which network security technology can block or restrict access if a computer does not have the latest antivirus update, a certain security patch, or a host firewall?
Answers
The network security technology that can block or restrict access if a computer does not have the latest antivirus update, a certain security patch, or a host firewall is called Network Access Control (NAC).
Network Access Control (NAC) is a security solution that ensures that only trusted and compliant devices are allowed to access the network. It verifies the health status of endpoints before granting access and can enforce policies such as requiring the latest antivirus updates, security patches, or host firewalls before allowing access to the network. Network Access Control (NAC) is a critical component of modern network security architecture, and it helps to prevent security breaches caused by non-compliant or compromised devices.
To learn more about NAC visit : https://brainly.com/question/23839429
#SPJ11
Network Access Control (NAC) is the name of the network security technique that can restrict or prevent access if a computer lacks the most recent antivirus update, a specific security patch, or a host firewall.
Only reliable and compliant devices are permitted to access the network thanks to Network Access Control (NAC), a security measure. Before authorising access, it checks the endpoints' health state. It can also impose rules such requiring the most recent host firewalls, antivirus updates, and security patches. A key element of contemporary network security design, network access control (NAC) aids in preventing security breaches brought on by non-compliant or compromised devices. By assessing the security posture of a device before giving network access, Network Access Control (NAC) technology can prevent or restrict access if a computer lacks the most recent antivirus update, a specific security patch, or a host firewall.
learn more about Network Access here:
https://brainly.com/question/28388830
#SPJ11
Related Questions
how to print something nad input on same line python
Answers
Which of the statements indicates that Shane & Co. is an ethical organization?
Shane & Co. deal in manufacturing plastic cups. Despite three years of operations, they haven’t been able to even break even. The irate investors are eagerly waiting for the next financial report that is due. Shane & Co. can manipulate the figures to show growth, however they choose to display the facts as it is. They are sure to lose some of the investors on board but are willing to take the risk.
Shane & Co. deal in manufacturing plastic cups
Despite three years of operations, they haven’t been able to even break even
Shane & Co. can manipulate the figures to show growth
however they choose to display the facts as it is
They are sure to lose some of the investors on board
but are willing to take the risk

Answers
Answer:
however they choose to display the facts as it isbut are willing to take the riskThe spreadsheet prepared on the computer is called..........
Answers
Answer:
electronic spreadsheet
Explanation:
I got it from google. Not 100% sure. Tell me if i'm wrong.
Answer:
Explanation:
electrion got it from goggle to sorry if it is wrong
If you’re paid hourly and work 40 hours in one week how much overtime have you worked? 8 hours none $48 or $80
Answers
Answer: You said 40 Hours. So $40
So, Isn't it $48, Because How Do You Get 80?
Answer:
$80.
Explanation:
Just go with it.
Clustering partitions a collection of things, such as objects and events presented in a structured dataset into segments whose members share similar characteristics. (True or False)
Answers
The statement "Clustering partitions a collection of things, such as objects and events presented in a structured dataset, into segments whose members share similar characteristics." is true.
Clustering is a machine learning technique that involves partitioning a dataset into segments or clusters based on the similarity of the objects or events in the dataset. The goal of clustering is to group together objects or events that are similar to each other and to separate those that are dissimilar.
In clustering, the dataset is analyzed to identify common characteristics that can be used to group objects or events together. These characteristics may include properties such as size, color, shape, or any other measurable attribute that can be used to differentiate between objects. Once the common characteristics are identified, the dataset is partitioned into segments or clusters, with each cluster containing objects or events that share similar characteristics.
To learn more about clustering visit : https://brainly.com/question/30881716
#SPJ11
what should the forensics specialist keep updated and complete in order to support his or her role as an expert and document enhancement of skills through training, teaching, and experience?
Answers
In order to defend his or her position as an expert and to demonstrate how training, instruction, and experience have improved their skills, forensics specialists maintain thorough and up-to-date "CVs."
Explain the term forensics specialist?Using various analysis techniques, such as chemical, instrumental, microscopic, as well as physical analysis, forensic specialists examine and assess physical evidence.
