Which of the following describe design themes in PowerPoint? Choose all that apply.
A. color scheme
B. colors, fonts, and formatting that coordinate
C. set of elements that unify your slides and complement your topic
D. set of coordinating fonts and colors from which you must choose
E. placement of text and graphics on a slide
Answers
Answer:
A. color scheme.
B. colors, fonts, and formatting that coordinate.
C. set of elements that unify your slides and complement your topic.
Explanation:
PowerPoint application can be defined as a software application or program designed and developed by Microsoft, to avail users the ability to create various slides containing textual and multimedia informations that can be used during a presentation.
Some of the features available on Microsoft PowerPoint are narrations, transition effects, custom slideshows, animation effects, formatting options etc.
To format an image on PowerPoint, you can either use the Artistic Effects or Picture Effects.
The Picture Effects gallery allows a user to access a variety of preconfigured formatting styles for images that are added to a PowerPoint presentation.
Basically, the Picture Effects consist of the following preconfigured formatting styles; transparent shadow, soft edge, reflection, glow, 3-D rotation, metal frame, bevels, perspectives etc.
The design themes in PowerPoint are described by the following;
A. Color scheme.
B. Colors, fonts, and formatting that coordinate.
C. Set of elements that unify your slides and complement your topic.
Answer:
A. color scheme.
B. colors, fonts, and formatting that coordinate.
C. set of elements that unify your slides and complement your topic.Explanation:
Related Questions
write a Visual Basic program that asks the user to enter their favourite colour and then displays the message "good choice" if they say "green" and the message "bad choice" otherwise.
Answers
Answer:
Module Module1
Sub Main()
Dim choice As String
Console.WriteLine("What is your favorite color?")
choice = Console.readline()
if choice == "green" Then
Console.WriteLine("Bad choice!")
Else
Console.WriteLine("Good choice!")
End Sub
End Module
which elements does the interaction model add to the action model?
a. Feedback and context
b. Message and context
c. Channel and noise
d. Encoding and decoding
Answers
The elements are channel and noise. The option C is the correct answer.
In order to determine the key components of communication, let's examine Joseph A. Devito's definition, which states that "communication refers to the act by one or more persons, of sending and receiving messages distorted by noise, within a context, with some effect and with some opportunity for feedback."
The channel refers to the medium through which the sender sends the message to the recipient. Our five senses—hearing, touching, smelling, tasting, and seeing—are the fundamentally natural means by which we communicate with one another. Five fundamental natural channels can be used to categorize communication.
Noise or communication barrier is anything that distorts message. Noise may originate in any of the components of communication like source, message, channel, context, receiver etc. Noise is present when there is difference between the message sent and received. Communication is not possible without noise, but its effects may be reduced through various methods such as using good grammar, clear voice, simple language, quality signal etc.
Learn more about channel here: https://brainly.com/question/15101442
#SPJ4
The main devices in a rectifier are:
Select one:
a. diodes.
b. transformers.
ion
c. transistors.
d. inductors.
Answers
A rectifier generally uses diodes.
Multiple Select
Which of the following statements about localization are true? Select 2 options.
The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
Really the only issue in localization is translating the text into another language.
You should avoid slang and idioms, since they will not be understandable to many audiences.
It is a good idea to use lots of images, since they are easily understood by all cultures.
For consistency, it is a good idea to use dollars as a currency in all versions of an application
Answers
Answer:
A. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
B. Really the only issue in localization is translating the text into another language.
Explanation:
In Computer science, localization can be defined as the process of designing, developing and adaptation of computer software applications or websites for different languages and geographical regions with peculiar differences.
This ultimately implies that, the main purpose for localization of a product such as a website or software application is to ensure they are specialized and specifically suited for a linguistic or geographical region.
The following statements about localization are true;
I. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
II. Really the only issue in localization is translating the text into another language.
Answer:
C. You should avoid slang and idioms since they will not be understandable to many audiences.
A. The goal of localization is to create an application or site that looks and feels like it was created for a specific market.
are the answers
Explanation:
What might happen to the wire if the uneven load is never balanced
Answers
If an uneven load on a wire is never balanced, it can lead to a variety of potential problems and risks. One of the most common consequences of uneven loading is the buildup of stress and tension in the wire, which can cause it to become overstretched and potentially snap or break.
When a wire is subjected to uneven loading, such as when a heavier weight is placed on one side of the wire than the other, the tension in the wire becomes unbalanced. This can cause the wire to become stretched beyond its normal limits, which can lead to deformation, fatigue, and ultimately failure. If the wire is not balanced, it may also be more susceptible to external factors such as wind, vibration, and temperature changes, which can exacerbate the stress and strain on the wire.
