What's the value of this Python expression? ((10 >= 5*2) and (10 <= 5*2))
Answers
Answer:
1 (true)
Explanation:
10 == 10 is valid=> 10 >= 10 is valid => 10 >=(5*2) is valid
10 == 10 is valid=> 10 <= 10 is valid => 10 <=(5*2) is valid
=> ((10 >= 5*2) and (10 <= 5*2)) is valid => Return 1 or True
Related Questions
5
Sondra is working on improving her skills with a specific painting style by using techniques such as soft or misty focus, added brush strokes,
color tinting, and marrying two or more images together to form a composite. What style of painting is Sondra working on improving?
O A. editorialism
OB. pictorialism
OC. impressionism
OD. tonalism
Answers
The style of painting is Sondra working on improving is known to be option d: pictorialism
What does pictorialism mean in art?Pictorialism is known to be a method in photography that tells more about beauty of subject matter, as well as the tonality, and makeup instead of the documentation of reality.
Hence, The style of painting is Sondra working on improving is known to be option d: pictorialism because Sondra is working on improving her skills with as soft or misty focus, added brush strokes, color tinting, and others.
Therefore, option B is correct.
Learn more about pictorialism from
https://brainly.com/question/27329670
#SPJ1
Answer: 1. genres
2. Tonalism
3. Experts claimed they had altered the photographs too much to qualify as journalism
4. special software
5. photojournalism
6. Editorial photography
7. photojournalism
8. Tonalism
9. Remaining virtually unseen
10. Ethical rules
11. Acknowledge them with a smile or nod
12. High-quality reproductions of the works of early American art photographers
13. Documentary photography and photojournalism
14. The right to privacy of the subjects
15. Visualize the image first
Explanation: Took the test
Python question
The following code achieves the task of adding commas and apostrophes, therefore splitting names in the list. However, in the case where both first and last names are given how would I "tell"/write a code that understands the last name and doesn't split them both. For example 'Jack Hansen' as a whole, rather than 'Jack' 'Hansen'.
names = "Jack Tomas Ponce Ana Mike Jenny"
newList = list(map(str, names.split()))
print(newList) #now the new list has comma, and apostrophe
Answers
Answer:
You can use regular expressions to match patterns in the names and split them accordingly. One way to do this is to use the re.split() function, which allows you to split a string based on a regular expression.
For example, you can use the regular expression (?<=[A-Z])\s(?=[A-Z]) to match a space between two capital letters, indicating a first and last name. Then use the re.split() function to split the names based on this regular expression.
Here is an example of how you can use this approach to split the names in your list:
(Picture attached)
This will give you the output ['Jack', 'Tomas', 'Ponce', 'Ana', 'Mike', 'Jenny', 'Jack Hansen']. As you can see, the name "Jack Hansen" is not split, as it matches the pattern of first and last name.
It's worth noting that this approach assumes that all first and last names will have the first letter capitalized and the last names capitalized too. If this is not the case in your data, you may need to adjust the regular expression accordingly.

To classify wireless networks by coverage, which of the following are wireless networks?
A- WPAN
B-WLAN
C- WMAN
D- WWAN
Answers
Answer:
B -WLAN
Explanation:
Use the edit icon to pin, add or delete clips.
what is information
Answers
Answer:
Information can be thought of as the resolution of uncertainty; it is that which answers the question of "What an entity is" and thus defines both its essence and the nature of its characteristics. The concept of information has different meanings in different contexts.
Explanation: idek if that helps let me kno
In which of the following situations must you stop for a school bus with flashing red lights?
None of the choices are correct.
on a highway that is divided into two separate roadways if you are on the SAME roadway as the school bus
you never have to stop for a school bus as long as you slow down and proceed with caution until you have completely passed it
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school bus
Answers
The correct answer is:
on a highway that is divided into two separate roadways if you are on the OPPOSITE roadway as the school busWhat happens when a school bus is flashing red lightsWhen a school bus has its flashing red lights activated and the stop sign extended, it is indicating that students are either boarding or exiting the bus. In most jurisdictions, drivers are required to stop when they are on the opposite side of a divided highway from the school bus. This is to ensure the safety of the students crossing the road.
It is crucial to follow the specific laws and regulations of your local jurisdiction regarding school bus safety, as they may vary.
Learn more about school bus at
https://brainly.com/question/30615345
#SPJ1
all foreign language results should be rated as fails to meet. True or false?
Answers
All foreign language results should be rated as fails to meet. This statement is true. Thus, option (a) is correct.
