Which Azure service can be enabled to enable Multi-Factor Authentication for administrators but not require it for regular users
Answers
Azure Active Directory (Azure AD) Conditional Access can be enabled to enforce Multi-Factor Authentication (MFA) for administrators while not requiring it for regular users.
Azure AD Conditional Access is a feature that allows organizations to define policies for accessing Azure AD resources based on certain conditions. This feature can be leveraged to enable MFA specifically for administrators while not mandating it for regular users.
By configuring Conditional Access policies in Azure AD, administrators can be required to authenticate with MFA when accessing Azure resources, such as Azure portals, management interfaces, or administrative APIs. Regular users, on the other hand, can continue to access these resources without the MFA requirement.
To implement this:
1. Access the Azure portal and navigate to Azure AD.
2. Configure a Conditional Access policy that targets the administrator roles or specific user groups representing administrators.
3. In the policy settings, enable the MFA requirement for the identified administrators. This can be achieved by selecting the appropriate controls and conditions related to MFA.
4. Save and apply the policy to enforce MFA for administrators while allowing regular users to access Azure resources without MFA.
By utilizing Azure AD Conditional Access in this manner, organizations can enhance security for administrative accounts by enforcing MFA, a strong authentication factor, while providing a more streamlined experience for regular users who do not require MFA for their access to Azure resources.
To learn more about portal Click Here: brainly.com/question/30479061
#SPJ11
Related Questions
A top investment bank is in the process of building a new Forex trading platform. To ensure high availability and scalability, you designed the trading platform to use an Elastic Load Balancer in front of an Auto Scaling group of On-Demand EC2 instances across multiple Availability Zones. For its database tier, you chose to use a single Amazon Aurora instance to take advantage of its distributed, fault-tolerant, and self-healing storage system. In the event of system failure on the primary database instance, what happens to Amazon Aurora during the failove
Answers
Answer:
Following are the solution to the given question:
Explanation:
Initially, Aurora will try and establish a new DB instance in the same AZ as the previous example. When Aurora can do it, he will try to create a new DB instance in another AZ.
Aurora will try and construct a new DB instance in the same disponibility zone as the original example if there is not an Amazon Aurora Replica (i.e. single instance) that does not execute Aurora Serverless. The replacement of the original example was better managed and may not work if there is, for example, an issue that impacts broadly the entire Access Service.
In many cases, the software in the PCM's memory can be updated by uploading software updates, called a ________ process.
Answers
The process of electronically updating the software component of a PCM by transferring approved file to the PCM's memory is called reflashing.
The PCM is called the Powertrain Control Module influences the working operation of a system. Hence, through the process of reflashing, software updates could be installed on the PCM memory electronically. This process is used in many Over - the - air software updates whereby vendor approved files are downloads and installed without having manually reconfigure the PCM.Hence, the process is called reflashing.
Learn more : https://brainly.com/question/25576453
here is an email written by Michelle to Pattie what is the main netiquette violation in sentence b ?
Answers
Answer:
Using unfamiliar abbreviations and acronyms
Explanation:
because he using RHFD and LTRE
a) Show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent by using series of logical equivalence. (3 marks)
b) Determine whether (p∧q)→(p∨q) is a tautology. (4 marks)
c) With the aid of a truth table, convert the expression (¬p→q)∧(¬q∨r) into Disjunction Normal Form (DNF) (5 marks)
Answers
a) To show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent, we can use a series of logical equivalences:
¬(p∨(¬p∧q)) (De Morgan's Law)
≡ ¬p∧¬(¬p∧q) (De Morgan's Law)
≡ ¬p∧(p∨¬q) (Double Negation)
≡ (¬p∧p)∨(¬p∧¬q) (Distributive Law)
≡ False∨(¬p∧¬q) (Negation Law)
≡ ¬p∧¬q (Identity Law)
Therefore, ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent.
b) To determine whether (p∧q)→(p∨q) is a tautology, we can construct a truth table:
p | q | (p∧q) | (p∨q) | (p∧q)→(p∨q)
-----------------------------------
T | T | T | T | T
T | F | F | T | T
F | T | F | T | T
F | F | F | F | T
Since the last column of the truth table always evaluates to true, (p∧q)→(p∨q) is a tautology.
