Which combination of options is the keyboard shortcut to access the find dialog box and search a worksheet for particular values? ctrl h ctrl r ctrl f ctrl e
Answers
A hot key is a key or group of keys on a computer keyboard that, when pressed simultaneously, carry out a task (such launching an application) more quickly than a mouse or other input device.
What is the uses of shortcut keys ?The Find and Replace dialog box, which enables you to look for a specific value in your worksheet and replace it with another value, is opened by pressing the keyboard shortcut Ctrl + F. Additionally, formatting can be found and changed with this shortcut.The function keys and keyboard shortcuts in Word for Windows are discussed in this article.
The Find tab appears in place of the Replace tab when using the CTRL+H keyboard shortcut or the Replace button on the ribbon to open the Find and Replace dialog box.Pressing Ctrl + R will refresh (reload) the current web page in all popular Internet browsers, including Chrome, Edge, Firefox, and Opera.To choose the search box, use Ctrl + E.
To learn more about shortcut key refer to :
https://brainly.in/question/135577
#SPJ4
Related Questions
What is Indigenous Technology??
Answers
Indigenous Technologies is a program of the Berkeley Center for New Media that engages questions of technology and new media in relation to global structures of indigeneity, settler-colonialism, and genocide in the 21st century.
Which of the following is NOT a legal variable name?
%information
appointment_hour
O grade3
firstName
Answers
Answer:
a
Explanation:
a
It is the "executable" phrase of Word
Wide Web with dynamic applications,?
Answers
Answer:
It is the “executable” phrase of Word Wide Web with dynamic applications, interactive services, and “machine-to-machine” interaction. In Web 3.0, computers can interpret information like humans and intelligently generate and distribute useful content tailored to the needs of users.
Can you guys help me with this coding assignments?

Answers
Explanation:
x ==50
while x< 100;
x -= 1
The iteration variable begins counting with which number?
O 0
O 1
O 10
O 0 or 1
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The iteration variable begins counting with 0 or 1.
As you know the iteration mostly done in the looping. For example, for loop and foreach loop and while loop, etc.
It depends upon you that from where you can begin the counting. You can begin counting either from zero or from one.
For example: this program counts 0 to 9.
int total=0;
for(int i=0; i>10;i++)
{
total = total+i;
}
Let's suppose, if you want to begin counting from 1, then the loop should look like below:
int total=0;
for(int i=1; i>10;i++)
{
total = total+i;
}
Answer:
I truly believe its 0
hope it helps :)
Explanation:
Mike needs to export some animation videos from his smartphone to an online platform. Which common file format can he use for this purpose?
A..swf
B..flv
C..mov
D..3gp
Answers
Answer:
The correct answer is D. 3gp
Explanation:
Hi Lesiana, After your presentation last week, the manager thinks an in-house solution is the way to go. Although our programmers have much experience with system integration and development, they have little experience with user design. You'll have to lay out all the pages of the system. For now, just create a hierarchical drawing of all the pages needed for this system. Think of the menu on the top of the screen and what you'd click on to move to the next screen.
Once you finish the hierarchy, I'll need you to draw out examples of a few of the screens. For example, show a screen with a menu, another which requests user input, one that has methods to contact us, and the last one as an informational page. The menu screen can be an opening page or even a page to decide on types of reports to run. The user input page can be one for any of the users, such as the appointment setters or technicians. Make sure that you outline all of the required validation rules for this input page. The informational page can either be a static page or results from a search. Make sure that you include navigation buttons on each of these example pages.
Answers
The Hierarchical drawing of the In- House solutions includes Four categories such as product, service, training, support and about.
What is Hierarchical drawing?Hierarchical drawing is also known as Layered Graph Drawing which includes the drawing in the vertices and are made on the Horizontal rows and layers.
The complete solution is attached below.
The In-House solutions' hierarchical diagram covers four categories, including product, service, training, support, and about.
Learn more about Hierarchical drawing here:
https://brainly.com/question/26031625
#SPJ1

Assume a 4KB 2-way set-associative cache with a block size of 16 bytes and physical address of 32 bits.
- How many sets are there in the cache?
- How many bits are used for index, tag, and offset, respectively?
Answers
Thus, there are 128 sets in the cache, and the number of bits used for index, tag, and offset are 7, 21, and 4, respectively.
In a 4KB 2-way set-associative cache with a block size of 16 bytes and a physical address of 32 bits:
1. To calculate the number of sets in the cache, first find the total number of blocks in the cache. The cache size is 4KB, which is equal to 4 * 1024 = 4096 bytes.