What is languages?
The term language refers to the spoken and written. The language is the structure of the communication. The language are the easily readability and understandability. The language are the component are the vocabulary. The language is the important phenomenon of the culture.
According to the languages are to explain the all the foreign languages are to learn in the study in the learning habits. But there is not the easy to learn. There are the must easy to the interest of to learn foreign languages.
As a result, the foreign language results should be rated as fails to meet. This statement is true. Therefore, option (a) is correct.
Learn more about on language, here:
https://brainly.com/question/20921887
#SPJ1
How will quantum computing affect artificial intelligence applications
Answers
Answer:
it is very helpful
Explanation:
Quantum computing opens the door potentially solving very large and complex computational problems that are basically impossible to solve on traditional computers.
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
Design a program that prompts the user to enter a number within the range of 1 through 10. The program should display the Roman numeral version of that number. If the number is outside the range of 1 through 10, the program should display an error message.write a pseudocode and draw a flow chart using the right diagrams and shapes
Answers
Answer:
Pseudocode:
Prompt the user to enter a number between 1 and 10
Read the input from the user
If the input is between 1 and 10, continue to step 4. Otherwise, display an error message and end the program.
Create an array of roman numerals I, II, III, IV, V, VI, VII, VIII, IX, X
Subtract 1 from the input number and use it as an index to retrieve the corresponding roman numeral from the array
Display the roman numeral to the user
End the program
Flowchart:
[Start] --> [Prompt user to enter a number] --> [Read input]
--> {input between 1 and 10?}
--> [Create array of roman numerals]
--> [Subtract 1 from input and use as index to retrieve corresponding roman numeral]
--> [Display roman numeral to user] --> [End]
--> [Display error message and end] --> [End]
Explanation:
Imagine that you have an image that is too dark or too bright. Describe how you would alter the RGB settings to brighten or darken it. Give an example.
Answers
Which feature enables you to make changes to all the slides of your presentation at the same time?
O A. Themes
• B. Slide Master
O C. Animations
O D. Background
Answers
Answer:
B
Explanation:
In PowerPoint, Slide Master allows you to modify all of your slides at the same time.
Question 24 Multiple Choice Worth 5 points)
(01.04 MC)
Zavier needs to compress several files. Which file type will allow him to do this?
ODOC
GIF
OJPG
O ZIP
Answers
Answer:
ZIP
Explanation:
ZIP is a type of compression file as Jpg is a picture file, Gif is a picture file, and ODOC stands for Oklahoma Department of Corrections
TBH:
it may be O ZIP but i've never heard of it.
Answer:
Zip (D)
Explanation:
Took The Test
In which sections of your organizer should the outline be located?
Answers
The outline of a research proposal should be located in the Introduction section of your organizer.
Why should it be located here ?The outline of a research proposal should be located in the Introduction section of your organizer. The outline should provide a brief overview of the research problem, the research questions, the approach, the timeline, the budget, and the expected outcomes. The outline should be clear and concise, and it should be easy for the reader to follow.
The outline should be updated as the research proposal evolves. As you conduct more research, you may need to add or remove sections from the outline. You may also need to revise the outline to reflect changes in the project's scope, timeline, or budget.
Find out more on outline at https://brainly.com/question/4194581
#SPJ1
Question #2
Multiple Select
Hofstede's cultural dimensions describe
Select 2 options
how the world's cultures share six similar values
how the world's cultures differ in six main ways
how different cultures should strive to become the same
how some cultures are better than others
ualistic than
Answers
Hofstede's cultural dimensions describe how the world's cultures differ in six main ways and how different cultures should strive to become the same.
What are the scale of lifestyle and its influences?According to Hofstede, the 5 principal dimensions are identity, power, gender, uncertainty, and time. You can reflect on consideration on cultural fee dimensions on a scale or a continuum, in which one element of the fee lies on one aspect of the dimensions and the opposite intense lies at the opposite give up of the dimensions.
To run VBA withinside the “Microsoft Visual Basic for Applications” window, you can surely press the “F5” key button or click on on the “Run” icon withinside the toolbar.The Visual Basic button opens the Visual Basic Editor, in which you create and edit VBA code. Another button on the Developer tab in Word and Excel is the Record Macro button, which routinely generates VBA code that may reproduce the actions that you perform withinside the application.Read more about the Hofstede's cultural dimensions :
https://brainly.com/question/7158663
#SPJ1
Answer:
-how the world’s cultures differ in six main ways
-how some cultures are more individualistic than others
Explanation:
ED22
Need some help with Discrete Mathmatics please help urgent?