They may occasionally need to handle biological materials such as blood, hair, and the remains of gunshots. The responsibilities of a forensic specialist depend on their specialty.The Latin word curriculum vitae (CV) means "course of life." Resumé, on the other hand, is French meaning "summary." CVs and resumes both: are customized for the particular position/business you are applying for. should demonstrate that you are the most qualified applicant.Thus, in order to defend his or her position as an expert and to demonstrate how training, instruction, and experience have improved their skills, forensics specialists maintain thorough and up-to-date "CVs."
To know more about the forensics specialist, here
https://brainly.com/question/28149413
#SPJ4
I hey could use the Internet access documents on the company network, and communicate with customers, managers and fellow employees using email, telephone and virtual access to reach out to their clients, conduct meetings as well as face to face . YOUR TASK FOR THE ASSIGNMENT - Write a MEMO to Heather Miller, your company president, discussing the pros and cons of the proposal plan. - Recommend whether or not she should adopt the plan. - Provide her with relevant information as to why it should be considered for the employees to work from home. - When providing your information consider the security measures of using your home equipment, how secure are they? - How reliable are they? - Also try to show the amount of time employees have to commute each day - Try to make your response in favor of the request of the employees KEY FACTORS TO LOOK AT IN THE CASE - Address the main subject of the Memo - Organize the most important points from the case before you begin writing - Address the main subject of the Memo (in the subject line as well as the opening sentence) - The use of the 5W
′
s - Remember to provide a Memo format for the assignment as shown in your online textbook.
Answers
It reduces commuting time, increases job satisfaction, and allows for a better work-life balance. However, it is crucial to address the security and reliability concerns associated with using home equipment.
I am writing to discuss the proposal for implementing remote work arrangements within our company. After careful consideration, I recommend adopting this plan due to the numerous benefits it offers. Remote work enables employees to access company documents, communicate with clients, managers, and colleagues through various means, and conduct meetings effectively.
I highly recommend adopting the proposed remote work plan for our employees. By allowing them to work from home, we can harness the power of the internet to provide them with access to necessary company documents and facilitate communication with clients, managers, and fellow employees. This will enhance productivity and efficiency, as employees can seamlessly collaborate and stay connected through email, telephone, and virtual meetings.
One of the significant advantages of remote work is the reduction in commuting time. Employees no longer have to endure long and stressful daily commutes, which can have a negative impact on their well-being and productivity. By eliminating this commute, they gain valuable time that can be devoted to work or personal activities, leading to increased job satisfaction and a better work-life balance.
However, it is important to address the security and reliability concerns associated with using home equipment. Adequate security measures, such as VPNs and encryption protocols, must be implemented to ensure the protection of company data. Additionally, employees should receive training on best practices for maintaining a secure work environment at home. Regular IT support and maintenance should also be provided to ensure the reliability of home equipment, minimizing any potential disruptions to work.
In conclusion, adopting the proposal for remote work arrangements offers numerous benefits for our employees and the company as a whole. It promotes efficient communication, reduces commuting time, increases job satisfaction, and provides a better work-life balance. While security and reliability concerns must be addressed, these can be mitigated through the implementation of appropriate measures. Therefore, I recommend moving forward with the plan and embracing the advantages that remote work can bring.
Sincerely,
[Your Name]
[Your Position/Department]
Learn more about commuting time here:
https://brainly.com/question/12951274
#SPJ11
_______ uses individual atoms and molecules to create computer chips and other devices.
a. Virtualization
b. Nanotechnology
c. Quantum computing
d. A minicomputer
e. On-demand computing
Answers
b. Nanotechnology. Nanotechnology uses individual atoms and molecules to create computer chips and other devices.
Nanotechnology is a field of science and engineering that deals with manipulating matter at the atomic and molecular scale, typically with structures ranging from 1 to 100 nanometers in size. It involves the use of individual atoms and molecules to create new materials and devices with unique properties and functionalities. In the context of computer chips and other devices, nanotechnology enables the precise placement and manipulation of individual atoms and molecules to design and fabricate ultra-small electronic components with enhanced performance and efficiency. This technology has the potential to revolutionize various industries, including electronics, medicine, energy, and more, by allowing the creation of advanced materials and devices with unprecedented capabilities at the nanoscale.
learn more about computer here:
https://brainly.com/question/30529533
#SPJ11
Write a Java program that is reading from the keyboard a value between 122 and 888 and is printing on the screen the prime factors of the number.