Since each block has a size of 16 bytes, the total number of blocks is 4096 / 16 = 256. As it's a 2-way set-associative cache, we divide the total number of blocks by 2, which gives us 256 / 2 = 128 sets in the cache.
2. To determine the number of bits used for index, tag, and offset:
- Offset: Since each block is 16 bytes, we need 4 bits to represent the offset (2^4 = 16).
- Index: As there are 128 sets, we need 7 bits for the index (2^7 = 128).
- Tag: The physical address is 32 bits, and we've already used 4 bits for offset and 7 bits for index, so the remaining bits for the tag are 32 - 4 - 7 = 21 bits.
In summary, there are 128 sets in the cache, and the number of bits used for index, tag, and offset are 7, 21, and 4, respectively.
Know more about the set-associative cache
https://brainly.com/question/23793995
#SPJ11
A network-related or instance-specific error occurred while establishing a connection to sql servera. Trueb. False
Answers
The statement "A network-related or instance-specific error occurred while establishing a connection to SQL Server" is true. SQL Server is a RDBMS developed by Microsoft.
It is a key component in many enterprise applications and is widely used to store and manage large amounts of data. When an application tries to connect to SQL Server, it may encounter an error message that says "A network-related or instance-specific error occurred while establishing a connection to SQL Server." This error message typically indicates that there is a problem with the connection between the application and SQL Server, and that the connection cannot be established.
The reason for the error can be due to various factors, including:
Incorrect configuration of SQL Server: The SQL Server instance may be configured incorrectly, such as specifying an incorrect server name or port number.
Network connectivity issues: The application and SQL Server may be on different network segments, and network connectivity may be lost or there may be a firewall blocking the connection.SQL Server is not running: The SQL Server service may not be running, and the application cannot connect to it.SQL Server is too busy: The SQL Server instance may be experiencing a high workload and may be unable to process the connection request.In conclusion, the error message "A network-related or instance-specific error occurred while establishing a connection to SQL Server" is a common problem that can be encountered when connecting to SQL Server. The root cause of the problem can be due to various factors, such as incorrect configuration, network connectivity issues, SQL Server not running, or SQL Server being too busy. To resolve the issue, you may need to check the configuration, network connectivity, and service status of SQL Server and make the necessary changes to resolve the issue.
To know more about SQL Server: https://brainly.com/question/29417398
#SPJ4
you work as the it administrator for a small corporate network. to accommodate specific network communication needs for an upcoming project, you need to upgrade the network connection's speed for the windows workstation located in the executive office.
Answers
We need to upgrade the network connection's speed for the windows workstation located in the executive office for that we will Install the network interface card and configure the Ethernet cable connection between the computer and the LAN network.
The connecting and communication of computer equipment is the function of the computer networking system. An adapter known as a network interface card allows the computer to connect to a network (NIC). The NIC's operations are managed by the operating system.
The speed and port state of the NIC are configured, and it is linked to the LAN using a straight through cable.
To check for LAN network connectivity on the PC, use the ipconfig/all and netstat commands. Another option is to use the ping command.
Launch Start. To open the console, perform a search for "Command Prompt," then select the top result. To check the connection speeds of all the Ethernet and Wi-Fi adapters, use the command after typing it: where netEnabled=true in wmic nic get name and speed.
Learn more about workstation:
https://brainly.com/question/17121112
#SPJ4
thor is working as a contractor for the department of defense (dod). to better secure their systems, each laptop is equipped with a device that requires all employees to insert their employee identification badges into the computer to log in. each identification badge has an electronic chip embedded into the badge. the employee must enter a pin to unlock the digital certificate stored in this badge to authenticate to the login server. which of the following technologies is used to read the employee's badge? smart card reader barcode scanner adf magnetic reader see all questions back skip question
Answers
The technology that is used to read the employee's badge is the smart card reader.
What is a Smart Card Reader?A smart card reader is a device that communicates with smart cards to read the contents of the card and access its contents. Smart cards are physical cards that are embedded with a microchip and can be used as a security device to authenticate access to systems and facilities.
Therefore, in the given scenario, to secure the systems of the Department of Defense (DoD), each laptop is equipped with a device that requires all employees to insert their employee identification badges into the computer to log in.
Each identification badge has an electronic chip embedded into the badge, and to authenticate the login server, the employee must enter a PIN to unlock the digital certificate stored in this badge. The technology that is used to read the employee's badge is the smart card reader.
