Which command can be used to print columns or fields that you specify from a file to the standard output using the tab character as a delimiter
Answers
The command that can be used to print columns or fields that you specify from a file to the standard output using the tab character as a delimiter is the `cut` command.
The `cut` command is used to extract sections of text from files. By default, it takes the input from `stdin` and sends the output to `stdout`.It can be used with different options and arguments to extract characters, columns, or fields from a file or a string.
The `-d` option is used to specify the delimiter, and the `-f` option is used to select the fields or columns to print.
For example, the following command can be used to print the second and the third columns of a file, where the columns are separated by tabs:`cut -f 2,3 -d $'\t' filename`Here, `-d $'\t'` specifies the tab character as the delimiter, and `-f 2,3` selects the second and third fields.
Learn more about the commands at:
https://brainly.com/question/32155942
#SPJ11
Related Questions
which of the following is not a common input device?
Answers
The device which provides any piece of information from a computer into human-readable form is known as the Output device.
Explanation:
Someone help pleaseee
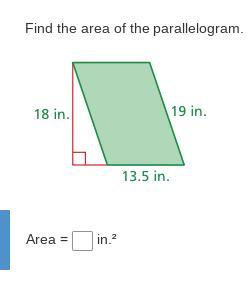
Answers
Answer:
243in^2
Explanation:
Area= base x height
base=13.5
height=18
A= 13.5 x 18
A=243in^2
hope this helps :)
Which command should you run after installing a new kernel module to update the module dependency database?
Answers
Answer:
depmod
Explanation:
Let's say you are the Robot (Give yourself a name) you are talking to the customer.
The customer wants to purchase a bicycle.
The customer wants to know the purchase of the 3 bicycles. What's included in the total cost? Taxes 8%
How will the customer be paying? Will this customer needs deliver or they will pickup?
Use your mathematical operators....
Answers
Let the robot's name be Alpha.
Alpha will follow a predetermined algorithm to interact with the customer.
Algorithm -
Alpha: Hello. Please select the model of the bicycle from the list.
Alpha: The selected model's MRP is $x.
Alpha: The MRP will be subject to an additional 8% tax.
Alpha: Total cost of 1 bicycle is MRP+(8% of MRP).
Alpha: Total cost of 3 bicycle is 3*(MRP+(8% of MRP)).
Alpha: Choose a payment option from the list.
Alpha: Choose the delivery option. Pickup or home delivery
What is an Algorithm?
A set of finite rules or instructions to be followed in calculations or other problem-solving operations or A procedure for solving a mathematical problem in a finite number of steps that frequently involves recursive operations.
For example,
An algorithm to add two numbers:
• Take two number inputs
• Add numbers using the + operator
• Display the result
To know more about how Algorithm works, kindly visit: https://brainly.com/question/15802846
#SPJ13
True or False:
QBASIC allows you to break lengthy programs into modules.
Answers
Answer:
True. Qbasic allows two distinct subdivisions of a program, functions and subroutines. The former of which can return a value, and the latter does not.
*Note I haven't used Qbasic in over a quarter of a century, so it may have evolved in time. My experience with it is on MS-DOS.
Which of the following is the BEST reason to use cash for making purchases? everfi
Answers
Answer: knowing what you spend".
Explanation:
The reason to use cash for making purchases is to know how much one has spent.
When we use cash rather than using credit card, it's easier for one to know how much that has been spent. Also, one can easily know when he or she need to stop spending. Therefore, the correct answer is "knowing what you spend".
She wants to use a different level for the uses of the gases.
What can Hope do to change the numbers 2, 3, 5, and 6 to lowercase letters?
Press the Space bar.
Use the Tab key.
Click the Sort option.
Use the Multilevel List icon.
Answers
Answer: d
Explanation: got it right in edge 2020
Answer:
D
Explanation:
Name two sensors which would be used in a burglar alarm system
Answers
1. Passive Infrared Sensor
This sensors type is passive in a way that it doesn't radiate its own energy. Instead, it detects the infrared light radiating from objects. This way, it can detect whenever there's a human or another living being in its field of view.
2. Photoelectric Beams
This is also another type of motion detector, but it doesn't work similarly to the others. For one, it doesn't have a coverage area. It only forms a fence, which triggers the alarm if broken.