In addition to the risk of wire failure, uneven loading can also lead to other safety hazards. For example, if the wire is used to support a structure or equipment, an imbalance in the load can cause the structure to become unstable or the equipment to malfunction. This can result in property damage, injuries, and even loss of life.
To prevent these types of issues, it is important to ensure that loads are evenly distributed on wires and other support structures. This can be achieved through the use of proper rigging techniques, such as the use of equalizer bars or spreader bars, and by carefully monitoring loads to ensure that they are balanced at all times. By taking these precautions, the risk of wire failure and other safety hazards can be minimized.
To learn more about Wire loading, visit:
https://brainly.com/question/25922783
#SPJ11
what is saturating arithmetic and what are its advantages and disadvantages in typical multimedia applications?
Answers
Saturation arithmetic is a version of arithmetic under which all operations are limited to a fixed range.It aids in the modelling of actual physical processes and is inapplicable to standard mathematical operations.
What are the benefits of saturation in arithmetic?The necessity for overflows and underflows on MMX instructions is removed by saturating arithmetic. A result is saturated to the nearest permissible value if it is outside of boundaries. By minimising wraparound effects, saturating arithmetic is advantageous for many multimedia applications.
What is saturation arithmetic' flaw?On a system that can only perform modular arithmetic operations, it is difficult to efficiently implement saturation since basic solutions necessitate branches that cause significant pipeline delays.
Learn more about saturating arithmetic here:
https://brainly.com/question/15557985
#SPJ1
How many bits within the IEEE 802.1q tag are used to identify the VLAN of the frame? a. 8 b. 12 c. 16 d. None of the above
Answers
The correct answer is option C, 16 bits are used to identify the VLAN of the frame within the IEEE 802.1q tag.
This tag is added to Ethernet frames to provide VLAN identification information to switches and other network devices. The 16-bit VLAN ID field allows for up to 4096 different VLANs to be identified and distinguished from one another. This helps to segment network traffic and improve network performance and security. The IEEE 802.1q tag is an important feature of VLANs and is widely used in modern networking environments.
learn more about VLAN here:
https://brainly.com/question/30651951
#SPJ11
how many ones dose it take to get 9 tens
Answers
Explanation: there are 10 ones in one 10 so if you multiply 10 times 9 it’s 90
Explain the purpose of the National Institute of Standards Technology (NIST) Cybersecurity Framework.
a. -The NIST Cybersecurity Framework is a set of mandatory rules for organizations to follow in order to protect themselves against cybersecurity risks.
b. -The NIST Cybersecurity Framework is a voluntary guide that helps organizations understand and protect themselves against cybersecurity risks.
c. -The NIST Cybersecurity Framework is a system of computers that monitors national cybersecurity threats and relays the information to businesses and other organizations.
d. -The NIST Cybersecurity Framework is a cybersecurity software package available to organizations from NIST intended to bolster firewall capabilities.
Answers
The correct answer is (b) - The NIST Cybersecurity Framework is a voluntary guide that helps organizations understand and protect themselves against cybersecurity risks.
The purpose of the NIST Cybersecurity Framework is to provide a standardized set of guidelines, best practices, and procedures for organizations to manage and reduce cybersecurity risks. It is a framework that assists organizations in assessing and improving their ability to prevent, detect, respond to, and recover from cybersecurity events. The framework is flexible, adaptable, and scalable, and can be customized to fit the needs of different organizations, regardless of their size, industry, or sector. The NIST Cybersecurity Framework is widely recognized as a valuable resource for organizations to enhance their cybersecurity posture and protect their assets, customers, and stakeholders.
Learn more about Cybersecurity here:-
https://brainly.com/question/27560386
#SPJ11
Nathan took a picture of his friends while they were on a field trip. He wants upload this picture to a photo-sharing site. He wants to remove a few strangers that appear in the picture to the left of his friends. What tool will help him remove the unwanted people in the photograph?
Answers
Answer:
photoshop
Explanation:
(if there are answer choices pls comment them and I'll pick an answer from them, but this is just my best guess. : )
Answer:
Crop
Explanation:
I am not fully sure but the answer might be the crop tool, as you use that tool to cut unwanted people or objects out of a photo.
. how many stars (in terms of n) are printed in the following code segment?10 for(i=1; i≤n; i=i 1) for(j=i 1; j ≤n; j=j 1) print(""*"");
Answers
The number of stars that are printed in the code segment above is given by the summation of n from i=1 to n. The code can be read as follows: For each i between 1 and n, it should print n-i+1 stars. Therefore, we can use summation to determine the number of stars.
