When you do not know how many items need to be sorted in a program, you can create an array that has _____.at least as many elements as the number you predict you will needvariable-sized elementsYou cannot sort items if you do not know the number of items when you write the program.at least one element less than the number you predict you will need
Answers
When you do not know how many items need to be sorted in a program, you can create an array that has "at least as many elements as the number you predict you will need."The correct answer is option A.
An array can be defined as a data structure that stores a collection of items of the same data type. In programming, the size of an array is determined during its creation, which makes it a static data structure. However, if the number of items to be sorted is unknown or cannot be determined before execution, we can create a dynamic array whose size can be modified during execution.
A dynamic array, also known as a vector or a variable-length array, is an array whose size can be changed dynamically during runtime.
Since the size of a dynamic array can be modified during execution, it can have "at least as many elements as the number you predict you will need."
Therefore, when you do not know how many items need to be sorted in a program, you can create an array that has "at least as many elements as the number you predict you will need."
Hence, option A is the right one.
To know more about array, visit https://brainly.com/question/28565733
#SPJ11
Related Questions
Someone help please I really need help

Answers
Answer:
Smallest value;
\(f(x) = { \sf{MIN}}(value)\)
Largest value;
\(f(x) = { \sf{MAX}}(value)\)
n cell b10, use a sumif formula to calculate the sum of annualsales where the value in the regions named range is equal to the region listed in cell b9.
Answers
SUMIF formula is used to calculate the sum of sales revenue for the year by checking the value in the regions named range equal to the region listed in cell B9.
The SUMIF formula is used when a specific criterion is to be applied to a range, and the sum of the cells meeting that criterion is required. For instance, to calculate the sum of annual sales where the value in the regions named range is equal to the region listed in cell B9. The formula is written in cell B10 as follows:=SUMIF(Regions, B9, AnnualSales)The formula means:
• Regions: is the named range in the worksheet• B9: the region for which the sum of sales is to be calculated• AnnualSales: the range where the annual sales data is locatedTo get a better understanding, the steps for calculating the SUMIF formula in cell B10 are:1. Select cell B10, where the sum is to be displayed.2. Type the formula “=SUMIF(Regions, B9, AnnualSales)” into the cell.
3. Press Enter, and the sum of sales revenue for the year will be displayed in cell B10.4. The SUMIF formula calculates the sum of annual sales for a particular region.
To know more about sales visit:
https://brainly.com/question/29436143
#SPJ11
which components of the endocrine system exert the most wide-ranging influence on the entire endocrine system?
Answers
The components of the endocrine system that exert the most wide-ranging influence on the entire system are the hypothalamus and the pituitary gland.
The hypothalamus and the pituitary gland play crucial roles in regulating and coordinating the activities of the entire endocrine system. The hypothalamus, located in the brain, produces and releases various hormones that control the secretion of hormones from the pituitary gland. The pituitary gland, often referred to as the "master gland," produces and releases hormones that influence the function of other endocrine glands throughout the body. Through its control over the pituitary gland, the hypothalamus regulates processes such as growth, metabolism, reproduction, stress response, and many other vital functions. The close interaction between the hypothalamus and the pituitary gland allows them to exert a wide-ranging influence on the entire endocrine system, maintaining homeostasis and coordinating hormonal activities.
Learn more about the hypothalamus here:
https://brainly.com/question/29699760
#SPJ11
Takes a 3-letter String parameter. Returns true if the second and
third characters are “ix”
Python and using function
Answers
Answer:
def ix(s):
return s[1:3]=="ix"
Explanation:
Which language paradigm interacts well with database systems in business environments that use SQL?
A) logic-based
B) fourth-generation
C) data-oriented
D) aspect-oriented
Answers
guillaume has a windows 10 personal laptop. he wants to ensure that the microsoft store apps on his computer are kept updated. what can guillaume do to ensure this?
Answers
For your Windows device, the Store has almost everything you could ever want, including the newest games, well-liked movies and TV episodes, creativity software, apps, and more.