Learn more about card reader at
https://brainly.com/question/31012792
#SPJ11
write a python program to initialize the value of two variables then find sum
Answers
Answer:
JavaScript:
Let x = 10
Let y = 10
Console.log(x + y)
//outputs 20
C++:
Let x = 10
Let y = 10
The file is Math.cpp so,
std::cout << "" + y + "" + x
g++ Math.cpp -o Maths
./Maths
//Outputs 20
Answer:
#Ask the user for a number
a = int(input("Enter a number: "))
#Ask the user for a number
b = int(input("Enter a number: "))
#Calculate the sum of a and b
sum = a + b
#print the ouput
print(str(a) + " + " + str(b) + " = " + str(sum))
What is the result when you run the following program?
print(2 + 7)
print("3+1")
9
Ost
3+1
an error statement
O
2 +7
4
9
O A
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
If you run the following program,
print(2 + 7)
print("3+1")
then, you can get the following result respectively against each print statement.
9
3+1
because when you print 2+7 without quotation, it will add the integer digit and print the result of adding 2 and 7.
And, when you run ("3+1") in the double quotation, the program will treat it as a string because of the enclosed double quotation (" ");
create a procedure that takes 2 parameters, a string that you get from a user input and an int. Make the procedure print the string the number of times the int parameter gives and call the procedure???

Answers
Answer:
Here is kind of an example: var greeting1 = "Hello, Jackson, how are you?";
println(greeting1);
var greeting2 = "Hello, Mr. H, how are you?";
println(greeting2);
var greeting3 = "Hello, Stranger, how are you?";
println(greeting3);
Explanation:
This tool lets you insert text anywhere in your document. O Cut О сору O Drag O Paste
Answers
Answer:
Drag or paste (im not 100% sure tho)
Explanation:
How do you fix a class, interface, or enum expected in this code
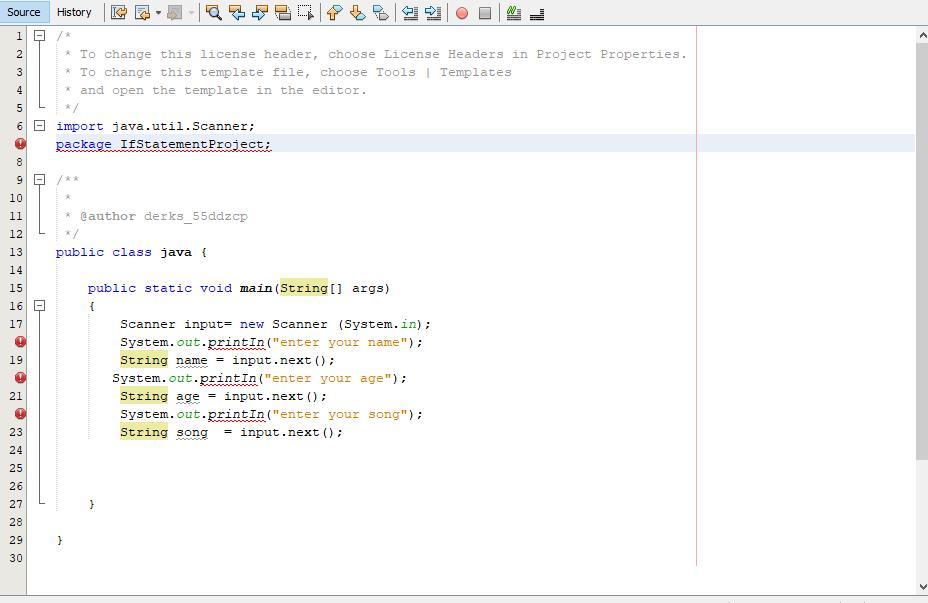
Answers
Answer:
The class interface or enum expected error is a compile-time error in Java which arises due to curly braces. ...Code. ...Here, the error can be corrected by simply removing the extra bracket, or by keeping an eye on the indentation.class Main { ...Case 2 (function outside class)
Explanation:
write a program to loop 1,2,3,4,5,....20th term using for...next statement
Answers
Here's a program that uses the for...next statement to loop through the numbers 1 to 20:
The Python Programfor i in range(1, 21):
print(i)
In this program, the for statement is used to iterate through the range of numbers from 1 to 20 (inclusive). The range function generates a sequence of numbers starting from the first parameter (1) and ending before the second parameter (21). Inside the loop, each number i is printed using the print function.
This program will output the numbers 1 to 20, each on a separate line.
Read more about programs here:
https://brainly.com/question/26497128
#SPJ1
Match the step to the order in which it should be completed to access the backup utility of Windows 7.
first
second
third
:: Open the Control Panel.