Your program should use a cycle for validating the input (if the value typed from the keyboard is less than 122 or bigger than 888 to print an error and ask the user to input another value).
Also the program should print the prime factors in the order from smallest to biggest.
For example,
for the value 128 the program should print 128=2*2*2*2*2*2*2
for the value 122 the program should print: 122=2*61
b. change the program at a. to print one time a prime factor but provide the power of that factor:
for the value 128 the program should print 128=2^7
for the value 122 the program should print: 122=2^1*61^1
a. Write a Java program to convert numbers (written in base 10 as usual) into octal (base 8) without using an array and without using a predefined method such as Integer.toOctalString() .
Example 1: if your program reads the value 100 from the keyboard it should print to the screen the value 144 as 144 in base 8=1*8^2+4*8+4=64+32+4=100
Example 2: if your program reads the value 5349 from the keyboard it should print to the screen the value 12345
b. Write a Java program to display the input number in reverse order as a number.
Example 1: if your program reads the value 123456 from the keyboard it should print to the screen the value 654321
Example 2: if your program reads the value 123400 from the keyboard it should print to the screen the value 4321 (NOT 004321)
c. Write a Java program to display the sum of digits of the input number as a single digit. If the sum of digits yields a number greater than 10 then you should again do the sum of its digits until the sum is less than 10, then that value should be printed on the screen.
Example 1: if your program reads the value 123456 then the computation would be 1+2+3+4+5+6=21 then again 2+1=3 and 3 is printed on the screen
Example 2: if your program reads the value 122400 then the computation is 1+2+2+4+0+0=9 and 9 is printed on the screen.
Answers
The provided Java programs solve various problems, including finding prime factors, converting to octal, reversing a number, and computing the sum of digits as a single digit.
Here are the Java programs to solve the given problems:
Prime Factors Program:
import java.util.Scanner;
public class PrimeFactors {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
int value;
do {
System.out.print("Enter a value between 122 and 888: ");
value = input.nextInt();
if (value < 122 || value > 888) {
System.out.println("Invalid input! Please try again.");
}
} while (value < 122 || value > 888);
System.out.print(value + "=");
int divisor = 2;
while (value > 1) {
if (value % divisor == 0) {
System.out.print(divisor);
value /= divisor;
if (value > 1) {
System.out.print("*");
}
} else {
divisor++;
}
}
}
}
Prime Factors Program with Powers:
import java.util.Scanner;
public class PrimeFactorsPowers {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
int value;
do {
System.out.print("Enter a value between 122 and 888: ");
value = input.nextInt();
if (value < 122 || value > 888) {
System.out.println("Invalid input! Please try again.");
}
} while (value < 122 || value > 888);
System.out.print(value + "=");
int divisor = 2;
int power = 0;
while (value > 1) {
if (value % divisor == 0) {
power++;
value /= divisor;
} else {
if (power > 0) {
System.out.print(divisor + "^" + power);
if (value > 1) {
System.out.print("*");
}
}
divisor++;
power = 0;
}
}
if (power > 0) {
System.out.print(divisor + "^" + power);
}
}
}
Convert to Octal Program:
import java.util.Scanner;
public class ConvertToOctal {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter a decimal number: ");
int decimal = input.nextInt();
int octal = 0;
int multiplier = 1;
while (decimal != 0) {
octal += (decimal % 8) * multiplier;
decimal /= 8;
multiplier *= 10;
}
System.out.println("Octal representation: " + octal);
}
}
Reverse Number Program:
import java.util.Scanner;
public class ReverseNumber {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter a number: ");
int number = input.nextInt();
int reversed = 0;
while (number != 0) {
int digit = number % 10;
reversed = reversed * 10 + digit;
number /= 10;
}
System.out.println("Reversed number: " + reversed);
}
}
Sum of Digits Program:
import java.util.Scanner;
public class SumOfDigits {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter a number: ");
int number = input.nextInt();
int sum = computeDigitSum(number);
while (sum >= 10) {
sum = computeDigitSum(sum);
}
System.out.println("Sum of digits as a single digit: " + sum);
}
private static int computeDigitSum(int num) {
int sum = 0;
while (num != 0) {
sum += num % 10;
num /= 10;
}
return sum;
}
}
These programs address the different requirements mentioned in the problem statement.