Other distribution platforms (Windows Marketplace, Windows Phone Store, Video, and Music) were combined into a single storefront for Windows 10 on all platforms, offering apps, games, music, movies, TV shows, themes, and e-books. Windows 10 was released with an updated version of the Windows Store. Administrators can use a management tool, add apps to the private store, or allocate apps to certain users. Apps can be assigned to users by buyers. In Windows 11/10/8, the Universal or Windows Store Applications are installed in the Windows Apps folder found in the Program Files directory on the C: drive.
Learn more about windows here-
https://brainly.com/question/13502522
#SPJ4
For your initial post, select a more complex input device such as a touchscreen, glove sensors, eye input, audio or voice input, a joystick, or anything else. Then, answer the following: where might the input device you selected be used? if possible, find an actual application where a different input device is used to control opengl objects or run applications that use opengl. Can you identify the libraries that would be necessary to run the input device? what challenges do you think you would encounter when navigating around the world using the input device? for example, if you are using a glove to move forward, your arm will only extend so far or your hand might come in contact with the view screen. What other considerations for the use of this input device can you identify? think about accessibility, cost, set-up, and size as a few possibilities
Answers
Eye input, an effective input device, allows users to interact with computers or devices using their eyes. Another name for this is Iris Recognition technology.
How is this so?This piece of technology is highly versatile and can be utilized in various sectors such as medical equipment, gaming, virtual reality, and communication devices for individuals with disabilities.
Note that Tobii Dynavox is a manufacturer that makes use of eye tracking to choose symbols and words for communication in its disability-assisting equipment.
Relevant software libraries required for operating eye input include OpenCV and Tobii EyeX SDK.
Learn more about input device at:
https://brainly.com/question/13014455
#SPJ4
the accountant for buddy's machine shop has just received a new windows 10 computer. his accounting software has been installed and is working well. however, he asks you to install a pdf printer that he uses to generate invoice pdfs to send out via email. this pdf printer is quite expensive. explain why this pdf printer is not necessary for windows 10.
Answers
Windows 10 comes with a built-in PDF printer called "Microsoft Print to PDF". This feature allows users to print any document to a PDF file without needing any additional software. As a result, there is no need to purchase an expensive PDF printer because the functionality is already built into Windows 10. The accountant can simply use the built-in PDF printer to generate invoice PDFs and send them out via email.
Learn more about printer here:
brainly.com/question/32073973
#SPJ11
For each product that has more than three items sold within all sales transactions, retrieve the product id, product name, and product price. Query 30: SELECT productid, productname, productprice FROM product WHERE productid IN (SELECT productid FROM includes GROUP BY productid HAVING SUM(quantity) > 3); duce. Query 31 text: For each product whose items were sold in more than one sales transaction, retrieve the product id, product name, and product price. Query 31: SELECT productid, productname, productprice FROM product WHERE productid IN (SELECT productid FROM includes GROUP BY productid HAVING COUNT
Answers
For each product whose items were sold in more than one sales transaction, retrieve the product id, product name, and product price is given below
Query 31:
sql
SELECT productid, productname, productprice
FROM product
WHERE productid IN (SELECT productid
FROM includes
GROUP BY productid
HAVING COUNT(DISTINCT transactionid) > 1);
What is the product code?So one can retrieve product id, name, and price for products sold in multiple transactions. The subquery retrieves product ids from includes table sold in multiple transactions.
One can COUNT(DISTINCT transactionid) for distinct product transactions. The outer query selects product information for items sold in more than one sales transaction. Use this query for relevant product information.
Learn more about product code from
https://brainly.com/question/30560696
#SPJ4
true or false A client is a computer that responds to requests from other computers.
Answers
Answer:
it's answer is option A )true
Scripting languages are unique computer languages with a specialized function. explain what scripting languages do, and how this is different from other types of
languages. describe one advantage of using scripting languages and one disadvantage.
Answers
Scripting languages are unique computer languages because they automate task that could be done by human operator and are easy to use.
What is a scripting language?Scripting languages are programming languages that is interpreted.
They are programming languages that automates the task that will originally be performed by a human operator.
Scripting languages are used to give instruction to other software to run accordingly to how you want it.
The scripting language is different form other language base on the fact that its interpreted . This means the code are translated to machine code when it is run.
