What Windows Server 2016 roles or features do you need to install on a server if you will be deploying Hyper-V containers
Answers
To deploy Hyper-V containers on a server running Windows Server 2016, you need to install the Hyper-V role and the Containers feature.
Which roles or features are necessary for deploying Hyper-V containers on a Windows Server 2016?Hyper-V containers require the installation of the Hyper-V role and the Containers feature on a server running Windows Server 2016. The Hyper-V role provides the necessary virtualization capabilities, allowing the creation and management of virtual machines. The Containers feature enables the use of Windows containers, which are lightweight, isolated environments for running applications.
With the Hyper-V role installed, you can create and manage virtual machines that host the container instances. The Containers feature, on the other hand, provides the necessary components for running Windows containers, including the container runtime and management tools.
By installing both the Hyper-V role and the Containers feature, you ensure that your Windows Server 2016 server is ready to deploy and manage Hyper-V containers effectively.
Learn more about Hyper-V containers
brainly.com/question/31075744
#SPJ11
Related Questions
5. If the stock currently sells for $30.70 per share, what is the price-earnings ratio? Display keyboard shortcuts for Rich Content Editor
Answers
The price-earnings ratio would be approximately 12.28.
To calculate the price-earnings (P/E) ratio, you need to know the company's earnings per share (EPS) and the current stock price per share. Without information on the company's EPS, it is not possible to calculate the P/E ratio.
Assuming we have the necessary information, the formula for calculating the P/E ratio is:
P/E ratio = Current stock price per share / Earnings per share (EPS)
For example, if the current stock price per share is $30.70 and the EPS is $2.50, the P/E ratio would be:
P/E ratio = $30.70 / $2.50 = 12.28
Therefore, the price-earnings ratio would be approximately 12.28.
Keyboard shortcuts for Rich Content Editor:
To bold text: Ctrl+B (Windows) or Cmd+B (Mac)
To italicize text: Ctrl+I (Windows) or Cmd+I (Mac)
To underline text: Ctrl+U (Windows) or Cmd+U (Mac)
To insert a link: Ctrl+K (Windows) or Cmd+K (Mac)
To insert an image: Ctrl+Alt+F (Windows) or Cmd+Option+F (Mac)
To align text left: Ctrl+L (Windows) or Cmd+L (Mac)
To align text center: Ctrl+E (Windows) or Cmd+E (Mac)
To align text right: Ctrl+R (Windows) or Cmd+R (Mac)
To create a bulleted list: Ctrl+Shift+8 (Windows) or Cmd+Shift+8 (Mac)
To create a numbered list: Ctrl+Shift+7 (Windows) or Cmd+Shift+7 (Mac)
Learn more about price-earnings here:
https://brainly.com/question/15520260
#SPJ11
First time using this site so be mindful if I make any mistakes
For Micro Econ AP I am having a problem with this one question
It goes:
In what ways do households dispose of their income? How is it possible for a family's persoal consumption expenditures to exceed its after-tax income?
Answers
Answer:
Okay... Well
I will. help you out dear
List the steps to look it install and then run a program or mobile app
Answers
Answer:
1. Open a cloud installer (the source), which is usually Play Store, Aptoide, or UpToDown, in the case of Android phones.
2. Request the package from the server, which will be transmitted via an internet connection. Usually called "downloading".
3. Allow the package provider (mobile store) to install the app on the system, this being the "install" part, where it's put together.
4. Run the app by, usually, pressing the icon in the app drawer.
PLEASEEE HELP HURRY

Answers
To start searching for a scholarly article on G. o. ogle Scholar, you should:
"Type the title of the article or keywords associated with it." (Option A)
What is the rationale for the above response?Here are the steps you can follow:
Go to Go. o. gle Scholar website In the search box, type the title of the article or relevant keywords associated with it.Click the "Search" button.Browse through the search results to find the article you are looking for.Click on the title of the article to view the abstract and other details.If the article is available for free, you can download or access it directly from the search results page. If not, you may need to purchase or access it through a library or other academic institution.Note that you can also use advanced search options and filters available on Go. ogle Scholar to narrow down your search results based on various criteria, such as publication date, author, and journal.