Learn more about Java programs: brainly.com/question/26789430
#SPJ11
You receive a worksheet in which the rows are numbered 1, 2, 3, 5,6. This means that row 4 is _____.
Answers
People often hide cells of worksheet due to different reasons. This means that row 4 is hidden.
A worksheet is commonly know as a sheet of paper/computer sheet with which work is done or performed.
An individual can hide any worksheet so that it can be removed from their view. The data in hidden worksheets is not visible to the person, but it can still be referenced from other worksheets and workbooks. One can unhide hidden worksheets if need be.
Learn more from
https://brainly.com/question/17106092
8.if converting scada systems to the internet protocol increases the risk of a hacker taking control of an industrial process, why are companies doing just that?
Answers
Companies are trying to convert SCADA systems to Internet Protocol in order to save money and perform remote maintenance and monitoring.
What is a hacker?Computer hackers are unauthorized users who gain access to computer systems with the intent of stealing, changing, or destroying data, frequently by installing dangerous malware without your knowledge or consent.
Their deft tactics and in-depth technical knowledge enable them to gain access to information you don't want them to have.
If a SCADA system is not properly supervised, it is vulnerable. These systems are designed to keep up with the latest technological advances.
Companies are attempting to convert SCADA systems to Internet Protocol in order to save money on maintenance and monitoring.
Thus, due to this, companies are converting SCADA systems to IP.
For more details regarding hacker, visit:
https://brainly.com/question/29215738
#SPJ1
An accountant initially records adjusting entries in a(n) _____.
A. revenue record
B. ledger
C. expense record
D. Journal
Answers
Adjusting entries are changes to journal entries you've already recorded.
Answer:
Ledger
Explanation:
Believe me it's not a journal
should i start playing this new rpg game called hordes,io after school work?
Answers
Answer:
yes
Explanation:
Which of the following is something that an Information Technology (IT) professional would do?
Collect and utilize data
Create and improve software
Manage grades and enrollments
Build and repair computers
Answers
Answer:
Probably the last one, build and repair computers.
Households can save approximately 6% off their electricity bill by running their dishwasher and washing machines off peak. On average how much can they cut off their bill if the bill for the year is $1000.
Answers
Answer: like up to 75%
an application layer process needs to transmit data with as little overhead as possible. the application protocol provides error detection and recovery if the data is lost. what transport layer protocol should this process use?
Answers
If the data is lost, the application protocol offers error detection and recovery. "User Datagram Protocol" is the transport layer protocol utilized for the procedure.
Explain the term User Datagram Protocol?A communications protocol called User Datagram Protocol (UDP) is largely used to establish low-latency, loss-tolerant connections between internet-based applications.
UDP allows data to be transferred before the receiving party provides an agreement, which speeds up transfers.The communication between application processes (clients & servers) operating on various end systems is governed by application layer protocols. An application layer, in particular, is indeed an abstract layer that manages the TCP/IP and OSI model's sharing protocol.For the stated question-
A procedure at the application layer must communicate data with the least amount of overhead. When errors occur, the application protocol offers error recovery in case the data is lost.Thus, the process uses "User Datagram Protocol," a transport layer protocol.
To know more about the User Datagram Protocol, here
https://brainly.com/question/20038618
#SPJ4
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
How has technology impacted and affected the customer service
industry? Be informative and provide examples.
Answers
Technology has transformed the customer service industry by improving communication, enabling self-service options, personalizing experiences, automating processes, providing omnichannel support, and leveraging data-driven insights. Businesses that embrace technology in their customer service strategies can enhance customer satisfaction, loyalty, and overall business performance.
Technology has had a significant impact on the customer service industry, revolutionizing the way businesses interact with their customers and enhancing overall customer experience. Here are some key ways technology has affected the customer service industry:
Improved Communication Channels: Technology has introduced various communication channels that allow customers to connect with businesses more conveniently. For example, the rise of email, live chat, social media platforms, and chatbots has enabled customers to reach out to businesses in real-time, get instant responses, and resolve issues efficiently.
Self-Service Options: Technology has empowered customers with self-service options, reducing the need for direct customer support. Customers can now access knowledge bases, FAQs, online forums, and video tutorials to find answers to their queries and troubleshoot common issues independently.
