = int(input())
if 20 <= n <= 98:
while n % 11 != 0:
print(n)
n -= 1
print(n)
else:
print("Input must be 20-98")
See more about python at brainly.com/question/18502436
#SPJ1

Which of these are examples of how forms are
used? Check all of the boxes that apply.
to input patient information at a doctor's office
O to store thousands of records
to check out books from a library
to choose snacks to buy from a vending
machine
Answers
Answer:to input patient information at a doctors office
To check out books from a library
To choose snacks to buy from a vending machine
Explanation:
A. To input patient information at a doctor's office, C. To check out books from a library, and D. To choose snacks to buy from a vending machine are examples of how forms are used. Therefore option A, C and D is correct.
Forms are used in various settings and scenarios to collect and manage data efficiently.
In option A, forms are utilized at doctor's offices to input and record patient information, streamlining the registration and medical history process.
In option C, library check-out forms help manage book borrowing, recording details like due dates and borrower information. Option D showcases how vending machines use forms to present snack options, allowing users to make selections conveniently.
All these examples demonstrate the versatility of forms as tools for data collection, organization, and user interaction, contributing to smoother operations and improved user experiences in different domains.
Therefore options A To input patient information at a doctor's office, C To check out books from a library, and D To choose snacks to buy from a vending machine are correct.
Know more about vending machines:
https://brainly.com/question/31381219
#SPJ5
I need help picture above
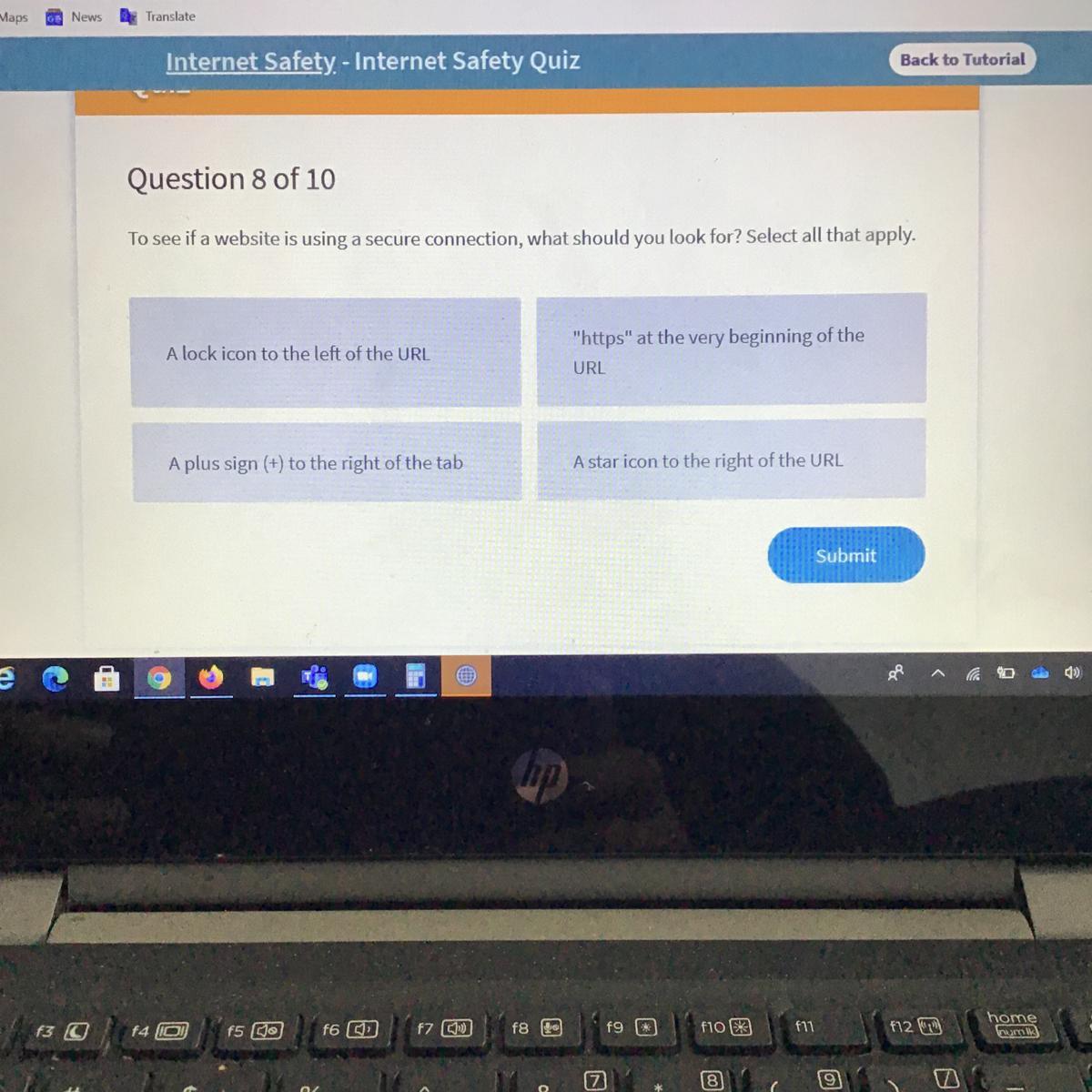
Answers
Answer:
The 2nd one on top and The Star ones.. (sorry if its wrong
Explanation:
can anyone help???
Consider the following website URL: http://www.briannasblog.com. What
does the "http://" represent?
A. FTP
B. Resource name
C. Protocol identifier
O D. Domain name

Answers
Answer: Protocol identifier
Explanation:
Just took the test and resource name was incorrect. Hope this helps :)
Consider the following website URL: http://www.briannasblog.com. The the "http://" represent the Protocol identifier. Thus, option C is correct.
What is the role of the parts of the Uniform Resource Locator?The resource name has been known as or it have the URL which has the name of the protocol that has been required for one to be able to gain entrance to a resource,