Learn more about G. o. ogle at:
https://brainly.com/question/28727776
#SPJ1
Suppose most hotels in a city offer only basic cable TV. If a
hotel offered premium cable channels like HBO, that feature would
be considered
O A. qualifier
O B. booster
O c. filter
O D. winner
O E. c
Answers
If a hotel in a city offers premium cable channels like HBO while most hotels only provide basic cable TV, this feature would be considered a booster. The option B is correct.
In the given scenario, most hotels in the city provide basic cable TV, implying that the availability of premium cable channels like HBO is not a common offering. In this context, the term "booster" accurately describes the feature. A booster is something that enhances or improves the value or attractiveness of a product or service.
By offering premium cable channels like HBO, the hotel sets itself apart from its competitors and provides an additional benefit to its guests. This feature can serve as a selling point, attracting customers who desire access to a wider range of entertainment options during their stay. Therefore, option B, "booster," is the most suitable choice in this situation.
Learn more about cable here:
https://brainly.com/question/10932960
#SPJ11
Conditional statements are useful to computer programmers because
A) they eliminate extra coding by reuse of materials.
B) they allow programmers to set conditions to be met for an action to take place.
C) they use shorthand symbols to represent quantities.
D) they are predefined for each programming language.
Answers
Answer:
Option B is correct.
Explanation:
Let look at each statement
A) No, Conditional statement do not eliminate extra code by reuse.
B) Yes, it allow programmers to set conditions to be met for an action to take place. so this option is correct.
C) No, shorthand symbols are not used to represent quantities.
D) No, They are not Predefined for each programming Language.
Answer:
the answer is B, The Second Opinion
Explanation:
the Conditional Statement or in other words the if Statement is used in a code to set conditions so when the need of the function is met true, then the code can execute the function.
what is the answer in online learning and digitalcitizenship

Answers
Answer: an online encyclopedia.
Explanation: encyclopedias often have constantly updated pieces of news, that are also accompanied by fact-checkers as well unlike newspapers.
Corinne would like to click on the link at the bottom of a Web page but she only sees the top portion of the page. She should _____. A.click twice on the status bar
B.use the scroll bar to scroll down to the bottom of the page
C.click on the back button
D.click on the display window and drag it up
Answers
Answer:
B
Explanation:
from 3dg3
Answer:
D.click on the display window and drag it up
Student B, lives in Phoenix, Arizona and is not on vacation. Student B, submits an assignment for science class and the teacher notices the student IP address is 1.4.127.255. Has this student committed one of the forms of plagiarism?
Answers
Answer:
Don't take this for your answer though, but no unless the student copied it off of somewhere else.
The IP address might have been spoofed or they could have used a vpn.
Otherwise it would mean that someone else used their account to sign in.
Explanation:
what policy/procedure must be signed by new hires at orientation and by all employees who ask for access to the corporate vpn using mobile devices
Answers
When new hires attend their orientation at a company, they are required to sign several policies and procedures that govern their behavior while employed. These policies and procedures are designed to ensure the safety and security of the company's assets and data.
In this context, one policy that must be signed by new hires and all employees who request access to the corporate VPN using mobile devices is the VPN Access Policy. The VPN Access Policy is a document that outlines the rules and guidelines for employees who want to access the company's Virtual Private Network (VPN) using their mobile devices. This policy sets out the requirements for employees to use the VPN securely and responsibly, including the installation of required software, adherence to password policies, and prohibitions against unauthorized access and sharing of company information. By signing this policy, employees agree to follow these guidelines and protect the company's data and network.