The major advantage of scripting languages is that it is human readable and understandable.
Examples of scripting languages are Python and JavaScript.
learn more on scripting here: https://brainly.com/question/12763341
#SPJ1
question 3 while performing web application testing, ruben, a software developer, found out that the web application failed to protect sensitive traffic flowing in the network. additionally, the web application supported weak algorithms and used expired or invalid certificates, making it susceptible to various attacks that revealed user data. identify the security misconfiguration detected by ruben in the above scenario.
Answers
When security choices are not defined in a way that maximises security, or when services are launched with insecure default settings, security misconfiguration occurs.
Any computing system, software programme, cloud, and network infrastructure could experience this.Your systems and data are at danger due to security controls that have been incorrectly set or left insecure
In essence, any incorrectly documented configuration changes, default configurations, or a technical issue with any component in your endpoints could result in a misconfiguration
Thus, while performing web application testing, ruben, a software developer, found out that the web application failed to protect sensitive traffic flowing in the network.
To know more about security choices please check the following link
https://brainly.com/question/31780008
SPJ11
An error in the sequence of words or rules in a program that prevents the program from running is what?
Syntax
Compiling
Executing
Interpreting
Answers
Answer:
Syntax
Explanation:
Syntax is generally defined as the rules of a language or the regulated structure needed to be understood. Programming languages interpret this meaning in a very similar way. An error in syntax refers to a misunderstanding or something that is missing in the line. Since computers cannot ignore mistakes, the program will stop as a result of processing something that cannot be processed. In general grammar is the whole system of a language consisting of syntax morphology, phonology, and semantics.
Answer:
I think it is:
A. Syntax
Explanation:
What statement is true about technology in relation to channel management?
A. Some businesses have the capacity to distribute most or all of their products through the internet.
B. Because technology continues to evolve, vertical conflict among channel memners is occurring less often.
C. Technological advancements generally require businesses to increase the number of intermediaries they
use.
D. For most businesses, technology makes it more difficult to monitor the channel members' activities.
Answers