Answers
Answer: 2, 4, 1, 5, 3
Explanation:
P: Arguments are not arranged in regular order like the one I am used to
Q: I cannot understand ~Q: I can understand
R: I grumble ~R: I do not grumble
S: Get a headache
T: Examples are not easy
Here is the logic order of the given sentences:
2) P
4) P → Q
1) ~Q → ~R
5) ~R → S
3) S → T
∴) T
In this lab, your task is to configure internet explorer's settings as follows: configure how cookies are handled as follows: accept first-party cookies. block third-party cookies. always allows session cookies. configure an exception to always allow cookies from mybank. allow pop-ups when managing your money through mybank. set a blocking level for all other pop-ups to high. add additional internet security by setting the security level for the internet zone to high.
Answers
I configured Internet Explorer's settings to accept first-party cookies, block third-party cookies, always allow session cookies, allow pop-ups when managing my money through my bank, and set a high blocking level for all other pop-ups. Additionally, I added additional internet security by setting the security level for the internet zone too high.
Configuring Internet Explorer Settings for Enhanced Security and Pop-up ManagementOpen Internet Explorer.Click the Tools icon and select Internet Options.Click the Privacy tab.Under the Cookies section, select the Advanced button.Under the First-party Cookies section, select the radio button for "Accept".Under the Third-party Cookies section, select the radio button for "Block".Check the box next to "Always allow session cookies".Click the Manage Exceptions button.Add an exception for "mybank.com" with the radio button for "Allow".Click the OK button.Under the Pop-up Blocker section, select the radio button for "Allow pop-ups when managing your money through mybank".Select the radio button for "High" under the Pop-up Blocker Settings section.Click the Security tab.Select the slider for Internet to the "High" position.Click the OK button.Learn more about Database: https://brainly.com/question/518894
#SPJ4
1. Write an algorithm to ask someone's
name and welcome her/him.
Answers
Answer:
user_name = input( "Enter your name:" )
print "Hello," , user_name
Explanation:
I made a Tesla account login ...
If my answer is incorrect, pls correct me!
If you like my answer and explanation, mark me as brainliest!
-Chetan K

Speeding is one of the most prevalent factors contributing to traffic crashes.
A. TRUE
B. FALSE
Answers
Answer:
A true
Explanation:
Speeding leads to an increase in the degree of crash severity, possibly resulting in more fatalities or injuries. More damage is caused to the vehicles involved at higher speeds, increasing likelihood vehicle will not be drivable after a crash.
The statement "Speeding is one of the most prevalent factors contributing to traffic crashes" is true.
What is speeding?Speeding causes crashes to be more severe, which could lead to more fatalities or injuries. Higher speeds result in more damage to the involved vehicles, increasing the risk that the vehicle won't be drivable following a collision. There are many accidents increasing because of high speed.
The term "speeding" refers to moving or traveling swiftly. He paid a penalty for speeding. For many American drivers, speeding has become the standard, whether it is going over the posted speed limit, driving too quickly for the road conditions, or racing. Nationwide, speeding contributes to road fatalities.
Therefore, the statement is true.
To learn more about speeding, refer to the link:
https://brainly.com/question/15297960
#SPJ2
8. Following your organization's rules when using the Internet is an example of
A. a digital right.
OB. empathy.
O C. catfishing.
O D. digital responsibility.
Answers
Following your organization's rules when using the Internet is an example of D. digital responsibility.
What is Digital Responsibility?This refers to the term that is used to describe and define the use of technology in a responsible and beneficial manner for both oneself and others. It includes managing a wide range of moral dilemmas pertaining to, among other things, "the digital gap," transparency, net neutrality, privacy, and other difficulties.
Hence, it can be seen that option D is an example of digital responsibility.