The code provided above prints a pattern of stars where every line consists of a total of n stars. The first line consists of n stars, the second line consists of n-1 stars, the third line consists of n-2 stars, and so on until the last line which consists of a single star. The value of n determines the height of the pattern.In order to determine the number of stars printed in the given code segment, we can use summation.
We need to calculate the total number of stars printed, which is equal to the sum of the number of stars printed in each row of the pattern. The formula for the number of stars printed in each row is given by: n - i + 1 where i is the row number.To find the total number of stars printed, we need to sum up the number of stars in each row. This can be expressed as follows:∑(n - i + 1) for i = 1 to n= ∑(n + 1 - i) for i = 1 to n= n(n + 1) / 2By using the above formula, we can calculate the total number of stars printed in the given code segment.
To know more about printed visit:
https://brainly.com/question/31960406
#SPJ11
Assignment: Blues Progression
Blues is a sub-genre of jazz that follows some specific guidelines: specifically, the Blues scale and the Blues chord progression.
In this assignment, you’ll write out a 12-bar Blues chord progression. This assignment is a MuseScore assignment. Do not turn in this document for grading.
Directions:
1. Create a new document in MuseScore
a. For the title, write “MuseScore Assignment: Blues”.
b. For the composer, write your name., then click "next".
c. Under "general", choose “Grand Staff”, then click “Next”.
d. Choose G major for your key signature (1 sharp), then click next.
e. Choose “Piano” (in the Keyboards section) for your instrument. (This step may or may not show for you. It's ok either way!)
f. Choose 4/4 for your Time Signature and 12 measures for number of measure.
g. Click “Finish”.
2. In the Bass Clef, write out a 12-bar Blues Chord Progression.
a. Use whole notes for your chords
b. I – I – I – I – IV – IV – I – I – V7 – IV – I – V7
Save your assignment (with your name!) and submit it to the Composition: Blues Progression Dropbox basket. Turn in the MuseScore file only.
Answers
Explanation:
I can provide you with the 12-bar Blues chord progression as you requested:
In the key of G major:
I (G) – I (G) – I (G) – I (G)
IV (C) – IV (C) – I (G) – I (G)
V7 (D7) – IV (C) – I (G) – V7 (D7)
The Roman numerals in parentheses represent the chords to play in each measure, and the chord names outside the parentheses indicate the actual chords to play in the key of G major.
write the steps how to insert an online images
Answers
Answer:
There are many ways but this way is to upload a pick from desktop to ur doccument ( TAE IS MY BIAS, STREAM BUTTER BBG)
Explanation:
0) Well obv u have to download a pick
1) Click in your where you want to insert your picture.
2) Click the Insert tab.
3) pick the picture you want to insert and select it.
4)Click Insert button
Worms and Trojans are typically harmless because the originator of such attacks are usually known to the recipient, and as such, are not intended to cause much harm.
(A) True
(B) False
Answers
Answer:
False
Explanation:
Viruses, worms and trojans are all malicious programs that can damage your computer. Also i got an A soo...
3. A file of unknown length needs to be read. The following algorithm is given: students File.open("students.txt") while (studentsFile.readLine() endwhilE Complete the condition in the WHILE loop. print JUTT [1] please help explanation + answer greatly appreciated
Answers
To read a file named "students.txt" of unknown length, use the following code snippet in Ruby:
The Programstudents_file = File.open("students.txt")
students_file.each_line do |line|
puts "JUTT [1]"
# Your code here to process each line
end
students_file.close
This code opens the file, iterates over each line, prints "JUTT [1]" for each line, and allows you to process the line within the loop. Finally, the file is closed.
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
What two choices do you have when you open the Remote tab of the System Settings?
Answers
Answer:
remote assistance and remote desktop
Explanation:
^
What is the average CPI for a processor with 3 instruction classes, A, B, and C having relative frequencies of 50%. 25%, and 25% respectively and individual CPI's of 1, 2, and 4 respectively?
Answers
On the other hand, if the CPI is 2, you have only spent half of what you ought to have.
The average number of clock cycles per instruction for a program or program fragment is known as cycles per instruction (also known as clock cycles per instruction, clocks per instruction, or CPI) in computer architecture. It is instructions per cycle's multiplicative inverse. You are going over your budget. A CPI of 0.5, for instance, means that by a particular period, you have spent twice as much as you ought to have. Then, they can utilize CPI to ascertain the economy's overall price levels to gauge the cost of living in a whole nation or a particular region.