Statement A is true about technology in relation to channel management. Some businesses have the capacity to distribute most or all of their products through the internet. This is made possible by the advancements in technology, specifically the rise of e-commerce platforms and online marketplaces. With these platforms, businesses can reach a global audience and sell their products directly to consumers without the need for intermediaries.
For example, companies like Amazon and Alibaba have created online marketplaces that allow businesses to sell their products to customers worldwide. These platforms provide a convenient and efficient way for businesses to manage their channels of distribution.
However, it is important to note that not all businesses have the capacity or resources to solely rely on the internet for distribution. Traditional brick-and-mortar stores and intermediaries still play a significant role in many industries. Additionally, some products may require physical distribution channels due to their nature or customer preferences.
In summary, while statement A is true and technology has enabled some businesses to distribute most or all of their products through the internet, the impact of technology on channel management varies across industries and products.
To know more about internet visit :-
https://brainly.com/question/16721461
#SPJ11
Helppppp meeeeee eee
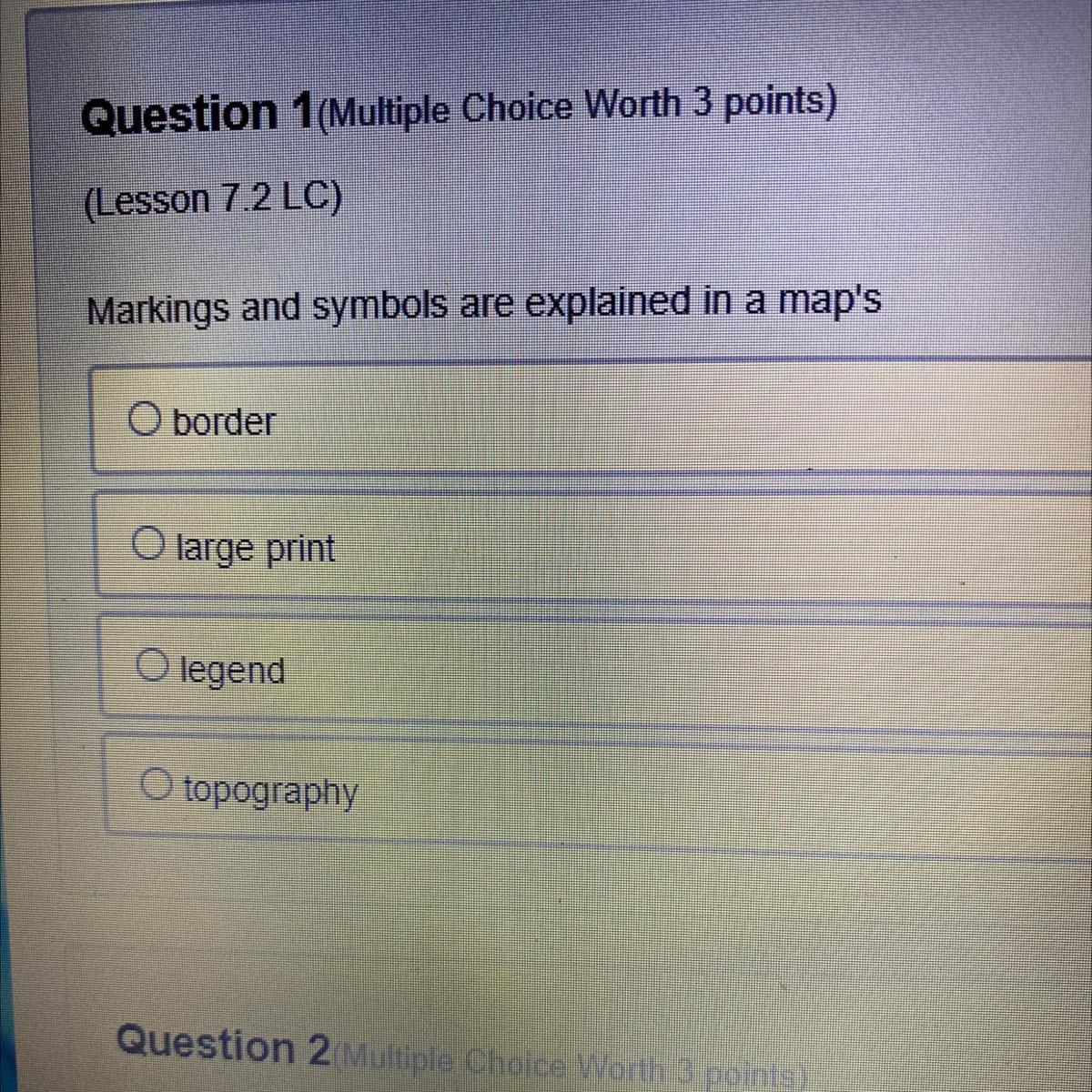
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
which of the following is true about which fl/sql data types you can access in an embedded sql statement? please select from the following A---The PL/SQL data type must be declared in a package.
B---The SQL statement needs to be embedded in the PL/SQL block where the type is defined.
C---The PL/SQL data type must be locally defined.
Answers
The PL/SQL data type must be locally defined is the true statement about which fl/sql data types you can access in an embedded sql statement. Option C is correct.
In embedded SQL statements, which combine SQL with procedural language code like PL/SQL, the PL/SQL data types used in the SQL statement must be locally defined.
This means that the PL/SQL data types need to be declared within the same PL/SQL block or program unit where the SQL statement is embedded.
The PL/SQL data type must be declared in a package is not correct because the PL/SQL data type does not necessarily need to be declared in a package.
It can be declared locally within the PL/SQL block.
The SQL statement does not need to be embedded in the PL/SQL block where the type is defined.
The SQL statement can be embedded in any PL/SQL block or program unit that has access to the locally defined PL/SQL data type.
To learn more on SQL click:
https://brainly.com/question/31663284
#SPJ4
Please helpppppppppppppppppp please I’m stuck!

Answers
do u know thw muffin man
Which of the following is an example of a technical ("hard") skill?.
Answers
Answer: Microsoft Office, Troubleshooting, Interpreting Data, Video Editing, Graphic Design
Explanation:
I have no errors in the code but for some reason it doesn't work... what i'm missing?