Read more about digital responsibility here:
https://brainly.com/question/27832386
#SPJ1
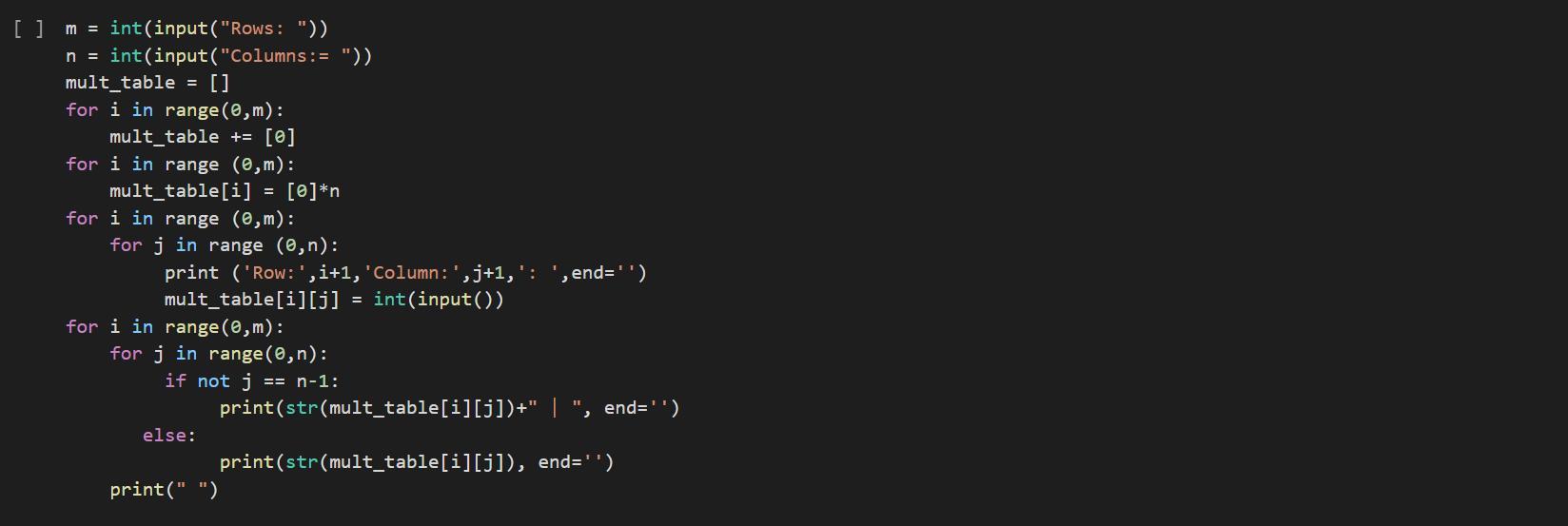
Print the two-dimensional list mult_table by row and column. Hint: Use nested loops.
Sample output with input: '1 2 3,2 4 6,3 6 9':
1 | 2 | 3
2 | 4 | 6
3 | 6 | 9
Must be in Python
Answers
Answer:
m = int(input("Rows: "))
n = int(input("Columns:= "))
mult_table = []
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
Explanation:
The next two lines prompt for rows and columns
m = int(input("Rows: "))
n = int(input("Columns:= "))
This line declares an empty list
mult_table = []
The following two iterations initializes the list
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
The next iteration prompts and gets user inputs for rows and columns
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
The following iteration prints the list row by row
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
In this exercise we have to use the knowledge of computational language in python to describe a code, like this:
The code can be found in the attached image.
To make it easier the code can be found below as:
m = int(input("Rows: "))
n = int(input("Columns:= "))
mult_table = []
for i in range(0,m):
mult_table += [0]
for i in range (0,m):
mult_table[i] = [0]*n
for i in range (0,m):
for j in range (0,n):
print ('Row:',i+1,'Column:',j+1,': ',end='')
mult_table[i][j] = int(input())
for i in range(0,m):
for j in range(0,n):
if not j == n-1:
print(str(mult_table[i][j])+" | ", end='')
else:
print(str(mult_table[i][j]), end='')
print(" ")
See more about python at brainly.com/question/26104476
ASAP PLZ!!!. Which command group is used to apply effects and modify color schemes of SmartArt graphics?
Reset Graphics
SmartArt Styles
Graphic Layouts
Create Graphics
NVM!! The answer is B. SmartArt Styles
Answers
Answer:
I think I am wrong but I assume it is C. Graphic Layout Sorry if I am wrong but if I am not please reward me brainlist.
How many subnets and host per subnet are available from network 192.168.43.0 255.255.255.224?
Answers
It should be noted that the number of subnets and hosts available from network 192.168.43.0 255.255.255.224 is 8 and 32, respectively. Only 30 of the 32 hosts are generally functional.
What is a host in computer networking?A network host is a computer or other device that is connected to a computer network. A host can serve as a server, supplying network users and other hosts with information resources, services, and applications. Each host is given at least one network address.
A computer network is a group of computers that share resources on or provided by network nodes. To communicate with one another, computers use common communication protocols over digital links.
So, in respect to the above response, bear in mind that we may compute the total number of: by putting the information into an online IPv4 subnet calculator.
8 subnets; and30 hosts available for 192.168.43.0 (IP Address) and 255.255.255.224 (Subnet)
Learn more about hosts:
https://brainly.com/question/14258036
#SPJ1
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under which of the following?
Answers
The issue “when a user deletes the data, whether all the copies are deleted or not is something that every needs to have a clear answer to” comes under aspect of data deletion and data lifecycle management.
What is the deletion?One need rules and practices to delete data to follow privacy laws, protect data, and meet user expectations. When a user gets rid of data, it is important to check if all copies of that data have been effectively removed from the system or storage.
Data Retention Policies: Organizations must create clear rules about how long they will keep certain data before getting rid of it.
Read more about deletion here:
https://brainly.com/question/30280833
#SPJ1
what would players do in Mobile legends bang bang report you for while playing The game
Answers
Answer:
For being Annoying
Explanation: because that game sucks.
To have integrity means that you
Answers
Code to be written in R language:
The Fibonacci numbers is a sequence of numbers {Fn} defined by the following recursive relationship:
Fn= Fn−1 + Fn−2, n > 3
with F1 = F2 = 1.
Write the code to determine the smallest n such
that Fn is larger than 5,000,000 (five million). Report the value of that Fn.
Answers
Here is the R code to determine the smallest n such that the Fibonacci number is larger than 5,000,000:
fib <- function(n) {
if (n <= 2) {
return(1)
} else {
return(fib(n - 1) + fib(n - 2))
}
}
n <- 3
while (fib(n) <= 5000000) {
n <- n + 1
}
fib_n <- fib(n)
cat("The smallest n such that Fibonacci number is larger than 5,000,000 is", n, "and the value of that Fibonacci number is", fib_n, "\n")
The output of this code will be:
The smallest n such that Fibonacci number is larger than 5,000,000 is 35 and the value of that Fibonacci number is 9227465.
Learn more about R language here: https://brainly.com/question/14522662
#SPJ1
12.2 E-Z LOAN
A loan obtained from a lending institution is typically paid off over time using equal monthly payments over a term of many months. For each payment, a portion goes toward interest and the remaining amount is deducted from the balance. This process is repeated until the balance is zero. Interest is calculated by multiplying the current balance by the monthly interest rate, which is usually expressed in terms of an Annual Percentage Rate (APR). This process produces an Amortization Schedule where the amount applied to interest is gradually reduced each month and the amount applied to the balance grows. For example, the following amortization schedule is for a loan of $ 10.000 at an APR of 3.9% over a term of 30 months:3 will match months 12, 24, and 30 respectively.
Answers
Following an amortization schedule, the monthly payments will be $350.39 and the total payment in 30 months will be $10511.7.
How much should be paid monthly to complete loan payment in 30 months?The loan payment follows an amortization schedule where the amount applied to interest is gradually reduced each month and the amount applied to the balance grows.
The amounts to be paid is calculated using the amortization formula:
P = a ÷ {{[(1 + r/n)^nt] - 1} ÷ [r/n(1 + r/n)^nt]}where
P is monthly paymenta is credit amountr is the interest ratet is the time in yearsn is number of times the interest is compoundedFor the loan of $10000;
a = $10000r = 3.9% = 0.039nt = 30 monthsHence,
P = $10000 ÷ {{[(1 + 0.039/12)^60] - 1} ÷ [0.039/12(1 + 0.0.039/12)^60]}
P = $350.39 per month
Total payment in 30 months = $350.39 × 30 = $10511.7
Therefore, the monthly payments will be $350.39 and the total payment in 30 months will be $10511.7.
Learn more about amortization schedule at: https://brainly.com/question/26433770
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
What are the dominant InfoSec-related credentials used to document knowledge and/or experience?
Answers
Answer:
One of the most widely cited information security certifications is the Certified Information Systems Security Professional (CISSP), offered by the International Information Systems Security Certification Consortium (ISC)2[1].
A function checkZeros accepts three double parameters. It checks to see if the sum of all three parameters is equal to zero. If this sum is equal zero, the function returns true, otherwise the function returns false. 1. Give an example CALL from main: 2. Write the prototype for the function: 3. Write down the definition (header and body) for the function.
Answers
Answer:
Explanation:
The following code is written in Java. It creates the interface/prototype, the function, and the main method call. The function takes in the three int parameters, adds them, and then checks if the sum equals zero, outputting the correct boolean value. Output can be seen in the picture attached below. Due to technical difficulties I had to add the code as a txt file below.