It consists of two separate parts that form a sort of a fence made of IR beams. When someone steps into the beams, between the two parts, they trigger the alarm.
HELP ME
what is the full form of BYE,AIDS,ASCC
Answers
CODEHS PLEASE HELP ME(check attached pic)

Answers
Answer:
JavaScript Notation (If it is not JavaScript, Comment on this problem and I will immediately change it.)
var width = prompt("Input width.")
var length = prompt("Input length.")
if (length === width) {
console.log(length*width , " is your area of the square.")
} else {
console.log(2*length*2*width , " is your perimeter of the rectangle.)
calculate the information gain when splitting on a and b. which attribute would the decision tree induction algorithm choose?calculate the gain in the gini index when splitting on a and b. which attribute would the decision tree induction algorithm choose?entropy and the gini index are both monotonously increasing on the range [0, 0.5] and they are both monotonously decreasing on the range [0.5, 1]. is it
Answers
By deducting the gain ratio of the splitting from the index of both the parent node, it is possible to determine the increase in the gain coefficient when dividing on a and b.
What is algorithm?
An algorithm is a set of instructions or steps that are designed to solve a problem or accomplish a task. It is an effective way of performing a task that can be repeated, with the same results each time. Algorithms are commonly used in computer programming and can range from simple to complex. They can be used to solve simple tasks such as sorting a list, to complex tasks such as playing a game of chess. Algorithms are also used in everyday life, such as when a person follows a recipe or drives to a destination. Algorithms help to make tasks easier and more efficient by breaking them down into smaller, manageable steps.
The information gain when splitting on a and b can be calculated by subtracting the entropy or gini index of the split from the entropy or gini index of the parent node. The attribute with the highest information gain would be chosen by the decision tree induction algorithm. The gain in the gini index when splitting on a and b can be calculated by subtracting the gini index of the split from the gini index of the parent node. The attribute with the highest gain in the gini index would be chosen by the decision tree induction algorithm. Yes, entropy and the gini index are both monotonously increasing on the range [0, 0.5] and monotonously decreasing on the range [0.5, 1].
To learn more about algorithm.
https://brainly.com/question/24953880
#SPJ4
In order to avoid slipping in the shop, your footwear should ___________.
Answers
Answer:
Be sticky or not slippery
Explanation:
Intro to Programming in C - Program must be in C
1.
Declare an array of doubles of size 145 called bonusPoints and initialize all the elements in the array to 1.5 (HINT: use a loop)
2.
Declare an integer and an array of doubles called scores The array can hold 145 doubles Ask the user how many scores they want to enter (up to 145) Get the number from the user Fill the array with with user input (HINT: use a loop and prompt for input) For example if the user entered 100 you would write a loop to have the user enter the 100 scores one by one
Answers
C is a procedural programming language that can be used to build software such as operating systems, databases, and others. The explanation below is to declare multiple arrays
To complete the tasks in the student question, you can follow these steps:
1. Declare an array of doubles of size 145 called bonusPoints and initialize all the elements in the array to 1.5:
```c
#include
int main() {
double bonusPoints[145];
for (int i = 0; i < 145; i++) {
bonusPoints[i] = 1.5;
}
return 0;
}
```
2. Declare an integer and an array of doubles called scores. The array can hold 145 doubles. Ask the user how many scores they want to enter (up to 145), get the number from the user, and fill the array with user input:
```c
#include
int main() {
int numOfScores;
double scores[145];
printf("How many scores do you want to enter (up to 145)? ");
scanf("%d", &numOfScores);
for (int i = 0; i < numOfScores; i++) {
printf("Enter score %d: ", i + 1);
scanf("%lf", &scores[i]);
}
return 0;
}
```
Combine both parts to complete the program:
```c
#include
int main() {
double bonusPoints[145];
int numOfScores;
double scores[145];
for (int i = 0; i < 145; i++) {
bonusPoints[i] = 1.5;
}
printf("How many scores do you want to enter (up to 145)? ");
scanf("%d", &numOfScores);
for (int i = 0; i < numOfScores; i++) {
printf("Enter score %d: ", i + 1);
scanf("%lf", &scores[i]);
}
return 0;
}
```
Learn more about programming language: brainly.com/question/16936315
#SPJ11
what new feature in windows server 2016 will allow up to eight identical physical adapters on the host system to be configured as a team and mapped to a virtual switch?