Personalization and Customization: Advanced technologies, such as artificial intelligence (AI) and data analytics, have enabled businesses to collect and analyze customer data. This data helps in personalizing customer experiences, offering tailored recommendations, and anticipating customer needs. For example, personalized product recommendations on e-commerce websites based on previous purchases or browsing history.
Automation and Efficiency: Technology has automated various customer service processes, leading to increased efficiency and faster response times. Businesses now utilize automated ticketing systems, chatbots, and AI-powered voice assistants to handle routine inquiries, process transactions, and provide instant support. This automation frees up human agents to focus on more complex customer issues.
Omnichannel Support: With technology, businesses can provide seamless customer service across multiple channels. Customers can initiate a conversation on one channel, such as social media, and seamlessly transition to another channel, like phone or email, without having to repeat information. This omnichannel approach ensures a consistent and integrated customer experience.
Data-driven Insights: Technology allows businesses to gather and analyze vast amounts of customer data, providing valuable insights into customer preferences, behaviors, and pain points. This data helps in identifying trends, making informed business decisions, and improving customer service strategies.
Examples of technology in customer service include:
Customer Relationship Management (CRM) systems that store and manage customer information, interactions, and preferences.
Voice recognition and natural language processing technologies used in voice assistants and chatbots for more accurate and efficient customer interactions.
Social media monitoring tools that track brand mentions, customer feedback, and sentiment analysis to address customer concerns and engage in proactive communication.
Virtual reality (VR) and augmented reality (AR) technologies that enable immersive product demonstrations, virtual tours, and remote troubleshooting.
To know more about customer service visit :
https://brainly.com/question/13208342
#SPJ11
in the lectures, there is an example of web server using multi-threading. it creates a new thread to serve every request. suppose you like to limit the resource consumption by allowing no more than 100 active threads simultaneously, how do you modify the code to realize this limit?
Answers
A style of program execution known as "multithreading" enables the creation of many threads that can run concurrently and independently while sharing process resources. If allocated to their own CPU core, threads may be able to operate in full parallel, depending on the hardware.
Performance is the main justification for adding threads to a program.
There is a web server example employing multi-threading in the lectures. In order to fulfill each request, it starts a new thread. How would the code be modified if you wanted to implement a limit of 100 active threads at a time to reduce resource consumption?
In this scenario, we may monitor the quantity of newly created threads.
To learn more about Multithreading refer to:
https://brainly.com/question/13155644
#SPJ4
which of the following is the practice of sharing computing resources, such as servers, like those in the accompanying figure? a. virtualization b. aggregation c. clustering d. concatenation
Answers
The practice of sharing computing resources, such as servers, like those in the accompanying figure, is a) virtualization.
Virtualization is the creation of a virtual version of a device or resource, such as a server, storage device, network, or operating system. It enables multiple virtual devices to operate on a single physical device, allowing the resources of the physical device to be used more efficiently. In this way, virtualization can be used to consolidate resources, reduce costs, and increase flexibility. Virtualization can be used in a variety of settings, including data centers, cloud computing, and desktop computing. It can also be used for a range of purposes, including server consolidation, disaster recovery, software testing and development, and desktop virtualization.
Virtualization is typically achieved through software that creates a virtual layer between the physical device and the virtual devices that run on it. This software is known as a hypervisor or virtual machine monitor (VMM). The hypervisor manages the virtual devices and allocates resources to them as needed.
Therefore, the correct answer is a) virtualization.
Learn more about Virtualization here: https://brainly.com/question/23372768
#SPJ11
Please! I need help matching this.