Learn more about instruction here-
https://brainly.com/question/21852411
#SPJ4
A search engine is giving you too many sites that are not relevant to your topic, how cell phones change culture. Placing quotes around "cell phones change culture" gave only five results. What can you try next?
A.
change your key words
B.
use an advanced search
C.
use a search directory
D.
all of the above
PLease hurry
Answers
Answer:
all of the above
Explanation:
Answer:
D. all of the above
Write a program to display "HELLO WORLD"
Answers
Explanation:
Here's a simple "Hello, World!" program written in Python:
```python
print("HELLO WORLD")
```
To execute this program, you need to have Python installed on your computer. Save the code above to a file named `hello_world.py` and then run it using the command `python hello_world.py` in the terminal or command prompt.
The ________ networks operate close to the legitimate free hotspots and typically provide stronger signals
Answers
Answer:
Rogue Hotspot
Explanation:
Which of the following is False with respect Python code?
class Student:
def __init__(self,id,age):
self.id=id
self.age=age
std=Student(1,20)
A. "std" is the reference variable for object Student(1,20)
B. id and age are called the parameters.
C. Every class must have a constructor.
D. None of the above
Q6.8: What is the output of the following piece of code?
class A:
def __str__(self):
return '1'
class B(A):
def __init__(self):
super().__init__()
class C(B):
def __init__(self):
super().__init__()
def main():
obj1 = B()
obj2 = A()
obj3 = C()
print(obj1, obj2,obj3)
main()
Answers
The statement that is False with respect to the Python code provided is:
C. Every class must have a constructor.
In Python which class have to have a constructor?In Python, a class does not necessarily have to have a constructor. If a class does not define an `__init__()` method, Python automatically provides a default constructor. However, if you want to initialize class attributes or perform any other actions during object creation, you can define a constructor explicitly. The code provided in the first part of the question shows an explicit constructor (`__init__()` method) defined in the `Student` class.
Regarding the code in the second part of the question, the output will be:
1 1 1
Learn more about Python
brainly.com/question/30391554
#SPJ11
Code Hs karal 3.4.2 lots of hurdles?? I cannot figure this one out at all
Answers
Answer:
codeHS 3.4.2: Lots of Hurdles answer
Explanation:
Suppose the xMethod() is invoked from a main method in a class as follows, xMethod() is _________ in the class.
public static void main(String[] args) {
xMethod();
}
Answers
In the given scenario, where the `xMethod()` is invoked from the `main` method in a class, the `xMethod()` is most likely a static method in the class.
In the given code, what is the nature of the xMethod() in the class?The code snippet demonstrates the invocation of the xMethod() from the main method in a class.
Since the main method is static, the xMethod() is also required to be static in order to be called directly from the main method.
Being a static method means that the xMethod() belongs to the class itself, rather than being associated with any specific instance or object of the class.
Static methods can be accessed and called without creating an instance of the class.
They are commonly used for utility methods or operations that do not require accessing instance-specific data or behavior.
In this case, the xMethod() can be directly invoked from the main method as both methods are static, enabling the execution of code within the xMethod() implementation.
The static nature of xMethod() allows it to be called without instantiating an object, providing a convenient way to execute specific functionality within the class.
Learn more about static method
https:/brainly.com/question/31454032
#SPJ11
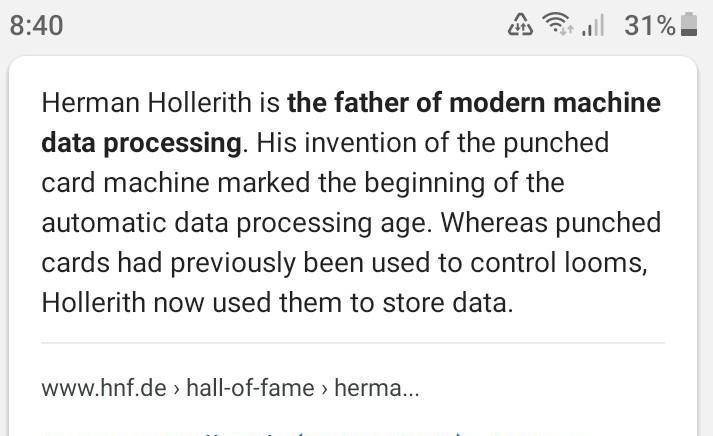
who was Dr. Hean Hollerith
Answers
Answer: Herman Hollerith, (born February 29, 1860, Buffalo, New York, U.S.—died November 17, 1929, Washington, D.C.), American inventor of a tabulating machine that was an important precursor of the electronic computer.