Answers
The new feature in Windows Server 2016 that allows up to eight identical physical adapters on the host system to be configured as a team and mapped to a virtual switch is called NIC Teaming.
NIC stands for Network Interface Card. NIC Teaming allows you to bundle several physical network interfaces together to form a single logical interface that provides fault tolerance and high-speed links.
By configuring multiple physical adapters as a team, you can increase the network bandwidth and provide redundancy in case a network adapter fails.
Learn more about Windows Server:
https://brainly.com/question/30468027
#SPJ11
consider the code for quick sort provided on the previous page. right before the function concat is called, what do we know about the contents of the arrays small and large with respect to what objects (integers) they contain in general and the order of the objects in the arrays?
Answers
An array is a set of items, images, or numbers arranged in rows and columns. Arrays are practical illustrations of multiplication theories (among other ideas in mathematics).
A grouping of comparable types of data is called an array. For instance, we can create an array of the string type that can hold 100 names if we need to record the names of 100 different persons. array of strings = new String[100]; In this case, the aforementioned array is limited to 100 names. Based on their dimensions, arrays can be divided into single-dimensional and multi-dimensional varieties. A two-dimensional array logically represents a mathematical matrix, while a single-dimensional array corresponds to a linear collection of data. A multidimensional array has various dimensions in a similar way.
Learn more about array here-
https://brainly.com/question/13107940
#SPJ4
tractor in reverse brainliest answer
Answers
Answer:
Valtra
Explanation:
It is the only tractor that goes in reverse.
Thank you so much!
Have a good day
Hope this helped,
Kavitha Banarjee
Consider the following code:
C = 100
C = C + 1
C = C + 1
print (c)
What is output?
Answers
Answer:
The output of C is 102.
100 + 1 + 1 = 102
What does data storage enable a browser to do?
O O O O
organize lists of bookmarks
edit open-source software
organize a hard drive
save browsing information
Answers
The data storage enables a browser to save browsing information. The correct option is d.
What is data storage?File backup and recovery are made simple by data storage in the case of an unanticipated computer failure or cyberattack. Physical hard drives, disc drives, USB drives, and virtually on the cloud are all options for data storage.
Data storage makes it possible for a browser to simply enable Web Storage capabilities when an IT administrator has disabled such exciting features. Additionally, you may easily clear any existing "Web Storage" data using the browser's cache.
Any one of them may be utilized, depending on the needs, to save data in the browser. Today's essay will compare local storage, session storage, and cookies in great detail.
Therefore, the correct option is d. save browsing information.
To learn more about data storage, visit here:
https://brainly.com/question/13650923
#SPJ2
4 cups
2 pints
Write the equivalent measure for each amount.
27.
4 quarts
28.
29.
30.
2 cups
31.
16 tablespoons
32.
4 tablespoons
33.
3 teaspoons
34.
16 ounces

Answers
Answer:
The correct equivalent measure of each amount are;
27. 1 gallon ≡ 4 quart
28. 1 quart ≡ 4 cups
29. 1 quart ≡ 2 pints
30. 1 pint ≡ 2 cups
31. 1 cup ≡ 16 tablespoons
32. 2.5 ounces ≡ 4 tablespoons
33. 1 tablespoon ≡ 3 teaspoons
34. 0.8 pint ≡ 16 ounces
Explanation:
In the imperial units of volume, we have the following equivalent volumes;
27. 1 imperial gallon is equivalent to 4 imperial quart
28. 1 imperial quart is equivalent to 4 imperial cups
29. 1 imperial quart is equivalent to 2 imperial pints
30. 1 imperial pint is equivalent to 2 imperial cups
31. 1 imperial cup is equivalent to 16 imperial tablespoons
32. 2.5 imperial ounces is equivalent to 4 imperial tablespoons
33. 1 imperial tablespoon is equivalent to 3 imperial teaspoons
34. 0.8 imperial pint is equivalent to 16 imperial ounces
Can you help me with Computer issues graphic organizer?
Will give out brainly

Answers
Third?: put all of the abov
Where does Juan Varlano teach his classes?
a. Oakland and Downtown
b. Oakland only
c. Oakland and Shadyside
d. Shadyside and Downtown
Answers
Professor Juan Varlano teaches his classes in option b. Oakland only.