Answers
We can see here that matching the term with its description, we have:
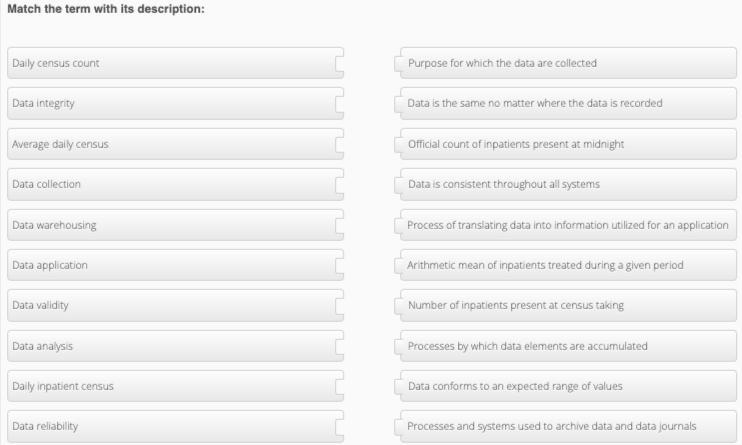
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
A feature that allows you to quickly apply the contents of one cell to another cell or range of cells selected.
O auto fill
O auto sum
O fill down
O fill right
Answers
Answer:
Auto fill
Explanation:
I took the test!
Write a program that reads two times in military format (0900, 1730) and prints the number of hours and minutes between the two times.
Answers
In order to write a program in Python that reads two military formatted times (0900 and 1730) and then prints the number of hours and minutes between the two times, we can follow these steps.
Input the two times from the userStep 2: Extract the hour and minute values from each timeStep 3: Convert both times to minutes and store them in separate variablesStep 4: Calculate the absolute difference between the two times in minutesStep 5: Calculate the hours and minutes from the difference in minutesStep 6: Print the output in the required format (i.e. hours and minutes)Here is the Python code that implements the above steps:# Step 1: Input the two timesfrom_time = input("Enter the first military formatted time (HHMM): ")to_time = input("Enter the second military formatted time (HHMM): ")# Step 2: Extract the hour and minute\(valuesfrom_hour1 = int(from_time[:2])from_min1 = int(from_time[2:])to_hour2 = int(to_time[:2])to_min2 = int(to_time[2:])\)# Step 3: Convert both times to \(minutesfrom_min_total = (from_hour1 * 60) + from_min1to_min_total = (to_hour2 * 60) + to_min2\)#
Calculate the absolute difference between the two times in \(minutesdiff_min = abs(from_min_total - to_min_total)\)# Step 5: Calculate the hours and minutes from the difference in \(minuteshours = diff_min // 60minutes = diff_min % 60\)# Step 6: Print the output in the required format (i.e. hours and minutes)print("The difference between", from_time, "and", to_time, "is", hours, "hours and", minutes, "minutes.")Note: This program works correctly only if the second input time is greater than the first input time. Also, the input time values must be in the 24-hour format (HHMM).
To know more about separate visit:
https://brainly.com/question/13619907
#SPJ11
In a ______, the bars that represent the categories of a variable are spaced so that one bar is not directly next to another; whereas in a ______, the bars actually touch one another.
Answers
Answer:
The correct answer would be "bar graph; histogram".
Explanation:
The bar graph has become a photographic arrangement of information which always practices that relate bars to consider various give information. Alternatively, this is indeed a diagrammatic comparative analysis of univariate data. This same histogram demonstrates the variation including its frequency of repeated measures, introduces numerical information.northern trail outfitters is using one profile for all of its marketing users, providing read-only access to the campaign object. a few marketing users now require comprehensive edit access on campaigns. how should an administrator fulfil this request
Answers
Configure the login policy to demand that users log in using https://nto.my.salesforce.com.
A purposeful set of rules designed to direct behavior and produce logical results is called a policy. A policy is a declaration of intent that is carried out through a method or protocol. Typically, a governance board inside a company adopts policies. Both subjective and objective decision-making can benefit from policies. Policies used in subjective decision-making typically aid senior management with choices that must be based on the relative merits of a variety of aspects, and as a result, are frequently challenging to assess objectively. An example of a policy used in this manner is the work-life balance policy. In addition, governments and other institutions have policies in the form of laws, rules, guidelines, administrative procedures, rewards, and voluntary practices. Resources are frequently distributed in accordance with policy choices.
Here you can learn more about policy in the link brainly.com/question/28024313
#SPJ4
Which type of cell references are automatically updated when copied?.
Answers
Answer:
By default, all cells are Relative Cell References within a formula and will update when copied or use of Autofill.
Explanation:
By default, all cells are Relative Cell References within a formula and will update when copied or use of Autofill.
Which of the following statements regarding nonqualified stock options (NQOs) is false?
