Which elements of photography does the Iso rating apply
Answers
Answer:its sensitivity to light if it has a lower iso it probably would need more alumination or a longer shuter speed.
Explanation:
Answer:
the film or the sensor
Explanation:
Related Questions
What would game programmers do when decomposing a task in a modular program?
Answers
1. Identify the overall task or feature: Game programmers start by identifying the larger task or feature they want to implement, such as player movement, enemy AI, or collision detection.
2. Analyze the task: They analyze the task to understand its requirements, inputs, and desired outputs. This helps them determine the necessary functionality and behavior.
3. Identify subtasks or components: They identify the subtasks or components that make up the larger task. For example, in the case of player movement, this could involve input handling, character animation, physics simulation, and rendering.
4. Break down the subtasks further: Each subtask can be further decomposed into smaller, more specific functions or modules. For example, input handling might involve separate functions for keyboard input, mouse input, or touch input.
5. Define interfaces: They define clear interfaces between the modules, specifying how they interact and communicate with each other. This helps ensure modularity and maintainability of the code.
6. Implement and test modules: Game programmers then proceed to implement each module or function, focusing on their specific responsibilities. They can test and iterate on these smaller units of functionality independently.
7. Integrate and test the modules: Finally, they integrate the modules together, ensuring they work harmoniously and produce the desired outcome. Thorough testing is conducted to verify that the overall task or feature functions correctly.
By decomposing tasks in this manner, game programmers can effectively manage the complexity of game development, promote code reusability, enhance collaboration, and facilitate the maintenance and future expansion of the game.
When decomposing a task in a modular program, game programmers follow a structured approach to break down the task into smaller, more manageable components.
This process is crucial for code organization, maintainability, and reusability. Here's an outline of what game programmers typically do:
1. Identify the task: The programmer begins by understanding the task at hand, whether it's implementing a specific game feature, optimizing performance, or fixing a bug.
2. Break it down: The task is broken down into smaller subtasks or functions that can be handled independently. Each subtask focuses on a specific aspect of the overall goal.
3. Determine dependencies: The programmer analyzes the dependencies between different subtasks and identifies any order or logical flow required.
4. Design modules: Modules are created for each subtask, encapsulating related code and functionality. These modules should have well-defined interfaces and be independent of each other to ensure reusability.
5. Implement and test: The programmer then implements the modules by writing the necessary code and tests their functionality to ensure they work correctly.
6. Integrate modules: Once individual modules are tested and verified, they are integrated into the larger game program, ensuring that they work together seamlessly.
By decomposing tasks into modules, game programmers promote code organization, readability, and ease of maintenance. It also enables parallel development by allowing different team members to work on separate modules simultaneously, fostering efficient collaboration.
For more such questions on programmers,click on
https://brainly.com/question/30130277
#SPJ8
Which of the following is the MOST important reason for creating separate users / identities in a cloud environment?
Answers
Answer:
Because you can associate with other
Answer:
Explanation:
To avoid cyberbully
You have been given an encrypted copy of the Final exam study guide here, but how do you decrypt and read it???
Along with the encrypted copy, some mysterious person has also given you the following documents:
helloworld.txt -- Maybe this file decrypts to say "Hello world!". Hmmm.
hints.txt -- Seems important.
In a file called pa11.py write a method called decode(inputfile,outputfile). Decode should take two parameters - both of which are strings. The first should be the name of an encoded file (either helloworld.txt or superdupertopsecretstudyguide.txt or yet another file that I might use to test your code). The second should be the name of a file that you will use as an output file. For example:
decode("superDuperTopSecretStudyGuide.txt" , "translatedguide.txt")
Your method should read in the contents of the inputfile and, using the scheme described in the hints.txt file above, decode the hidden message, writing to the outputfile as it goes (or all at once when it is done depending on what you decide to use).
Hint: The penny math lecture is here.
Another hint: Don't forget about while loops...