In conclusion, the VPN Access Policy is a critical policy that new hires must sign at orientation, and all employees who want to access the corporate VPN using mobile devices must sign and adhere to it. By following this policy, employees can securely access the company's network while protecting its assets and data. Failure to follow this policy may result in disciplinary action, up to and including termination.
To learn more about VPN, visit:
https://brainly.com/question/26327418
#SPJ11
a. Write a qbasic program to generate the following series: 1, 4, 9, 16, 25
b. 5, 25, 125, 625, 3125
(urgent need for project work.)
Answers
Here's a QBasic program to generate the series:
Series of squares:
css
Copy code
FOR i = 1 TO 5
PRINT i * i;
NEXT i
Output: 1 4 9 16 25
Series of powers of 5:
css
Copy code
x = 5
FOR i = 1 TO 5
PRINT x;
x = x * 5
NEXT i
Output: 5 25 125 625 3125
In the first program, we use a loop to iterate through the values 1 to 5, and for each value of i, we calculate its square and print it to the console.
In the second program, we set the variable x to 5, and then use a loop to iterate through the values 1 to 5. For each value of i, we print the current value of x, and then update x by multiplying it by 5. This gives us a sequence of powers of 5.
What are examples of criteria used in conditional formatting? Check all that apply.
less than
equal to
added to
divided by
greater than
multiplied by
Answers
Answer:
- Less than
- Equal to
- Greater than
Explanation:
First, I'll assume this question relates to Microsoft Office Excel.
From the list of given options, only Less than, Equal to and Greater than can be said to be instances of conditional formatting.
The essence of conditional formatting is to compare values of selected cells or cells with another value;
Take for instance;
- if cellB10 is less than 2
- if cellB11 is equal to 2
- if cellB13 is greater than 2
.....And so on
To access the conditional formatting tools;
- You need to highlight the cells to format
- Select Conditional Format from Styles option on the Home tab
- Select Highlight Cells Rules
- Select format type (e.g. greater than, less than, etc.)
- Enter format value and how you want it to be formatted
- Press OK
What two factors make up the skills of a good typist
Answers
Answer:
I feel to be a good typist one would have to have a good grasp of reading, grammar, and the ability to make errors to a lesser degree than more so. I can type, myself, 120-150 wpm with an error rate of 0-2. I also have the ability of not having to look at the keyboard as I type, and have a good eye on catching errors.
Explanation:
What is the full meaning of BCC?
Answers
Answer: Blind Carbon Copy(BCC) means Email address of the recipients specified in this field do not appear in the received message header and the recipients in the To or Cc fields will not know that a copy sent to these address.
Activity Sheet 2
A.Illustrate how to create the object below using draw and modify commands.
Answers
Answer:
Vjfxfffccvvvvvv
Explanation:
Hgvjhgxxgyjjbvccjkn Hugh bună vvvvhg un www buukbbchfcvbvc. Hggvhhvbhchgx
Need help! Brain list to anyone who responses quick.

Answers
Detail loop tasks, also known as iterative tasks or repetitive tasks, serve the purpose of executing a specific set of instructions multiple times.
These tasks are designed to repeat a block of code or a series of actions until a certain condition is met or a specific number of iterations are completed.
The purpose of detail loop tasks can vary depending on the context and the specific requirements of the program or problem at hand. Some common purposes of detail loop tasks include:
Process large sets of data.Perform calculations or computations.Validate or filter data.Control program flow.User interaction and input handling.Thus, the purpose of detail loop tasks is to automate repetitive operations, streamline data processing, control program flow, and handle user interactions efficiently.
For more details regarding data processing, visit:
https://brainly.com/question/30094947
#SPJ1
requires that a completed transaction, once committed, becomes part of the database and is not reversible. select one: a. atomicity b. consistency c. isolation d. durability
Answers
The property that requires a completed transaction to be permanent and non-reversible once committed is called durability.