A) If the value of the options that accrue is greater than the bargain element of options exercised, the book-tax difference for that year is unfavorable.
B) All stock option-related book-tax differences are temporary.
C) No expense recognition is required for NQOs for financial accounting purposes.
D) Book-tax differences associated with NQOs may be either permanent or temporary.
Answers
In fact, expense recognition is required for NQOs( nonqualified stock options) for financial accounting purposes under Generally Accepted Accounting Principles (GAAP).The false statement regarding nonqualified stock options (NQOs) is option C, "No expense recognition is required for NQOs for financial accounting purposes."
When an employee is granted NQOs, the company records an expense equal to the fair value of the options on the grant date. This expense is then recognized over the vesting period of the options as compensation expense. The expense recognition for NQOs follows the same principles as for other forms of equity compensation, such as restricted stock units (RSUs).
The other statements regarding NQOs are true. Statement A is true because the book-tax difference for NQOs can be unfavorable in the year of exercise if the value of the options that accrue is greater than the bargain element (the difference between the exercise price and the fair market value of the stock on the exercise date).
Statement B is true because all stock option-related book-tax differences are temporary due to the nature of the tax treatment of stock options. Statement D is true because the book-tax differences associated with NQOs can be either permanent (if the options expire unexercised) or temporary (if the options are exercised).
To know more about nonqualified stock options visit:
https://brainly.com/question/28538067
#SPJ11
Which statement is true about input and output devices? A. An input device receives information from the computer and an output device sends information to the computer. B. An output device receives information from the computer and an input device sends information to the computer. C. Neither statement is true. D. Both statements are true
Answers
Answer:
B. An output device receives information from the computer and an input device sends information to the computer.
Explanation:
Output device: The term "output device" is described as a device that is responsible for providing data in multitude forms, a few of them includes hard copy, visual, and audio media. The output devices are generally used for projection, physical reproduction, and display etc.
Example: Printer and Monitor.
Input device: The term "input device" is determined as a device that an individual can connect with the computer in order to send some information inside the computer.
In the question above, the correct answer is option-B.
Which types of computer hardware are internal?
Answers
Answer:
Here are some :) (sorry if there are too many)
Explanation:
RAM (Random Access Memory): It's a fast-access memory that is cleared when the computer is powered-down. RAM attaches directly to the motherboard, and is used to store programs that are currently running.
Video Card/GPU (Graphics Processing Unit): It's a specialized processor originally designed to accelerate graphics rendering.
Sound Card: USB sound "cards" are external devices that plug into the computer via USB.
Storage: SSD (Solid State Drive): It is a data storage device that uses solid-state memory to store persistent data.
HDD (Hard Disk Drive): It is a non-volatile storage device which stores digitally encoded data on rapidly rotating platters with magnetic surfaces. Just about every new computer comes with a hard disk these days unless it comes with a new solid-state drive.
CPU (Central Processing Unit/ sometimes just called a processor) It's a machine that can execute computer programs, and sometimes called the brain of the computer.
Motherboard: The motherboard is the body or mainframe of the computer, through which all other components interface. It is the central circuit board making up a complex electronic system.
Firmware: Firmware is loaded from the Read only memory (ROM) run from the Basic Input-Output System (BIOS). It is a computer program that is embedded in a hardware device, for example a microcontroller.
Power Supply: The power supply as its name might suggest is the device that supplies power to all the components in the computer.
CD-ROM Drive: There are two types of devices in a computer that use CDs: CD-ROM drive and a CD writer. The CD-ROM drive used for reading a CD. The CD writer drive can read and write a CD.
Floppy Disk: A floppy disk is a type of data storage that is composed of a disk of thin, flexible(“floppy”) magnetic storage medium encased in a square or rectangular plastic shell.
Internal Storage: Internal storage is hardware that keeps data inside the computer for later use and remains persistent even when the computer has no power.
Disk Array Controller: A disk array controller is a device which manage the physical disk drives and presents them to the computer as logical units.
On some computers the speakers are internal as well. :)
Need help Fast
Question #3
Multiple Choice
What is the missing line of code?
>>> answer = "happy birthday"
"Happy birthday
o answer uppert)
O capitalize answer)
o answer capitalize()
O upper answer
Answers
Answer: answer.capitalize()
Explanation: this is the correction