Answers
Answer:
Explanation:
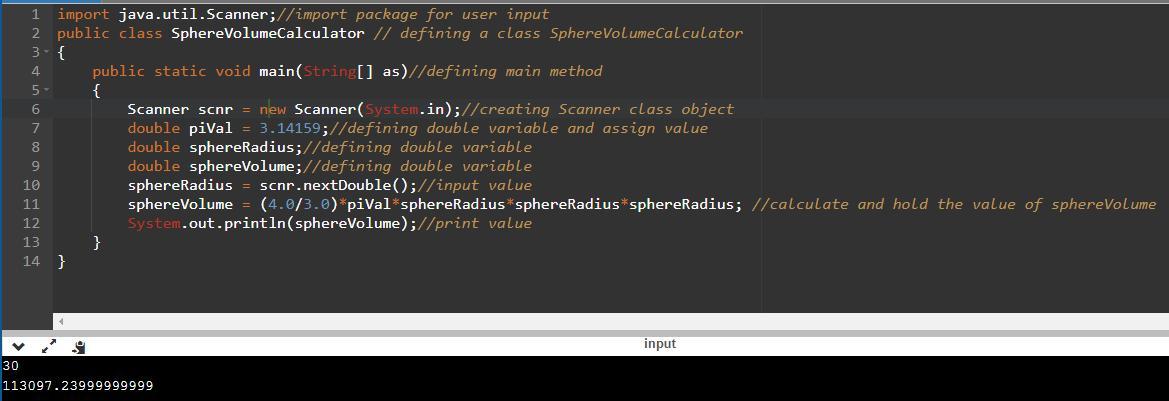
Given sphereRadius and piVal, compute the volume of a sphere and assign sphereVolume with the result. Use (4.0 / 3.0) to perform floating-point division, instead of (4 / 3) which performs integer division.
Volume of sphere = (4.0 / 3.0) Ï r3 (Hint: r3 can be computed using *)
import java.util.Scanner;
public class SphereVolumeCalculator {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
double piVal = 3.14159;
double sphereVolume;
double sphereRadius;
sphereRadius = scnr.nextDouble();
*insert code*
System.out.println(sphereVolume);
}
}
Answers
Answer:
The code to this question can be defined as follows:
sphereVolume = (4.0/3.0)*piVal*sphereRadius*sphereRadius*sphereRadius; // defining a double variable sphereVolume that calculate and hold its value
Explanation:
Please find the complete code in the attachment file.
In the code, a class "SphereVolumeCalculator" is declared, and inside the main method Three double variable "piVal, sphereRadius, and sphereVolume" , in which "piVal" is used to hold a value, in the next step scanner class object is created for holding the "shereRadius" value and the sphereVolume is used for calculate and print its value.
In an ancient land, the beautiful princess Eve (or handsome prince Val) had many suitors. Being royalty, it was decided that a special process must be used to determine which suitor would win the hand of the prince/princess. First, all of the suitors would be lined up one after the other and assigned numbers. The first suitor would be number 1, the second number 2, and so on up to the last suitor, number n. Starting at 4 the suitor in the first position, she/he would then count three suitors down the line (because of the three letters in his/her name) and that suitor would be eliminated and removed from the line. The prince/princess would then continue, counting three more suitors, and eliminate every third suitor. When the end of the line is reached, counting would continue from the beginning. For example, if there were 6 suitors, the elimination process would proceed as follows:_____.
12456 Suitor 3 eliminated; continue counting from 4.
1245 Suitor 6 eliminated; continue counting from 1.
125 Suitor 4 eliminated; continue counting from 5.
15 Suitor 2 eliminated; continue counting from 5.
1 Suitor 5 eliminated; 1 is the lucky winner.
Write a program that creates a circular linked list of nodes to determine which position you should stand in to marry the princess if there are n suitors. Your program should simulate the elimination process by deleting the node that corresponds to the suitor that is eliminated for each step in the process.