:: Click Set up Backup. :: Choose System and Security, Backup and Restore
Answers
The step to order in which it should be completed to access the backup utility of Windows 7 is
1. Open the Control Panel.
2. Choose System and Security.
3. Click on Backup and Restore.
4. Click Set up Backup.
Open the Control Panel: you can click on the "Start" button in the bottom left corner of the screen, then select "Control Panel" from the menu. for opening the Control Panel on Windows 7, select "Control Panel" from the menu.
Choose System and Security: For navigation the System and Security section, which contained settings related to system management, security, and backups.
Click on Backup and Restore: now look for the "Backup and Restore" option and click it. That opens the backup utility in Windows 7.
Click Set up Backup: click on the "Set up Backup" option to start the backup configuration process, This will guide you through the steps to configure your backup preferences and select the backup destination.
Learn more about configuration here:
https://brainly.com/question/32103216
Which of the following individuals is most qualified to become a marketing
entrepreneur?
A. Scott has worked as a public relations manager for two years.
Although he is good at his job, his coworkers report that they do
not enjoy working with him.
B. Mark recently earned a bachelor's degree in marketing. He has
strong computer skills and has a passion for social media
marketing
C. Laura has worked as a market research analyst for 15 years. She
is able to quickly identify which marketing strategies will be most
beneficial to her company.
D. Claire has worked as a marketing manager for a decade. She has
strong leadership skills and is able to maintain confidence even
when things go wrong.
Answers
Answer:
d claire
Explanation:
Laura has worked as a market research analyst for 15 years. She is able to quickly identify which marketing strategies will be most beneficial to her company is a good entrepreneur. The correct option is C.
Who is an entrepreneur?An entrepreneur is a person who creates and manages a business venture while taking financial risks.
Option C - Laura, who has worked as a market research analyst for 15 years and is able to quickly identify which marketing strategies will be most beneficial to her company, appears to be the most qualified to become a marketing entrepreneur based on the information provided.
Her extensive market research experience and ability to identify effective marketing strategies would be beneficial in the launch and growth of a new marketing venture.
While the other candidates have relevant experience, they lack Laura's level of marketing strategy expertise.
Thus, the correct option is C.
For more details regarding entrepreneur, visit:
https://brainly.com/question/31104672
#SPJ2
Write a function that takes the name of a file with a .csv extension (a comma-separated value file), and writes a new file that is equivalent (same name and same data) but with a .tsv extension (a tab-separated value file: like a CSV but with tabs instead of commas separating the elements of the file). Note: the character used to represent a tab is ‘\t’.
Answers
Answer:
import pandas as pd
def convert_to_tsv( csv_filename ):
df = pd.read_csv("csv_file")
df.to_csv("csv_filename.tsv", sep='\t')
Explanation:
The python program uses the pandas' module to read in the csv file in the function "convert_to_tsv". The file is saved as a tsv file with the pandas to_csv method and the " sep= '\t' " attribute.
___Is pop-up screen when you right click the mouse where in it shows.
Answers
Answer:
A context menu.
Explanation:
A context menu is a GUI that appears when the user takes an action, such as right-clicking, that causes a pop-up screen to appear. That pop-up screen is referred to as a context menu.
David has created a lot of styles and now his Quick Style Gallery contains styles he no longer uses.
How can he remove the unwanted styles?
Answers
step by step solution
Answer:
C) Right-click the style in the Quick Styles Gallery, and select the Remove from Quick Style Gallery option.
Explanation:
3 alternativas donde puedas utilizar la tecnologia que nos ayude a reducir el impacto ambiental al medio ambiente
Answers
Answer:
El correo, las notas y las agendas ahora están archivados en el mundo digital, ayudando a reducir la deforestación. Coches eléctricos: se está trabajando meticulosamente en reducir la contaminación que producen los vehículos, haciendo que cada vez sean más sostenibles.
Explanation:
q1 (8 points): create a physical data flow child diagram for the following situation: the local running club holds meetings once a month, with informative speakers, door prizes like pre-paid entry fees for races, designer running gear, and so on, and sessions for special interest groups (people who want to coach, people who want to run marathons, those who want to get fit, and so on). a laptop computer is taken to the meetings and is used to add the names of new members to the group. the diagram represents an online process and is the child of process 1, add new members. the following tasks are included: a. key the new member information. b. validate the information. errors are displayed on the screen. c. when all the information is valid, a confirmation screen is displayed. the operator visually confirms that the data are correct and either accepts the transaction or cancels it. d. accepted transactions add new members to the membership master file, which is stored on the laptop hard drive. e. accepted transactions are written to a membership journal file, which is stored on a second hard drive
Answers
To create a physical data flow chart diagram for the given situation,
Follow these steps:
1. Start by identifying the main entities involved: the laptop, the operator, the membership master file, and the membership journal file.
2. Draw a rectangle labeled "Process 1: Add New Members" to represent the main process.
3. Connect the operator to Process 1 with a flow labeled "a. Key New Member Information" to represent Task a.
4. Add a decision point inside Process 1, labeled "b. Validate Information," to represent Task b. Connect this decision point to an output flow labeled "Errors Displayed on Screen" that goes back to the operator.
5. Connect the validated decision point to another decision point labeled "c. Confirmation Screen" to represent task c. Connect this decision point to two output flows, one labeled "Accept Transaction" and the other labeled "Cancel Transaction," both going back to the operator.
6. Connect the "Accept Transaction" flow to an output flow labeled "d. Update Membership Master File" which goes to the Membership Master File stored on the laptop hard drive, representing task d.
7. Connect the "Accept Transaction" flow to another output flow labeled "e. Write to Membership Journal File," which goes to the Membership Journal File stored on the second hard drive, representing task e.
Your physical data flow chart should now represent the entire process of adding new members to the local running club, including the validation and confirmation steps as well as the storage of information in the Membership Master File and Membership Journal File.
Learn more about data flow diagram here:
https://brainly.com/question/14285485
#SPJ11
What is computer Network?
Answers
Answer:
\(\boxed{\sf {view \: explanation}}\)
Explanation:
A computer network is a network of computers that can share data among the computers.
What type of software can you run to help fix computer problems?
Answers
Answer:
IOBit Driver Booster.
Explanation:
First, you want to make sure your computer is entirely updated. You can go into your settings, to do so.
If this doesn't solve the problem, here are some other alternatives, they're free repair tools.
IOBit Drive Booster
FixWin 10
Ultimate Windows Tweaker 4
O&O ShutUp10
What are the simularities between the solar eclipse & lunar eclipse?
Answers
Answer:
An eclipse occurs when one celestial object obscures another celestial object. In the case of a solar eclipse, the moon moves between the Earth and the sun, thus obscuring the sun. A lunar eclipse occurs when the Earth moves directly between the sun and the moon. Either type of eclipse can be total or partial
which of the following best summarizes the fetch-decode-execute cycle of a cpu? question 13 options: the cpu fetches an instruction from registers, the control unit executes it, and the alu saves any results in the main memory. the alu fetches an instruction from main memory, the control unit decodes and executes the instruction, and any results are saved back into the main memory. the cpu fetches an instruction from main memory, executes it, and saves any results in the registers. the control unit fetches an instruction from the registers, the alu decodes and executes the instruction, and any results are saved back into the registers.
Answers
The best summary of the fetch-decode-execute cycle of a CPU is "The CPU fetches an instruction from main memory, executes it, and saves any results in the registers."
What is the fetch-decode-execute cycle of a CPU?Fetch-decode-execute cycle is the procedure by which a computer executes machine language instructions. The CPU executes the cycle over and over, processing instructions from a software program until it is complete or until the computer is shut down.The fetch-decode-execute cycle is divided into three parts: fetch, decode, and execute.
During the fetch step, the CPU fetches an instruction from main memory. During the decode step, the CPU determines which operation the instruction is requesting and what inputs are required for the operation. During the execute step, the CPU executes the operation and writes any results back to memory or to registers.
Learn more about CPU at:
https://brainly.com/question/16254036
#SPJ11
who got houseparty and tryna play uno
Answers
Answer:
awww shiiiii yessss
Mail Tips can be displayed on the top of the message address bar for different circumstances, such as
automatic replies when the recipient is
and can refer the sender to another
a moderated group where the message requires
before it can be sent to the recipients.
Answers
Answer:
automatic replies when the recipient is
✔ out of the office
and can refer the sender to another
✔ recipient
.
a moderated group where the message requires
✔ approval
before it can be sent to the recipients.
Explanation:
got it right on edge 2020-2021
Automatic replies when the recipient is out of the office and can refer the sender to another recipient. A moderated group where the message requires approval. Before it can be sent to the recipients.
What are office gestures?In the workplace, gestures can communicate a lot of information without the speaker ever saying a word. Employees respond to other people's body language as perceived at work.
Interactions at work are influenced by facial expressions, eye contact, and touch. Some refer to it as body language. Some refer to it as kinesics. A gesture is a visible body activity that conveys specific messages in place of or in addition to words. It is a type of nonverbal or nonvocal communication.
Therefore, Automatic responses can direct the sender to another destination if the intended recipient is unavailable. A discussion forum where messages must be approved. Before the recipients can receive it.
To learn more about office gestures, refer to the link:
https://brainly.com/question/25547729
#SPJ2