c) Truth table for the expression (¬p→q)∧(¬q∨r):
p | q | r | ¬p | ¬p→q | ¬q | ¬q∨r | (¬p→q)∧(¬q∨r)
--------------------------------------------------
T | T | T | F | T | F | T | T
T | T | F | F | T | F | F | F
T | F | T | F | F | T | T | F
T | F | F | F | F | T | T | F
F | T | T | T | T | F | T | T
F | T | F | T | T | F | F | F
F | F | T | T | T | T | T | T
F | F | F | T | T | T | T | T
Converting the truth table into Disjunction Normal Form (DNF):
(¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r)
Therefore, the expression (¬p→q)∧(¬q∨r) in Disjunction Normal Form (DNF) is (¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r).
To know more about DNF, visit
https://brainly.com/question/31326308
#SPJ11
Security breaches are easier to address with which payment form?
Answers
Answer:
Cause #1: Old, Unpatched Security Vulnerabilities. ...
Cause #2: Human Error. ...
Cause #3: Malware. ...
Cause #4: Insider Misuse. ...
Cause #5: Physical Theft of a Data-Carrying Device
Explanation:
Answer:
i think the second one
Explanation:
4. How could you apply some of the ideas, principles, or structures of coding to fields of study, industries, or tasks outside of creating computer programs? Propose at least one way to use "coding" or creating programs outside of computer science and explain how it uses coding-related concepts.
Answers
Answer:
a production plant
Explanation:
"Coding" brings with it a linear way of thinking and problem solving, where one step needs to be taken before moving on to the next step. This can be applied to a wide range of real-life scenarios and industries. For example, a production plant starts with an initial input, that input is taken and used in a set of instructions (method), those instructions take that input and create a new output. Once the new output is created it is then passed on to another set of instructions that takes that output as an input to create a new output. Just like a computer program, a power plant repeats this process in order to a fully working and realized product.
Type the correct answer in the box. Spell all words correctly.
George is creating a professional presentation for his client and wants to add his company’s logo, some images, and a video of his manufacturing unit into a slide. Which parts of the slide layout should he use?
George must use the [ ? ] of the slide layout to insert the company logo, images, and the video into his slide.
Answers
George must use the media of the slide layout to insert the company logo, images, and the video into his slide.
What is a slide?A slide can be defined as a single page of a presentation that is made up of text-based information or images, which can be used to teach and educate an audience on a subject matter.
What is a slide layout?In Computer technology, the slide layout feature of a presentation software’s interface such as Microsoft PowerPoint, can be used to insert two or more tables, logo, images, and the video in a slide and format the text on all slides.
In this scenario, George must use the media of the slide layout to insert the company logo, images, and the video into his slide.
Read more on slides here: brainly.com/question/7019369
#SPJ1
Which reclusive writer announced two new novels to be published this fall, ending a 16-year hiatus?.
Answers
Harper Lee is the reclusive writer who announced two new novels to be published this fall, ending a 16-year hiatus.Harper Lee is an American novelist known for her critically acclaimed and Pulitzer Prize-winning novel To Kill a Mockingbird (1960).
She was born on April 28, 1926, in Monroeville, Alabama, and she died on February 19, 2016. Lee, who was known for her private nature and reclusive lifestyle, announced in February 2015 that a second novel, Go Set a Watchman, would be published in July 2015. The novel is set in the same fictional town as To Kill a Mockingbird, but 20 years later. Another novel, The Mockingbird Next Door: Life with Harper Lee, was also published in 2015 by Marja Mills, a journalist who lived next door to Lee in Monroeville.
It is worth noting that Harper Lee did not announce two new novels to be published in the fall of 2021 or any other year after 2015.
To know more about Prize-winning visit:
brainly.com/question/31551611
#SPJ11
Both instructions and data in a digital
computer are represented as binary
digits. True False
Answers
Answer:
False
Explanation:
insturctions are represented in binary numbers, data are represented in decimal numbers.
what are the answers for these question?




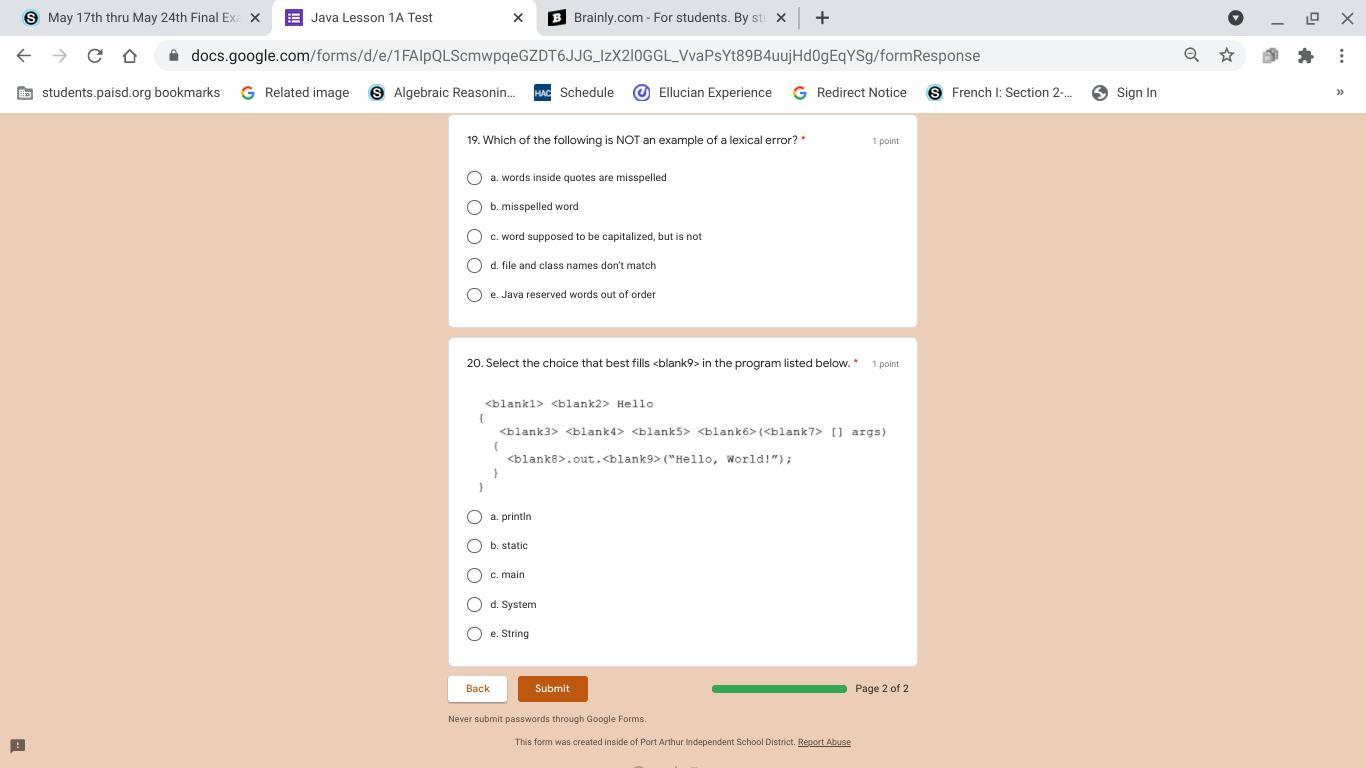
Answers
Answer:
tbh u gotta give more points in order for me to solve that:)
Explanation:
After completing initial diagnostic procedures and allocating system resources, a startup BIOS program checks for information about secondary storage devices that might contain the OS. The list of devices and the order in which they should be checked can be found and arranged in the CMOS setup utility. This option is commonly referred to as a:
Answers
Answer:
Boor sequence
Explanation:
Fill in the blank: Sticker sheets are useful in a design system because _____.
designers can work faster and avoid rework
Answers
Answer:
Sticker sheets are useful in a design system because they enable designers to quickly and easily copy and paste components into new designs, reducing the amount of time needed to create designs and avoiding the need for rework.
Explanation:
They enable designers to produce reusable visual components that are consistent with the brand, enhancing user experience all around.
Technical definition sheet: What is it?A technical data file (TDS) is just a document that comes with a product and contains a variety of details about the item. Technical data sheets frequently feature information about the product's composition, usage guidelines, technical specifications, typical applications, cautions, and product images.
What does the word "sheets" mean?Paper each is typically rectangular in appearance. especially: equipment specifically engineered for printing. (2) : a mounted plant specimen on a relatively thin, rectangular sheet of paper. a 100,000 sheet important to the advancement.
To know more about Sheets visit :
https://brainly.com/question/30277396
#SPJ4
Olivia made spreadsheet art using conditional formatting where cells with different numbers are different colors. she now wants to hide the numbers in the cells. how should she hide the numbers?
Answers
The user can choose the colors and the kind of data that has to be highlighted in checkboxes, that can be found under the Home tab of Microsoft Excel.
What does the word highlight mean in a sentence?"That encounter was a particular high point for him." "The main real highlight was meeting the president," He enjoys viewing football highlights, "His World Series victory was the pinnacle of his career."
Why is text highlighted?What does highlighting accomplish? To bring attention to crucial information in a text, highlights are used Effective highlighted entails the reader to recognize the important portions before offering a helpful technique for later assessing that content.
To know more about highlighted visit:
https://brainly.com/question/11609589
#SPJ4
This tool lets you insert text anywhere in your document. O Cut О сору O Drag O Paste
Answers
Answer:
Drag or paste (im not 100% sure tho)
Explanation:
4. 5 Facts about Alternating Current and direct current
Answers
Answer:
1. The Alternating current comes from a power plant. The direction of the electricity switches back 60 times every second.
2. Alternating current: The same amount of current flows through a circuit regardless of the direction of the current.
3. Direct current: Even when no current is flowing through the wire, the electrons in the wire are moving at speeds up to 600 miles (1000 kilometers) per second but in random directions because the wire has a finite temperature.
4. Direct current: As opposed to alternating current, the direction and amperage of direct currents do not change. It is used in many household electronics and in all devices that use batteries.
5. Alternating current is five times more dangerous than Direct current. The frequency of the alternating current is the main reason for this severe effect on the human body. The frequency of 60 cycles is in an extremely harmful range. At this frequency, even a small voltage of 25 volts can kill a person.
Explanation:
operational crm supports back-office operations and strategic analysis and includes all systems that do not deal directly with the customers. group of answer choices
Answers
Operational CRM supports back-office operations and strategic analysis, encompassing systems that don't involve direct customer interactions.
Operational CRM refers to the use of technology and systems to streamline and automate various business processes related to customer interactions. It includes different tools and applications designed to manage customer data, sales automation, marketing campaigns, and customer service.
One aspect of operational CRM is its support for back-office operations. These are the internal processes and functions of a company that are necessary to support the overall customer experience. This can include activities such as order processing, inventory management, billing, and fulfillment. By integrating and automating these back-office operations, operational CRM improves efficiency and helps deliver a better customer experience.
Additionally, operational CRM also facilitates strategic analysis. The systems and tools involved in operational CRM capture and store vast amounts of customer data, which can be leveraged for strategic decision-making. Through data analysis and reporting capabilities, companies can gain insights into customer behavior, preferences, and trends. This information is invaluable for developing marketing strategies, identifying opportunities for growth, and improving overall business performance.
It's worth noting that operational CRM focuses on the internal processes and systems that support customer interactions, rather than the direct interaction with customers themselves. Customer-facing activities such as sales calls, customer support interactions, and marketing campaigns fall under other CRM components like sales force automation, customer service management, and marketing automation.
Learn more about Operational CRM here:
https://brainly.com/question/31645596
#SPJ11
Which CRM supports back-office operations and strategic analysis and includes all systems that do not deal directly with customers?
The project team identified the completion of the first module to be the first significant event. The completion of Module One is a _____.
requirement
risk
stakeholders
milestone
Answers
APCPS B U10L12 exam (Connexus)
Hi if anyone has done this already, I would appreciate if you could help.
Answers
I don't know how to that i don't even know how to do my work
Hey does anyone think nervegear would be possible? (Just asking)
Answers
Answer:
Depends
Explanation:
Technology is not advanced yet, so building a fully functional nerve gear is difficult. It could be possible in a few years though.
Answer:
No, the Nerve Gear cannot be possible at the moment. However, in Japan, they are creating the Nerve Gear and is to be released in May 2022 told by the creator, Kayaba Akihiko. So, the Nerve Gear cannot be possible in 2020 but in 2022. We just have to wait for two more years.
Explanation:
please choose me as brainliest if that is ok ;)
What is the best gaming name you can come up with?
Answers
Can someone help me with Unit 7 of cmu cs academy python. PLSS EMERGENCYY
Answers
Carnegie Mellon University's CMU CS Academy is an online, graphics-based computer science curriculum taught in Python.
Why is Phyton important?Python has become a data science industry standard, allowing data analysts and other professionals to do complicated statistical computations, produce data visualizations, design machine learning algorithms, handle and analyze data, and accomplish other data-related jobs.
Development time is far more essential than computer run time in today's society. Python just cannot be beat in terms of time-to-market. Python is also efficient and dependable, allowing developers to design complex programs with minimal effort.
Learn more about Phyton:
https://brainly.com/question/31768977
#SPJ1
hello friend!
make it a great day!
- smile
- laugh
- celebrate
Answers
hello friend! make it a great day! smile laugh celebrate..................
discuss the problem of the rapidly changing cybersecurity environment juxtaposed with the slow-moving government regulation and legal system in general
Answers
The rapidly changing cyber security environment poses a significant challenge due to the slow-moving government regulation and legal system, resulting in an inadequate response to emerging threats.
The cyber security landscape is evolving at an unprecedented pace, with new threats and vulnerabilities emerging almost daily. Hackers are constantly finding innovative ways to exploit weaknesses in digital systems, making it increasingly challenging for organizations and individuals to protect their sensitive data.
However, the government regulation and legal system, which are responsible for establishing and enforcing cybersecurity standards, often struggle to keep up with these rapid changes.
One of the primary reasons for the slow pace of government regulation is the bureaucratic nature of the legislative process. Drafting and passing new laws can be a time-consuming and complex process involving multiple stakeholders, including lawmakers, legal experts, and industry representatives.
By the time a cybersecurity-related bill is introduced, debated, and enacted, the threat landscape may have evolved significantly, rendering the legislation outdated or inadequate.
Moreover, technology moves much faster than the legal system. Cyber security innovations and advancements occur at a rapid pace, while the legal system tends to be slow and cautious, ensuring that laws are well thought out and their consequences are thoroughly considered.
This disconnect between the speed of technological progress and the speed of legal adaptation creates a significant gap, leaving organizations and individuals vulnerable to cyber threats.
Learn more about Cyber security
brainly.com/question/30724806
#SPJ11
1. Which of the following is the closest definition of embedded systems?
-a software that performs a specific function
-devices that perform multiple tasks
-hardware designed to perform a distinctive function*
-the combination of hardware and software designed for a specific purpose
2.Select the function of keypunches that were used as one of the earliest input devices.(1 point)
-It was used for punching holes in the paper at relevant positions for the computer to understand the instructions.
-It was used to control the cursor on the screen.
-It was used to press the buttons feed information into the computer.*
-It was used to insert one character on the paper at a time.
3.Which of the following set defines the storage devices?(1 point)
-magnetic disks, optical disks, flash drive, SSD, and floppy disk*
-floppy disk, magnetic disks, SSD, and mouse
-typewriter, SSD, and mouse
-SSD, optical disks, and keypunches
4. What does computational thinking involve?(1 point)
-breaking down complex problems into smaller pieces for easy resolution
-thinking like a computer
-disregarding non-essential information*
-hiding unnecessary details from the user
5.What is a complex problem?(1 point)
-a problem that can only be resolved using a computer
-a problem with no obvious or immediate resolution
-a problem that requires multiple computers to resolve
-a problem that requires collaboration*
Answers
The option that is the closest definition of embedded systems is option d: the combination of hardware and software designed for a specific purpose.
The function of keypunches that were used as one of the earliest input devices is that It was used for punching holes in the paper at relevant for the computer to understand the instructions.
The set that defines the storage devices are magnetic disks, optical disks, flash drive, SSD, and floppy disk*
Computational thinking involve breaking down complex problems into smaller pieces for easy resolution.
A complex problem is a problem with no obvious or immediate resolution.
What is an embedded systems?An embedded system is known to be a kind of a system that is said to be the combination of both the computer hardware and that of the software and it is one that is set up for a specific function.
Note that the Embedded systems may function inside a larger system and thus The option that is the closest definition of embedded systems is option d: the combination of hardware and software designed for a specific purpose.
Learn more about embedded systems from
https://brainly.com/question/13014225
#SPJ1
Write a python function that will return true if the two given integer values are equal or their sum or difference is 5
Answers
Here's a Python function that checks if two given integer values are equal or if their sum or difference is 5.
def check_integer_values(a, b):
if a == b or a + b == 5 or abs(a - b) == 5:
return True
else:
return False
In this function, a and b are the two integer values being compared. The function checks if a is equal to b (a == b), if their sum is 5 (a + b == 5), or if their absolute difference is 5 (abs(a - b) == 5).
If any of these conditions are true, the function returns True. Otherwise, it returns False.
You can call this function and pass your integer values to check if they satisfy the conditions. For example:
print(check_integer_values(3, 8)) # False
print(check_integer_values(2, 3)) # True
print(check_integer_values(7, 2)) # True
Learn more about Python here:
brainly.com/question/30391554
#SPJ11
An important part of the development of transport is safety. how can you, when you get around in different ways, contribute to making it safer on the roads
Answers
Answer:
I need help I don't get a this questions please asap?
Explanation: Head-on collisions. Some simple solutions can help to reduce the risk of head-on crashes. ...
Run-off road crashes. This is when a vehicle collides with a stationary object, such as a sign or lamppost, after leaving the road. ...
Intersection crashes. ...
Vulnerable road users. ...
Much work to be done.
Aug 31, 2018
from the current view (layout view), group this report by values in the dob field. change the grouping to group by year instead of by quarter.
Answers
To group the report by values in the "dob" field and change the grouping to group by year instead of by quarter, follow these steps in the layout view:
1. Open the report in layout view.
2. Locate the grouping section in the report layout. This section usually appears in the "Group, Sort, and Total" pane.
3. Find the grouping that is currently set to group by quarter.
4. Right-click on the grouping and select "Group Properties" or a similar option.
5. In the Group Properties dialog box, look for the "Group On" section or a similar option.
6. In the "Group On" section, select the field that represents the "dob" or date of birth.
7. If the field is not available in the dropdown, you may need to add it to the report's data source or adjust the query accordingly.
8. Below the "Group On" section, look for a "Group Interval" or similar option.
9. Change the group interval to "Year" or select a specific option that represents grouping by year.
10. Click "OK" or a similar button to apply the changes.
11. Preview the report to verify that the grouping has been changed to group by year based on the "dob" field.
Following these steps should help you group the report by the values in the "dob" field and change the grouping to group by year instead of by quarter in the layout view.
For more such questions layout,Click on
https://brainly.com/question/29411651
#SPJ8
plz help with this question this is really important for me plus plz do not fool around plz this is really really important

Answers
you need to enter a password under " Ibrahim " and enter any username but not your real name double click on it to change and enter the password down again it's like a confirmation and btw Good Luck
which function of a soho router blocks unwanted traffic initiated from the internet and can restrict internet access for local computers?
Answers
A firewall is a function of a SOHO router that blocks unwanted traffic initiated from the internet as well as restricts internet access for local computers.
SOHO routers are primarily designed to provide wired and wireless broadband network routing. As opposed to traditional routers, SOHO routers are specifically structured for small offices and home office networks; which is from where the SOHO acronym comes in. There are many functions of SOHO routers, among them, one function of the SOHO routers is they work as a firewall.
By serving as a firewall, the SOHO router blocks unwanted traffic originating from the Internet and provides Network Address Translation (NAT) so that computers on the Local Area Network (LAN) can use private or link-local IP addresses. Another firewall feature of SOHO routers as a firewall is to restrict Internet access for local computers.
You can learn more about SOHO routers at
https://brainly.com/question/14700535
#SPJ4
b. What significant values have you learned while learning the tools and utensils?