Answers
Explanation:
public class CircularLinkedListTest
{
private Node head;
private int size;
private class Node
{
private int num;
private Node next;
public Node(int n)
{
num = n;
next = null;
}
public int getNum()
{
return num;
}
public void setNext(Node n)
{
this.next = n;
}
public Node getNext()
{
return next;
}
}
public CircularLinkedListTest ()
{
head = null;
int numNodes = 0;
}
public void add(int num)
{
int numNodes = 0;
if(head == null)
{
head = new Node(num);
head.setNext(head);
numNodes++;
}
else
{
Node temp = head;
while(temp.getNext() != head)
temp = temp.getNext();
temp.setNext(new Node(num));
temp.getNext().setNext(head);
numNodes++;
}
}
public int size()
{
int numNodes = 0;
return numNodes;
}
public int get(int index)
{
Node t = head;
for(int i = 0; i < index; i++)
t= t.getNext();
return t.getNum();
}
public int remove(int index)
{
if(index < 0 || index >= size)
{
System.out.println("Error, index out of Qbounds.");
System.exit(0);
}
Node temp = head;
if(index == 0)
{
while(temp.getNext() != head)
temp = temp.getNext();
int value = head.getNum();
if(size > 1)
{
head = head.getNext();
temp.setNext(head);
}
else
head = null;
size--;
return value;
}
else
{
for(int i = 0; i < index - 1; i++)
temp = temp.getNext();
int answer = temp.getNext().getNum();
temp.setNext(temp.getNext().getNext());
size--;
return answer;
}
}
public static void main(String args[])
{
CircularLinkedListTest suitors = new CircularLinkedListTest ();
for(int i = 1; i <= 6; i++)
suitors.add(i);
int currentIndex = 0;
while(suitors.size() != 1)
{
for(int i = 1; i <= 2; i++)
{
currentIndex++;
if(currentIndex == suitors.size())
currentIndex = 0;
}
suitors.remove(currentIndex);
if(currentIndex == suitors.size())
currentIndex = 0;
for(int i = 0; i < suitors.size(); i++)
System.out.print(suitors.get(i) + " ");
System.out.println();
}
}
}
What type of file is MyFile.xlsx? data file batch file executable file helper file
Answers
Answer:
executable file. c. 3.
Explanation:
Write a program that asks the user to enter a city name, and then prints Oh! CITY is a cool spot. Your program should repeat these steps until the user inputs Nope.
Sample Run
Please enter a city name: (Nope to end) San Antonio
Oh! San Antonio is a cool spot.
Please enter a city name: (Nope to end) Los Angeles
Oh! Los Angeles is a cool spot.
Please enter a city name: (Nope to end) Portland
Oh! Portland is a cool spot.
Please enter a city name: (Nope to end) Miami
Oh! Miami is a cool spot.
Please enter a city name: (Nope to end) Nope
Answers
A program is a noun that refers to a collection of instructions that process input, manipulate data, and produce a result. It is also referred to as an application or software.As an illustration, the word processing tool Microsoft Word enables users to generate and write documents.
What is write a program in a computer?
enter user name
If you want to stop the software, type Nope or input a name.
if user name!= "Nope," then
"Nice to meet you," user name, print
enter user name
If you want to stop the software, type Nope or input a name.
The user name variable contains the name that is obtained from the user as an input.Till user name does not match the value of Nope, continue the while loop.Display the user's name and keep asking the same question inside the while loop until the user responds with Nope.
To learn more about program refer
https://brainly.com/question/15637611
#SPJ1
Design a kernel module that creates a proc file named /proc/seconds that reports the number of elapsed seconds since the kernel module was loaded. This will involve using the value of jiffies as well as the HZ rate. When a user enters the command
cat /proc/seconds
your kernel module will report the number of seconds that have elapsed since the kernel module was first loaded. Be sure to remove /proc/seconds when the module is removed.
Answers
The kernel module that creates a proc file named /proc/seconds that reports the number of elapsed seconds since the kernel module was loaded is in the explanation part.
What is kernel module?Kernel modules are chunks of code that can be loaded and unloaded from the kernel as needed. They enhance the functionality of the kernel without requiring a system reboot. A module can be set to be built-in or loadable.