Juan Varlano is an experienced instructor who teaches classes in Oakland. His classes are designed to help students become more confident, motivated, and productive. Juan has a wealth of knowledge and experience in the areas of communications, media, and public speaking. He is focused on helping his students to develop the skills needed to succeed in their chosen career paths. As such, Juan only teaches classes in Oakland and does not offer classes in Shadyside or Downtown.
Learn more about classes: https://brainly.com/question/16571478
#SPJ11
What is distributed switching in networking?
Answers
Answer:
Distributed switching is an architecture in which multiple processor-controlled switching units are distributed.
Multiple processor-controlled switching units are deployed in an architecture known as distributed switching. There is frequently a hierarchy of switching components, with distant switches placed close to user concentrations and a central host switch.
What is networking?Interconnected computing equipment that may share resources and exchange data are referred to as being in a computer network. To send data across wired or wireless technologies, these networked devices employ a set of guidelines known as communications protocols.Networking is the sharing of knowledge and ideas among those who share a profession or a particular interest, typically in a casual social situation. A single area of agreement serves as the foundation for networking.-Involves establishing connections between various computer networks using various protocols. -Requires that a standard interconnection protocol be developed on top of the local protocols. - By defining distinct addresses for a network and a host machine, the Internet Protocol (IP) fills this function.To learn more about networking, refer to:
https://brainly.com/question/1167985
#SPJ4
In a Simplified Single-cycle Implementation of a Datapath, the main inputs to the Register File are a. 64 bits which are the contents of two registers b. 6 bits which are the opcode of the instruction c. 32 bits which are the machine code of an instruction d. 15 bits which are the numbers of three registers In a simplified single-cycle Datapath, the ALU has as outputs. a. only 32 bits b. 64 bits c. 32+1 bits d. 16 bits Convert the below instruction to machine language. SLT \$t6, \$t5, \$s3 Select one: a. 0×1CD982 A b. 0×01 B3702 A c. OX01AE982A d. None of the options e. 0×01D3682 A
Answers
In a Simplified Single-cycle Implementation of a Datapath:
The main inputs to the Register File are:
a. 64 bits which are the contents of two registers.
In a single-cycle implementation, the Register File typically takes two register identifiers as inputs, each identified by a 5-bit register number. As each register holds 32 bits of data, the total input size to the Register File is 64 bits.
In a simplified single-cycle Datapath:
The ALU has as outputs:
c. 32+1 bits.
The ALU in a simplified single-cycle Datapath typically produces a 32-bit output, representing the result of the arithmetic or logical operation. Additionally, there is usually a 1-bit output representing the Zero flag, indicating whether the result of the operation is zero or not. Hence, the total output size of the ALU is 32+1 bits.
Converting the instruction "SLT $t6, $t5, $s3" to machine language:
The correct answer is:
e. 0×01D3682A.
The instruction "SLT" stands for "Set on Less Than" and is typically used in assembly language. The machine language representation of this instruction is encoded into binary format. The specific binary representation can vary depending on the architecture and instruction encoding scheme. Given the options provided, option e (0×01D3682A) represents the closest match to the machine language representation of the given instruction.
To know more about datapath, visit:
https://brainly.com/question/33562430
#SPJ11
Complete the crossword polynomials by finding the indicated products.
Answers
apologize, but as a text-based AI model, I cannot directly view or interact with specific crossword puzzles or visual content.
If you provide the crossword puzzle clues and the number of letters for each answer, I would be happy to help you find the indicated products or provide assistance with any related questions. I apologize for the confusion, but it seems there was a misunderstanding. If you could provide the crossword puzzle clues and the number of letters for each answer, I would be glad to assist you in finding the indicated products or answering any related questions. However, I would like to clarify that providing a might not be applicable in this context without specific information about the crossword puzzle. Please provide the necessary details, and I'll do my best to help you.
learn more about apologize here :
https://brainly.com/question/31108667
#SPJ11
all the application environments in windows 10 restrict apps to running in which of the following modes?
Answers
All the application environments in Windows 10 restrict apps to running in User Mode.