Answers
The JavaScript code that you have written is one that tends to retrieves data from a table that is called "Busiest Airports" . The corrected code is given below.
What is the getColumn code about?In regards to the given code that was corrected, the user input is one that can be obtained from the text input element with the use of the ID "yearInputBox" via the act of getText function as well as been saved in a variable named inputYear.
Therefore, when there is a match that is found, the output is said to be made by the use of the corresponding elements that is obtained from the year, as well as country, and that of airport arrays, and later on set to the "outputBox" element via the use of the setText function.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1
See text below
1
var year getColumn("Busiest Airports", "Year");
var country = getColumn ("Busiest Airports", "Country");
var airport = getColumn("Busiest Airports", "Airport");
onEvent("goButton", "click", function() {
/*call the "calculateOutput" function here,
*passing in the user input as a paremeter 10 */
calculateOutput (getText("year InputBox"));
function calculateOutput (years){
var output="";
for (var i = 0; i < year.length; i++) { /*write the list element being accessed*/ if (years[i] == "inputYear"){ output "In "
=
+ year + "the busiest airport was
11
+ country + "
in "airport[i];
21
}
}
setText("outputBox", output );
}

Enter an integer
5
6
7
Answers
/* This program prompts the user to enter an integer
* and then determines whether the integer is between 4-6. */
start();
function start(){
var int = readFloat("Enter an integer to print in this program: ");
println("An integer from 5-6 is entered (True/False)");
if(int <= 6 || int == 4){
println("True: " + int + " was entered.");
}else{
println("False: " + int + " was entered.");
}
}
... If this isn't what you were looking for, I apologize. I'm uncertain on what you really need help with, your question isn't quite clear... I answered to the best of my ability in simple js.
edit: brainly deletes my indents... just make sure to indent properly :-)
which is the first thing the compiler does when a function is called? group of answer choices creates a jump instruction to the function
Answers
Store the address of the function call is the first thing the compiler does when a function is called.
What Are CompilersCompiler is a program used to convert code written in natural language processing so that it can be understood by computers.
In compilating process, the compiler executes code that indicates when a binary high and low signal is needed in the processor arithmetic logic unit.
Types of compilersThere are two types of compilers that are commonly used by web developers.
A cross compiler that runs on machine 'A' and generates code for another machine 'B'. This compiler is capable of generating code for different platforms besides the platform it runs on. Source-to-source compiler or also called transcompiler, namely a compiler which translates source code written in one programming language into source code in another programming language.Even though the main job of the compiler is converting the code, there are several other tasks that it also performs. Here are some of them.
Breaking the source program into parts and applying grammatical structures to them. Build the desired target program from the intermediate representation and create a symbol table. Compiles source code and detects errors in it. Manages the storage space of all variables and code. Performs support for split compilation. Read and analyze the entire program to be translated into semantic equivalents. Translate source code into object code according to the type of machine used.Your question is incomplete but most probably your full question was:
Which is the first thing the compiler does when a function is called?
a.Converts the function's code to assembly b.Creates instructions to jump to the function c.Stores the address of the function call
d.Creates a jump instruction to the function
Learn more about compiler at https://brainly.com/question/27882492.
#SPJ4
Replace the nulls values of the column salary with the mean salary.
Answers
When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
What is Column salary?
One tactic is to impute the missing data. A wide range of algorithms, including simple interpolation (mean, median, mode), matrix factorization techniques like SVD, statistical models like Kalman filters, and deep learning techniques.
Machine learning models can learn from partial data with the aid of approaches like replacement or imputation for missing values. Mean, median, and mode are the three basic missing value imputation strategies.
The median is the middle number in a set of numbers sorted by size, the mode is the most prevalent numerical value for, and the mean is the average of all the values in a set.
Thus, When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
Learn more about Data, refer to the link:
https://brainly.com/question/10980404
#SPJ4
On march 12, medical waste services provides services on account to grace hospital for $9,400, terms 2/10, n/30. grace pays for those services on march 20.
Answers
The allowed discount was $276. while Mar. 12 Dr. Receivables $9,200 Cr. $9,200 in service revenue and on Mar. 20 Dr. Cash $9,200 (97%), $8,924.