Durability is one of the four key properties of a transaction, also known as the ACID properties, which stands for Atomicity, Consistency, Isolation, and Durability. Durability ensures that once a transaction is successfully completed, the changes made to the database will be saved and available even in the event of a system failure or crash. In other words, once the database system confirms that a transaction is successfully committed, it guarantees that the changes made will be persisted permanently and will not be lost due to any failure.To know more about durability visit:
https://brainly.com/question/18800411
#SPJ1
An Emergency Action Plan (EAP) does which of the following?
the answers are
A assigns responsibility to thise affected and outlines evacuation routes
C Identifies emergencies that might reasonably occur and provides procedures for alerting people about the emergency
D identifies medical responses options and designate an assembly area
E labels the types of equipment present at the worksite
Answers
Answer:
A
Explanation:
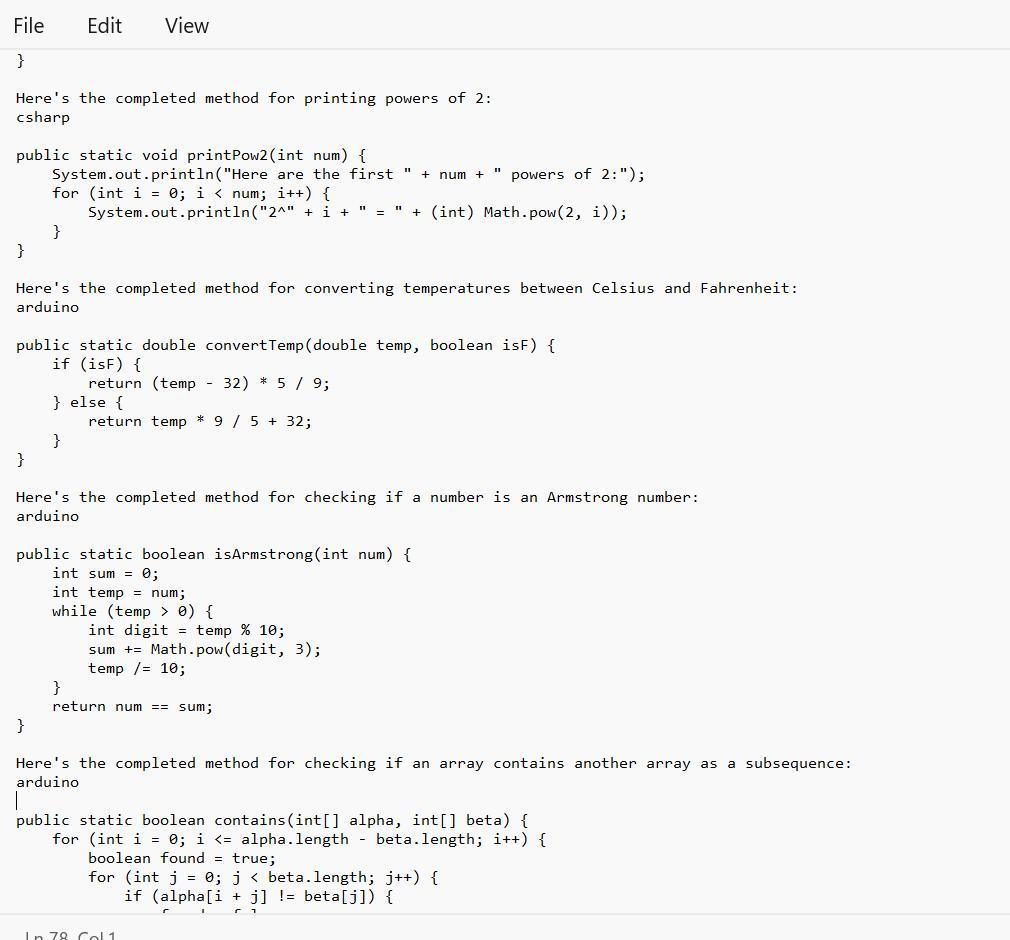
I think u should try A because EAP does itJava Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


a good technique for choosing a password is to use the first letter of each word of a phrase.