Windows 10 utilizes a protected mode of operation where applications run in a restricted environment known as User Mode. In User Mode, applications have limited access to system resources and are isolated from each other to ensure stability, and security, and prevent unauthorized access to critical system components. User Mode provides a layer of protection by enforcing user-specific permissions and restrictions on applications. This helps prevent applications from interfering with the operating system or other applications, enhancing overall system security and stability. In contrast, the operating system itself runs in a privileged mode called Kernel Mode, which has direct access to system resources and controls the execution of applications. Kernel Mode is restricted to trusted system processes and is responsible for managing hardware, memory, and other critical functions. By running applications in User Mode and separating them from the Kernel Mode, Windows 10 ensures a secure and controlled execution environment, reducing the risk of system instability or malicious activities impacting the operating system.
learn more about User Mode here:
https://brainly.com/question/31486134
#SPJ11
which protocol can be used to encrypt transmissions like ftp?
Answers
The File Transfer Protocol (FTP) is a standard network protocol used for transferring files between computers. To encrypt FTP transmissions, the Secure File Transfer Protocol (SFTP) protocol can be used.
FTP is a standard network protocol used to transfer files between a client and a server over the Internet or other TCP/IP-based networks, such as LANs or WANs. FTP is built on a client-server architecture and uses separate control and data connections between the client and server.FTP can be used to transfer data of any type, including text and binary files. However, FTP is not secure because it does not encrypt transmissions, making it vulnerable to interception and other security threats.
SFTP stands for Secure File Transfer Protocol. It is a network protocol used for secure file transfers over an SSH (Secure Shell) connection. SFTP is often used as a secure alternative to FTP because it encrypts transmissions, making them resistant to interception and other security threats.SFTP uses a similar command set to FTP, making it easy to use for those who are familiar with FTP. However, unlike FTP, SFTP provides end-to-end encryption, making it more secure for transferring sensitive data.
Learn more about FTP
https://brainly.com/question/14299412
#SPJ11
ftps is the protocol that can be used to encrypt ftp transmissions.
ftp (File Transfer protocol) is a standard network protocol used to transfer files between a client and a server on a computer network. However, FTP does not provide encryption for data transmission, which means that the data being transferred can be intercepted and read by unauthorized individuals.
To secure FTP transmissions and protect the data being transferred, a protocol called ftps (FTP Secure) can be used. FTPS is an extension of FTP that adds support for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. These protocols provide encryption and authentication, ensuring that data is transmitted securely between the client and the server.
FTPS can be used with both explicit and implicit modes. In explicit mode, the client requests encryption from the server and the server responds by initiating a secure connection. In implicit mode, the client assumes that the server requires encryption and immediately establishes a secure connection.
Learn more:
About protocol here:
https://brainly.com/question/28782148
#SPJ11
Jenn wants to assign a value to the favorite sport variable: 4favoriteSport = "soccer" but gets an error message. What does she need to fix for the code to work?
a Create a shorter variable name.
b Remove the equal sign.
c Remove the quotation marks around the string.
d Remove the number from the variable name.
Answers
Answer:
D. Remove the number from the variable
Explanation:
Because in normal coding it would only be favoriteSport = "soccer" not with a 4
Answer: it would be to move the number from the variable name
Explanation:
Because the code dose not understand that you need to say that your favored sport is soccer
Which feature in Print Preview would allow you to rotate your document's placement on the page?
Color
Orientation
Destination
Margins
Answers
The feature in Print Preview that would allow you to rotate your document's placement on the page is Orientation. Option B
What is the orientation feature?The Orientation feature enables you to change the direction in which the content is printed on the page, whether it's portrait (vertical) or landscape (horizontal).
By changing the orientation, you can adjust the page layout to best fit the content, making it easier to read and more visually appealing.
Other features such as margins can also be adjusted in Print Preview to fine-tune the appearance of your document before printing.
Read more about page orientation at: https://brainly.com/question/26089245
#SPJ1
Describe how a cell’s content and format attributes are related.
Answers
Answer: They are independent and not related.
Explanation: Changing the format affects the content. Which of the following is NOT a way to change the column width in Excel?
hope this helps
why do most operating systems let users make changes
Answers
By these changes you most likely are thinking of the term 'Over Clocking'
Over Clocking is used on most Operating Systems to bring the item your over clocking to the max.
Over Clocking; is mostly used for Crypto mining and gaming.