Account receivable is the term used to describe the company's legally enforceable demand for payment for the goods and services it has provided. Receivables are categorized as a current asset.
the process of creating journal entries
Mar. 12 Dr. Receivables $9,200 Cr. $9,200 in service revenue (To record service revenue)
Mar. 20 Dr. Cash $9,200 (97%), $8,924
Dr Discount and Allowances $276 (3 % $9,200) Cr. $9,200 in accounts receivable (To record collection from receivables)
Learn more about receivables here-
https://brainly.com/question/14032135
#SPJ4
write a program to find a perimeter of rectangle using SUB.. ..End SUB
Answers
\(\\ \tt l=float(input("Enter\:the\: length:"))\)
\(\tt b=float(input("Enter\: breadth:"))\)
\(\tt P=2*(l+b)\)
\(\tt print ("Perimeter=",P)\)
Web technologies like Flash, CSS, Java, and HTML often depend on APIs to accomplish what task?
Answers
In Programming, web technologies like the front end part e.g Flash, CSS, Java, and HTML depends on back end APIs for task like data persistence, sending and getting data e.g post and get request in summary perform CRUD(Create, read, update and delete) operations
The development of web application is basically divider into two
The front end, done basically with technologies like HTML CSS, JavaScriptBack end, this can be done using Python, C#, Java, or any suitable languageTh front end depends on the back end for sending and retrieving information
Learn more:
https://brainly.com/question/8391970
what does the hipaa security rule cover? select one: a. how to protect all forms of phi b. how to prevent patients from accessing ephi c. standards for those who may gain access to phi d. requirements to ensure only authorized individuals access ephi
Answers
The HIPPA security rule covers the requirements to ensure only authorized individuals access EPHI. The correct option is d.
What is HIPPA?The HIPAA Privacy Rule applies to health plans, healthcare clearinghouses, and healthcare providers who conduct some medical transactions electronically. It establishes national standards to safeguard people's medical records and other personal health information.
Your physician will need a HIPAA consent and release form from you before sharing your PHI and ePHI with the insurance companies covering your medical expenses.
Therefore, the correct option is d.requirements to ensure only authorized individuals access EPHI.
To learn more about HIPPA, refer to the link:
https://brainly.com/question/14305829
#SPJ1
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive File Definition
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option. The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files athttps://brainly.com/question/15355917.
#SPJ4
give 4 example for echinodermis cnidarians poriferas platyhilminthes nematodes and annerids
Answers
Answer:
Among the largest and most important invertebrate phyla are Porifera (sponges), Cnidaria (jellyfish, corals, and sea anemones), Platyhelminthes (flatworms), Nematoda (roundworms), Mollusca (snails, bivalves, squids, and octopuses), Annelida (segmented worms), Arthropoda (horseshoe crabs, spiders, crabs, centipedes, ..
What is logistics?
The commercial activity of transporting
Answers
Answer:
ctycricyyitc57ou5ir57ir56ir75ie65ie56ie65ie65ur65r65ie65urytie
valueerror empty vocabulary perhaps the documents only contain stop words
Answers
It seems that you are encountering a ValueError related to an empty vocabulary when processing documents.
This error usually occurs when the documents you are working with only contain stop words or no words at all. Stop words are common words that carry little meaningful information, such as "the", "and", or "in". Many text processing tools filter out stop words to focus on more significant words that better represent the content of the documents. If all the words in a document are stop words, the resulting vocabulary becomes empty, leading to the ValueError you mentioned.
To resolve this issue, you may want to consider the following steps:
1. Check your documents to ensure they contain meaningful content with more than just stop words.
2. Reevaluate the stop words list you are using. It might be too extensive, causing the removal of important words from the documents.
3. Modify your text processing pipeline to better handle cases with a high percentage of stop words or empty documents.
By addressing these points, you can improve the quality of your vocabulary and avoid the ValueError associated with an empty vocabulary. Remember that a robust and diverse vocabulary is crucial for accurate text analysis and understanding the context of the documents.
Learn more about text processing :
https://brainly.com/question/14933547
#SPJ11