The protocol identifier has been known to be where the URL known which protocol to be used as the form of the primary entrance means. It has been known to the identify the IP address or domain name.The two part of the Uniform Resource Locator are protocol identifier and the resource name.
A subdirectory has the directory within the directory, which has been used to organize files and other directories. The URL can be broken down into two main parts: the domain name.
Therefore, two part of the Uniform Resource Locator are protocol identifier and the resource name.
Learn more about Uniform Resource on:
https://brainly.com/question/30074834
#SPJ7
Which of the following tabs in the PowerPoint Ribbon is unique to PowerPoint,
not found in other Microsoft Office applications?
a.
b.
Home
Animations
Insert
View
Answers
Answer:
The answer to this question is given below in the explanation section
Explanation:
The correct option for this question is Animation tab.
Animation tab in PowerPoint ribbon is a unique tab that is not found in other office applications such as in word, excel, outlook, publisher etc.
Because in PowerPoint you can use animation to make your slides animated and all animation can be managed and animation-related settings, you can find in the animation tab.
However, other tabs such as Home, Insert, and View are common in all office applications.
Question 1 of 4
OSHA requires which of the following trenches to have a protective system installed?
Select the best option.
O
A trench 1 foot deep.
A trench 3 feet deep.
A trench 14 feet deep.
Answers
Answer:
These are all wrong. OSHA requires a trench to have a protective system starting at 5 feet.
Explanation:
OSHA's own rules state this, unless it is in stable rock. If it is under 5 feet, it isn't required and can be decided by someone qualified.
Based on the description below which website is more appropriate
A. a site that asks you to send $10 to help schoolchildren in Uganda
B. a site that describe violent behavior
C. a site that asks for your personal information to win a contest for a new bike
D. a site sponsored by a government agency that gives you factual information
Answers
Answer:
D
Explanation:
Answer:
The answer is d
Explanation:
because asking for 10 dollars is the first website is not normal and in the second describing violent behavior is not ok and the third asking for personal information for a free bike is not good but d a site sponsored giving you factual information that made by the government is trustworthy
The are two schools of ____________ are Symmetry and Asymmetry.
Answers
The two schools of design that encompass symmetry and asymmetry are known as symmetrical design and asymmetrical design.
Symmetrical design is characterized by the balanced distribution of visual elements on either side of a central axis. It follows a mirror-like reflection, where the elements on one side are replicated on the other side, creating a sense of equilibrium and harmony.
Symmetrical designs often evoke a sense of formality, stability, and order.
On the other hand, asymmetrical design embraces a more dynamic and informal approach. It involves the intentional placement of visual elements in an unbalanced manner, without strict adherence to a central axis.
Asymmetrical designs strive for a sense of visual interest and tension through the careful juxtaposition of elements with varying sizes, shapes, colors, and textures.
They create a more energetic and vibrant visual experience.
Both symmetrical and asymmetrical design approaches have their merits and are employed in various contexts. Symmetry is often used in formal settings, such as architecture, classical art, and traditional graphic design, to convey a sense of elegance and tradition.
Asymmetry, on the other hand, is commonly found in contemporary design, modern art, and advertising, where it adds a sense of dynamism and creativity.
In conclusion, the schools of symmetry and asymmetry represent distinct design approaches, with symmetrical design emphasizing balance and order, while asymmetrical design embraces a more dynamic and unbalanced aesthetic.
For more such questions on symmetry,click on
https://brainly.com/question/31547649
#SPJ8
20 POINTS Which of the following statements is true of subroutines? Check all that apply.
They can be used in multiple places.
They can be used in one place only.
They save a programmer time since they are reusable.
They can be used only once.
They can contribute to excessive use of a computer’s resources.
Answers
Answer:
1,3,5?
Explanation:
What is the output?
class car:
model = "
age = 20
myCar = car()
myCar.age= myCar.age + 10
print(myCar.age)
Output:
Answers
Answer:
The answer to this question is 30
The explanation is given below
You can also see the attachment section to see the image of result
Explanation:
This question want use to print the value of myCar.age
print(myCar.age)
If we look at line 3, age=20
So the previous value is 20 and we have to add 10 to add as shown
myCar.age= myCar.age + 10
The value will become 30
Answer:
30
Explanation:
trust
in this phase, your program should receive two filenames as command line arguments, the new books file and request file, which the program should read in. the list of new books and list of requested books should be stored in only two std::vector containers. because some code to open these two files will probably be equivalent, you are encouraged to write generic functions in order to avoid code duplication. new books file
Answers
The program should receive two filenames as command line arguments, which it should read in. The two files should be stored in two std::vector containers. To avoid code duplication, generic functions should be written to open and process the files.
What is program?A program is a set of coded instructions designed to produce a specific result when executed by a computer or other electronic device. It is a set of instructions that can be executed by a processor in order to carry out a specific task or set of tasks. Programs are usually written in a high-level programming language, such as C or Java, which are then compiled into machine language and loaded into memory. Programs allow computers to do specific tasks, such as running an operating system, accessing data, and playing games.
The new books file should contain a list of new books that have been added to the library. The request file should contain a list of books that have been requested by patrons. The program should use the information from these two files to determine which books from the new books list should be sent to fulfill the patron requests. The program should then output the list of books that should be sent.
To learn more about program
https://brainly.com/question/23275071
#SPJ4
Temperature converter. This program should prompt the user for two arguments, first a decimal number and second, a single letter, either C or F. The decimal represents a temperature, the character represents which system that degree is in (50.0 F would be 50.0 degrees Fahrenheit etc.). This program should take the given number and convert it to a temperature in the other system. The output string format should be degree(s) is equal to degree(s) . Eg. input 0 C would give the string 0.0000 degree(s) C is equal to 32.0000 degree(s) F. You can assume that either F or C will be given for input, no need to account for invalid input.
Answers
Answer:
\( \boxed{ \tt{I \: wrote \: the \: program \:with \:( c++)}}\)