Answers
Using the first letter of each word in a phrase is a good technique for creating strong passwords. This technique, often called the passphrase method, is effective for choosing secure passwords because it creates a seemingly random combination of characters, while remaining memorable for the user.
This technique is known as passphrase or mnemonic password, and it makes it easier to remember complex passwords. The passphrase should include a mixture of upper and lowercase letters, numbers, and special characters. For instance, the phrase "I love to eat pizza every Friday" could be transformed into the password "ILtepeF". This password is strong because it is not a dictionary word, and it is not easily guessable by attackers.
It is essential to avoid common phrases or expressions, as they are more likely to be used by attackers in their password cracking attempts. Additionally, using a different passphrase for each account is critical to prevent a data breach in case one of your passwords is compromised. Remember, passwords are the first line of defense against cyber attacks, so it is vital to create strong and unique ones to keep your sensitive data safe.
Learn more about cyber attacks here:
https://brainly.com/question/29997377
#SPJ11
how many layer masks can a single layer have applied without using groups or smart objects?
Answers
A single layer can have only one layer mask applied without using groups or smart objects.
What is a layer mask?A layer mask is a tool used in digital image processing to separate and control the transparency of a layer. A layer mask is a grayscale picture, with white areas being opaque, black areas being transparent, and gray areas being semi-transparent.
The layer mask is used to control the transparency of a layer, allowing the layer beneath it to show through the opaque portions of the layer mask. Layer masks are also used to modify the transparency of a layer, allowing you to create a gradient effect across a layer.
Learn more about layer mask at
https://brainly.com/question/9176110
#SPJ11
Which tab can be used to change the theme and background style of a presentation?

Answers
Answer:
Design IS the correct answer
Explanation:
Suzanne Brett wants to borrow $55,000 from the bank. The interest rate is 6.5% and the term is for 5 years.
What is the yearly payment amount?
Answers
Answer:
$14575
Explanation:
$550006.5%5 yearsTotal payment amount:
$55000+5*6.5%= $55000 +32.5%= $55000 *1.325= $72875Yearly payment:
$72875/5= $14575Answer:
$3,575
Explanation:
how often should you backup the data on your computer
Answers
It is highly recommended to backup your computer data on a regular basis in order to prevent the loss of important data due to a system crash or hardware failure.
The frequency of backups depends on the amount and type of data that needs to be backed up and the importance of the data.
For example, if you work with sensitive data, it's important to backup your data daily or every time there is a change. On the other hand, if you don't use your computer much and have minimal data stored on it, you might only need to backup your data once every few weeks or months.
Some people prefer to backup their data once a week, while others prefer to backup their data daily. It ultimately depends on your own personal preferences and how important your data is to you. Regardless of how often you choose to backup your data, it's important to store the backup in a secure location, such as an external hard drive or cloud storage.
Learn more about backups at
https://brainly.com/question/30826635
#SPJ11
When is the possibility of solar weather affecting terrestrial weather the highest?(1 point)
during solar minimum
during solar minimum
during the solar cycle
during the solar cycle
during solar maximum
during solar maximum
during Total Solar Irradiance
during Total Solar Irradiance
Answers
The possibility of solar weather affecting terrestrial weather the highest is option c: during solar maximum.
Does solar weather have an effect on terrestrial weather?There are different forms of weather on Earth, this is one that ranges from the surface of the planet out unto the outer space.
Note that Space weather as well as terrestrial weather are known to be influenced by the little alterations that the Sun undergoes during its solar cycle.
Hence, The possibility of solar weather affecting terrestrial weather the highest is option c: during solar maximum.