Here is an example kernel module that creates a proc file named /proc/seconds that reports the number of elapsed seconds since the kernel module was loaded:
#include <linux/module.h>
#include <linux/kernel.h>
#include <linux/proc_fs.h>
#include <linux/jiffies.h>
#include <asm/uaccess.h>
#define PROC_NAME "seconds"
static struct proc_dir_entry *proc_entry;
static unsigned long start_time;
static int proc_read(char *page, char **start, off_t off,
int count, int *eof, void *data)
{
int len;
unsigned long elapsed_seconds = (jiffies - start_time) / HZ;
if (off > 0) {
*eof = 1;
return 0;
}
len = sprintf(page, "%lu\n", elapsed_seconds);
return len;
}
static int __init seconds_init(void)
{
proc_entry = create_proc_entry(PROC_NAME, 0, NULL);
if (proc_entry == NULL) {
printk(KERN_INFO "Failed to create proc entry\n");
return -ENOMEM;
}
start_time = jiffies;
proc_entry->read_proc = proc_read;
proc_entry->mode = S_IFREG | S_IRUGO;
proc_entry->uid = 0;
proc_entry->gid = 0;
proc_entry->size = 0;
printk(KERN_INFO "/proc/%s created\n", PROC_NAME);
return 0;
}
static void __exit seconds_exit(void)
{
remove_proc_entry(PROC_NAME, NULL);
printk(KERN_INFO "/proc/%s removed\n", PROC_NAME);
}
module_init(seconds_init);
module_exit(seconds_exit);
MODULE_LICENSE("GPL");
MODULE_DESCRIPTION("Seconds kernel module");
Thus, in this module, we first define the name of the proc file to be created (#define PROC_NAME "seconds").
For more details regarding kernel module, visit:
https://brainly.com/question/13441311
#SPJ1
i need the solution to this task please anyone
Answers
Answer:
.
Explanation:
list different power options of computer
Answers
Answer:
1. System Standby
2. System Hibernation
3. System shutdown
4. System restart
define a function that will return the length of a list
Answers
Answer:
len()function:
Explanation:
that's for python btw
i also know java if you want a java version
what type of collection is used in the assignment statement
info: [3:10,4:23,7:10,11:31]
tuple
list
Duque
dictionary
Answers
Answer:
The correct answer to this question is given below in the explanation section.
Explanation:
There are four data types in Python used to store data such as tuple, list, set, and dictionary.
The correct answer to this question is option D: Dictionary
Dictionary data type is used to store data values in key:value pairs as given in the question. It is a collection that is changeable, unordered, and does not allow duplicate entries.
Dictionaries in Python are written with curly brackets and have keys and values such as car={name="honda", model=2010}
when you run the given assignment statment such
info= {3:10,4:23,7:10,11:31}
print(info)
It will print the info dictionary (key:value pair)
{3: 10, 4: 23, 7: 10, 11: 31}
While other options are not correct because:
Tuples in Python are used to store multiple items in a single variable. For example:
info=("apple", "banana", "cherry")
List is used to store multiple items in a single variable. for example
myList = ["apple", "banana", "cherry"]
print(myList)
The list is ordered, changeable, and allows duplicate entry. But you can not put key: value pair in the list.
Deque is a double-ended queue that has the feature to add or remove an element on it either side.
Answer:
Dictionary is the answer
TRUE or FALSE: HTML is used to style web pages.
Answers
Answer:
TRUE
Explanation:
The Clean Air Act Amendments of 1990 prohibit service-related releases of all ____________. A) GasB) OzoneC) MercuryD) Refrigerants
Answers
Answer:
D. Refrigerants
Explanation:
In the United States of America, the agency which was established by US Congress and saddled with the responsibility of overseeing all aspects of pollution, environmental clean up, pesticide use, contamination, and hazardous waste spills is the Environmental Protection Agency (EPA). Also, EPA research solutions, policy development, and enforcement of regulations through the resource Conservation and Recovery Act .
The Clean Air Act Amendments of 1990 prohibit service-related releases of all refrigerants such as R-12 and R-134a. This ban became effective on the 1st of January, 1993.
Refrigerants refers to any chemical substance that undergoes a phase change (liquid and gas) so as to enable the cooling and freezing of materials. They are typically used in air conditioners, refrigerators, water dispensers, etc.
Answer:
D
Explanation:
Find out about the different technological solutions available for interconnecting LANs to from larger networks such as wide area networks (WANS) and Metropolitan area networks. Consider the solutions for wired and wireless networks separately.
Answers
The different technological solutions available for interconnecting LANs to from larger networks are:
Ethernet Wi-FiWhat technology is used by wide area network?The use of WAN Connections and Technology is known to be often used in wide areas or places.
Note that Wired WANs makes use of broadband internet services and also the use of multiprotocol label switching (MPLS) in traffic flow control and network speed up process.
Note also the use of wireless WANs such as 4G/5G and Long-Term Evolution (LTE) networks can help interconnecting LANs to from larger networks.
Learn more about LANs from
https://brainly.com/question/8118353
#SPJ1
Help meeeee - Improved Pet App
Try out the improved version of the pet app that gives the user information about pet stores close by, which uses new sources of input. Determine the information that the app gets from each source of input.
User
Phone Sensors
Internet
Answers
Answer:
Did you do it? Can you give me the answers please♀️
Explanation:
Pleaseeeeeeeeeeeeeeeeeeeeeeeeeeeee
Although you always wanted to be an artist, you ended up being an expert on databases because you love to cook data and you somehow confused database with data baste. Your old love is still there, however, so you set up a database company, ArtBase, that builds a product for art galleries. The core of this product is a database with a schema that captures all the information that galleries need to maintain. Galleries keep information about artists, their names (which are unique), birthplaces, age, and style of art. For each piece of artwork, the artist, the year it was made, its unique title, its type of art (e.g., painting, lithograph, sculpture, photograph), and its price must be stored. Pieces of artwork are also classified into groups of various kinds, for example, portraits, still lifes, works by Picasso, or works of the 19th century; a given piece may belong to more than one group. Each group is identified by a name (like those just given) that describes the group. Finally, galleries keep information about customers. For each customer, galleries keep that person's unique name, address, total amount of dollars spent in the gallery (very important!), and the artists and groups of art that the customer tends to like. Draw the ER diagram for the database. Exercise 3.18 Write SQL statements to create the corresponding relations to the ER dia- gram you designed for Exercise 2.8. If your translation cannot capture any constraints in the ER diagram, explain why.
Answers
Artists, with names (which are distinctive), locations of birth, ages, and art forms. "For each work of art, who created it, what year it was created, what is its special title, and what kind of art is it? and its cost must be kept in storage.
What does a SQL ER diagram mean?A visual representation of a table's structure and the connections among logically related tables is an entity-relationship (ER) model. The data model is visualised in ER modelling using an ER diagram (ERD). A better grasp of the entire database structure is provided by an ER diagram.
Why do we draw ER diagram?To illustrate the content of a data store, ERD diagrams are frequently used in combination with a flow chart. They are very helpful when building a relational database since they enable us to broadly visualise how data is connected.
To know more about ER diagram visit:
https://brainly.com/question/29898277
#SPJ4
Can anyone give me the answers to CMU CS Academy Unit 2.4? Any of the practice problems such as Puffer Fish or Alien Eye will do. I’ve already done drum set, animal tracks, and the spiderman mask one. Thanks!
Answers
Unfortunately, it is not possible to provide the answers to the practice problems for CMU CS Academy Unit 2.4 as these are meant to be solved by the students themselves.
What is CMU CS Academy?CMU CS Academy is an online, interactive, and self-paced computer science curriculum developed by Carnegie Mellon University (CMU). It is designed to give students the opportunity to learn computer science fundamentals in a fun and engaging way. With its interactive and self-paced structure, students can learn at their own pace and engage with the materials in an engaging, dynamic way. The curriculum covers topics such as problem solving, programming, algorithms, data structures, computer architecture, and more. With its intuitive and interactive design, students can learn and apply the concepts learned in a step-by-step manner. CMU CS Academy also provides tools and resources to help students on their learning journey, such as online quizzes, tutorials, and project-based learning.
To learn more about Carnegie Mellon University
https://brainly.com/question/15577152
#SPJ9
1.Create a function that accepts any number of numerical (int and
float) variables as positional arguments and returns the sum ofthose variables.
2.Modify the above function to accept a keyword argument
'multiplier'. Modify the function to return an additional variable
that is the product of the sum and the multiplier.
3.Modify the above function to accept an additional keyword
argument 'divisor'. Modify the function to return an additional
variable that is the quotient of the sum and the divisor.
Answers
Answer:
This function accepts any number of numerical variables as positional arguments and returns their sum:
python
Copy code
def sum_numbers(*args):
return sum(args)
This function accepts a multiplier keyword argument and returns the product of the sum and the multiplier:
python
Copy code
def sum_numbers(*args, multiplier=1):
total_sum = sum(args)
return total_sum * multiplier
This function accepts an additional divisor keyword argument and returns the quotient of the sum and the divisor:
python
Copy code
def sum_numbers(*args, multiplier=1, divisor=1):
total_sum = sum(args)
return total_sum * multiplier, total_sum / divisor
You can call these functions with any number of numerical arguments and specify the multiplier and divisor keyword arguments as needed. Here are some examples:
python
# Example 1
print(sum_numbers(1, 2, 3)) # Output: 6
# Example 2
print(sum_numbers(1, 2, 3, multiplier=2)) # Output: 12
# Example 3
print(sum_numbers(1, 2, 3, multiplier=2, divisor=4)) # Output: (8, 3.0)
Which of the following operating systems would allow a user to add functionality and sell or give away their versions?
Answers
Answer:open source
Explanation: what is's called
Linux is the operating systems would allow a user to add functionality and sell or give away their versions.
What is Linux Operating system?Linux has been defined as known to be a kind of an an Operating system which is known to be an open-source. It is one that is compared to Unix-like form of operating system but it is one that is often based on the the use of Linux kernel.
It has been said that to be an operating system kernel that was said to be released in 1991, by Linus Torvalds. Linux is said to be one that is often packaged as a service of a Linux distribution.
Linux has been used in a lot of ways such as the Server OS that is made for web servers, database servers, as well as file servers. They are known to be set up to aid high-volume as well as multithreading applications and also used for a lot of server types.
Therefore, Linux is the operating systems would allow a user to add functionality and sell or give away their versions. Hence, option A is correct.
Learn more about Linux on:
brainly.com/question/12853667
#SPJ2
Which of the following operating systems would allow a user to add functionality and sell or give away their versions?
-Linux
-macOS
-Windows
-UNIX
asumme the input amalog voltage is changing between -5 to 5V;using a10bit A/D cconverter.calculate the number of quantization levels.calculate the voltage resolution
Answers
Answer:
0.0098 V or 9.8 mV.
Explanation:
A 10-bit ADC can convert an analog input voltage into one of 1024 discrete values. The formulas to find the number of discrete values and the voltage resolution are:
- Number of discrete values = 2^n, where n is the bit depth of the ADC. For a 10-bit ADC, n = 10, so the number of discrete values is 2^10 = 1024.
- Voltage resolution = (Vmax - Vmin) / (Number of discrete values - 1), where Vmax and Vmin are the highest and lowest voltages of the analog input. For an analog input range of -5V to 5V, Vmax = 5V and Vmin = -5V, so the voltage resolution is (5 - (-5)) / (1024 - 1) = 0.0098 V or 9.8 mV.
Order the steps to successfully create a data table.
Answer: Write the formula used to create table values
Select the range
Select the Data tab and What-If Analysis
Select Data Table
Select the values for row/column input.
Answers
Here are the steps to successfully create a data table:
Select the range.Select the Data tab and What-If Analysis.Select Data Table.Write the formula used to create table values.Select the values for row/column input.How to create the data tableFor achieving the desired outcome of generating a data table, it is suggested to adhere to the following measures:
Choose the cells group in which you intend to generate the data table. Include both the cells for input and presentation of results in the specified range.
Provide the equation that you intend to apply for computing the figures enlisted in the data chart. This equation must refer to the designated cells and yield the intended outcome.
Access the What-If Analysis feature by navigating to the Data tab within your spreadsheet program. To access the menu, simply click on it.
Choose the Data Table option from the What-If Analysis menu. This action will trigger the appearance of a dialog box or prompt that will require you to input the required details.
Determine the desired input values for either the row or the column in the data table dialogue box. The table's outcomes will be computed based on these values.
By adhering to these guidelines, you can produce a chart of data that exhibits computed figures derived from various input situations, aiding you in scrutinizing and comprehending the ramifications of different factors on your data.
Read more about data tables here:
https://brainly.com/question/32534586
#SPJ1
What exactly is github?
Answers
Explanation:
Hope it helps you!!electronic age,what format/equipment people use to communicate with each other?
Answers
Answer:
They share or broadcast information by making a letter or information in a papyrus material. in industrial age they use Telegraph or typewriter to communicate each other.
In electronic age, people use electronic medium for communication, like emails and messegers.
write c program that ask user for a two-digit number, then prints the english word for the number using if statements
Answers
Create a C program that requests a two-digit user input. Enter a two-digit number: 11, You have entered: eleven.
C is a general-purpose computer programming language that can be used for system management, network programming, and embedded applications. It is recommended for certain applications because of a variety of qualities, such as: Because C programs have an easy-to-understand syntax, debugging code is easier and faster. Since it was created in 1972, the C programming language has been a vital part of our software-filled world and continues to rule. Most programmers start off with the general-purpose language C before on to ones that are more complicated. A number of the most popular software today were created with C, including Windows, Unix, Photoshop, Tic Tac Toe, and many others. Because: Learning is simple a concise syntax with just 32 keywords
#include <stdio.h>
int main(void)
{
int first_digit, second_digit;
printf("Enter two digits: ");
scanf("%1d%1d",&first_digit,&second_digit);
if (first_digit == 1) {
switch(second_digit % 10) {
case 0: printf(" ten"); break;
case 1: printf(" eleven"); break;
case 2: printf(" twelve"); break;
case 3: printf(" thirteen"); break;
case 4: printf(" fourteen"); break;
case 5: printf(" fifteen"); break;
case 6: printf(" sixteen"); break;
case 7: printf(" seventeen"); break;
case 8: printf(" eighteen"); break;
case 9: printf(" ninteen"); break;
}
return 0;
}
switch(first_digit % 10) {
case 1: printf("ten"); break;
case 2: printf("twenty"); break;
case 3: printf("thirty"); break;
case 4: printf("forty"); break;
case 5: printf("fifty"); break;
case 6: printf("sixty"); break;
case 7: printf("seventy"); break;
case 8: printf("eighty"); break;
case 9: printf("ninety"); break;
}
switch(second_digit % 10) {
case 0: break;
case 1: printf(" one"); break;
case 2: printf(" two"); break;
case 3: printf(" three"); break;
case 4: printf(" four"); break;
case 5: printf(" five"); break;
case 6: printf(" six"); break;
case 7: printf(" seven"); break;
case 8: printf(" eight"); break;
case 9: printf(" nine"); break;
}
return 0;
}
Learn more about tablet here
https://brainly.com/question/15683939
#SPJ4
Which are the top 10 Popular Cars and Video Games get max ammount of point that we can give
Answers
Ferrari F50. ...
Ferrari F40. ...
Ford E-Series Ambulance. ...
Toyota HiLux. ...
Toyota Supra Mark IV. ...
Ferrari Enzo. ...
Chevrolet Step Van. ...
Ford Crown Victoria.
Which of the following is true of a procedure? Check all that apply. It can be reused. It saves programmers time. It is a block of code that performs a single task. It lets you exit a function. DONE
Answers
Answer:
Its 1,2,3
Explanation:
You are working with a database table that contains invoice data. The table includes columns for billing state, billing_country, and total. You want to know the average total price for the invoices billed to the state of Wisconsin. You decide to use the AVG function to find the average total, and use the AS command to store the result in a new column called average_total. Add a statement to your SQL query that calculates the average total and stores it in a new column as average_total. NOTE: The three dots (...) indicate where to add the statement. 1 2 SELECT billing state, billing_country, 3 4 5 6 FROM invoice WHERE billing_state 7 Run 8 "WI" Reset What is the average total for Wisconsin?
Answers
Using the as command, you decide to create a new column called average total and use the avg function to determine the average total.
Fourth is the average of the invoice totals for each vendor, represented as VendorAvg, followed by the sum of the invoice totals for each vendor, represented as VendorTotal, VendorCount, and VendorCount. We use VendorID in the query since the result set needs to contain each vendor's unique invoices. You are utilizing a database table that holds information about invoices. The table has columns for total, billing state, and billing country. You're interested in learning the average total cost of the bills paid.
Learn more about command here-
https://brainly.com/question/3632568
#SPJ4
What are the reasons for breaking up a long data transmission into a number of frames?
Answers
Answer:
Buffer size may be limited.
Which one is not found in edit manu?
a. Prin b. Find
с . copy d. Replace
Answers
which software are you talking about?