Explanation:
Answer:
☝️here is a answer ......
A software developer is setting up a system for a medium-sized business to
encrypt large amounts of data on its own servers. Which cryptography
technique should the developer use and why?
A. Biometric encryption, to secure the data from everyone who
shouldn't have access
OB. Hash encryption, to convert the data into hash values so it can't be
easily read
OC. Asymmetric encryption, to protect the personal data of senders
and receivers
D. Symmetric encryption, since the data isn't being shared across an
open network
SUBMIT
Answers
The most appropriate cryptography technique for a software developer to use in this scenario would be symmetric encryption.
What is the Symmetric encryption?Symmetric encryption is a fast and efficient method for encrypting large amounts of data on local servers, and it is well-suited for situations where the data is not being shared across an open network.
Asymmetric encryption would be overkill in this situation, and biometric encryption would only protect against unauthorized physical access to the server.
Hash encryption, while useful for verifying the integrity of data, does not provide confidentiality and would not be appropriate for encrypting large amounts of sensitive data.
Read more about cryptography here:
https://brainly.com/question/24261371
#SPJ1
Wireless communication requires the use of a ________ signal to ________ the message so it can be sent at a preassigned _________.
Answers
Wireless communication requires the use of a modulated signal to encode the message so it can be sent at a preassigned frequency.
In wireless communication systems, information is transmitted through the air using electromagnetic waves. These waves are created by varying or modulating a specific characteristic of the carrier signal, such as its amplitude, frequency, or phase. This process, known as modulation, is essential for converting the original message, which can be in the form of voice, data, or multimedia content, into a format suitable for wireless transmission.
The preassigned frequency is crucial in maintaining an organized and efficient communication system. Each wireless device operates within a specific frequency range, which is allocated by regulatory bodies like the Federal Communications Commission (FCC) or International Telecommunication Union (ITU). This allocation ensures that different communication services can coexist without causing interference with one another.
Modulation techniques, such as Amplitude Modulation (AM), Frequency Modulation (FM), or Phase Modulation (PM), are used to represent the message in the carrier signal. These techniques allow the message to be efficiently transmitted over long distances with minimal loss of quality. At the receiving end, a process called demodulation is used to extract the original message from the modulated carrier signal.
know more about Amplitude Modulation here:
https://brainly.com/question/10060928
#SPJ11
You are doing a multimedia presentation on World War I, and you want to use a visual aid to show the battle areas. What visual aid is best suited for this purpose?
Answers
Answer:
You are doing a multimedia presentation on World War I, and you want to use a visual aid to show the battle areas. What visual aid is best suited for this purpose?
Explanation: it is a map.
The visual aid that will be good for the multimedia presentation is a map.
Visual aids are simply referred to as items of a visual manner like graphs, maps, video clips, etc that are used in addition to spoken information.
In this case, since the individual is doing a multimedia presentation on World War I, and wants to use a visual aid to show the battle areas, a map will be the appropriate visual aid to use in this case.
Read related link on:
https://brainly.com/question/3198345
Anyone know the logic notation of this following logic circuit?

Answers
Answer:
Concept: Logic Circuit
You have two variables A and B A and B go to the XOR logic command.B goes to the NOT operator Lastly the result of both XOR & NOT go to the OR operator Please rate positively and give brainlisti need a computer science help.....and I rlly want it right now...this the question
calculate all multiples of 5 that are less than a randomly generated number between 12 and 45. for example the random number is 16. the output is then 5,10,15 python
so basically if type a number between 12 and 45 it shud give me all the multiples of 5 less than the number i typed......pls help;-;
Answers
(01.01 LC)
Programmers perform which of the following tasks?
Build and maintain network connections
O Create web and mobile applications
O Design graphics for websites
Repair computers and servers
Answers
Answer:
Create web and mobile applacations
Explanation:
Programmers primarily build and maintain software applications, including web and mobile applications.
What is software?Programmers typically work with software, which is a collection of instructions and programmes that instruct a computer or other electronic device on what to do.
They create, test, and maintain software applications for desktops, mobile devices, and the web using programming languages such as Java, Python, and C++.
Programmers create and maintain software applications, such as web and mobile applications.
They may also design the application's user interface and user experience, but they are not typically in charge of designing graphics for websites.
Furthermore, while programmers may be involved in troubleshooting and resolving issues related to the software application they have created, they are not typically in charge of repairing hardware such as computers and servers.
Thus, the correct answer is "Build and maintain network connections".
For more details regarding software, visit:
https://brainly.com/question/985406
#SPJ2