Learn more about solar weather from
https://brainly.com/question/15279276
#SPJ1
what is computer hardware
Answers
Answer:
stuff like a mouse or a keyboard and that kind of stuff
A _________________ operating system accepts random enquires from remote locations and provides an instantaneous response
Answers
Answer:
Real-time operating system (RTOS) are
Explanation:
Real-time operating system (RTOS) are operating systems that are meant for use with time sensitive applications and systems that have very strict time requirements such as in computers serving air traffic control systems, robot systems, or missile control systems.
The processing time for each process are in the order of tenths of a second or shorter time frames using given constraints.
Real-time systems are applied in life saving systems like parachutes or air bags so as to prevent injuries in the event of an accident.
Which of the following are characteristics of spyware? (Choose all that apply.) Negatively affects availably Negatively affects confidentiality Secretly collects information about users Negatively affects integrity Tracking cookies and browser history can be used by spyware It is greyware
Answers
Spyware is a type of malicious software that can negatively affect the confidentiality, availability, and integrity of a user's system. It secretly collects information about users, which can include browsing habits, keystrokes, login credentials, and personal information. This data can be used for nefarious purposes, such as identity theft, financial fraud, or targeted advertising.
Spyware can negatively affect the availability of a user's system by slowing it down, causing crashes, or blocking access to certain websites or applications. It can also negatively affect the confidentiality of a user's data by stealing sensitive information and transmitting it to third-party servers. In addition, spyware can negatively affect the integrity of a user's system by altering settings, installing additional software, or modifying files without the user's knowledge or consent. This can result in system instability, security vulnerabilities, or other unwanted consequences.
Tracking cookies and browser history can be used by spyware to monitor a user's online activity and collect information about their interests and preferences. This information can be used to deliver targeted advertisements or other types of content. Overall, spyware is considered to be a type of greyware, as it may not always be explicitly harmful or illegal, but it can still have negative consequences for users and their systems. It is important for users to take steps to protect themselves from spyware, such as using anti-malware software, practicing safe browsing habits, and avoiding suspicious downloads or email attachments.
Learn more about malicious software here-
https://brainly.com/question/14309905
#SPJ11
which of the following are true? a. avoid memory accesses entirely by using only local variables. b. try to maximize the temporal locality by using a data object as often as possible once it has been read from memory. c. focus attention on the inner loops, where the bulk of the computation and memory accesses occur. d. try to maximize the spatial locality by reading data objects sequentially, with stride 1, in the order they are stored in memory.
Answers
The performance of programs by reducing memory access times and improving cache efficiency. The given options, b, c, and d are true.
Avoiding memory accesses entirely by using only local Variables is not a feasible approach as there are some variables that need to be accessed frequently and cannot be stored locally.
Maximizing the temporal locality by using a data object as often as possible once it has been read from memory is a good approach. This is because the data object is already in the cache and can be used repeatedly without having to access memory again.
Focusing attention on the inner loops is important as this is where the bulk of the computation and memory accesses occur. Optimizing these loops can lead to significant performance improvements.
Maximizing the spatial locality by reading data objects sequentially, with stride 1, in the order they are stored in memory is another important approach. This is because it reduces the number of cache misses, as data objects are stored in contiguous memory locations and can be accessed together.
To Learn More About memory
https://brainly.com/question/28483224
#SPJ11
You are a trainer for your company and often teach courses in a classroom located on-campus or in a hotel conference room. In your office, which is separate from the classroom, you have two external monitors connected to your laptop, and you are able to display different content on each monitor. However, when teaching, you only have your laptop and a projection unit. To make teaching easier, you want the same content to show on both the laptop monitor and the projection screen.
Which of the following multiple display options would be BEST to select when teaching?
A. Show only on 1.
B. Extend these displays.
C. Show only on 2.
D. Duplicate these displays.
Answers
Answer:
Duplicate these displays.
Explanation:
A. Show only on 1 displays only the first screen and disconnects the second one
B. Extend these displays displays two different outputs on the same computer
C. Show only on 2. displays only the second screen and disconnects the first one
D. Duplicate these displays. displays the same output for both screen
Answer:d. Duplicate these displays
Explanation: